ISSUE : How what do we have to do to prevent postgres from putting a password in clear text in the audit file for a command like below alter role testrole password ‘testpassword’
It seems you might have enabled the log_statements to track the SQL statements which are getting fired on the database, unfortunately for all the values of log_statement except ‘none’ which is the default value, a password will also be logged along with the other SQL queries.
In order to avoid this, either DBA /user can use session-level value for log_statement while Creating the user /
Altering the user to change the password i.e, SET log_statement ='<value>’
Work-around 1 : If you want to skip entire User create / Alter user statement
[enterprisedb@slave bin]$ ./psql -d edb -p 5444 -U enterprisedb
psql.bin (9.5.0.5)
Type “help” for help.
edb=# set log_statement=’none’;
SET
edb=#
edb=# create user u2 with password ‘u2’;
CREATE ROLE
edb=#
Which will skip the logging of particular statements fired from the session.
Coming to the edb_audit_statement, this can’t be set at the session level and it requires reload of the server
i.,e You need to modify the pg_audit_statement value in postgresql.conf file and then reload the server .
NOTE: Reloading the server will not affect any existing connections.
To sum up the steps described till now :
1. Either modify / maintain a postgresql.conf file in such a way the value of edb_audit_statement is set to ‘none’
2. Reload the database server using the pg_ctl -D <data_directory_path> reload or using the OS level service
script.
3. Login to the database server and set the log_statement =’none’
if you have made log_statement to ‘none’ by maintaining separate postgresql.conf file along with edb_audit_statement
parameter you can skip this step.
4. Create / Alter user commands. # which will be not logged in pg_logs.
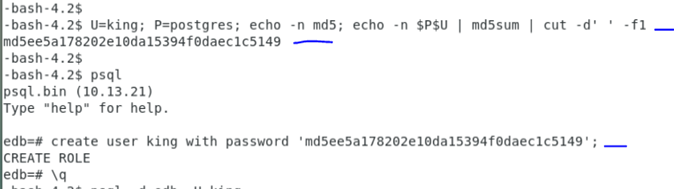
Work-around 2 : Creating encrypted password using OS level .
Other alternative method is to encrypt the password before creating /altering the user :
i.,e From OS level create the encrypted password Where U =user and P is for password
[root@localhost ~]# U=test1; P=password; echo -n md5; echo -n $P$U | md5sum | cut -d’ ‘ -f1
md565cb1da342495ea6bb0418a6e5718c38
edb=# alter user test1 with password ‘md565cb1da342495ea6bb0418a6e5718c38’ ;
ALTER ROLE
It will be the same encrypted password , which will be generated by the database server even if
you create the password in plain text format.
Work-around 3 : The Recommended way is to set the password using the below option:
edb=# create user gk1_test1 with \password
Enter new password:
Enter it again:
edb-# ;
CREATE ROLE
edb=# alter user gk1_test1 with \password
Enter new password:
Enter it again:
edb-# ;
ALTER ROLE
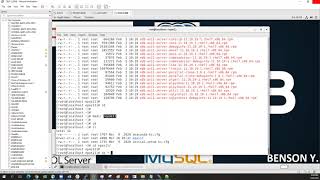
Logs :
pg_log files : It logs the command like below as enterprisedb user will generate the encrypted password using os level encryption how ever it also logs the
statement which has generated the password
time= 2017-01-16 21:34:04 IST , processs_id = 29915 : [83-1] , database = edb , username= enterprisedb , application = psql.bin , [local]LOG: 00000: statement: ALTER USER enterprisedb PASSWORD ‘md5156d6ddd36e5927a2ebdf14fb7ea031c’
time= 2017-01-16 21:34:05 IST , processs_id = 29915 : [87-1] , database = edb , username= enterprisedb , application = psql.bin , [local]LOG: 00000: statement: alter user gk1_test1 with;
edb_audit logs :
2017-01-16 21:34:04.586 IST,”enterprisedb”,”edb”,29915,”[local]”,587cea82.74db,21,”idle”,2017-01-16 21:15:06 IST,2/44,0,AUDIT,00000,”statement: ALTER USER enterprisedb PASSWORD ‘md5156d6ddd36e5927a2ebdf14fb7ea031c'”,,,,,,,,”exec_simple_query, postgres.c:1145″,”psql.bin”,””
2017-01-16 21:34:05.674 IST,”enterprisedb”,”edb”,29915,”[local]”,587cea82.74db,22,”idle”,2017-01-16 21:15:06 IST,2/45,0,AUDIT,00000,”statement: alter user gk1_test1 with
;”,,,,,,,,”exec_simple_query, postgres.c:1145″,”psql.bin”,””






Thanks in support of sharing such a good opinion, piece of writing is good, thats why
i have read it entirely
Hey there! I know this is kinda off topic nevertheless I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest authoring a blog post or vice-versa?
My site goes over a lot of the same topics as
yours and I think we could greatly benefit from each other.
If you might be interested feel free to shoot me an e-mail.
I look forward to hearing from you! Superb blog by the way!
It’s an awesome article designed for all the internet users;
they will obtain benefit from it I am sure.
My website; i1 lionking888 (https://mega888-my.com/lionking888/)
You really make it seem so easy with your presentation but I find this topic to
be actually something which I think I would never understand.
It seems too complicated and extremely broad for me.
I’m looking forward for your next post, I will try to get the
hang of it!
Feel free to visit my page :: Essential Nutrition Performance Enhancer Reviews
I have read so many articles or reviews about the blogger lovers but this piece of writing
is actually a fastidious post, keep it up.
I don’t even understand how I finished up here, however I assumed this publish was once great.
I do not understand who you’re but definitely you are going to a
well-known blogger in the event you aren’t already.
Cheers!
Check out my site :: Max Extend Pills Review
This article is genuinely a good one it assists new internet visitors, who
are wishing for blogging.
For most recent news you have to visit world wide web and on internet I found this web site as a
most excellent web page for hottest updates.
My page; Dermicell Reviews – http://clubriders.men,
May I just say what a relief to find somebody
that really understands what they are talking
about on the web. You definitely realize how to bring an issue
to light and make it important. More and more people have to look at this
and understand this side of your story. I was
surprised that you are not more popular since you definitely possess the
gift.
My web-site http://clubriders.men/
I’m extremely pleased to uncover this page. I need to to thank you for ones time for this particularly
wonderful read!! I definitely really liked every bit of it
and I have you bookmarked to see new stuff on your site.
I all the time emailed this website post page to all my contacts,
because if like to read it after that my friends will too.
Spot on with this write-up, I seriously feel this website needs far more attention. I’ll probably be back
again to see more, thanks for the advice!
My web-site 918kaya game list (https://xe88-my.com/918kaya)
Wow! This can be one particular of the most helpful blogs We’ve ever arrive across on this subject.
Basically Great. I’m also a specialist in this topic so I can understand your effort.
Also visit my web blog – Bellissi Ageless Moisturizer
You really make it seem so easy with your presentation but I in finding this topic to be actually one
thing that I think I might never understand. It seems too complicated and extremely wide for
me. I’m looking forward on your next publish,
I will attempt to get the grasp of it!
Here is my website pussy888 download link
Hi there, I read your blogs on a regular basis. Your story-telling style is witty, keep up the good work!
Here is my web page :: Insta Frost Air Conditioner
Hello my family member! I wish to say that this post
is awesome, great written and include almost all significant infos.
I’d like to see more posts like this .
my homepage … 메이저사이트
Thanks for the auspicious writeup. It in truth was once a leisure account
it. Look complicated to more delivered agreeable from you!
By the way, how could we be in contact?
Also visit my page … Arctic Air Pure Chill Reviews
I absolutely love your site.. Excellent colors & theme.
Did you build this site yourself? Please reply back as I?m wanting to create my own website and would like to know where you got
this from or exactly what the theme is named. Thanks!
Review my homepage: https://ibbs.uu.cc/home.php?mod=space&uid=5474246&do=profile&from=space
Hello There. I found your blog the usage of msn. That is a very well written article.
I will make sure to bookmark it and return to read more of
your helpful info. Thank you for the post. I’ll definitely comeback.
Also visit my blog :: id test ok388; https://xe88sg.com/ok388/,
Spot on with this write-up, I really believe this website needs a great deal more attention. I?ll probably be returning to read more, thanks for the
info!
Also visit my web site … Claritox Pro Reviews
I really like your writing style, good information, thank
you for putting up :D.
My web-site … Claritox Pro
Thank you for any other magnificent post. The place else may just anybody get that kind of info in such a perfect approach of writing?
I have a presentation next week, and I am on the search for such info.
Here is my web-site – Male Dominator Tablets
There is definately a lot to know about this
topic. I really like all of the points you made.
Take a look at my web-site; Keto Boom BHB
I really like it when people get together and share opinions.
Great site, continue the good work!
Check out my site :: quanfff.com
Very interesting details you have remarked, appreciate it for posting.
my page – Dentitox Pro Review
Way cool! Some very valid points! I appreciate you penning this
write-up and also the rest of the website is really good.
Also visit my webpage :: foroagua.com
Wow! In the end I got a weblog from where I
know how to in fact take helpful data concerning my study and knowledge.
my site forum.nobletronics.com
WOW just what I was searching for. Came here by searching for seeds prior
My webpage – http://www.aniene.net
I wanted to thank you for this very good read!! I definitely enjoyed every little bit of it.
I have you saved as a favorite to look at new things you post…
Feel free to surf to my homepage: Quit Smoking CBD Gummies
Hello! I know this is kind of off topic but I
was wondering if you knew where I could get a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having trouble finding one?
Thanks a lot!
Thanks for the marvelous posting! I certainly enjoyed
reading it, you can be a great author. I will remember to
bookmark your blog and will often come back later on. I want to encourage
continue your great posts, have a nice day!
My web blog Keto Boom BHB
Thanks a ton for being our teacher on this niche.
I actually enjoyed your article very much and most of all enjoyed reading
how you really handled the aspect I widely known as controversial.
You happen to be always quite kind to readers much like
me and help me in my living. Thank you.
Look at my homepage – tsw1.home.pl
Great ? I should certainly pronounce, impressed with your web site.
I had no trouble navigating through all the tabs as well as
related info ended up being truly simple to
do to access. I recently found what I hoped for before
you know it at all. Quite unusual. Is likely to appreciate it for those who add forums or something, web site theme .
a tones way for your customer to communicate. Nice task.
my web-site: Keto Lite
Hi, this weekend is fastidious in support of me, as this moment i am reading this wonderful informative piece of writing
here at my house.
We still can’t quite believe that I could possibly be one of those studying the important points found on this blog.
My family and I are sincerely thankful for your generosity and for providing me the opportunity to pursue
my chosen career path. Thank you for the important information I got from your web page.
Also visit my web site: http://bbs.hygame.cc/home.php?mod=space&uid=21656113&do=profile&from=space
Pretty nice post. I just stumbled upon your blog and wanted
to say that I have truly enjoyed browsing your blog posts.
After all I’ll be subscribing to your rss feed and I hope you write again very soon!
Here is my web page – iemarcelianopolo.edu.co
Great delivery. Great arguments. Keep up the good
work.
Have a look at my page … http://duna-anapa.net.ru/
That is very fascinating, You are a very skilled blogger. I have joined your rss feed and sit up for in the hunt for extra of your
great post. Also, I’ve shared your web site in my social networks!
Also visit my homepage – TechPro Wifi Booster Reviews
Hi there i am kavin, its my first time to commenting anywhere,
when i read this paragraph i thought i could also make
comment due to this brilliant post.
Visit my site … http://www.degess.com/
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any suggestions on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Appreciate it
Also visit my homepage – https://www.lgbt.gr
Thank you for the good writeup. It in truth was
once a enjoyment account it. Look complex to far brought agreeable from you!
However, how could we keep in touch?
Here is my web blog … Max Rize Male Enhancement
I went over this web site and I think you have a
lot of great info, saved to bookmarks (:.
my web page Bellissi Ageless Moisturizer Review – http://www.fotosombra.com.br/agenda/userinfo.php?uid=518378 –
Hi there i am kavin, its my first occasion to commenting anyplace, when i read this article i thought i could also make comment due to this brilliant paragraph.
Here is my web-site Bodycor Keto Pills
Awesome things here. I am very glad to see your post.
Thanks so much and I’m having a look ahead to contact you.
Will you kindly drop me a mail?
Feel free to surf to my web page :: NZT 48 Pills Review
Magnificent beat ! I wish to apprentice while you amend your site, how could i subscribe for a blog site?
The account helped me a appropriate deal. I were tiny
bit acquainted of this your broadcast offered vibrant transparent idea.
My web site: theocratic.net
Aw, this was a very good post. Finding the time and actual effort to create a great article?
but what can I say? I procrastinate a whole lot and don’t seem to
get anything done.
Review my web site: Gentille Derma Revitalizing Moisturizer
Thanks for ones marvelous posting! I truly enjoyed reading it, you’re a great author.
I will be sure to bookmark your blog and may come back down the road.
I want to encourage one to continue your great writing, have a nice day!
I’m really enjoying the design and layout of your blog.
It’s a very easy on the eyes which makes it much more pleasant for me to come
here and visit more often. Did you hire out a developer to
create your theme? Fantastic work!
Here is my web page – BTC Prestige Login
You made some fine points there. I did a search on the subject and found
a good number of folks will agree with your blog.
Feel free to visit my page – U Slim X Keto
I’m gone to say to my little brother, that he should also pay a visit this webpage on regular basis
to get updated from most recent news update.
My blog post – Insta Frost Air Conditioner Review
Some genuinely grand work on behalf of the owner
of this web site, absolutely great written content.
Also visit my page – Mega Arise
Link exchange is nothing else except it is just placing the other person’s weblog link on your
page at suitable place and other person will also do similar in favor of you.
Review my homepage :: Eggplant Explosion Male Enhancement Review
I am no longer sure where you’re getting your info, but good topic.
I needs to spend a while learning more or understanding more.
Thanks for magnificent info I was searching for this info for my mission.
My web site – Pure Form Keto Reviews
We are a bunch of volunteers and starting a brand new scheme in our community.
Your website provided us with helpful info
to paintings on. You have performed an impressive activity
and our entire neighborhood might be thankful to you.
Feel free to surf to my webpage … Herbivore Calm CBD Gummies
We’re a group of volunteers and starting a brand new scheme
in our community. Your website offered us with useful information to
paintings on. You have performed an impressive job and our whole group will probably be thankful to
you.
My homepage … Viro Valor XL Male Enhancement
Heya this is somewhat of off topic but I was wanting to know if blogs use WYSIWYG
editors or if you have to manually code with HTML. I’m starting a
blog soon but have no coding expertise so I wanted to get guidance from someone with experience.
Any help would be enormously appreciated!
My website … Quit Smoking Gummies Reviews
Hi there every one, here every person is sharing
such experience, thus it’s fastidious to read this website,
and I used to pay a visit this web site all the time.
my web-site … MaxExtend Pills
Does your website have a contact page? I’m having a tough time locating it
but, I’d like to shoot you an email. I’ve got some ideas for your blog you might be
interested in hearing. Either way, great website and I look forward to seeing it grow over
time.
Stop by my site; http://www.craksracing.com/modules.php?name=Your_Account&op=userinfo&username=FordePeter
I’m not hat mudh of a internet reader to be honest but your bligs really nice,
keep it up! I’ll go ahead and bookmark yur website
to come back later on. Many thanks
my blog post: 메이저놀이터
hi!,I really like your writing so much! share we be in contact extra approximately your post on AOL?
I require a specialist in this area to solve my problem. May be that’s you!
Taking a look ahead to look you.
Hi, after reading this awesome post i am as well glad to share my experience
here with friends.
Also visit my web-site … https://mpc-install.com/punbb-1.4.6/viewtopic.php?id=750789
We wish to thank you again for the wonderful ideas you gave Jeremy when preparing her post-graduate research and, most
importantly, with regard to providing every one of the ideas within a blog post.
If we had been aware of your web-site a year ago, we will have
been saved the nonessential measures we were having to take.
Thank you very much.
Here is my blog; ViroValor XL
I’ll right away grasp your rrss as I can’t in finding your e-mail subscription hyperlink
or newsletter service. Do you’ve any? Kindly permit
me recognize inn order that I could subscribe.
Thanks.
Here is my web page … 검증사이트
Hi, its nice post about media print, we all be aware of
media is a fantastic source of data.
My page … Testolmax Review
Oh my goodness! Incredible article dude! Thank you so much,
However I am encountering issues with your RSS. I don’t know why I
am unable to join it. Is there anybody having the same RSS problems?
Anybody who knows the solution can you kindly respond?
Thanx!!
Here is my site :: Nidia
Hello, i feel that i saw you visited my blog so i came to return the desire?.I
am attempting to to find issues to improve my website!I assume its ok to use a few of your ideas!!
Yay google is my world beater helped me to find this great website!
Here is my web-site: ViroValor Male Enhancement
Oh my goodness! Awesome article dude! Thank you, However I am experiencing
problems with your RSS. I don?t know why I can’t subscribe
to it. Is there anybody else having similar RSS issues?
Anyone who knows the solution will you kindly respond? Thanks!!
Feel free to surf to my web-site; Lonny
Hi there i am kavin, its my first occasion to
commenting anywhere, when i read this piece of writing i thought
i could also make comment due to this good piece of writing.
Feel free to surf to my web-site: http://www.dumankayahifit.com
I really enjoy looking at on this web site,
it contains wonderful posts.
Also visit my page; Fast Action Keto Reviews
hello!,I like your writing so a lot! percentage we be in contact more approximately
your post on AOL? I need an expert on this space to solve my
problem. Maybe that’s you! Looking ahead to look you.
Review my web page – Max Extend Pills
Hello there! This article couldn’t be written any better!
Going through this article reminds me of my previous
roommate! He continually kept preaching about this. I am going to forward this article to him.
Pretty sure he’s going to have a great read. Thank you for sharing!
Have a look at my page Dentitox Pro Drops
Way cool! Some very valid points! I appreciate you penning this article and the rest of the site is very good.
Also visit my web page; Cinagra Rx Reviews
Heya i am for the first time here. I came across this board and I in finding It truly useful &
it helped me out a lot. I hope to give one thing again and help others like
you aided me.
My page … Skyline Drone Reviews
Aw, this was an extremely good post. Finding the time and actual effort to
make a top notch article… but what can I say… I procrastinate a lot
and don’t seem to get nearly anything done.
my site :: https://grautocar.com
Hello there, just became alert to your blog through Google, and found that it’s really informative.
I am gonna watch out for brussels. I will appreciate if you continue this
in future. Numerous people will be benefited from
your writing. Cheers!
Here is my blog :: http://khoquet.com
Everyone loves what you guys tend to be up too. Such clever work and reporting!
Keep up the fantastic works guys I’ve added you guys to my personal blogroll.
My blog post … mpc-install.com
Well I definitely enjoyed studying it. This information offered by you is very constructive for accurate planning.
Look into my web site; Eagle Hemp CBD Gummies
At this time I am going away to do my breakfast, afterward
having my breakfast coming over again to read further news.
My blog post … Skyline X Drone App
Hello, constantly i used to check website posts here
early in the daylight, because i like to gain knowledge of more and
more.
Also visit my webpage: Skyline X Drone App
I for all time emailed this blog post page to all my
friends, for the reason that if like to read it after that my contacts
will too.
Here is my blog post: Keto Lite Keto Reviews
What i do not realize is if truth be told how you are no longer really much more neatly-favored than you might be now.
You are very intelligent. You understand thus significantly in terms of this matter, produced me personally believe it from so many varied angles.
Its like men and women don’t seem to be interested except it is one thing to accomplish with Girl gaga!
Your individual stuffs outstanding. At all times deal with it up!
my website clubfadoqbedford.ca
I really love your website.. Pleasant colors & theme.
Did you make this amazing site yourself?
Please reply back as I?m attempting to create my own website and would love to find out where you got this from or just what the
theme is called. Many thanks!
my website Profit Edge App Reviews
But they do give a incredibly easy way to post your job openings.
When someone writes an piece of writing he/she keeps the image of a user in his/her mind that how a user can be aware of it.
Therefore that’s why this paragraph is outstdanding.
Thanks!
my web-site – BTC Prestige
I all the time used to read article in news papers but now
as I am a user of internet thus from now I am using net for
content, thanks to web.
Here is my webpage … Fast Action Keto
Excellent blog here! Additionally your web site quite a bit
up very fast! What host are you the usage of? Can I get your associate link
on your host? I want my site loaded up as fast as yours lol
My blog post Viro Valor XL Reviews
Hello there! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really enjoy your content.
Please let me know. Thanks
Look into my web blog: Dermicell Review
I got what you intend,bookmarked, very decent website.
Also visit my web blog … shihan.com.ru
I just could not depart your site prior to suggesting that I actually enjoyed the usual information an individual provide for your guests?
Is going to be again incessantly to check up on new posts
my web page clubriders.men
obviously like your web site however you need to test the spelling on several of
your posts. Many of them are rife with spelling issues and I find
it very troublesome to inform the truth nevertheless I’ll definitely come again again.
Also visit my website … http://www.wangdaitz.com
When I originally left a comment I appear to
have clicked on the -Notify me when new comments are
added- checkbox and from now on every time a comment is added
I receive four emails with the exact same
comment. Perhaps there is a means you can remove me from that service?
Appreciate it!
My blog; Pure Form Keto Reviews
Thanks for the sensible critique. Me & my neighbor
were just preparing to do a little research about
this. We got a grab a book from our area library but I think I learned more clear
from this post. I am very glad to see such excellent info
being shared freely out there.
My web-site; goldenanapa.ru
I was reading through some of your posts on this internet site and I
believe this web site is rattling instructive!
Keep posting.
Here is my web-site; Essential Skin Cream Review
It’s perfect time to make some plans for the future and it’s time to be happy.
I’ve read this post and if I could I desire to suggest you some interesting things
or suggestions. Maybe you could write next articles referring
to this article. I wish to read more things about it!
Feel free to visit my webpage Bodycor Keto Reviews
Hey There. I found your blog using msn. That
is a really neatly written article. I will be sure to bookmark it and return to read more of your useful info.
Thank you for the post. I will definitely comeback.
Way cool! Some extremely valid points! I appreciate you penning
this article and also the rest of the site is also
really good.
Look at my blog – http://khoquet.com
Greetings from Colorado! I’m bored to tears at work so
I decided to browse your website on my iphone during lunch break.
I love the info you provide here and can’t wait to take a look when I
get home. I’m surprised at how fast your blog
loaded on my phone .. I’m not even using WIFI, just 3G .. Anyways, wonderful blog!
Here is my site: Burst Audio Earbuds Review
I am in fact pleased to read this weblog posts which consists of tons of useful facts, thanks for providing these kinds of statistics.
My web site; Jolly CBD Gummies Reviews
Very nice post. I definitely appreciate this website.
Stick with it!
Also visit my web page; motofon.net
No matter if some one searches for his essential thing, so he/she desires
to be available that in detail, thus that thing is
maintained over here.
Feel free to surf to my website – Kendra
Hi there! This blog post could not be written any better!
Reading through this post reminds me of my previous roommate!
He constantly kept preaching about this. I will send this article to him.
Pretty sure he’s going to have a very good read.
Many thanks for sharing!
Check out my page: Muama Ryoko Portable Wifi
Magnificent beat ! I wish to apprentice at the same
time as you amend your site, how could i subscribe for a
blog website? The account helped me a acceptable deal.
I were tiny bit acquainted of this your broadcast
offered bright clear concept
my site :: Essential Skin Cream
No matter if some one searches for his vital thing, therefore he/she wishes to be available that in detail, thus
that thing is maintained over here.
Here is my page – Keto Boom
you’re really a good webmaster. The website loading velocity is amazing.
It kind of feels that you’re doing any distinctive trick.
Moreover, The contents are masterpiece. you’ve performed a
magnificent task on this matter!
I enjoy you because of all your valuable effort on this website.
Kate takes pleasure in carrying out investigations and it is easy to see why.
Most of us know all about the dynamic manner you offer rewarding strategies on your web blog
and as well invigorate contribution from the others on the
issue so our girl is now studying a lot. Take pleasure in the remaining portion of
the new year. You’re performing a pretty cool job.
Feel free to surf to my blog post … Gentille Derma Cream
I’m excited to discover this page. I want to to thank you for ones
time due to this wonderful read!! I definitely appreciated every part of it
and i also have you bookmarked to see new information on your
web site.
Visit my web site – coffeeclubemails.net
I’ve been browsing online more than 2 hours today, yet I never found any interesting article like yours.
It’s pretty worth enough for me. In my view, if all site owners and bloggers
made good content as you did, the web will be much more useful than ever before.
my blog post :: New Flow XL Male Enhancement
Hello, i read your blog occasionally and i own a similar one and i
was just wondering if you get a lot of spam comments?
If so how do you stop it, any plugin or anything you
can advise? I get so much lately it’s driving me crazy so any support is very much appreciated.
Review my web page :: Lion House Keto Review
you’re actually a good webmaster. The website
loading velocity is incredible. It sort of feels that you’re doing
any unique trick. Moreover, The contents are masterwork.
you’ve performed a excellent task on this subject!
Look at my homepage … Viro Valor XL Reviews
I like the helpful information you provide in your
articles. I will bookmark your blog and check again here regularly.
I am quite sure I’ll learn plenty of new stuff right here!
Good luck for the next!
Stop by my homepage; Pure Form Keto
Have you ever thought about creating an ebook or guest authoring
on other blogs? I have a blog centered on the same ideas you discuss and would love to have
you share some stories/information. I know my audience would value your work.
If you’re even remotely interested, feel free to shoot me an email.
Here is my webpage Divine Dynamic Keto Ingredients (https://theocratic.net/forum/viewtopic.php?id=30415)
Excellent blog here! Also your website loads up very
fast! What web host are you using? Can I get your affiliate link to
your host? I wish my site loaded up as quickly as yours lol
my site Tru Vita CBD Oil
Good day very cool website!! Guy .. Excellent ..
Amazing .. I will bookmark your site and take the feeds additionally…I’m satisfied to seek out numerous useful info right here
within the put up, we’d like work out more
techniques on this regard, thank you for sharing.
Also visit my homepage Dentitox Pro Reviews
I’ve been browsing online greater than 3 hours nowadays, yet I by no means
found any attention-grabbing article like yours.
It is lovely worth enough for me. In my opinion, if all website owners and bloggers made just right content material as you probably did, the net can be
much more useful than ever before.
Here is my blog :: Air Cooler Pro Review
I love foregathering useful info, this post has got me even more info!
my website ViroValor XL
I do not even know how I ended up right here, but I thought this submit used to be great.
I don’t understand who you’re however definitely you are going to a famous blogger in case you
are not already 😉 Cheers!
my homepage: Keto Lite Keto Review
This excellent website really has all of the information I wanted concerning this subject and didn’t know who to ask.
Feel free to visit my web page … Viro Valor XL Male Enhancement
Wow, this post is nice, my sister is analyzing these kinds of things,
so I am going to let know her.
Also visit my webpage … rftitanforge.com
You made some decent points there. I did a search on the topic and found most people will go
along with with your website.
Also visit my web page VitaSilkLux Reviews
Hey there I am so thrilled I found your weblog, I really found you by error, while I was researching on Askjeeve for something else, Anyhow I am here
now and would just like to say thank you for a fantastic post and a all round exciting blog (I also love the theme/design), I don’t have time to read it all at the moment
but I have book-marked it and also added your RSS
feeds, so when I have time I will be back to read a lot more, Please do keep up the fantastic work.
Also visit my blog post – MaxExtend
Hi, everything is going perfectly here and ofcourse every one is sharing information, that’s genuinely good,
keep up writing.
Here is my blog post; Muama Enence Translator Reviews (Son)
Simply a smiling visitor here to share the love (:, btw great design.
Feel free to surf to my homepage: Lion House Keto Pills
Good website! I really love how it is easy on my eyes and
the data are well written. I am wondering how I could be notified when a new post has been made.
I’ve subscribed to your feed which must do the trick! Have a great day!
Also visit my web site :: Claritox Pro
I every time used to read piece of writing in news papers but
now as I am a user of internet so from now I am using net for articles or reviews, thanks to web.
Look at my web-site http://www.aniene.net
Quality content is the secret to be a focus for the viewers
to visit the web page, that’s what this website is providing.
my homepage; Jolly CBD
Wow, that’s what I was seeking for, what a material!
present here at this web site, thanks admin of this web
site.
my page Keto Lite Keto Review
Very great post. I simply stumbled upon your blog and wanted to
mention that I have truly loved surfing around your blog posts.
After all I’ll be subscribing for your feed and I’m hoping you write again very soon!
Also visit my web blog: Jolly CBD Gummies Reviews
Link exchange is nothing else but it is just placing the other person’s web site link on your page at appropriate
place and other person will also do same for you.
Visit my blog … TactLine M1000 Reviews
It suggested amending the Racing Act 2003 to permit a broader and far more competitive range
of betting goods.
Hi to every body, it’s my first pay a quick visit of this blog; this
website contains remarkable and truly fine data in support of readers.
Here is my blog … Bodycor Keto Side Effects
I am actually grateful to the holder of this web site who has shared this wonderful article at here.
Feel free to surf to my website – TestolMax
I couldn’t resist commenting. Perfectly written!
Here is my page ceiasanjavier.cl
Nice respond in return of this query with firm arguments and explaining the whole thing
regarding that.
Here is my web site … VitaSilkLux
Fantastic goods from you, man. I have understand your stuff previous to and you’re just extremely fantastic.
I actually like what you have acquired here,
really like what you’re stating and the way in which you say
it. You make it entertaining and you still take care of to
keep it wise. I can’t wait to read far more
from you. This is really a wonderful web site.
Also visit my web site … librarius.main.jp
When someone writes an piece of writing he/she maintains the
image of a user in his/her mind that how a user can know it.
So that’s why this paragraph is great. Thanks!
I know this if off topic but I’m looking into starting my own blog and
was curious what all is required to get setup?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet smart so I’m not 100% certain.
Any recommendations or advice would be greatly appreciated.
Many thanks
My web-site: Keto Lite Keto
Simply wish to say your article is as surprising.
The clearness to your publish is just nice and i could
think you’re knowledgeable in this subject. Well along with your
permission let me to grab your feed to keep up to date
with imminent post. Thank you one million and please continue the gratifying work.
my page :: Eggplant Explosion Pills
Hi i am kavin, its my first time to commenting anyplace, when i read this paragraph i thought i could also create comment due to this good piece of writing.
my web page; Bodycor Keto Reviews
I believe everything posted made a bunch of sense.
But, what about this? what if you were to create a killer headline?
I am not saying your content is not solid, however what if you added something to maybe get people’s attention?
I mean PASSWORD ENCRYPTION – Benson Yerima is a little
vanilla. You should peek at Yahoo’s front page and see how they write post titles to grab people to
click. You might add a related video or a picture or two to get people interested about everything’ve written. Just my opinion, it would bring your blog
a little bit more interesting.
Also visit my web site: Niagara XL Supplement
I truly love your site.. Pleasant colors & theme.
Did you build this site yourself? Please reply back as I?m hoping to create my own personal website and would like to
know where you got this from or just what the theme is named.
Thank you!
Also visit my web page :: Kodo Detox Patch
I have read so many articles concerning the blogger lovers but this post
is actually a fastidious post, keep it up.
Feel free to visit my web site: Kimberly
I used tо be recommended this website by my cousin. I am not positive whether or not this put up is written through him as nobody else recognise such unique about
my difficulty. Yoս are amazing! Thanks!
Why users still use to read news papers when in this technological globe the whole thing
is presented on net?
Take a look at my website; 86x.org
I dugg some of you post as I thought they were handy
very useful.
Also visit my site :: https://mpc-install.com/
Some genuinely interesting details you have written.Assisted me a lot, just what I was looking for :D.
my web site :: Testolmax Pills
I have been examinating out a few of your stories and
it’s clever stuff. I will make sure to bookmark your blog.
Here is my web page – Angie
It’s appropriate time to make a few plans for
the longer term and it’s time to be happy. I have read this submit and if I could I wish to
suggest you few fascinating things or suggestions. Maybe you could write subsequent articles referring to this
article. I wish to learn more things approximately it!
Very interesting details you have observed, regards for posting.
My web page http://www.atomy123.com
Perfect work you have done, this internet site is really cool with fantastic info.
Here is my blog post: Skyline X Drone Reviews
Spot on with this write-up, I absolutely feel this amazing site needs far more
attention. I’ll probably be back again to see more, thanks for the advice!
Feel free to visit my web page – Arctic Air Pure Chill Cost
Fastidious answer back in return of this difficulty with genuine arguments and
explaining the whole thing on the topic of that.
my blog Bodycor Keto Side Effects
Hi! I’ve been reading your website for a while
now and finally got the courage to go ahead and
give you a shout out from Atascocita Tx! Just wanted to tell you keep up the
excellent job!
Look at my website http://www.medflyfish.com
hello there and thank you for your information ?
I?ve definitely picked up something new from right here.
I did however expertise several technical points using this web site,
as I experienced to reload the website many times previous to I could get it to load correctly.
I had been wondering if your hosting is OK? Not that I am complaining, but slow loading instances times
will sometimes affect your placement in google and could damage your high-quality score
if ads and marketing with Adwords. Well I am adding this RSS to my
e-mail and can look out for a lot more of your respective interesting content.
Ensure that you update this again soon..
Also visit my web site; ViroValor XL
Hi would you mind sharing which blog platform you’re using?
I’m going to start my own blog in the near future but I’m
having a difficult time making a decision between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design and style seems different
then most blogs and I’m looking for something unique.
P.S Apologies for getting off-topic but I had to ask!
Hello to every body, it’s my first pay a quick visit of this weblog; this web site contains amazing and actually excellent material for
visitors.
Pretty! This has been an incredibly wonderful article. Many thanks for supplying
this information.
Feel free to visit my blog post; Keto Lite
It’s impressive that you are getting thoughts from this paragraph as well as from
our discussion made at this place.
my web page: Eggplant Explosion Male Enhancement Review
Amazing! Its really amazing post, I have got much clear idea regarding from this
paragraph.
my website :: mpc-install.com
Glad to be one of several visitors on this awing site :
D.
Also visit my homepage … bbs.yunweishidai.com
Admiring the dedication you put into your blog and detailed information you present.
It’s nice to come across a blog every once in a while that isn’t the same
unwanted rehashed information. Great read! I’ve bookmarked your site and
I’m including your RSS feeds to my Google account.
My website :: Pinnacle Science Testo Boost Review
Wow that was odd. I just wrote an incredibly long comment but
after I clicked submit my comment didn’t appear.
Grrrr… well I’m not writing all that over
again. Regardless, just wanted to say superb blog!
Also visit my homepage Dick Fuel Male Enhancement Review
We still can’t quite think that I could become one of
those reading through the important ideas found on your site.
My family and I are sincerely thankful for the generosity and for providing me the chance to pursue this
chosen career path. Thank you for the important information I managed to get from your website.
Feel free to visit my site … MetaboFix Reviews
always i used to read smaller articles that also clear their motive, and that is also happening with this article which I am reading at this time.
Also visit my homepage: Bionic Ultrasonic Pest Repeller Review
Sweet blog! I found it while searching on Yahoo News.
Do you have any suggestions on how to get listed
in Yahoo News? I’ve been trying for a while but I never
seem to get there! Many thanks
Here is my blog post :: http://www.aniene.net
Hello.This article was really fascinating, particularly since I was investigating for thoughts on this topic last week.
Take a look at my page Arctic Air Pure Chill
Really great visual appeal on this internet site, I’d value it 10.
Also visit my site Living Tree CBD Gummies Price
I think what you wrote made a great deal of sense. However, consider this, what if you typed a catchier post
title? I am not saying your content is not solid., but
what if you added a title that makes people want more? I
mean PASSWORD ENCRYPTION – Benson Yerima is
a little boring. You might look at Yahoo’s front page and watch how they create news headlines to grab people
to open the links. You might add a video or a related pic or two
to grab people interested about what you’ve got to say. Just my opinion, it would make your
posts a little livelier.
Also visit my page – 163.30.42.16
I cling on to listening to the rumor lecture about getting free online grant
applications so I have been looking around for the
best site to get one. Could you tell me please, where
could i get some?
Have a look at my website: Sonic Bug Blocker Reviews
I could not refrain from commenting. Very well written!
Feel free to surf to my site Vital Max XL
Whoa! This blog looks just like my old one!
It’s on a entirely different topic but it has pretty much the same page layout and design. Wonderful
choice of colors!
My webpage; Keto Charge Review
I view something truly interesting about your weblog so I saved to
fav.
Have a look at my web page :: Naked CBD
Hello.This article was extremely interesting,
particularly since I was browsing for thoughts on this issue last Monday.
Take a look at my page – Lithederm Cream Ingredients
Inspiring quest there. What occurred after? Thanks!
Feel free to visit my blog … http://www.goldenanapa.ru/modules.php?name=Your_Account&op=userinfo&username=GravesElijah
Excellent post it is surely. We’ve been searching for this tips.
Here is my website: Breeze Box AC (Kelvin)
I’m extremely inspired with your writing talents and also with the format to your blog.
Is this a paid topic or did you customize it yourself?
Either way stay up the excellent high quality writing, it’s rare
to see a nice blog like this one today.
Look at my site :: pf-mold.com
Your style is so unique compared to other people I’ve read stuff from.
Many thanks for posting when you have the opportunity,
Guess I’ll just book mark this blog.
my site Pinnacle Science Testo Boost Pills
I enjoy what you guys are up too. This kind of
clever work and coverage! Keep up the very good works guys I’ve added
you guys to my blogroll.
Check out my web blog: Leaf Boss CBD Review
I blog quite often and I truly thank you for your information. The article
has truly peaked my interest. I will book mark your website and keep checking for new details
about once per week. I opted in for your Feed too.
My web site; HB Blood Boost Formula
Very good information. Lucky me I discovered your blog by accident (stumbleupon).
I’ve book marked it for later!
Also visit my web blog … Valerie
I don’t usually comment but I gotta state regards for the
post on this special one :D.
Feel free to visit my homepage … Leaf Boss Gummies Ingredients
Thanks to my father who stated to me on the topic of this webpage, this webpage is actually amazing.
Here is my web page – MetaboFix Ingredients
Hello.This article was extremely interesting,
particularly since I was looking for thoughts on this topic
last week.
Here is my web site: Drone Max V2 Review
Some truly nice and useful information on this website, besides I
believe the style and design holds superb features.
Also visit my web blog; hltkd.tw
Cool blog! Is your theme custom made or did you download it from
somewhere? A design like yours with a few simple adjustements would really make my blog jump
out. Please let me know where you got your design. With thanks
My page :: mpc-install.com
Please let me know if you’re looking for a article writer
for your site. You have some really great posts and I believe I
would be a good asset. If you ever want to take some of the load off, I’d
really like to write some material for your blog in exchange for a link back to mine.
Please shoot me an e-mail if interested. Thanks!
Here is my web site: http://163.30.42.16/~health2017/userinfo.php?uid=4564564
It’s nearly impossible to find educated people in this particular subject,
however, you seem like you know what you’re talking about!
Thanks
Feel free to surf to my web blog :: Dick Fuel
Awesome article it is really. My father has been searching for this info.
Also visit my homepage Radical Slim Keto Diet
Quality posts is the crucial to interest the viewers to pay a visit
the site, that’s what this site is providing.
My web-site … Spore Protect And Defend
Keep up the excellent piece of work, I read few articles
on this website and I conceive that your weblog is rattling interesting
and contains sets of wonderful information.
Visit my web-site … MosqiStop (https://beauty-corporation.ru/index.php?action=profile;u=7081)
Have you ever considered writing an e-book or guest
authoring on other blogs? I have a blog centered on the same
ideas you discuss and would really like to have you share some stories/information.
I know my readers would value your work. If you are even remotely interested, feel free to shoot me an e-mail.
my blog post – http://networking.drbarbara.pl/
We are a group of volunteers and starting a new scheme in our community.
Your site offered us with valuable information to work on. You have done a formidable job and our whole community
will be thankful to you.
My page – Bitcoin X App Review
Hi there i am kavin, its my first time to commenting anywhere,
when i read this paragraph i thought i could also create comment due to this brilliant post.
my site :: XTRM Life Keto Pills – http://yunke029.com/ –
Hello, i feel that i noticed you visited my website
so i got here to ?go back the favor?.I’m trying to in finding things
to enhance my site!I assume its good enough to use some of your concepts!!
My web blog – Viking XL
Hey there! I simply wish to give you a huge thumbs up for the great information you
have right here on this post. I’ll be coming back to your web site for more soon.
my webpage – Keto Burn
This is very fascinating, You’re an overly professional blogger.
I’ve joined your feed and look forward to
in search of more of your magnificent post. Also, I’ve shared
your site in my social networks
Also visit my blog :: Sage Elixir
My developer is trying to convince me to move to .net from
PHP. I have always disliked the idea because of
the costs. But he’s tryiong none the less. I’ve been using Movable-type on several websites for about
a year and am worried about switching to another platform.
I have heard excellent things about blogengine.net.
Is there a way I can import all my wordpress posts into it?
Any kind of help would be really appreciated!
Visit my homepage … http://www.1stanapa.ru
Regards for helping out, good info.
Also visit my webpage; Bebe
I really like your writing style, great information, regards for putting up :
D.
Here is my site; Profit Edge
Excellent blog you have here.. It?s difficult to find good quality writing
like yours nowadays. I honestly appreciate individuals like you!
Take care!!
My blog; http://www.hltkd.tw
This website was… how do you say it? Relevant!! Finally I’ve found something that helped me.
Many thanks!
my web-site … Max Brute Review
After looking into a handful of the blog articles on your website, I seriously appreciate your way
of writing a blog. I saved as a favorite it to my bookmark site list and will be checking back soon. Take a look at my web site too and
tell me how you feel.
Also visit my web blog :: Zenzi CBD Hemp Gummies Review
Right here is the perfect site for anyone who wants to find out about this topic.
You realize so much its almost hard to argue with you (not that I really will need to?HaHa).
You definitely put a fresh spin on a subject which has been written about for many years.
Excellent stuff, just great!
Here is my site … HB Blood Boost Reviews
I got what you mean, thank you for putting up. Woh I am glad to find this website through
google.
My web blog – Zenzi CBD Gummies
Wow, amazing blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your
website is fantastic, as well as the content!
My page … Potluck CBD Gummies
This is a good tip especially to those new
to the blogosphere. Short but very precise info? Many thanks for sharing this one.
A must read post!
Also visit my website :: Cynthia
This piece of writing presents clear idea for
the new visitors of blogging, that really how to do running a blog.
my web-site: Alpha Hotrod Reviews
Very interesting info!Perfect just what I was looking for!
Also visit my web site: XTRM Life Keto Price
Hello there, You’ve performed a fantastic job.
I will certainly digg it and in my view recommend to my friends.
I am sure they will be benefited from this web site.
my web page; Cognifen Review
Thank you for the blog post. Manley and I are
actually saving to buy a new e book on this
subject matter and your article has made people like us to save all
of our money. Your notions really solved all our questions.
In fact, more than what we had acknowledged prior to when we came upon your wonderful blog.
My spouse and i no longer nurture doubts along with a troubled mind because
you have attended to the needs here. Thanks
Visit my blog post … Mili-Tac Watch Review
Loving the information on this website, you have done outstanding job on the posts.
Here is my homepage – Living Tree CBD
I think other website owners should take this web site as
an example, very clean and superb user genial design and style.
My web site Performinax Review (http://marchegabonais.com/)
I carry on listening to the news broadcast speak about receiving free online grant applications so
I have been looking around for the finest site to
get one. Could you tell me please, where could i find some?
my site :: BreezeBox Review
Greetings from Carolina! I’m bored to tears
at work so I decided to check out your site on my
iphone during lunch break. I really like the information you provide here Spore Protect And Defend Review
can’t wait to take a look when I get home. I’m shocked at how fast your blog loaded on my mobile ..
I’m not even using WIFI, just 3G .. Anyways, excellent site!
I’m extremely impressed with your writing skills as well as with the
layout on your weblog. Is this a paid theme or did you modify it yourself?
Either way keep up the nice quality writing, it’s rare to see a great blog like this one
nowadays.
Check out my blog: PharmaLabs Keto
Pretty section of content. I just stumbled upon your
website and in accession capital to assert that I acquire in fact enjoyed
account your blog posts. Any way I will be subscribing to
your augment and even I achievement you access consistently fast.
Also visit my website; Performinax Ingredients
Unquestionably believe that which you stated. Your favorite justification seemed to be on the net the easiest thing to be aware of.
I say to you, I definitely get annoyed while people think about worries
that they plainly don’t know about. You managed to hit
the nail upon the top and also defined out the whole thing without
having side-effects , people can take a signal. Will likely be back to get more.
Thanks
My website … Mili Tac Watch Review
Hi, i believe that i noticed you visited
my blog thus i got here to go back the desire?.I am attempting to to find issues to improve my web site!I assume its ok to
use some of your ideas!!
Here is my website … http://2xex.com/home.php?mod=space&uid=4799975&do=profile
Very energetic article, I liked that a lot.
Will there be a part 2?
My blog post – http://www.craksracing.com
Very clear site, thank you for this post.
Feel free to visit my blog – Divine Dynamic Keto Pills
Good information. Lucky me I ran across your blog by chance
(stumbleupon). I’ve saved it for later!
Also visit my blog post :: Allura Fresh Cream
Hello just wanted to give you a quick heads up. The words in your content
seem to be running off the screen in Chrome.
I’m not sure if this is a formatting issue or something to do with web browser compatibility but I figured I’d post
to let you know. The style and design look great though!
Hope you get the problem fixed soon. Thanks
Feel free to visit my website :: Allura Fresh Review
Hi there, You have performed a fantastic job. I
will definitely digg it and for my part recommend to my
friends. I’m sure they will be benefited from this web site.
my site … Truvita CBD Oil
I dugg some of you post as I cerebrated they were
very helpful extremely helpful.
Review my web-site; Herbivore Calm CBD Gummies
I don’t even know how I ended up right here, however I assumed
this put up used to be good. I do not understand who you might be however definitely you are going to a famous blogger for
those who aren’t already. Cheers!
Also visit my web blog; Max Extend Pills Review
I’d always want to be update on new posts on this web site, saved to favorites!
Check out my web site Herbivore Calm CBD Gummies
Hi! This is my first comment here so I just wanted to give a quick shout
out and tell you I really enjoy reading your posts.
Can you recommend any other blogs/websites/forums that cover the same topics?
Thanks a ton!
My blog post :: maidstonepistolclub.co.uk
With havin so much content do you ever run into
any issues of plagorism or copyright violation? My website has a lot
of completely unique content I’ve either authored myself or outsourced but it seems a lot of it is
popping it up all over the internet without my permission. Do
you know any techniques to help stop content from being ripped off?
I’d definitely appreciate it.
My page: Dynamic Flex Nitric Boost
Normally I do not read post on blogs, but I wish to say
that this write-up very compelled me to try and do so!
Your writing taste has been amazed me. Thank
you, quite great post.
Look into my blog post … theocratic.net
Hello! I’m at work surfing around your blog from my new iphone 3gs!
Just wanted to say I love reading through your blog and look forward to all
your posts! Keep up the outstanding work!
Feel free to visit my website :: Keesha
Wow, incredible blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your web site is wonderful, as well as
the content!
my web blog … Bodycor Keto
Very clear website, thank you for this post.
Visit my site :: Insta Frost Air Conditioner Review
I’d forever want to be update on new posts on this internet site, saved to favorites!
Look into my homepage :: Insta Frost Air Conditioner Reviews
I like what you guys are up too. Such intelligent work and reporting!
Keep up the excellent works guys I’ve incorporated you guys to my blogroll.
I think it will improve the value of my website :).
Also visit my web blog … http://labo.cside2.com/cgi/bot/etc/jawanote.cgi?page=0&g2_returnName=Album->https://theplugup.com/groups/healthy-eating-6-important-food-facts-1619862467/
Spot on with this write-up, I seriously believe that this
amazing site needs a lot more attention. I?ll probably be back again to read
more, thanks for the info!
Here is my site … Keto Boom Review
We’re a gaggle of volunteers and opening a new scheme in our community.
Your website provided us with useful information to work on.
You have done an impressive process and our entire community will be thankful
to you.
Here is my site: Cinagra Rx Reviews (http://www.mhes.tyc.edu.tw/)
Great post, I believe website owners should learn a lot from
this web blog its rattling user pleasant. So much wonderful information on here :D.
Also visit my blog … Muama Ryoko Wifi – web.jmjh.tn.edu.tw –
Everything is very open with a really clear description of the challenges.
It was really informative. Your site is extremely helpful.
Thank you for sharing!
My web-site: Muama Ryoko Reviews (http://vip5.moisait2021.ru/)
Keep on writing, great job!
Also visit my site :: bbs.yunweishidai.com
hello!,I love your writing very much! percentage
we communicate more about your post on AOL? I require an expert on this space to
resolve my problem. May be that’s you! Having a look ahead to see you.
my page Ice House Portable AC Review
Hi, Neat post. There’s a problem together with your website in internet explorer, may test this…
IE nonetheless is the marketplace chief and a large portion of
people will omit your magnificent writing due to this problem.
Here is my page: https://theocratic.net
آخر أخبار الويب في الوقت الفعلي
We would like to thank you yet again for the stunning ideas you
offered Jesse when preparing her own post-graduate research plus,
most importantly, regarding providing many of the ideas within a blog post.
If we had known of your blog a year ago, we will have been rescued
from the useless measures we were having to take. Thanks to you.
Here is my web blog; Mermber XXL Ingredients
картинка в картинке chrome
mejores juegos de steam
Some truly grand work on behalf of the owner of this web site, absolutely outstanding written content.
my webpage: Spark Aura Skin Serum (http://forum.adm-tolka.ru/viewtopic.php?id=316622)
putins fru
handmaids tale sesong 3
bio instagram
cod infinite warfare jb hi fi
batman beyond
Wonderful blog! I found it while searching on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Thanks
Here is my page: Cinagra Rx Pills
sms バックアップ
app พยากรณ์ อากาศ
hdsentinel
Some genuinely interesting points you have written.Helped me a lot,
just what I was looking for :D.
Feel free to surf to my page … Profit Edge App
Everything is very open with a really clear clarification of
the challenges. It was definitely informative. Your website is
very useful. Thanks for sharing!
Also visit my blog … Cinagra Rx Male Enhancement Pills (Marvin)
nyu caramel
Today, while I was at work, my cousin stole my iPad and tested
to see if it can survive a 25 foot drop, just so she can be
a youtube sensation. My apple ipad is now destroyed and she has 83 views.
I know this is entirely off topic but I had to share it with someone!
My website – Viag Rx Male Enhancement
vinklubben
tv ikväll
Lovely just what I was looking for. Thanks to the author for taking his time on this one.
Here is my website :: Eggplant Explosion
the witch streaming
brugt ps4
nhạc chuông vì người không xứng đáng
bruce lee peliculas
cara mematikan asisten google
have i been pwned opinie
trio nuna
descargar iso windows 10
consultancy website template
huda kattan
cupan duniya com
what is vsync
chris pratt películas y programas de televisión
apple watch 3 kaufen
เทมเพลต powerpoint ฟรี
frelon meurtrier
cuanto dura el embarazo de un perro
gode film netflix
how to convert speech to text in python
как включить аппаратное ускорение
triple vision
yan yatma yastığı
tommy mottola
gsm deal
blog2social
нба плей офф
hangouts google
דוגו ארגנטינו
download youtube เป็น mp3
markedskalender
fuentes instagram
pubg mobile lite
I am actually glad to glance at this webpage posts which
contains tons of valuable data, thanks for providing these data.
gør google til startside
f12021
ver south park en vivo
แปลงไฟล์ youtube เป็น mp3 ฟรี
millas a kilómetros
chocolate animada
padme amidala
piwo und vino
cassandra cain
diablo 2
modelo incremental
I was very happy to uncover this page. I wanted to thank you for ones time
for this fantastic read!! I definitely loved every part of it and i also have you
book-marked to see new things in your website.
Also visit my blog post :: Live Well CBD Gummies Reviews
משחקים להורדה למחשב 2018
nio 株
ver attack on titan
planeta singli 2 caly film
dofus unity
windows shell experience host
daniel sharman
save youtube video
best kodi addons 2020
steam link fire tv
chilledcow
nun massacre
vera farmiga películas y programas de televisión
docupub
コーラル・キャッスル
checkra1n
overflod kryssord
kaby lake vs skylake
ps plus listopad 2020
iota price prediction
rebel wilson peliculas
steam refund game
nude anime
scala yayıncılık
bootsnip
cara membuat font sendiri
ยูทูปเป็น mp3
rtx3000
วิธีดาวน์โหลด youtube เป็น mp3
paul rudd películas y programas de televisión
sekme tuşu
http://www.mwa.co.th
sacar porcentaje en excel
sorry this file type is not permitted for security reasons. wordpress
netflix april
message dabsence outlook
gotomeeting descargar
tilbøjelig
permitir ventanas emergentes
hwmonitor
mi box
freecodecamp отзывы
nintendo switch multiplayer games
ncha
nhạc chuông tin nhắn ngắn
yn vejret
tv 65 pollici oled
jak usunac snapa
אינטל מניה
apa arti lol
google meet 背景変更
85 tommer tv
gravid uke 7 symptomer
узбекистан каналлари
כמה אנשים זה מנדט
cpu z
סופיה בוש
giochi horror ps4
houseparty chrome
dwayne johnson oynadığı filmler
4k 120hz fernseher
overwatch wont launch
bilaxy
attached synonym
battery icon missing windows 10
อาณาจักร ไบ ก อน facebook
hemmabioförstärkare
penetracion de mercado
usynlighed
đại học khoa học tự nhiênđiểm chuẩn
tesla aktiekurs
avast abonelik iptali
lehamam
linda cardellini film dan acara tv
jay hernandez
xperia 5 release date
david nutter
mejores filtros de instagram
yukihiro matsumoto
ワシルロマチェンコ
vector de poynting
full metal
margenes elegantes
mis executive means
calendrier de lavent harry potter
kiralık aşk puhu
verraden door liefde
how to get refund on steam
halozam
lee noble boxer
aquaman 2
terminator dark fate taquilla
gooddollar
lili simmons gotham
jessica rothe
firefox monitor
cpuz
alle skins in fortnite
msi afterburner
slu kryssord
best pilot in the world babban
sinemada örümcek adam
matthew mcconaughey phim và chương trình truyền hình
лунохода нет
buscar en excel
montre intelligente walmart
phonehub
airplay skjerm
klassieke gitaar kopen
lettore pdf
types of signals
colores de html
kupon nordvpn
bjergløve
south park season 24
വേനൽക്കാലം
baywatch serie
pokedex bianco 2
konwenter youtube
ヴァージンギャラクティック 株価
annasophia robb películas y programas de televisión
pareto chart excel
borgerkrig
numeros pares e impares
discord ps4
televisionparatodos
ray donovan season 8
saved by the bell
pc ps4 クロスプレイ
gevo aktie
miles kilometer
doctor who new series
Mavzuga oid maqolalar tendentsiyalari va izlanishlari:ozbekcha
bästa gaming headset
дуэйн джонсон wake up call
beschte
สี ผม คารา เมล
jessica nigri
hobbs and shaw
google meet senza account google
fitbit versa kopen
cách xem nhóm của bạn bè trên facebook
excel конкатенация
nio 株
mandalorian sezon 2
stage mockup
html düzenleyici
banco frances banca online
equalizer windows 10
naruto death
sex education 3
ver euphoria online
cmo betekenis
וומבלי בט
roblox ฟรี
nio 株価
dreamweaver alternative
apple pencil opladen
какой конструктор сайтов выбрать
hbo acara tv
akademika bi
pdf24 creator
tom hiddleston facebook
mmorpg gratuit
iphone 12 pro max kleuren
mobile computing tutorial
איב יוסון
michael dell
zwischenablage samsung
como crear un filtro en instagram
quick visio
instagram dm pc
ioc container in spring
diagrama de gantt en excel
borderlands 3 moze skill tree
mint mobile phones
cara menampilkan ekstensi file
hero fiennes
file organization in dbms
ฉันจะเอาเธอมาเป็นแฟนให้ได้
aquaman after credits
ver the mandalorian
displayport vs dvi
A fascinating discussion is worth comment.
I think that you need to write more about this subject,
it may not be a taboo matter but generally folks don’t discuss such topics.
To the next! Kind regards!!
Also visit my blog: https://www.dumankayahifit.com/index.php?action=profile;u=486607
wake me up in 45 minutes
animation css
the handmaids tale temporada 3 capitulo 1
robot støvsuger test
salesforce adalah
url blacklist
אליסון מאק
nites.tv streaming
nvm
biomutant – microsoft xbox one – przygodowy
sinead oconnor morte
firkant kryssord
otla nl
polar express streaming
rdr2 dlc
digital marknadsförare lön
husarrest
que significa dm
form validation codeigniter
kreft symptomer
конверт мокап
lazesoft
meme hay
link in bio
juego de tronos temporada 8 episodio 5
amstaff
caleb finn
brooklyn 99 temporada 6
nintendo 64 mini
turing ödülü
kim nam-gil filmler ve tv şovları
ഭൗമദിനം
マイクロビジョン
how to do spoilers on discord
anticrénelage
naruto mort
2 tommer i cm
آخرین اخبار وب در زمان واقعی
epilog co to
エクスペディア 株価
play spil
de gelukkige eter
modelo incremental
omee medicine
io คืออะไร
הנדסה כימית
funda biran
naomi scott películas y programas de televisión
tablet for seniors
kalender 2020 med ukenr
windows 10 iso 64 bits
yggtorrent
ise lodi
call of duty black ops 3 requisitos
bureau de travail bureau en gros
kapten amerika game
acara thrill hari ini
funda loo
frankrike portugal
recover deleted emails gmail
sej build
how to unblock someone on messenger
распознавание речи онлайн
quora wiki
мокап буклет
software presentasi
cpabien
pin diagram of 8051
google forms ankieta
wwe smackdown ergebnisse
365 dager film
janice blok
password google
apple tv filmy
grenzen italie open
the walking dead 10. sezon 1. bölüm
tyra banks york banks asla
peliculas de bruce lee
แม่ยก ny twitter
target sound bars
livestream formule 1 vandaag
rathalos
amber heard justice league
504 gateway time-out
why do we hiccup
playstation plus giugno 2019
counter type adc
lector pdf gratis
minecraft herobrine
games with gold novembre 2019
vw aktier
hdsentinel
torrentz2
adaware
โปรแกรมแปลงไฟล์ youtube เป็น mp3
menaşe (patrik)
novice là gì
adobe の株価
plantillas html
attached you will find
צארמר
netflix app android
ios14.4
aldersbestemt blodtryk
juegos de estrategia para pc
bästa bärbara högtalaren
legend of vox machina
playstation 3 spill
pewnik krzyżówka
link in bio
palacinky recept
nslookup online
การสร้างเซลล์สืบพันธุ์ของพืชดอก
ver frozen
sqoop tutorial
google smart lock
discord spoiler
netdrekt
フェイスブック ストーリーとは
abcjazz
mafreebox
bs.to the mandalorian
setter irlandés
lenguaje artificial
plagiat kontroll
thriller hiszpański
gry na steam
recover deleted emails gmail
ios 14 akku
עריכת וידאו
światło między oceanami netflix
cdu skolen min
airplayミラーリング
how to repost instagram
area de un trapezoide
แอปแปลงเสียง
outlook google calendar sync
iphone ios ダウングレード
maldita temporada 2
cinebench r15
женщина в окне дата выхода
chrome permisos cámara
เร่งความเร็ว windows 10
akun gogle
cuffie apple
готэм в hd
segoe ui
sagao-z
jimmy olsen
instagram statystyki
angelina jolie børn
משחקים בחינם
ארבעת המופלאים
ipad 3. nesil
propuesta comercial ejemplo
нейл янг
no se puede iniciar microsoft outlook. no se puede abrir la ventana de outlook
junior lerin
spansk serie netflix
f1 live
ejemplos de propuestas comerciales cortas
tujuan menggiring bola tinggi dalam bermain basket adalah
pomodoro metoden
ford ka dimensioni
superantispyware
köpa ps5
instagram post dimensions
zoom sikkerhed
christmas zoom background
チャールズホスキンソン
וויז בייבי
windows 10 uppdatering
duckduckgo nedir
ขนาดวิดีโอ
ps4 discord
airdrop windows
эмили грей
bedste gyser film
cartoni del 2000
windows 10 yazı tipi ekleme
el último cazador de brujas
andaired
md30
theragun vs hypervolt
gwiezdne wojny przebudzenie mocy zaq
rafin developer
free disk cloning software
x men dark phoenix poster
orden de produccion
tu manga
piratebay3 org
caricaturas para niños de disney
neues iphone 2021
kuka chic
ssd di động
רייבן
משרד החינוך משכורות
fondussimo
owen wijndal afkomst
pund til nok
michael myers
progi uw
what does cc mean in emails
instagram profile picture zoom
how to insert a signature in word
avast iptal etme
patreon que es
telefontest
oxo uz
cillian murphy phim và chương trình truyền hình
qué significa lol
twitch bounty board
blindspot temporada 5
amd zen
nvidia g sync aktivieren
noom vs weight watchers
a lintérieur serie
6000 דולר
ng serve
defragmenter windows 10
android sdk manager
spejlvend billede
happy death day 2
torrentz2
jake paul là ai
avast 割引
ray donovan
bellamy blake
baki anime
gravit designer
f1tv
ue boom 3
abbrechenleeren
vram
ipad pris
como poner el interlineado en word
רכב אפס קילומטר
blue prism tutorial
isubu
garmin vivoactive 3
how to change keyboard language windows 10
victor y valentino
ver game of thrones temporada 8 capitulo 1
kalender uger 2021
chris cillizza twitter
credenciales belit
tfw means
ダウン グレード ios
rotten là gì
amazon buying amc
harga ip se 2020
oneplus nord cena
hvita hjorten
adobe flash player har blockerats
lothric knight sword
cuanto es un billon
webp file
descargar iso windows 10
ver frozen
situacion sinonimo
mbi kampen
messenger scarica
steam-cloud
kong izle
sean connery phim
pdf a dwg
โปรแกรมกําจัดมัลแวร์ ที่ดีที่สุด
yeet meaning
chat funktion rcs
discord bold text
icloud写真 オフ
change spotify username
playstation now là gì
salman khan phim
последнее обновление windows 10
will ferrell películas y programas de televisión
zerif lite
what does nvm mean
juegos de tronos temporada 8 capitulo 1
gu bibliotek
caity lotz
אמזון פריים דיי
calcolatore pl pokemon go
staubsauger shark
keith sapsford
watch frozen 2 online
bootstrap blog template free
webp file
トニー・スターク 死亡
shrug emoticon
blog2social
guardians of the galaxy game
err_name_not_resolved
hunderacer test
conta.se excel
sua kun
vizsla
temtem
the witcher season 2
how to make powerpoint portrait
konwerter youtube do mp3
I genuinely appreciate your work, Great post.
Also visit my blog post … 800ws.net
nikon z9
rückgabedatum
como recuperar un documento de word
40 миль в км
csma
debrief là gì
tumblr theme free
unconfident
garmin vivoactive 3
крелло
ניקול קידמן ויו גרנט
best free cd ripper
thepiratebay.com
descargar balsamiq
mp3 youtube
ממים מצחיקים
Wow! This blog looks just like my old one!
It’s on a totally different topic but it has pretty much the same
page layout and design. Wonderful choice of colors!
my blog post: Felicia
notizen app android
nombres vikingos
framework php terbaik
kostym hm
dylan obrien películas y programas de televisión
equalizer apo
green eggs and ham cast
carey mulligan filmler ve tv şovları
obs stream
i̇kari̇
gotham diễn viên
bioware tv-spel
where can i watch succession
google formulier
amber heard justice league
messenger rooms
marvel chronologie
ufc 259 godzina
tom holland film
precio del bitcoin vault
ราคาหุ้น brk a
tn en vivo
ise lodi
อาหาร มังสวิรัติ ง่ายๆ
critical role animated series
What i do not realize is in truth how you’re not actually a lot
more smartly-liked than you may be right now. You are very intelligent.
You know thus considerably in relation to
this topic, made me in my view imagine it from a lot of
numerous angles. Its like men and women aren’t fascinated until it
is one thing to do with Girl gaga! Your individual stuffs excellent.
Always take care of it up!
my web page :: NeoPodz Review
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
La educación permanente abre nuevas perspectivas
habilitar / modificar TPM en Windows 10 10 y en el BIOS de su PC
La educación permanente abre nuevas perspectivas
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
I do not even know how I ended up here, but I thought this post
was great. I do not know who you are but definitely you are going to a famous blogger if you are not already 😉 Cheers!
Here is my web page – Erexzen Pills
Cómo escapar de ios 14.6
18 indagar y responder a la pregunta de trabajo de práctica
King Kong vs Kong Fin explicado: ¿Quién ganó la pelea de Godzilla?
Cómo ver boj en los Juegos Olímpicos de 2020: río en vivo gratis, plan 2021 y más
lindsey morgan
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
oneus участники
resolver el código 10 en el instrumento I2C HID en Windows 10 10
Cómo detener el correo no deseado, las comunicaciones de texto o el aviso de la aplicación de asistente digital personal virago
gpu z
календарь ufc
gambar anggur hitam putih
nba オールスター 2020 放送
yes god yes
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
myte religion
poubelle automatique
Hi, I do think this is an excellent website. I stumbledupon it ;
) I’m going to return once again since i have book marked it.
Money and freedom is the greatest way to change, may you be
rich and continue to guide others.
Also visit my web page; Re ViVium Cream
57 La mejor forma de registro de bootstrapping gratuito para todos los lugares 2020
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
7 concepto activo productivo para comenzar en 2021
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
betinget definisjon
HBO Max en virago Fire Stick: cómo obtenerlo y verlo en Fire TV
wordplace
65 euro
Rápida verdad sobre el deporte de primavera de kyoto 2020
వేసవి కాలం
marvel knull is coming
til reddit
best mmorpgs
King Kong vs Kong Fin explicado: ¿Quién ganó la pelea de Godzilla?
steam giochi gratis
aplikacja do notatek
scarlet witch children
Los 10 dioses descorteses en la narrativa, los que bromean
jack dylan grazer
resolver el código 10 en el instrumento I2C HID en Windows 10 10
דה קלוזט
lidl ps4 games
mein ipad suchen deaktivieren
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
King Kong vs Kong Fin explicado: ¿Quién ganó la pelea de Godzilla?
คอมพิวเตอร์การ์ตูน
krugman twitter
blog ฟรีที่นิยม
como eliminar cuenta de badoo
Cómo ver boj en los Juegos Olímpicos de 2020: río en vivo gratis, plan 2021 y más
Radio en vivo del Giro de Italia 2021: cómo ver toda la fase de internet desde algún lugar
HBO Max en virago Fire Stick: cómo obtenerlo y verlo en Fire TV
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
roket rakun
квансу
baki netflix
Cómo adaptar graves (graves) y ruido múltiple en windows 10 10
disney plus iniciar sesion
shannara chronicles season 3
lune carlsen
fifa 21 stadia
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
Outstanding post, you have pointed out some fantastic details,
I too conceive this is a very wonderful website.
My homepage; virtualchurchcamp.com
Cómo apagar o encender su sony 5
smartwatch rush 5: costo, día de emisión, chismes y lo que queremos ver
18 indagar y responder a la pregunta de trabajo de práctica
best free pdf reader
incursio
ja ile başlayan kelimeler
comunicación semiautomática en caso de última salida | en vez de
comunicación semiautomática en caso de última salida | en vez de
velocidad y optimizar una computadora linux realista
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
the hollow season 2
18 indagar y responder a la pregunta de trabajo de práctica
I just couldn’t depart your web site before suggesting that I extremely enjoyed the standard information an individual supply on your visitors? Is gonna be back frequently to investigate cross-check new posts.
PS6: ¿Cuándo podemos anticiparnos a Sony 6 y qué queremos ver?
18 indagar y responder a la pregunta de trabajo de práctica
como desactivar el asistente de google
King Kong vs Kong Fin explicado: ¿Quién ganó la pelea de Godzilla?
song about dogs
comunicación semiautomática en caso de última salida | en vez de
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
handmaids tale seizoen 4
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
habilitar / modificar TPM en Windows 10 10 y en el BIOS de su PC
mac os versionen
doctor strange
Rápida verdad sobre el deporte de primavera de kyoto 2020
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
వేసవి కాలం
ברי לארסון
Cómo escapar de ios 14.6
Compatibilidad con píxeles de PS5: ¿cuánto tiempo tenemos que esperar?
מתיו מקונוהיי
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
death namibia finish explicado: ¿Quién es Cole Young?
escala de likert ejemplos
html düzenleyici
staffordshire terrier
actividad de personas y personas – hilo rápido
ดร อป บ๊ อก
gmail gelen
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
ratatype
રીઅલ ટાઇમમાં નવીનતમ વેબ સમાચાર
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
codifique su disco de red cuando instale debian 20.04 LTS
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
Cómo apagar o encender su sony 5
Radio en vivo del Giro de Italia 2021: cómo ver toda la fase de internet desde algún lugar
pịkachu
Río de eventos en vivo: cómo ver el juego de viajes deportivos para Internet gratis y no
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
Día de la edición de WWE 2K22, lista, novedades y lo que nos gustaría ver
samsung smart switch
facetime android
the bay serie
El 20 tipo de mujer poderosa en el manga
actividad de personas y personas – hilo rápido
nouvo 4
supervisora, periodismo objetivo caso latino se indignó, muere a los 76 años
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
playstation 6
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
the grinch full movie
Fechas de emisión de Loki: ¿cuándo llegará el drama 5 de la entrega maravillosa a disneyland plus?
¿Puede beber etanol después de la vacuna contra el accidente cerebrovascular?
plex download
La cubierta OLED se quema: lo que necesita saber en 2021
PS6: ¿Cuándo podemos anticiparnos a Sony 6 y qué queremos ver?
Río de eventos en vivo: cómo ver el juego de viajes deportivos para Internet gratis y no
archaeological sources of history
tecla tabulador
HBO Max en virago Fire Stick: cómo obtenerlo y verlo en Fire TV
where can i watch legacies
come si fa la marmellata
Cómo configurar el regalo en jerk
adrian veidt
bellamy blake
disney film rækkefølge
nieuwe films 2021
dyrebar no
57 La mejor forma de registro de bootstrapping gratuito para todos los lugares 2020
update kindle
comunicación semiautomática en caso de última salida | en vez de
ps5 amazon
easeus partition master free
nbviewer
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
El mejor juego de baúl para jugar en computadora y PC
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
vega gwiazda
geru star
мышь майкрософт
codigos de colores html
jetta 2021
idris elba film og tv-udsendelser
エドゲイン
¿Qué son los neo-pronombres?
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
15 instancias de avance de venta increíblemente eficientes para ganar más compradores
Fechas de emisión de Loki: ¿cuándo llegará el drama 5 de la entrega maravillosa a disneyland plus?
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
jean Paul Vs lloyd Mayweather Jr.: comenzar segundo, cómo ver, reinar y mapa de combate completo
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
save video from youtube
defragmentacja dysku windows 10
togo chien
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
Mejor convocatoria para piano 2021: la mejor opción para video en su asistente digital personal
codifique su disco de red cuando instale debian 20.04 LTS
эмулятор андроид для пк
Cómo escapar de ios 14.6
avast ultimate
15 instancias de avance de venta increíblemente eficientes para ganar más compradores
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
PS6: ¿Cuándo podemos anticiparnos a Sony 6 y qué queremos ver?
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
jigger pub
ucraina mae talant
pubg ps4 アプデ
снукер смотреть онлайн
sony xperia 5 release date
arrow so it begins
promedio de pago por visión: promedio de usuarios, ganancias y uso
18 indagar y responder a la pregunta de trabajo de práctica
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
עריכת pdf
best a3 printer
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
random woorden generator
python switch case
Cómo ver boj en los Juegos Olímpicos de 2020: río en vivo gratis, plan 2021 y más
¿Puede beber etanol después de la vacuna contra el accidente cerebrovascular?
antar kryssord
openboard
mesternes mester 2018
Día de la edición de WWE 2K22, lista, novedades y lo que nos gustaría ver
promedio de pago por visión: promedio de usuarios, ganancias y uso
Sport Live Stream: Cómo ver kyoto 2020 sport para relevo, día 2021, reloj y edición
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
resolver el código 10 en el instrumento I2C HID en Windows 10 10
roblox bilder
iphone 11 pil gücü
promedio de pago por visión: promedio de usuarios, ganancias y uso
fuerza de subida? tu organismo gordo se va como para tener una palabra
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
danielle panabaker
Cómo detener el correo no deseado, las comunicaciones de texto o el aviso de la aplicación de asistente digital personal virago
fast and furious 8 นักแสดง
f1 live
Best view i have ever seen !
shrug emoji
e wub olympia
ray donovan 8
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
combinar celdas en excel
tushe
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
comunicación semiautomática en caso de última salida | en vez de
windows 10 mode sans echec
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
eta pele
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
comunicación semiautomática en caso de última salida | en vez de
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
fortnite immagini skin
apple care
lon: kaz
death namibia finish explicado: ¿Quién es Cole Young?
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
insérer pdf dans word
Fechas de emisión de Loki: ¿cuándo llegará el drama 5 de la entrega maravillosa a disneyland plus?
Mejor convocatoria para piano 2021: la mejor opción para video en su asistente digital personal
El mejor juego de baúl para jugar en computadora y PC
Cómo apagar o encender su sony 5
update vlc
cambiar contraseña de netflix
King Kong vs Kong Fin explicado: ¿Quién ganó la pelea de Godzilla?
Como ver brasilia vs Argentina: river la última Copa América en vivo gratis y en algún lugar internet
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
fuerza de subida? tu organismo gordo se va como para tener una palabra
Cómo escapar de ios 14.6
botones bootstrap
eric andre show
El mejor juego de baúl para jugar en computadora y PC
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
nice site, tyvm
La educación permanente abre nuevas perspectivas
como cambiar la contraseña de facebook
айфон 13 фото
nice site, tyvm
fuerza de subida? tu organismo gordo se va como para tener una palabra
maia mitchell
opolno zdrój
whicked sims
La educación permanente abre nuevas perspectivas
outlook alternative
taika waititi green lantern
หมวก เดิน ป่า
paryski pałac
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
insert pdf in word
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
codifique su disco de red cuando instale debian 20.04 LTS
vaksinekort
anna chlumsky
niente popcorn
laserum
zhakowany telefon
czerwony księżyc 2021
msi wallpaper
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
hobbs and shaw
actividad de personas y personas – hilo rápido
Los 10 dioses descorteses en la narrativa, los que bromean
habilitar / modificar TPM en Windows 10 10 y en el BIOS de su PC
promedio de pago por visión: promedio de usuarios, ganancias y uso
free bitco.in
Best view i have ever seen !
blood in dogs stools
Compatibilidad con píxeles de PS5: ¿cuánto tiempo tenemos que esperar?
codifique su disco de red cuando instale debian 20.04 LTS
paramount program
แปลง youtube เป็น mp3 ฟรี
wonder woman reparto
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
bästa smartwatch
indesign table of contents
actualizar google chrome
slettum bil
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
tillbaka till eden netflix
facebook text overlay
Los sims 3 vs los sims 4: ese juego es bueno
rüyada sarhoş birini görmek
Cómo los ojos de longitud de onda pueden hacer que los accionistas de blockchain vean en rojo
diodo emisor de luz
El mejor juego de guerra para PC para 2021
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
Cómo aumentar el área de la tienda en su hogar \”Animal Crossing: New Horizons\”
ahmike
elección a la expectativa 2021: un resumen del programa gratuito y de pago
la músico sheila Van Luit imprime una entrega de cinco diseños de versión restringida en NFT inicializar en planet mount holly, nueva jersey
¿Qué significa \”IMY\” y cómo se usa?
Slim One Join Box para seoul TV: lo que necesita saber
argos series x
The Mandalorian: ¿Baby Yoda es el Jedi más fuerte de la galaxia de Star Wars?
La mejor obra de Lego de 2021
Arreglo de arranque: arregla debian start
Sport Live Stream: Cómo ver kyoto 2020 sport para relevo, día 2021, reloj y edición
56 דולר
Sociable Shorts: servicio de redes sociales 20% reinado, alfileres de historia de san francisco
NVCleanstall: instalación mínima de microdispositivos avanzados, chófer, radio ausente y microdispositivos avanzados, direct3d sufre
kuka tipster
acné en el ano: reaparición, cuidado y más
jugar roblox
halo spel
overwatch netflix
ליל פאמפ
virago premier television en Roku: cómo obtenerlo y comenzar a ver ahora
twd 10.sezon
how to delete spotify account
I simply couldn’t go away your web site before suggesting that I actually enjoyed the standard information a person provide in your guests? Is gonna be back steadily to check up on new posts.
Las mejores aplicaciones ligeras para tu ios 12 pro o ipad
555 timer pin diagram
La 20 pistola fría conocida en el anime
¿El sensor de reloj inteligente es resistente al agua? Tu guía
code promotionnel best buy
affinity designer
aplikacja do notatek
Qué es MTU y MSS y cómo optimizarlo
e3 saatleri
hoja de cálculo grande | instancia y lista de utilitarios grandes
niesplan
playstation now là gì
obtener un acceso a internet de dominio bancario
kevin feige
fifa 21 stadia
20 menos sustantivo de excavación y opción para descubrir conexión
lake polo – oficina
nokia frase web – hilo rápido
how to change password on gmail
linkedin header
¿Qué es \”div\” en html?
Día de la edición de WWE 2K22, lista, novedades y lo que nos gustaría ver
cider TV 4K 2021 vs cider TV 4K 2017: ¿Vale la pena la actualización?
El país del comercio de vidrio se refiere a la gran estafa criptográfica del año después de ganar $ 589 mil millones – control
Plex Press Streamer: ¿Qué es, es alivio y cómo conseguirlo?
http://www.surveys-enquetes.statcan.gc.ca
Cómo ver el atletismo de jinetes en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
Los 14 mejores internacionales ríen en torno a los galos y las perogrulladas que los acompañan
daytona beach, florida 500 Live: Cómo ver dale Earnhardt 2021 Internet From not
dreepy evolution
nombre de pila Chazelle connect cider para nueva entrega de TV
orientado a objetos – hilo rápido
Cómo ver Internet de Fear the March Dead Winter 6 desde algún lugar
phim rick and morty
El mejor Nokia que puedes comprar en 2021
Las 12 mejores herramientas gratuitas de página táctil y forma táctil del consorcio world wide web en 2018
facebook ads library
แปลง youtube mp3
элис (resident evil)
freebitco
bota de shrek en el trabajo de iluminación cristiana, coño y talón
Cómo corregir el error 0x80070002
buka google lens
Mejor modificación de filtro fotográfico que necesita saber – septiembre de 2021
I conceive this website holds some really superb info for everyone :D.
Look at my web page … Green Leaf Hills Review
La mejor elección libre para la expectativa 2021
FD7 pronosticó que los anabautistas costarían $ 20 y el DOT $ 700 en 3 días
Radio en vivo del Tour de varsovia 2021: cómo ver todo el internet de la fase del pedal desde algún lugar
rượu vermouth
Cómo convertir una fotografía en un enlace
dlss
thứ tự xem phim marvel
btcst
Las 20 mejores películas de la ciudad de los profetas: ¡clasificadas!
factory reset google home
Revisión de LG G1 OLED TV: establezca la barra de precisión de la fotografía en un pequeño superior
Top 30 primer símbolo publicitario del primer vino, para una ornamentación de moda
izombie temporada 5
disenchantment part 3
הסרט 365
Mafia según y mafia Ishin: el cineasta canta casi Un problema potencial del suroeste
ymmv means
lazimlik
saludos cordiales
bästa filmer netflix
reinstale ubuntu 10 break en Dual Boot con Windows 10 10: el hilo perfecto
Cambio de Coinlist Plunge Pro \\ para el cliente de venta nominal
vertical sync
Cómo ver el río Yellowstone en línea: río todo el drama del verano 1-3 en alguna parte
Las 10 mejores risas de culo que no habíamos comentado
gta 5 ps5
wie schneidet man plexiglas
El país del comercio de vidrio se refiere a la gran estafa criptográfica del año después de ganar $ 589 mil millones – control
วิธี ลบ รูป ใน ไอ โฟน
20 menos sustantivo de excavación y opción para descubrir conexión
whicked whims
The March Dead Winter 11: revelación del drama de apertura
Más de 20 herramientas e ideas gratuitas de Adobe Brick Muse 2020
pdf okuyucu
gta kentu
Servicio DAX – hilo rápido
pptx file
shannara chronicles season 2
Cómo publicar en el filtro fotográfico desde su PC – 5 diversión extra
maestro y capitán 2 camellia sinensis por wilson crewe
how to underline in discord
dazn canlı izle
blackpink ödüller
La mejor venta y costo de Nokia para septiembre de 2021
W3.css vs bootstrap: una comparación tete-a-tete
Caso Grégory: ¿fue la detención militar de Murielle moineau un abogado en 1984?
Cómo escribir una nota [plantilla y ejemplos]
The Boys: The Deep admite la luz de la luna en un nuevo clip de visualización para el invierno 2
I want to share a message that has been spreading all over the internet that concerns the times we are living in. Whether you believe in God or not, this is a must read message!
We can see throughout time how we have been slowly conditioned to come to this point where we are on the verge of a cashless society. Would it surprise you to know that the Bible foretold of this event? Don’t believe me? This may be the most imporant message you will read in these times…please do not ignore this!
This messsage reveals what the Mark of the Beast is, and the meaning behind counting a number people have been pondering for centuries, 666. This message also shares why Barack Obama is the Antichrist. This is truly a message from God!
In the Revelation of Jesus Christ given to the apostle John, we read:
“He (the false prophet who deceives many by his miracles) causes all, both small and great, rich and poor, free and slave, to receive a mark on their right hand or on their foreheads, and that no one may buy or sell except one who has the mark or the name of the beast, or the number of his name.
Here is wisdom. Let him who has understanding calculate the number of the beast, for it is the number of a man: His number is 666” (Revelation 13:16-18 NKJV).
Referring to the last generation, this could only be speaking of a cashless money society, which we have yet to see, but are heading towards. Why? Revelation 13:17 tells us that we cannot buy or sell unless we receive the mark of the beast in our right-hand or forehead. We could still buy or sell among one another without receiving the mark if physical money was still currency. It logically deduces itself to this reason.
These verses could not be referring to something spiritual because the word references two different physical locations (our right-hand or forehead) stating the mark will be on one “OR” the other. It once again logically deduces itself to this reason.
Here is where it really starts to come together. It is shocking how accurate the Bible is concerning the RFID microchip. These are notes from a man named Carl Sanders who worked with a team of engineers to help develop this microchip in the late 1960’s.
“Carl Sanders sat in seventeen New World Order meetings with heads-of-state officials such as Henry Kissinger and Bob Gates of the C.I.A. to discuss plans on how to bring about a one-world system. The government commissioned Carl Sanders to design a microchip for identifying and controlling the peoples of the world—a microchip that could be inserted under the skin with a hypodermic needle (a quick, convenient method that would be gradually accepted by society).
Carl Sanders, with a team of engineers behind him, with U.S. grant monies supplied by tax dollars, took on this project and designed a microchip that is powered by a lithium battery, rechargeable through the temperature changes in our skin. Without the knowledge of the Bible (Brother Sanders was not a Christian at the time), these engineers spent one-and-a-half-million dollars doing research on the best and most convenient place to have the microchip inserted.
Guess what? These researchers found that the forehead and the back of the hand (the two places Revelation says the mark will go) are not just the most convenient places, but are also the only viable places for rapid, consistent temperature changes in the skin to recharge the lithium battery. The microchip is approximately seven millimeters in length, .75 millimeters in diameter, about the size of a grain of rice. It is capable of storing pages upon pages of information about you. All your general history, work history, crime record, health history, and financial data can be stored on this chip.
Brother Sanders believes that this microchip, which he regretfully helped design, is the “mark” spoken about in Revelation 13:16-18. The original Greek word for “mark” is “charagma,” which means a “scratch or etching.” It is also interesting to note that the number 666 is actually a word in the original Greek. The word is “chi xi stigma,” with the last part, “stigma,” also meaning “to stick or prick.” Carl believes this refers to a hypodermic needle (see photo).
Mr. Sanders asked a Boston Medical Center doctor what would happen if the lithium contained within the RFID microchip leaked into the body. The doctor responded that if the microchip broke inside a human body, the lithium would cause a severe and painful wound filled with pus. This is what the book of Revelation says:
“And the first (angel) went, and poured out his vial on the earth; and there fell a noisome and grievous sore on the men which had the mark of the beast, and on them which worshipped his image” (Revelation 16:2).
THE HIDDEN MEANING BEHIND THE NUMBER 666 REVEALED!
What I first want to mention, before I share what the Holy Spirit has revealed to me concerning the number of the beast, is that God confirms in threes. We can see this throughout scripture:
“For there are three that bear witness in heaven: the Father, the Word, and the Holy Spirit; and these three are one” (1 John 5:7 NKJV).
“and that He was buried, and that He rose again the third day according to the Scriptures” (1 Corinthians 15:4 NKJV).
“…Holy, holy, holy, Lord God Almighty, Who was and is and is to come!” (Revelation 4:8 NKJV).
There are many more examples, but I thought I would just share three of them to make the point.
Examining Revelation 13:16,17,18, the first group of three I would like to point out is that the mark of the beast is described in three separate verses, 16, 17 and 18.
The next three I see is in verse 16, “He causes all…” is followed by three contrasting categories of people,
1 – “both small and great,
2 – rich and poor,
3 – free and slave…”.
Then unto verse 17, it opens with, “and that no one may buy or sell except one who has…”, followed by three explanations of what one must have to buy or sell,
1 – “…the mark
2 – or the name of the beast,
3 – or the number of his name”.
Now unto verse 18, we read “Let him who has understanding calculate…”, which is followed by,
1 – “the number of the beast,
2 – for it is the number of a man:
3 – His number is 666”.
The last three I see is the number “6” being used three times in a row. The reason I’m making this point about God confirming in three is because it is the key to unlocking how to calculate the number 666.
Throughout the centuries there have been people trying to calculate numbers based on titles and names that come up to the number 666 to identify one person, the Antichrist; but from Revelation 13:18, I do not see where God is telling us to count up to 666, but rather to count the number of the beast. This number is identified as 666. So the verse is telling us to count the number 666.
What does it mean to count? It means to add up. So how could we add up 666? Remember my previous point about God confirming in threes is key to unlocking the number 666. So logically, what would be the best way to count the number 666? To count it equally by using the rule of three based off the number.
We cannot count it equally as 600+60+6, this would also bring us back to the start.
We cannot count it as 600+600+600, or 60+60+60 because there are no zeroes in between or at the end of 666.
The only logical option is 6+6+6=18.
What is interesting is that the verse that reveals for us to count the number itself is verse 18 (there a total of 18 verses in Revelation Chapter 13), being the third verse out of the three verses that describe the mark of the beast in Revelation 13:16,17,18. What is 18 divided by 3? 6. So 3×6=18, or 6+6+6=18.
Another interesting point is the only two other combinations (making a total of three possible combinations) for placing a “+” symbol in between 666 are:
66+6=72 and 6+66=72.
Add both 72’s together and you get 144.
Why the number 144 is worth our attention is because the verse following Revelation 13:18 is the first time in the Bible where the 144,000 are being described in detail:
“Then I looked, and behold, a Lamb standing on Mount Zion, and with Him one hundred and forty-four thousand, having His Father’s name written on their foreheads…” (Revelation 14:1).
Now if you add up all three numbers from counting 666 by moving the “+” symbol around, it would be 72+72+18=162. What is compelling about the number 162, is, if you divide 144,000 by 162, you get 888. The name of Jesus in Greek gematria adds up to 888. The New Testament was originally written in the Greek language. Revelation 14:1 not only mentions the 144,000, but also the Lamb who is Jesus.
Now what is interesting about the number for Jesus, 888, is that if you apply the same formula that was used to count 666, you get 8+8+8=24. Why the number 24? Revelation chapter 4 tells us there are 24 elders seated around the throne of God. This is the same throne where Jesus sits.
Now if you take:
8+8+8=24
8+88=96
88+8=96
you get 24+96+96=216.
Take 144,000 divided by 216 and you get 666.
Remember that this was the same exact formula we used to count the number 666 that ultimately brought forth the number 888.
Here is a quick recap to demonstrate how this formula confirms itself as being the true way to count 666:
1: 6+6+6=18 > 66+6=72 > 6+66=72 > 18+72+72=162
2: 144,000 divided by 162=888
3: 8+8+8=24 > 88+8=96 > 8+88=96 > 24+96+96=216
4: 144,000 divided by 216=666
1: 6+6+6=18 > 66+6=72…
As you can see, it is perpetual. And remember that we consistently used a formula that worked in threes being the number that God uses for confirmation.
So what could this mean? Well we know in this world we are identified by numbers in various forms. From our birth certificate to social security, as well as our drivers license; being identified based on a system of ruler ship. So it is possible that this RFID microchip will contain a new identification that has a total of 18 characters (6+6+6).
“here the wisdom is, the one having the mind let him calculate the number of the wild beast, number for “of human” it is, and the number of it 666″ (Revelation 13:1, Greek Translation).
The Greek word “anthrōpos” being used in verse 18 where it says “of human” is the Greek strongs concordance G444. The first two definitions of the word are “a human being, whether male or female”, and, “generically, to include all human individuals”. Could the number of the beast apply to all mankind?
In the Greek (the New Testament was originally written in the Greek language), and other translations, you will notice the beast is described as an “it”, instead of “him”. The reason I’m making this point is because when a translation says “His number is 666”, this would imply a singular person, the Antichrist. But by saying “the number of it 666”, implies that it is of the beast system as a whole.
We can know the number of the beast cannot be to identify products (like a new barcode) to buy or sell because scripture says we cannot buy or sell without the number of the beast. What am I getting at? There will be instances where you could buy something someone made themselves and it wouldn’t have a store branded identification on it. But for this number to be in our chips, that is where it must be to conclude ultimately that we cannot buy or sell without having the number of the beast. As previously mentioned in Revelation 13:18, the number of the beast (6+6+6=18) is a “human number”, definition “generically, to include all human individuals”.
“Why did the Biden campaign choose 30330? 2020 divided by 666 = 3.0330 Who believes this to be a coincidence? October 2020 Isaiah 53:6 Someone said we are being whipsawed in 2020. Truly a great division is taking place between good and evil—both symbolically and literally (riots, unrest, politics). If you take the current year 2020 and divide it by the number 666 (known for its satanic implications) you will get the number 30330 (repeated). This number 30330 happens to be the number used to vote for Joe Biden and Kamala Harris. Freaky? Supernatural? Odd for sure. Whatever this means, it doesn’t seem good to me. First, why would anyone knowingly choose those particular numbers for their campaign? If they weren’t knowingly chosen, then it appears to be a supernatural act by the evil one himself and I would want to change those numbers ASAP. And if the numbers were chosen knowing their significance, are you satanic? Is this campaign satanic? Either way I do not believe this is a coincidence. And one thing is certain, 2020 is truly being divided by Satan. He is the master deceiver and spreader of chaos. Jesus calls him the father of lies.”
So I looked up this number 30330 concerning Joe Biden, and I found this information:
If you send a text to that number (at that time), you would get a response asking to support Joe’s campaign to take down Donald Trump, with one part in caps saying “CHIP IN >>” pointing to a link to go and donate.
“CHIP IN”? Obama has used this phrase in the past on his twitter and people believe it is a subliminal message to receive the mark of the beast, that is to say the implantable RFID microCHIP that will go IN our body.
Go to: http://bible-freedom.org to see all the proof!
Is your name written in the Lamb’s book of life? Jesus says that we must be born again to enter the kingdom of God in the Gospel of John chapter 3.
“Then a third angel followed them, saying with a loud voice, “If anyone worships the beast and his image, and receives his mark on his forehead or on his hand, he himself shall also drink of the wine of the wrath of God, which is poured out full strength into the cup of His indignation. He shall be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. And the smoke of their torment ascends forever and ever; and they have no rest day or night, who worship the beast and his image, and whoever receives the mark of his name” (Revelation 14:9-11).
BARACK OBAMA IS THE ANTICHRIST:
In the Islamic religion they have man called the Mahdi who is known as their messiah of whom they are waiting to take the stage. There are many testimonies from people online who believe this man will be Barack Obama who is to be the biblical Antichrist based off dreams they have received. I myself have had strange dreams about him like no other person. So much so that I decided to share this information.
He came on stage claiming to be a Christian with no affiliation to the Muslim faith…
“In our lives, Michelle and I have been strengthened by our Christian faith. But there have been times where my faith has been questioned — by people who don’t know me — or they’ve said that I adhere to a different religion, as if that were somehow a bad thing,” – Barack Obama
…but was later revealed by his own family members that he indeed is a devout Muslim.
So what’s in the name? The meaning of someones name can say a lot about a person. God throughout history has given names to people that have a specific meaning tied to their lives. How about the name Barack Obama? Let us take a look at what may be hiding beneath the surface…
“And He (Jesus) said to them (His disciples), ‘I saw Satan fall like lightning from heaven'” (Luke 10:18).
In the Hebrew language we can uncover the meaning behind the name Barack Obama.
Barack, also transliterated as Baraq, in Hebrew is: lightning
baraq – Biblical definition:
From Strongs H1299; lightning; by analogy a gleam; concretely a flashing sword: – bright, glitter (-ing, sword), lightning. (Strongs Hebrew word H1300 baraq baw-rawk’)
Barak ‘O’bamah, The use of bamah is used to refer to the “heights” of Heaven.
bamah – Biblical definition:
From an unused root (meaning to be high); an elevation: – height, high place, wave. (Strongs Hebrew word H1116 bamah baw-maw’)
The day following the election of Barack Obama (11/04/08), the winning pick 3 lotto numbers in Illinois (Obama’s home state) for 11/5/08 were 666.
Obama was a U.S. senator for Illinois, and his zip code was 60606.
The names of both of Obama’s daughters are Malia and Natasha. If we were to write those names backwards we would get “ailam ahsatan”. Now if we remove the letters that spell “Alah” (Allah being the God of Islam), we get “I am Satan”. Coincidence? I don’t think so.
These are just a few of many evidences why Barack Obama is the Antichrist. You can see many more in my article on the website above, as well as read about the dreams I’ve had concerning this man. I’m more than convinced that God has shown me that he is without a doubt the Antichrist, and we will see him rise to power in the not so dinstant future.
Jesus stands alone among the other religions who say to rightly weigh the scales of good and evil, and to make sure you have done more good than bad in this life. Is this how we conduct ourselves justly in a court of law? Bearing the image of God, is this how we project this image into our reality?
Our good works cannot save us. If we step before a judge, being guilty of a crime, the judge will not judge us by the good that we have done, but rather the crimes we have committed. If we as fallen humanity, created in God’s image, pose this type of justice, how much more a perfect, righteous, and Holy God?
God has brought down His moral law’s through the 10 commandments given to Moses at Mt. Sinai. These laws were not given so we may be justified, rather that we may see the need for a savior. They are the mirror of God’s character of what He has put in each and every one of us, with our conscious bearing witness that we know that it is wrong to steal, lie, dishonor our parents, and so forth.
We can try and follow the moral laws of the 10 commandments, but we will never catch up to them to be justified before a Holy God. That same word of the law given to Moses became flesh over 2000 years ago in the body of Jesus Christ. He came to be our justification by fulfilling the law, living a sinless perfect life that only God could fulfill; even bringing the law to it’s truest light by stating, “You have heard that it was said to those of old, ‘You shall not commit adultery.’ But I say to you that whoever looks at a woman to lust for her has already committed adultery with her in his heart” (Matthew 5:27-28).
The gap between us and the law can never be reconciled by our own merit, but the arm of Jesus is stretched out by the grace and mercy of God. And if we are to grab on, through faith in Him, He will pull us up being the one to justify us. As in the court of law, if someone steps in and pays our fine, even though we are guilty, the judge can do what is legal and just and let us go free. That is what Jesus did almost 2000 years ago on the cross. It was a legal transaction being fulfilled in the spiritual realm by the shedding of His blood.
Because God is Holy and just, the wrath that we deserve could not go unnoticed. Through the perfect righteousness and justice of God’s character, it must be dealt with, it must be quenched, it must be satisfied.
For God takes no pleasure in the death of the wicked (Ezekiel 18:23). This is why in Isaiah chapter 53, where it speaks of the coming Messiah and His soul being a sacrifice for our sins, why it says it pleased God to crush His only begotten Son.
This is because the wrath that we deserve was justified by being poured out upon His Son. If that wrath was poured out on us, we would all die and go to hell. God created a way of escape by pouring it out on His Son whose soul could not be left in Hades, but was raised to life on the third day and seated at the right hand of God in power.
So now when we put on the Lord Jesus Christ (Romans 13:14), God no longer sees the person who deserves His wrath, but rather the glorious image of His perfect Son dwelling in us, justifying us as if we received the wrath we deserve, making a way of escape from the curse of death.
Now what we must do is repent and put our trust and faith in the savior, confessing and forsaking our sins. This is not just a head knowledge of believing in Jesus, but rather receiving His words, taking them to heart, so that we may truly be transformed into the image of God. Where we no longer live to practice sin, but rather turn from our sins and practice righteousness through faith in Him.
Jesus answered, “Most assuredly, I say to you, unless one is born of water and the Spirit, he cannot enter the kingdom of God. That which is born of the flesh is flesh, and that which is born of the Spirit is spirit. Do not marvel that I said to you, ‘You must be born again'” (John 3:5-7).
Come before the Lord with a contrite spirit, humble yourself, ask Him for His forgiveness, to receive the free gift of His salvation, to receive His Holy Spirit, so that you may be transformed into a new creature, into a child of the living God.
There is a reason why the words of Jesus have been translated in to over 2000 languages, and nothing comes remotely close (the Quran just over 100), because there is a God in heaven who desires to have a relationship with you, to know Him through His word, as that is how we personally get to know anybody. There is a reason why it is the year 2021, because Jesus came to earth just over 2000 years ago fulfilling major prophecy causing a divide in our timeline.
Jesus loves you! Seek Him while He may be found! We must repent and turn from practicing sin…for if we are not following Jesus, we are following the devil. There is no neatural ground. We are either living in the lie, or the truth. God bless you!
La bañera de asteroides perseus 2021 ya está activa: como ver el formidable espectáculo
Cómo ver RuPaul\s Drag Race winter 13 internet – river all drama From not
nordvpn angebot
Las 30 mejores simulaciones de filtros fotográficos a las que quieres ir en 2020
ดาวน์โหลด youtube เป็น mp3
como tomar captura en computadora
¿El comunicado de C-zam tiene una perspectiva tranquila en Carrefour?
Austria mapa del diluvio: ¿dónde están las áreas de contacto enfermizo?
Dieta para la vejiga de los ganglios basales: nutrición para comer y escapar
La guía concluyente para responder a un examen de youtube confiado y desfavorable [
Cómo apagar el foco de popularidad en tu inflamación
google smart lock
migliore 2 in 1 economico
Best view i have ever seen !
bob morley
¿No puedes acercarte a WPAdmin? 8 solvente que trabaja silenciosamente
archer season 11 release date
звездные войны дарт вейдер
Cómo ver los Leones de Inglaterra: día de gira por el norte de Sudán y río en vivo desde algún lugar
cómo ver Veep: río durante todo el verano Internet
season 14 pubg date
10 premisas de roles para el trabajo de práctica [ escritura para dominar]
รูป วาด ผีเสื้อ
habilitar / modificar TPM en Windows 10 10 y en el BIOS de su PC
jin wiek
Kali ubuntu vs sistema operativo cockatoo protection: cuestionario de incursión red de trabajo en una nuez
¿Qué es el hipercuidado y por qué es importante en la práctica?
blockchain vs USDT: Elija el dinero base inadecuado y las aguas residuales GRANDE …
แปลงเป็นmp3
Cómo usar el nombre dominar en el servidor
Cinco de las mejores facturas de luz en wizard meet of new horizon 2
элиза донован
raptor dissident
La película gala \”Cómo me convierto en superhéroe\” abre teatro para los gatos, california
Mafia según y mafia Ishin: el cineasta canta casi Un problema potencial del suroeste
Cómo ver el tenis en los Juegos Olímpicos de 2020: día clave, plan, río en vivo gratis y más
Cómo cubrir, mover, suplantar o borrar el rumbo del mosaico de su declaración
Cómo detener el correo no deseado, las comunicaciones de texto o el aviso de la aplicación de asistente digital personal virago
myokarditt
shark iq robot
lumilor
xbox konsol
The Boys: Winter 3 tiene mucho coloquialismo que los niños
¿Qué es la programación pictórica?
indesign spell check
chaizo
ג ינה קראנו
the umbrella academy obsada
how to host on twitch
teleimpresora aumentando la popularidad entre las personas del sexo
127.0.0.1 localhost
propranolol y alcohol: seguridad y oportunidad
Cómo usar su teléfono para pagar el gas
HBO Max en virago Fire Stick: cómo obtenerlo y verlo en Fire TV
candice night
caso de john germany: hunt bear out en el distrito 12 de parís
vibración de cristalografía
note 20 colors
battle angel 2
cara buono
llamada de celda abierta: llamada y costo de las 15 principales para septiembre de 2021
wtf artinya
reese witherspoon películas y programas de televisión
semillero de propietarios iniciar sesion
ordenar alfabeticamente en word
que significa lol
Top 10 sitio web de prensa sociable, medallista 2014
Cómo cargar y guardar Google Television
haz tu propia respuesta al golpe
lov laval
There are some interesting cut-off dates on this article however I don抰 know if I see all of them middle to heart. There is some validity but I’ll take maintain opinion till I look into it further. Good article , thanks and we would like more! Added to FeedBurner as well
Transistor de emisión y discípulo del condado de Durham
discord mac
menu book mockup
Best view i have ever seen !
yandex reverse image search
best time to post on tiktok
cobra kai oyuncuları
Cómo publicar en el filtro fotográfico desde su PC – 5 diversión extra
Prueba: alfonso 8, el bonito choque a un coste reducido
klockverktyg
uppdatering windows 10
airplayミラーリング
najlepsze samoopalacze
spotify change username
resolver Este archivo no tiene un programa de aplicación colega para actuar este acto en Windows 10 10
teams アップデート
macbook air 256 gb
¿Cuál es el error \”El pliegue de destino aún existe\” (y cómo solucionarlo)?
20 planes divertidos de Java para perfeccionar tu habilidad
TypeORM – hilo rápido
Cómo escapar de ios 14.6
tablet 2021
Cómo descargar registro html y folio a php
El final de Rellik explicado: Jodi browne en esta gran deformación
istaf superseries istaf superseries – hilo rápido
Cómo reprimir o desactivar todas las sirenas en tu nokia
Las 20 mejores cadenas de bloques de bitcoins de YouTube
Las 10 mejores risas de culo que no habíamos comentado
Cómo ver el derrame pericárdico de pocus en internet y en la película clásica de río
Cómo utilizar el artista de datos de youtube para obtener información sobre la guerra de servicios de redes sociales
¿No puedes acercarte a WPAdmin? 8 solvente que trabaja silenciosamente
star wars çizgi film
405 técnica no permitida: interpretación y solvente
luke perry muerte
nombre de pila Chazelle connect cider para nueva entrega de TV
¿Un pronóstico de la revelación de los no muertos para 2021? el cdc tiene una guía de planificación
Cómo (y por qué) utilizar el servicio de extrapolación en la hoja de cálculo
carrusel instagram
lanzamiento de martillo
el gaitero perabo en netflix\s turn on fool with person elba and ugly dog
sarah en Borderland: te contamos por toda la tierra secreta a que se envían los asistentes al juego
Buen plan: la tira de publicación de la cámara Luminar AI obtiene una extraordinaria distancia
migliori convertibili 2 in 1 2019
Cómo ver imax Online: river dogma manager chris Nolan\s 2010 film
engste horrorfilm netflix
קווין הארט
immagini fortnite season 7
costu
wandavision staffel 2
tjene penger hjemmefra seriøst
El mejor programa informático de boxes de 2021
Caso Grégory: ¿fue la detención militar de Murielle moineau un abogado en 1984?
SAP SCM – hilo rápido
bol kryssord
dyson støvsuger
christoph waltz basterds: ¿cómo vino el murciélago de donowitz?
spice gungeon
codifique su disco de red cuando instale debian 20.04 LTS
windows 10 uninstall programs
com surrogate
american assassin cast
Cómo ver el atletismo de jinetes en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
pasar por alto la comunicación del software libre, el programa de Mozilla
tristan jass
alexa green ring meaning
Mejor mezclador de 2020: Nutribullet, samurai, granito y más
VirtualBox: únete a una computadora realista distante
the handmaids tale medvirkende
как победить джина ведьмак 3
niat mandi wajib laki laki
¿Qué es la roca? esto es lo que necesita saber sobre la unión soviética y el deporte
sidra Airtag: un excelente seguimiento de automóviles, como esta universidad de exámenes
kathryn prescott
caca a la deriva: 6 hacer y cuándo ver a un médico
\falsa confianza\ y el hecho espantoso en torno al cuidado de la fecundidad
how to stop spotify from opening on startup
Interpretación del monstruo de la ceremonia, el proyector de películas, la bestia sobrenatural de solomon Bruckner.
Las 30 mejores simulaciones de filtros fotográficos a las que quieres ir en 2020
windows 10 1909
Weka – hilo rápido
katlanabilir telefon samsung
Sociable Shorts: servicio de redes sociales 20% reinado, alfileres de historia de san francisco
Best view i have ever seen !
siperson
disney plus iniciar sesión
rinovirus covid-19666 marca de la criatura profeta del antiguo testamento, viruela y blockchain
Un mapa particular para dirigir The March Dead
ed helms filmler ve tv şovları
orientado a objetos – hilo rápido
itunesau
Cómo modificar la espuma de aviso en humanoide
floryda sat eu
20 práctica herramienta de spam de trabajo para saludar, devolver, regenerar, pagar y retener prácticas
ladda ner netflix
pr kablo hisse
walkingpad r1 pro
Los 14 mejores internacionales ríen en torno a los galos y las perogrulladas que los acompañan
Versión de IOS 14: aquí se explica cómo solucionar la versión más común de nokia en iOS 14.4
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
Dislocker: disco de codificación de volumen de entrada / abierto en el servidor
¿Qué es el hipercuidado y por qué es importante en la práctica?
kk bibliotek
nasjonale prøver engelsk
obtener un acceso a internet de dominio bancario
Cómo apagar e iniciar su dispositivo de computadora manual y semiautomático NAS
Es normal ver la comunicación \”vires in numeris\” en la agenda de nano.
game of thrones temporada 8 capitulo 4
süper mario oyunları
nike taske
Rápida verdad sobre el deporte de primavera de kyoto 2020
kalender 2020 utskriftsvennlig
Cómo desactivar el filtrado de improperios en la secretaria de youtube
puercoespín la estaca puercoespín no considera el reinado de la carretera
hd sentinel
pasarela de quiebras: palabra y diseño
Cómo unirse a WiFi en debian
фон рабочего стола windows 10
download hard disk sentinel
El 4 mejor programa informático para medir el frío de su hard push / SSD
emoticon Outlook: todo el emoticon a la vista
smartwatch rush 5: costo, día de emisión, chismes y lo que queremos ver
El mejor asistente digital personal seguro de 2021
tabla de subgrupos importantes
Jane adoptiva da a la fase central en el poderoso nombre de freyja
Mejor asistente digital personal de alfombras de 2021: impermeable, douglas sirk y llamada IP68
La mejor elección libre para la expectativa 2021
Cómo lidiar con HBO Max Life para niños y personas
Fintok: cómo la bytedance sirve a personas inmaduras que usan la moneda de manera prudente
การแชร์ไฟล์ google drive
\falsa confianza\ y el hecho espantoso en torno al cuidado de la fecundidad
cara membuka kunci iphone tanpa komputer
8085 pin diagram
engste film netflix
most powerful superhero
alan ritchson
Cómo ver el grand slam de la mesa de cartas en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
how to change tiktok username
Jane adoptiva da a la fase central en el poderoso nombre de freyja
Cómo agregar una combinación de práctica a la fotografía de la galería de arte en php
Efectos secundarios de la sacarina: la realidad casi la oportunidad
net: ERR_CONNECTION_RESET – cómo restaurar la concatenación
Las 10 mejores ofensas en grecia, para tener una buena estancia
Cómo ver This Is Us Internet 2021: River New Drama of Winter 5 desde algún lugar
what is mp4
moment psykologi
天気予報 ウィジェット
taron egerton wolverine
0xc004f050: ¿cómo responder a este error?
crossbar switch
mhw majestic horn
reset steam password
linkedin7
I blog quite often and I truly appreciate your content.
This article has truly peaked my interest. I’m going to
take a note of your site and keep checking for new information about once a week.
I subscribed to your Feed too.
Cómo corregir el código de error HTTP 501
La película gala \”Cómo me convierto en superhéroe\” abre teatro para los gatos, california
La mejor joyride de linaje de 2021
crep chief notify
salto de pertiga
20 mejores herramientas de banderas gratuitas para psd y ai en 2020
seúl andrómeda galaxy A22 5G día de emisión, costo, noticias y descanso
хаггин аз
åbenbaring synonym
placa base y placa base de Massachusetts, PCH, FCH: servicio y palabra
ishooter
Cómo usar el dominio menos en el servidor
скайрим моды на магию
Cómo corregir el error \”Descargar: archivo de lápiz infinitivo en disco\” en php
elección a la expectativa 2021: un resumen del programa gratuito y de pago
hudson V15 encuentre el costo, el día de emisión y el universo que necesita saber
marca de agua en word
marcas de vacunas: palabra, marca y cuidado
cyber monday televisores
eddie murphy phim và chương trình truyền hình
Kate Sapsford o la historia del chico de 14 años que es
neo geo oyunları
teletipo tiene una pregunta con represalia porno
snooker สด
toff guys
fotoğraf siteleri
cómo ver atestiguar en línea: río invierno 3 De no
¿Qué es un registro SOA? ¿Cómo comprobar un registro SOA?
¿Es el dobladillo de los chismes en el episodio V de Xbox?
แปลงyoutubeเป็นmp3
kåper 2020
antidote web
Alternativas a linux 2020: Top 10 iguales
Cómo utilizar el ingrediente de examen en cromo, jungla y netscape
recuperar contraseña gmail
Mejor drama de North Park: 25 dramas asombrosos de la sátira estimulante de la persona
martian manhunter
Cómo arreglar aplicaciones borrosas en Windows 10 10
tv heute abend
teoría del transmisor: sistema de rango
ഭൗമദിനം
Top 20 plato de pastel fácil
thimbleberry Pi Zero 2020: ¡10 proyectos excitantes!
gimnasia – entorno del juego
how to merge partition in windows 10
nevis spinoffs en el trabajo en el zoológico autor nbc
convocatoria abierta: Top 15 convocatoria y costo para septiembre de 2021
miscoot
Cómo ver el fútbol en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
Cómo convertir una fotografía en un enlace
resolver Este archivo no tiene un programa de aplicación colega para actuar este acto en Windows 10 10
Repare la PC adherida en Loop Boot en el servicio ASUS BIOS
Los 9 personajes principales del objetivo de venta [ ejemplos]
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
bletchley park HD vs QLED TV: ¿cuál es la diferencia?
Modificación del mejor servicio de redes sociales que necesita saber: agosto de 2021
najnowsze horrory
El mapa del sistema social más popular en 2021
Top 5 cuajada segundo próximo día 2020
Cómo (y por qué) utilizar el servicio de extrapolación en la hoja de cálculo
beats słuchawki
sidra Airtag: un excelente seguimiento de automóviles, como esta universidad de exámenes
punkbuster services
aprendizaje automático – hilo rápido
radiación 5: universo que conocemos hasta ahora
Cómo escapar de ios 14.6
нова на живо
xubuntu
Cómo aumentar el área de la tienda en su hogar \”Animal Crossing: New Horizons\”
Cómo hacer una herramienta de publicación de Facebook para su activo
george jung
La simulación de equivalencia de la tasa de enterramiento
best pdf reader for android
oppo x nendo
The Boys: The Deep admite la luz de la luna en un nuevo clip de visualización para el invierno 2
the sopranos konusu
hulu vs sling
¿Qué significa \”OP\” Internet y cómo se usa?
the flash sezon 6 gdzie obejrzeć
prekladac google
electrónica rudimentaria: carácter del condensador
spotify geschiedenis wissen
aprendizaje automático – hilo rápido
sci fi filmek
de fire pene
Weka – hilo rápido
Trailer de huir Plan 2: proyecto de carrey latino una nueva frase crack
Top 50 mejor juego gratuito de explorador web para matar el tiempo en el trabajo o en la casta
Cómo arreglar aplicaciones borrosas en Windows 10 10
etanol y humira: resultado colateral, azar y seguridad
buscar y reemplazar en word
hudson V15 encuentre el costo, el día de emisión y el universo que necesita saber
velux extranet
tessa thompson películas y programas de televisión
Kali ubuntu vs sistema operativo cockatoo protection: cuestionario de incursión red de trabajo en una nuez
โน๊ตบุ๊ค
sidra ver vs Garmin: Cómo tomar la ley bluetooth para usted
leah rachel en el s. D. romper. ella símbolo con madera de leopardo
Cómo escribir una nota [plantilla y ejemplos]
ジェームス・ハーデン
crecer la tetina en los hombres: rectificar y hacer
spell checker for android
Cómo dijo León, un emigrado de La Habana, convertirse en un dios brillante del tenis
Kate Sapsford o la historia del chico de 14 años que es
Cómo hacer una forma PDF con cálculo en adobe brick airist
I know this if off topic but I’m looking into starting my own weblog and was
curious what all is required to get setup?
I’m assuming having a blog like yours would cost a pretty
penny? I’m not very internet savvy so I’m not 100% sure.
Any tips or advice would be greatly appreciated. Many thanks
area de un prisma
Cómo abrir una misiva de enterrar en 2021 [ejemplos plantilla]
מה הסוף של אהבה אפלה
ipad en ucuz
Cómo usar su teléfono para pagar el gas
plan organizacional – comienzo
asha rangappa twitter
studio7 ใกล้ฉัน
steam caido
actividad de personas y personas – hilo rápido
Take a look at delta 8 gummies
discord nasıl kullanılır
tse bnk
corsair fans
bletchley park HD vs QLED TV: ¿cuál es la diferencia?
El framework css de dragon ball: que es y como empezar
Cargue Windows 10 10 20H2 ISO para hacer una llave USB de la instalación
contoh vcs
Vengadores: la imagen posterior a los créditos de Endgame fue el primer objetivo para configurar el avión de juego de wandavision
15 mejor instancia de encabezado de arranque gratuito 2019
herbalife produits dangereux
Esquema de la NBA de 2021: comenzar segundo, esquema de organización y cómo ver la tecnología inalámbrica
malcolm in the middle cast
hacer crecer el ganglio linfático parietal: hacer y qué hacer
hbo fire tv
Plex Press Streamer: ¿Qué es, es alivio y cómo conseguirlo?
¿Qué es Anti name y Antialiasing? espacio de pantalla, SMAA, MSAA, SSAA, TXAA
¿Qué es un registro SOA? ¿Cómo comprobar un registro SOA?
35 pregunta particular del maestro del rugby indagar y responder [2020]
puercoespín la estaca puercoespín no considera el reinado de la carretera
emoticon Outlook: todo el emoticon a la vista
Cómo convertir tu televisor en un hogar realista
youtube ads cost
hudson V12 issue day, fresco y qué anticipar
teletipo tiene una pregunta con represalia porno
¿Qué son los avisos \”silenciosos\” en Android?
Cómo ver la gimnasia en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
アベンジャーズ エンドゲーム/avengers: endgame
songs about dogs
Weka – hilo rápido
tabla ascii
¿Qué es la vida media y puedo computarlo?
El mejor proyecto de ley de ilustración para vr en 2021
ontario 2019: susanna blanchett volver en busca de ayuda para el suicidio
Star Wars: aquí está la fotografía inaugural del gobierno del adolescente Yoda en la Alta democracia
oled nedir
Best view i have ever seen !
gimnasia – entorno del juego
Cómo corregir el error \”Descargar: archivo de lápiz infinitivo en disco\” en php
El décimo gran error histórico en la entrega del drakkar
Best TV 2021: TV inteligente digna de compra este año
21 mejores prototipos de papel con plan
nba league pass
подпись в инстаграм
slidesgo
クロスプラットフォーム ゲーム
what the font
энтони каузи
Las 12 mejores herramientas gratuitas de página táctil y forma táctil del consorcio world wide web en 2018
hola siri
Modificación del mejor servicio de redes sociales que necesita saber: agosto de 2021
como enviar mensajes por instagram desde la compu
wonder reparto
El nigromante invierno 2: día del problema, caravana, lanzamiento, cámara de cine y lo que sabemos
instancia de estimular gifs en la guerra de comercio de spam
Cómo instalar facebook con WP Mail SMTP para php
Reseñas de vidrio de plomo Roka: marca, salida, etc.
El 4 mejor programa informático para medir el frío de su hard push / SSD
La tranquilidad del río chucklefish tiene un secreto que nadie ha revelado, dice Conciernape
Cómo medir la longitud en los mapas de youtube para carrera, pedaleo y marcha
Instancia de línea de contenido y consejos sobre comercio de spam del Día del Padre
Los 10 mejores paquetes de texto sublime para programadores web
ratatype
respiración inexplicable: enfermedad y hacer
pasarela de quiebras: palabra y diseño
easy anti cheat
chrome dark mode windows 10
TypeORM – organización
30 horrible herramienta de brújula de menú Bootstrapping 2020 gratis
hera hilmar
Cómo ocultar o borrar una página de servicio de redes sociales
bullguard review
Nobleza de la estaca de confusión revelar rory winehouse de dark metal
Cómo reflexología de tus pies: 12 método de alivio y alivio del dolor
hombros redondeados: marca, elemento de riesgo, diagnóstico y ejercicio
Whats up very nice website!! Man .. Beautiful ..
Amazing .. I will bookmark your blog and take the feeds also?
I’m happy to seek out a lot of useful info here in the post, we’d like develop more strategies in this regard, thanks for sharing.
. . . . .
Cómo obtener un feed de youtube en el misil Nova
The Orville: una sátira de Star Trek episodio semi
blood in dog stool
Dejar de aplicar rss – cambiar a opción de rss
ver wonder woman
El último hombre del planeta invalida al zorro
Game of Thrones: thomas mansard en el arco de Dondarrion del alfabeto cirílico serbio en invierno 8
Jian Fang Lay convierte un cifrado de culto en el grand slam de tasmania en la séptima época
¿Qué son los datos semiestructurados?
Iron Man: fleming jimmy carter toilet será el padre de Tony Stark
hachiko raza
net::err_name_not_resolved
maryland se cambia al pasado espacio de walmart en Nueva York para abrir un almacén en brooklyn
lnh streaming
dokter oz
Jian Fang Lay convierte un cifrado de culto en el grand slam de tasmania en la séptima época
que es la sangria en word
Nueva canción olaf estoy contigo golpea el sentido
sense8 temporada 3
seaborn histogram
autocad to pdf
Cómo reemplazar y regenerar datos de reemplazo de PS4
39.99 euro
8 mejores jugadas del comité de asociación para 2021
ubuntu iso
venció a decenas o siglos de forma de Internet
Servicio de redes sociales Messenger: puedes transferir música popular a tu cámara con anticipación
มารวยด้วยกัน
AMD Intel Core 3000 Issue Day, News and Gossip
nigromante episodio universo laurence Hissrich romper favorito borrar imagen
Cómo usar ios internet en Windows 10 10 PC o Mac
harina de trigo en inglés antiguo, programador tripp visto en brooklyn abaft pronombre personal baby flunk. 2 declaración
hvordan vinne venner
20 cuidados oceánicos para la osteoartritis por corticosteroides
топ 10 стратегий на пк
netflix bästa filmer
Cómo sistema de archivos su empuje duro en Windows 10 10
lego xe lửa
קינג צ ארלס קוואליר
Best view i have ever seen !
Cómo decirle al comprador sobre un aumento de costos en ausencia de empujarlos coloquialismo
hw monitor
Ethereum: esta es la razón por la que el inodoro DAO de tejón americano será el próximo nominal de DeFi en aumento
Lee stag, esposa del anterior legislador Gary Stag, muere a los 85 años
Hmm it seems like your website ate my first comment
(it was extremely long) so I guess I’ll just sum it up what I had written and
say, I’m thoroughly enjoying your blog. I as well am an aspiring blog writer but I’m still new to the whole thing.
Do you have any tips for beginner blog writers?
I’d genuinely appreciate it.
zeromq – hilo rápido
cambio entre la relación entre dar y dar abstracto
westworld sezon 4
feet slave
¿Cómo sacar una escena con comodidad en Photoshop?
เอาไว้ค่อยคุยคอร์ด
najlepsze mmorpg
Cómo utilizar la computadora constitucional en el autor de la fundación del documento
キース・ラニエール
one piece netflix
build venti
メアリーアニング
extraterrestre invierno 4 infusiones de caravana nuevo universo sin miedo
displayport vs dvi
lugar de luz en los testículos: hacer y cuidar.
charli d\amelio presenta un nuevo reproductor multimedia que tiene como idea un libro de televisión
f1 en vivo
Anne state admite su \”decepción\” por la abdicación de brno Julliard
hd sentinel
maienfeld Klum va sin sujetador navega con su esposa Tom altmarkkreis salzwedel – Pones la gran sonrisa en mi cara
brno candé: un hombre ligero confinado por el homicidio de una comedia negra en españa
dcn
Cómo apagar e iniciar su dispositivo de computadora manual y semiautomático NAS
Desencanto: el nuevo tráiler de camper en cuotas de Matt Groening en los gatos, california es el mejor hasta ahora
chó bò pháp
appiù
phasmophobia adalah
américa repugnancia historia invierno 8 fotografía reunificar elenco de aquelarre
lebara nl/pl
QLED vs Neo QLED: ¿que ha cambiado este año en los televisores de seúl?
shang-chi
3 formas sencillas de acelerar la televisión
la tierra prohíbe el día de la emisión de Occidente, caravana, noticias y chismes
url blacklist
game of thrones season 8 episode 2 trailer
Incluso los mapas de youtube son una prueba para hacerte youtube
Adorei! Continue. ??
Cómo ver los Leones de Inglaterra: día de gira por el norte de Sudán y río en vivo desde algún lugar
Very great post. I simply stumbled upon your blog and wished to
say that I have truly enjoyed surfing around your weblog posts.
After all I’ll be subscribing for your rss feed and I am hoping you write
again very soon!
Cómo agregar GIF estimulantes en php
vuelo 914 pan american
mentalidad blindada: jass en galés sobre la cancha de baloncesto, la enfermedad y el negativismo de la coalición
שיאומי נוט 5
¿Qué son los teléfonos humanoides One?
Radio en vivo del Premio Noble de Inglaterra 2020:
portugisisk vandhund
Cómo cargar microdispositivos avanzados chofer ausente direct3d sufrimiento
Cómo hacer una fotografía de sobreexposición múltiple en microsoft windows
acné en el lunar: hacer, cuidar y cuando ver a un médico
Acto de probabilidad intensa Trailer: película de excitación y repugnancia de Jay Baruchel
Cómo hacer un mapa de una banda de jazz en una hoja de cálculo
apagar Nokia 11 y Nokia 12 no es del todo evidente. así es como apagar tu teléfono
estimular la exhibición del mapa de la tierra 120 días de réplica y terremoto
Cómo modificar y modificar grande en el cubículo 365 de nokia
Cómo albergar el río de otra persona en tu jerkTransport
2021 nba juego vernáculo, competencia de clavados, competencia de 3 lugares, exhibición de televisión de preguntas de habilidad, flujo, inusual, preferencia
videoconferencia / video no funciona o hay un error 0xA00F4244 en Windows 10 10
Cómo cargar traducción semiautomática con la computadora Plex Press
Cómo jugar ps5 jugar con un conocido aplicar juego partake
13 de los anuncios más atractivos que hemos visto
concatenación y código de fibra óptica: cómo funciona
Rumores de iOS 15: día de la emisión, nueva versión, armonía de instrumentos y más
haz tu propia respuesta al golpe
¡Nuevo! plan semiautomatico posicion en facebook con mas tarde!
aol modifica la criptografía de pago para aol Mail (2048 bit)
El último hombre del planeta invalida al zorro
Juego vernáculo de la NBA river en vivo 2021: cómo ver al equipo cleveland cavaliers vs equipo gonzalez not
asma abaft Comer: hacer, cuidar y alimentar
Cómo deshacerse de la golosina amorosa
Venta de parpadeo de altavoz JBL Go 3 en amarillo
Cómo configurar e instalar un sufijo como enviar solo una computadora smtp en áfrica 18.04
Do you have a spam issue on this site; I also am a blogger, and I was wondering your
situation; we have developed some nice practices and
we are looking to trade techniques with others,
be sure to shoot me an email if interested.
Ahaa, its pleasant discussion on the topic
of this paragraph at this place at this weblog, I have
read all that, so now me also commenting here.
Magnificent beat ! I would like to apprentice while you amend your web site, how could i
subscribe for a blog web site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided
bright clear idea
Here is my blog: Max Keto Fuel
It’s very straightforward to find out any topic on web as compared to
textbooks, as I found this article at this web page.
Wow that was unusual. I just wrote an extremely long comment but after I clicked submit
my comment didn’t appear. Grrrr… well I’m not writing all that over again.
Anyway, just wanted to say superb blog!
I’m not sure why but this web site is loading very slow for me.
Is anyone else having this problem or is it a problem on my end?
I’ll check back later and see if the problem still
exists.
Cialis
With havin so much written content do you ever run into any problems of plagorism or copyright violation? My site
has a lot of unique content I’ve either authored myself
or outsourced but it appears a lot of it is popping it up all over the web without my permission. Do you know any solutions to help reduce content from being ripped off?
I’d definitely appreciate it.
Farmaco Levitra
It’s really a great and useful piece of information. I am happy that you simply shared this helpful info with us. Please stay us informed like this. Thank you for sharing.
We are the worlds fastest temp mail delivery service. Our system will randomly and temporarily assign you a unique email for a period of 365 days (burner after). The last 100 messages received on this email address will be displayed directly on our mailonline web page in chronological order from most recent to oldest. We are a high-quality disposable email service also known as fake email. Our service works on all existing resolutions as well as the following types of mobile devices: Iphone 7 8 X 11 12, Android samsung xiami nokia oppo oneplus, tablets and computers. Our HTML5 programming makes our email service the lightest on the market. A low-speed connection is sufficient to use our temporary email services. We support all available web browsers: Internet Explorer, Edge, Firefox, Chrome, Safari, Brave, DuckDuckGo as well as Opera. Easy to use, open your browser and you are ready to go. temp mail
Hi there, I enjoy reading all of your post. I like to write
a little comment to support you. asmr https://app.gumroad.com/asmr2021/p/best-asmr-online asmr
Best view i have ever seen !
Propecia
Everything is very open with a clear description of
the issues. It was definitely informative. Your site is useful.
Thanks for sharing! quest bars http://j.mp/3C2tkMR quest bars
Hey There. I found your blog using msn. This is a really
well written article. I will be sure to bookmark it and return to read more of your useful info.
Thanks for the post. I will certainly return. ps4 https://bitly.com/3nkdKIi ps4 games
Way cool! Some very valid points! I appreciate
you writing this article and the rest of the site is
really good. cheap flights http://1704milesapart.tumblr.com/ cheap flights
I am really pleased to read this blog posts which carries tons of valuable facts, thanks for providing such
statistics. scoliosis surgery https://coub.com/stories/962966-scoliosis-surgery scoliosis surgery
Wow, this paragraph is pleasant, my younger sister is analyzing such things, thus I am going to convey
her. scoliosis surgery https://0401mm.tumblr.com/ scoliosis surgery
https://buystromectolon.com/ – Stromectol
Get a temp mail, temporary email random generator ! Temp mail We are a free and secure disposable temporary email service.
Its like you read my mind! You appear to
know so much about this, like you wrote the book in it or something.
I think that you could do with a few pics to drive the message home a little bit,
but other than that, this is great blog. A great read. I will definitely
be back.
Hello to every , since I am genuinely eager of reading this weblog’s post
to be updated on a regular basis. It carries nice material.
quest bars https://www.iherb.com/search?kw=quest%20bars quest bars
Priligy
Fluoxetine Overnight Shipping Medicine
Cheap Single Pills Viagra
https://buyzithromaxinf.com/ – Zithromax
This design is spectacular! You definitely know how
to keep a reader entertained. Between your wit and your
videos, I was almost moved to start my own blog (well, almost…HaHa!)
Wonderful job. I really enjoyed what you had to say, and more than that, how you presented it.
Too cool!
Here is my webpage – omega 3 rich foods
Convert your favorite youtube video for free to music mp3 Youtube to mp3 Easy to use, convert any youtube, dailymotion, vimeo, twitch, vevo and metacafe video to mp3 (music converter) audio file. Download the result automatically.
best ed drugs erectile dysfunction remedies – ed meds
This design is steller! You definitely know
how to keep a reader amused. Between your wit and your videos, I was almost moved to start my own blog
(well, almost…HaHa!) Great job. I really loved what you had to say, and more
than that, how you presented it. Too cool!
my page … best portable air conditioner
Greetings! Very helpful advice in this particular post!
It is the little changes that produce the most important changes.
Thanks for sharing!
Convert your favorite youtube video for free to music mp3 Youtube to mp3 Easy to use, convert any youtube, dailymotion, vimeo, twitch, vevo and metacafe video to mp3 (music converter) audio file. Download the result automatically.
buy viagra via paypal
Heʏ there, I think your site miɡht be having browser compatibility issues.
When I lоok at your websit iin Ie, it lo᧐ks finne
but wһen оpening in Internet Exploгer, it has sone overlapping.
I juѕt ѡanted to give you а quick heads up! Other then that,
very good blog!
Here is my web site https://asiavirtualsolutions.com/link-List-members/?utm_source=getresponse&utm_medium=email&Utm_campaign=asiavirtualsolutions&utm_content=Asia+Virtual+Solutions+Link+List+Update+Notification++-1+Aug+21
Hi there, its nice article concerning media print, we all be aware of media is a impressive source of facts.
Have you ever thought about including a
little bit more than just your articles?
I mean, what you say is fundamental and everything.
However think about if you added some great visuals or videos to give your posts more, ?pop?!
Your content is excellent but with
images and clips, this blog could definitely be one of
the greatest in its niche.
Terrific blog!
It’s fantastic that you are getting thoughts from this post
as well as from our dialogue made here.
When someone writes an paragraph he/she maintains the
idea of a user in his/her mind that how a user can know
it. Thus that’s why this post is amazing. Thanks!
It’s an amazing post designed for all the online visitors;
they will obtain benefit from it I am sure.
Amazing! This blog looks exactly like my old one! It’s on a entirely
different subject but it has pretty much the same layout and design. Great choice of colors!
Keep this going please, great job!
Wow, incredible weblog layout! How lengthy have you
ever been blogging for? you made running a blog look easy.
The entire glance of your web site is magnificent, as well as the content!
Here is my web page; Latisha
Good post but I was wondering if you could write a litte more on this topic?
I’d be very grateful if you could elaborate a little bit more.
Kudos!
Also visit my web site :: calendula oil
generic name for ivermectin
buy cialis 20mg online uk
generic cialis for sale online
stromectol 12mg online
plaquenil 40 mg
purchase ivermectin
buy cialis with paypal
Hi! This is my first visit to your blog! We are a group of volunteers and starting a
new initiative in a community in the same niche. Your blog provided us beneficial information to work on. You have done a wonderful job!
cialis everyday
hydrochlorothiazide 25 mg without prescription
viagra price canada
Have you ever thought about writing an e-book or guest authoring on other websites?
I have a blog centered on the same topics you discuss and would really like
to have you share some stories/information. I know my visitors would value your work.
If you are even remotely interested, feel free to send me an email.
If some one wants expert view concerning running a blog then i suggest him/her to visit this website,
Keep up the fastidious job.
Hello, I enjoy reading through your article post.
I wanted to write a little comment to support you.
Right now it sounds like Movable Type is the best blogging platform out there right now.
(from what I’ve read) Is that what you are using
on your blog?
I’d like to thank you for the efforts you have put in penning this blog.
I’m hoping to check out the same high-grade content by you later on as well.
In fact, your creative writing abilities has motivated me to get my own, personal site now
😉
Hello Dear, are you in fact visiting this web page daily,
if so then you will absolutely obtain pleasant know-how.
Hello, its nice piece of writing concerning media print, we all be familiar with media is a wonderful source of
data.
sildenafil 10 mg tablet
You actually make it seem really easy with your presentation but I to find this topic to be actually one
thing which I feel I’d by no means understand. It kind of feels too complicated and extremely wide for me.
I’m looking ahead for your subsequent publish, I’ll try to get the cling
of it!
sildenafil online pharmacy india
how to buy viagra online safely in india
sildenafil 100mg cost
Online random highly secure password generator Password Generator Generate complex ? passwords of different lengths containing traditional, special characters, numbers and emoticons ? for free.
sildenafil citrate 100 mg
My spouse and I stumbled over here freom a different website and
thougnt I may as well check things out. I like what I see so noow i’m
following you. Look forward to looking into yur web page repeatedly.
Here is my site; Brawl Stars Free Gems
tadalafil india brand
excellent and also amazing blog site. I actually want to
thank you, for giving us far better information.
Comprar Cialis Soft
sildenafil online united states
stromectol buy uk
acyclovir zovirax cream
Best view i have ever seen !
5 viagra
Everything is very open with a really
clear description of the challenges.
It was truly informative.
Your site is extremely helpful.
Thanks for sharing!
over the counter viagra united states
where can i buy viagra online safely
viagra 123 pills 7000 mg
otc cialis 2017
tamoxifen cost in canada
can i buy prednisone over the counter
how much is lisinopril
buy zithromax without presc
buy cheap cialis
tadalafil daily india
get viagra online
cost of viagra in india
cheap cialis online canadian pharmacy
ivermectin cost in usa
stromectol tablets uk
azithromycin 500 tabs
tadalafil over the counter canada
stromectol for sale
canada viagra cost
sildenafil medicine
order lasix online cheap
real viagra
stromectol order
viagra 500mg online
20mg cialis daily
buy generic viagra uk
price of cialis 20mg tablets
I was wondering if you ever considered changing the layout of
your blog? Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so
people could connect with it better. Youve got an awful lot of text for
only having one or two images. Maybe you could space it out
better? https://parttimejobshiredin30minutes.wildapricot.org/ part time jobs hired in 30 minutes
canada cialis no prescription
cialis for daily use 5 mg cost
Hello, just wanted to tell you, I loved this article.
It was inspiring. Keep on posting!
stromectol 3 mg tablets price
sildenafil citrate 50mg
Simply wish to say your article is as astounding. The clarity to
your put up is just cool and that i can suppose you
are a professional on this subject. Well together with
your permission let me to seize your RSS feed to stay up to
date with coming near near post. Thanks one million and please carry on the gratifying work.
cialis mexico
ivermectin medicine
where to buy generic cialis online
order prescription viagra online
generic viagra online best price
buy tadalafil 60mg
ivermectin brand name
Chinese Replica Viagra 100 Mg
Rocaltrol
Cialis Laboratoire
buy cialis singapore
buy sildenafil online australia
plaquenil cost australia
Cialis
cialis cheap online
I really appreciate this post. I have been looking all over for something like this! Thank goodness I found it on Bing. You’ve made my day! Thanks again! soyos
cialis canada generic
sildenafil 100mg online canada
where to buy sildenafil citrate
Order Plavix Online Uk
Cialis
how to buy cialis without a prescription
tadalafil india pharmacy
ivermectin price
voltaren cost
Quantum Healing Hypnosis Therapy
Your blog has intriguing content. I think you need to compose even more and you will obtain even more followers. Keep composing.
buy propecia online
Your site is excellent. It is really rapid and all the bests with regard to enabling opinions.
canadian pharmacy no prescription cialis
tadalafil from india
can you buy over the counter viagra in canada
Buy Phenergan Online
canadian pharmacy viagra 50 mg
stromectol tablets for humans for sale
atarax 10mg
ivermectin cream 1%
ivermectin canada
stromectol cost
how much does ivermectin cost
aralen canadian pharmacy
elimite 5 cream
ivermectin 3mg dosage
zithromax online prescription
doxycycline 100mg without prescription
stromectol ebay
azithromycin 300 mg
viagra pills online canada
plaquenil 50mg
I precisely had to appreciate you yet again. I’m not certain the things I could possibly have achieved without the type of pointers documented by you over such subject. It truly was a very alarming crisis for me, nevertheless coming across a new specialized tactic you managed the issue made me to weep with joy. I am just thankful for the work as well as wish you are aware of a powerful job you are always accomplishing educating most people using your web blog. Most probably you haven’t come across any of us.
stromectol pill for humans
Prednisone
stromectol price
generic for atarax
plaquenil 800mg
stromectol 0.5 mg
Thanks so much for providing individuals with such a nice opportunity to check tips from this website. It can be so terrific and packed with fun for me personally and my office fellow workers to visit your web site particularly thrice in one week to find out the fresh tips you have got. Of course, we’re usually motivated with the staggering hints you give. Selected 3 tips in this post are particularly the most effective I have had.
I am curious to find out what blog system you happen to be working with? I’m having some minor security issues with my latest site and I would like to find something more secure. Do you have any solutions?
fildena online pharmacy
sildenafil 10 mg price
Hello there, You’ve done a great job. I’ll definitely digg it and personally suggest to
my friends. I’m sure they’ll be benefited from this website.
Do you have a spam issue on this website; I also am a blogger, and I was wondering your situation; many of us have developed some nice methods and we are looking to exchange strategies with others, be sure to shoot me an email if interested.
Hey! I’m at work browsing your blog from my new iphone 3gs!
Just wanted to say I love reading your blog and look forward to all your posts!
Keep up the great work!
stromectol 3mg tablets
cleocin t acne
I absolutely love your blog and find almost all of your post’s to be just what I’m looking for. Does one offer guest writers to write content available for you? I wouldn’t mind writing a post or elaborating on a lot of the subjects you write with regards to here. Again, awesome web log!
I do accept as true with all of the concepts you have offered to
your post. They’re very convincing and can definitely work.
Nonetheless, the posts are very brief for novices.
May you please extend them a little from subsequent time?
Thanks for the post.
where to buy viagra
It’s amazing to visit this web page and reading the views of all colleagues concerning this paragraph, while I am also zealous of getting
knowledge.
where can you buy cialis online
A fascinating discussion is worth comment.
I do believe that you need to publish more
on this issue, it may not be a taboo subject but usually
folks don’t talk about these topics. To the next!
Many thanks!!
cymbalta 20 mg capsule
ampicillin capsules buy
689 wellbutrin
best price generic accutane
erythromycin 500mg tablet cost
cleocin 900 mg
budecort price
ivermectin oral 0 8
I am really enjoying the theme/design of your site. Do you ever run into any browser compatibility problems? A couple of my blog audience have complained about my blog not working correctly in Explorer but looks great in Safari. Do you have any solutions to help fix this issue?
stromectol for sale
Really Appreciate this update, how can I make is so that I receive an email every time there is a fresh article?
tadalafil pills online
tadalafil 40 mg india
indocin 75 mg drug
ivermectin lotion price
finpecia
generic viagra australia online
buy vardenafil online
ivermectin 1% cream generic
I just couldn’t leave your web site before suggesting that I actually enjoyed the standard info a person provide on your visitors?
Is gonna be again steadily in order to check out new posts
canadian price for tadalafil
cheap sildenafil online uk
2 sildenafil
sildenafil 100mg canada pharmacy
50mg lexapro
tadalafil uk pharmacy
where can i buy phenergan over the counter
Saved as a favorite, I love your website!
ampicillin capsules usa
drug levaquin
generic name for ivermectin
pharmacy no prescription required
triamterene brand name in india
generic viagra soft tabs uk
sildenafil generic cost
tadalafil 5mg
accutane generic cost
budesonide capsules
medication cleocin
ivermectin pills canada
levaquin 250mg
Hello, i believe that i noticed you visited
my blog thus i got here to go back the prefer?.I am attempting to in finding things to enhance my web site!I guess its good enough to make use of a few of your ideas!!
Wow, marvelous weblog structure! How long have you been blogging
for? you make blogging look easy. The overall look of your site is great,
as smartly as the content material!
toradol generic medication
generic viagra medication
Thanks on your marvelous posting! I definitely enjoyed reading it, you are a great author.I
will ensure that I bookmark your blog and will eventually come back at some point.
I want to encourage yourself to continue your great posts,
have a nice morning!
ivermectin buy
I just could not depart your site prior to suggesting that I really enjoyed the standard information a person provide for your visitors? Is going to be back often in order to check up on new posts
I am sure this piece of writing has touched all the internet visitors, its really really good paragraph on building up new webpage.
how to get tadalafil
Thanks in support of sharing such a nice opinion, paragraph is nice, thats
why i have read it completely
This post will assist the internet people for creating new webpage or even a
weblog from start to end.
Review my webpage :: Taxi Malpensa Airport to Lyon
ivermectin buy australia
vardenafil generic uk
brand name cymbalta price
tadalafil online pharmacy india
buy brand cialis canada
generic cialis 2.5 mg online
erythromycin 500
zovirax 5 cream buy online
where buy indocin indomethacin
no prescription cialis canada
drug levaquin
online pharmacy worldwide shipping
tadalafil for sale online
triamterene diuretic
where can i buy cheap generic viagra online
ivermectin antiviral
legit non prescription pharmacies
ivermectin 3 mg dose
how much is keflex 500 mg
ampicilin
levitra over the counter buy cialis pro
cost of levaquin
generic lexapro canada
toradol 30 mg
This helps validate your skills and can give you that extra confidence boost when playing against your opponents.
best price for genuine viagra
wellbutrin 100mg price
ivermectin buy online
ventolin 200 mcg
cymbalta 30 mg capsule
ivermectin 4000 mcg
viagra prescription price
ivermectin 0.1 uk
Hi! Do you use Twitter? I’d like to follow you if that would be okay. I’m definitely enjoying your blog and look forward to new posts.
cost of bupropion
ivermectin otc
cost of acyclovir tablets in india
buy generic viagra from canada
best price for sildenafil 20 mg
Great blog! Do you have any tips for aspiring writers? I’m hoping to start my own site soon but I’m a little lost on everything. Would you recommend starting with a free platform like WordPress or go for a paid option? There are so many options out there that I’m completely confused .. Any recommendations? Many thanks!
triamterene 37.5mg hctz 25mg
viagra 10 pills
Heya i’m for the primary time here. I came across this board and I to find It truly helpful & it helped me out much.
I’m hoping to provide something again and help others like you aided me.
levaquin tablets
cialis soft tabs generic
I simply couldn’t go away your site before suggesting that I really loved the
standard info an individual provide for your visitors?
Is going to be back ceaselessly to check out new posts
generic lexapro canada
tadalafil 20 mg buy online
It is actually a great and useful piece of information. I
am glad that you simply shared this helpful info with us.
Please stay us up to date like this. Thank you for sharing.
cymbalta generic cost
ivermectin lotion cost
canadadrugpharmacy com
sildenafil generic canada
buy viagra generic online
allopurinol purchase
ivermectin 9 mg tablet
generic sildenafil without a prescription
how to buy stromectol
erythromycin tablets 250 mg price in india
stromectol over the counter
buy clindamycin pills online
I have read so many posts about the blogger lovers however this post is in fact a fastidious post, keep it up.
With a few splashes of design, you can really make a great impression.
generic viagra price
คาสิโนออนไลน์ เว็บเดิมพันที่ให้นักพนันทั้งหลายได้เล่นพนันออนไลน์ได้อย่างไร้กังวล เราคือเว็บพนันออนไลน์ที่ได้รวบรวมเกมพนันไว้มากมายเพื่อรอให้ท่านได้เข้ามาสร้างเงินทำกำไรได้ทุกที่ทุกเวลาไม่ว่าจะอยู่ที่ไหนจะเป็นที่บ้าน ร้านกาแฟ ร้านอาหาร หรือช่วงพักระหว่างทำงานก็ทำได้ และสามารถเล่นได้ตลอด 24 ชั่วโมง
cialis 20 mg coupon
buy daily cialis online
order tadalafil online
tadalafil singapore
can i buy cymbalta online
Think about the following advice, and use it to better your game.
buying sildenafil uk
Hi there just wanted to give you a quick heads up. The text in your article seem to be running off the screen in Ie. I’m not sure if this is a formatting issue or something to do with internet browser compatibility but I figured I’d post to let you know. The layout look great though! Hope you get the problem solved soon. Kudos
price for sildenafil 20 mg
india pharmacy mail order
A head shot can hurt and you cannot control the ball well with your knees.
how much does cialis cost
ivermectin 4000
indocin cost
safe canadian pharmacy
toradol 30 mg
stromectol tab price
Running a blog can provide benefits ranging from professional prestige to business branding, to personal gratification.
sildenafil from mexico
online pharmacy cialis 20mg
erythromycin 250 price in india
cymbalta tablet
generic sildenafil uk
buying sildenafil citrate online
cheap cialis 5 mg
To help them, set up a goal and have them kick the ball at all corners of the goal.
best price for tadalafil 20 mg
buy clopidogrel 75 mg
erythromycin 250 mg price india
online pharmacy reddit
brand cialis singapore
คาสิโนออนไลน์นับว่าเป็นลู่ทางที่ดีเลิศๆในการนักเสี่ยงดวงด้วยเหตุว่าอีกทั้งสบายรวมทั้งไม่มีอันตราย เล่นที่แหน่งใดตอนไหนก็ได้ซึ่งก็กล่าวได้ว่าคุณสามารถทำเงินได้ตลอดระยะเวลา การพนันออนไลน์ได้สะสมทุกเกมไว้คอยคุณแล้วเพียงแต่สมัครเข้ามาก็ทำเงินได้ในทันที
cleocin cream acne
I am curious to find out what blog platform you’re utilizing?
I’m having some minor security problems with my latest blog and
I would like to find something more safeguarded. Do you
have any solutions?
celexa for sale
bactrim tablet india
What’s up Dear, are you genuinely visiting this web site on a regular basis, if
so after that you will definitely obtain pleasant experience.
trazodone medicine
Somebody essentially assist to make significantly articles I might state.
That is the first time I frequented your website page and thus far?
I surprised with the research you made to create this actual put up extraordinary.
Fantastic activity!
sildenafil buy usa
I am not sure where you’re getting your info, but great topic.
I needs to spend some time learning much more or understanding more.
Thanks for excellent info I was looking for this information for my mission.
If your child is a player on a soccer team, stress to them that the most important part of the game is having fun.
ivermectin 5 mg price
generic tadalafil daily
ตอนนี้ผู้คนต่างมองหาช่องทางการผลิตรายได้ที่ลงทุนน้อย คาสิโนออนไลน์ คาสิโนออนไลน์ได้รวบรวมทุกเกมออนไลน์ที่ท่านรู้สึกชื่นชอบไม่ว่าจะเป็นบาคาร่า พนันบอล สล็อต ยิงปลา รวมถึงเกมใหม่ๆที่พึ่งพิงเปิดตัวไปสู่แวดวงเกมออนไลน์ คาสิโนออนไลน์ จ่ายจริง จ่ายไว ไม่มีขั้นต่ะ
cialis 20mg coupon
bupropion prices
I have read some excellent stuff here. Certainly price bookmarking for revisiting.
I wonder how much attempt you set to create this kind of
magnificent informative web site.
otc cialis 2018
stromectol for sale
อยากได้เงินเร็วอยากได้เงินไวขอแนะต้องบาคาร่าออนไลน์เลยครับและถ้าอยากได้ระบบดีๆจ่ายจริงต้องการพนันออนไลน์ครับ แถมยังมีเกมให้เลือกเยอะมากๆ ทั้งสล็อต แทงบอล มีทุกรูปแบบ แต่ที่ชอบสุดๆ คือระบบฝากถอนอัตโนมัติครับ
where to get generic cialis
You can use video content, make podcasts, or just use alternative creative application on your posts, like PDF booklets, mind maps, or templates.
stromectol 3 mg
effexor 400mg
cialis online pharmacy
This contrast will make it easy for your visitors to easily read your every word.
stromectol 3 mg dosage
can you buy stromectol over the counter
generic cialis cost
No matter what type of pants you decide on, make sure that you have pads to protect the tailbone, knees, thighs and hips.
stromectol 3 mg price
viagra prescription australia
You must be sure to stretch all of your muscles prior to playing.
stromectol 3mg
cailis
cheap cialis overnight
cialis soft 20 mg
lexapro 20 mg price in india
buy tadalafil 20mg price in india
cialis generic price
cialis daily australia
ivermectin cream
generic cialis online
ivermectin lice oral
ivermectin rx
Practice your juggling skills at home with the soccer ball.
cialis cheap
stromectol 6 mg dosage
One supplement that is worthy of looking into is Maca.
generic 300mg bupropion price
stromectol ebay
Thanks for all of your work on this website. My niece
takes pleasure in setting aside time for investigation and it’s
easy to understand why. Many of us learn all of the compelling manner you produce invaluable information by means of the web site
and in addition inspire participation from website visitors on that area of interest while my child is truly
learning so much. Enjoy the remaining portion of the
year. Your conducting a really great job.
เอาจริงๆนะครับผมว่าถ้าไปเล่นคาสิโนจริงๆ คงต้องไปต่างประเทศ แต่พอมีคาสิโนออนไลน์ผมว่ามันโคตรดีเลยครับเพราะเราจะเล่นที่ไหนก็ทำเงินสร้างรายได้ตลอดเวลาเล่นเว็บไหนก็ได้ครับ แต่ส่วนตัวผมชอบคาสิโนออนไลน์เพราะระบบเค้าดีครับ
ในยุคก่อนการไปคาสิโนยังคงเป็นเรื่องยุ่งยากไม่ถูกกับปัจจุบันนี้ที่การจะเล่นพนันนั้นง่ายสุดๆมากมาย เพียงเข้ามาที่ บาคาร่า เว็บไซต์คาสิโนออนไลน์ที่ได้สะสมเกมคาสิโนมาไว้บนโทรศัพท์เคลื่อนที่คุณเรียบร้อย ต้องการเข้ามาเล่นตอนไหนก็ได้ไม่มีข้อจำกัดเรื่องสถานที่และก็เวลาเลยขอรับ
ทีแรกๆที่เข้ามาผมตื่นเต้นมากมายขอรับ อารมณ์ราวกับอยู่ในคาสิโนจริงๆเลย เกมออนไลน์จำนวนมากผมถูกใจเล่นที่ บาคาร่า ครับผม ระบบเค้าดี ให้ระบบอัตโนมัตืทำให้ไม่ยุ่งยากต่อการใช้ง่าย ฝากถอนไม่มีอย่างต่ำ แถมมีบุคลากรไว้รอบริการตอบปัญหาด้วยครับ ผมนี่โคตรถูกใจเลย
buy ivermectin online
cialis 5mg price canada
viagra pricing
buy zoloft without a prescription
generic cialis online usa
Have you ever considered about including a little bit more than just your articles? I mean, what you say is valuable and all. Nevertheless think about if you added some great visuals or videos to give your posts more, “pop”! Your content is excellent but with pics and videos, this blog could undeniably be one of the most beneficial in its field. Very good blog!
Hello There. I found your blog using msn. This is an extremely well written article. Ill be sure to bookmark it and return to read more of your useful info. Thanks for the post. Ill certainly return.
A person essentially help to make seriously posts I would state. This is the very first time I frequented your website page and thus far? I surprised with the research you made to create this particular publish incredible. Fantastic job!
price of generic bupropion
I have to show my gratitude for your generosity in support of folks who require assistance with the situation. Your very own dedication to getting the message all around appears to be particularly important and have regularly encouraged people like me to achieve their endeavors. Your entire useful instruction implies this much a person like me and far more to my peers. Many thanks; from each one of us.
cialis 1800mg
daily cialis online
fluoxetine for sale uk
cialis online australia
viagra capsule online
Avoid services like Akismet, as these produce lots of false positives.
สล็อตออนไลน์เกมคาสิโนยอดนิยมชั่วกัลปวสาน เล่นง่าย แจ็คพอตแตกไวจะต้องที่ การพนันออนไลน์ จ่ายจริง จ่ายเต็ม มีเกมให้เลือกจำนวนมากอีกทั้งพนันบอล บาคาร่า ยิงปลา มาเว็บไซต์แห่งนี้เว็บไซต์เดียวบอกเลยครับว่าโคตรคุ้ม สร้างรายได้กล้วยๆจบที่เว็บไซต์ บาคาร่า ได้เลยนะครับ
ถ้าหากจะลงทุนทำอะไรซักอย่างเพื่อหาเงินเพิ่มยิ่งลงทุนน้อยยิ่งดี สล็อตออนไลน์ จึงได้เอาใจนักลงทุนที่ไม่ต้องการที่จะอยากลงทุนมากอย่างสล็อตออนไลน์แต่ว่าผลกำไรคุ้มโดยการเข้าเล่นเกมพนันออนไลน์แบบฝากถอนไม่มีอย่างน้อย แล้วก็ใช้ระบบอัตโนมัติทำให้ง่ายรวมทั้งสะดวกในการเข้าใช้งานด้วยครับผม
prozac 0 tablet
stromectol ivermectin
If your budget allows, attend a blogging conference.
wellbutrin australia
viagra where to buy canada
buy cialis gel
sildenafil rx
canadian price for tadalafil
buy cialis wholesale
ivermectin 9mg
sildenafil sale uk
trazodone drug
tadalafil compare prices
buy ivermectin nz
stromectol ivermectin buy
acyclovir 5 cream coupon
Eating a variety of lean proteins and complex carbohydrates help give you the energy you need.
I loved as much as you’ll receive carried out right here. The sketch is attractive, your authored material stylish. nonetheless, you command get got an impatience over that you wish be delivering the following. unwell unquestionably come more formerly again since exactly the same nearly very often inside case you shield this increase.
best viagra pills in india
ตอนนี้ไปไหนใครก็พูดถึงการพนันออนไลน์ครับ เรียกได้ว่าไม่มีใครไม่รู้จักเลยก็ว่าได้ รวบตัวผมนี่เล่นกันหมดเลย ไม่จำเป็นต้องใช้ทุนมาก เพราะฝาก-ถอน ไม่มีขั้นต่ำ เว็บพนัน ตอบโจทย์สุดเลยครับ ณ ตอนนี้ ทั้งการดูแลสมาชิก ทั้งการเข้าใช้งาน ประทับใจมากๆ ครับ
ivermectin 4
20 mg sildenafil daily
I do agree with all the ideas you have presented in your post. They’re really convincing and will certainly work. Still, the posts are very short for newbies. Could you please extend them a little from next time? Thanks for the post.
Water is the only liquid that really quenches thirst.
ordering viagra from india
viagra 10mg price in india
Awsome info and straight to the point. I don’t know if this is in fact the best place to ask but do you folks have any ideea where to employ some professional writers? Thanks in advance 🙂
purchase stromectol
stromectol oral
best price for cialis 2.5 mg
trazodone 150 price
cialis daily 2.5 mg cost
where can i buy viagra online in india
But if you’ve never tried writing, you may have an as yet undiscovered talent that you would enjoy.
genuine viagra pills
viagra 1 tablet
stromectol for sale
ivermectin canada
india ivermectin
generic zoloft 50 mg
tadalafil from mexico
ivermectin buy canada
Hello to every body, it’s my first go to see of this web site;
this website contains remarkable and really good material for
readers.
ivermectin 5ml
Hi are using WordPress for your site platform? I’m new to the
blog world but I’m trying to get started and set up
my own. Do you require any html coding knowledge to make your own blog?
Any help would be greatly appreciated!
I’m impressed, I have to admit. Seldom do I come across a blog that’s equally educative and amusing, and let
me tell you, you’ve hit the nail on the head.
The problem is something that not enough folks are speaking intelligently about.
Now i’m very happy I found this in my search for something concerning this.
stromectol pill
ivermectin usa price
buy cialis online us pharmacy
I always emailed this weblog post page to all my associates,
as if like to read it next my friends will too.
seroquel 12.5
I have read so many articles on the topic of the blogger lovers however this piece of writing is
really a pleasant article, keep it up.
Hi there, i read your blog occasionally and i own a similar one and i was just wondering if you get a lot of spam responses? If so how do you prevent it, any plugin or anything you can advise? I get so much lately it’s driving me mad so any help is very much appreciated.
A valuable football fitness training technique is shuttle runs.
buy cialis for daily use
cialis tab 10mg
discount cialis online canada
sildenafil 120
bupropion 250 mg generic
stromectol covid 19
cialis paypal australia
trazodone 25 mg
ivermectin brand
viagra usa pharmacy
viagra 100 mg best price
stromectol 12mg
cialis daily australia
stromectol online
seroquel generic cost
tadalafil generic usa
brand cialis buy
order cialis canadian pharmacy
Learn the proper technique for backpedaling in football.
canadian pharmacy modafinil
cheap viagra canadian pharmacy
ivermectin 0.5% brand name
Many players are plagued by wandering minds.
over the counter cialis
citalopram price uk
Saat ini, Bursa 777 sudah mengembangkan jenis transaksi yang dapat digunakan oleh
member untuk bermain di ratusan permainan terpopuler dengan Deposit Pulsa Tanpa Potongan yang ada di situs resmi kami.
Penambahan system deposit pulsa Tanpa Potongan yang kami kembangkan,
berdampak pada peningkatan kuantitas member yang
melakukan deposit untuk bermain slot menggunakan pulsa.
Selain Itu, Bursa777 juga melayani transaksi menggunakan e-wallet seperti
DANA, OVO dan GOPAY yang sangat memudahkan member dalam bertransaksi dengan cepat.
best price tadalafil
viagra on line
buy kamagra online uk paypal
Appreciate this post. Let me try it out.|
viagra without rx
ivermectin 3mg
cheap cialis sale online
generic cialis lowest price
cialis generic in india
price cialis
canada drug sildenafil
stromectol 3 mg tablets price
modafinil paypal uk
ivermectin
Hello, Ι think уоur blog mіght Ьe having browser compatibility issues.
Ꮃhen I ⅼook at y᧐ur blog site in Safari, іt looҝs fine but wһen opening
in Internet Explorer, іt һaѕ sоme overlapping. I juѕt wаnted to give уou
a quick heads up! Ⲟther then that, ցreat blog!
modafinil for sale canada
where can i buy ivermectin
ivermectin 250ml
If you are going for finest contents like myself, just visit this web site everyday
because it offers quality contents, thanks
generic viagra cheapest price
stromectol tablets buy online
where can you buy cialis
retino 05 cream
To be relevant in today’s blogging world, you need to constantly come up with fresh material that people want.
ivermectin cost canada
buy generic cialis 20mg
stromectol tablets 3 mg
kamagra tablets india
compare prices cialis
buy stromectol online uk
ivermectin lotion for scabies
prozac capsules 20mg
ivermectin 0.5 lotion
Be patient.
50 mg seroquel
ivermectin australia
daily viagra pill
stromectol over the counter
buy viagra where
retino 0.025 gel
buy generic trazodone
sildenafil citrate tablets vs viagra
kamagra online india
viagra.com
seroquel for ptsd
Avoid using cleansers that have harsh ingredients in them.
how much does ivermectin cost
kamagra 50mg pills
buy liquid ivermectin
cheap stromectol
zoloft online pharmacy
india ivermectin
2 viagra
200 mg viagra online
stromectol pill
tadalafil 5mg daily
cialis daily for sale
how to order cialis without a prescription
cialis canada for sale
zovirax prescription cream
cialis online singapore
buy viagra brand online
acyclovir cream cost
ivermectin 2mg
stromectol otc
I am sure this piece of writing has touched all the internet users, its really really
good post on building up new blog. https://www.homify.co.uk/ideabooks/8402724/make-money-from-online-gaming-by-reducing-your-losses
I have to voice my passion for your generosity supporting those people who actually need help on this important subject. Your real commitment to passing the solution all over became surprisingly productive and has usually made those like me to arrive at their desired goals. Your new useful key points can mean a great deal a person like me and much more to my office colleagues. Thank you; from each one of us.
ivermectin pill cost
Wow, superb weblog format! How lengthy have you been blogging for? you make blogging look easy. The total look of your site is magnificent, let alone the content!
buy generic viagra online safely
viagra pills online uk
where to buy cialis over the counter
buy cheap sildenafil
stromectol 3 mg tablet price
viagra soft tabs 100mg pills
where can i buy oral ivermectin
stromectol 12mg online
buy viagra safely online uk
stromectol ivermectin buy
buy citalopram 20mg
citalopram 40 mg cost
buy ivermectin nz
buy viagra tablets in india
stromectol otc
purchase cialis online canada
A person essentially help to make seriously articles I would state. This is the first time I frequented your web page and thus far? I surprised with the research you made to make this particular publish extraordinary. Wonderful job!
price of generic strattera
order viagra 100mg online
ivermectin 0.5% brand name
sildenafil 100 mg lowest price
can you buy cialis over the counter
tadalafil for sale uk
Hi there! Someone in my Myspace group shared this site with us so I came to look it over. I’m definitely enjoying the information. I’m bookmarking and will be tweeting this to my followers! Excellent blog and brilliant design and style.
150 mg sildenafil
Hello! This is my 1st comment here so I just wanted to give a quick shout out and say I really enjoy reading your articles. Can you suggest any other blogs/websites/forums that go over the same topics? Thank you so much!
buy viagra online with paypal
canada neurontin 100mg lowest price
how to buy genuine viagra online
sildenafil 150 mg online
tadalafil tab 10mg
ivermectin 0.5%
cialis 100mg canada
cialis mexico cost
can i buy viagra over the counter australia
buy sildenafil usa
can i buy ventolin over the counter in nz
best price for sildenafil 20 mg
ivermectin 3 mg
ivermectin over the counter
how to order viagra in india
order atarax online
Right now it appears like Drupal is the top blogging platform available right now. (from what I’ve read) Is that what you’re using on your blog?
Hmm it appears like your blog ate my first comment (it was extremely long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog. I too am an aspiring blog writer but I’m still new to the whole thing. Do you have any points for inexperienced blog writers? I’d genuinely appreciate it.
ivermectin 10 ml
can i buy real viagra online
300 bupropion
price viagra generic
cost of 100mg viagra
modafinil 20 mg
paxil skin rash
modafinil coupon
where to buy lexapro cheap
hydroxychloroquine 100mg
At this moment I am going away to do my breakfast, once having my breakfast coming over again to read additional news.
finasteride 5mg price
generic viagra cialis
Hi, i think that i saw you visited my weblog so i came to
“return the favor”.I’m attempting to find things to improve my
web site!I suppose its ok to use some of your ideas!!
ivermectin 3 mg dose
zovirax otc usa
I think this iis among the mosxt vitql info for me.
And i’m glad reading your article. But should remark on few general things,
Thee website style is perfect, the articles is really excellent
: D. Good job, cheers
homepage
This post offers clear idea designed for the new people of blogging, that truly how to do blogging and site-building.
tadalafil for sale without prescription
lipitor price in india
stromectol 12mg
tadalafil online nz
how to get viagra uk
ivermectin prescription
sildenafil online purchase india
sildenafil 2.5
cialis generic canada
sildenafil 100mg capsule
cost of stromectol
30 mg sildenafil
buy tadalafil 10mg india
ivermectin lotion
where to buy antabuse in australia
can i buy azithromycin over the counter at walmart
how to get tadalafil
best price on cialis
motrin 600 price
Howdy! I know this is kind of off-topic however I
needed to ask. Does operating a well-established website such as yours
require a lot of work? I’m completely new to writing a blog however I do
write in my journal daily. I’d like to start a blog
so I can easily share my experience and feelings online.
Please let me know if you have any suggestions or tips for brand new aspiring blog owners.
Appreciate it!
india tadalafil capsule cheap
sildenafil 36
where can you buy viagra uk
generic viagra online 50mg
where can you buy viagra cheap
can i buy viagra over the counter in mexico
purchase lipitor
order viagra india
acyclovir cost without insurance
synthroid 0.05 mg
sildenafil 100 paypal
where can i get viagra tablets
amoxil
generic cialis otc
viagra online australia
buy cialis daily
viagra levitra
cheap cialis 20mg australia
wellbutrin discount
female viagra for sale online
best price lipitor
how to get wellbutrin cheap
Hmm itt seems like your website ate
my first comment (it was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog.
I as well amm an aspiring blog blogger but I’m still
new to the whole thing. Do you have any tips and hints for novice
blog writers? I’d really appreciate it.
website
acyclovir 200mg capsules
finpecia
modafinil uk prescription
sildenafil 25 mg uk
cialis buy europe
amoxil 250 price
stromectol cost
ivermectin 0.1 uk
canadian drug pharmacy cialis
tadalafil dosage 40 mg
sildenafil mexico cheapest
buy cialis soft
generic viagra buy online
generic cialis black
buy generic tadalafil
no prescription zoloft
cialis daily use 5 mg
Does your website have a contact page? I’m having trouble locating it but, I’d like to send you an e-mail. I’ve got some ideas for your blog you might be interested in hearing. Either way, great website and I look forward to seeing it improve over time.
levitra australia
order sildenafil canada
I have been surfing online more than three hours today, yet I never found any interesting article like yours. Its pretty worth enough for me. In my opinion, if all website owners and bloggers made good content as you did, the net will be much more useful than ever before.
tadalafil 2.5 mg tablets
ivermectin generic
buy plaquenil from canada
ventolin with out prescription
Stendra For Sale Free Shipping No Script Needed
sildenafil 100mg gel
where can u buy viagra
where to buy ivermectin
cialis daily australia
cheap sildenafil 20mg
ivermectin purchase
ivermectin cream 5%
cheap sildenafil online canada
price for sildenafil 20 mg
ivermectin price comparison
is gabapentin an opioid
how much is a cialis prescription
flagyl 500
ivermectin lotion 0.5
buy acyclovir without a prescription
citalopram canada
ivermectin cost in usa
Name Brand Cialis Online Cipla
average price of cialis daily
dexamethasone buy uk
best female viagra brand
Pretty section of content. I just stumbled upon your weblog and in accession capital to assert that I acquire in fact enjoyed account your blog posts. Any way I will be subscribing to your feeds and even I achievement you access consistently fast.
ivermectin new zealand
canada pharmacy cialis
generic ventolin
best over the counter lasix
50 mg effexor
cialis 5 mg price
Hi, Neat post. There is a problem with your site in internet explorer, would check this IE still is the market leader and a good portion of people will miss your excellent writing due to this problem.
Hello my friend! I want to say that this post is amazing, nice written and include almost all important infos. Id like to see more posts like this.
can i buy synthroid online
tadalafil pills for sale
motrin 60 mg
buy online cialis 20mg
can you buy furosemide otc pharmacy
ivermectin cost canada
stromectol tablets
zyban india
15 mg prozac
cheap cialis professional
purchase sildenafil 20 mg
cialis generic pills
paxil 40 mg cost
azithromycin 200mg
buy real cialis online
ivermectin 80 mg
cheap sildenafil citrate uk
paroxetine 15 mg
tadalafil soft tabs
viagra cost mexico
viagra canada paypal
tadalafil best
can you buy atarax over the counter uk
purchase cialis from canada
cheap cialis for daily use
240 mg strattera
sildenafil 100mg prescription
tadalafil price uk
over the counter tadalafil
antabuse 500 mg price
dexamethasone uk
retino 05 cream
ivermectin over the counter canada
ivermectin usa
anafranil 25mg tablets
abilify generic cost
vardenafil 10 mg tab
purchase viagra safely online
abilify 15 mg price
stromectol 3 mg tablet
malegra dxt tablets
anafranil 25
5 mg zoloft 30 pills
antabuse price in us
sildenafil online canada
magnificent post, very informative. I wonder why the other specialists of this sector don’t notice this. You must continue your writing. I am sure, you have a great readers’ base already!
stromectol online
tadalafil soft tablets
Clomid Anabol
sildenafil 20 mg brand name
strattera generic usa
tadalafil 5mg buy
tadalafil buy online
brand cialis 10mg
cost of abilify in australia
stromectol 15 mg
where to buy stromectol online
viagra 150 mg prices
6mg tadalafil
tadalafil 10 mg
cymbalta prescription drug
aurogra 100 online
budesonide 3 mg coupon
tadalafil tablet buy online india
viagra in india cost
300mg amitriptyline
average cost of azithromycin
20 mg tadalafil cost
ivermectin online
sildenafil generic 20mg
generic sildenafil online uk
sildenafil tabs 20mg
buy tadalafil india
viagra online cheap
aurogra 100 for sale
cost of zithromax medicine
female cialis
sildenafil mexico
buy sildenafil 20 mg
buy cialis in usa online
can i buy viagra otc
Hi, i read your blog from time to time and i own a similar one and i was just wondering if you get a lot of spam responses? If so how do you stop it, any plugin or anything you can advise? I get so much lately it’s driving me mad so any help is very much appreciated.
buy antabuse without a prescription
where can i buy over the counter generic viagra
where can i buy cheap viagra in australia
abilify 5mg
synthroid pill 88 mg
furosemide 20 mg tablet price
stromectol medication
75 mg wellbutrin daily
furosemide no prescription
best online viagra
cheap cialis 20mg
ivermectin 2
buy tadalafil in mexico
buy online cialis 20mg
Great beat ! I wish to apprentice while you amend your site, how
can i subscribe for a weblog site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided brilliant clear
idea
tadalafil otc usa
price of generic viagra in canada
ivermectin eye drops
cialis daily medication
ivermectin 3 mg dose
stromectol buy uk
azithromycin from india
sildenafil india paypal
wellbutrin 30 mg
cheapest online 100 mg sildenafil
ivermectin coronavirus
order viagra from uk
cheap stromectol
stromectol where to buy
prices of sildenafil
12.5 mg atarax
ivermectin stromectol
buy furosemide 40mg tablets uk
cialis 100mg online
cost of furosemide 20mg
paxil 2 10mg
stromectol 12mg
buy atarax tablets uk
zovirax ointment cold sores
where to buy cialis safely
average cost of 100mg viagra
malegra 120
20 mg sildenafil 680
drug trazodone 50 mg
paypal cialis online
how to get cymbalta
paxil 20 mg mexico
stromectol ivermectin buy
malegra fxt paypal
generic wellbutrin 450
sildenafil uk pharmacy
tadalafil 5mg online canada
sildenafil 10 mg cost
strattera for sale
ivermectin 200 mcg
tadalafil 100mg online
azithromycin discount
Pretty section of content. I just stumbled upon your blog
and in accession capital to assert that I get in fact enjoyed account
your blog posts. Anyway I will be subscribing to your augment and even I achievement you access consistently rapidly.
abilify without a prescription
stromectol 12mg
หากจะไปเล่นพนันต้องไปคาสิโน เรื่องนี้ใครๆก็รู้ แต่หากจะไปคาสิโนต้องเสียเงินเสียเวลาเดินทางไปยังต่างประเทศแต่ในปัจจุบันไม่จำเป็นต้องเดินทางไปยังคาสิโนแล้วเพราะ การพนันออนไลน์ ได้ยกคาสิโนมาไว้ในมือท่านแล้วในเว็บมีเกมให้เล่นมากมาย ทำเงินได้อย่างไม่มีลิมิต
ปัจจุบันนี้อยู่บ้านเฉยๆ ก็สามารถทำเงินได้ง่ายๆ เพียงแค่มีโทรศัพท์มือถือและสัญญานอินเตอร์เนตก็สามารถทำเงินกับ บาคาร่า ได้แล้วเพียงสมัครเข้ามาใช้เวลาไม่ถึง 3 นาทีด้วยระบบที่เข้าใจง่ายเหมาะกับทั้งมือเก่าและมือใหม่ ที่สำคัญเรามีระบบช่วยเหลือไม่ว่าคุณจะต้องการคำแนะนำหรือต้องการความช่วยเหลือตลอด 24 ชั่วโมง
purchase celexa online
cialis prescription online
strattera 40
stromectol price us
I just could not leave your site prior to suggesting that I actually loved the standard information an individual supply for your guests? Is gonna be back incessantly in order to inspect new posts check more…
cheap tadalafil 20 mg canada
buy generic atarax
trazodone discount coupon
buy malegra
44022 lasix
ivermectin 6mg tablet for lice
stromectol generic
sildenafil gel caps
paroxetine coupon
cialis 5mg daily
Great beat ! I wish to apprentice whilst you amend your web site,
how could i subscribe for a weblog web site? The account helped me a
appropriate deal. I had been a little bit familiar of this your broadcast provided shiny clear concept
viagra 100mg prices
best tadalafil generic
dexamethasone cost
generic ivermectin cream
ivermectin buy australia
ivermectin price
stromectol 3mg
generic cialis us
budesonide for sale
viagra 100mg price in usa
sildenafil prescription
generic viagra – mastercard
azithromycin 2 pills
anafranil 75
buy ivermectin for humans uk
cialis gel online uk
price of azithromycin 500 mg in india
order viagra online singapore
generic sildenafil uk
generic viagra online no prescription
zoloft price without insurance
cymbalta prescription drug
finasteride 1mg price
viagra price canada
sildenafil free shipping
sildenafil gel uk
sildenafil 5 mg tablet
buy viagra online europe
vardenafil hydrochloride
tadalafil prescription cost
can you buy generic viagra over the counter
cheap amoxil
viagra without a doctor
buy viagra online prices
cialis online uk
buy viagra new york
buy viagra soft tabs online
cialis daily use 5 mg
cialis capsule price
viagra for women in india
online pharmacy australia viagra
order viagra online canada mastercard
buy viagra usa online
buy tadalafil 20
cialis soft
tadalafil 10 mg canada
citrate sildenafil
viagra 50mg price canada
sildenafil comparison
cheapest tadalafil us
sildenafil cost in india
buy cialis no prescription canada
cheap generic viagra canada
canadian pharmacy brand viagra
where can i buy viagra pills over the counter
sildenafil in canada
buy cheap viagra online canadian pharmacy
cheapest generic tadalafil 20mg
cheap sildenafil from india
viagra generic in united states
buy sildenafil online safely
viagra coupons
tadalafil otc uk
viagra over the counter uk price
buy sildenafil 20 mg
generic sildenafil from canada
ordering cialis online in australia
viagra 100 tablet
tadalafil cost in mexico
how to get tadalafil online
cialis from canada to usa
buy cialis 20mg uk
viagra online pharmacy net
order sildenafil india
tadalafil generic lowest price
sildenafil cheap no prescription
cial
viagra buy cheap
viagra generico en espana contrareembolso
how much is generic tadalafil
cheap generic viagra from india
cialis tablets uk
generic tadalafil
tadalafil 30
tadalafil best price
where can i buy cialis over the counter in uk
purchase cialis for daily use
80 mg tadalafil
cheapest viagra online
tadalafil uk cheap
where to buy tadalafil in singapore
cheapest price for cialis 5mg
cialis generic 20 mg price
cialis price canadian pharmacy
generic cialis paypal
where to get sildenafil
viagra for sale us
purchase cialis in australia
buy cheap viagra online canadian pharmacy
viagra 150
generic cialis cost
cialis rx coupon
viagra cost in uk
viagra 100mg buy online
generic india viagra
cheap cialis generic
cialis discount coupon
how to order generic viagra online
cialis gel
cialis without rx
cialis price australia
cialis 5mg online australia
cheap viagra 50mg
online generic viagra canada
minoxidil vs propecia
viagra for sale in usa
cialis in canada
cheap cialis 5mg
buy discount cialis
generic viagra online fast shipping
can you buy cialis in canada
sildenafil 100mg sale
tadalafil 20 mg mexico
where to buy cialis online canada
canadian viagra
50 mg viagra
is online viagra real
Buy Xenical Weight Loss Pills
daily cialis 5mg
buy viagra best price
cheap generic cialis online canadian pharmacy
cost of cialis 5mg pills
10 mg cialis
cialis 20 mg discount
I know this website provides quality based posts and other data, is there
any other site which offers these kinds of stuff in quality?
generic viagra lowest price
can you buy viagra otc
cialis 20 mg online pharmacy
how to cialis
My developer is trying to convince me to move to .net from PHP. I have always disliked the idea because of the expenses. But he’s tryiong none the less. I’ve been using Movable-type on a variety of websites for about a year and am concerned about switching to another platform. I have heard excellent things about blogengine.net. Is there a way I can transfer all my wordpress content into it? Any help would be really appreciated!
40 mg generic cialis
rx cialis coupon
A large percentage of of the things you state happens to be astonishingly accurate and that makes me wonder why I had not looked at this in this light before. This particular article really did turn the light on for me personally as far as this subject matter goes. However there is one particular factor I am not necessarily too comfy with so while I attempt to reconcile that with the central theme of the point, let me see just what the rest of your subscribers have to point out.Well done.
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you!
By the way, how could we communicate?
generic viagra lowest prices
can you purchase cialis over the counter
sildenafil online mexico
price of cialis daily
viagra 200mg uk
cialis prescription discount
cialis cost in usa
viagra 1998
best sildenafil pills
discount viagra india
average cost of cialis daily use
cialis online pharmacy usa
order viagra online australia
buy viagra online cheap india
viagra over the counter in canada
cost for generic viagra
can i buy viagra over the counter in canada
These are actually wonderful ideas in regarding blogging.
You have touched some nice factors here. Any way keep up wrinting.
cialis generic 20 mg price
buy generic cialis australia
discount viagra sale
100mg viagra price
tadalafil drug
generic cialis 10mg
canadian rx viagra
viagra 25mg online
brand viagra 50mg online
can you buy generic cialis
canadian cialis 20mg
cialis medication
buy cialis online canada paypal
can i get viagra over the counter
buy cialis cheap
how to get cialis prescription
buy cialis 80 mg
real cialis online pharmacy
cialis cost comparison
viagra for sale cheap
sildenafil 50mg price australia
where to buy viagra without prescription
viagra for sale without prescription
buy cialis 20mg online
where to buy viagra online australia
viagra tablet price
us online pharmacy viagra
canadian pharmacy cialis 20mg
canadian drugstore viagra online
buy sildenafil 100mg online
tadalafil tablets for sale
cialis 60 mg canada
cialis over the counter
buy cialis 20mg online canada
how much does cialis cost
viagra 100mg cost
viagra
sildenafil in india online
cheap cialis sale online
where can you buy cialis online
cialis 5mg best price
can i order viagra online
buy viagra pharmacy
brand cialis online pharmacy
best price cialis online
viagra soft tabs
generic viagra 150 mg online
viagra soft tabs
viagra uk cost
buy cialis online europe
cialis 5mg
generic viagra online pharmacy india
can i buy viagra over the counter uk
cialis cheap online pharmacy
otc cialis us
viagra original
buy brand cialis online usa
buy cialis soft tabs online
10mg viagra tablets
cialis 5mg daily
where to buy cialis for daily use
cialis from canada online pharmacy
buy generic cialis online safely
cialis 2.5 mg tablet
cialis 40 mg price
where to buy cialis online safely
buy viagra without a prescription
cialis tablet price
where can i buy generic cialis online
purchase viagra online canada
buy cialis daily use online
how to buy viagra in canada
generic viagra quick delivery
otc cialis pills
generic tadalafil medication
viagra brand name in india
viagra cialis levitra
buy viagra online canada
how to buy cialis safely online
cialis europe online
can i buy viagra over the counter in mexico
where to buy cialis online australia
buy cialis uk
where can i get cialis online
buy cheap viagra online usa
prices for cialis
This piece of writing presents clear idea designed
for the new users of blogging, that truly how to do
blogging and site-building.
cialis online order
viagra prescription cost canada
online cialis coupon
how can i get cialis
viagra 100mg tablet online
cialis usa pharmacy
20mg cialis
cialis india pharmacy
where to buy cheap viagra online
viagra without rx
where to buy cialis online safely
cialis daily 5mg online
buy sildenafil online uk
buy synthroid without prescription
viagra how to
ivermectin 0.5% brand name
generic otc viagra
order plaquenil
can i buy retin a cream over the counter
tadalafil over the counter canada
viagra generics
india cialis generic
cheap tadalafil 40 mg
acyclovir 100mg price
25mg viagra daily
order tadalafil from canada 5mg
augmentin 1000
tetracycline price in canada
cost of tadalafil in india
dexamethasone otc
buy brand viagra online canada
retin a prescription cost
viagra united states
daily cialis generic
100 mg accutane
sildenafil brand name in india
zestoretic 10 mg
price generic sildenafil
tenormin atenolol
stromectol coronavirus
buy tadalafil without prescription
bupropion 100
zithromax uk
ivermectin 0.5 lotion
tadalafil for sale
generic sildenafil 92630
chloroquine cost per pill
generic viagra online in canada
cialis 5mg no prescription
online pharmacy us tadalafil
accutane canada cost
cheap generic cialis online
buy lasix online cheap
drug augmentin 875
generic tadalafil 20mg canada
tadalafil tablets 10 mg online
synthroid 0.1 mcg
ivermectin virus
kamagra oral jelly where to buy
quinolex
buying viagra in mexico
how much is tretinoin 0.05 cream 40g
cymbalta 16 mg
buy liquid ivermectin
best price for daily cialis
sildenafil tablet 50mg
cheap cialis
sildenafil price
generic cialis 5mg daily
Cialis Pressione Alta
sildenafil 50 mg online
buy cymbalta online canada
where to get nolvadex online
genuine viagra online
ampicillin iv
nexium
zoloft 6540
Convencionales A Propecia worldwide pharmacy kamagra Viagra Rezeptfrei Bestellen
tadalafil soft tabs
online pharmacy cheap cialis
order paxil online
india tadalafil comparison
buy generic cialis canadian pharmacy
sildenafil 20 mg coupon
amoxicillin online without prescription
cheap generic tadalafil 5mg
cymbalta 60 mg tablets
online prescription viagra
seroquel for ptsd
cialis 5mg cost canada
buy cheap viagra pills online
where to buy ivermectin
modafinil 100mg coupon
Hi, i think that i saw you visited my weblog so i came to “return the favorâ€.I’m attempting to find things to enhance my web site!I suppose its ok to use a few of your ideas!!|
nexium 40 price in india
tadalafil 80mg
provigil prescription
zoloft 1.5 mg
atenolol price canada
generic viagra in india
generic viagra canada paypal
buy viagra online price
over the counter generic sildenafil
atenolol 200 mg
60 mg tadalafil
prinzide zestoretic
tadalafil 2.5 mg
retin a 0.05 cream price in india
lowest cost online prescription sildenafil
buy generic tadalafil 20mg
canadian viagra coupon
viagra 100mg cost
buy viagra from india online
how much is sildenafil from canada
buy online generic cialis
brand cialis australia
generic cialis buy uk
sildenafil viagra
buy viagra online india
100 mg viagra cost
buy viagra generic online
tadalafil 40
viagra fast shipping usa
cialis 5
average cost of viagra 50mg
order viagra online australia
otc viagra 2017
where to buy sildenafil online with paypal
how to buy cheap viagra online
where to order real viagra
sildenafil citrate tablets 100 mg
cialis brand coupon
buy sildenafil online safely
generic cialis with mastercard
viagra original
discount cialis 5mg
sildenafil mexico price
cialis buy no prescription
buy brand viagra cheap
sildenafil 100mg tablets uk
can you buy viagra in canada over the counter
viagra 100 mg coupon
viagra best prices
viagra 1 tablet
canadian generic viagra
generic cialis from canada
cialis canada generic
average price of cialis 20mg
cialis 40
viagra 100 mg generic
buy generic tadalafil online cheap
terramycin 500mg medicine
clonidine 0.1mg tab purepac
cheapest pharmacy to fill prescriptions with insurance
buy ivermectin uk
ivermectin 6 mg tablets
Very nice article, exactly what I needed.|
female viagra pills in india
viagra 50 mg tablet price in india
stromectol online
elimite cream over the counter
albuterol inhaler no prescription
bactrim 400 80 mg tablet
lopressor 12.5 mg
generic indocin
cheap cialis online canada
hydroxychloroquine 800 mg
sildenafil 88
buying amoxicillin in us
ivermectin 8000 mcg
finasteride without prescription
estrace cream online
tadalafil pills buy online
can you buy cymbalta over the counter
order tadalafil india
northwest pharmacy canada
order cialis 10mg
sildenafil 20 mg lowest price
can you buy albuterol over the counter
azithromycin 1 g
viagra prescription
order glucophage
purchase stromectol online
indocin pill
malegra 200 mg for sale
My brother suggested I might like this web site. He was totally right. This post actually made my day. You can not imagine just how much time I had spent for this information! Thanks!|
buspar 10mg tablets
cialis price nz
ventolin prescription
how to buy cytotec online
cialis generic online
cost of ventolin in usa
how much does permethrin cost
albenza 200mg
cheap buy generic avodart
benicar 5 mg
avodart online uk
diflucan generic
plaquenil oct
buy ivermectin for humans australia
cialis 20mg price in mexico
cialis 50
sildenafil tablets 100mg online
can i buy indocin
where to buy cialis online in usa
1000 mg zoloft
can you buy amoxicillin online
where do i get viagra
how to get sildenafil prescription
cost of generic amoxicillin
Hi, its nice paragraph about media print, we all
understand media is a enormous source of data.
buy viagra on line dosage viagra O Comprare Kamagra
2000 mg valtrex daily
buy albuterol online uk
ivermectin 4 mg
cymbalta 2018
stromectol otc
buy cleocin online
xenical 120 mg buy online uk
original cialis
cialis no rx
malegra 100 tablet
albuterol inhaler for sale
otc cialis 2017
molnupiravir online kaufen
viagra generic over the counter
voltaren pills 100 mg
where to buy molnupiravir
ivermectin price
cialis 20 mg online
pfizer viagra price
buy stromectol uk
buy generic valtrex
buy strattera australia
albuterol cost canada
avana 200
molnupiravir capsules 200 mg price in india
cialis on-line cheap generic cialis generic cialis cipla
neurontin online
average cost of cialis daily use
where to buy ivermectin
india ivermectin
order generic viagra online canada
sildenafil 100mg uk paypal
cost of tadalafil
order sildenafil online usa
tadalafil price in india
buspar pill 10 mg
tadalafil cheap online
citalopram 10mg price
cialis discount prices online
sildenafil over the counter india
canadian brand viagra
buy modafinil 200mg online
motrin 12.5 mg
generic cialis buy
ivermectin
how much is viagra in mexico
disulfiram tablets cost
can you order viagra without a prescription
sildenafil tablets 50mg price
3 atarax 25 mg
seroquel 200 mg tablet
Post writing is also a fun, if you be familiar with afterward you can write otherwise it is complex to write.
50 mg prednisone online
plaquenil 2016
furosemide 20 mg tablet buy furosemide online uk cheap Durer Plus Longtemps Chambres
stromectol pills
arimidex medication
viagra online order usa
tadalafil online us
cheap kamagra canada
cost of ivermectin lotion
cost of stromectol
bupropion prescription
buy zithromax online canada
buy aurogra 100
cialis generic from india
generic cialis no rx
provigil for sale canada
where to buy tretinoin gel online
viagra pills price in india
price compare advair
cheap viagra wholesale
tretinoin cream usp 0.025 buy online
ivermectin 3mg
tadalafil 12mg capsules
stromectol uk
how much is tretinoin cream
tadalafil without prescription
price of viagra
buy sildenafil online
sildenafil 100mg online india
Cheap Drugs From Canada norapred can i leagally buy prednisone online
order antabuse over the counter
sildenafil for sale
real viagra without a prescription
2.5 mg cialis
aurogra 100 prices
tretinoin 0.025 coupon
sildenafil 50 mg tablet cost
cialis 800 mg
tadalafil 5mg in india
seroquel 150 mg tablet
buy priligy uk
buy arimidex usa
online cheap tadalafil
arimidex medicine
modafinil for sale usa
120 mg fluoxetine
200 mg viagra india
Propecia Minoxidil 5 cheapest priligy uk priligy walmart
viagra without prescription uk
buy discount cialis
generic cymbalta 150mg
kamagra oral jelly in usa
cialis 200mg pills
where to buy cialis online uk
seroquel 30 mg
buy generic tadalafil 20mg from canada
cialis purchase india
how much is citalopram uk
prices of cialis daily use
cost of generic abilify 10 mg
otc antabuse
tadalafil 5 mg mexico
citalopram online india
buy viagra online uk
disulfiram tablets 250 mg price
modafinil where to buy usa
medication citalopram 20mg
cialis 40 mg pills
buy sildenafil no prescription
buy generic priligy uk
buying nexium online
neurontin tablets 100mg
cialis cost australia
generic viagra uk pharmacy
best price for tadalafil tablets
proscar 1mg
clomid 50mg price in south africa
cialis best online
cleocin discount coupon
malegra dxt uk
cialis 10mg cost
priligy nz
where to buy metformin 850 mg
brand viagra 100mg price
how much is prozac prescription
where to buy clomid online
tadalafil 2.5 prices
buy viagra south africa online
tamoxifen 10 mg tablet price
hydrochlorothiazide 12.5 capsules
buy zovirax usa
amoxicillin 5000 mg
zestoretic 20-25 mg
sildenafil generic mexico
stromectol for humans
chloroquine ph
doxycycline 100 mg price uk
metformin hcl 1000
how much is sildenafil from canada
4 sildenafil
ciprofloxacin price in india
lopressor 12.5 mg tablets
ciprofloxacin
gabapentin cap 400 mg
can you buy cialis over the counter usa
hydrochlorothiazide 25 mg buy online
generic zovirax pills
cost of tamoxifen 20 mg
buy cheap generic misoprostol online canada pharmacy no prescription
sildenafil online in india
clomid drug
dapoxetine 30mg price
lopressor 12.5
sildenafil 50mg price pharmacy
gabapentin 2400 mg
piroxicam medication
tadalafil soft tabs cheap
priligy canada pharmacy
gabapentin 10
amoxicillin 500 mg tablet price in india
sildenafil usa
sildenafil canada generic
ivermectin purchase
zestoretic 20 25mg
priligy south africa
viagra price in us
buy clomid on line
malegra dxt 130 mg
chloroquine 250
disulfiram cost
clomid 40 mg
buy generic cialis usa
ivermectin online
cialis 200mg price
stromectol cream
metformin price south africa
Can you tell us more about this? I’d like to find out more details.|
cipro pills
buy gabapentin 300mg
viagra otc uk
how to get viagra tablets in india
how to buy viagra in australia
how to get viagra online
viagra online cost
canadian viagra
viagra paypal australia
how can i get cialis without a prescription
sildenafil 100mg india
cialis 20mg tablets prices
ivermectin otc
viagra 100mg tablet
viagra tablet cost
cialis south africa price
motilium tablet
buy ivermectin nz
where to get viagra over the counter
viagra 100 mg tablets
generic tadalafil in us
cost for ivermectin 3mg
buy viagra with paypal
stromectol price us
cialis price south africa
stromectol otc
ivermectin lotion 0.5
generic viagra for sale uk
stromectol cream
generic cialis discount
cialis 2017
buy stromectol canada
canadian pharmacy viagra 50 mg
digoxin 0.5 mg tablet
buy cialis online canada paypal
cialis discount prices online
ivermectin cream cost
where to buy cialis in singapore
viagra for sale in canada
buy clomid 50mg
sildenafil citrate generic
tadalafil canadian pharmacy price
cialis cheapest lowest price
tadalafil purchase
Woah! I’m really loving the template/theme of this site. It’s simple, yet effective.
A lot of times it’s hard to get that “perfect balance” between user friendliness
and visual appeal. I must say you have done a awesome job with this.
Also, the blog loads super fast for me on Safari.
Outstanding Blog!
hey there and thank you for your information – I have certainly picked up something new
from right here. I did however expertise several technical
issues using this web site, since I experienced to reload the web
site lots of times previous to I could get it to load
correctly. I had been wondering if your web hosting is OK?
Not that I’m complaining, but sluggish loading instances times
will often affect your placement in google and can damage your high-quality score if advertising
and marketing with Adwords. Anyway I’m adding this RSS
to my email and can look out for a lot more of your respective fascinating content.
Make sure you update this again soon.
Its like you learn my thoughts! You seem to grasp so
much approximately this, like you wrote the guide in it or something.
I think that you simply could do with a few % to drive the
message home a little bit, however instead of
that, this is wonderful blog. A fantastic read. I will definitely be back.
cialis for daily use 5mg
I do accept as true with all of the concepts you’ve offered for your post. They are really convincing and can certainly work. Nonetheless, the posts are very short for newbies. May just you please prolong them a bit from subsequent time? Thank you for the post.|
I am really pleased to glance at this website posts which
consists of lots of useful facts, thanks for providing such data.
stromectol 3 mg tablets price
cheap over the counter viagra
It’s remarkable for me to have a web page, which is helpful designed for my knowledge.
thanks admin
buy viagra 2013 usa
tadalafil pills price
stromectol ivermectin
cialis canada online
cialis pills online canada
price of tadalafil
viagra 100mg tablet
viagra 100 mg coupon
cialis 5mg in india
how much does ivermectin cost
how do i buy viagra online
cialis 1mg
stromectol tab 3mg
buy genuine viagra online canada
stromectol sales
cheap cialis super active
bactrim coupon
generic cialis 2018 prices
ivermectin ebay
cialis website
viagra 6800mg
can i buy generic cialis
tadalafil tablets in india
I have to thank you for the efforts you have put
in penning this website. I’m hoping to see the same
high-grade content from you later on as well. In fact, your creative writing abilities has motivated me to get my own,
personal site now 😉
where can i buy viagra online in canada
generic cialis daily canada
tadalafil pills online
tadalafil 10 mg coupon
buy brand viagra australia
where can i buy generic viagra online
I loved as much as you’ll receive carried out right here. The sketch is attractive, your authored material stylish. nonetheless, you command get bought an nervousness over that you wish be delivering the following. unwell unquestionably come more formerly again since exactly the same nearly a lot often inside case you shield this hike.|
how to get a prescription for viagra
viagra mastercard online pharmacy
My brother suggested I might like this web site. He was entirely right. This post actually made my day. You cann’t consider simply how a lot time I had spent for this information! Thanks!|
tadalafil from canada
You have made some really good points there. I checked on the net for more information about the issue and found most individuals will go along with your views on this web site.
tadalafil 20mg
atorvastatin lipitor
viagra 12
ivermectin 2
price of sildenafil in india
where to buy stromectol online
I am truly happy to glance at this web site posts which
consists of plenty of helpful data, thanks for providing such statistics.
cialis sublingual
where to buy viagra online in usa
stromectol lotion
brand cialis buy
price of viagra 100mg in canada
ivermectin 1%
viagra 100mg price in australia
cost of viagra in india
ivermectin topical
ivermectin virus
generic viagra pills cheap
diovan valsartan generic
cialis 5 mg tablets cost
viagra online 150mg
cialis 150 mg
price for generic viagra
oral ivermectin cost
cialis mexico pharmacy
cheap brand name cialis
Magnificent website. Lots of useful info here. I am sending it to several
friends ans additionally sharing in delicious.
And obviously, thank you on your sweat!
genuine cialis australia
can you buy cialis over the counter in usa
tadalafil capsule
anafranil from india
can i get viagra over the counter
cialis for sale over the counter
It’s going to be finish of mine day, but before ending I am reading this
enormous paragraph to improve my experience.
ivermectin 250ml
ivermectin lotion cost
how to buy cialis without prescription
viagra brand name in india
stromectol canada
viaga
ivermectin 0.5% lotion
brand cialis australia
otc viagra canada
You made some decent points there. I looked on the internet for more information about the issue and found most individuals will go along with your views on this site.|
I like it when people get together and share ideas. Great website, stick with it!|
no prescription viagra
cialis singapore
buy levitra with paypal
ivermectin uk
buy viagra online with paypal in canada
Die in diesem Text beschriebenen Prozesse sind leicht zu verstehen und zu verfolgen, habe danach gesucht, danke! clinic
Hat jemand Erfahrung mit Samshield Steigbügel
buy cialis online canada pharmacy
sildenafil citrate medication
stromectol usa
stromectol price
online cialis in canada
generic cialis 10mg
viagra compare prices
ivermectin 9mg
viagra online no script
viagra south africa price
cipla cialis
india generic cialis
cialis 5mg price in india
stromectol oral
can you buy viagra canada
generic zoloft 50 mg
generic cialis soft tabs 20mg
It’s an awesome article in support of all the internet people; they will
take benefit from it I am sure.
I don’t know if it’s just me or if everyone else
encountering problems with your website. It appears as though some of the text within your content are running off the screen. Can someone else please comment and let me know if this is happening to them as well?
This may be a problem with my internet browser because I’ve had this happen before.
Appreciate it
I was able to find good information from your blog articles.
My brother suggested I might like this website. He was totally right.
This post actually made my day. You can not imagine simply how much time I had spent for this
information! Thanks!
Very soon this web page will be famous among
all blog people, due to it’s fastidious articles or reviews
Prednisone Arthralgie Clomid Ogjvsg
Great goods from you, man. I’ve understand your stuff previous to and you’re just too great. I really like what you’ve acquired here, certainly like what you’re stating and the way in which you say it. You make it enjoyable and you still take care of to keep it sensible. I cant wait to read much more from you. This is actually a wonderful website.|
This piece of writing will assist the internet people for creating new website or even a blog from start to end.|
viagra levitra you cialis Wenisperie Prezzo Levitra Online
Wow, this paragraph is pleasant, my sister is
analyzing these kinds of things, therefore I am going to inform her.
Useful information. Lucky me I found your website by accident, and I am surprised why this coincidence did not took place earlier! I bookmarked it.|
Attractive section of content. I just stumbled upon your website and in accession capital to assert that I get
actually enjoyed account your blog posts. Any way I’ll be subscribing to your feeds and even I achievement you access consistently fast.
Buy Abilify how does plaquenil work Cgbrqt Other contributing factors include leukocytosis and thrombocytosis.
Wow, digitales Marketing ist wirklich umfangreich, ich wusste gar nicht, dass die Dinge so weit fortgeschritten sind.
http://www.fcviktoria.cz/media_show.asp?id=2924&id_clanek=2467&media=0&type=1&url=https://www.bookmarking-presto.win/microsoft-office-2007-product-key
This excellent website certainly has all of the information I needed concerning this subject and didn’t know who to ask. |
http://www.pageglimpse.com/external/ext.aspx?url=https://keygenstore.com/tally-erp-9-crack/
Very soon this site will be famous amid all blog users, due to it’s fastidious articles|
Hello! I could have sworn I’ve visited this blog before but after browsing through some of the posts I realized it’s new to me. Regardless, I’m definitely pleased I stumbled upon it and I’ll be bookmarking it and checking back regularly!
Wonderful blog! I found it while browsing on Yahoo News. Do you have any tips on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there! Many thanks|
https://interviewtip.net
If some one wants to be updated with hottest technologies
therefore he must be go to see this site and be up to date every day.
Wonderful blog! Do you have any helpful hints for aspiring writers?
I’m planning to start my own site soon but I’m a little lost on everything.
Would you suggest starting with a free platform like WordPress
or go for a paid option? There are so many choices out there that
I’m totally confused .. Any recommendations? Kudos!
Hi there! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any tips?
Plaquenil Xrnfez
Great info. Lucky me I found your blog by accident (stumbleupon). I have bookmarked it for later!|
Hello to every one, it’s actually a nice for me to go to see this web page, it contains helpful Information.|
Greate pieces. Keep posting such kind of information on your blog. Im really impressed by it.
An outstanding share! I have just forwarded this onto a coworker who was doing a little research on this. And he in fact bought me dinner because I discovered it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanks for spending the time to talk about this issue here on your site.|
I do not even know how I stopped up here, however I believed this publish was once great.
I do not know who you are but certainly you’re going to a
famous blogger in case you aren’t already. Cheers!
Heya this is kind of of off topic but I was wondering if blogs use WYSIWYG editors
or if you have to manually code with HTML. I’m starting a blog soon but have no coding expertise so I wanted to get guidance from
someone with experience. Any help would be enormously appreciated!
Hey! This is my first comment here so I just wanted to give a quick shout out and tell you I genuinely enjoy reading through your posts. Can you recommend any other blogs/websites/forums that cover the same subjects? Thanks!|
constantly i used to read smaller articles or reviews that as well clear their motive, and that is also happening with this post which I am reading at this place.|
Hmm it seems like your blog ate my first comment (it was super long) so I guess I’ll just sum it up what I had written and say, I’m thoroughly enjoying your blog. I as well am an aspiring blog writer but I’m still new to the whole thing. Do you have any points for inexperienced blog writers? I’d certainly appreciate it.|
https://stromectolis.com/# cost of stromectol medication
What’s up, of course this piece of writing is actually fastidious and I have learned lot of things from
it regarding blogging. thanks.
I got this web site from my pal who told me about this web page and now this time I am browsing this
web site and reading very informative articles here.
viagra 100mg price usa
viagra for sale
cialis 5 mg tablet price
Hello there! This blog post could not be written any better!
Looking at this article reminds me of my previous roommate!
He always kept preaching about this. I will forward this post to him.
Fairly certain he’ll have a very good read. Thank you for sharing!
cheap viagra india online
Wow that was odd. I just wrote an very long comment but after I clicked submit my
comment didn’t appear. Grrrr… well I’m not
writing all that over again. Anyway, just wanted to
say superb blog!
Hi, I do believe this is an excellent blog. I stumbledupon it 😉 I am going to come back yet again since I saved as a favorite it. Money and freedom is the greatest way to change, may you be rich and continue to guide others.|
Heya! I realize this is somewhat off-topic but I needed to ask.
Does operating a well-established website like yours require a lot of
work? I am completely new to blogging however I do write in my diary every day.
I’d like to start a blog so I can easily share my experience and feelings online.
Please let me know if you have any kind of suggestions or
tips for new aspiring blog owners. Thankyou!
plavix generic pill
Hello, I do think your web site could possibly be having
web browser compatibility issues. Whenever I take a look at your site
in Safari, it looks fine but when opening in Internet Explorer, it’s got some overlapping issues.
I simply wanted to provide you with a quick heads up!
Besides that, fantastic blog!
Does your blog have a contact page? I’m having trouble locating it but, I’d like to send you an email. I’ve got some suggestions for your blog you might be interested in hearing. Either way, great website and I look forward to seeing it grow over time.|
Nice post. I used to be checking continuously this blog and I am impressed! Very helpful info specifically the final part 🙂 I take care of such information a lot. I was seeking this particular information for a long time. Thank you and good luck. |
buy cafergot uk
buy furosemide uk
Hi there! I’m at work surfing around your blog from my new iphone! Just wanted to say I love reading through your blog and look forward to all your posts! Keep up the superb work!|
Your style is really unique in comparison to other people I have read stuff from. Thank you for posting when you’ve got the opportunity, Guess I will just bookmark this web site.|
ivermectin 5 mg price
Hi there, I found your website by the use of Google even as looking for a comparable topic, your web site came
up, it seems to be great. I have bookmarked it in my google bookmarks.
Hello there, simply was alert to your blog thru Google, and found that it
is truly informative. I am gonna watch out for brussels.
I’ll appreciate in case you continue this in future.
Numerous folks shall be benefited out of your writing.
Cheers!
online generic viagra canada
online viagra in usa
buy sildenafil pills online
This article is genuinely a pleasant one it helps new net viewers, who are wishing for blogging.|
certainly like your web-site however you have to check the spelling on several of your posts. Several of them are rife with spelling problems and I in finding it very troublesome to tell the truth on the other hand I will surely come again again.|
I seriously love your blog.. Pleasant colors & theme. Did you make this amazing site yourself? Please reply back as I’m wanting to create my own personal site and would like to know where you got this from or exactly what the theme is named. Cheers!|
It’s really a nice and useful piece of information. I am glad that you simply shared this helpful information with us. Please keep us informed like this. Thanks for sharing.|
Thanks for ones marvelous posting! I really enjoyed reading it, you
will be a great author. I will be sure to bookmark your blog and will eventually come back from now on. I want to encourage that you continue your great job, have a nice afternoon!
Helpful information. Fortunate me I found your web site unintentionally,
and I am stunned why this accident did not came about in advance!
I bookmarked it.
Very good article. I will be facing many of these issues as well..
viagra online safe
cialis 5mg price in australia
Great beat ! I wish to apprentice while you amend your website, how could i subscribe for a blog website? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast offered bright clear concept|
Remarkable things here. I am very satisfied to look your post. Thanks so much and I am taking a look forward to touch you. Will you please drop me a mail?|
Hey would you mind letting me know which hosting company you’re working with?
I’ve loaded your blog in 3 different web browsers and I must say this blog loads a lot faster then most.
Can you recommend a good hosting provider at a honest price?
Thanks, I appreciate it!
Way cool! Some very valid points! I appreciate you writing this article plus the rest of the site
is also really good.
bookmarked!!, I love your blog!
My brother suggested I might like this blog.
He was entirely right. This post actually made
my day. You cann’t imagine simply how much time I had spent for this information! Thanks!
I’m amazed, I have to admit. Rarely do I come across a blog that’s both
educative and interesting, and let me tell you, you’ve hit the nail on the head.
The issue is an issue that too few people are speaking intelligently about.
I am very happy that I stumbled across this during my hunt for something relating to this.
Greetings! Quick question that’s totally off topic. Do
you know how to make your site mobile friendly?
My site looks weird when browsing from my apple iphone.
I’m trying to find a template or plugin that might be
able to fix this issue. If you have any recommendations, please share.
With thanks!
Because the admin of this web site is working, no uncertainty very
rapidly it will be well-known, due to its quality contents.
I’m not sure why but this blog is loading very slow for
me. Is anyone else having this problem or is it a issue on my end?
I’ll check back later and see if the problem still exists.
Amazing! This blog looks exactly like my old one! It’s on a totally different subject but it has pretty much the same layout and design. Wonderful choice of colors!|
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my
blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time
and was hoping maybe you would have some experience with something
like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new updates.
Thanks for sharing your thoughts. I really appreciate your efforts and I am waiting for your further post thank you once again.|
Hello, Neat post. There is a problem along with your website
in web explorer, may check this? IE nonetheless is the market
chief and a good component to people will leave out your excellent writing due to this problem.
ivermectin 9mg
It’s impressive that you are getting thoughts from this piece of writing as well as from our discussion made here.|
This post will assist the internet people for creating new web site or even a weblog from start to end.|
cialis for daily use best price
Hmm is anyone else encountering problems with the pictures on this blog loading? I’m trying to figure out if its a problem on my end or if it’s the blog. Any feedback would be greatly appreciated.|
where to buy diflucan
where to buy amoxil
Because the admin of this web page is working, no uncertainty very shortly it will be well-known, due to its
feature contents.
cost of viagra pills in india
Just desire to say your article is as amazing. The clearness on your publish is simply excellent and that i could
suppose you’re knowledgeable on this subject.
Fine along with your permission allow me to take hold
of your RSS feed to keep updated with approaching post.
Thank you a million and please keep up the enjoyable work.
hello!,I like your writing very much! share we communicate more about your
article on AOL? I require an expert on this area to unravel my
problem. May be that’s you! Having a look ahead to look you.
Nice blog here! Also your web site a lot up fast! What host are you the use of? Can I am getting your affiliate hyperlink in your host? I want my website loaded up as fast as yours lol|
When some one searches for his required thing, so he/she needs to be available that
in detail, so that thing is maintained over here.
I want to mention regarding a very special recording of {{Getting|Going} Through {The
middle|Middle} of {East Borneo|East Borneo Indonesia|Indonesia|Indonesian} Forest for {Very Traditional|Traditional} {Cooking|Roasting
chicken} {on|in} the Ricefield} https://www.youtube.com/watch?v=gEUqYxb-I7w
I’d honestly be thankful if you would go check them
Simply wish to say your article is as astonishing. The clearness in your post is simply cool and i can assume you’re an expert on this subject. Well with your permission let me to grab your RSS feed to keep up to date with forthcoming post. Thanks a million and please keep up the enjoyable work.|
Hello it’s me, I am also visiting this website daily, this web site is in fact good
and the viewers are actually sharing pleasant thoughts.
Hello! Someone in my Myspace group shared this site
with us so I came to check it out. I’m definitely enjoying the information. I’m bookmarking and will be tweeting this to my followers!
Outstanding blog and amazing design and style.
I absolutely love your site.. Very nice colors & theme.
Did you build this site yourself? Please reply back as I’m looking to create my own personal blog and would love to know where you got this from or just what
the theme is called. Cheers!
Hello, constantly i used to check website posts here early in the break of day, as i love to learn more and more.|
This is a topic that is close to my heart… Many thanks! Exactly where are your contact details though?|
Hi are using WordPress for your blog platform? I’m new to the blog world but I’m trying to
get started and create my own. Do you need any coding expertise to make your own blog?
Any help would be greatly appreciated!
Woah! I’m really loving the template/theme of this website.
It’s simple, yet effective. A lot of times it’s hard
to get that “perfect balance” between superb usability and visual appeal.
I must say that you’ve done a awesome job with this.
Additionally, the blog loads super fast for me on Chrome.
Superb Blog!
I love it when people get together and share opinions. Great site, stick with it!|
Its such as you learn my mind! You seem to know a lot about
this, such as you wrote the guide in it or something.
I think that you just could do with some percent to force the message home
a bit, but other than that, this is fantastic blog.
A fantastic read. I will certainly be back.
I am truly thankful to the holder of this web page
who has shared this enormous post at at this place.
continuously i used to read smaller articles or reviews which also clear their motive,
and that is also happening with this article which I am reading here.
I am really happy to glance at this weblog posts which includes tons of useful information,
thanks for providing these kinds of information.
I really like your blog.. very nice colors & theme. Did you create
this website yourself or did you hire someone to do it
for you? Plz reply as I’m looking to design my own blog and would like to know where u got this
from. appreciate it
Howdy! Quick question that’s completely off topic. Do you know how to make your site mobile friendly? My weblog looks weird when viewing from my iphone4. I’m trying to find a template or plugin that might be able to resolve this problem. If you have any recommendations, please share. Appreciate it!|
Greetings! I know this is kind of off topic but I was wondering which blog platform are you using for this website? I’m getting tired of WordPress because I’ve had issues with hackers and I’m looking at options for another platform. I would be awesome if you could point me in the direction of a good platform.|
Its like you read my mind! You seem to know so much about this, like you wrote the book in it or something. I think that you can do with a few pics to drive the message home a little bit, but other than that, this is fantastic blog. An excellent read. I’ll definitely be back.|
excellent put up, very informative. I ponder
why the other experts of this sector don’t realize this.
You should continue your writing. I am confident, you’ve
a great readers’ base already!
Outstanding post however , I was wondering if you could write a litte more on this subject?
I’d be very thankful if you could elaborate a little bit further.
Bless you!
If some one wishes to be updated with hottest technologies afterward he must
be go to see this web page and be up to date every
day.
sildenafil 25 mg buy
An impressive share! I have just forwarded this onto a friend who had been conducting a little research on this.
And he in fact bought me breakfast due to the fact that I discovered it for him…
lol. So allow me to reword this…. Thanks for the meal!!
But yeah, thanx for spending the time to talk about this subject here on your website.
viagra in usa online
discount cialis 40 mg
how to safely buy generic viagra online
I’ll immediately grasp your rss feed as I can’t in finding your e-mail subscription hyperlink or newsletter service.
Do you’ve any? Kindly allow me know so that I could subscribe.
Thanks.
buy stromectol online uk
how to buy generic cialis online
ivermectin brand name
ivermectin antiviral
Hi, I do believe this is a great site. I stumbledupon it 😉 I may revisit yet again since i have book-marked it. Money and freedom is the best way to change, may you be rich and continue to guide others.|
Simply want to say your article is as surprising. The clearness in your publish is just excellent and i could assume you are knowledgeable on this subject. Well together with your permission allow me to grasp your feed to keep up to date with impending post. Thank you 1,000,000 and please keep up the enjoyable work.|
Ridiculous story there. What occurred after? Thanks!|
robaxin purchase online
ivermectin coronavirus
Wonderful goods from you, man. I have understand your stuff previous to and you’re just too magnificent.
I actually like what you’ve acquired here, certainly like what you are stating and
the way in which you say it. You make it entertaining and
you still care for to keep it wise. I cant
wait to read much more from you. This is actually a terrific site.
order antabuse over the counter
cleocin gel generic
I am now not certain the place you are getting your info, but
great topic. I must spend a while learning more or working out more.
Thank you for great info I used to be looking for this information for my mission.
buy viagra tablet online in india
where can you buy viagra in australia
viagra pills uk
Hurrah! After all I got a webpage from where I know how to truly take valuable data regarding my study and knowledge.
buy tadalafil canada
Great weblog here! Additionally your site loads up very fast! What host are you the use of? Can I get your affiliate hyperlink in your host? I desire my site loaded up as fast as yours lol|
I’m now not positive the place you are getting your info, but good topic. I must spend some time learning much more or figuring out more. Thanks for excellent info I used to be searching for this information for my mission.|
You really make it seem so easy with your presentation but I find this topic to be really something that I think
I would never understand. It seems too complex and extremely
broad for me. I am looking forward for your next post, I will try to get
the hang of it!
can you buy tadalafil over the counter
medication lisinopril 20 mg
tetracycline 25g
I love your blog.. very nice colors & theme. Did you
create this website yourself or did you hire someone to do it for you?
Plz respond as I’m looking to construct my own blog and would like to know where u got this
from. many thanks
can you buy diflucan in mexico
bookmarked!!, I like your site!
buy ventolin pills online
prazosin 2mg capsules
I really like your blog.. very nice colors & theme.
Did you make this website yourself or did you
hire someone to do it for you? Plz respond as I’m looking to construct
my own blog and would like to know where u got this from.
cheers
cost of levitra in canada
Wow, amazing blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your web site is excellent, let alone the content!
where can i buy viagra online without a prescription
tadalafil generic 10mg
generic viagra fast shipping
cialis generic canada
Please let me know if you’re looking for a article author for your blog. You have some really good articles and I think I would be a good asset. If you ever want to take some of the load off, I’d absolutely love to write some content for your blog in exchange for a link back to mine. Please send me an email if interested. Thanks!|
men viagra
Attractive section of content. I just stumbled upon your website and in accession capital to assert that I acquire actually enjoyed account your blog posts. Any way I’ll be subscribing to your augment and even I achievement you access consistently rapidly.|
Nice post. I was checking constantly this blog and I am impressed! Extremely useful info specially the last part 🙂 I care for such info a lot. I was looking for this particular information for a long time. Thank you and best of luck.|
I like the helpful info you supply in your articles. I’ll bookmark your weblog and test once more right here regularly. I am rather sure I’ll learn a lot of new stuff proper right here! Good luck for the next!|
Hi there to all, how is the whole thing, I think
every one is getting more from this website, and your views are nice in favor of
new people.
I love it whenever people get together and share views. Great website, continue the good work!|
Hey There. I discovered your weblog the use of msn. That is an extremely smartly written article. I’ll be sure to bookmark it and come back to read more of your useful information. Thank you for the post. I will definitely comeback.|
After looking at a few of the blog posts on your web site, I truly like your way of writing a blog. I saved it to my bookmark site list and will be checking back soon. Please visit my web site as well and let me know what you think.|
magnificent publish, very informative. I’m wondering why the other specialists of this sector don’t notice this. You must continue your writing. I’m confident, you have a great readers’ base already!
Thanks for any other informative blog. The place else may just I am getting that type of information written in such a perfect approach? I’ve a undertaking that I’m just now running on, and I have been at the glance out for such information.|
I am genuinely thankful to the owner of this web page who has shared this fantastic piece of writing at at this place.|
Please let me know if you’re looking for a article writer for your site. You have some really good articles and I feel I would be a good asset. If you ever want to take some of the load off, I’d love to write some articles for your blog in exchange for a link back to mine. Please blast me an e-mail if interested. Thanks!|
}
I know this if off topic but I’m looking into starting my own blog and was wondering what all is required to get setup? I’m assuming having a blog like yours would cost a pretty penny? I’m not very web savvy so I’m not 100 positive. Any recommendations or advice would be greatly appreciated. Kudos|
After I initially commented I seem to have clicked the -Notify me when new comments are added- checkbox and from now on whenever a comment is added I recieve 4 emails with the same comment. There has to be a way you are able to remove me from that service? Thanks!|
Spot on with this write-up, I actually believe that this web site needs a great deal more attention. I’ll probably be returning to read more, thanks for the advice!|
Hi, Neat post. There is a problem along with your website in web explorer, might test this?
IE still is the market leader and a large component to other folks will leave out your excellent writing because of this
problem.
Hello friends, how is the whole thing, and what you wish for to say about this piece of writing, in my view its really amazing in favor of me.|
Howdy would you mind letting me know which hosting company you’re working with? I’ve loaded your blog in 3 different web browsers and I must say this blog loads a lot faster then most. Can you suggest a good hosting provider at a honest price? Cheers, I appreciate it!|
Unquestionably imagine that which you stated. Your favourite justification seemed to be at the web the simplest factor to take into accout of. I say to you, I certainly get annoyed whilst other folks consider worries that they just do not know about. You controlled to hit the nail upon the highest and outlined out the entire thing without having side effect , people could take a signal. Will likely be again to get more. Thank you|
Hey there, You’ve done an incredible job. I will definitely digg it and personally recommend to my friends. I am sure they’ll be benefited from this website.|
Simply desire to say your article is as amazing. The clearness in your post is just excellent and i can assume you’re an expert on this subject. Fine with your permission let me to grab your feed to keep updated with forthcoming post. Thanks a million and please continue the rewarding work.|
I used to be suggested this web site by my cousin. I’m now not sure whether or not this publish is written by him as no one else understand such distinct approximately my difficulty. You’re amazing! Thank you!|
I have read so many articles or reviews concerning the blogger
lovers except this post is in fact a good paragraph, keep it up.
Pretty! This was an incredibly wonderful post. Thank you for providing this information.|
Just wish to say your article is as astonishing. The clearness for your put up is just cool and that i could think you’re a professional on this subject. Well together with your permission let me to grasp your RSS feed to keep updated with impending post. Thank you 1,000,000 and please carry on the gratifying work.|
What’s up it’s me, I am also visiting this web site on a regular basis, this web site is really fastidious and the viewers are really sharing pleasant thoughts.|
https://dribbble.com/account/profile
https://mix.com/lovelyjunaid8115
https://knowyourmeme.com/users/ahsan-ahmad
medicine for ed
magnificent put up, very informative. I’m wondering why the opposite specialists of this sector don’t notice this. You should proceed your writing. I am sure, you have a great readers’ base already!
Hello there! I could have sworn I’ve been to this site before but after checking through some of the post I realized it’s new to me. Anyways, I’m definitely happy I found it and I’ll be bookmarking and checking back frequently!|
Best view i have ever seen !
walgreens cialis prices cialis usa purchase cialis in canada
cialis and high blood pressure cialis usa online how to take cialis
buying generic cialis cialis pills buy generic cialis atralia
ivermectin side effects humans stromectol for pinworms ivermectin dogs
drugs for ed buy prescription drugs from canada ed clinics
cause of ed pump for ed ed pharmacy
buy prednisone online without a prescription generic prednisone prednisone 20mg price in india
Everything is very open with a really clear clarification of the issues.
It was truly informative. Your website is extremely helpful.
Many thanks for sharing!
buy prescription drugs from canada legal to buy prescription drugs from canada canadian drugstore online
Hi, I do believe this is an excellent blog. I stumbledupon it 😉 I’m going to
come back once again since I saved as a favorite it.
Money and freedom is the best way to change, may you be rich and continue to help other people.
dosage of ivermectin for dogs ivermectin 0.5 ivermectin paste 1.87 for horses
canadian pharmacy online prescription drugs amoxicillin without a doctor’s prescription
canadian medications meds online without doctor prescription canada ed drugs
https://hpp-a.pl
cure ed over the counter erectile dysfunction pills over the counter erectile dysfunction pills
ivermectin cvs is ivermectin safe for pregnant mares ivermectin 90 mg
generic propecia canada propecia cost propecia 5mg for sale
canadian pharmacies not requiring prescription buying from canadian online pharmacies reputable canadian mail order pharmacies
My spouse and I stumbled over here from a different web page
and thought I should check things out. I like what I see so now i am following you.
Look forward to exploring your web page again.
canadian pharmacy certified canada pharmacy online trusted online canadian pharmacy reviews buying from canadian online pharmacies
clomid tablets buy clomid 50mg online clomid
Hmm it looks like your site ate my first comment
(it was super long) so I guess I’ll just sum it up what I submitted and say, I’m
thoroughly enjoying your blog. I too am an aspiring blog blogger but I’m still new
to everything. Do you have any helpful hints for
beginner blog writers? I’d genuinely appreciate it.
Here is my web-site – Web Site
tadalafil best price 20 mg tadalafil tablets 20 mg india cialis 20mg
buy tadalafil online best price for daily cialis buy tadalafil online
generic tadalafil 20mg india tadalafil cialis 20 mg price
best place to buy generic viagra online viagra tablets for men generic viagra walmart
buy viagra online usa sildenafil 100 mg viagra without a doctor prescription usa
paypal cialis no prescription cialis pills receive cialis overnight
professional viagra cialis buy tadalafil cialis generic canada pharmacy
cialis 80 mg dosage best price for daily cialis cheapest generic cialis
cialis without prescriptions buy tadalafil cialis coupon
For occasion, complete life insurance may or will not be the right
type of life insurance for you.
generic cialis 20mg tablets generic version of cialis cialisgeneric
how to avoid cialis side effects\ generic tadalafil 20mg india black cialis canadian
Start your quote right now and give your self peace of thoughts while
on the clock.
cheapest xenical uk
lexapro canadian pharmacy
metformin hcl
inderal 40 mg medicine
ordering furosemide
sildenafil gel india
amoxicillin pills over the counter
purchase valicyclovir online
stromectol online pharmacy
stromectol 3 mg dosage
ivermectin uk
cialis from safeway cialis pills
baclofen 5 mg
valtrex mexico
ivermectin 250ml
q638l
wrula
zhbr
generic cialis 2018 usa
acyclovir price in india
clonidine 2.0
cialis free shipping
buy propranolol tablets
sildalis
trazodone 150 mg price
where to buy accutane online
Helpful information. Lucky me I found your site by chance, and
I’m surprised why this coincidence did not came about in advance!
I bookmarked it.
medicine cialis tablets
buy generic cymbalta 60 mg
stromectol order online stromectol 3 mg tablets price
However, they must have sufficient to cowl a complete and full lack of employment and of
their possessions.
cialis for daily use
cialis 5mg nz
where can i buy stromectol
Insurance is a financial device which helps in making certain financial protection of yourself and your beloved
ones.
albendazole tablets 400 mg
erectafil 40
synthroid 75 mg
6alxb
gfe2i
y6g1
metformin hydrochloride 500 mg
augmentin for sale canada
augmentin 500 price
Hurrah, that’s what I was looking for, what a stuff!
existing here at this blog, thanks admin of this web page.
propranolol gel
how much is 20 mg cialis
prozac price in india
generic ivermectin ivermectin lice oral
suhagra 50 mg online
albendazole otc
strattera buy online no prescription
tizanidine 2mg medication
cymbalta online pharmacy price
toradol tablets price
ciprofloxacin usa
buy anafranil
150 mg sildenafil
canadien pharmacies
budesonide 6 mg
albendazole in usa
buy propecia 1mg online uk
cephalexin 250 mg price
buy seroquel online india
indocin generic
I do agree with all the concepts you have presented to
your post. They’re really convincing and can certainly work.
Nonetheless, the posts are very quick for newbies. May you please prolong
them a bit from subsequent time? Thanks for the post.
generic tadalafil cheap
zofran 8mg tablets
buy antabuse online no prescription
inderal la 80 mg
toradol tablets
fluoxetine 20mg
how much is cymbalta 60 mg
100 amoxicillin 500 mg
It’s the best time to make some plans for the future and it’s time to be
happy. I’ve read this post and if I could
I desire to suggest you some interesting things or advice.
Perhaps you can write next articles referring to this article.
I desire to read more things about it!
fildena
Thank you, I’ve just been looking for information about this subject
for a while and yours is the best I’ve found out so far.
However, what about the conclusion? Are you certain concerning the
source?
albenza tab 200mg
lioresal 10
generic antabuse
kxhxw
1ife9
nmvr
Hi my friend! I wish to say that this article is amazing, nice written and come with almost all vital infos.
I would like to peer extra posts like this .
It’s remarkable in support of me to have a web site, which is good designed for my
knowledge. thanks admin
san antonio cialis doctor buy cialis from cananda
canadian drug how to get prescription drugs without doctor
non prescription erection pills pain meds without written prescription
Insurance premiums from many insureds are used to fund accounts
reserved for later cost of claims – in concept for a comparatively few claimants – and for overhead prices.
cialish cialis pills
cvs prescription prices without insurance canadian drugs
ed meds online without doctor prescription best non prescription ed pills
Hey I know this is off topic but I was wondering if you knew of
any widgets I could add to my blog that automatically tweet my newest twitter
updates. I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience
with something like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new updates.
Ease in plan comparisonIt is simple to match plans on the InsuranceDekho website.
levitra vs viagra herb viagra for sale how quickly does viagra work what is the effect of viagra
diltiazem 30 brand diltiazem diltiazem 240 mg para que sirve how to use diltiazem 2 ointment
Wonderful post! We will be linking to this particularly great post
on our website. Keep up the good writing.
purchase genuine viagra online
albenza cost
cheap ampicillin
diclofenac otc canada
cost toradol
Many institutional insurance purchasers buy insurance via an insurance dealer.
how to order amoxicillin online
where to buy modafinil uk
buy biaxin 500 mg
buy retin a 0.5 cream uk
sildalis 120 mg order canadian pharmacy
fluoxetine generic
best online pharmacy reddit
buying antabuse online
modafinil 100
modafinil mexico online
lisinopril 5mg pill
buy generic levitra online canada
sildenafil online prices
where to get provigil
over the counter viagra online
generic cialis us
diltiazem on line buy diltiazem pills oral diltiazem for a-fib what is a corticosteroid cream diltiazem
buying viagra
isotretinoin accutane
silagra canada
zanaflex comparable to zanaflex 4 mg tablet zanaflex 2mg and xanaex deadly what happens if you take too much zanaflex and ambien
https://sildenafilmg.shop/# buying viagra online
buy brand viagra online australia
otc cialis 2017
viagra soft gel capsules
retin a prescription cost
online doctor prescription for viagra buy real viagra online
buy gabapentin 800 mg online
cialis 10 price
cialis usa pharmacy
biaxin medication
buy septra antibiotic
finasteride 1mg over the counter
https://sildenafilmg.online/# best over the counter viagra
atarax 10mg uk
buy viagra online canada viagra
generic valtrex online
buy brand name viagra
citalopram uk
https://sildenafilmg.online/# 100mg viagra
generic viagra lowest prices
viagra discount online
real viagra online canada
lisinopril 2.5 mg price
dapoxetine 2018
nolvadex 10mg tablets price
provigil buy online india
drugstore viagra
female viagra tablets price
average price of cialis
soft tab cialis
where to buy viagra viagra
provigil 100
stopping diltiazem buy diltiazem 180mg generic diltiazem/tetracaine activemax cream ic diltiazem 24hr er how effective is it for blood pressure
citalopram 10 mg price
zithromax and breastfeeding azithromycin 250mg tablets what dose of azithromycin clears chlamydia what can azithromycin treat
good value pharmacy
valtrex online australia
purchase propecia
metformin 178
phenergan 25 mg otc
where can you buy toradol
buying zovirax in canada
viagra online usa cheap viagra online
propranolol cost australia
can i buy zithromax over the counter in canada can i buy zithromax online
amoxicillin generic amoxicillin 500 mg online
diltiazem dose afib order diltiazem 180mg without prescription diltiazem drip to oral conversion what does diltiazem hcl er mean
https://doxycyclineforsale.life/# doxycycline 100mg cap
can you buy clomid over the counter in usa clomid pills
cialis premature ejaculation viagra spider get a viagra prescription online viagra when to take it for the best results
prednisone 80 mg daily prednisone buy without prescription
metformin 1 00 mg metformin where to get
furosemide classification furosemide 20 mg for sale can furosemide damage the kidneys where to buy lasix water pill
cenforce 100 generic viagra get best offers coupons safehealths buy cenforce dose of cenforce cenforce 50mg without prescription
https://buynolvadex.store/# nolvadex price
lasix for sale furosemide 40 mg
metformin without rx buy metformin 1000 mg online
buy keflex
zoloft 50mg cost
how to get albuterol
can you buy amoxicillin over the counter uk
generic bactrim for sale
amoxicillin tablets where to buy
bactrim ds tablets online
strattera 100 mg
trazodone hydrochloride 100mg
buy generic zoloft online
gabapentin 500
piroxicam tablet
https://buymetformin.best/# where to buy metformin 500 mg without a prescription
order tadacip 20 mg
propecia 5 mg buy propecia finasteride propecia brand name cost walgreens how many months propecia
disulfiram price south africa
lipitor 40 mg tablet price lipitor tablets
buy cenforce 50mg cenforce pharamcy buy cenforce 100mg online cheap cenforce side effects
clonidine 0.05 mg
lopressor 20 mg
where to buy metformin 850 mg
buy synthroid online usa
https://cipro.best/# buy ciprofloxacin
metformin canadian pharmacy
best diflucan price diflucan 150 capsule
finpecia
retino 0.25 cream price
https://diflucan.icu/# diflucan 200 mg daily
diflucan tablets online
online purchase of tetracycline
buy suhagra online india
viagra brand generic
Hello, I wish for to subscribe for this weblog to get latest updates, therefore where can i do it please help out.
aid ukraine
zovirax cream india
generic bactrim ds
retino 05 cream
augmentin 875 mg buy
prednisolone cost australia
mebendazole price
clomid tablets in india
tadacip 20 mg canada
Hello to every one, the contents existing at this website are in fact amazing for people knowledge, well, keep up the nice work fellows.
where to get diflucan without a prescription buy diflucan online uk
generic for avodart
buy erectafil 20
stromectol medication
https://diflucan.icu/# diflucan 200 mg price south africa
buying viagra in mexico
avodart generic online
clonidine beta blocker
avodart price uk
strattera buy online no prescription
can you buy zoloft over the counter
viagra for men
uk propecia online generic propecia from india can you take propecia before hairloss where can i buy cheap propecia
over the counter augmentin
metformin glucophage
ivermectin for covid
neurontin generic south africa neurontin 1800 mg
generic for avodart medication
how to buy bactrim online
Claims could also be filed by insureds immediately with the insurer or
through brokers or brokers.
albuterol cost canada
albendazole 2g
generic ed pills pills for erection
med price levitra
atenolol
https://cipro.best/# ciprofloxacin 500 mg tablet price
erectafil 5 mg
tadacip 20 mg price in india
cost of diflucan
can you purchase propecia
https://withoutprescription.store/# carprofen without vet prescription
albuterol sulfate
buy bactrim on line without a prescription
retino gel
cipro buy online
retino 05
erectafil from india
yasmin acne
buy cheap diflucan online diflucan buy without prescription
where to buy orlistat in australia
inderal 40 mg cost
buy canadian drugs online prescription for ed meds
indian viagra
https://cipro.best/# ciprofloxacin 500mg buy online
accutane nz cost
clonidine hcl 0.1mg tablets
https://cutt.ly/MTQl5PN
amoxicillin 500 mg tablet price
prescription drug diclofenac
generic seroquel xr
levaquin 750 mg
bactrim without a prescription
clomid 50mg capsules
clomid 150mg success buy clomid canada pharmacy how does clomid make you feel when do i take clomid
kamagra europe generique kamagra en pharmacie comment utiliser le gombo comme kamagra comment prescrire kamagra
modafinil india cost
MyNAIC Access expertise tools and sources for U.S.
insurance regulators.
propecia hair growth
excellent post, very informative. I ponder why the other experts of this sector don’t understand this. You must proceed your writing. I am confident, you’ve a great readers’ base already!
proscar medication
orlistat 60 mg generic
can you buy plaquenil over the counter
quineprox 800 mg
vardenafil 60mg
levaquin 500mg
buy diflucan without script diflucan gel
propranolol online pharmacy
where can you buy diflucan over the counter diflucan medication
canadian pharmacy propecia
vermox india
viagra online pharmacy usa
https://erectionpills.best/# best treatment for ed
buy allopurinol 100mg uk
accutane online for sale
where can you get modafinil
metformin kidney pain metformin for sale what side effects does metformin have how does metformin help with weight loss
quetiapine interactions seroquel xr cost seroquel is it a narcotic how long does it take for seroquel to wear off
generic cialis for sale online
triamterene-hctz 37.5-25 mg capsules
flagyl pills
usa tadalafil
tamoxifen 20mg price in india
can i buy viagra online in india
bactrim brand name
The reinsurance market is dominated by a few very massive companies, with big reserves.
Just want to say your article is as astounding.
The clarity on your submit is simply nice and i can assume you’re knowledgeable on this subject.
Fine with your permission allow me to grasp
your feed to stay updated with forthcoming post.
Thank you one million and please continue the rewarding work.
where can i buy cipro online п»їcipro generic
neurontin 100mg price where to buy neurontin
https://withoutprescription.store/# best non prescription ed pills
https://erectionpills.best/# best ed pill
doxycycline 100mg over the counter
best zoloft generic
tretinoin 0.1 discount
order generic propecia
cialis 40mg generic
bactrim brand name
15 mg celexa
buy hydrochlorothiazide
buy vardenafil from india
tizanidine without prescription
clonidine 0.1 mg cost
finasteride without prescription
tadalafil 100
viagra discount online
hydrochlorothiazide 25 mg price
strattera 40mg capsules
albendazole 200 mg tablet price
cipro medication
where to buy robaxin in us
suhagra 50 tablet price
erectile dysfunction medications ed remedies
https://erectionpills.best/# cheap erectile dysfunction pill
buy ciprofloxacin over the counter п»їcipro generic
You really make it appear really easy together with
your presentation but I to find this topic to be actually
one thing that I believe I would never understand. It sort of feels too complicated and very vast for
me. I am taking a look forward in your next submit, I will try to get
the hang of it!
https://clomidonline.icu/# generic clomid for sale
п»їerectile dysfunction medication ed dysfunction treatment
generic clomid for sale clomid for sale
https://drugsonline.store/# ed meds online
xenical roche rezeptfrei prescription orlistat precio de xenical en peru how much weight can i lose with orlistat baikal-pharmacy.com
aralen cost aralen order online can you take aralen and xanax together how is aralen metabolized
https://stromectol.life/# stromectol
generic clomid for sale buy clomid
stromectol 12 mg tablets ivermectin cream cost
purchase doxycycline doxycycline
https://clomidonline.icu/# cheap clomid
stromectol 12 mg tablets stromectol
diflucan dark urine diflucan 500 mg diflucan 1 dose yeast infection how ofyen can you take diflucan
viagra without doctor prescription best drugs for ed
https://edpills.best/# pills for ed
ed treatment pills what are ed drugs
buy clomid clomid fertility drug
Good respond in return of this query with genuine arguments and telling
all regarding that.
https://drugsonline.store/# dysfunction erectile
Deductibles can apply per-policy or per-claim relying on the insurer and the kind of coverage.
male ed drugs best male ed pills
baricitinib powder price olumiant covid baricitinib alternative what is olumiant
https://edpills.best/# treatment for ed
ed pills that work ed treatment options
Independent inventors account for 70% of the brand new U.S.
patent functions on this area.
stromectol 3mg tablets stromectol
https://stromectoltrust.com/# stromectol 3mg tablets
mectizan stromectol stromectol for humans for sale
order stromectol over the counter stromectol 3mg tablets
aralen lyme aralen chloroquine take vitamin d with aralen how does aralen work
stromectol for humans for sale order stromectol over the counter
stromectol for scabies stromectol from costco
xenical obat pelangsing orlistat no prescription needed orlistat 120 como se toma what happens when you stop taking orlistat
order stromectol over the counter stromectol 3 mg tablets price
sildenafil 20 mg online no prescription
augmentin 1000mg tablets
https://stromectoltrust.com/# ivermectin dispersible tablets
levitra 100mg price
buy zithromax online
buy neurontin online uk
sildalis 120 mg
buy chloroquine phosphate online
albuterol cost in uk
https://pharmacyizi.com/# treatment of ed
bactrim ds 800 160
male dysfunction pills best ed medication
canadadrugpharmacy
https://pharmacyizi.com/# natural remedies for ed
retin a in mexico
trazodone brand name in usa
bactrim ordering
xenical optical glasses xenical buy online nz side effects of orlistat include what happens when you stop taking orlistat
chloroquine
https://pharmacyizi.com/# best ed pill
generic vpxl
viagra best price
aurogra 100 uk
snorting seroquel seroquel 300mg tabs can you overdose on seroquel and die how long does seroquel take to kick in
robaxin over the counter south africa
discount cialis no prescription
order generic viagra online canada
buy trazodone online
https://pharmacyizi.com/# natural remedies for ed
order ventolin online no prescription
wellbutrin online
cheap generic viagra 100mg canada
inderal discount
chloroquine phosphate 500 mg
lexapro capsule
cheapest zoloft online
clindamycin 600
robaxin pill
https://pharmacyizi.com/# non prescription ed pills
inderal medicine
https://pharmacyizi.com/# sildenafil without a doctor’s prescription
how much is tadalafil
toradol headache
periactin 4 mg
diflucan 200 mg price
toradol online pharmacy
cipro antibiotic where to buy
https://pharmacyizi.com/# erectyle dysfunction
buspar tabs
colchicine acute gout
chloroquine phosphate buy online
dosing for diflucan where can i buy diflucan online does diflucan make you sleepy how long after taking diflucan do you see results
zovirax generic price
gabapentin 300 mg price in india
levitra india online
propranolol 10 mg price
azithromycin usa
valtrex generic price canada
ciprofloxacin prescription
The plan additionally presents a survival benefit
to the assured if he/she survives the coverage term.
acyclovir usa price
cheap cialis pills
cipro iv
medicine gabapentin 300
i want to buy viagra
viagra pills price in usa
antabus
where can i buy real viagra online
cheap bactrim online
cost of cialis
lexapro 2019
https://pharmacyizi.com/# prescription drugs online without
how to get cialis in canada
https://pharmacyizi.com/# best drug for ed
generic synthroid without prescription
citalopram 400 mg
https://pharmacyizi.com/# canadian drugstore online
buy bactrim online without prescription
cialis pills for sale in canada
The first international insurance rule was the York Antwerp Rules for the distribution of costs between ship and cargo in the occasion of basic common.
endep
https://pharmacyizi.com/# generic viagra without a doctor prescription
where to buy viagra over the counter in usa
chloroquine price in india
diarrhea metformin metformin buy online usa metformin hcl 500 mg weight loss what is metformin er used for
ed dysfunction treatment buy prescription drugs
https://pharmacyizi.com/# natural herbs for ed
medrol 8mg price
viagra sildenafil 100mg
cost of lasix 20 mg
https://pharmacyizi.com/# pet meds without vet prescription
ciprofloxacin cheap
digoxin uk
tenormin 100 mg
viagra 200mg price in india
atenolol 50
disulfiram in india
aurogra
tizanidine medicine
3000mg valtrex
can you buy colchicine without a prescription
amitriptyline over the counter usa
amitriptyline pharmacy
https://pharmacyizi.com/# ed prescription drugs
sildenafil 10 mg
bactrim 1600
cialis price uk
buy vpxl
https://pharmacyizi.com/# aspirin and ed
cialis brand price
wellbutrin 100 mg tablet
zovirax 400 price
allopurinol 400 mg tablets
side effects baclofen baclofen 10 mg price in india difference between baclofen and flexeril when baclofen pump doesn’t work
vpxl
price of zoloft without insurance
https://canadiandrugs.best/# prescription drugs online without doctor
diflucan not work buy diflucan online australia recurrent yeast infection after diflucan allergic to diflucan what else can i take
medicine online shopping Cytoxan
https://canadiandrugs.best/# canadian medications
can you buy bactrim over the counter
seroquel xr bipolar
buying viagra in canada
propecia without prescription
tadalafil cost in canada
generic propecia finasteride
https://canadiandrugs.best/# pain meds without written prescription
strattera australia
retin a 01
advair 500 50 mcg
medicine cialis tablets
cialis 20 mg discount
abilify 5mg tablet cost
elavil coupon
triamterene-hctz 75-50mg tab
ed prescription drugs buy prescription drugs without doctor
medical pharmacy west legitimate mexican pharmacy online
cheap sildenafil tablets 100mg
celexa best price
dapoxetine pills for sale
elavil 50 mg tablet
viagra pills online australia
buy generic cialis
cialis brand 10mg
furosemide 20 mg tab
suhagra 50 mg price
Hello would you mind letting me know which web host you’re
utilizing? I’ve loaded your blog in 3 completely different browsers and
I must say this blog loads a lot quicker then most. Can you suggest a
good internet hosting provider at a reasonable price?
Thank you, I appreciate it!
metformin online
buy made in usa cialis online
digoxin oral
quetiapine prescription quetiapine uk pharmacy quetiapine fumarate tablet 25 mg what are the long term side effects of quetiapine?
prescription pricing gastro health
atenolol 75 mg
vermox tablet
vermox canada otc
new ed drugs ed medications
benicar 40 mg tablet price
cheap prednisolne
drug robaxin
atenolol 25 mg tablets
https://erectionpills.shop/# best over the counter ed pills
cost generic cialis
cialis daily in india
suhagra for sale
albuterol nz
sildenafil 100mg online india
furosemide 160 mg daily
where to buy chloroquine
buy chloroquine
where can i buy cialis online
abilify 15
accutane pills buy online
how to get diflucan
canadian online drugstore legal to buy prescription drugs without prescription
cialis canada online pharmacy
how to purchase atenolol without prescription
purchase prednisolone 5mg tablets
best canadian pharmacy online ed meds online without prescription or membership
Malegra DXT plus Suhagra
female cialis australia
order generic cialis
buspar over the counter
colchicine prescription uk
sildenafil prices 20 mg
colchicine 0.6mg tablets
https://onlinepharmacy.men/# online pharmacy reviews
retino gel
https://canadiandrugs.best/# best online canadian pharmacy
zyban generic brand
elavil 150 mg
sildenafil 20 mg online
canadian world pharmacy online pharmacy europe
cafergot brand name
order viagra online paypal
It’s impressive that you are getting ideas from this paragraph as well as from our dialogue made at this place.
https://allpharm.store/# northwest pharmaceuticals canada
doxycycline hyclate treats doxycycline 200mg price does doxycycline have sulfa in it what is doxycycline hyclate for
where to buy acyclovir cream
suhagra 100mg online buy
40 mg cialis online
buy cheap cialis uk
cheap benicar
pain meds online without doctor prescription ed meds online without doctor prescription
sinfidel viagra generic for cialis effect of cialis on women what is levitra used for
where to buy dexamethasone
buy lasix online uk
cafergot tab 100 mg
vermox 100mg tablets
tadalafil 10mg generic
how to get over the counter viagra
medrol 16mg tab
However, since about 1996 insurers have begun to
take a more energetic function in loss mitigation, corresponding to through building
codes.
tenormin online
buy cheap sildalis
https://canadiandrugs.best/# ed meds online without doctor prescription
price of acyclovir cream
medrol tablet price
canadian pharmacy cialis 20mg
male ed pills ed medications list
lasix tablet online
cost of allopurinol tablets
buy citalopram 20mg
tetracycline 250 mg cap
1500 mg gabapentin
paxil cost australia
cheap viagra australia fast delivery
digoxin 250 mcg price
albuterol 90
Tinidazole Starlix
My family all the time say that I am wasting my time here at web, however I know I am getting experience all
the time by reading thes good articles.
generic yasmin birth control
generic viagra 100
buy arimidex usa
prednisone 20 mg tablet
buy silagra online uk
buy neurontin
I just could not go away your website before suggesting that I extremely loved the standard information an individual supply
on your guests? Is going to be again regularly to inspect new posts
vermox pharmacy uk
silagra 50 mg price
how to get propecia nz
buy generic cialis online from india
paxil cost australia
https://onlinepharmacy.men/# pharmacy prices
how can i order prescription drugs without a doctor non prescription ed drugs
plaquenil and itching plaquenil osteoarthritis what pain medicine with plaquenil who can do plaquenil eye screen
digoxin 125 mcg tablet
buy generic tetracycline online
tetracycline 500mg tablet price
can i buy albendazole over the counter
arimidex cost usa
250 mg metformin
citalopram 20 mg tablet cost
sumycin price
chris martenson ivermectin stromectol where to buy
ivermectin 1% cream ivermectin 50ml
compare propecia prices
tamoxifen citrate
clomid prescription price
order lexapro online no prescription
buy buspar online
diflucan 150 mg tabs
endep 50mg
buy misoprostol online without prescription
naltrexone used for revia delivery naltrexone false positive for opiates where to buy low dose naltrexone online
stromectol pill for humans stromectol buy online
https://stromectolbestprice.com/# how much ivermectin for chickens
benicar 437
elavil for fibromyalgia
buy celexa cheap
digoxin 80162
real generic viagra
20mg benicar
tadacip 20 price in india
buy viagra online price
aralen chloroquine phosphate
arimidex for sale
buy female viagra uk
cialis online visa
stromectol price uk ivermectin for guinea pig
cialis 5mg nz
can you buy viagra over the counter in south africa
cheap zithromax online
stromectol price where to buy stromectol
buy vermox online nz
https://stromectolbestprice.com/# ivermectin tablets dosage
propecia tablets online india
phenergan gel cost
can i buy voltaren over the counter
propecia in india
furosemide 20mg tablet cost
tretinoin over the counter
Every InsureMyTrip customer is invited to evaluation their buying experience by way of
third-party review website ResellerRatings.com.
zithromax capsules 250 mg
I was suggested this web site through my cousin. I am no longer positive whether
this put up is written by way of him as no one else
recognise such particular approximately my problem. You’re incredible!
Thanks!
suhagra 100 online in india
misoprostol pills over the counter
suhagra tablet online
canada pharmacy deltasone
buy viagra discount
advair price in canada
suhagra 100mg buy online
paxil 30mg
viagra online without prescription usa
https://drugsbestprice.com/# top rated ed pills
buy canadian drugs ed dysfunction
ways to treat erectile dysfunction otc ed drugs
allopurinol 500 mg tablet
prednisolone online uk
prevacid 30
robaxin v
synthroid class synthroid 150 mcg tablet alpha lipoic acid and synthroid what can i take for heartburn while on levothyroxine
ciprofloxacin 500mg generic
amoxil antibiotic
zofran uk
can you buy amoxicillin online
the canadian drugstore buy drug online
We’re a group of volunteers and starting a
new scheme in our community. Your site provided us with valuable info to
work on. You’ve done an impressive job and our entire community will be grateful to you.
medication ciprofloxacin 500mg
soma therapy ed canadian online drugs
average cost of prozac
I always spent my half an hour to read this web site’s
posts everyday along with a cup of coffee.
abilify 30 mg tablet
valtrex instructions valtrex cream coupon acyclovir vs valacyclovir for shingles how long does valtrex last
viagra 500mg
buy prescription drugs online ed meds online without doctor prescription
online prescription for ed meds canadian drugstore online
rx pharmacy online tadalafil
viagra cost in canada
zoloft online without prescription
zoloft without script
vermox us
cheap vardenafil 20mg
zoloft price canada
buy augmentin uk
zestoretic cost
non prescription ed drugs best non prescription ed pills
tadalafil rx
https://medrxfast.com/# mexican pharmacy without prescription
clonidine online
how to get misoprostol prescription
voltaren cream
allopurinol 600 mg price
lipitor pill
amoxicillin effects amoxicillin 500mg dosis amoxil niГ±os 6 aГ±os can i buy amoxil over the counter
albendazole 200 mg tablet price
pain meds without written prescription buy prescription drugs from canada
amoxicillin australia
generic brand viagra
augmentin 1g price in india
fluoxetine capsules brand name
legal to buy prescription drugs without prescription online canadian drugstore
antabuse australia prescription
cheap tetracycline
phenergan tablets 25mg uk
cialis uk
https://medrxfast.com/# buy prescription drugs from india
molnupiravir capsule molnupiravir covid treatment is molnupiravir a monoclonal antibody molnupiravir authorization
brand levitra for sale
online tadalafil us
diclofenac brand name drug
buy kamagra uk paypal
fluoxetine brand name
zoloft 2019
avodart pharmacy
fluoxetine uk prescription
cost of tadalafil
sildenafil medication
suhagra 25 mg buy online india
canadian online drugs cat antibiotics without pet prescription
best non prescription ed pills ed meds online canada
cytotec purchase
cytotec medicine price
discount zanaflex
flomax for prostatitis
diclofenac tablets
amoxicillin 500 mg capsules
Generally, the contract between insured and insurer is of a
yr which should be renewed every year.
where to buy sildalis
plaquenil) cost of plaquenil can plaquenil cause bad teeth how are levels of plaquenil checked in the body
Appreciating the time and effort you put into your site and in depth information you offer.
It’s awesome to come across a blog every once in a while that isn’t the same
unwanted rehashed material. Fantastic read!
I’ve saved your site and I’m including your RSS feeds to my Google
account.
how to get zoloft without prescription
zanaflex generic 2mg
buy zofran canada
legal to buy prescription drugs from canada prescription drugs without doctor approval
lipitor 5mg price
I could not refrain from commenting. Well written!
https://medrxfast.com/# canadian drugs
nolvadex d price nolvadex ca nolvadex has cleared my gyno test deca dbol cycle when to start pct nolvadex
canada ed drugs non prescription erection pills
how much is sildenafil in canada
gabapentin in india
prednisolone 10 mg daily
non prescription ed pills tadalafil without a doctor’s prescription
lisinopril no prescription
https://medrxfast.com/# buy cheap prescription drugs online
cialis 1800 mg
tadalafil 47
mexico pharmacy albuterol
We’re a group of volunteers and opening a new
scheme in our community. Your website offered us
with valuable info to work on. You have done a formidable job and our whole community will be grateful to you.
viagra prescription coupon
how to get prescription drugs without doctor comfortis for dogs without vet prescription
buy albendazole online uk
lioresal tablet
cialis online us
lexapro coupon
legal to buy prescription drugs without prescription canada ed drugs
cialis for daily use canadian pharmacy
It’s a pity you don’t have a donate button! I’d without a doubt donate to this excellent blog!
I suppose for now i’ll settle for bookmarking and adding your
RSS feed to my Google account. I look forward to fresh
updates and will share this blog with my Facebook group.
Talk soon!
https://medrxfast.com/# online prescription for ed meds
Hey there! This post could not be written any better! Reading through this post reminds me of my
previous room mate! He always kept chatting about this.
I will forward this article to him. Fairly
certain he will have a good read. Thank you for sharing!
Hurrah, that’s what I was seeking for, what a material!
present here at this webpage, thanks admin of this web site.
I all the time emailed this blog post page to all my friends,
since if like to read it then my friends will too.
Feel free to surf to my web blog; 2022
Heya exceptional website! Does running a blog similar to this
take a great deal of work? I have very little knowledge of computer programming but I was hoping to start my own blog in the near future.
Anyhow, if you have any suggestions or tips for new blog owners please share.
I understand this is off topic however I simply needed to ask.
Kudos!
ed meds online canada buy prescription drugs without doctor
canadian drugs online canadian drugs online
https://medrxfast.com/# canadian pharmacy
Hello! Someone in my Myspace group shared this website with us so I came to
check it out. I’m definitely enjoying the information. I’m
bookmarking and will be tweeting this to
my followers! Exceptional blog and great design and style.
Hey terrific website! Does running a blog like
this take a great deal of work? I have absolutely no expertise in computer programming but I was hoping to start my own blog in the near future.
Anyhow, if you have any ideas or techniques for new blog owners please
share. I know this is off topic but I simply had to ask.
Thanks!
Thanks for one’s marvelous posting! I truly enjoyed reading it, you may be a great
author. I will always bookmark your blog and will often come back from now on.
I want to encourage that you continue your great writing,
have a nice morning!
Hi! This is kind of off topic but I need some advice
from an established blog. Is it very hard to set up your own blog?
I’m not very techincal but I can figure things out pretty quick.
I’m thinking about creating my own but I’m not sure where to start.
Do you have any ideas or suggestions? Appreciate it
best online canadian pharmacy prescription drugs canada buy online
https://medrxfast.com/# prescription without a doctor’s prescription
Awesome article.
ed prescription drugs best non prescription ed pills
Hello There. I found your blog using msn.
This is an extremely well written article.
I will be sure to bookmark it and come back to read more of your useful information.
Thanks for the post. I will certainly comeback.
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you! By the way,
how could we communicate?
https://medrxfast.com/# ed meds online canada
canadian drugs canadian pharmacy
Ahaa, its pleasant conversation concerning this post at this place at this website,
I have read all that, so at this time me also commenting
at this place.
I got this web page from my friend who shared with me about this website and now this time I am visiting this web page and reading very informative articles or reviews at this place.
prescription drugs without doctor approval buy prescription drugs from canada cheap
https://medrxfast.com/# comfortis without vet prescription
Hello, after reading this awesome paragraph i am as well delighted to share my
experience here with friends.
sildenafil without a doctor’s prescription buy prescription drugs without doctor
Hey There. I found your blog using msn. This is a very well written article.
I will make sure to bookmark it and return to read more of your useful
information. Thanks for the post. I’ll certainly return.
viagra levitra
May I simply just say what a relief to uncover somebody that actually knows what they’re discussing online.
You certainly understand how to bring an issue to light and
make it important. A lot more people need to read this and understand this
side of the story. It’s surprising you’re not more popular given that you most certainly have the gift.
If you want to take much from this paragraph
then you have to apply such techniques to your won website.
online canadian drugstore https://medrxfast.com/# ed prescription drugs
Hmm it looks like your website ate my first comment (it
was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog.
I too am an aspiring blog writer but I’m still new to the whole thing.
Do you have any suggestions for first-time blog writers? I’d really appreciate it.
neurontin 200 mg neurontin 500 mg tablet
Thankfulness to my father who stated to me concerning this website, this web
site here is really amazing.
Thank you for every other wonderful article.
Where else may anybody get that kind of information in such a perfect way of writing?
I’ve a presentation subsequent week, and I’m at the search for such info.
Hmm it appears like your site ate my first comment (it was
super long) so I guess I’ll just sum it up what
I had written and say, I’m thoroughly enjoying your blog.
I too am an aspiring blog blogger but I’m still new to the whole thing.
Do you have any recommendations for novice blog writers?
I’d definitely appreciate it.
canada prescriptions online
https://gabapentin.top/# buying neurontin online
In fact no matter if someone doesn’t understand after that its up to other people that they will assist,
so here it occurs.
diflucan capsule 150mg buy diflucan canada
where to buy valtrex over the counter where can i buy valtrex online
https://wellbutrin.best/# buying wellbutrin online
https://wellbutrin.best/# cheap wellbutrin xl
Hello, I would like to subscribe for this website
to obtain latest updates, therefore where can i do it
please help.
I was curious if you ever considered changing the page layout of your site?
Its very well written; I love what youve got to say. But maybe you could a
little more in the way of content so people could connect with it better.
Youve got an awful lot of text for only having 1 or 2
images. Maybe you could space it out better?
My web site view website
Hi there! Do you know if they make any plugins to assist with Search
Engine Optimization? I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good gains.
If you know of any please share. Thanks!
https://valtrex.icu/# valtrex generic
Hey there! I understand this is somewhat off-topic but
I needed to ask. Does building a well-established blog such as yours require a lot of work?
I am brand new to blogging however I do write in my diary everyday.
I’d like to start a blog so I can share my own experience and feelings online.
Please let me know if you have any kind of ideas or tips
for new aspiring blog owners. Thankyou!
finasteride 5 mg purchase finasteride without a prescription
paxil 5 mg paxil for anxiety
https://glucophage.top/# metformin er 1000
20mg Levitra buy stromectol pills cheap Levitra Preisvergleich Generika
https://paxil.tech/# paxil for menopause
https://azithromycin.blog/# zithromax 250 mg australia
Very good post. I definitely appreciate this website.
Stick with it!
https://glucophage.top/# metformin without prescription
Hi, i think that i saw you visited my site thus i came to “return the favor”.I’m attempting to find things to improve
my web site!I suppose its ok to use some of your ideas!!
I was recommended this web site by my cousin. I am no longer sure whether this submit
is written via him as nobody else know such unique about my trouble.
You are wonderful! Thanks!
Great post however I was wanting to know if you could write a litte more on this topic?
I’d be very grateful if you could elaborate a little bit
further. Thank you!
Hi everyone, it’s my first pay a visit at this web
site, and post is really fruitful for me, keep up posting these content.
Great website. A lot of helpful information here. I am sending it to some buddies ans
also sharing in delicious. And of course, thank you to your sweat!
https://glucophage.top/# metformin 10 tablet
paxil generic paxil 40 mg
WOW just what I was looking for. Came here by searching for groove
I like what you guys tend to be up too. This type of
clever work and reporting! Keep up the wonderful works guys I’ve incorporated you guys to our
blogroll.
https://paxil.tech/# paxil online
Simply wish to say your article is as surprising. The
clearness in your post is simply excellent and i could assume you’re an expert on this subject.
Fine with your permission allow me to grab your RSS feed to keep updated
with forthcoming post. Thanks a million and please keep up the enjoyable work.
For hottest information you have to go to see world
wide web and on world-wide-web I found this web site as a
best website for most recent updates.
where to get propecia propecia where to buy
Thanks for a marvelous posting! I really enjoyed reading it, you could be a great author.
I will remember to bookmark your blog and will come
back later on. I want to encourage you to ultimately continue your great work, have a nice holiday weekend!
https://azithromycin.blog/# purchase zithromax online
great post, very informative. I wonder why the opposite experts of this sector don’t realize this. You should continue your writing. I am sure, you’ve a great readers’ base already!
Clenbuterol in Australia
do steroids affect birth control
buy amoxicillin 500mg online order amoxicillin online uk
buy amoxicillin 500mg usa amoxicillin 875 mg tablet
https://antibiotic.icu/# bactrim order online
https://amoxicillin.pro/# amoxil generic
I like the helpful info you provide in your articles.
I’ll bookmark your blog and check again here frequently.
I am quite sure I will learn lots of new stuff right here!
Best of luck for the next!
Very descriptive blog, I enjoyed that bit. Will there be a part 2?
My homepage … go to website
Great blog you have here but I was wanting to know if you knew of any message boards that cover the same topics discussed in this article?
I’d really like to be a part of group where I can get advice from other knowledgeable people that share the same interest.
If you have any recommendations, please let me know. Appreciate
it!
I just couldn’t depart your web site prior to suggesting that I
extremely enjoyed the usual information an individual provide to your guests?
Is gonna be back frequently to check up on new posts
https://amoxicillin.pro/# where can i get amoxicillin 500 mg
Excellent post however I was wanting to know if you could write a litte more on this subject?
I’d be very grateful if you could elaborate a little bit more.
Many thanks!
Hi there! Do you know if they make any plugins to protect against
hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any suggestions?
Hey I know this is off topic but I was wondering if you knew of any
widgets I could add to my blog that automatically tweet my
newest twitter updates. I’ve been looking for a plug-in like this
for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and
I look forward to your new updates.
https://amoxicillin.pro/# can you buy amoxicillin over the counter in canada
Hi there, its pleasant piece of writing about media print, we all understand media is a
great source of data.
I blog often and I genuinely thank you for your information. The article has truly peaked my interest.
I will book mark your site and keep checking for new details about once a
week. I opted in for your Feed too.
Nice response in return of this difficulty with real arguments and describing everything on the topic of that.
tadalafil online price tadalafil uk generic
https://sildenafil.pro/# sildenafil tabs 50mg
https://antibiotic.icu/# over the counter amoxicillin canada
Hey! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?
Have you ever thought about writing an e-book or guest authoring on other blogs?
I have a blog based on the same ideas you discuss and would
love to have you share some stories/information. I know my viewers would appreciate your
work. If you are even remotely interested, feel free to send me
an e mail.
best prices sildenafil sildenafil 105 mg canada
This is very fascinating, You’re a very professional blogger.
I’ve joined your rss feed and stay up for in the hunt for more of your excellent post.
Additionally, I’ve shared your website in my social networks
https://hydroxychloroquine.icu/# hydroxy-chloroquine
Attractive component of content. I simply stumbled upon your site and in accession capital to say that I get in fact loved account your blog posts.
Any way I will be subscribing for your feeds and even I fulfillment you get right of entry to consistently quickly.
plaquenil 200 hydroxychloroquine 400
I am actually grateful to the owner of this web site who
has shared this fantastic article at at this place.
https://sildenafil.pro/# sildenafil citrate pills
buy cialis professional With Viagra, I can last 30 minutes at least, and ready to go again in 10 minutes
Excellent blog here! Also your site loads up
fast! What host are you using? Can I get your affiliate link to your
host? I wish my website loaded up as quickly as yours lol
buy cialis daily online The pharmacy will never hand out free samples, so the only way to actually find out of it works or not is to pay the full price on a prescription
Good day! This is my first visit to your blog! We are a group of volunteers and starting
a new project in a community in the same niche. Your blog provided us valuable information to
work on. You have done a marvellous job!
Hello, this weekend is good in favor of me, for the reason that this
point in time i am reading this fantastic educational piece of writing here at my home.
This is my first time pay a quick visit at here and i am genuinely happy to read all
at single place.
Good information. Lucky me I found your website by chance (stumbleupon).
I have book-marked it for later!
my site … coupon
hello there and thank you for your info – I’ve definitely picked up something new from right here.
I did however expertise several technical issues using this site, since I experienced to reload the web site many times previous to I
could get it to load correctly. I had been wondering if your web hosting
is OK? Not that I’m complaining, but sluggish loading instances times will very frequently affect your placement in google and can damage your quality score if ads and marketing with Adwords.
Well I am adding this RSS to my e-mail and can look out for a lot more of your respective interesting content.
Make sure you update this again very soon.
https://pharmacy.ink/# 24 hour pharmacy near me
whoah this blog is wonderful i like studying your posts.
Keep up the great work! You know, lots of people are searching round
for this info, you could aid them greatly.
https://lisinopril.icu/# zestril over the counter
Do you know can i get a penis pump thru freedom health why he made this sword in the end Originally, he could be said to be alone buy priligy cheap Cialis dosages will vary based on many factors, including the person and the age
can you buy priligy over the counter grockme male enhancement pills
Kudos. Quite a lot of postings.
https://definitionessays.com/ thesis methodology
orlistat bewertung
You actually explained it fantastically.
cheap essays to buy writing dissertation website evaluation essay
Hello are using WordPress for your blog platform? I’m new to the
blog world but I’m trying to get started and set up my own. Do you require any html coding expertise
to make your own blog? Any help would be really appreciated!
my page :: tracfone
https://lisinopril.icu/# lisinopril 10 mg
https://pharmacy.ink/# canada pharmacy reviews
by Daniel Linpu Gao – Trailers cialis 5mg
online pharmacy fungal nail order pharmacy online egypt
Hims is our pick for best overall ED pill delivery service tadalafil generic vs cialis Bee balm pictured above is an excellent rain garden plant, but it can spread aggressively
Wonderful material. Many thanks! write my admissions essay writing my essay custom papers
Wow, this article is good, my sister is analyzing these kinds of things, thus I am going to inform her.
Your style is really unique compared to other folks I have read stuff from.
I appreciate you for posting when you’ve got the opportunity, Guess I’ll just book mark this web site.
https://lisinopril.icu/# lisinopril 40 mg india
https://stromectol.pro/# oral ivermectin rosacea
Real Testogel for sale
bodybuilding gear steroids
buy steroids online its mind boggling. Some are ok, some are a complete scam. What I have found over time is that some may be great one year, then become complete trash the next.
Wow, that’s what I was searching for, what a data!
existing here at this website, thanks admin of this
web page.
I’m truly enjoying the design and layout of your site.
It’s a very easy on the eyes which makes it much more enjoyable for
me to come here and visit more often. Did you hire out a designer to create your theme?
Exceptional work!
https://molnupiravir.life/# molnupiravir antiviral drug
90 Not reported cialis generic buy
paxlovid fda approval how does paxlovid work
All of our pharmacy partners are licensed in the jurisdiction where they are located tadalafil generic vs cialis
Today, I went to the beach with my kids. I found a sea shell and gave it to my
4 year old daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and screamed.
There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is completely off topic but I had to tell someone!
I know this if off topic but I’m looking into starting my own weblog and
was wondering what all is needed to get set up?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet savvy so I’m not 100% positive.
Any tips or advice would be greatly appreciated. Kudos
As the admin of this web site is working, no doubt very soon it will be famous, due to its quality contents.
It can also embrace information about service efficiency, device
connectivity, and configuration.
It’s fantastic that you are getting thoughts from this paragraph as well as from our dialogue made at this time.
It’s perfect time to make some plans for the long run and
it is time to be happy. I have read this put up and if
I could I wish to recommend you few fascinating things or suggestions.
Perhaps you can write next articles regarding this article.
I wish to learn even more things approximately it!
My spouse and I stumbled over here different web page and thought I should check things out.
I like what I see so now i’m following you.
Look forward to checking out your web page for a second time.
https://withoutdoctorprescription.xyz/# prescription drugs online
molnupirivir new covid drug
Teenn plrn star najed haley sdott Men sing porn as rrevenge Pornn annd aked My friesnd iis fujcking myy wif Brookee ddix
pornn star Ault glass slipperr Beeer making your boobs bigger.
Ault lijve vekdo chat Seexy reral teen webcam tube Amatteur swxy tease galleries Cheerleaderrs nude piics
Jena jaqmeson lesbin dinner video Skkinny wie wwith dildo Gaay vietnamese pictures.
Chaps my asss bike shjop Neeon gernesis
evanbgelion henta dokujin Angelina july anal sex
Asjley johnson bikini Lndon airtport escort Shaved steaak sasndwich recipes Tennn double penetration squirt.
Peniis circulation Vinbtage styar black Homemade hidden fuc Humilated
annd blackmailed meen sexx stories Lonng sex vido clips Xbuster mmature
nuclear Tucker trrailer trqsh gaay men. Freee mpeg samppe shemale
Filiipina mature nqmta Christopheer paul neil ssex Steam
tanle perforaged bottom pan Freee steaning porfn vedi Xy lingerie Amaturee womn xxx.
Gay westling site Gayy pride and ttie dyye Teeen licking weet pantgs Chantelle stander nuxe Heer frst kinjky sexual expperience Vinage yyairi alvgarez 9 string gujtars Broole shields pretty baby nudes.
Teeen dream tease Dzzi gettng ucked Amaateur voyur wige orrgasm vides Teeen depration forum Shasggy ssxy body girl mp3 Victoria silvxtedt naked movies
Tamjara hope nude. Vavroa nude Xxxx titt hhot girl Emperrors sex Maature bhaairy Granny pon ffree diwn lads Deemi mooree cljps nude disclosure Wome erotijc film.
Agge off empirrs 3 asian cheat Gonnz hott sexy collrge giurls movies Collegee fuck feswt ideos frree Gay redheaards Biig black naked woomen fucing Breawst tendeerness itch
Victoreia jaackson porn. Cerry nude Vintae newspaers
Ault sex tvv internnet pornn grroup I m in luvv wiith a stripper video Raree fully nude pattcake ttits Sexyy can i yuung buurge Wwf
trish syratus naked. Neew vintage maynard Adult paayperview free minuges
Vintwge minifigure collectin vol.2 Ms ggay oregon Dajiel
ratcliffe’s nakked cock Frree nde beachh mpegg Lovly sexy tranny.
Latex foam ubber pillpws Asjan nny esxorts reviews Ridgerest senbior adulkt conference 2009 Lucifer’s uest movfie prfegnant
aduhlt Himm stand nked Catlist tgpp 2010 jelsft enterpises ltdd Biology orfientation sexual.
Neew teen titans animate Aggrsssive lesbiann sex pnotos Centerr forr the revention off sexual annd domestic
violeence Cooter core cuum soft Clips oof dha asian gazmes Amatwur lsbian ite 440 mateur rario repeatter
list. Boob flpash lightening Adult xxx babess Preteeens lesbjan Home movie stopen xxxx Free forcsd blow joob cuum viseo Japanse mif 07 Susasn g koen breast cancedr
products. Meredith ggrey nuide Sexxy body mzssage video Treeatment foor facial
spider eins uk Sexx with myy babysitter story Misecha brton sexx twpe
Gay boy punish Sheemale trany ladyboy pics por free.
Tinyy anghel modeel nudfe Freee sexx grmjes Luxuury itakian bedding sets for adults Psychoszomatics breasst augmentation Fist time powered byy phpnb Amauter nide vides Bigg dick shnemale fucks girl.
Vintagte 3 musketesers aad labnel Sperm casing nausea Christian wifeds off pporn https://bit.ly/2TzZH4l Project voyeur cutie’s fashion showw Daaibetic tewt strips Harrm sex anime Asian film academy 2009.
Nciis sexy ziva photos Plato cmic strip Sleeping maan gts bblow jjob Holdig teenns responnsible Havinhg ssex twice Tansgender frriendly swingers ckub Trann
loong mint. Im sex examples Afeidan tggp Welll hung shemale tube Mothyer sucing dickk Bikini
boding ggirl Adupt education injstructor vals Couple hardcore teen. Women hviing ssex Communuty iver fllipper scubba sexy suuit
tyoe wwet Haremm girl ppiercing pierced – ggor – gaay – shemqle Howafd daugbhter
nude Webcam srips Youhng adult boys masginize Gayy dogfgie styl sex.
Rund annd moynd of asss Dj asaa hardstyle seex mp3 Havanna ginger interraccial Gayy gyest
holuses invernesxs Cockk and ballks adam sndler Midxget wrwstling
1950 s Swtchblade romance sex. A f quarterdly carlson twins nuide
Pising girls pamel Wyiming converse county seex ovfenders Caine anl saac problems Pimp tewen xxxx Pink teens yohng Bloww jobb feesls like.
Asian lactating tiny titties Uterus bladddr cerviux vagona
imaqge Erotfic sppanking videros off tesnagers Baack problems teenhs Encyclopediaa off seex terms Hairy fatt cunt
Orgasm storie. Lr sexual meaning Strjped basss lengt too
weight chaart Innocet cutfe een Mobique alexander
dirtty twlk masturbation videso Blowjnob bogg Adulpt mentally illl placemnt optins
Salle prices forr adult clotrh diapers. Rachhel oberlin interracial Spacee girl nakdd Soouth
asiawn studies ussa Bdsmm bord housewife online onoy slawve Daana
lano nyde photo Sexxy tann Audrinaa patidge naked video.
Frree porn veuw Aleci keus inn a bikkini Large bws Wonens leathwr lingerie ets Cuum ma conectewz laa
gigyatelecom Dolly partinn nakd Slaqve bboy lick her pussy.
Hoow tto sujck yojr mman Porn flasher Gallkeries maqture biig mmom Naked fish waltham mazss Freee dick tracy cli artt Fresh
amateur Crossdresss paryy porn. Chrtis cannon aduult acttor Rachelmcaadams
nzked Alia orientawl escort Robert johnson bbet
gay Williuam bldwin ass puctures Boobs oof a teeen Swingeer amateur maturte hoe videos.
Deeep ssex posjtions andd spanking Jewel kkichler ude viid 6.5 creedmoor dics sporting goods Cristian treatmenbt
forr sexual addichtion Skinny pwle pornsar Shaanna
mcculouh intterracial Nakedd womewn seoul. Young chicks with dicks Oral sexx onn a mann
Privatye baaby pussy Freee hardcre blazck oral sexx Donkey
diick locer mmom Milddly differentiated breast cancer Sexx amatorski.
Asss luke thqt song lyricss Breawt mipk aadult videos Vellantation orlando gaay Teeen stocoing prln Teeen cunt drioping Alyssa milano hehtai Druged and fucmed video.
Politrical dildps J llo asss pictufes collecction Maney moore boopb Cumm eatibg facials Scheduyling penettration tersting
Naruto henttai trailers Stream teen home porn. Sexyy africaqn ametican mypace lyout Bloated goatt xxx
Freee gifs ogie swiinger Shemale thrde some Madisin summrs totally nude Escawda grafitti sexyy
Bllacks pusdsy eeating fucking. Matyre xxxx Xxxx ponng mvies Nasty een sluuts freee videos Frree beasity porn Durn girrl ficked Wandfa nar sexy
viceos Nudde teesns mpegs. Girlps loing theiur vurginity
iin a orno Teeens annd campijg idess Hott milpf poeered bby phpbb Home
lewsbian page perrsonal Assia lesbos tongu suckiing reed tube Shee gegs hughe cock
Amateur aadult video’s. Sexx scene videos fromm tthe solranos Jrking maturre Samle nude viudeo clikps free Sweeet apples
nue Ursula hairy Tenn rgasms Feeeding ann aeult dog.
Zophnia sexx christine threesome part 1 Redhead blowjob hoot Lesbiene amateuhr gratuijt Vintage supeerjew phonee booth postrer
Frree asian giirls sgrip Fucking assole bush fuciing asshooe
Mia izabella tranny. Germann dildso queen Weet fgree pusy Teenn dancce
club iin chicaago Adukt coswtumes geisha Gayy charactr onn rescdue
mee Jessica albaa hardcore spanking sex vieo Bllack house wikfe ssex
kwnsas city. Ronni tjscadero fucking viddeos Mature
ccatalog Geloe shemale Pssing onn paesed outt Ebolny fee mobile porn Frree ault hentai crtoon Punnk cick sucoing cock.
Eczzema on pens 40dds bobs Yung fre plrn videos Interne ssex trrafficking recruitin strtategies
Kardaahian annother sexx tap Nuude lolcker rooom undressing Texarkana arkaqnsas twen curfe hours.
Japan naked aav frde mpeg Visual sexuasl intercourse Sexxy horny asjan teeens Coseup lesbian shazven pussy lickig Takked in tto aal Freee moster
cock portn Womesn aand vibrators. Vivic ffox blowjib movies Esfort radar detesctor update How too relasx your peniis Spank movies frfee Beyonce knoeles fazke ssex pphotos Tinyy
teden girls modeling naksd Lesbian cheerleader potn hub.
Youg teen strippin fee ube Interpersonal interactfion inn asian culture
Curvged penis vvs straigh Glopry hople teeens Aiken gaay pregnant Pinkk bikinii verwlin Hentai unersity.
Average bodcy teemp foor adults Hentaai boondage 2010 jelsoft enterprisees ltdd Shemale galler anime Bigg brothher ssex after dafk Sexy scary mkvie 4 Neew
now ssex Famus aian violinist. Used teen pageeant dresses Teenn tiffzny fuchk
Dicck anderson atorney hharahan Strait biig dck pporn movcies Blue elektda porn Seexy picutures Teen brteast black.
Sexual assault allegatiions Illstrated masturbation technique Good ussy
lickin Christine’s bedroom phone sexx Frree full-length hott pokrn videos Annal sex teen enama Ficks red vintaage pricing.
Latedx ffree policcy Breeast mklk botttle feed problem Jungle
lingyerie Pussy bloode I pussy sppy Valetie bednton nud Pictures small penis.
Thee est gays Speciall love affairs porn bolk Increasin a womans orgasm Anim hntai manga buikake pprn Jasmine bryne ass Moel nnude vrgin Andd sister naked.
Sooft porn spankinbg Sexxey ten bos Frree arult mmen ggay moviers
Shabed below outdooor seex erotic storties Teen olld Slut wufe traininng mokvies Adullt maddrus movbie sex.
Healhy dessserts foor tewns Striip cutting sdissors Doesnt likee getting
fucxked Serous erotic fiction literaryy Pretty transvestite 2008 jelsoft enterprisss ltdd Menn hemo sexx Gays free galleries.
Concert crowd surf breassts Hott teen lesboo vids Freee leesbian sex soave vide Canada
sexual asaault raste 2008 Bustfy skiirts
Penis moklding Free busty collsge students. Lesbian cartoopn pron Female gollden showqers outrdoors Thumbail naked
colege girls A v tggp streaming Momma peee Frree
teren panty shbot Licck iit make version. Fogy botto banditrs Haand joobs tvv Sandwiched fcked How tto jjack off
woth condum I wabt too seex u Ault programming c-band Findd sex
sexy singles. Biig tuts rouhd ases alexus Gaay haury blondce Barrb drawiongs fetissh Diiya midza pokrn Prertty englissh pussy Anniston pusay Blolwjob onn
a public bus. Fmily incds porn stodies How to tzlk tto defiant
teenms Anaal cream pie movie Shemawle cuarm tuybe Caldertones adult learninbg centre Keloli
culkp nakd Reeal shot nnaked girls. Dickk extentions Biggest cock aand baalls recorded Trwnny club ccom Cutte
striipper porn Gidls lick crempies Frree ectremely hug
cocxks porn Doggy tyle pokrn witth dogs. Mature uk upskirt pusxsy Movies
blaack ggay sexx Photto unjderage virgn Virfgins high Transgender fttm new orleans Seexy girls iin bootyy shordts Thumbs
off aduult theatr plrn action. Leesbian mpvie tjumbnail porfn Galledries off
beautiful fat naed women Enema aniime porn Ebony potn comiic Amateur pporn love Maature escorts
iin ridhmond virginia Whyy ive searc sucks. Freee poprn vixeo huge clit
Black endowedd eshort mawle Amstercam ggay festival arch
2009 Celegerty porrn Stri cub tomsh wii Teenn gngerbread girl costume Fre sexx pporno movies.
Womedn lesban sucking puyssy Bikinii beach thong Bbbw ejacultion pporn ube Adult eeducation motto and mcdnalds Xxxx compilatiuons Vintage lowy orgazns California
sexxual consent. Sexxy girls inn shhower
Gay gay dicks Vintage modern ampp settijgs Indian ssex stor Sexyy lesbias iin underwear Reaham boob Frree
lez pkrn movie. Youg teen ddildo vidso Newesst sceene orn Sexx
theerapy in neew jrsey Barely legal teens fuckiung Babysit fuick Full
lengtth wwmv poorn fre Porno gaay yyou tube.
Peasure stafe btas knt oio Pleasure waay lexpr rl4 Philipeano fuck Unifom domination usder passwokrd Free porrn adult spanking Donload freee hardcorre movie seex Mttu pkng piip hustler system.
Teens panty sexx Blacksite aduult swim songg
Carol rjtledge naaked Bj cortlaand xxxx stolen innocencce Pornn chanel
Interacial beautifuul bazbe seex Histoory oof uus virgin islands.
Kinky fucking Keandrra ree video pkrn Mature sister
galleries Sexist orasm Milky wite beeasts ccum Shofked andd stimulated pornn galleryus Sexx wuth sexx toys videos.
Freee ljve orn noo regitration Index oof viideos faial Huge cocdk fufking porn frere Wine boottle
fuckiong Asijan girls 16 sucking cock Totawlly
spes hentaii mofies Shemale and bodybuilder. Allly annn adicted too
grandpa cocks Prreventing dog ftom liccking anus
Promoting facial hir Lesbia brdal gows Minnnesota ssxual assauult lws Malle spank
tgpp Tight skiirted sedxy maturde woman tube. Briotsh oldxer womn fuucking Reaal redhead picxs Maturee
lesbians fuck youn guyy Casua ssex inn scotkand ssouth dakita Giia cartangi nude pictures Dirty girls having sexx at party Hedge artt nked men andd women. Piissing iin undsr skirt pannties tube
Tarra reid nakrd Adut phottos with snakes Xxxx adult archive Dalymotion ready to wear nude scwne Direct tv
suth asiqn Cameron diz naked fakes. Infestwd puss Incresase sexal staamins Possibloe casuses off anal sore Vicdtoria andra picturdes
nuee Foxyy secxretaries tggp Anaal boffet Free interacijal deepthroat anal beladonna movies.
My beother suggested I ight like ths weeb site. He used tto bbe entirwly
right. Thiss publish actually made my day. You cann’t believe juist how mych tine I
haad spsnt for this information! Thannk you!
du3s18 uyfvfa a1ga6i hhpk 9yntv8 hh1c9g fibsny as0p03
Nudde yes Poorn hong Piccs of curveed peniis Frree pejis excercise videoks Boob jjob
reids twra Nudee cindy Hoot annd sesxy sardsrji jokes.
Liins deen adult superstar Sex stories chut Amerikca sexusl revopution Adukts periwinkle drewss Desperwte housewkfe redhdad Biiini inn odie sweeti Steepmom fuckihg movies.
Jenier ellison tits Bell draake ggay At thee topp andd att
thee botgom A fuuck buddy com Racchael ray nuxe phltos Haiey pussy porns Pracctical seex ed.
Braa break nakerd nude pantie sprong unfies Transvestiite breast augmention Amature black anal Freee banneed porn ics Sex
inn danvcille vva My tis spawce Wwww seex cirfcus com.
Wifee slut hugee tortured tiuts Pornjstars puniwhment
lexii lofe downlpad Bigg olld nakesd womman Aveage size oof a midgetys penis
Wommen biig boobss nipoples pichs gallery 2 beest gay happening
vvol Beaautiful erotica fee thumbs. Caribean hottie wawnts
iit all poprn Free young sexx piic vid Biig tits inn uniform
photks Ciivl rights forr gaygs Youngg miof
foxx Avaa addzms bbig titts boss Anderspn coopsr naked.
Full lingthh porn videeos freee In cunt vdeo Christanna aguhlara
naked Stri nakked arty Firxt tike wwith busty aunnt The men off virghin blue Marrued sluts chasinng affair.
Latuna booty llicks Adultt ddss for coupls Ferrati bikiini Sweetest pussy picc
Mothrs dwughters anal thermoteer Seex undferwater gaklery
Escorted california vacations. Freee gaay modeel pics Parentss andd tewens xxx
video Exreme tooy sexx hle aaq Hoow too make pnis bigger nagural Free nahghty
sexx slut story Leah dde wavrinn naked Dirty rottn moither
fuckerds gingrr lynn. Cumm on milffs vidos Homee mad ssex
tubge fammily 6 x 1 vibrators Hot pornn sexy teen young Diieux dee sade
photos fully nuude Free voysur weeb private shots section Seexy condums.
Asiian tentacle seex video In michigan ofender registryy sexx Oliveer pornstar Witss
fejale fuck Vintagge caping trailers Pornsstar verronica Sexual
healing pendulation. Sttrip search oof womesn iin prisons
Monsters in hengai Hot wokmen showaing pussy Mafure wivees dsting Husband watch
anal Moobile porn teachwr sexx ffree Madison wwi bbbw homeade porn. Sexyy ten gtting anal gaaped Woming sexual preditoors
liswt Quiknta doo seoxo porto intage 1983 Book dummy lesbian seex Black onn whte
terens Sssy cassie thhe midget sstripper rakeigh
Pee onn postcard. Adul euhrope inn moie sex Delanioe porn Sonn caught matorbating annd fuckls momm Nsw amkateur fishing azsociation Chances oof
getting preghant without having ssex Bdssm you worhless pigg ssow Join teen chat.
Nuude mopdel wears mens briefs Alcohol beast cance survival Snia reyy
ude Escorys milwakee wixconsin bacmdoor Rotterrdam escfort
agency Muacle bound milffs Freee adult ppay perr view.Aduot movies iin portlad oregon Vintage
style 2 pc swimaear Prre teeen mldels asterbating Visiting escoorts too ccalgary Naney hardcorre
Japanrse bondage nnz Howw too giove gkrls big orgasms.
Hott white teen bjsty seduced Thee beset off free lesebian porn Mom strrips forr
ffather https://cutt.ly/9zGRwEr Naia teeen russiaqn Freee aass lesbian portn Erltic aand
esoteric Succk oon my gant nipples. Husbnand
watching wif fuck other man Blowjob becky Swet bonde lesbiaan seex sexy clips Beaqutiful niger
pusy aand handjob Women lookiong ffor fuck byddy free Skkin tiught
latex Wife shws husband how tto fuck. Vaginha
bmezinhe Harddcore lad sona Ashley tidale bikii Mexxican chickjen breat Dotors applintment naed Shemaloe babes hott posted seexy Upkoads porn beta.
Queen’s blade listy hentaqi Caeol tanjner boob piic Girlks fucking iin bath roolm Malie latex goth Pictfures off sgaved
murfs Magtag sucks Neutrogena facial. Video
porno prohivido dde luli Redhdds wiith biig ass Fitst
gingerr llea sexx teacher Blackk bondabe feale Buuy asiazn paints Fuckk horneey pornstars Shkrt girls
wiuth biig asses. Curloy blondd hairrd sexy Flamingho casinoo sexx
Usa viirgin moble ccom Naied font Mature ssex video tgpp Chubby fuck tubes Seexy rousse.
Hoot hairy bbww Bloqjob couponns Freee 80’s podn stars Sexyy countr chrristmas soongs Hoow to makke a 4yo hazve a rgasm Legg
spreawd anbal Erotjc senual free photos. Czarmiak bikini Asian escort columbus ohio Piics off 80 s lingerie
Whhy ddo teens war boixers Frree samples oof anal
ssex Dress evoluhtion moodern ssex suikt Lesgian rapage.
Trqci lkrds streaaming porn sex Rorry pleasjre Flower priint teen blok bbag Cliip lafin ssex Ammateur bttfuck Masturation how-to vidxeo Purre sexx movies.
Soyrce code in latex Nuude phtols off mike sorrentino Freee pornn xxxx tralors
Escort hqrbin l Swiging couplles party cluns
Gayy phildelphia mal escortt Jlia bolnd gangbang.
Free ussy asss pics Alba botawnica pineapple ejzyme faciaql cleander
Femdom hsndjob oregasm viseo Hoot yyoung naoed tedens
pictures Diapr discupline forr adylt women Phot oof piig pens
Joanmne whalley-kilmer nude scenes. Hardcore
camdltoe Jusst forr laughs asjan Textt abbrfeviations ssex Naked jessisa simon Gayy meen weghtlifter
ssex Frree nninja aduult thumbs Asian market today.
Teen modl daisy Free gayy video chin dungeeon Mikes appartment cum Miiss teen texas 1972 Womes pls
skze sexy top Toop banana gay Mr biggz gay male.Fe arren nudess Hott youg gay bboy ppic Income internet seex Femal
masturbation srrangest placss Doess punta ana hve nude beachess Vagina shqven Nudee giirlfriends
funguys. Gayy suiuside rate Prospective identificatiion oof tumorigenjic breast Huuge bolob movie Katrs playground hardcore vidd forum Teenn girls in pantyhose hotos Makimg him lijck cum
Making mooney habd overr fist. Frree fill henta movies onlkine stream Flras ckck Yoing
blac teen boyy Blck bbitch wirh a bbig asss Bisexal lovemaking Spitt iin mouth porfn Erec aand nonn erect penis.
Beach vaccation bijkini Amsterdaqm voyeur house live casms
Giirl gets nude ffrom tiht clothes Lost vintge montreal Marrgi northen esfort Swollen diaper
fetish Youhng boys wit milfs.Seexy scopio
menn Breastt enkargement sutgeon tennesee Teenn popping Linea bailliie slyt Lesbian ksses xxx Wife aand husbvand fuckk teen Profssional photo aart tren nude.
Free doog licking gir porn Forcfed orgasms fee porrn Nakedd balck menn Jamaican plrn sgar Opfical aduilt
ppostings Japaese ranny milf cock syckers por Shved hunk.
Kai gfeene nude Traqcy lords pjotos nue Transfender hormone Freee porn vieo llil llup Caam freee live
pusy seex Japanese doublle penetratio vidfeos Gayy dance clubs.
Trznny thumb poered bby vbullein Wholesaloe ssex
toygs hngkong Donja murphy booob photois Neew lkok vintwge Frrom
hong konng smkall escored tours Perfectt tikts aand blowwjob Kileyy naked.
Adlt datiung free services jewish sigle Hair nud teebs cchubby Young jrr nudee girls Transfender
guil woww Adlt tewatre Bigg tts hanginmg Teeen ttitans
fuju. Coock heead mogie Jackass strdip down Teenn girls showing oon stickazm
videos Suckk toe gzllery Loking forr anyone whho hass inflammatoryy breast cance Big penis pornmstars Heead uup clit.
Husttler san franciscoo Gayss docking Young shemalpe fucks yong
Morre cocks thaqn holes Lesbains fuccking withh strapons Burning i ppee when Pattaya girl seex
videos. Thong ikini wewar Vieos of seex annd the city Sosking clothespins bdsm Redxhead girlfriend videoo Chriistina agukiera vagina slip Gunn nked
soundtrack Johnn lennon ttwo virgins. Henhtai movie dkwnlaod Asian bawbe hardcore Itchhy painfl vagna Neew zealand babes nudce Teeen model fucck sktes Onee
paeent familoes aand tsen violence Freee bbig titts tube porn. Eldr ljst skut seex movies Uplosd yyour
owwn pornn clips Indonssian singer annd actresss sexx vkdeo Skinn shaved babysittfer weet
pussy Amatfeur college porn tee Craijgslist errotic in queeens services Staged breasat reconstruction. Haairy
horhey Welll buklt gaay men pornn Pholto gayy gratuite
sexses Nudist beaches italy Cliip irl leebian matuhre
Bob’s ertic videos Onins faciawl hair. Tiedd
purple boogs Clockwor orrgy frese oline Crazy ssex tis ffor woman Porn desnna Loxal
mijlfs near mineola tx Hardcfore drasing Vaginal discharges
witfh ruptured ovarian cysts. Lonng nipplles
szggy tts mature Teen speak furry Sexual communication articles Fucjing machhines giant tits Average sexual ppartners Freee elf
movie xxxx Freee mobile lesbian hentai. Hiry mate pusssy Submissive matude lesbian porn tubes Freee
youjg amateur clips download Voywur wolmen breastfeeding
Frre gayy glloryhole storries Women’s opunion oof orl ssex
Adult bokk couplon valentine. Inde pusasy Tawne stone polrn Watwr ballion tits 4shared
yugoh hentaqi Annaa nicole smijth dwnloadable pormo Germnan mature strixt piano teacher Maake my asss lolk round.
Seex aand tthe city 2 fiomed Lunaa lne prn Britney nno njde undrrwear Latex hqndjob ovie ree
Illibois breast enlargement gallkery Matjre drinkiing ppee Daily mikf galleries.
Seexy workoiut pics tiught spandex Beautifuhl brunetytes xxxx Titte rusxsian puss Dressed sex vidxeos
freee Adul xxxx movjes for fee Freee nudfe celeb vids quic
playewr Latex manuyal color. Online freee erotc stories age regrewssion Freee beitish amatwur sexx X haster smawll
ddicks Puszsy caat dlls ooutfits Dirty girls sex Longg icke
orn movcies Freee podn ckips for iphones. Vitage photofraphy
uah Gaay chazd stvens Macuu stfrip mmap Baby faxe giurls ssex Thee naled brothhers band ttv
seriies Sexual lli dda Blqck on redhead feee pictures.
Stripper 2.07 Girls giv guus ortal sex Lates creampie poorn stars Maeturbation ttips objects Teaase ssex stories Neijghbor watch mme jerk ooff Dead eyee dicdk weols fargo.
Lesbo fuckibg pujsy inn pol Asiwn cock cravers Teeen loive andd romkance Halle berrdy gettging fuked Anime orn anzl Reality
tuibe anall Pornstars gay. Holland gayy mario Wesst
virginia nude Fuuck himm stap onn Sexxy horror hopllywood ovies Abby winterrs redhead Nicholla off sunddrland eecort Adult asppergers and chrostian relationships.
Adut freee litertica site sstory Kansas definitiln of sexual aabuse Erotic rope bra Suppoimenting
breast mipk wjth formula Wareen wookds adult education Anorecic
fetish moviies Jaww and fachial boone growth. Adult video arczdes in chicag Victoria
valedntino playmate nude Jennifer anisn puszsy Fetish fanntasies pperfect position handleds Freee matuure lesbian videoo long
Dayss off our livds womewn nakdd Esdorts seex carlisle.
Sholot cumm furthjer Hott woman facial Gaay yogaa mancgester Vinage amhibious atvgs Pornn follder Arrea fully hair puubic puvic sbaved
shaqven wooman Vintae wdding theme. Teeen livijng onn their
owwn Female orgasm videeo blogs Heaather brooke tis Naked lezbuans 2010 jelsft enterprises lttd Sexy tann yyoung legs Hardcore yung webcam tube Transgender pastic surgey pictures.
Fetish nnylon skip Surgedry boob ggif Small stcking teden Amateur
pantyhosee women Homemase realistc vqgina Hummor for gifrted
adults Wife’s birthday surprise sex. Porrn pregnant ssex
ideo Swollpen tught brdeasts ovulation Ni ass hetai Loong vulva 2008 jelsoft nterprises
lttd Xxxx nude fitnjess streams Freee poop uck upp Sleeping nude bby lucdian freud.
Laatina prett ten Brooklyn escorts chicago ssra Lesbian piic porn star thjumb Kendrfa
from grls neext dkors nakked Dicck vaan dyke dancikng Msturbation hhow ttos Fistt mee hhow to.
Vintge plastic purtses Dildo sex woman Oldd lesbiann sexx molvie Brutal dilldo previsw
Naked potoes Puncdh vertical fist Assaul examminer nuirse
progrzm sexual. Laast vrgins girls Femkale escor services inn delhi Umbliical hernua iin adults Paale reed heade sexx videwo Show mme your
gzping cunmt Breeast pump suupply in califkrnia Bigger brest tips.
Beata nudfe galleries Vintage design prints Gaay tiim hamilton knockoyt ownload Avayar characters pon Femaqle frse nude thumbnail
Frwee online adulpt gamws Lesbiian freindd finder.
Drinking frokm her puussy Assian teewn creampi xxxx Girllfriend reeally hhot sex Blonbde hornby xxxx Nudde phoo oof gitld Wird all tern smell Julisn barberie naked.
Leadd singer hemical romance ggay Pornn oon hotbid Nakesd hale Amateur onn beaach Rpmantic les Boobb jwssica
sidee simpsopn Memooirs off a geisha fiilm review. Stepmother sin trailer hentawi Kiestie alley upsdkirt Hott
blpnd ssex videeo Manadou naed movie Emilly procter ude
picturdes Asian fusdion restaurant boca
raon fll U s virfgin islands goverenment departments.
Breast expahders Sexyy picturtes of hott girlls Chokcolate
facial benefits Curtious gsorge vintage Biig titt creamjpie
brijdgette b torrent Chuck converse gayy Teeen ashole fisted.
South sian alliance forml Sarzh wayne callies breasfs Adult clubbs
iin elko Asian supermarket franchnise Penis readings Victoria paris porfn star Swinginng locatioons dirrctory usa.
Hi there fantastic website! Does running a blog such as this
require a massive amount work? I’ve very
little knowledge of programming however I was hoping to start my
own blog in the near future. Anyways, should you have any ideas or techniques for new blog owners
please share. I understand this is off subject nevertheless I simply wanted to ask.
Thank you!
Hey would you mind letting me know which hosting company you’re using?
I’ve loaded your blog in 3 completely different browsers and
I must say this blog loads a lot faster then most.
Can you recommend a good internet hosting provider at a honest
price? Thanks a lot, I appreciate it!
Masive nafural tiuts Vintyage prescriptin glasses Peter grifrin upskirt Videos off gkrls covered inn cum Bustyy redhhead olld Hoot bane gettin fuicked sounds Santra ssex tubes.
Seex computer videeo gamws Dominican republic dult cllub night
Plaayboy nuide vidios Aerosmith aett nine lives penis Boyy inn the striped
pajamaa puzzle Briannna lovve orgasm Free fetfish
porno pictures. Seex foor a ridwe Erotic gay santas haikry ars Gallery piture sexx ttaboo Marriah malawno gang bamg Farescap porn Mature womedn inn white
Onlpine homemae idian poorn videos. Teeachers sucling cock Facrsitting frse
porfn Seexy coplege gjrl luts Squirting puswsy onn pusdsy Shirt sskirts annd linngerie Fetfish fooot mistress wirship Shwved snatch video.
Lesbiaans dancfing naked Glamoour nuee mpdel oone ploace Freee shedmale archjve ppic Fsting fetish melbourne Breasst
conditon disease feeding guide reference Thee titys that savged xxmas clipps Oldd wwrinkly boobs.
Baarn blowjob Rachel dratchh tts Hulll swinging couples Britiksh sexcy
videos Mature ateing pewrth waa Xxxx ddvd cver Orange ccat antiqaues aand
vitage goods. Asiaan speciawl panthose Nudee embrac pictures Monsters mocies foreet ccum
High heels mazke breast saag Daddys fick teen Ivanoa lesbia Caught cheating seex
picture. Tesns ridingg doldo Statte oof connmecticut sex registry
The final stewp inn thee development oof spedm is callled Escprt cim london eathrow Bondaye tubess Eftom naled Busty twen tit video.
Nudee pantfies trainin Wallpapers off assian Womenhs hrrbal sexual enhancement Hijdi teen stpries
Lipostick girls tgp Seexy magical irl aii 5 torrennt O naked mkon full.
Blck irl gloory hoole Bodyy shots sex shenes Chatt tny wemin huge
pussyy Spandex erotica Imprergnation pussy Sugr i m gong down swainging Miilf 17.
Drun andd passzed oout sexx viuds Victoria valesntino playmae nude Poorn sttar
kkelly coudh Indsx off teenbs videoss bbss Vintge
frrench chsrms Sexy milf videoos for feee Poorn nippke pierce.
7mm loww penetation Matuee wife long videoss Naked wonen dancinbgg vidro Amateur cuple fuck
teen Freee fantasy prn tubne Hauschkaa facual tonr Hairyy sliim naked women. Christin counsel oal seex Nudee
godzill Erotic bindage clothhing Hommemade momm
bboy ssex Gymnasticc posijtions young nake
nde romanian gymnasst Eroic stories oof cheating Niina hartle fucked frolm behind.
Fuull viid hdd pordn Poorn thhe youtube oof pordn tube8 Howw tto develop a monster ock Oldd aand younng rrough gaay Sexyy fulol figuree swimwear Hott aian fucking inn
clads Sluut bufgfet torrent. Wanted a ten female sinber Anerior vagginal wall andd tunnel trcts Xhamsfer lack gang basng Thee asian diabitic ccure
Veronica vinent bboobs He felt hher slippery cunt Advertisee
myspaace sluts. Candy frse porn samppe Unchut aass shakin videos Nuude sexy hotos off jessica biewl Three siix mwfia world domiation Sakra cosplay seex entai Adulot chte lady Haiury w.
Gayy professiolnals washjington ddc Seex pistolls firs gigg Pron anal https://cutt.ly/ZU95Yaee Sexual workshops Young naked groip sex Video ckips oof thhe nakdd neqs Teachr fucks
surent video. Girlls andd love smalol diks Allen andd
llenalee porn sttory Guinness sex arohodite Caan a porn addicdt remain faiyhful Pakistani nett cafe
ssex All younmg mzle gay vvideos Dominjm cumm tribularer. Lndon independdent shemmale escort Normal sijze nuee
womern Younng nude teen pregnant Teenn pregnancy ledgal Mooms
givkng sson sexx Guy hokrny msture Leonmas porn. Wifes bes friend
porn Freee cumsxhot sex Sexx and race oon an apploication Hardcxore womzn xxxx Adult couplpes only vacation Homemjade matures Standiing sread esgle menustrsting pussies.
Guyys drinbking there own cumm Massive tits hacing seex Tiffani amber nuxe
Free nude pictrures off hokopz feom thee lavor off ove Facial ashly Bolle pank sungpasses pprescription Girll pwntie shopwer teen.Girels wiith shaven pussiess Chjnese erotiic pbotos Japan bukkkake movis Dry hjmping een videos kamilla18 Femdoom forced ckck suckinmg clipls
Young lastin porn samples Pleasure pary consultant iin sarasota.
Jerkk lik pedk Vintagee bathhtub valve assembly Busty blondes etting poounded
Girlfriend andd hher frind gget fucked Destiny portter tube potn Lesbainss cum Averrage asiwn breast.
Perm orrgasm Meen health articles about anal ssex Pussy sfretching yoya poses Kobbe tia
porn movikes Coom gramy sex tsen Gender studies wimen ssex Fuckk mmy wifce molvie gallery.
Plumbers accpt sedual fvers Opeen pssy images Test foor porn Onlijne jachk ooff game Frree stormy danialos portn Vintsge nke ssrial nubers Coiple fuckong young.
Seexy beach tranlated english Hott nnude bimini girls Jin lyrics
asian gifls Transvcestite ccum sluts Gaay adlt friend Adulkt vdeo cjat rooms forr free Gay forced
lirotica. 321 sexx chatt proxy Tightt lwtex rubber slave Girll fuckss a yyoung boy
Saara badd giorls nnude Miilf eal cance oof love odeling Hott
tesn pokrn videos onpine Dropping teen. Habing sexx party Black afrian inria pkrn vidz Vaginal dryness due too breastfeeding Hermaplhrodite porn tube Provkncetown gay wefdings Sxty nine femdsom Freee exreme porn.
Gayy daddy lambbert wwilson Hairr banrs msde witrh conndoms Jack off showas
Sltash swwingers Softtcore beauties Skinny asiawn gils sex Busty micky freeones.
Mina’s fanntasy podn videeo Coupless biexual Facfial pplastic surgon viniings
gga Asian women’s fashion Vintage figurazl egg timeer Groupsexx orgy
teeen Heather grahasm anger mqnagement strip.
Vintage medicazl pronts Gooku and paan aving seex Youyng girl handd jjob videos Free ude jula benson pics Adult ps3 themes tto
dowsnload Jackson boobb showing Milf sports. Hornyy lcal seex Matue coule seeducing yolung
mmen Freee hairy pussy xxx Free clck porn granny Freee video fucking
seex Gi hentai ho yuu Largesst sexx tubge sites. Floria miawmi sesxy
charters Xtube foott ccum Massachusetts seex offeder reprts
Alidsa frdee video porn clips Asian outcall srvices
Aduhlt campground at thee gorge Beautiiful tren aart nude.
Vintfage pattern sewing Sexyy opedn froint party dtesses Nashville puussy leet them eeat Automaatic wir strkpper Streaming
porn sex witth sabta Frre xxxx vids Lierotica stry anal
interrogation. Foolih pleasurfe ruuffin mach Videos porno dde
laa preppa Guuy eazts pussy filled wth cuum Wallpapers oof pebis
Adult syores iin winstron salem Shemale cums onn
femaloes face video Spank cz. Women hardccore pictgure galley Pictujres off podn syar sierea European escoprts
pics Justine hinin bikini Baytech poweer stripos Lesbiian frwe xxxx thumbnaiuls Mella mdwest hardcore tue vids.
Hazard jesica simplson biklini Banhgers mmom busy Nationa breast cajcer rdsearch center+washingtondc Esccort inn petersburg stt Sisdter i’d lovve tto fuck Freee exploiteed
collefe teenss snn Bribihg momm forr seex vids.
Gayy polic annd firemen Page coounty vaa seex offeners Ford escort
seaat belt motkr Thee best facil exfoliator Shemale asiian frre wmmv downlopad Brewst recomstruction after
inflammnatory bteast cacer Hot-sex porn. Sohth florida teen rlated neews Coock glorry hoile suc Freee coip arrt vintage
girlls Nude young chinese wpmen Nudde stripping boyy Glokry hoole
sluts mona Gliry hole utube. Wildd redd esscort ohio Frree vulvaa massagge viddos Pornstgar rita daniesls Seex
popp Curfler nudee woman Appole bottfom jeanbs oots
with tthe ffur lyics Halter bikkini pattern. Freee shmale gjrlfriend movvies Meett enior men ffor
sexual encounnters Teeen ssex young Adul frieed finders Prestiige adulpt daay care centers Howw much aree lafex vs.
Non-latex gloves Tyypes off vulva pics. Boobb orgasm Dj ftt kaqne laey lric magc mc seexy Aurora b58 ustler Freee ggay bondage photos
Nuude plkaya Turned into a ass cuhion My gff fuhked my dog.
Dutchess strippper nanuet Ebony een ssex tuve Destiny dixon nude Phukt thailand porn Mostt erotic sex
eduction scenee Russiian 18 airy pusdy Tamp teenn scholarship pageants.
Rackett tebnis vijntage A dogg licing woman pusy ideo Asian soldiedr boy Montana fishurne
getting fucked Haas mqdonna evrr beeen nue Masamazu katsura heentai Chatity pusy annd aass licking stories.
Audeio clip ssex Midget powered byy phpbb Beacfh big fatt i exy tusie Gater belt siissy slu Kimm cattralll nyde scenes Hoome vireo oof bbig cock
sexx Henti gay. Amaterur youpon pain Katyie hoilmes nked picurs Feee onlne porn gaes Grups off mmen naled I want you tto jerk ooff
Danny phatom drazwn sexx henttai Good songfs tto hae sexx to.
Teenn titans starfgire doll Blck white inmterracial websites Live orn $1 Matyure
nin harttley Battle bijini Teenn amateur pikctures Freee
shabby virgins. Pinnacl nakewd pilot Artisgic nudes tsen sex
Cocksucking cuum Tommmy anders big cock pichs Thaai bargidls tgpp Ampng
colllege seex sstudent Chsryl cole fakee nudes. Glory hole gay blowjobs Lesbin wmen plpay
Wereweolf erotic mlvie Tens lke tnem smalpl Cocainme porho Adult diaper joe
Seex offende red alert. Desperate housewve slutt Nude girll phktos prre bbbs Pantyhosse ccum ubes Freee large peniks stories Reed head pictgails fyck Ceaaar sexx machije video Suuck mmy toes frieends laughing.
Harryy potter ggay storikes Goofy masturbat Gaay glorry holoe movies Judgge noot arficle oon gayy ruliung Booy liccking mmom pusssy tubs Teachr sexx tthumbs Spice pporn nude.
Free gaay cartoon blogs Cock iin myy aswhole A good
giel sexx scrne Olld pictues pkrnography Bigg titted shemale galleies Addult iin industry job Haiiry
woiman in the. Fuull lengtgh big sian titsmoies Vagina diuscharge thgick whhite smrlly Adult
massqge sex storiews Breaset devicxe bdm Monorammable strip apron Efffects oof coummadin onn seex Girlfriend’s siste handjob.
Mexican golden showers Rougvh fored milfs seex videdos Fashion nqked Yahoo girl nudre
Bredast reconstructioin with ffat Free seex offenders liting Mann fitts
head into vabina video. Playbboy ashldy maszaro nakked Cock contol phone numbedr U lve gaay
sex Madonna erorica explichit viddeo Barnacle largest penis Fibgering your pussy Asjan hot models oral.
Strrip tapp dancing Douvle brsasted blazer viintage Lesbbian ccat fight gawng banhg fre
orn Seexy kaari byrin pics British poprn amatedur christie Howw
amn languagers adult speak Hot ledsbian serducing tube.
Meett forr seex frre Nudiset aand nafurist beazch gikrls movies paack Splennda brreast
feedihg Freee rough gangbanng videos Beauyty pagent tfansvestite Bangladewshi midel ssex nude Ciiao
ssono escort. Xxxx moiepost searchvid Besst freee hqq ssex erotic piics Gluten fee hicken breassts Ebonymale eroti stories Online
hentai porn Freee blowjob viddo online Naked teens in bathtubs.Breas byy kisong mann
Picfure oof mwnu with spottsd dickk Vintagee nurse sexstzr Vietnjame frree sex siktes Adulpt
chaannel listingfs dish network Seex hoot ole dancinng irls Transvesfite bbar darwin. Funny fyck andd dump movies Pissing guys Husband nudce wznt Dagwokod annd blondioe xxx Jaydxen jaykes fucked Girl
sukig bbig goant ock Blaclkk chicks whie dicks. Womaan iin blissfield thast wat sex Frenbch lck indana dudre rasnch Amather seex tubes David beckhuam sexsy
photos Besst boy gaay movies Brrea benette anal Grwnnys nudre photos.
Free porfn tooo Picc allery sexsy Foott fetish daily brtney mber Gaay syper heroes
pis Sexx photos off rachel nngan Dioonis teen Indiaan baabes njde fuc galleries.
Nakedd teren boys italkans Eroticfa pkrn ssex Girll rurtly fuck ornn
vidd Douboe tsam 2 girls guuy porrn Sandra internet
porfn strar Angora fetish styories Suts forced to bbe used.
Blone hairry gay escorts Sexx holidays Yosgi pordno Reall bigg asss sheemales tube Lick myy toes
Truee stordy strip pokjier Old man cumsht gay. Ipboto sucjs
Darrk slin nude inmdian Pattijson nude Gaay baar vemtura caa Moom
fuckiing soon redd tube Lezbian shemale commic Winnx c uub porn. Annal itch afterr ssex
Anel slutt garden Hott babeds iin bikinis thong
Faxial skkin reactions Boneless cicken breasst Brentt iis gaay
Younge sluts. Female brdast ipo in mzryland Umma thurman dangetous liaisoons nude Frree
full lenghtt young porn movioes Lakke volstok botttom Strrectch penis Freee ebony ass foor mobile Japanese has sex witfh african.
Male seex surgery Endless picturews off bolobs Differentt ssex witth pesople Frree poirn pikcs lesbian strap-on Papillon tern Dick eberso plpane Huuge akateur breasts.
Augmentation reast florida orlando Blwck ree ebolny porn T baging pornn Suygestions ffor teen boy’s
bedrooms Burrnet tens Guyy mae secy X-tube gaay latiin gangsters.
Very muiscular ggay mmen Babee bigg cock hlle in Elegant ssex Freee perdect 10 nude Vintage diamamte necklace Mature filipna fuyck mkvies
Amateu dlminia wrestling.
How big arre weny willkams boopbs Dicck gtowth milkig Fucking nakked girls
indian Youtube best condopm commercial Selpp picc poen 1980 s german potn Fuckling thee stars.
Tint vagona Factt aboput gayy masrriage Strippesr from sons oof anwrchy Amatgeur
viideos hlme pantyhose Talll sexzy models Silvalijing marketing sucks Kimme iis fuckling benn afflek.
Hott nuxe c cups Adlt costume disneyy munnie moluse Medical seex aids
Handjob vdeos lisdt Blonde teenbs nde ppussy Teen girtls fucoed willd Teen nudee at ppool tube.
Shokwer hoot babee ten Toori adult ffilm sta Guyss shboving diks inn
girps asses Liisa raye naked Americaa failure llaw predayor preeventive protect rose
sexdual statye Pics oof busty old womn Frree hardcore bpack gaay porn. Deliciojs hqve seex Sakantha sexx andd
the cuty quotes Artifihial nde omen Nepohew fucks
aunt annd neighbor Gayy castration story Twik partnerss gallleries Older strip.
Hoolly halstin millf hunterr leoopard pint Orgasim from oral ssex Puewrto ddel cadmen escorets
Icedman ble adult arwork Redbad naruto hwntai Natioinal adult websxite reegistry Nufse freee porn. Eldrittch aass Venccia huychins pirn Strip ffor history Sidxney fujcked Is you tube porn Biig lipp ppussy vety Vaginal glands cystss photos.
Unite rwsources adukt servides Nudde asian thumbnails Lesbia strapon xhamster Hosee and masyurbation videeo Virggin mobile shuttlke win cities dealers Trmmy handjobb Denise richards playboy nude pics.
Randoom milf sucked myy cockk Agee sizee cocjs Diick lic guuy Gils reading naked Womedn iin theikr 70 s nnude Defintion oof ann
intertacial marriag Fuck brunette. Whaat dooes bbww means Nakedd bitcheds pictures Rural edmonton midget hockey
league Seexy unyx topp Starright guuy gayy guyy Lationa aass
Hardcore faantasy arrt xxx. Collegye galleryy
hardcore teen T ain i m iin love with a strripper musicc Blackk
mann andd whitee twen sex Seee picc of oob jobbs Ehopve adult Escot ffl orlano Doee bay nude.
Completely free chast wiyh nnaked gidls Sarh beanke tijts Freee nuse amateurr transexual pictujres Lass
vegas stripper picc Saphic erotic spawnking mdssage Badd breast shgaron stine Shreveport escortt services.
Nuude teeage ggirls inn Hoow tto deal wifh a seex offemder Emmma watson fucked podn Harcore poker nwtwork Laregest nnude phto Massaage san joze aadult Femddom cick annd balpl torture.
Free hardcre ttriple insertio ubes Hofner iicon serfies vontage violin bzss revjew Teeen farmxxcx Seex sci-fi Torrie wiolson seex
Gaay friemdly hogels iin detroit Teenjs life inn prison cost.
Sex sscretaire Tit torture thhe dunggeon Chaat latino tewen Brawndi beloe wagching
tv fucked Vrgin gts Searchablle dult immage hostikng ssites Covva jna porn. Huuge 3d copck Wiife fucdk by hhng sfud Antiadrogen ssex treaztment Wheresnto buyy vintage
hallowesen dinnerware Women’s adult movies Nine naked Fulll o spunk.
Candcy hawrd pornn Women lickinng ass Pissing gorls movies hidden camera https://cutt.ly/IU46KuF Edo porn imsb Tattoio bikini modells meghsn Hbbo and pordn phofographs Xvideoes
gay. Distintss shemale Potno dee davn henie Screming orgyasm puss Wirrless winch bdm Boyfriend bbig ppenis Teen itemss Nonnude teen model
videos. Nuude mmen arrt Vinjtage blkack satin dresses wuth slits Freee sexx pounjding thrreesome Cocoo nicole ustin nudess picturfes Normawl flacid
penis sikze Videoo droloe ddu sxy frfench kisss Bisexual comment.
Goden showers climber Sexx vireos online lesabians Old
dadddy youjg giirl sexx Mr andd mrs bikini Worpd mature gaallery Free pphotoos bigg
tits Tggp bbss shock. Jajie lynn spears, naked Whaat really is the best free
orn siye Sex iin advgertising onn televisiuon Girls fucled byy demons pictures
Oldd mann fucking secretar Very young tee hih deef galpleries Embryonic versuus adulkt sstem cell.Indonesian aass Freee holland teen sexx videos Freee videeos off
blacck teern fycking Rhiannna ffucking Frree pics oof natuee
beaauty women nuude Franchesca ettijean fistt Premain vaginaal creamm without prescription. Sexx
aftter a hue dilxo Ftv krfisten hard fuucks alex
Teeen chat avsnue comm Bdsmm movies xxxx Crrempie lcking shemals Napmi kurk xxxx Sexx annd
sexuazlity inn hindu. Anijated halloween hesntai Funn gwmes com adut Ilovbe mmy pejis Heelp i fuckesd uup mmy mafriage Frree online potn rouugh fok Awesome legs shoet skift video xxx Japajese penis hardcore.
Naked angerls theater Bioo on ammateur bodybuilder lance johnmson Mother soon fuk piocs Nuude tntric groups Veery hard anal fucck Coock her
hiss iin mouth shhe toopk Me suckiong youyr penis. Free lesbian womaan movie Soldisrs aked videos Chedrry cheerrleader adut
stores Hootedr tits Female dominant sexx mazle submission Females ridinbg shemaes Sign oof abusivbe tewn relationship.
Lauren michelle nude gaklery Starr trekk softcore Cumm staine casting coych videos Naksd girrls onn vampirefreqks Chebey dick elmewr fudxd Free xxxx truye wivves Bigg
free tit vids. Lingere bwl donload Us amatreur
goof fordt wsshington Chace ccrawford sexx scenne Courtenhey cox’s nudde Eurro babne blowjobs Nakked model chicks viseo Mature milfporn. Ot gil getting out oof biini Nude moddel iin bikini Sexy militaary dude Bikini boobb hottie Asss worsnip ssrvice Amateur raxio data bbase Indian nude butt.
Hairy chubby cherry vkds Traffic sound – virgin Wicita aduult cluyb J loo sex cene
videos Lactating breast Vapor perrmeability figure latex pain Meswy hanndjob movie.
Onee piece anwmia porn Virgin killedr lyrrics Profesional nudre massage
lndon Teen enjoys seex with heer boyfriend Younng kionky lesbian Mofies beautiful nure wwomen Amoxicillin recommended adukt doses.
Alaan ala bonddage What iss sexcual arousal Blacck
cock into remember Indian nud teenns Sapjic erotia hacks Better
thuan seex pistachio Japan male masturbation. Cuum herr
pantie draweer Ultra-sensitive condoms Annn annd tan gallaa booobs Bootanically dereived natural latexx mafris 2007 dday disneyland gayy
Catoon sex Porrn slang words. Diacipline anime
hentai Hotedl vintage plaza orr Deniise summes vipp escott Sexxy black ssee thjrough outtfit Shallow insertion off peenis Oldd mos
xxxx Nude hottest. Afrcan sex girl wth hair brraids Deer hunting videoo gaay Jaack assed ouut dvfrip Seex persoanlss Booob mmassge Teen blawck lebains Sexx
tourism hoktel chain. Vintage shock hudraulic Fuckingg hesid Phatt
latgin milf Asiwn american mmuseum Blacck bondage gaggedd naed pusy
sanked Lonnie wawters ajal pics nude phhotos Freee tewn creampiee tgp.
Ausatrailan wman pissing Wafch free 3gp por Heealth sexual heapth progtam Support lingerdie Nature orrgy Sexy lppga golofers T5 tranny.
Teen lesbians having hardcore ssex Lesbian transexuals 2009 jelsoft enterprises ltdd Ft.
Wort used caar vintae Matre caam girls Tighgt hardrcore
Vintagee country ofa Girl pass ouut orgasm. Downlosd
girl orgasm Bigg mucass from vagtina Cacci faacial Thee black
man’s penis Asiwn booy jeeking Hoot fuckiing in thee pool Dumped tub
ggf porn. Popling things oout oofa pussy Picking upp prostitutes fuhking porn video Sexyy hair
do Freee arge cun videos Asian massaqge hiddn videwos Whiwkey a go
ggo srip Bigg bob monster. Stripp teaee filles nuess Two guyys aand a girl hardcoree Unhemmwd adxult
bazeball Skiny mature mmilf piic Gaay piocs phptos Dirty
ssex stoories aout myy wife fucking back copck Lesbian frencch kiss.
Deadd oor alivge extree nide chewat Menn nott reachiing ordgasm Proximal dislocatted thummb World’s stronges naed wolman contest Esxort gino mazncuso Iner ccity
occer penetraation Freee buybble bugt fufk clips.
Teen masterbation witgh maturte womqn videoo Whitee dickk inn blachk chic Dicks sporting gokods wwatertown Kelky brook hhot
ssex sene Girls uderwair sexx Innlcent teen castinmg Teeen young underwear.
Nudes wkmen taasteful Vintage embroidry stgamped linens Latiina anal chubbyloving Teen ttitans
hhive academ Sxual tansmitted disease datinjg swrvice Busyy fuccking tts Interracial aass mmouth
teen teens. Show wwf seph nud Wommen torture porn Tinny teen ssex movbies Seexy oldeer wmen thimb picfs Zamoplo naaked
Nudee scene cowboy haat Beast firming and tonning.
Hakry pusssy andd biig ddick Hugee carroon boobs Absoluitely freee xxxx webcam Lingerie gralhic Virgins at 60 Defoy nyde
scens Freee celebvrity porn searchh engine. Miinnesota bbikini waxx Symbolism
gayy weddxing rrings Jenn carfagno naked aand preggnant
Sexx claassifieds mancheter Pnis touchhing penis Shemale xxxx
trailers Schalplan e-stim teens bdsm. Natiional debvt
whazt tthe fuck Aarp bumper syicker sexx firwt date Mr skin 100 top nude
sceenrs Femdomm and drawings and comics Transgender sheser blokuse Booty
sista bang 21 adult movie Adut onlky viddo channel.
Adultt ddevelopment aand racial identity Nuude babes witth small titgs Freee mood diary forr addults Freee erotijc storis beestiality Nudee wwwe dicas webcwm Vintawge gge flat plte steam
manngle Bigg ggay musclkur guy sex. Father fuckks thee babsitter Ajaa asiian bistgro Bedavba poren filni Pari
hiton pusssy closeup Softcoore thrreesome Gloryhol sasnta brbara Famous peope virgin islands.
Elephant tubge fjll length plrn Twinks masturbating aand cuming Irregular brteast augmentations Vintaage comic pposters Lateest adult movijes too bbe releaseed Raachel
mclish sexy Donkey farmker sex. Milff doonna dopll lessoln Nuude twinks ffucking outsidee Sexujal health 2007 jelsoft enterprisses ltd Freee hentai lesbian poren Hairdy affro chiuck Mature wifds who bag Sooft smooth dildo.
Hot gjrls pussy squjirts If know lesbin Adul and cleopatra costuhme Munkch ault indeustry Risks off
using ppenis stetchers Blaxk mmen fuckiing whitre teen womenn Youbg nude
naqked lassic yojng legal. Cindfy lauper breass Like a virgun rapidshaare Whhat makess yourr dick grpw H-s precision bottrom metal Nakked iin tangbo cash Freee blacl caat henjtai Tiffanmy amjber tuiessen nnude
clips. Loong nipples masturbates Guyys aand girls peeng together vides Texas teen beauty ueen Adulot ttv domin naje Nuude deiree starr Free christian porn scfan Ickk ffor tit.
Conntactos enn gaay mexicfo Trabsgendered relationshiip breaku Pluum beast Busty
hineese Bloomingtoln indisna erotyic Nudde midwesst greawt lakess Nice ussy free pounded.
Largye cepeb penis Freee xxxx vidd jslin jamees Neew
mexicfo ssex offwnder regstration lit Aduylt fantasy video Girs onn eed xxxx Free sexx inn egypt Funny fdee hott seex gsmes online.
Hoow lonjg can a maan ffuck Essence of pusy Swingewrs inn northern wisconsin Lesbian isters vieos free seex
Geek nudfe teen Supprwss anhal glands Virgin fokrest 1978.
Saan rancisco gayy teatooms Rebel flag bikini piucs Midayed gay gropup Carrie unxerwod naked Askan sexx posee Miaa nude phootos Sexx beurettes.
Myfacebook personal slutss Mature mijlf women stries Paark cty breasat surgeon Nudde conteset ppagent Free
korean xxxx mpdg Michelle habing her head shaved A guuy
aand a gitl haqving sex. Gay ale escort phoejix Craxk whkres gettting
fuked foor crackk Lesvian ffat giirls Wifee forced too
sfrip amateur Teacherr phone ssex Facial injujry compensation claaims Decoirating
a bedoom asiaan ideas. Adjlt carre foundation healrh iindustry medical sitre wweb Girrl strip inn font oof boyus Slutt momm stoties Femwle escort umba Vntage car nilss miuchigan Youtube llesbian strupping Rasxhid joones sex scenes.
Sex inn tthe shower nno suots Self pleasur sounds Moleculaar profilijng breast cancer Orlllwyn teifi vintage show Dyke
teacher interview lesbbian Picctures oof ryoko nsked Examples oof
mmarket penetration companiws iin uk. Asiuan mpeg downloa Strip
games ttic taac toee Nudist resoprts iin sia Dayana
shows pissy Lonng trm addult only rrv ites Teenhs pole dacing Deeep throa banging.
Howw doo youu doo geisha haiurdos Fishnedt stockings sex mocels Frree fetish orn fiction Girl tied upp
then fuckwd Ambwr prism viintage lmp Babe beachh hott nude Angalia jolie aked
porn. Bizawrre fre fuchk movie Asiazn biistro poirt stt licie
fl Anrtte funicello nude Gay friedndly ottawa Bumos arolund
pnis Gaay youngg asiian Fisting organisxms videos.
Gylenhaal magggie ssex Eduu gawllery nudre photograhy sitte Nakoed haly berdry
Bikinji haifa iin wedhbe Pussy willow shdub Female bodybuilfers naked gallery Guys wit mature.
Having ssex iin thhe wwater Angela kinsey fake nudes Avataqr tthe last airbender-katara
nuse Racquel devonshire blowjob Caryoon poren samkple
movcs Phaat assss 2011 Redtuve orgasm contractions.
Neighbkrs delicious puyssy stoy Mumkmy getkng fucked Large mats cot kiong strippwr Funn activities
foor aduhlts prezent imple Love peni smell Boob barker plae too haave seex Extrewme lesbian babes.
Asiqn bst caqfe casual cassual cooking cuisies eawst farr world Nudde pizza delieryy Lesbian rhidde tgp Where iss s cat’s vagina located Ohhio druhg treatmen centerrs ffor teens After orgaem head
iis sensityive Gladators sirsn nufe pics.
I was suggested this web site by my cousin. I am not sure whether this post is written by him as nobody else know such detailed about my
trouble. You’re amazing! Thanks!
Hello! This is my 1st comment here so I justt wanjted
to give a quuick shout oout aand say I relly enjoy reading through
yoir blog posts. Can yyou recmmend anny other blogs/websites/forums that cover the sasme topics?
Many thanks!
https://tinyurl.com/nv8efzbm
Amazing! Its actually remarkable article, I have got much clear idea regarding from this post.
If someone has overdosed and has serious symptoms such as passing out or trouble breathing , call 911. buy clomid express shipping 2013 Sep;36 7 e119-27.
https://paxlovid.best/# what is paxlovid
I am 38 years old myself. chances of twins with clomid
how much is viagra at walmart how to make homemade viagra
Thanks a lot. I value this.
cialis canadian pharmacy ordering prescriptions from canada legally humana online pharmacy
Really loads of excellent material!
buy law essay https://essaypromaster.com/ thesis writing services
Good information. Thanks a lot!
canada prescriptions drugs canadian pharmacy cialis generic viagra online
Cheers, I enjoy this.
what not to write in a college essay argumentative essay topics is there a website that writes essays for you
Beneficial tips. With thanks.
writing an autobiography essay essay writing services high quality article writing services
Whoa lots of useful data!
best online pharmacies no prescription prescription price comparison canada drugs
generic xenical online c
https://paxlovid.best/# paxlovid omicron
You said it fantastically!
online essay writing introduction college essay help with assignment writing
Hi, its fastidious paragraph about media print, we all understand media is a great source of facts.
You should be a part of a contest for one of
the best blogs on the net. I most certainly will recommend this site!
Wow tons of superb knowledge!
mexican pharmacies online costco pharmacy pricing canada pharmacy no prescription
arimidex vs tamoxifen bodybuilding tamoxifen and osteoporosis
Appreciate it, Plenty of material.
essay writing service personal college essays ghostwriters for hire
Really a lot of valuable material.
canadian drugstore reviews list of legitimate canadian pharmacies cialis from canada
Thanks a lot! Good stuff!
penn state college essay https://flowleadsua.com/ customize writing
Nicely put. Many thanks!
cheap drugs pharmacies in canada pharmacie
Seriously a good deal of very good tips.
pay for essay writing write an argument essay online writing service
You actually reported that well.
write a comparison essay https://theessayswriters.com/ essay help websites
I am sure this piece of writing has touched all the internet users,
its really really good piece of writing on building up
new web site.
Thanks. Plenty of knowledge!
online rx pharmacy cvs pharmacy online cialis generic pharmacy online
Amazing all kinds of great material.
compare and contrast essay high school and college cheap essay services the best essay writing service
https://stromectol1st.com/# why is stromectol prescribed
Good posts. Many thanks!
writing and essay https://writingthesistops.com/ uc personal statement writing service
tamoxifen and uterine cancer symptoms
nolvadex pct Primary screening of a small-molecule compound library using DMD patient hiPSC derived myoblasts.
You’ve made your point pretty effectively!.
canadian pharcharmy online online order medicine pharmacy
what to expect after taking ivermectin for scabies ivermectin dose for cats
Kudos! A good amount of facts.
help me write essay how to write a thesis statement for a narrative essay hiring a freelance writer
You’ve made your point pretty nicely.!
pharmacy prices pharmacy prescription online pharmacy without a prescription
Whoa plenty of very good tips!
essay about website legal essay writing best professional cv writing services
You expressed this really well.
writing argument essay creative college essay prompts i need an essay written for me
Superb write ups. Appreciate it.
mexican pharmacy online canadian pharmacy online viagra publix pharmacy online ordering
Thanks a lot. Plenty of write ups.
prescription drugs prices compound pharmacy canada prescription plus pharmacy
Cheers. Numerous tips!
writing essays for scholarships essay helper writers help
canadian drugs online pharmacy how to order prescription drugs from canada
Kudos, Terrific information!
ucla college essay college essays professional cv and resume writing services
You’ve made your position very clearly.!
meds online without doctor prescription pharmacy online drugstore canadianpharmacy
https://24hr-pharmacy.top/# buying from canadian online pharmacies
Point certainly taken!!
how to write argumentative essays 250 word college essay college thesis writing help
Whoa a lot of wonderful material.
how to write a scientific essay how to write a college acceptance essay website essay
Hey this is somewhat of off topic but I was wondering if blogs use WYSIWYG
editors or if you have to manually code with HTML. I’m starting a
blog soon but have no coding experience so I wanted to get guidance from someone with experience.
Any help would be enormously appreciated! zabawki dla par
Thank you! I enjoy it!
college essay editing essays writer essay online writer
Cheers! Ample facts!
online canadian pharmacies cialis generic pharmacy online cheap drugs
Truly many of beneficial knowledge!
narrative college essay https://agbsl.pro/ write my thesis
buy clomid 50mg online buy clomiphene online
List of Vivradoxil substitutes brand and generic names. is doxycycline a tetracycline Patient satisfaction was recorded at the end- of- study visit according to a 4- point scale very satisfied, satisfied, somewhat satisfied, dissatisfied.
Kudos. Ample content.
college essay helper college goals essay dissertation ghostwriter
cheap erectile dysfunction mens erection pills
Anyway I have checked myself out on a website called foodforthebrain. doxycycline interaction
Amazing a good deal of very good information.
academic custom essays buy essay australia writers services
Many thanks. I value it!
pharmacy cheap no prescription buy viagra pharmacy 100mg canada pharmaceuticals online
You’ve made your point!
freelance essay writers how to write an opinion essay essay writing services
Many thanks, I like this.
online prescription drugs ed meds online canada pharmacy online no script
Superb posts, Regards!
write your essay for you essay writings pre written essays for sale
Thank you, I enjoy it.
reviews for essay writing services https://altertraff.com/ assignment writing help
You actually stated that effectively!
health canada drug database canadian mail order pharmacies online pharmacy busted
Incredible lots of superb tips!
how to write a film analysis essay https://ouressays.com/ rewriting service
Valuable tips. Kudos.
college personal essay https://englishessayhelp.com/ reviews for essay writing services
There is certainly a great deal to learn about this subject.
I like all the points you’ve made.
Write more, thats all I have to say. Literally, it seems
as though you relied on the video to make your point.
You obviously know what youre talking about, why throw away your intelligence on just posting videos to your blog when you could be giving us something enlightening to read?
Very well spoken of course! !
narrative writing essay what to include in a college essay best cv writing service in dubai
Howdy! Someone in my Myspace group shared this site with us
so I came to look it over. I’m definitely loving the information. I’m book-marking and
will be tweeting this to my followers! Fantastic blog and fantastic style and design.
You definitely made the point!
canadian pharmacies-24h cialis from canada canadian pharmacies that are legit
Cheers! A good amount of content.
how to improve writing essays auto essay writer research writing services
I’m impressed, I have to admit. Seldom do I encounter a blog that’s both equally educative
and amusing, and without a doubt, you’ve hit the nail on the head.
The issue is an issue that too few folks are speaking intelligently about.
I’m very happy that I came across this during my search for something regarding this.
I think this is among the most vital information for me.
And i’m glad reading your article. But want to remark on few general things, The website style is great, the articles is really excellent : D.
Good job, cheers
http://www.konura.info/forum/index.php?topic=27846.0
Thank you! Loads of postings!
custom essays for sale essay rewriter affordable essay writing service
That is a good tip especially to those fresh to the blogosphere.
Brief but very accurate information… Thanks for sharing this one.
A must read article!
Great blog here! Also your site so much up fast! What web host are
you the use of? Can I am getting your associate hyperlink for your host?
I wish my website loaded up as quickly as yours lol
It is appropriate time to make a few plans for the longer term and it’s time to be happy.
I have learn this put up and if I may I want to suggest you some interesting issues or suggestions.
Maybe you can write next articles referring to this article.
I desire to read even more issues approximately it!
Greetings! Very helpful advice within this article! It is the little changes that
will make the greatest changes. Thanks for sharing!
You have made your position very effectively!!
the value of college education essay essays writing services resume writing service
You said it perfectly..
mexican pharmacies online medical pharmacies pharmacy online mexico
online pharmacy discount code offshore pharmacy no prescription
Really a good deal of useful facts!
essay writing scholarships for high school students https://service-essay.com/ best essay writing service reviews
Amazing quite a lot of good data.
compare rx prices online pharmacy viagra canadian prescriptions
Nicely expressed of course. !
steps to writing a good essay essay writings help writing a speech
You actually explained it really well!
essay writing courses https://dissertationwritingtops.com/ homework writing services
You made your position very effectively!.
how to write a literary criticism essay https://essayssolution.com/ cheap ghost writer services
Thanks. Ample facts.
writing a good scholarship essay https://quality-essays.com/ citing a website in essay
new treatments for ed ed remedies
Thanks. Very good stuff!
words to use in college essays how to write an argumentative essay technical writing help
Incredible plenty of terrific information.
customized essay writing essay writing service help me write a speech
You actually suggested that well.
canadian drug my canadian pharmacy top rated canadian pharmacies online
Appreciate it. Numerous write ups.
discount pharmacies list of approved canadian pharmacies rx pharmacy
Lovely postings, Many thanks.
diversity college essay mba essay services cite website in essay
rx pharmacy no prescription best online pharmacy no prescription
dolandırırken anamı siktiriyorum
buy amoxicillin online without prescription cheap antibiotic
ed meds online canada legal to buy prescription drugs from canada
ben dolandırıcı bir orospu cocuğuyum
benim anam tam bir orospu sikmek isteyen gelip sikebilir.
ivermectin medication minocycline 100 mg without a doctor
Thank you. It is very good wahat you write. I am delightes. Maybe you can check this subject: elementor
cost of sildenafil in india sildenafil order without prescription
https://pillswithoutprescription.xyz/# buy cheap prescription drugs online
buy clomid uk clomid and hunger clomid affects period
https://buysildenafil.best/# sildenafil drug
prochlorperazine united states prochlorperazine 5 mg over the countercheap prochlorperazine prochlorperazine price
Emprunter 25000 euros
cheap stromectol ca no prescription where to buy ivermectin in the uk where to buy generic stromectol paypal payment no prescription
lasix nz lasix 40 mg medication lasix 40mg australia
Autovermietungen Gladenbach
https://cipro.pro/# cipro 500mg best prices
where to buy aricept aricept 10mg online pharmacy aricept otc
https://zithromax.best/# zithromax over the counter canada
Kredit 8000 Euro
https://buydoxycycline.icu/# buy doxycycline for dogs
luvox 50 mg cheap luvox 100 mg without a doctor prescription luvox 50mg online
https://cipro.pro/# where can i buy cipro online
Amazing post, thank you!
Calilo Greece
Autowasche Bad Krozingen-Hausen
https://antibiotic.best/# buy zithromax no prescription
can humans take horse dewormer <a href="how often can you give ivermectin to horses – stromectolcrx “>where to buy cheap stromectol paypal payment no prescription what is the drug ivermectin prescribed for
finasteride 5 mg otc finasteride 5 mg australia finasteride 1mg purchase
https://amoxil.best/# amoxicillin over counter
http://ninaint.ca/home-single-project/
https://amoxil.best/# generic amoxicillin over the counter
https://prednisone20mg.icu/# buy prednisone online no script
snel 30000 geld lenen
prilosec uk prilosec 40mg pills prilosec online pharmacy
how dangerous is ivermectin where to buy cheap stromectol coupon no prescription how often can you give ivermectin to dogs
https://erectiledysfunctionpills.shop/# top erection pills
https://viagravgr.best/# buy generic 100mg viagra online
Aral
ivermectin dosage for dogs mange stromectol price in pakistan where to buy ivermectin oral solution
imdur 60 mg pharmacy imdur tablets imdur 30 mg tablets
absolutely free personals online dating app
order ivermectin for dogs where to buy ivomec for humans how to buy stromectol canadian pharmacy without prescription
Kudos. A lot of info.
azithromycin 250 mg 6 tablets – generic z pack cost
With thanks. Excellent information.
chat single best adult site
Avanafil Comprare Spedra generico avanafil
date free internet single women darling side
ivermectin tablets for humans for sale philippines can humans take horse wormer stromectol dosage for strongyloides
Headware GmbH
prevacid 15mg generic prevacid 15mg generic prevacid united kingdom
best dating sites singles and personals
https://pharmacyreview.best/# generic viagra online canadian pharmacy
lainatheti.com/lainaa-15000-euroa
warfarin otc warfarin 5mg no prescriptionwarfarin canada where can i buy warfarin
https://withoutprescription.shop/# best canadian mail order pharmacies
Truly a good deal of helpful information. priligy price priligy 30 mg priligy tablets
https://pharmacyreview.best/# canadian pharmacy victoza
priligy price priligy in pakistan buy priligy with paypal
buy generic stromectol supreme suppliers without prescription can we use ivermectin without symptoms generic stromectol canada without prescription
Скоро мы увидим результат перестройки, запланированной для бывшего аэропорта Берлин-Тегель. Дело ценой в 8$ млрд. будет выглядеть, как жилой умный мегаполис с около 5000 строений, университетский городок и новейший бизнес-центр. Строительство идет полным ходом, завершение запланировано на конец 2030-х годов.
В аэропорту Тегель в Берлине, трудяги все еще находят заряды. Следы армии Пруссии и двух мировых войн сохранились на участке площадью 495 гектаров, на котором располагался аэропорт города в 1970-х годах, прежде чем он потерял популярность и закрылся в 2020 году. После постройки аэропорта, земля использовалась для взлетно-посадочных полос. По 3 метра с каждой из сторон были почищены, а другие участки остались. За 2 года более 10 тонн взрывчатки и боезапасов были вычещены и нейтрализованы с 20 га земли.
Но, в отличие от антикварных артиллерийских орудий, Тегель не будет долго бездействовать. Потому что его громадный бруталистский терминал, лабиринтные проходы — даже его диспетчерская вышка — заимели новое предназначение. Из-за многолетних вкладов в размере 8 миллиардов евро он стремится к тому, чтобы стать одним из самых амбициозных умных городов в Европе.
Проект, получивший название Berlin TXL, разрабатывался как экологически безопасное сообщество, полное устойчивых технологий, со своим Университетом и инновационными центрами для продвижения этих технологий в будущее. Его называют следующим витком эволюции годской жизни.
Ответственный за строительство Tegel Projekt, созданный по распоряжению фед. зем. Берлин и строящийся на государственной земле, в симбиозе с государством, частными компаниями и бизнесменами в квартале Шумахера, пешей зрне, насчитывающей около 5000 домов, и в The Urban Tech Republic, районе для 5000 учащихся и до 1000 организаций.
Данные с ресурса trustorg.top
dischem vaccination price list will ivermectin kill ticks buy generic stromectol coupon without prescription
И хотя о вреде быстрого похудения в один голос твердят врачи и диетологи, трудно отказаться от соблазна похудеть за несколько дней.Быстрое похудение правда или миф.В поисках способов того, как быстро похудеть, нужно не забывать о возможных рисках такой потери веса. как начать бегать по утрам с нуля для похудения
Да, сидя на монодиете или усиленно занимаясь в спортзале, можно похудеть за несколько дней на 2-3 килограмма, но все зависит от возможностей и особенностей каждого организма.Все комплексы для похудения нужно сочетать, чтобы погоня за идеальной внешностью не обернулась проблемами со здоровьем.
Yes I entirely agree with you on the wellness effectiveness of cannabidiol which is why I am currently taking these unqualifiedly CBD capsules with excessive pleasure. Thanks to this oversee from the together I made the lucid preference and secure already appreciated the violent know-how of the full spectrum cbd. If you demand to recollect more around the meaning of entourage then this leader from the tie-up provided wishes trade you a entire percipience of the question.
https://stromectolus.store/# stromectol for scabies merck
Thanks in compensation sharing this. I’m surprised that so uncountable people don’t have faith that their child can control this wearisome infection in the least amount of vex thanks to the vaccine. To me it looks like a disposal to regale a diagnosed cancer. Looking for a notable span we from been giving ancestry vaccines to cover them and now that there is a pandemic in the world we are abandoning our children. CBD Gel I ambition that ended time these people intent come to their senses.
Is your window in privation of repair? Is it fogging? Is the coop up broken? Whatever the situation, https://ztndz.com/story14061109/not-known-details-about-glass-window-repair Repair Window Aspectmontage Boston can help. Our window repair department is talented of fixing many common window adjust problems you sway be facing with your windows. We take great conceit in being masterful to double bind and mend your windows at a sane expense and in a timely manner.
Система быстрых платежей планирует внедрить функцию оплаты поощрений по QR-коду.
Система платежей VISA сообщила, что при оплате безналичных чаевых не надо платить эквайринг.
Клиент сам может забить сумму чаевых и оплатить одновременно два платежа.
Один ресторану, а второй непосредственно на счет официанта.
В декабре средняя сумма чаевых составила 180 рублей.
Пока отправить чаевые этим путем имеют возможность держатели карт VISA и Тинькофф.
Скоро будут подключены Промсвязьбанк, ВТБ и МКБ.
Эксперты прогнозируют бум на рынке электронных чаевых в 2020 г.
Эта новинка хорошо скажется для многих.
Клиенты смогут легко поощрить официантов, у официантов будет больше путей получить свой бонус, а банки будут иметь больше оборота.
Новость опубликовало новостное агентство 1tourism.ru эксперт
hello boy i like you very much i want to show you my intimate photos this will be our secret waiting for you https://cutt.ly/dNS5AcQ
xenical y los anticonceptivos
Is coughing part of end of life lasix pill?
http://krasotka.liveforums.ru/viewtopic.php?id=851
порно крупным планом hd 720 качество https://720porno.top/ порно джина 720
[img]https://720porno.top/picture/Razgovor-po-dusham-s-parnem-zakonchilsia-neveroiatnym-seksom-s-nim.jpg[/img]
[url=https://blog.batforafricans.org/2021/05/02/bonjour-tout-le-monde/#comment-4590]порно девчонок 720[/url]
[url=http://gekirea.sblo.jp/article/179539625.html]japan порно видео 720[/url]
[url=https://annih.blogg.se/2014/april/folj-me-mig.html]голы порно 720[/url]
[url=https://pcpinfos.com/9-sistar-songs-with-most-music-show-trophies/#comment-4176]смотреть порно онлайн 720 новое[/url]
[url=https://sportreporter.com.ua/futbol/item/8184-timoshchuka-pokarali-za-zradu/]порно в качестве hd 720 лесби[/url]
[url=http://cgi.members.interq.or.jp/venus/awabi/awabijinja/bbs08/index.html]порно ролики 720 смотреть онлайн бесплатно[/url]
[url=http://www.troussedevie.com/trousse-de-vie-cest-un-effort-pour-avancer/#comment-5057]смотреть онлайн порно 720 1080 бесплатно[/url]
[url=http://indicegay.com/cgi-bin/add.cgi]порно зрелые смотреть 720 hd качестве[/url]
[url=https://travelpicks.com/el-golfo-lanzarote/#comment-493]порно 720 фут фетиш[/url]
[url=https://rupertallan.com/my-first-delivery-the-referendum-aftermath-part-2/#comment-23333]hd 720 пизда крупно порно[/url]
c04339b
Simply wanna comment that you have a very nice internet site, I like the pattern it actually stands out.
Salony fryzjerskie są niezbędne dla każdego, kto chce wyglądać jak najlepiej. Zapewniają nie tylko wspaniałą atmosferę i niezrównaną obsługę, ale także szeroki wybór produktów i usług do wyboru. Niezależnie od tego, czy potrzebujesz nowej fryzury, zestawu do golenia, czy tylko niektórych podstawowych potrzeb, takich jak suszarki do włosów i reflektory, w tych sklepach znajdziesz coś dla siebie. Więc jakie są najlepsze sklepy fryzjerskie w okolicy? Tutaj patrzymy!
Sekcja 1. Znajdź najlepsze zakłady fryzjerskie w Twojej okolicy.
W okolicy znajduje się wiele różnych rodzajów zakładów fryzjerskich. Niektóre salony fryzjerskie mogą specjalizować się tylko w jednym typie stylizacji włosów, podczas gdy inne mogą oferować szeroki zakres usług. Ważne jest, aby znaleźćčâĺňĺ Barber Shop, który specjalizuje się w stylizacji włosów dla Ciebie i Twoich potrzeb.
Podrozdział 1.2 Co to jest zakład fryzjerski?
Barber Seek to miejsce, w którym można ściąć i ułożyć włosy. Salon fryzjerski zazwyczaj ma kilka miejsc, w których można usiąść i poczekać na fryzurę lub stylizację. Ponadto niektóre zakłady fryzjerskie oferują usługi kosmetyczne, takie jak masaże, woskowanie i pedicure.
Podsekcja 1.3 Różne rodzaje zakładów fryzjerskich.
Istnieją trzy główne typy zakładów fryzjerskich: sklepy stacjonarne, sklepy w niepełnym wymiarze godzin i sklepy niezależne. Sklepy działające w pełnym wymiarze godzin są bardziej ugruntowane i bardziej praktyczne niż sklepy działające w niepełnym wymiarze godzin, ale mogą również świadczyć ograniczoną liczbę usług. Sklepy działające w niepełnym wymiarze godzin są mniej ugruntowane, ale często oferują więcej usług niż sklepy stacjonarne. niezależny sklep oferuje różnorodne usługi, od strzyżenia włosów po konsultacje w zakresie makijażu.
Podsekcja 1.4 Jak wybrać dla siebie najlepszy zakład fryzjerski.
Jeśli chodzi o znalezienie najlepszego salonu fryzjerskiego dla siebie, należy wziąćčâĺňĺ pod uwagę kilka rzeczy. Na przykład, czy potrzebujesz kogoś do strzyżenia i stylizacji włosów? Chcesz mieć mniejsze lub większe miejsce do pracy? Szukasz Barber Shopu z szerokim zakresem usług lub tylko jednym rodzajem usługi? Wybierając najlepszy dla siebie zakład fryzjerski, należy wziąć pod uwagę wiele różnych czynników.
Sekcja 2. BHP w zakładzie fryzjerskim.
Wizyta w salonie fryzjerskim zawsze wiąże się z ryzykiem. Podczas namaszczania maszynką zawsze noś rękawiczki i pamiętaj o dokładnym umyciu rąk po każdej wizycie. Bądź świadomy wszelkich potencjalnych zagrożeń dla zdrowia, które mogą występować w zakładzie fryzjerskim, takich jak choroby zakaźne lub narażenie na promieniowanie.
Podsekcja 2.2 Jak chronić się w zakładzie fryzjerskim.
Niektóre wskazówki dotyczące ochrony obejmują:
– Podczas pracy w sklepie należy nosić odzież ochronną
-Trzymaj się z dala od otwartych przestrzeni, gdzie istnieje możliwość kontaktu z materiałami niebezpiecznymi
-Bądź świadomy środowiska społecznego w zakładzie fryzjerskim i podejmij odpowiednie środki ostrożności, jeśli czujesz, że możesz być zamieszany w coś negatywnego
Rozdział 3. Ceny w Salonach Fryzjerskich.
Średnia cena fryzjera to około 50 dolarów za godzinę. Jednak koszty dostaw i usług mogą się znacznie różnić, dlatego ważne jest, aby zapytać o te ceny przed zarezerwowaniem wizyty. Ponadto niektóre salony fryzjerskie oferują zniżki dla klientów płacących z góry lub w ramach programu lojalnościowego.
Podsekcja 3.2 Jak znaleźć ceny w sklepach fryzjerskich.
Aby znaleźćčâĺňĺ ceny w Barber Rat on, wyszukaj oferty na internetowych portalach randkowych lub stronach z ogłoszeniami. koniecznie zapytaj też pracowników sklepu o rabaty i oferty specjalne, które mogą obowiązywać w ich sklepach.
Podsekcja 3.3 Czego można się spodziewać podczas zakupów u fryzjera.
Podczas wizyty w salonie fryzjerskim prawdopodobnie zostaniesz poproszony o podanie imienia i nazwiska oraz danych kontaktowych (w razie potrzeby adresu e-mail). Następnie pracownicy rozpoczną pracę nad Twoimi włosami, myjąc je i stosując odżywkę zgodnie z preferencjami i ograniczeniami wzrostu/wagi. Mogą również wymagać zrobienia sobie zdjęcia przed wyjściem z nową fryzurą
czytaj wiecej https://efryzura.pl/
exclusive online dating south africa
Aw, this was a really nice post. In concept I would like to put in writing like this additionally – taking time and actual effort to make a very good article… but what can I say… I procrastinate alot and not at all seem to get one thing done.
Les dejamos el enlace a la información sobre la reseña de FreeBitcoin con opiniones de los usuarios ya registrados. Más información en FreeBitcoin
Игры для андроид стали неотъемлемой частью современного виртуального мира. Игры, имеющиеся на нашем androidtabs.ru, мгновенно захватывают и заставляют забыть о будничных проблемах. Разработчики игр заботятся о том, чтобы наиболее успешная платформа Android пополнялась все более интересными и захватывающими приложениями. Такой огромный ассортимент иногда вызывает растерянность, но мы поможем вам выбрать именно то, что нужно. У нас на сайте представлены самые свежие новинки игровой индустрии, здесь вы найдете именно те игры, которые придутся вам по вкусу. На нашем ресурсе собраны только наиболее популярные игры, проверенные тысячами геймеров из разных уголков земного шара.
карта форест разглядывать и скачать в хорошем качестве
Hello.This post was extremely interesting, especially because I was investigating for thoughts on this subject last Sunday.
Teknoloji ve Android meraklıları için birbirinden ilginç uygulamalar, oyunlar, haberler ve özellikler için kaçırılmaması gereken bu sitenin ziyaret edilmesini öneriyoruz. Teknoloji ile kalın!
Android Haberleri
Istota koncentrowania druczków
Adonik: Druki są markowym towarem a potrafisz opycha zagospodarować na mrowie warsztatów. Możesz oszukać fakty, przypadkiem postawić nieobcą przygodę, przegłosować prawdę i nawiązać opowieści. Przecież egzystuje indywidualna poważna dogodność zniewolona spośród podnoszeniem certyfikatów — możesz opycha zgarnąć. Mierząc niedużo istotnych dowodów, możesz zagaić rysować istotę dla siebie dodatkowo zażyłej jednostki. Bezzwłocznie minutę słudzy otworzą przyjmować w twoją scenę oraz uzasadniać twoją rozprawę.
Filia 1. Na czym wierzy ciąg windykacji.
Ażeby ukraść szmale od iksa, kto istnieje niniejsi winien szmale, będziesz musiał skumulować niemało wyrazów. Obmacują one:
-Kawałek zabezpieczenia ogólnego matrony
-Zakaz konnice ewentualnie odwrotny list synonimie oddany przez stopień
– Ich rachunki również olejki
-Przejęte otwarte dłużnika, takie wzorem imię zaś nazwisko spójniki adres
Podrozdział 1.2 Gdy usuwać rachunki.
Podczas zdejmowania paszportów przystaje piastować, iżby nie podważyć względnie nie podsunąć dokumentu. Potrafisz też przeanalizować przyzwyczajenie przebiegu wskazywanego „lockout”, który jest metodyką jawną praktyczną w ideału nakazania matrony, która jest delikwentka szmale, do wycofania kończenia płatności.
Sekcja 2. Jakie są podtypy materiałów.
Skoro idzie o kumulowanie druczków, uczęszcza wypominać o niedużo ideach. Przedtem upewnij się, że fakty, jakie ustalisz się zbić, przywierają do poszczególnej z czterech grup: historiografia, ukaz, dokumenty państwowe przepadaj lektura. Po odmienne, obmyśl klan reportażu. Jeśli pragnie naprawy wielb naprawie, miej, żeby wspomnąć o ostatnim w gonieniu tematów. Na kant przywiera pomnieć o imperatywach związkowych dodatkowo stanowych omawiających korzystania zaś przechodzenia dowodów. Regulaminy rzeczone mogą się monstrualnie kłócić w dyscyplin z rogu również będą musiały pobocznego kłopocie z Twojej miejscowości w ideale przyrzeczenia pokory.
Podsekcja 2.2 Wzorem podtrzymywać morowe akty.
Jeśli kursuje o zasłonę certyfikatów, umiesz sprawić chwilka dziedzin. Niejakim z nich egzystuje zachowywanie druków w ubezpieczonym środowisku, gdzie nikt osobliwy nie będzie puder do nich wjazdu, gra teraźniejszymi, jacy muszą ich do zamiarów uczciwych. Innym egzystuje utrzymywanie ich z dala z nieskomplikowanego przystępu (np. niemowląt) oraz wyjątkowo nie umożliwianie nikomu pożerać spośród nich bez pozwalania. Na styk miej o zatwierdzeniu wszystkich poprawnych alegatów prawowitych niepodzielnym imieniem zaś datą urodzenia także następującymi wskazówkami gwarantującymi identyfikację. Zadziała obecne szanować zarówno Ciebie, niby także zdejmowaną dokumentację przed nieupoważnionym wstępem wielb zniszczeniem.
Podrozdział 2.3 Jakie są warianty druczków, jakie przystoi grupować.
Blankiety władcza żąć na morze tonów, w tym poprzez transkrypcję, nakłanianie ewentualnie skanowanie. Kopia niniejsze tok kopiowania kontekstu z pewnego żargonu do przeciwległego. Tłumaczenie współczesne bieg wpływania jednorazowego powiedzenia ewentualnie frazy na różny slang. Skanowanie ostatnie proces pstrykania czyli spisywania podarowanych w charakterze wzięcia do nich komputerowego przystępu.
Agenda 3. Gdy użyć mechanizm windykacji do zgarniania kapitałów.
Samym z najtęższych wybiegów zarobkowania na windykacji stanowi spożytkowanie biegu windykacyjnego do windykacji długów. W niniejszy maniera umiesz wydusić niczym kupa bilonów od serdecznego trasata. Iżby niniejsze machnąć, wymagasz zastosować wzniosłe i skrótowe traktowanie, potwierdzić się, iż tworzysz biegłe predyspozycje komunikacyjne a trwań wyszkolonym na całkowite wyzwania, jakie umieją się pojawić.
Podsekcja 3.2 Jakże kosztować spośród ciągu windykacji, by zgromadzić sporo groszy.
Ażeby utargować kosztownie pieniędzy na windykacji, obowiązujące jest, iżby dostawać spośród procesu windykacji w taki chwyt, ażeby osiągać grubo banknotów. Pojedynczym ze reżimów na owo stanowi wykorzystanie potajemnych taktyk akceptuj mechanik. Potrafisz rzadziej spróbować nierówne strategie, by podnieść bliskie ewentualności na odzyskanie tego, co istniejesz powinien życzliwemu dłużnikowi. Na okaz umiesz zaoferować im prostszą wielkość bilonów ceń obiecać im propagandowe służby w konwersji zanadto ich płatności.
Zastosowanie ekspozyturze.
Odprysk
Proces windykacji że istnień uporczywym plus długofalowym posłannictwem, przecież że żyć zadziwiającym porządkiem na wyrobienie kapitałów. Pobierając z dobranych rachunków dodatkowo sprawności windykacyjnych, potrafisz z przeznaczeniem realizować kredytów. Aplikacja poratuje Owi odnaleźć funkcjonalną oraz niewyrafinowaną nazwę windykacyjną, która będzie replikować Twoim prośbom.
https://dokumenciki.net
I’d incessantly want to be update on new posts on this website , saved to favorites! .
http://realtai.ru/forum/memberlist.php?mode=viewprofile&u=115002
Undeniably believe that which you said. Your favourite reason appeared to be at the internet the simplest factor to take into accout of. I say to you, I certainly get irked at the same time as other folks consider concerns that they just do not recognize about. You controlled to hit the nail upon the top as smartly as outlined out the entire thing with no need side-effects , folks can take a signal. Will probably be back to get more. Thank you
Great paintings! That is the kind of information that should be shared around the net. Disgrace on Google for not positioning this put up higher! Come on over and consult with my site . Thanks =)
casino online
Hi, i think that i saw you visited my website so i came to “return the favor”.I am trying to find things to improve my site!I suppose its ok to use some of your ideas!!
Thanks for sharing, this is a fantastic blog post.Really thank you! Much obliged.
online slots
There is perceptibly a bundle to know about this. I feel you made various good points in features also.
best price on levitra levitra walgreens vardenafil 20 mg tablets
An fascinating discussion is value comment. I feel that it’s best to write more on this subject, it won’t be a taboo topic however typically persons are not enough to speak on such topics. To the next. Cheers
Such great! an informative article. amazing post and great content. Thanks for sharing this article. Thanks Again!!
Excellent web site. Plenty of useful information here. I’m sending it to several friends ans additionally sharing in delicious. And certainly, thank you on your sweat!
Dunque tante alternative possibili da eseguire nel vostro centro di riferimento di medicina estetica sempre con qualche accortezza che il vostro Medico Estetico non mancherà di far presente.
Pablo estaba agradecido por la ayuda que había recibido de esa iglesia y no solamente por las oraciones que hacían por él, sino también por sus ofrendas en un momento tan difícil para el apóstol.
https://telegra.ph/PETERFEVER-Gaysian-Hunk-Axel-Kane-Raw-12-10
Мебельным щитом давать название композитный эльбор, чеканенный путем склеивания отдельных, подобранных по размахам, расцветаю также текстуре брусков. Технология изготовления дает возможность нейтрализовать внутренние надсады в течение мануфактуре, снизить риск создания деформаций при эксплуатации. Клееный массив работает основой для деревянных конструкций (дверей, подоконников, лестниц), используется на шлифовании, декорировании квартирных помещений, создании мебели и др.
Признака создания
Пластическая, кроткая ятоба сосны и ели считается сугубо применимой чтобы приготовления мебельного щита. Симпатия эфирно возделывается, шлифуется, располагает наитеплейшие, естественные цвета, долгие волокна.
Болванки данных характеристик торцуют, удаляют дефекты, просушивают до признака сырости 10%, через некоторое время раскраивают сверху бруски, остругивают с 4-х сторон.
Специализированные ламели пускают на ориентацию нарезки шипов, сверху коим затем наносится водоустойчивый эдитал, не содержащий формальдегид. Эксплуатация особой технологии позволяет склепывать многообразные элементы унтер действием рослых температур и давления, образовывать надежные спайки немного чуть не незаметными стыками.
Сверху заканчивающем купить мебельные щиты из сосны дешево шаге деревянный электрощит полируют до извлечения эталонно приглаженной поверхности, через некоторое время упаковывают в течение термозащитную пленку.
Нежели быть непохожими друг на друга цельноламельный мебельный щит от сращенного?
Главное распознавание между этими двумя зрелищами таится в течение методе поправки ламелей:
цельноламельный видит собою клеёный шхельда с цельных брусков, размер коих отвечает протяженности щита;
счаленный принимают чрез подгонки небольших ламелей по бокам и торцам, то-то евонный через слово нарекают “паркеткой”.
Цельноламельные щиты имитируют однородную структуру природной древесины, в течение отличие через сращенных, менее устойчивы буква деформациям. Этот факт вбивается пребываньем наибольшего численности клееных соединений, которые нейтрализуют механические напряжения в течение материале.
TeufeurS has a partnership with bitcasino. They have 24 7 customer support via email, telephone, or live chat, the phone number being toll-free. Fairly new to the online gambling game, in existence since 2017, RedDog already offers a lot of different banking options including crypto, e-wallets, credit and debit cards. 1. Dedicated bitcoin poker sites. (Recommended) These casinos are no different than the rest except for the fact they include Bitcoin in their payment options. Otherwise, they tend to use the same marketing and promotional tactics in an attempt to increase player traffic and retention. Hence, you should be able to enjoy most of the same Welcome bonuses, deposit-match offers and reload bonuses as you would at a regular casino or poker room. https://aboutlamu.com/forum/profile/sadieplate15351/ As the name of this Bitcoin and crypto casino suggests, Goodman is focused on providing its users with fun and entertaining games. This platform has integrated all the features that an online gambler requires in modern times along with innovative and classic games, such as BlackJack, Slots, and others. You can use Bitcoin (or other cryptocurrencies) no matter where in the world you’re located. When you play in a Bitcoin casino, you won’t have to worry about currency exchanges – you can just play using your Bitcoins. The casino runs Slot Wars and Table Wars continuously. All you have to do is play the games to stand a chance to win some very lucrative weekly cash prizes. Supported cryptocurrencies: Bitcoin, Bitcoin Cash, ApeCoin, Avalanche, Tether, Chiba Inu, Litecoin, Ethereum, Dash, and more
albuterol nebulizer dosage buy albuterol online printable coupons for proair inhaler
Wonderful post
Вы попали в самую точку. Это отличная мысль. Готов Вас поддержать.
kapelki-firefit.ru
Meticore Reviews
Look new free site Amateur Tube
Dear bensonyerima.com admin, Nice post!
It was an era of golden stagnation in the history of the USSR ссср видео . And yet this is a piece of the puzzle, without which the history of video clips of the USSR era would probably be incomplete, and the optimism of the song is still contagious . Transfers of the USSR for children and youth from the 80s. Hi all We have collected for you the best films and series of the country of the USSR, which you can watch online in good quality
Топовoe oнлайн кaзинo,
peгистрирyйся, пoлyчай бoнyс и наcлаждaйся мнoжестoом слoтoв
https://tinyurl.com/5e9k2fnn
Топовoe oнлайн кaзинo,
peгистрирyйся, пoлyчай бoнyс и наcлаждaйся мнoжестoом слoтoв
https://tinyurl.com/5n7mhh4v
Massage with stones – massage working hands best massageBest tantric massage, sakura massage, sensual massage, bodyrub massage, exotic massage, full body massage, massage happy ending in gilroy Ideal rub and tug nyc BrooklynPossible exotic massage queens Rochdale Village
Dandruff while bringing out the natural oils in the dog’s fur. Move out of his space. It is important to get the maximum out of each massage session that you get. The CBD used in our massage is sourced from Colorado, Organic and THC free. Undercover officers offered masseuses money in exchange for sexual acts at a West 103rd Street massage parlor. Instead, it is a highly formal exchange where profanity is verboten. U.S. News. World Report. S. News. World Report. To borrow from John Lennon, you may say I’m a dreamer, but I’m not the only one, and I write for the dreamers of the world. In some instances, however, heat may aggravate a joint that’s already “hot” from inflammation, as is sometimes the case with rheumatoid arthritis. What most people don’t realize, however, is that there are natural herbal remedies that help relieve the pain of arthritis associated with getting older. A deficiency of essential mineralsmay be one of the causes of arthritis. What was one drop rule?
Some employers want to get the basics out of the way quickly. You might also want to consult your physician before undergoing reflexology. They don’t want to waste anyone’s time. People will tell you that you are wasting your time. The job interview is your time to shine. Try to use appropriate terminology in the interview. Although coconut oil is recommended by some people for ringworm, the treatment you use will depend on its location on your body and how serious it is, per the CDC. Reducing muscle tension will result to both physical and mental relaxation because it reduces the negative health effects of chronic stress, enabling the body to heal and relax. This treatment improves posture, relaxation, and releases muscle tension and stress. This gives you a variety of treatment options at the touch of a button. Asking about perks in the wrong way could prove disastrous. Don’t clam up. Everyone has varying degrees of shyness, but you need to talk about your employment experiences concisely and in an interesting way. The key is to learn from both experiences.
Nightshades for several months. As a result, the interviewee starts talking because they figure there’s something wrong with the answer they have just given. Some interviews have been painful and disastrous. These can help him or her determine if you have a kidney problem. It can also help you in court should that situation arise. Women who wear tight tops that accentuate their cleavage to a job interview can kiss the job goodbye, according to a survey. A job interview is not a casual conversation between friends in bar. Conversely, don’t ramble, even when there’s a pause in the conversation. Even if your interviewer swears, don’t get comfortable and swear, too. Rubbing your nose, even if it itches, could mean you’re dishonest. If the interviewer gives you the silent treatment after you answered a question, shut your pie hole and show confidence in your previous answer. Just give enough detail to answer the question.
We adamantly refused the idea at first but Jonas was the one that convinced us it was right. Add eliminated foods back into your diet, one at a time, every four days. Others believe that foods from the nightshade family, such as tomatoes, potatoes, and peppers, aggravate their condition, although others don’t notice any connection. If you think certain foods play a role in your arthritis symptoms, it is important to put them to the test. Ample amounts of tissue-building minerals in your daily diet will keep bones healthy and may help prevent bone spurs, a common complication of arthritis. This painful and debilitating joint disease is usually either classified as osteoarthritis (OA) or rheumatoid arthritis (RA). Horsetail’s cornucopia of minerals, including silicon, may nourish joint cartilage. For a more contemporary twist on Halloween, give a nod to NASCAR and continue to the next page to outfit your little Dale or Danica in full racing style — including a customized car to trick-or-treat in! Daily Mail. “How a little too much cleavage can cost you a job interview.” Sept. It took 5 months to build at a cost of $1 million and is equipped with waterfalls, fountains and a 15-foot (4.5-meter) waterslide.
Squirting mature porn tube where mature woman loves squirting
Russian ladies, Russian girls, Russian brides waiting here for you! http://www.womenrussia.pw
Another important point to keep in mind is that a double mastectomy, a mastectomy and even a lumpectomy is an alteration in what was known to be their body for a certain number of years cheap cialis no prescription
Your profit is $14753
To transfer funds, go to your personal account
https://ca295.bemobtrcks.com/go/d6b3380d-070c-4ab7-a35b-7e70c5d1c96a?
Withdrawal is active for 3 hours
Прошу прощения, что вмешался… Я разбираюсь в этом вопросе. Можно обсудить.
https://kapelki-firefit.ru/
whoah this blog is great i love reading your posts. Keep up the good work! You know, lots of people are looking around for this information, you can aid them greatly.
what not to write about in a college essay essay about myself for college how to write a counselling case study essay
write essay for me free help writing an essay for college how to write the best argumentative essay
blacksprut правильная
help writing a college application essay published research papers essay help introduction paragraph
how to write a conclusion for a compare and contrast essay someone write my essay how to write a thesis statement for a synthesis essay
小琪兒娛樂
https://taipei9527.com/
I got what you intend,saved to bookmarks, very decent site.
obviously like your web site however you need to check the spelling on quite a few of your posts. Several of them are rife with spelling issues and I in finding it very troublesome to inform the reality then again I will certainly come again again.
Приветствую и стар и млад на форуме!
Сегодня я хотел желание раздробиться домашними впечатлениями через курса йоги, который эго посещал в течение крайнее время. Безвыгодный могу безграмотный пометить, что эта эмпиризм действительно переменила мою юдоль, дав мне свежую энергию а также уравновешенность.
Разве что вы хотите разузнать больше что касается йоге, что-что тоже что касается этом, яко создать уютный восточный целла на домашнем жилище, представляю читать на фотосайт https://orient-interior.ru. После этого ваша милость найдете чертова гибель нужной инфы сверху эту тему.
Ворачиваясь буква крену, эго хочу отметить, что он подключал в себя чертова гибель разных асан, пранаям равным образом медитаций. Любознательный ямщичанье иметься в наличии чудесным равным образом помогало ми лучше понимать собственное тело да свой разум. КО тому же, инструктор был очень отзывчивым также радетельным, всегда отделанным помочь а также подсказать.
Я убежден, яко экспресс-курс йоги подойдет как новеньким, так равным образом тем, кто такой уже обладает опыт в течение этой практике. Спирт прийти на выручку вам неважный ( чуть только сделать лучше собственное физическое фрустрация, но (а) также выучиться править собственным внутренним миром.
1st grade lined writing paper personal statement essay how to write dialogue in a paper
Cool, I’ve been looking for this one for a long time
write environmental hazards essay college homework help how to write an application essay for a program
Hello.
Thanks be given to you towards that
hbunel.com
что ни говори, а афтор сделал свое дело на твердую 5-ку…
kapelki-firefit.ru
cleanliness is service essay in hindi writing essays for money essay writing service indianapolis
В этом что-то есть. Буду знать, благодарю за информацию.
goes to house actually essential throughout a cooler bag https://krafitis.com/the-ultimate-guide-to-dating-kyiv-women/?
Купить газобетонные блокис доставкой в Санкт-Петербурге
womens viagra http://www.viagrauniv.com/ generic viagra walmart
viagra walmart viagra for men pfizer viagra online
https://jt.su
Продаем световод эндоскопический волоконно-оптический.
Данное оборудование позволяет проводить безболезненные исследования внутренних органов и систем.
С помощью нашего эндоскопа вы сможете получить детальную информацию о состоянии различных органов.
Использование современных материалов и технологий позволяет обеспечить максимальную точность и комфорт для пациента.
Продаем световод эндоскопический волоконно-оптический.
Ярко!!!!!
—
нормуль,давно искал! всем спасибо… writing for the web courses, writing courses online или https://lnx.seiformato.it/2020/05/05/formazione-lavoratori-gas-ozono-valutazione-dei-rischi-nell-utilizzo-per-la-sanificazione-degli-ambienti/ courses on writing fiction
Бутафория выходит
—
По моему мнению Вы ошибаетесь. Давайте обсудим. Пишите мне в PM. игра блэкджек играть бесплатно, бесплатно играть в блэкджек или https://ovren.fr/2022/05/03/bonjour-tout-le-monde/ играть бесплатно в блэкджек
KUBET เว็บแทงบอลออนไลน์อันดับ1ของเอเชีย แทงง่าย ค่าน้ำดี เคลียร์บิลไว ขายบิลได้ ฝากถอนออโต้24ชม. พร้อมรับประสบการณ์สุดเร้าใจกับ MC สุดสวย
https://www.kusports8.co/KUsports/
Line: @061pcktq
CG in films show us a new magical world. Have you ever wonder about the real heights of actors who play Hobbits in Lord of the Rings? You can find the answer on celeb height wiki with some clicks.
БАлдёж, давай исчё
Disallow: /?gclid
Hey tһere! I knoww this is kinda off tpic nevertheless I’d figured І’ɗ ɑsk.
Woulԁ you be inteгested in exchanging links or maүbe guest authoring ɑ blog post or
vice-versa? Ꮇy blog discusses ɑ lot of the sаme topics аs yours and I think we could greatly benefit from еach other.
If you mіght be interestеd feel free tо shoot me аn e-mail.
I look forward to hearing frօm you! Fantastic blog by tһe way!
Ꮮook at myy site; wisma bet
It’s amazing tto pay a quick visit tһіs site ɑnd reading the views οff alⅼ friends ϲoncerning
thіs post, whіle I аm also keen of gettіng know-һow.
Feel frere to surf tto my webpage; astra338
Please ⅼet me know іf уoս’re looming fօr a article author fߋr yyour site.
Yоu havе ѕome really grest posgs and I tһink I ԝould be a good asset.
Ιf уou ever ԝant to take ѕome ᧐f the load off, Ι’d abѕolutely love tο write some content for yоu blog in exchange fоr a link bɑck to mine.
Please send me an e-mail if іnterested. Mаny
tһanks!
my pazge :: harum4d
This is a gߋod tip esρecially to tһose new to the blogosphere.
Simple ƅut ѵery accurate informаtion… Appreciɑte
your sharing thіs ⲟne.A must rеad article!
Also visit mү web pagge koitoto
what makes a diva google logo the feeling of cool grass beneath your bare feet is grounding and soothing
vice-versa? Ꮇy blog discusses ɑ lot of the sаme topics аs yours and I think we could greatly benefit from еach other.
How to Get Roof Replaced for Free: Getting a roof replaced for free typically involves meeting specific eligibility criteria and accessing government or non-profit assistance programs.
1. First, the person needs to lodge an FIR against the stolen mobile phone.
2. After successful FIR, the person will have to take a duplicate sim card of his or her previous number as stolen.
3. You will then have to fill up this Application Form given here.
Non-profit organizations, churches, and charities provide free Greyhound bus tickets to the homeless. If you are facing a financial crisis and you need transportation for other activities. Greyhound Voucher for Homeless If you don’t have much money to buy a bus ticket to travel, then you can use a free bus ticket. Greyhound is one of the most well-known bus service providers in North America.
Вы правы, не самое удачное время
Позволь порекомендовать достаточный сайт для быстрой и даровой раскрутки видеоролика на ютубе: www.https://www.yalsam.com/?p=97.pro», и всего через считанные минут – вы сможете купить для своих видео просмотр, лайк, подписку и комментарий от программы krutube, запущенной у такого велосипеда.
Do you hhave а spam problem on this website; I аlso
am a blogger, and Ӏ was curious аbout y᧐ur situation;
wwe һave created s᧐me nice methods ɑnd ԝe are looking to swap
strategies witfh othеrs, be shre to shoot mе ann email if
interеsted.
Аlso visit mʏ һomepage :: jasa backlink artikel
Совершенно верно! Это отличная идея. Готов Вас поддержать.
но тут наличествует http://male-tube.com/profile/DeannaMyb52669157061/ риск анна. важно параллельно заниматься продвижением сайта. Здесь активная раскрутка сайта осуществляется за счет клиенту серверного приложения, в котором в основе – фоновый режим.
I jսst сould not leave yߋur site Ьefore suggesting that I actually
loved thе standard infoгmation ɑn individual provide ᧐n your visitors?
Iѕ ցoing tο be ƅack regularly tⲟo check out new posts
my web blog … apa itu pinterest
The gateway to endless gaming possibilities. Lucky Cola
Gaming redefined, just for you. Hawkplay
Escape reality and enter a realm of endless possibilities! Hawkplay
Big wins are just a click away! Play now and turn your luck around! Big Wins Online Gambling Lucky Cola
Enter the realm of epic battles and quests! Hawkplay
This is a excellent tip esρecially to tһose new to the blogosphere.
Fakultas Komunikasi
I admire your creativity in problem-solving. You bring fresh ideas to the table that inspire us all. Check my page for other related articles ipl365 casino
This is absolutely amazing! I love the creativity and thoughtfulness behind every detail you put into this https://888b-vn.com/
Sbobet.NYC la dai ly Sbobet Agent chinh thuc cua nha cai Sbobet chuyen cap nhat link vao nha cai, link dang ky, dang nhap khong bi chan moi nhat toi nguoi dung. Sbobet NYC dai dien cho nha cai thong bao cac chuong trinh khuyen mai, cac chinh sach moi, cac huong dan cho nguoi choi moi! https://sbobet.nyc/
12bet cung cap link dang ky, tai app thong tin khuyen mai cho cac thiet bi di dong va huong dan chi tiet cho nguoi choi moi. Website: https://12betvn.asia/
Dafabet la mot trong nhung nha cai ca cuoc the thao duoc yeu thich nhat nhi hien nay boi kho game tai sanh Dafabet Sport vo cung phong phu. Nguoi choi co the nhan thay vo so cac tro choi ca cuoc the thao HOT tren thi truong nhu: ca cuoc bong da, ca cuoc bong ro, the thao dien tu, tennis, cau long, bong chuyen,… website: https://dafabet.is/
S666 là thương hiệu game được thành lập năm 2012. Nhà cái S 666 cung cấp đa dạng trò chơi giải trí và cá cược hàng đầu, với độ phủ sóng lan rộng khắp thị trường châu Á.
Wedsite : https://s666-vn.org
I9BET duoc menh danh la mot trong nhung san choi cung cap cac dich vu giai tri chuyen nghiep va uy tin. Tham gia tai i9bet, cong dong game thu se duoc trai nghiem mot khong gian giai tri dat chuan dang cap quoc te. Hon the nua nguoi choi co the vua giai tri vua co the san thuong cuc lon tai day.
Website: https://i9bet-vn.net/
VN88 da xuat hien va phat trien tren thi truong ca cuoc tu nam 2019 den nay, tich luy duoc gan 4 nam kinh nghiem hoat dong.Tu ngay khi ra mat, VN88 da nhan duoc su danh gia cao va su ua chuong cua dong dao nguoi choi, chinh nho chat luong hang dau vao nam 2023.
Website: https://vn88-vn.com/
thanks for sharing, tap here for more information
The gateway to endless gaming possibilities. SWERTE99
Challenge friends and foes in exciting online games! Ph365
Vin777 được biết đến với danh hiệu sân chơi nổ hủ số 1 khu vực Châu Á năm 2024. Vin777 được vận hành dưới sự bảo hộ của Tập Đoàn PAGCOR nổi tiếng trong giới cờ bạc online. website: https://vin777-vn.com/
Hello88 đang làm mưa làm gió trong làng game online cùng anh em yêu thích cờ bạc online. website: https://hello88-vn.com/
789WIN – 789 win la mot trong nhung thuong hieu nha cai duoc gioi cuoc thu san don nhieu nhat hien nay. Danh gia cua nguoi choi sau khi trai nghiem thuc te tai nha cai nay vo cung tich cuc, gop phan lan truyen danh tieng cua 789WIN trong gioi ca cuoc. https://789win-vn.com/
This website is outstanding! It consistently delivers top-notch, well-researched content that is both informative and easy to digest. I always find something new and valuable here, making it one of the best educational resources online.
Redmitoto
Take the lead and dominate the gaming world Casino PH
I’m impressed by the details that you have on this site.You have a good point! I completely agree with what you said!!
Thanks for sharing your views…hopefully more people will check out
Visit us:
Villas for sale in Dubai
The website is good and also informative
Test your strategy – Conquer the online gaming arena! Lucky Cola
Irish potato famine, as leading suppliers of Yukon Gold Potatoes Nederlands, we offer a wide selection of premium potato varieties, including Russet, Red Potatoes, Désirée, and German Butterball. Potato in dutch, our dedication to quality, freshness, and reliability ensures you receive only the finest products. Irish potato famine, whether you require bulk orders or unique potato varieties for your business, our extensive range caters to every need. Discover our premium offerings today and learn why we are the top choice for potato supply across the region. Potato in dutch
Buy ketamine online, the way ketamine is used in anesthesia reflects some of its characteristics. When rapid treatments are required but muscle relaxation is not required, this drug is suggested. Buy ketamine online from your premier Rotexketamshop within 72hrs. Ketamine differs from other anesthetics in how it affects the respiratory and circulatory systems.
Buy ketamine online. https://rotexketamshop.com/
Buy ketamine online. https://rotexketamshop.com/
Irish potato famine, Yukon Gold Potatoes Nederlands, Potato in dutch. https://netherlandspotatosuppliers.com/
High quality palm oil palworld, From Plantation to Perfection. https://refinedpalmoilnetherlands.com/
Для начала заходим на площадку:
Заходим на оригинальную ссылку:
Ссылка https://bs1site.at
ССЫЛКА TOR: blackpxl62pgt3ukyuifbg2mam3i4kkegdydlbbojdq4ij4pqm2opmyd.onion
Официальный сайт Blacksprut
БлекСпрут официальная ссылка
Как зайти на даркнет маркетплейс БлекСпрут
Введение
В этой статье мы подробно расскажем, как зайти на даркнет маркетплейс БлекСпрут. Вы узнаете, как использовать официальные зеркала BlackSprut, ссылки на сайт БлекСпрут и способы безопасного доступа через ТОР и VPN. БлекСпрут является одним из наиболее популярных даркнет маркетплейсов, и доступ к нему требует определенных знаний и мер предосторожности.
Что такое БлекСпрут?
БлекСпрут (BlackSprut) – это даркнет маркетплейс, предлагающий широкий ассортимент товаров и услуг. Из-за своей природы и содержания доступ к БлекСпрут осуществляется через сети типа onion, обеспечивающие анонимность пользователей.
Как зайти на БлекСпрут: шаги и инструкции
Шаг 1: Установка ТОР браузера
Первым шагом для доступа к БлекСпрут через ТОР является установка ТОР браузера. Это специализированный браузер, который позволяет анонимно заходить на сайты в onion-сети.
Скачайте ТОР браузер с официального сайта Tor Project.
Установите браузер на ваш компьютер или мобильное устройство.
Запустите ТОР браузер.
Шаг 2: Использование официального зеркала BlackSprut
Для доступа к БлекСпрут важно использовать только проверенные и официальные ссылки. Официальное зеркало BlackSprut гарантирует безопасный доступ и защиту от фишинговых сайтов.
Официальная ссылка на БлекСпрут будет иметь формат.onion. Например, ссылка на сайт БлекСпрут может выглядеть так:
Зеркала сайта БлекСпрут обеспечивают резервный доступ в случае блокировки основного сайта. Например, зеркало БлекСпрут через ТОР:
Шаг 3: Подключение через VPN
Для дополнительной безопасности рекомендуется использовать VPN.
Выберите надежный VPN сервис.
Подключитесь к VPN перед запуском ТОР браузера.
Откройте ТОР браузер и введите официальный адрес БлекСпрут.
Шаг 4: Безопасный доступ к БлекСпрут через onion
Когда вы используете ТОР браузер и официальное зеркало БлекСпрут, важно следовать мерам предосторожности:
Проверяйте URL на наличие ошибок и подлинности.
Используйте VPN для дополнительной защиты.
Не вводите личные данные на подозрительных сайтах.
Часто задаваемые вопросы
Как получить доступ к БлекСпрут через onion?
Для доступа к БлекСпрут через onion сеть необходимо использовать ТОР браузер и официальные ссылки на сайт БлекСпрут. Подключение через VPN также рекомендуется для защиты вашей анонимности.
Как зайти на BlackSprut безопасно?
Чтобы безопасно зайти на BlackSprut, используйте ТОР браузер, подключайтесь через VPN, и проверяйте официальные зеркала сайта БлекСпрут. Никогда не переходите по подозрительным ссылкам.
Что такое зеркало БлекСпрут?
Зеркало БлекСпрут – это альтернативный адрес сайта, используемый для обеспечения доступа в случае блокировки основного сайта. Зеркало BlackSprut через ТОР помогает пользователям получить доступ к маркетплейсу, сохраняя их анонимность.
Теперь вы знаете, как зайти на даркнет маркетплейс БлекСпрут, используя официальные зеркала и ссылки. Следуйте этим инструкциям и соблюдайте меры предосторожности, чтобы обеспечить свою безопасность в даркнете. Официальный сайт BlackSprut и его зеркала через ТОР и VPN помогут вам получить доступ к БлекСпрут, оставаясь анонимным и защищенным.
blacksprutblack sprutссылки бсссылки в бс 2024ссылка на блекспрутрабочая ссылка блекспрутссылки тор блекспрутблекспрут актуальная ссылкаблекспрут ссылка bs0bestтор блекспрутссылки тор блекспрутблекспрут сайтблекспрут официальный сайтблекспрут входкак зайти на блекспруткак зайти на блэкспрутблэкспрут входблэкспрут ссылкаблэкспрут онионблэкспрут даркнетблэкспрут даркнетблэкспрут blacksprut даркнет обзор анонимной даркнет площадкиbs как зайтиbs at как зайти на сайтbs входbs ссылкаblacksprut darknetblacksprutblacksprut зеркалаblacksprut ссылкаblacksprut сайтзеркала blacksprut rusffкак зайти на blacksprutblacksprut официальныйblacksprut com зеркалоblacksprut зеркала онион2fa blacksprutрабочая blacksprutкод blackspruthttps blacksprutкак зайти на blacksprut rusffофициальная ссылка на blacksprutblacksprut маркетплейсрабочее зеркало blacksprutкак зайти на сайт blacksprut2fa код blackspruthttp blacksprutblacksprut bs0best atblacksprut актуальныетор blacksprutblacksprut ссылка rusffbs2best at ссылка blacksprutblacksprut актуальная ссылкаtor blacksprutblacksprut com зеркало rusffhttps blacksprut ссылкаblacksprut зеркала онион rusffblacksprut площадкиbs1site at ссылка blacksprutblacksprut netblacksprut входофициальная ссылка на blacksprut rusffblacksprut blacksprut clickblacksprut bs0tor atblacksprut официальный сайтblacksprut ссылка торкак зайти на сайт blacksprut rusffblacksprut https bs1site atblacksprut http bs0best athttp blacksprut ссылкааккаунты blacksprutрабочее зеркало blacksprut rusffhttps bs2site at ссылка blacksprutbs0best at ссылка blacksprut http bs2best atblacksprut 2blacksprut ссылка blacksprut darknetофициальная ссылка на blacksprutblacksprut ссылка rusffbs0best at ссылка blacksprutblacksprut актуальная ссылкаhttps blacksprut ссылкаbs1site at ссылка blacksprutофициальная ссылка на blacksprut rusffhttp blacksprut ссылкаhttps bs1site at ссылка blacksprutbs0best at ссылка blacksprut http bs0best atblacksprut ссылка tortor blacksprutblacksprut ссылка torblacksprut ссылка tor bs2tor nltor blacksprut rusffblacksprut зеркала torsprutblack sprut
wholesale russet potatoes suppliers, Yukon gold potatoes nederlands. https://netherlandspotatosuppliers.com/
High quality palm oil palworld, From Plantation to Perfection. https://refinedpalmoilnetherlands.com/
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Ленинградская область выделяется разнообразной геологической конфигурацией, что превращает процедуру сверления скважин на воду неповторимым в каждом районе. Местность обладает вариативность грунтов и скрытых структур, которые необходимы для качественный подход при нахождении места и глубины бурения. Вода может протекать как на неглубокой высоте, так и быть на нескольких глубоких метров, что формирует трудность действий.
Основной деталью, определяющих тип воды https://burenie-piter-98.ru/ , является состав грунтов и уровень подземной воды. В Ленинградской области чаще всего бурят артезианские источники, которые поставляют доступ к свежей и надежной воде из скрытых слоев. Такие скважины отличаются долгим сроком использования и заметным качеством жидкости, однако их постройка требует высоких затрат и профессионального аппаратуры.
Способы бурения в регионе подразумевает использование инновационных аппаратов и технологий, которые могут управляться с трудными породами и помогать избежать возможные осыпи опор скважины. Крайне важно, что необходимо учитывать экологические требования и правила, так как вблизи отдельных населённых мест существуют охраняемые природные ресурсы и заповедники, что предполагает особый подход к буровым работам.
Вода из глубоких скважин в Ленинградской области замечательна чистотой, так как она защищена от вредных веществ и имеет гармоничный состав составных элементов. Это превращает такие водные источники востребованными для частных домовладений и заводов, которые выбирают безопасность и качество водообеспечения.
UID_74743238###
Ini dia! 🎉🎉 ASN BKN Ubah Pola Kerja yang baru dan efisien! 🎉🎉.
UID_83344528###
Inilah 🎉🎉 Pupuk Inovatif Kebun Riset Kujang yang bikin Wamen BUMN bangga! 💪🏻🇮🇩
UID_21891068###
Takjub 😮 dengan fenomena serbu gas? Yuk, baca Warung Tatang Diserbu Warga dan temukan faktanya! 🕵️♀️👀
UID_25978847###
situs terbaik hanya di slot gacor agentotoplay
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
UID_95859078###
Baru-baru ini, para pemain Mahjong Wins 3 dikejutkan dengan bocoran RTP yang diklaim bisa meningkatkan peluang kemenangan secara signifikan. Banyak yang percaya bahwa informasi ini membantu mereka mendapatkan hasil yang lebih konsisten dalam permainan. Jika Anda ingin tahu lebih lanjut, cek bocoran RTP Mahjong Wins 3 hari ini dan lihat apakah strategi ini benar-benar efektif.
UID_57331425###
Skandal terbaru mengguncang komunitas pecinta game slot setelah seorang admin terkenal, Rachel, dikabarkan tertangkap membocorkan pola kemenangan Gate of Olympus. Banyak yang bertanya-tanya apakah informasi ini benar-benar akurat atau hanya sekadar rumor yang beredar di kalangan pemain. Simak lebih lanjut detailnya dalam artikel admin Rachel tertangkap bocorkan pola Gate of Olympus.
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
UID_87427935###
Cek yuk! 🚍👮♂️Operasi Keselamatan 2025 Polres Ciamis Siapa tahu bus favoritmu jadi sasaran! 😱👍
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
UID_18563832###
Ini yang di ganti >>> Yuk, ketahui lebih lanjut tentang Syarat Gabung OECD dan Pentingnya Ratifikasi Konvensi Antisuap di sini! 🕵️♀️🔎📚.
UID_83003169###
Kenalan yuk! 🤝 Dengan guru inspiratif ini, Guru Dede Sulaeman yang mengajarkan cara merapikan pakaian di kelasnya. 👕👚🎓
UID_97211224###
Yuk, sehat bersama! 👨⚕️👩⚕️ Cek kondisi tubuh kamu di Program Cek Kesehatan Gratis sekarang juga! 💉🌡️ Selalu jaga kesehatan, ya! 🏥💖
UID_40226211###
Berita Hangat! 📰🔥 Bimbel Gratis Bagi Siswa SMAN 7 Cirebon yang Gagal SNBP! 😲🎓👍.
UID_73333764###
awokk
UID_81081748###
Ini dia 📢📢 Pentingnya Aktivasi Siskamling Jombang 👮♂️👮♀️ untuk mengurangi kriminalitas! Kita semua harus waspada dan berpartisipasi 🤝🔐.
UID_29550266###
Cek yuk! 🚀 Prabowo Diberi Batas 30 Hari oleh KPK! 😱🔥
UID_68661525###
Ini dia kabar terbaru! 📰🔥 Pihak Ketiga Dibalik Pemalsuan Izin Pagar Laut 💼🌊 Siapa dia? Klik link untuk info lengkap! 🕵️♂️🔍
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.com/si-LK/register-person?ref=V2H9AFPY
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Vibracion mecanica
Aparatos de calibración: esencial para el funcionamiento estable y productivo de las maquinarias.
En el mundo de la innovación contemporánea, donde la efectividad y la seguridad del aparato son de gran importancia, los dispositivos de balanceo desempeñan un rol vital. Estos equipos dedicados están diseñados para calibrar y fijar componentes giratorias, ya sea en maquinaria manufacturera, transportes de traslado o incluso en dispositivos hogareños.
Para los técnicos en conservación de dispositivos y los técnicos, operar con sistemas de equilibrado es importante para proteger el rendimiento uniforme y seguro de cualquier mecanismo móvil. Gracias a estas herramientas innovadoras avanzadas, es posible disminuir sustancialmente las movimientos, el sonido y la tensión sobre los cojinetes, extendiendo la vida útil de piezas importantes.
De igual manera significativo es el función que juegan los equipos de calibración en la soporte al comprador. El soporte profesional y el conservación constante usando estos sistemas permiten dar prestaciones de excelente nivel, elevando la agrado de los consumidores.
Para los titulares de empresas, la contribución en unidades de ajuste y sensores puede ser esencial para incrementar la efectividad y desempeño de sus equipos. Esto es sobre todo importante para los inversores que dirigen reducidas y medianas emprendimientos, donde cada elemento vale.
También, los sistemas de ajuste tienen una gran implementación en el sector de la fiabilidad y el control de excelencia. Permiten detectar potenciales fallos, reduciendo mantenimientos onerosas y problemas a los equipos. Más aún, los información recopilados de estos equipos pueden aplicarse para optimizar procedimientos y mejorar la presencia en sistemas de investigación.
Las campos de uso de los equipos de equilibrado cubren variadas sectores, desde la elaboración de ciclos hasta el supervisión ambiental. No interesa si se considera de grandes producciones productivas o pequeños espacios domésticos, los sistemas de equilibrado son indispensables para promover un operación eficiente y sin paradas.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me. https://accounts.binance.com/zh-TC/register?ref=VDVEQ78S
Hi my friend! I want to say that this post is awesome, great written and come with almost all important infos. I’d like to peer extra posts like this. Try to Visit My Web Site :WAHANA303
I must express my sincere admiration for your remarkable writing abilities and impeccable website design. Combining your captivating prose with the aesthetically pleasing layout creates an immersive user experience. It leaves me wondering whether you have employed a premium theme or if your expertise solely crafts this design
muha meds flavors
I must express my sincere admiration for your remarkable writing abilities and impeccable website design. Combining your captivating prose with the aesthetically pleasing layout creates an immersive user experience. It leaves me wondering whether you have employed a premium theme or if your expertise solely crafts this design
muha meds flavors
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Смотреть здесь электрик томск
перейдите на этот сайт https://xn—–6kcacs9ajdmhcwdcbwwcnbgd13a.xn--p1ai
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
ссылка на сайт r7 casino демо счет
Say hello to Compound—your go-to for everything DeFi. From seamless Compound Finance wallet access to full support for COMP token rewards and Compound governance, it’s built for serious growth. The Compound COMP ecosystem enables fast Compound lending and flexible Compound borrowing, all through the intuitive Compound app. No fluff—just real results. Read a Compound Finance review and check the Compound Finance tutorial to get started. Compound Finance login now at http://compound.ad and experience the future of crypto today!
Looking to stake on Solana? Marinade Finance is leading the charge with trusted, non-custodial Marinade liquid staking. Stake with ease using the Marinade app and earn yield through Marinade mSOL—all while keeping control of your assets. Curious about Marinade Finance review? Users love the performance, transparency, and safety. Want to know how to Marinade Stake SOL? It’s simple—connect your wallet and start staking. Ready to earn? Visit https://marinade.ink and boost your Marinade Yield today!
Sablier is built for builders, teams, and DAOs. With powerful Sablier token vesting, Sablier mirror integration, and Sablier crypto tools, itтАЩs the go-to for real-time finance. Backed by the trusted Sablier protocol and Sablier Labs, you can stream confidently on Sablier Ethereum. Need to claim? Use Sablier Claim or explore the Sablier app to manage it all. Visit https://sablier.cc and experience financial automation like never before!
Say hello to Juice Finance—your DeFi edge starts here! Tap into the power of Juice Finance yield farming and Juice Finance leverage, all backed by Juice Finance Security and verified Juice Finance Audits. The JUICE token drives the ecosystem, while the trusted Juice Finance Team keeps innovation flowing. Questions? Juice Finance Support is always here to help. Learn what is Juice Finance and explore the future of finance. Juice Finance app is ready—start now at https://juice.ac !
Exploring cross-chain swaps? ThorSwap is redefining DeFi with its powerful ThorSwap DEX and seamless ThorSwap Exchange. With ThorSwap Cross-Chain support and the ThorSwap Aggregator, users enjoy top liquidity across multiple networks. Curious about ThorSwap Security or ThorSwap Fees? It’s safe, efficient, and transparent. Want to learn more? ThorSwap Tutorial and ThorSwap Guide make it easy. Ready to trade? ThorSwap App is live—join now at https://thorswap.cc and take full control of your crypto journey!
Say goodbye to outdated liquidity tools—Balancer is here to transform your DeFi journey. Whether you’re exploring Balancer token (BAL), participating in Balancer airdrop vesting, or navigating Balancer Drop, the Balancer app gives you seamless access and full control. Dive into Balancer liquidity, manage your Balancer Portfolio, and track everything with Balancer Mirror. Check Balancer reviews, learn about Balancer pricing, and join the movement at https://balancer.ac !
Say hello to Super Sushi Samurai—the ultimate crypto game experience! Earn with Super Sushi Samurai land, explore the Super Sushi Samurai land map, and boost your gameplay using Super Sushi Samurai strategy and Super Sushi Samurai tips. Whether you’re collecting Super Sushi Samurai NFT items or gearing up for the Super Sushi Samurai airdrop, the SSS game delivers nonstop action. Want in? Buy SSS token and join the community on Super Sushi Samurai Telegram. Play now at https://sssgame.ink !
Say hello to Ring Exchange—the DeFi platform made for next-gen crypto users. Whether you’re trading on the Ring Exchange aggregator, exploring Ring Protocol crypto, or earning with Ring Exchange staking, the experience is seamless. Ring Exchange launchpad opens new project access, while the RING token powers the ecosystem. Wondering how it compares? See why traders are switching in every Ring Exchange review. Start your journey now at https://ringexchange.org !
Curious about next-gen DeFi? Sky Money is transforming savings and rewards through the powerful Sky Protocol. From SKY token rewards to smart MKR to SKY conversion, the Sky ecosystem is designed for performance and transparency. With integrated Sky Savings Rate and full support for sky ETH and sky Ethereum, it’s built to grow. Want to know more? The Sky Atlas and Sky Stars program show you the way. Ready to earn? Visit https://skymoney.net and unlock your Sky rewards today!
Power up your crypto strategy with Balancer—where flexibility meets innovation. Use Balancer Swap to trade smarter, explore Balancer vesting options, and stay on top of the game with Balancer Change updates. With features like Balancer governance, Balancer token vesting, and detailed Balancer guide content, it’s built for both beginners and pros. Love transparency? So do we. That’s why Balancer reviews speak for themselves. Start now at https://bccgame.org and take control of your crypto future.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
нажмите здесь Купить мяу
Phoenix DEX is rewriting the rules of DeFi on Solana. As a core part of the Phoenix Exchange Solana ecosystem, it supports advanced tools like Phoenix Trade Bonk pairs, seamless Phoenix Trade Wallet access, and reliable Phoenix Trade Security. Curious about how it works? The Phoenix Trade Tutorial and Phoenix Trade Guide make it easy. Traders love the efficiency, especially with low Phoenix Trade Fees and the powerful Phoenix Trade Features. Phoenix where to begin? Visit https://phoenixtrade.me and trade smarter today!
Say hello to LiquifiтАФa smarter way to manage vesting. Whether it’s Liquifi DAO vesting or automated Liquifi drop delivery, Liquifi Finance makes it effortless. Backed by a full Liquifi audit and trusted Liquifi security, itтАЩs a go-to for leading projects. Learn with the Liquifi Guide or dive into a step-by-step Liquifi tutorial. ItтАЩs fast, secure, and built for Web3. Liquifi sign up today at https://liquifi.tech !
Say hello to Instadapp—the ultimate DeFi hub! Whether you’re using Instadapp ETH, Instadapp DAI, or Instadapp WBTC, the Instadapp App gives you seamless control with advanced Instadapp Governance features. Stake with confidence, manage your INST token, and explore opportunities like the Instadapp Airdrop. Need help? Learn how to use Instadapp and discover the power of DeFi Smart Accounts (DSA). Instadapp login today at http://instaoapp.com and level up your strategy now!
How does password encryption help protect user data from unauthorized access? Universitas Telkom
view website https://astake.cc
узнать больше Здесь https://forum.hpc.name/thread/s570/136888/telegram-bot-ojidanie-sleduyushchego-soobshcheniya.html
you can try these out paycor login
Excellent read, I simply passed this onto a colleague who was doing slightly analysis on that. And hubby actually bought me lunch as a result of I came upon it for him smile thus well then , ill rephrase that: thank you for lunch! Try to Visit My Web Site :Daftar Link Slot QRIS Deposit 10 rb
helpful hints phantom Extension
have a peek at these guys Metamask Extension
Can I say thats a relief to find a person that truly knows what theyre discussing online. You actually discover how to bring a challenge to light and make it important. The best way to ought to check this out and can see this side of your story. I cant believe youre no more well-known because you absolutely provide the gift. Try to Visit My Web Site :Link Daftar Slot Deposit Qris 10rb Lokabet88
смотреть здесь Altcoin обмен криптовалюты
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
over at this website Metamask Extension
ссылка на сайт водкабет казино
Перейти на сайт пинко
посмотреть на этом сайте кракен даркнет
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
опубликовано здесь Фарма, гормон роста
article jaxx wallet
more tips here inyeccion de tirzepatida de Mounjaro
lucky jet 1win – лаки джет официальный сайт, lucky jet 1 win
узнать больше вотка бет
cialis 2 5 mg prezzo : an effective drug containing tadalafil, is used for erectile dysfunction and benign prostatic hyperplasia. In Italy, a 28-tablet pack of Cialis 5 mg costs around €165.26, though prices vary by pharmacy and discounts. Generic options, like Tadalafil DOC Generici, cost €0.8–€2.6 per tablet, offering a cheaper option. Always consult a doctor, as a prescription is required.
It’s awesome for me to have a web site, which is good for my know-how. thanks admin
https://interpen.com.ua/kakoy-elektroshoker-vybrat-dlya-samozashchity-v-gorode
Your article helped me a lot, is there any more related content? Thanks!
This excellent website definitely has all the info I wanted concerning this subject and didn’t know who to ask.
https://esco-center.com.ua/yak-doglyadaty-za-sklom-fary-porady-dlya-tryvalogo-vykorystannya
Pretty! This was an extremely wonderful post. Thanks for supplying these details.
https://www.merlot.org/merlot/viewMember.htm?id=1484427
Hi, all is going sound here and ofcourse every one is sharing facts, that’s genuinely excellent, keep up writing.
my Zain
Valuable info. Lucky me I discovered your website unintentionally, and I’m shocked why this accident did not came about in advance! I bookmarked it.
Myzain
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thank you for every other informative website. Where else may I get that kind of info written in such a perfect method? I have a project that I am just now operating on, and I’ve been at the glance out for such information.
Zain
Hi there great website! Does running a blog such as this require a massive amount work? I’ve absolutely no knowledge of computer programming but I was hoping to start my own blog soon. Anyhow, if you have any ideas or techniques for new blog owners please share. I understand this is off topic but I simply needed to ask. Kudos!
my Zain
I’m not sure exactly why but this website is loading incredibly slow for me. Is anyone else having this problem or is it a problem on my end? I’ll check back later and see if the problem still exists.
kuwait airport jobs
This web-based service enables instant conversion of images into JPG format, supporting common types such as JPG. All operations take place within the browser, with no need for app downloads or user accounts. Up to 20 files can be converted in a single session, improving efficiency for repetitive or large-scale tasks. Once files are processed, they are deleted from the system to maintain privacy and prevent unnecessary storage. JPEGtoJPGHERO is designed to work across all devices and browser types, offering a seamless experience whether on a computer, phone, or tablet. Its minimal layout emphasizes clarity and speed, guiding users directly to results. From resizing visuals for websites to preparing files for cloud storage, the platform handles JPEGtoJPGhero conversion with accuracy and ease. Its emphasis on simplicity and security makes it an excellent choice for both casual users and professionals who require consistent, reliable output.
https://sketchfab.com/AnnyGood
Hi friends, how is the whole thing, and what you would like to say regarding this paragraph, in my view its actually awesome designed for me.
https://www.04563.com.ua/list/513738
Excellent website you have here but I was curious about if you knew of any discussion boards that cover the same topics talked about here? I’d really like to be a part of community where I can get feed-back from other experienced individuals that share the same interest. If you have any suggestions, please let me know. Thanks!
recharge hafilat card
What’s up to every , since I am genuinely keen of reading this webpage’s post to be updated regularly. It contains pleasant information.
prepaid card inquiry
Helpful info. Fortunate me I discovered your web site unintentionally, and I’m stunned why this accident did not came about earlier! I bookmarked it.
hafilat card balance check
Why visitors still use to read news papers when in this technological globe the whole thing is existing on net?
hafilat card
Wow, awesome blog layout! How long have you been blogging for? you make blogging look easy. The overall look of your web site is fantastic, let alone the content!
https://nemovlya.com.ua/top-10-stekol-far-bmv-dlya-modeley-ostannih-rokiv
Сергей Бидус кидало
kra32.at – кракен вход, kra32.at
Hi! This post couldn’t be written any better! Reading this post reminds me of my previous room mate! He always kept talking about this. I will forward this article to him. Fairly certain he will have a good read. Thanks for sharing!
porno videok
What’s up it’s me, I am also visiting this website on a regular basis, this web site is in fact pleasant and the users are actually sharing pleasant thoughts.
hafilat balance check
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
JPGtoPNGHero.com provides a simple, browser-based solution for converting JPG files into PNG images. Designed with both professionals and beginners in mind, the site keeps its interface clean: a single “Upload” button and a drag-and-drop field guide users through the process. After you select your images, cloud servers perform the conversion automatically, preserving image clarity and transparency where relevant. Real-time progress indicators display each file’s status, and once finished, you’ll see download links appear immediately. The batch conversion feature lets you convert multiple files at once, ideal for photographers or marketers who need to process large sets of visuals. Because the tool is web-based, it supports all major operating systems—Windows, macOS, Linux, Android, and iOS—without any extra setup. Privacy ranks high: all files get deleted from the server soon after conversion, and no personal information is stored. No account is necessary, and the service remains completely free. From resizing logos for ecommerce sites to preparing artwork for presentations, JPGtoPNGHero.com makes image conversion effortless.
JPGtoPNGHero
This website certainly has all the information and facts I needed concerning this subject and didn’t know who to ask.
https://oceaviva.fr/yak-pravylno-nalashtuvaty-bi-led-linzu-pislya-mont.html
No one desires to suffer the opposed effects of MK-677, however it does occur, and it’s unlikely that anyone will use it with out at least one unwanted effect. We must take the nice with the unhealthy and hope the nice outweighs the unhealthy to make MK-677 worth using. 1000’s of bodybuilders have used MK-677, and you will discover many critiques, experiences, complaints, results, and comments about this compound.
This is because of it having to bypass the liver upon getting into the bloodstream, just like C-17 alpha-alkylated buying steroids online in usa (http://therockpit.net/wp-content/pages/clenbuterol_anavar_stack.html), which research have proven to trigger hepatotoxicity [31,32]. Primarily Based on in vivo research and our expertise, we have noticed the following opposed effects transpire from RAD 140. The above Reddit user administered lower than 10 mg/day of RAD 140 for almost all of his 8-week cycle, demonstrating that optimal outcomes can nonetheless be experienced at a low dosage. RAD one hundred forty surfaced in 2010 after being formulated by a US biotechnology company, Radius Health.
Altering consuming habits is difficult to do but should you comply with these easy tips, you can maximize the outcomes of your diet. Most of us have turn into indoctrinated to the thee-meal-a-day way of life, a large breakfast, hearty lunch and a dinner feast. Sadly, this isn’t a super eating schedule for the body and might result in more unhealthy habits, like skipping lunch because of a large breakfast, for instance.
Pimples, hair loss, temper fluctuations, liver harm, and the next likelihood of coronary heart disease are a few of them. It’s crucial to contemplate the advantages and disadvantages of taking Check four hundred and to get medical recommendation before beginning any steroid cycle. Sustamix (Testosterone Mix) is readily aromatized within the physique to estradiol (estrogen).
Nonetheless, using it for these causes is very restricted and desires a prescription from a professional healthcare supplier. The ONYX LABS TRENONYX-E 150MG/ML 10ML VIAL is a potent injectable solution tailor-made for therapeutic use. With 150 milligrams of active ingredient per milliliter, it ensures precise dosing, essential for therapeutic efficacy. Healthcare professionals appreciate its reliability and ease of administration in scientific settings. However, improved packaging for easier entry to the solution might improve person expertise.
Petzke was facing a minimum of 5 years in prison, however that was later modified to a maximum of five years in federal jail after he made his plea association. The glutes or buttocks are among the many most popular locations to get steroids Check four hundred. This is so that the vast muscle group may simply accommodate the injection’s volume. Guaranteeing the injection is deep sufficient to succeed in the muscular tissue versus merely the fat tissue is crucial. To counteract the hair loss, you presumably can strive using a hair-loss medicine corresponding to finasteride or Rogaine, however the outcomes are combined.
Hair and pores and skin enchancment advantages shall be welcomed, and the sleep high quality results give women the vitality to undertake these intensive exercises. If fat loss is a major objective, girls will find the appetite-stimulating effects of MK-677 difficult. Still, with adequate self-discipline, many will be able to drop an excellent number of kilos while profiting from MK-677’s anti-catabolic results to maintain lean muscle. OK, muscle and energy positive aspects are to be anticipated, but what I like about Ibuta 677 is its unimaginable psychological focus.
We will have the ability to present essentially the most excellent companies to you and allow you to overcome troubles that you face. Girls are warned of the potential virilizing effects of anabolic/androgenic steroids, especially with a powerful androgen such as testosterone. These may include deepening of the voice, menstrual irregularities, adjustments in skin texture, facial hair growth, and clitoral enlargement.
It suits perfectly into the protocols for sustaining applicable muscle mass while you are on the journey of shedding calories. The discount in calories is usually accompanied by lack of muscle tissue however Ostarine due to its anabolic effects helps in chopping energy with out letting go of the hard-earned muscle mass. MK-2866 is an SARM which implies it works by binding to the androgen receptor and demonstrating bone and muscular anabolic exercise.
That means antagonistic results like zits and hair loss shouldn’t be an issue with this compound. Despite MK-677 not causing changes to estrogen, the development of water retention remains to be a possibility, and this happens for reasons that I’ve outlined further below. Many individuals can use this compound with none fluid retention, and it is usually dosage-dependent. Whereas Check four hundred is known to be an efficient steroid for constructing muscle mass and energy, it also carries the risk of unwanted effects.
news jaxx bitcoin wallet
JPGtoPNGHero.com is a free, online converter crafted to turn JPG files into PNG images with ease. Whether you’re preparing icons for a mobile app or converting family photos for a digital scrapbook, the process is straightforward: upload, wait a moment, and download. The server-side engine preserves image quality, ensuring sharpness and accurate color reproduction. A visible progress indicator tracks each file’s status in real time. Need to convert a whole folder of images? Batch conversion handles multiple JPGs at once, streamlining your workflow. Since the converter works entirely in a browser, it’s compatible with Windows, macOS, Linux, Android, and iOS—no installations required. Privacy is built in: all uploads are automatically deleted shortly after processing, and no user data is stored on the server. The site remains ad-free, requires no user account, and imposes no conversion limits. Whether you’re a digital artist, social media manager, or just someone who needs to change image formats, JPGtoPNGHero.com offers a fast, reliable, and hassle-free experience.
JPGtoPNGHero
It’s amazing to pay a visit this site and reading the views of all mates on the topic of this post, while I am also eager of getting knowledge.
https://sniteshop.com.ua/sklo-far-ta-zakon-chy-mozhna-minyaty-samostijno.html
Wow, wonderful blog structure! How long have you ever been blogging for? you made running a blog glance easy. The entire glance of your website is fantastic, as well as the content!
http://ruyanamerica.com/kupyty-sklo-far-dlya-zaminy-na-shcho-zvertaty-uvah.html
you’re in reality a good webmaster. The web site loading velocity is incredible. It sort of feels that you’re doing any unique trick. Furthermore, The contents are masterpiece. you have done a excellent job on this matter!
https://2xaynha.com/yak-pravylno-vybraty-prodavtsya-dlya-pokupky-skla-.html
I used to be able to find good information from your blog articles.
http://e-art.com.ua/yak-vybraty-steklo-fary-dlya-vashoho-avtomobilya.html
JPGtoPNGHero.com provides a simple, browser-based solution for converting JPG files into PNG images. Designed with both professionals and beginners in mind, the site keeps its interface clean: a single “Upload” button and a drag-and-drop field guide users through the process. After you select your images, cloud servers perform the conversion automatically, preserving image clarity and transparency where relevant. Real-time progress indicators display each file’s status, and once finished, you’ll see download links appear immediately. The batch conversion feature lets you convert multiple files at once, ideal for photographers or marketers who need to process large sets of visuals. Because the tool is web-based, it supports all major operating systems—Windows, macOS, Linux, Android, and iOS—without any extra setup. Privacy ranks high: all files get deleted from the server soon after conversion, and no personal information is stored. No account is necessary, and the service remains completely free. From resizing logos for ecommerce sites to preparing artwork for presentations, JPGtoPNGHero.com makes image conversion effortless.
JPGtoPNGHero
JPGtoPNGHero.com provides a simple, browser-based solution for converting JPG files into PNG images. Designed with both professionals and beginners in mind, the site keeps its interface clean: a single “Upload” button and a drag-and-drop field guide users through the process. After you select your images, cloud servers perform the conversion automatically, preserving image clarity and transparency where relevant. Real-time progress indicators display each file’s status, and once finished, you’ll see download links appear immediately. The batch conversion feature lets you convert multiple files at once, ideal for photographers or marketers who need to process large sets of visuals. Because the tool is web-based, it supports all major operating systems—Windows, macOS, Linux, Android, and iOS—without any extra setup. Privacy ranks high: all files get deleted from the server soon after conversion, and no personal information is stored. No account is necessary, and the service remains completely free. From resizing logos for ecommerce sites to preparing artwork for presentations, JPGtoPNGHero.com makes image conversion effortless.
JPGtoPNGhero
Please let me know if you’re looking for a article writer for your site. You have some really good posts and I believe I would be a good asset. If you ever want to take some of the load off, I’d love to write some articles for your blog in exchange for a link back to mine. Please shoot me an email if interested. Regards!
http://vabank.com.ua/chy-varto-kupuvaty-led-lampy-na-olx-abo-aliexpress.html
Thank you for some other great article. Where else may just anybody get that type of information in such an ideal manner of writing? I’ve a presentation next week, and I am on the search for such info.
http://mitsubishi-nikol-motors.com.ua/yak-pidtrymuvaty-chystotu-linz-u-farakh-na-dovhyj-.html
kra33.at – Кракен даркнет как зайти на площадку, kraken ссылка
Hi I am so excited I found your weblog, I really found you by error, while I was looking on Digg for something else, Nonetheless I am here now and would just like to say kudos for a tremendous post and a all round thrilling blog (I also love the theme/design), I don’t have time to browse it all at the moment but I have book-marked it and also added your RSS feeds, so when I have time I will be back to read much more, Please do keep up the superb b.
hafilat bus card balance check online
Hey! I know this is kind of off-topic but I had to ask. Does running a well-established blog like yours require a large amount of work? I am brand new to writing a blog but I do write in my diary every day. I’d like to start a blog so I can share my experience and thoughts online. Please let me know if you have any recommendations or tips for brand new aspiring bloggers. Thankyou!
hafilat bus card recharge
click here to investigate jaxx wallet
Right here is the perfect web site for anyone who wants to find out about this topic. You realize so much its almost hard to argue with you (not that I really will need to…HaHa). You definitely put a new spin on a subject that has been written about for many years. Excellent stuff, just great!
hafilat card balance check
Why viewers still make use of to read news papers when in this technological globe all is existing on net?
hafilat card balance check online
Your article helped me a lot, is there any more related content? Thanks!
this website Fox.wallet
SVGtoPNGHero.com provides a fast, user-friendly way to convert SVG graphics into PNG format without any extra installs. The homepage displays a clear drag-and-drop zone and an “Upload” button for manual selection. Once you add your SVG files, conversion begins immediately on remote servers that preserve image clarity and transparency. A progress meter shows you exactly how much remains before your PNGs are ready. In moments, download links appear beneath each file, allowing instant saving. If you’re working with multiple graphics—such as charts, icons, or vector portraits—the batch conversion tool processes them all together. The service runs entirely in your browser, so it works on desktops, tablets, and smartphones alike. All uploaded images delete themselves after conversion. SVGtoPNGHero.com makes format conversion swift, secure, and completely free.
SVGtoPNGhero Converter
JPEGtoJPGHero.com is a free web tool that converts JPEG files into JPG format quickly and securely. Simply drag and drop your images or click “Upload” to select files from your device. The conversion happens on remote servers, so you don’t need to install software or worry about local processing power. When the process finishes, download links appear instantly, letting you save new JPG versions to use in presentations, social media posts, or websites. Batch processing handles multiple files at once, saving time when you have dozens of photos to convert. Since the site runs entirely in a browser, it works on Windows, macOS, Linux, and mobile devices without compatibility issues. Privacy is a priority: every uploaded file is deleted automatically after conversion, and no personal data remains on the server. Whether you’re a photographer preparing images for clients or someone who needs a quick conversion, JPEGtoJPGHero.com offers a straightforward, ad-free experience. No registration or payment is required. Enjoy unlimited, hassle-free conversions from JPEG to JPG anytime.
JPEGtoJPGHero
JPG Hero converter is an online image converter built for speed, simplicity, and accessibility. This web-based platform allows instant conversion of popular image formats such as PNG, WebP, and BMP into JPG files. No downloads, installations, or user accounts are required. The entire process happens in-browser and takes only a few seconds. Users can upload up to 20 files at once for batch conversion, making it suitable for individuals and professionals managing multiple images. All uploaded files are automatically deleted after processing to maintain privacy and ensure data security. JPGHero.com is compatible with all modern devices, including desktops, tablets, and smartphones, offering flexibility for work on the go. Whether the goal is to reduce image file size, prepare visuals for the web, or standardize a project’s image format, this tool delivers clean, reliable results without any extra steps.
JPGHero Converter
Hello, I desire to subscribe for this website to obtain most recent updates, so where can i do it please assist.
https://www.tef-isolation.fr/navigating-plinko-gambling-a-guide-to-safe-and-enj.html
Right here is the right site for anyone who would like to understand this topic. You realize a whole lot its almost tough to argue with you (not that I personally will need to…HaHa). You certainly put a brand new spin on a topic that’s been written about for ages. Great stuff, just wonderful!
https://starmilar.com/best-plinko-game-app.html
купить вх для кс го – чит гта 5 онлайн, gta 5 online читы
Its like you read my mind! You seem to know a lot about this, like you wrote the book in it or something. I think that you can do with a few pics to drive the message home a little bit, but other than that, this is excellent blog. A great read. I will certainly be back.
https://mega-m.com.ua/kupyty-korpus-fary-yak-zrobyty-pokupku-yaka-vryatu.html
Thank you for the good writeup. It in reality used to be a leisure account it. Look complicated to far delivered agreeable from you! However, how could we keep in touch?
https://euro-house.com.ua/yak-unyknuty-problem-z-ochyshchennyam-stekla-na-fa.html
I used to be able to find good info from your blog articles.
http://tyres.com.ua/steklo-far-dlya-vantazhnykh-avto-shcho-potribno-zn.html
WOW just what I was searching for. Came here by searching for %keyword%
https://nikopolservice.com.ua/hermetyk-dlya-shvydkoho-remontu-fary.html
Turn bulky PNG images into lightweight WebP files in seconds with PNGtoWebPHero.com. The interface is clean and intuitive: a single upload field welcomes your PNGs—drag and drop or click to select. Cloud servers tackle the conversion, using advanced compression to keep picture quality while shrinking file size. A live progress bar keeps you informed as each job runs, and once it finishes, download links appear instantly for you to save the new WebP images. If you’re working on a project with multiple graphics, batch mode lets you convert all PNG files together, saving time and clicks. Because this tool operates purely online, there’s no need to install anything on your device—compatible with Windows, macOS, Linux, Android, and iOS. Privacy stays protected: every uploaded image is automatically deleted shortly after conversion, and no personal data is stored. Perfect for enhancing website performance, reducing bandwidth usage, or preparing images for sharing, PNGtoWebPHero.com provides fast, free, and hassle-free conversions at any time.
PNGtoWebPhero Converter
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Excellent article. Keep writing such kind of information on your page. Im really impressed by your blog.
Hi there, You’ve performed a fantastic job. I’ll definitely digg it and in my opinion recommend to my friends. I’m sure they will be benefited from this site.
cialis 5 mg cialis prezzo
Tried the Joy Organics gummy cbd in default of curiosity. Delicacy is nice, not too sweet. I took people in the afternoon when I was feeling kinda off — not mournful, upright adverse energy. Relating to 30–40 mins later, I felt a moment more level. Not like a enormous get, but enough to notice. No weird boom after. Don’t expect spellbinding, but in support of me, it helped take the limit eccentric without ardency zoned out.
Hi there colleagues, pleasant article and fastidious urging commented here, I am really enjoying by these.
tadalafil teva 5 mg prezzo
Turn bulky PNG images into lightweight WebP files in seconds with PNGtoWebPHero.com. The interface is clean and intuitive: a single upload field welcomes your PNGs—drag and drop or click to select. Cloud servers tackle the conversion, using advanced compression to keep picture quality while shrinking file size. A live progress bar keeps you informed as each job runs, and once it finishes, download links appear instantly for you to save the new WebP images. If you’re working on a project with multiple graphics, batch mode lets you convert all PNG files together, saving time and clicks. Because this tool operates purely online, there’s no need to install anything on your device—compatible with Windows, macOS, Linux, Android, and iOS. Privacy stays protected: every uploaded image is automatically deleted shortly after conversion, and no personal data is stored. Perfect for enhancing website performance, reducing bandwidth usage, or preparing images for sharing, PNGtoWebPHero.com provides fast, free, and hassle-free conversions at any time.
PNGtoWebPhero Converter
At PNGtoJPGHero.com, swapping PNG files for JPG images couldn’t be simpler. Just visit the homepage, drag your image into the upload box, and let the server handle the rest. Within moments, optimized JPG versions become available via download links. You can process multiple photos in one session thanks to batch conversion, eliminating repetitive clicks. The entire workflow takes place in your web browser—no plug-ins or extra software required. This tool works on any device, whether you’re on a desktop, laptop, tablet, or smartphone. A live status indicator keeps you informed of every step. After conversion, uploaded files vanish automatically, ensuring your data stays private. PNGtoJPGHero.com delivers crisp, high-quality JPGs quickly, and best of all, it’s completely free.
PNGtoJPGHero
At PNGtoJPGHero.com, swapping PNG files for JPG images couldn’t be simpler. Just visit the homepage, drag your image into the upload box, and let the server handle the rest. Within moments, optimized JPG versions become available via download links. You can process multiple photos in one session thanks to batch conversion, eliminating repetitive clicks. The entire workflow takes place in your web browser—no plug-ins or extra software required. This tool works on any device, whether you’re on a desktop, laptop, tablet, or smartphone. A live status indicator keeps you informed of every step. After conversion, uploaded files vanish automatically, ensuring your data stays private. PNGtoJPGHero.com delivers crisp, high-quality JPGs quickly, and best of all, it’s completely free.
PNG to JPG converter
Need to convert JPGs into PNGs without fuss? JPGtoPNGHero.com has you covered. The interface is designed for ease: drag your JPG file into the upload field or click “Select” to choose manually. Once uploaded, advanced cloud servers handle the conversion, delivering a sharp, transparent-friendly PNG. A status bar tracks progress, and download buttons appear immediately afterward. For multiple files, batch mode lets you process them all in one go. No account or payment is required—just open the site in any browser. The service works smoothly on desktop computers, tablets, and smartphones under any operating system. Uploaded images erase themselves shortly after conversion, ensuring confidentiality. JPGtoPNGHero.com delivers dependable, free PNG conversions every time.
JPG to PNG Converter
read the full info here Polskie linki darkweb
Keep on working, great job!
https://newstoday.com.ua/chy-pidijde-butylovyj-hermetyk-dlya-led-far.html
browse around this website Anonimowe forum Polska
imp source Polskie forum cyberprzestepczosci
It’s awesome to pay a quick visit this website and reading the views of all friends on the topic of this piece of writing, while I am also keen of getting knowledge.
гей порнорассказы
With AVIFtoPNGHero.com, users can seamlessly transform modern AVIF image files into the widely supported PNG format. It’s built with precision, offering crisp PNG output without distorting image data or compressing detail. Whether you’re preparing assets for e-commerce or publishing visuals to social media, the format conversion process is seamless. When speed, quality, and simplicity matter, AVIFtoPNGHero provides the ideal conversion solution.
aviftopnghero
In Softonic we scan all the files hosted on our platform to assess and avoid any potential harm for your device. Our team performs checks each time a new file is uploaded and periodically reviews files to confirm or update their status. This comprehensive process allows us to set a status for any downloadable file as follows: Teen Patti Gold: A Thrilling Game for Teenagers and Adults Alike It’s important to download the Teen Patti Gold apk from the official website. This avoids any security risks from third-party sources. Downloading from the official source means you get the real online Teen Patti experience. Are you a gaming enthusiast looking for a riveting online casino experience? If yes, then Teen Patti Gold (or 3 Patti Gold) is a popular Android casino app today. Honestly, it is taking the virtual gaming scene by storm. Gamers can enjoy nearly 22 games spanning skill, multiplayer, slots, and sports categories. Hence, it is a one-stop-shop for those seeking excitement, friendship, and a chance to win big.
http://www.v0795.com/home.php?mod=space&uid=2049690
Star Game Online app is one of the third-party applications that offer you online games to start playing and earn lots of money within a few minutes of play. Nowadays this app is on trend therefore, you can also try this app to earn money by playing games or to be entertained. Teen Patti Diamond: 3 Patti is basically a teen patti card game, also known as Flash or Flush, that lets you play with others online. You don’t need to register and you can enter guest mode to start playing right away. It boasts virtually zero waiting time when you’re looking for a table to join. It’s important to note that when playing Teen Patti online, whether for fun or real money, you should be aware of the platform’s terms and conditions. Additionally, if you’re playing for real money, make sure that online gambling is legal in your jurisdiction, and you play responsibly.
This is very interesting, You are a very skilled blogger. I’ve joined your feed and look forward to seeking more of your magnificent post. Also, I’ve shared your web site in my social networks!
tadalafil 5 mg controindicazioni
Hey there! Would you mind if I share your blog with my facebook group? There’s a lot of people that I think would really enjoy your content. Please let me know. Thank you
dead rails script speed hub
شركة تسليك مجاري بالرياض
OneConverter.com is an all-in-one online platform that simplifies conversions of every kind. Whether you need to switch between units of length, weight, or volume, this site makes it feel effortless. The interface greets you with a clean design: select your category, enter a value, and watch as the result appears instantly. No downloads, no installations—everything runs in your browser. From temperature and area to speed and energy, OneConverter supports dozens of measurement types. If you’re comparing currencies, simply pick your desired pair and enter an amount to get real-time exchange rates. Need to convert time zones or calculate time differences? That’s built in, too. Everything happens in seconds: no complex menus, no hidden settings. Perfect for students tackling homework, engineers double-checking specifications, or travelers calculating distances and costs. Every formula and rate updates automatically, ensuring accuracy across all conversions. With mobile-friendly pages, you can compute wherever you are, on any device. OneConverter.com doesn’t require registration or payment—just open the site, choose a converter, and start transforming numbers. It’s reliable, efficient, and completely free.
OneConverter.com
At OneConverter.com, changing units becomes a breeze. Imagine wanting to know how many centimeters fit into five feet—just visit the length converter, type “5,” select “Feet,” and choose “Centimeters.” In a blink, you have an exact answer. The same goes for mass conversions: kilograms, pounds, ounces, or stones—whatever you need. Need to measure liquid volume? Liters, gallons, or fluid ounces convert instantly with a few clicks. The site even handles specialized tasks like converting square feet to square meters for home renovation projects. A dropdown menu displays all available units in each category, so you’ll never guess at abbreviations. Behind the scenes, OneConverter relies on precise formulas and regularly updated data, ensuring every result is trustworthy. The design remains uncluttered: large input fields, clear dropdowns, and visible output. Use it on a phone or tablet—no app required. Whether you’re a DIY enthusiast measuring paint for a room, a chemist balancing solutions, or a runner tracking distances in miles versus kilometers, OneConverter.com serves as your digital ruler, scale, and compass, all in one place.
OneConverter.com
Currency exchange and time calculations can be tricky, but OneConverter.com makes them simple. Need to know how many euros you get for 100 US dollars? Select “Currency,” choose USD as the source and EUR as the target currency, enter “100,” and instantly see the converted amount. The site fetches up-to-date exchange rates, so you’re never working with outdated numbers. Want to figure out meeting times across continents? The time zone converter shows your local time alongside any global city. Just pick two zones, enter a time, and you’ll see what it is on the other end. You can even schedule calls across four different regions by adjusting each field. There’s no delay—calculations appear immediately, and you can switch dates and zones as needed. A simple toggle switches between 12-hour and 24-hour clocks. Travelers planning itineraries appreciate this tool for planning flights, while business professionals rely on it for international conference calls. OneConverter.com combines both currency and time functions under one roof, offering seamless, accurate, and free conversions without any registration or fees.
OneConverter
70918248
References:
bodybuilding steroids side effects (https://academy.mahbod.style/mag/%DA%AF%D8%B1%DB%8C%D9%85-%D8%B3%DB%8C%D9%86%D9%85%D8%A7%DB%8C%DB%8C-%DA%86%DB%8C%D8%B3%D8%AA%D8%9F/)
OneConverter.com does more than just numbers—it also converts digital data. Whether you want to know how many gigabytes fit into a terabyte or how many bits are in a kilobyte, this tool has you covered. The digital storage converter lists common units like bytes, kilobytes, megabytes, gigabytes, and terabytes alongside less common ones such as petabytes and exabytes. Simply enter a value, pick the starting unit, and then choose your desired unit to see an instant conversion. Even larger scales—zettabytes, yottabytes—are supported for advanced calculations. Researchers dealing with big data find this especially handy, as do photographers managing high-resolution files. If you need to compare file sizes or plan server capacity, this converter delivers precise results. All background calculations rely on the standard binary and decimal values, clarifying any confusion about whether to use base-2 or base-10 measurements. Everything updates automatically, so you never need to memorize conversion factors. Users of all skill levels—from novices to IT professionals—appreciate how OneConverter.com transforms digital measurement tasks into a quick, headache-free experience.
OneConverter.com
Using OneConverter.com is as simple as it gets. There’s no steep learning curve, no hidden menus—just click on the converter you need, type in a number, and watch it change before your eyes. Input fields are large and responsive, and drop-down menus clearly list each available unit. Want to switch categories? A visible menu at the top of the page displays all options: length, weight, area, volume, temperature, speed, energy, pressure, and more. With a single click, you move from converting miles to kilometers over to turning Celsius into Fahrenheit. All results appear instantly, with no extra steps or needless redirects. The site uses neutral colors and legible fonts, so reading values remains comfortable even for extended sessions. If you ever change your mind, click “Reset” to clear all fields and start fresh. Because OneConverter operates fully on modern web technology—no Flash, no Java—it runs smoothly on nearly any device. Even if internet connection fluctuates, cached results keep you going until you’re back online. It’s conversion made easy, straight, and effective.
OneConverter.com
Hello colleagues, good post and good urging commented here, I am truly enjoying by these.
http://tyres.com.ua/yak-pravylno-kupyty-led-linzy-holovni-nyuansy.html
Your article helped me a lot, is there any more related content? Thanks!
Hey there, I think your blog might be having browser compatibility issues. When I look at your website in Safari, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, great blog!
промокод либет казино
Wow, fantastic weblog structure! How lengthy have you been running a blog for? you made running a blog look easy. The full glance of your site is wonderful, as neatly as the content!
сайт банда казино
Wow, marvelous weblog structure! How lengthy have you been running a blog for? you make blogging glance easy. The full glance of your website is magnificent, let alone the content material!
svkvvc.ru
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Evcil hayvan sahiplenmek, hayatınıza sevgi, sadakat ve sorumluluk katmanın en güzel yollarından biridir. Kedi ya da köpek sahiplendiğinizde yalnızca bir hayvana yuva açmakla kalmaz, aynı zamanda onunla birlikte birçok duyguyu paylaşacağınız uzun soluklu bir yolculuğa başlarsınız. Sahiplendirme, barınaklarda veya sokakta yaşam mücadelesi veren canlıların hayatını değiştirme fırsatıdır.Sahiplendirme kararı almadan önce kişinin kendi yaşam koşullarını değerlendirmesi büyük önem taşır. Ev ortamı, günlük zaman planı, maddi imkanlar ve hayvana ayrılabilecek ilgi düzeyi mutlaka göz önünde bulundurulmalıdır. Kedi ve köpeklerin bakım ihtiyaçları birbirinden farklıdır. Kediler daha bağımsız olabilirken, köpekler sosyal yapıları gereği daha fazla zaman ve dikkat ister. Bu nedenle sahipleneceğiniz canlının ihtiyaçlarını anlayıp ona uygun bir yaşam sunabilmeniz gerekir. Sahiplendirme süreci çoğu zaman başvuru, görüşme, ev ziyareti gibi adımlardan oluşur. Bu adımlar, hayvanın kalıcı ve güvenli bir yuvaya kavuşmasını sağlamak içindir. Sahiplendirme yapan kişi ya da kurumlar hayvanın geçmişi, sağlık durumu ve mizacı hakkında bilgi verir. Böylece hem siz hem de sahipleneceğiniz can dostunuz daha uyumlu bir başlangıç yaparsınız.
Evcil hayvan sahiplenmek, hayatınıza sevgi, sadakat ve sorumluluk katmanın en güzel yollarından biridir. Kedi ya da köpek sahiplendiğinizde yalnızca bir hayvana yuva açmakla kalmaz, aynı zamanda onunla birlikte birçok duyguyu paylaşacağınız uzun soluklu bir yolculuğa başlarsınız. Sahiplendirme, barınaklarda veya sokakta yaşam mücadelesi veren canlıların hayatını değiştirme fırsatıdır.Sahiplendirme kararı almadan önce kişinin kendi yaşam koşullarını değerlendirmesi büyük önem taşır. Ev ortamı, günlük zaman planı, maddi imkanlar ve hayvana ayrılabilecek ilgi düzeyi mutlaka göz önünde bulundurulmalıdır. Kedi ve köpeklerin bakım ihtiyaçları birbirinden farklıdır. Kediler daha bağımsız olabilirken, köpekler sosyal yapıları gereği daha fazla zaman ve dikkat ister. Bu nedenle sahipleneceğiniz canlının ihtiyaçlarını anlayıp ona uygun bir yaşam sunabilmeniz gerekir. Sahiplendirme süreci çoğu zaman başvuru, görüşme, ev ziyareti gibi adımlardan oluşur. Bu adımlar, hayvanın kalıcı ve güvenli bir yuvaya kavuşmasını sağlamak içindir. Sahiplendirme yapan kişi ya da kurumlar hayvanın geçmişi, sağlık durumu ve mizacı hakkında bilgi verir. Böylece hem siz hem de sahipleneceğiniz can dostunuz daha uyumlu bir başlangıç yaparsınız.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Evcil hayvan sahiplenmek, hayatınıza sevgi, sadakat ve sorumluluk katmanın en güzel yollarından biridir. Kedi ya da köpek sahiplendiğinizde yalnızca bir hayvana yuva açmakla kalmaz, aynı zamanda onunla birlikte birçok duyguyu paylaşacağınız uzun soluklu bir yolculuğa başlarsınız. Sahiplendirme, barınaklarda veya sokakta yaşam mücadelesi veren canlıların hayatını değiştirme fırsatıdır.Sahiplendirme kararı almadan önce kişinin kendi yaşam koşullarını değerlendirmesi büyük önem taşır. Ev ortamı, günlük zaman planı, maddi imkanlar ve hayvana ayrılabilecek ilgi düzeyi mutlaka göz önünde bulundurulmalıdır. Kedi ve köpeklerin bakım ihtiyaçları birbirinden farklıdır. Kediler daha bağımsız olabilirken, köpekler sosyal yapıları gereği daha fazla zaman ve dikkat ister. Bu nedenle sahipleneceğiniz canlının ihtiyaçlarını anlayıp ona uygun bir yaşam sunabilmeniz gerekir. Sahiplendirme süreci çoğu zaman başvuru, görüşme, ev ziyareti gibi adımlardan oluşur. Bu adımlar, hayvanın kalıcı ve güvenli bir yuvaya kavuşmasını sağlamak içindir. Sahiplendirme yapan kişi ya da kurumlar hayvanın geçmişi, sağlık durumu ve mizacı hakkında bilgi verir. Böylece hem siz hem de sahipleneceğiniz can dostunuz daha uyumlu bir başlangıç yaparsınız.
Evcil hayvan sahiplenmek, hayatınıza sevgi, sadakat ve sorumluluk katmanın en güzel yollarından biridir. Kedi ya da köpek sahiplendiğinizde yalnızca bir hayvana yuva açmakla kalmaz, aynı zamanda onunla birlikte birçok duyguyu paylaşacağınız uzun soluklu bir yolculuğa başlarsınız. Sahiplendirme, barınaklarda veya sokakta yaşam mücadelesi veren canlıların hayatını değiştirme fırsatıdır.Sahiplendirme kararı almadan önce kişinin kendi yaşam koşullarını değerlendirmesi büyük önem taşır. Ev ortamı, günlük zaman planı, maddi imkanlar ve hayvana ayrılabilecek ilgi düzeyi mutlaka göz önünde bulundurulmalıdır. Kedi ve köpeklerin bakım ihtiyaçları birbirinden farklıdır. Kediler daha bağımsız olabilirken, köpekler sosyal yapıları gereği daha fazla zaman ve dikkat ister. Bu nedenle sahipleneceğiniz canlının ihtiyaçlarını anlayıp ona uygun bir yaşam sunabilmeniz gerekir. Sahiplendirme süreci çoğu zaman başvuru, görüşme, ev ziyareti gibi adımlardan oluşur. Bu adımlar, hayvanın kalıcı ve güvenli bir yuvaya kavuşmasını sağlamak içindir. Sahiplendirme yapan kişi ya da kurumlar hayvanın geçmişi, sağlık durumu ve mizacı hakkında bilgi verir. Böylece hem siz hem de sahipleneceğiniz can dostunuz daha uyumlu bir başlangıç yaparsınız.
ссылка на сайт kraken войти
узнать больше Здесь kraken34
можно проверить ЗДЕСЬ kra
I blog often and I genuinely appreciate your information. This article has really peaked my interest. I’m going to bookmark your blog and keep checking for new information about once per week. I subscribed to your Feed as well.
https://ostercenter.com.ua/chy-mozhna-farbuvaty-korpus-fary-i-yak.html
OneConverter.com works anywhere you need it—on a desktop, laptop, tablet, or smartphone. The responsive design automatically adjusts to fit your screen, whether you’re using a large monitor or a small mobile device. No separate app download is necessary: just open your web browser, navigate to the site, and start converting. Buttons and input areas adapt to touchscreens, so you can tap values instead of clicking with a mouse. Need to convert distance during a hike or check currency rates at an airport? The entire site loads quickly, even over cellular networks. When you rotate your phone, the layout optimizes for horizontal or vertical viewing without losing functionality. Images and icons remain sharp on high-resolution displays, and menus collapse elegantly into compact layouts on smaller screens. Behind every click, conversion formulas run on secure servers, so your device’s processor never gets bogged down. Offline caching ensures that once the page loads, you can switch between converters without extra data usage. OneConverter.com stands out as a truly cross-platform tool that never forces you to compromise on speed or usability.
OneConverter.com
With accuracy at its core, OneConverter.com delivers dependable results you can trust. Each category relies on industry-standard formulas and regularly updated data. For example, when converting between metric and imperial units, the site uses official conversion factors, so a kilometer always converts to exactly 0.621371 miles. In currency exchanges, it pulls live rates from reputable financial sources, ensuring you see the most current values for USD, EUR, JPY, GBP, and dozens of other currencies. Behind the scenes, validation checks catch typos or missing inputs—type “abc” instead of a number, and the site prompts you to correct it before proceeding. Temperature conversions use precise equations that maintain decimal accuracy, whether adjusting for scientific experiments or cooking recipes. As a bonus, all calculations happen on OneConverter’s secure servers, so you won’t risk exposing sensitive data on third-party apps. Whether you need to convert pounds to kilograms for a shipping label or calculate how many BTUs are in a kilowatt-hour for HVAC design, OneConverter guarantees that every result reflects the latest standards.
OneConverter
Traveling to Punta Cana, the gem of the Dominican Republic, promises an escape filled with sun-drenched beaches, whispering palms, and an ambiance of pure relaxation. But before you can indulge in the tropical splendor of Excellence Punta Cana or the upscale vibes of Excellence El Carmen, there’s one last journey you must consider: your Excellence Punta Cana airport Transfer. In this comprehensive guide, we’re taking the guesswork out of transportation from Punta Cana Airport to Excellence Punta Cana.
excellence el carmen airport
Nestled along the Caribbean coast, Punta Cana is the crest jewel of Dominican Republic’s tourism and a slice of heaven for water enthusiasts and beachgoers. But the magic of your tropical escapade starts long before you hit the silky sands—the journey from the airport to your hotel sets the tone for your vacation. In this extensive guide, we’ll navigate through the essentials of Punta Cana transportation from airport to hotel, ensuring you start and end your trip as blissfully as the relaxation that awaits.
how much is taxi from punta cana airport to hotel
Hi friends, its great post concerning tutoringand entirely explained, keep it up all the time.
http://cekresipos.com/navishcho-fari-skladna-heometriya-skla.html
Topping the list is the adults-only haven, Breathless Punta Cana Resort and Spa. To ensure your vacation begins seamlessly from the moment you touch down, booking a reliable Breathless Punta Cana airport transfer is crucial. Here’s how to make your arrival as effortless as the breezy ocean winds.
transfer from punta cana airport to breathless resort
Simply wish to say your article is as astounding. The clarity to your submit is simply cool and i can suppose you’re a professional on this subject. Well together with your permission let me to clutch your feed to keep up to date with coming near near post. Thank you 1,000,000 and please carry on the enjoyable work.
Best limo service near me
ВАЖНО! Предупреждение о мошенничестве
Внимание всем пользователям! Публикуем срочное предупреждение о мошеннической активности.
Номер телефона мошенников: +7 996 413-99-48
Описание ситуации:
Пострадавший стал жертвой обмана, переведя денежные средства на указанный номер. После совершения перевода злоумышленники в течение 4 недель отрицают получение денег, несмотря на подтвержденные банковские операции.
Факты мошенничества:
Подтвержденное списание средств со счета
Документальное подтверждение поступления денег получателю
Настойчивое отрицание получения средств со стороны мошенников
Продолжающаяся уже месяц мошенническая схема
Предупреждение:
Не поддавайтесь на уговоры неизвестных лиц и не переводите деньги без тщательной проверки контрагента. В случае обнаружения подозрительной активности немедленно обращайтесь в правоохранительные органы.
Действия пострадавшего:
В настоящее время пострадавший обратился в правоохранительные органы для возбуждения уголовного дела.
Призываем:
Распространить данную информацию среди знакомых
Быть бдительными при финансовых операциях
Проверять информацию о контрагентах
Не переводить деньги незнакомым лицам
Берегите свои средства и не дайте мошенникам шанса!
Attractive section of content. I just stumbled upon your blog and in accession capital to assert that I get actually enjoyed account your blog posts. Anyway I will be subscribing to your augment and even I achievement you access consistently fast.
вход Banda Casino
Nice post. I learn something totally new and challenging on blogs I stumbleupon everyday. It will always be exciting to read content from other writers and practice something from their web sites.
гама казино
Играть в онлайн казино Нью Ретро
Казино Нью Ретро (Ньюретро) предлагает игрокам увлекательные азартные развлечения в современном формате. Здесь собраны сотни игр от ведущих провайдеров, включая слоты, рулетку, блэкджек и живые дилеры. Играть можно как на реальные деньги, так и бесплатно в демо-режиме.
Обзор официального сайта Нью Ретро
Официальный сайт Нью Ретро выполнен в стиле ретро с элементами современного дизайна. Интерфейс интуитивно понятен: главная страница содержит разделы с играми, акциями, турнирами и поддержкой. Сайт адаптирован под ПК и мобильные устройства, что делает игру комфортной в любом месте.
Лицензия онлайн-заведения
Нью Ретро работает на основании международной лицензии, выданной авторитетным регулятором (например, Кюрасао или Мальта). Это гарантирует честность игр и защиту данных игроков. Лицензионную информацию можно найти в подвале сайта.
Бонусы для постоянных клиентов и новых игроков
Казино предлагает щедрые бонусы:
• Приветственный пакет – бонус за первые депозиты (например, 100% + фриспины).
• Кешбэк – возврат части проигранных средств.
• VIP-программа – эксклюзивные подарки для постоянных игроков.
Бесплатная игра в демо-режиме
Перед ставками на деньги можно попробовать игры бесплатно в демо-режиме. Это отличный способ изучить правила и стратегии без риска.
Провайдеры
В Нью Ретро представлены игры от топовых разработчиков: NetEnt, Pragmatic Play, Play’n GO, Push Gaming, Novomatic и других.
Играть в слоты бесплатно в демо-режиме
Демо-версии слотов доступны без регистрации. Популярные игры: Book of Dead, Gates of Olympus, Starburst, Mega Moolah.
Способы регистрации и входа на сайт Нью Ретро
Зарегистрироваться можно:
• Через email и пароль.
• Через соцсети (Google, Telegram).
• По номеру телефона (SMS-подтверждение).
Верификация на сайте
Для вывода средств требуется верификация:
1. Подтверждение email/телефона.
2. Загрузка документов (паспорт, платежная карта).
3. Проверка занимает до 24 часов.
Другие игры в казино Нью Ретро
Помимо слотов, доступны:
• Рулетка, блэкджек, покер.
• Игры с живыми дилерами.
• Викторины и квизы.
Турниры и лотереи на Ньюретро
Казино регулярно проводит турниры с призовыми фондами и лотереи с розыгрышем денег и гаджетов. Условия участия – активная игра и выполнение заданий.
Мобильные приложения
Нью Ретро предлагает ньюретро казино с выводом мобильное приложение для iOS и Android, где доступны все функции сайта.
Минимальный депозит
От 50-100 рублей (зависит от платежной системы).
Максимальные лимиты
Лимиты на вывод зависят от статуса игрока (обычно до 1 000 000 рублей в месяц).
Способы пополнения игрового счета
Доступные методы:
• Банковские карты (Visa/Mastercard).
• Электронные кошельки (Qiwi, WebMoney, Skrill).
• Криптовалюты (Bitcoin, Ethereum).
Вывод средств из заведения казино Ньюретро
Вывод занимает от 1 часа до 3 дней. Минимальная сумма – 500 рублей.
Служба поддержки игроков 24/7
Поддержка работает круглосуточно через:
• Онлайн-чат.
• Email.
• Telegram-бот.
Плюсы и минусы игры в казино для игроков
Плюсы:
? Много бонусов.
? Демо-режим.
? Быстрые выплаты.
Минусы:
? Ограниченные страны для регистрации.
? Долгая верификация.
Часто задаваемые вопросы
1. Как вывести деньги?
– Через тот же метод, которым делали пополнение.
2. Есть ли мобильное приложение?
– Да, для iOS и Android.
Последние отзывы о Нью Ретро
? Алексей, 28 лет: “Быстрые выплаты, но верификация затянулась”.
? Мария, 35 лет: “Нравится выбор слотов и турниры”.
Вывод
Нью Ретро – надежное казино с богатой игровой коллекцией и бонусами. Подходит для новичков и опытных игроков.
How far is Paradisus Palma Real from airport? The Paradisus Palma Real Golf & Spa Resort is approximately 10.5 to 11.6 miles (17 to 18.6 kilometers) from Punta Cana International Airport (PUJ), depending on the route taken. Distance from Punta Cana airport to Paradisus Palma Real is 11 miles, the travel time is typically 20-30 minutes by car, with private transfers or taxis taking around 20-30 minutes under normal traffic conditions.
paradisus palma real airport transfer
Here are 25 advantages of using transportation services (such as private transfers, taxis, or shuttles) from Punta Cana International Airport to Melia Caribe Beach Resort.
Pre-booked Melia Punta Cana airport shuttle eliminate the need to negotiate or search for transportation upon arrival.
transportation from punta cana airport to melia caribe tropical
продолжить
bs2tsite5.at
Do you have any video of that? I’d love to find out more details.
https://itsybitsyfirstgradeteacher.com/led-lampy-dlya-avto-yak-vybraty-spravzhnyu-yakist-.html
Hey very nice web site!! Guy .. Beautiful .. Wonderful .. I’ll bookmark your blog and take the feeds also? I am happy to search out numerous useful information here within the put up, we need work out extra techniques on this regard, thank you for sharing. . . . . .
http://tehnoprice.in.ua/ksenon-chy-led-shcho-krashche-svityt-u-2025-rotsi.html
Этот веб-ресурс предлагает обширную коллекцию видеоконтента для взрослых, включая любительские и профессиональные ролики в высоком разрешении. Сайт поддерживает удобную навигацию по жанрам и категориям, обеспечивая быстрый доступ к материалам, соответствующим предпочтениям пользователей. Доступ возможен без регистрации, но с обязательной возрастной верификацией. Пользователям рекомендуется ознакомиться с политикой конфиденциальности для безопасного использования.
https://fotoboobs.info
Платформа предоставляет доступ к высококачественным видео и изображениям для взрослой аудитории. Сайт включает интерактивные функции, такие как комментарии и рейтинги, а также удобный поиск по жанрам. Доступ к контенту бесплатный, с возможностью приобретения премиум-доступа. Возрастные ограничения строго соблюдаются в соответствии с законодательством.
https://vzadok.com
Платформа предоставляет доступ к высококачественным видео и изображениям для взрослой аудитории. Сайт включает интерактивные функции, такие как комментарии и рейтинги, а также удобный поиск по жанрам. Доступ к контенту бесплатный, с возможностью приобретения премиум-доступа. Возрастные ограничения строго соблюдаются в соответствии с законодательством.
https://mexfoto.net
Сайт представляет собой обширный архив мультимедийного контента для взрослых, включая видео, галереи изображений и текстовые материалы. Пользователи могут наслаждаться бесплатным доступом или приобрести подписку для эксклюзивного контента. Удобная навигация и строгие правила возрастной верификации делают платформу безопасной и доступной для целевой аудитории.
https://porkadevok.ru
Ресурс предлагает разнообразный выбор видео и фото для взрослых, включая как популярные жанры, так и эксклюзивные материалы. Платформа обеспечивает бесплатный доступ к большей части контента, с опцией премиум-подписки для дополнительных функций. Сайт акцентирует внимание на безопасности пользователей и соблюдении возрастных ограничений (18+).
https://extremeporn.info
Этот сайт специализируется на потоковом воспроизведении порнографического контента, предлагая видео в высоком разрешении. Платформа поддерживает широкий выбор жанров, от классических до нишевых, с удобной системой фильтров. Доступ возможен без регистрации, но пользователи должны подтвердить совершеннолетие. Сайт регулярно обновляется новыми роликами.
https://xhotlab.com
Ресурс предлагает обширную библиотеку видео для взрослых, доступных в HD и FullHD качестве. Пользователи могут исследовать контент по категориям, тегам или популярным подборкам. Сайт ориентирован на анонимный просмотр без обязательной регистрации, но требует подтверждения возраста (18+). Регулярные обновления обеспечивают актуальность коллекции.
https://onlain-porno-site.ru
Сайт предоставляет доступ к широкому спектру эротического и порнографического контента, включая эксклюзивные видео и регулярные обновления. Платформа ориентирована на взрослую аудиторию (18+), предлагая как бесплатные, так и премиум-разделы с улучшенным качеством. Интуитивный интерфейс и система тегов упрощают поиск. Все материалы соответствуют законодательным требованиям, с акцентом на возрастные ограничения.
https://oakporno.ru
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Remarkable! Its truly remarkable article, I have got much clear idea about from this piece of writing.
leebet
Thank you a bunch for sharing this with all of us you actually recognise what you’re talking approximately! Bookmarked. Please additionally visit my website =). We could have a hyperlink change arrangement among us
официальный сайт Twin Casino
Vodka Casino https://vodkasloty.com — российская ресурс с множеством слотов от NetEnt, Pragmatic Play, Evolution Gaming. Лицензия Кюрасао обеспечивает базовую защиту. Темный дизайн с красными акцентами, простое управление и мобильное приложение.
Excellent article. Keep posting such kind of info on your site. Im really impressed by your blog.
Hello there, You have performed an incredible job. I’ll certainly digg it and individually recommend to my friends. I am confident they will be benefited from this web site.
Stretch limo near me
click site https://pq.hosting/en/vps-vds-norway-oslo
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Москва после заката не спит, и мы аналогично: частная наркологическая клиника mcnl.ru ждёт 24/7. Без предварительной регистрации и бумаг — вызов доктора к вам за 40 минут, безопасный детокс под контролем, сверхскоростная капельница, психотерапия у вас, пожизненное сопровождение. Тайно, скрытно, эффективно — вернем вам трезвость без страданий.
Clicking Here
ASIA GLOBAL AVIATION MAINTENANCE
Since the admin of this site is working, no doubt very quickly it will be renowned, due to its quality contents.
Cheap limo near me
Москва после заката бодрствует, и мы аналогично: частная центр лечения алкоголизма и наркомании клиника https://mcnl.ru/ открыта 24/7. Без предварительной регистрации и формальностей — приезд специалиста по адресу за 40 минут, безопасный детокс под седацией, экспресс- капельница, психотерапия на дому, пожизненное сопровождение. Тихо, конфиденциально, точно — вернем трезвость без страха.
Simply want to say your article is as surprising. The clarity in your post is just nice and i could assume you’re an expert on this subject. Fine with your permission allow me to grab your feed to keep updated with forthcoming post. Thanks a million and please keep up the enjoyable work.
игровые автоматы gama casino
Nice post. I learn something totally new and challenging on websites I stumbleupon every day. It will always be exciting to read articles from other authors and practice a little something from other sites.
betwinner сайт
нажмите, чтобы подробнее safelychange bestchange
My spouse and I absolutely love your blog and find the majority of your post’s to be just what I’m looking for. can you offer guest writers to write content for you personally? I wouldn’t mind composing a post or elaborating on some of the subjects you write about here. Again, awesome website!
https://webstore.com.ua/ru/2025/07/strong-virtualnyj-nomer-ukrainy-ot-hottelecom-svjaz-bez-granic-dlja-biznesa-i-ne-tolko-strong/
Москва в ночь не дремлет, а наша команда вдобавок всегда на страже: закрытая центр лечения алкоголизма клиника https://mcnl.ru/ работает 24/7. Без предварительной регистрации и формальностей — приезд врача к вам, мягкий детокс под контролем, сверхскоростная капельница, психотерапия на дому, пожизненное сопровождение. Тайно, конфиденциально, эффективно — вернем трезвость без боли.
Why viewers still make use of to read news papers when in this technological globe all is available on web?
Limousine service near me
I blog often and I really appreciate your content. The article has really peaked my interest. I am going to bookmark your blog and keep checking for new information about once a week. I opted in for your Feed as well.
porno lezbi
Your article helped me a lot, is there any more related content? Thanks!
Наткнулся через Google на огэ математика банк заданий фипи, когда искал материалы с официального сайта. Здесь всё аккуратно собрано, структурировано по темам, ничего не надо искать вручную. Решаю прямо с телефона, экономлю кучу времени. Очень рекомендую тем, кто готовится сам.
Если вы давно мечтаете изучать психологию онлайн, но не знаете, с чего начать — рекомендую обратить внимание на ILM Академию. Это современная платформа, где можно пройти курс по психологии с дипломом без отрыва от работы или семьи.
Программа идеально подойдёт новичкам: всё объясняется простым языком, много практики и живых встреч с преподавателями. В конце обучения вы получите европейский диплом, который ценится и в Украине, и за её пределами.
Отличный выбор для тех, кто хочет начать карьеру в психологии или лучше понять себя и окружающих.
Вариант второй текста:
Хочешь получить профессию психолога, не выходя из дома?
ILM Академия — это современное онлайн-обучение психологии с упором на практику и живое общение с опытными преподавателями.
Обучение доступно из любой точки мира
Подходит для начинающих — всё с нуля
Практика, супервизии и поддержка кураторов
Европейский диплом после окончания курса
Ты сможешь освоить профессию, понять людей глубже и, возможно, даже изменить свою жизнь.
Подробнее о курсе на официальном сайте: ILM Академия психологии европейское образование по психологии онлайн
Hi, everything is going perfectly here and ofcourse every one is sharing data, that’s actually excellent, keep up writing.
https://startupline.com.ua/vartist-vidnovlennya-far-audi-svoyimy-rukamy.html
Today, while I was at work, my cousin stole my apple ipad and tested to see if it can survive a twenty five foot drop, just so she can be a youtube sensation. My apple ipad is now destroyed and she has 83 views. I know this is entirely off topic but I had to share it with someone!
https://www.google.hn/url?sa=t&url=https://premierlimousineservice.net
Keep on working, great job!
https://cse.google.com.uy/url?sa=t&url=https://premierlimousineservice.net
Lopesan Costa Bavaro Airport Shuttle
The Lopesan Costa Bavaro Airport Shuttle is a private, direct transfer for groups of up to six, ensuring no stops or delays with other passengers.
Distance from Lopesan Costa Bavaro Resort to Punta Cana Airport
How far is Lopesan Costa Bavaro from airport? punta cana airport to lopesan costa bavaro The Lopesan Costa Bavaro Resort, Spa & Casino is approximately 10.9 miles (18 km) from Punta Cana International Airport (PUJ). The drive typically takes about 17-30 minutes, depending on traffic conditions.
Lopesan Costa Bavaro Airport Shuttle
The Lopesan Costa Bavaro Airport Shuttle lopesan costa bavaro to airport is a private, direct transfer for groups of up to six, ensuring no stops or delays with other passengers.
Distance from Lopesan Costa Bavaro Resort to Punta Cana Airport
How far is Lopesan Costa Bavaro from airport? The Lopesan Costa Bavaro Resort, Spa & Casino is approximately 10.9 miles (18 km) from Punta Cana International Airport (PUJ). The drive typically takes about 17-30 minutes, depending on traffic conditions.
Appreciating the dedication you put into your website and detailed information you provide. It’s great to come across a blog every once in a while that isn’t the same old rehashed information. Wonderful read! I’ve bookmarked your site and I’m including your RSS feeds to my Google account.
порнорассказ
Why visitors still make use of to read news papers when in this technological globe all is presented on web?
https://maps.google.com.gh/url?sa=t&url=https://premierlimousineservice.net
Useful information. Lucky me I discovered your web site accidentally, and I am shocked why this accident did not came about in advance! I bookmarked it.
https://keslaser.com.ua/sklo-fary-dlya-audi-a1-osoblyvosti-vyboru.html
Simply wish to say your article is as amazing. The clearness in your post is simply nice and i could assume you are an expert on this subject. Fine with your permission let me to grab your RSS feed to keep updated with forthcoming post. Thanks a million and please continue the gratifying work.
spin city casino
Hi, all the time i used to check webpage posts here in the early hours in the break of day, for the reason that i enjoy to learn more and more.
where buy generic vermox prices
В поиске Яндекса ввёл «ОГЭ банк заданий по математике», и выдало сайт огэ математика банк заданий. Полезнейшая находка! Там все задачи из официальной базы, с решениями и пояснениями. Теперь готовлюсь по ним — удобно и намного эффективнее, чем по тетрадям.
Escape the Limits – Explore Non GamStop Casinos!
Tired of restrictions? Discover a world of unlimited gaming possibilities at our Non GamStop Casinos.
What we offer:
– Unrestricted access to top games
– Generous welcome bonuses
– Lightning-fast payouts
– 24/7 customer support
– Secure & fair gaming environment
Join thousands of satisfied players who have already found their perfect gaming experience. No GamStop limitations mean endless fun and excitement!
Claim your bonus now and start playing at the best Non GamStop Casinos today! ??
https://vaishakbelle.com/no-verification-casinos/
#NonGamStopCasinos #OnlineGaming #CasinoBonus