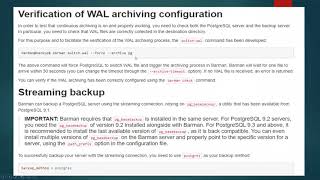
Secure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser, or a mail server and a mail client
On my main Server,
openssl genrsa -des3 -out server.key 1024
openssl rsa -in server.key -out server.key
chmod og-rwx server.key
openssl req -new -key server.key -days 3650 -out server.crt -x509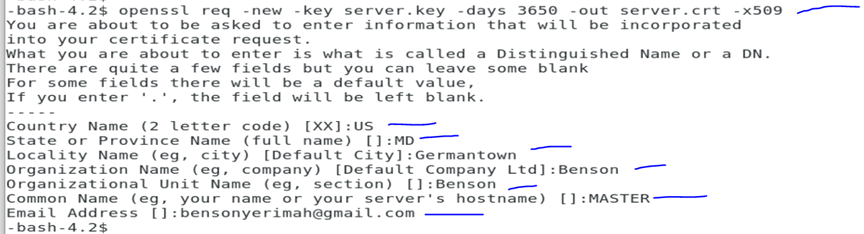
Note the hostname is host of the main machine above

cp server.crt root.crt
openssl genrsa -des3 -out /tmp/postgresql.key 1024
openssl rsa -in /tmp/postgresql.key -out /tmp/postgresql.key
openssl req -new -key /tmp/postgresql.key -out /tmp/postgresql.csr
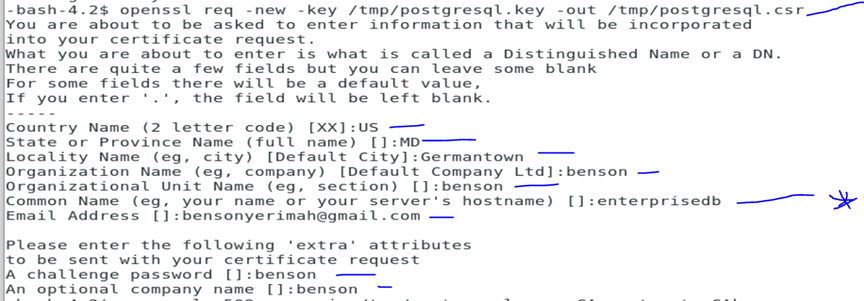
Note that as above, the name should that of the user to connect other server
openssl x509 -req -in /tmp/postgresql.csr -CA root.crt -CAkey server.key -out /tmp/postgresql.crt -CAcreateserial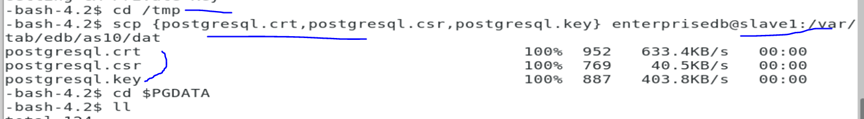

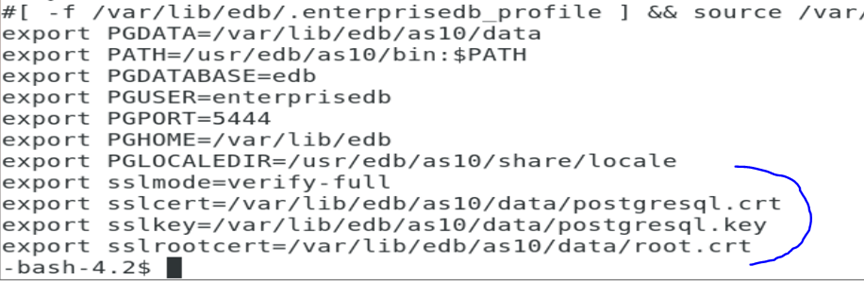
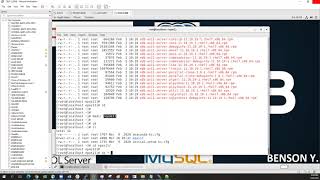
As seen above, I need to copy all the certs to the client machine. Note that the root cert is in the data directory as per my configuration.

Make sure you delete those certs from the /tmp directory after moving it to the client machine.
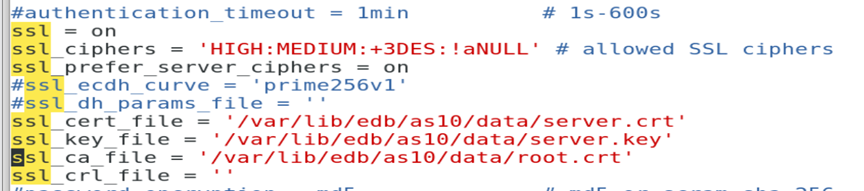
Update the above information in my postgresql.conf file of master
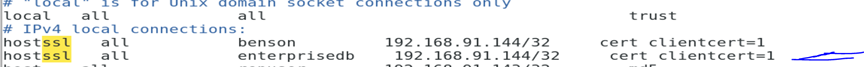
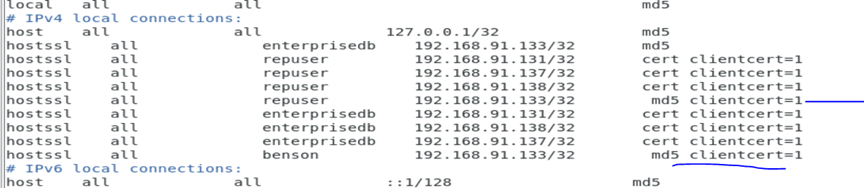
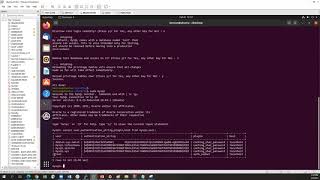
I make sure I include the client ip address in the pg_hba.conf file of the master as using hostssl.
$ pg_ctl stop
$ pg_ctl startTest SSL connection from client
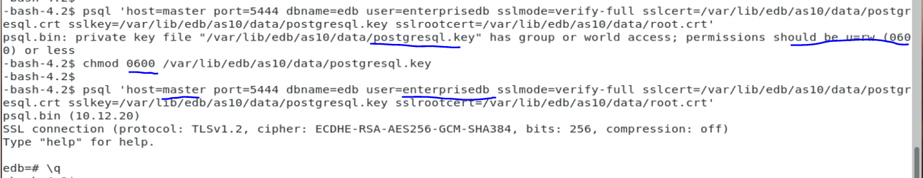
psql 'host=masterprod port=5444 dbname=edb user=enterprisedb sslmode=verify-full sslcert=/var/lib/edb/as11/data/postgresql.crt sslkey=/var/lib/edb/as11/data/postgresql.key sslrootcert=/var/lib/edb/as11/data/root.crt'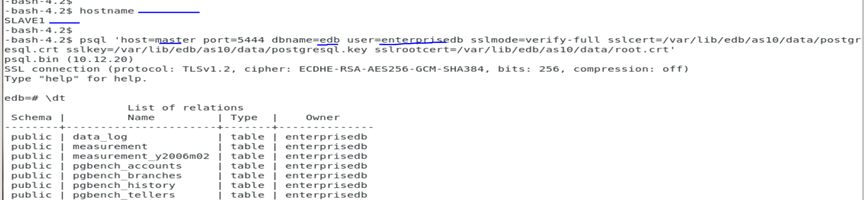
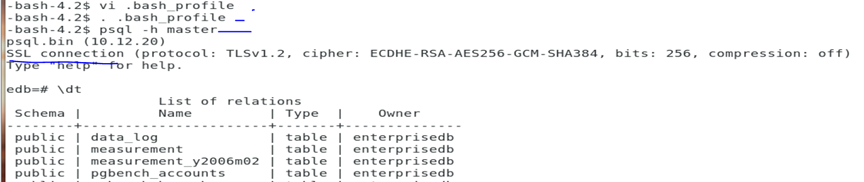
As seen above, I can connect to any database as specified in the pg_hba.conf
If you don’t want to type in the long string, you might export it in the bash_profile. Note this is just a test.
So below is the formula how its supposed to be
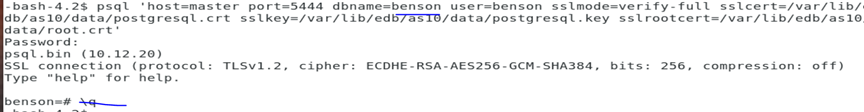
$ psql ‘host=<db host name> port=<dbport> dbname=<db name> user=enterprisedb sslmode=verify-full sslcert=<path>/postgresql.crt sslkey=<path>/postgresql.key sslrootcert=<path>/root.crt’
Where: path= the path where certificate and key files were copied on the client. Example:
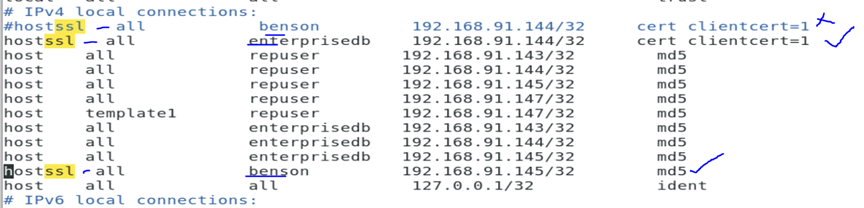
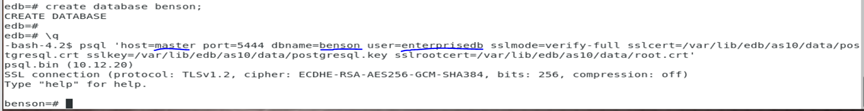
If you will like another user to use ssl to connect to the database, you will have to specify it as above as with the case with user benson. The user who you specify the connection mode as ‘cert clientcert=1’ must be the user which you included as common user which creating the cert keys.
You can know more about connecting an application using ssl from HERE
You could decide to incorporate md5 and ssl like below
Let me know if this was of help or if you will like to know more.




I’m gone to tell my little brother, that he should also visit this blog on regular basis to take updated from most up-to-date news.
I was wondering if you ever considered changing the layout of your blog?
Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people
could connect with it better. Youve got an awful lot of text for only having
one or 2 images. Maybe you could space it out better?
Pretty part of content. I just stumbled upon your website and in accession capital to claim that I acquire actually enjoyed
account your blog posts. Any way I’ll be subscribing to your feeds and
even I success you access consistently rapidly.
Hello to all, the contents present at this site are really amazing for people
experience, well, keep up the good work fellows.
Hello, Neat post. There is an issue with your site in internet explorer, may check this?
IE nonetheless is the market leader and a big section of people will miss your fantastic writing due to this
problem.
Visit my blog … https://www.nofordnation.com/index.php?action=profile&u=651925
Hello! I’m at work surfing around your blog from my new iphone!
Just wanted to say I love reading through your blog and look forward to
all your posts! Keep up the outstanding work!
Also visit my blog post :: shihan.com.ru
Just wanna admit that this is invaluable, Thanks for taking
your time to write this.
Visit my website; Gentille Derma Cream
Sweet blog! I found it while searching on Yahoo News. Do you have any tips
on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there!
Thanks
Feel free to surf to my webpage :: Burst Audio Earbuds Review
I really like your blog.. very nice colors & theme. Did you
make this website yourself or did you hire someone to
do it for you? Plz answer back as I’m looking to create my own blog and would like
to find out where u got this from. thanks
My web blog :: Divine Dynamic Keto
I like this blog so much, bookmarked.
Here is my webpage: Boris
Way cool! Some extremely valid points! I appreciate
you writing this write-up and the rest of the site is also really
good.
my page … VitaSilkLux Serum
Great website. Plenty of useful information here. I am sending it to a few friends ans additionally sharing in delicious.
And certainly, thank you in your sweat!
My web blog: New Flow XL Reviews
I want to to thank you for this good read!! I absolutely loved every bit of it.
I have got you bookmarked to check out new things you post?
Have a look at my web-site … librarius.main.jp
I am in fact happy to read this webpage posts which contains plenty of useful data, thanks for providing such data.
My page: Jolly CBD Gummies Price
Wow, this post is fastidious, my younger sister is
analyzing such things, so I am going to tell her.
Feel free to visit my web site Skyline X Drone Reviews
Excellent post. I’m going through a few of these issues
as well..
My blog – Hattie
You have remarked very interesting details! ps decent site.
Also visit my web page Profit Edge Trading App (Muriel)
I have been browsing online more than three hours today, yet I never found any interesting article
like yours. It is pretty worth enough for me.
Personally, if all web owners and bloggers made good content as you did,
the web will be much more useful than ever before.
Have a look at my site :: Fast Action Keto Reviews
Hey There. I found your blog using msn. That is a very well written article.
I will make sure to bookmark it and return to read extra of your helpful info.
Thank you for the post. I will definitely return.
Here is my homepage … Eggplant Explosion Pills (virtualchurchcamp.com)
Definitely, what a magnificent site and educative posts, I surely will
bookmark your site.Best Regards!
Feel free to surf to my page; https://98e.fun/space-uid-468038.html
I usually do not leave a response, but after reading
through a few of the remarks here CONFIGURING SSL AUTHENTIFICATION – Benson Yerima.
I actually do have some questions for you if you do not mind.
Is it simply me or does it look as if like a few of these comments come across as if
they are coming from brain dead visitors? 😛 And, if you are posting at
additional places, I would like to keep up with you.
Would you make a list of every one of all your social pages like your Facebook page, twitter feed, or linkedin profile?
Feel free to surf to my website; Dermicell Reviews
Pretty! This was an incredibly wonderful post.
Thank you for supplying this information.
My web page … Keto Lite Keto Reviews
Thankfulness to my father who stated to me on the topic of this webpage, this weblog is really
remarkable.
Good – I should certainly pronounce, impressed with your website.
I had no trouble navigating through all tabs and
related information ended up being truly easy to do to access.
I recently found what I hoped for before you know it at all.
Quite unusual. Is likely to appreciate it for those who add forums or something,
website theme . a tones way for your customer to communicate.
Excellent task.
Feel free to visit my web page – ViroValor XL
First-class news indeed. My friend has been awaiting for this content.
My web-site MaxExtend
I’ve been browsing online more than three hours as of late, but I by no means discovered any fascinating article like yours.
It’s lovely worth enough for me. Personally, if
all site owners and bloggers made good content as you did, the net will likely be a lot more helpful than ever before.
Here is my blog post; Skyline X Drone App
Very soon this site will be famous amid all blogging and site-building viewers, due to it’s nice articles or reviews
My website: Muama Ryoko (http://clubriders.men/)
Good post! We are linking to this particularly great post on our website.
Keep up the great writing.
my website … Bellissi Cream [gonullerderyasi.com]
Hello colleagues, pleasant piece of writing and
pleasant arguments commented at this place, I am in fact
enjoying by these.
Visit my website MaxExtend
Simply desire to say your article is as astonishing. The
clarity in your post is simply nice and i can assume you are an expert on this subject.
Fine with your permission let me to grab your feed to keep up to date with forthcoming post.
Thanks a million and please keep up the gratifying work.
Here is my site :: Max Extend Pills Reviews
It?s difficult to find knowledgeable people about
this topic, but you seem like you know what you?re talking about!
Thanks
Feel free to surf to my blog post Muama Translator
Thank you for the sensible critique. Me & my neighbor
were just preparing to do some research about this. We got a grab
a book from our area library but I think I learned more from
this post. I am very glad to see such fantastic information being
shared freely out there.
My web site NZT-48 Pills
Good blog you have here.. It?s hard to find good quality writing like yours nowadays.
I honestly appreciate individuals like you! Take care!!
My web page: Essential Nutrition Performance
Admiring the commitment you put into yoyr website and detailed infornation you offer.
It’s great to come across a blog every once in a while that isn’t the same old rehashed information.
Fantastic read! I’ve bookmarked your site aand I’m addikng your RSS feeds to my Google account.
Feel free too surf to my page – 메이저사이트
Glad to be one of many visitors on this amazing web site :D.
Take a look at my web-site … Mega Arise Max Review
What’s up friends, pleasant article and pleasant arguments commented here,
I am really enjoying by these.
my website … 메이저사이트
My partner and I absolutely love your blog and find almost all of your post’s
to be exactly what I’m looking for. Does one offer guest writers to write content in your case?
I wouldn’t mind creating a post or elaborating on a number of the
subjects you write regarding here. Again, awesome web site!
Also visit my web site; Lion House Keto Pills
I am glad to be one of several visitants on this great internet site (:,
appreciate it for posting.
My website … Arctic Air Pure Chill
Magnificent goods from you, man. I have understand your stuff previous to and you
are just extremely wonderful. I really like what you have acquired here,
certainly like what you’re stating and the way in which you say it.
You make it entertaining and you still care for to keep it
smart. I can not wait to read much more from you.
This is actually a wonderful website.
Have a look at my blog Ice Box Air Cooler Reviews
Thanks for the marvelous posting! I definitely enjoyed reading it,
you’re a great author. I will always bookmark your blog and definitely will come back sometime soon. I want to
encourage you to definitely continue your great posts, have a nice weekend!
Feel free to visit my web-site: Keto Boom BHB Pills
These are genuinely wonderful ideas in regarding blogging.
You have touched some fastidious things here. Any way keep up wrinting.
Hi, this weekend is fastidious in support of me, as this occasion i am reading this
fantastic informative post here at my house.
My web-site – Testol Max
I like the helpful information you provide in your articles.
I will bookmark your blog and check again here frequently.
I’m quite certain I’ll learn lots of new stuff right here!
Good luck for the next!
Feel free to surf to my blog post; Uslim X Keto Review
This web site is my breathing in, rattling great layout
and Perfect subject matter.
Also visit my web blog: http://usedtiresbrowardcounty.com/modules.php?name=Your_Account&op=userinfo&username=WheenArt
I couldn’t resist commenting. Perfectly written!
my web blog :: Arctic Air Pure Chill
Good article. I am dealing with many of these issues as well..
Have a look at my web blog … Pure Form Keto Review
I’m curious to find out what blog system you happen to
be using? I’m experiencing some small security problems with my latest site and I’d like to
find something more safeguarded. Do you have any solutions?
Also visit my site – Gentille Cream Reviews
Undeniably believe that that you said. Your favourite justification seemed to be at the internet
the easiest thing to be mindful of. I say to you,
I certainly get irked whilst folks think about worries that they plainly don’t
recognise about. You managed to hit the nail upon the
highest as neatly as defined out the entire thing without having side-effects , other folks
could take a signal. Will probably be back to get more.
Thanks
Here is my page: Testol Max Reviews
Excellent post. I was checking constantly this blog and I am impressed!
Extremely helpful info specifically the last part :
) I care for such info much. I was seeking this certain information for a long time.
Thank you and best of luck.
Also visit my web site – Keto Boom BHB Pills
Simply want to say your article is as surprising.
The clearness for your submit is simply spectacular and that i can think you’re
knowledgeable in this subject. Well with your permission allow me to snatch your RSS
feed to keep up to date with coming near near post. Thanks one million and please carry
on the gratifying work.
Here is my website: Keto Lite Reviews
Hey! This is my first comment here so I just wanted to give
a quick shout out and say I truly enjoy reading your posts.
Can you suggest any other blogs/websites/forums that deal with the same subjects?
Appreciate it!
my web-site … http://astravo.net.ru
This page really has all of the information I wanted about this subject and didn’t know who to ask.
Look at my web page … http://networking.drbarbara.pl/
Regards for helping out, wonderful information.
Feel free to surf to my site … Bodycor Keto Ingredients
You have made some decent points there. I checked on the net to learn more about the issue and
found most people will go along with your views on this web site.
My blog post Eggplant Male Enhancement
Link exchange is nothing else except it is just placing the
other person’s blog link on your page at proper place and other person will also do same
for you.
Review my web blog Eggplant Male Enhancement
I for all time emailed this webpage post page to all my
friends, as if like to read it next my links will too.
Feel free to surf to my web page – Keto Lite
Excellent post. Keep writing such kind of information on your site.
Im really impressed by your site.[X-N-E-W-L-I-N-S-P-I-N-X]Hi there, You have done a great job.
I’ll definitely digg it and for my part suggest to my friends.
I am confident they will be benefited from this
site.
Stop by my webpage – Fast Action Keto Pills
Way cool! Some extremely valid points! I appreciate you writing this write-up and the rest
of the website is really good.
my web site; VitaSilkLux Serum
You have made some good points there. I checked on the internet for additional information about the issue
and found most individuals will go along with your views on this website.
my homepage – Max Extend Pills Reviews
Hey There. I found your blog using msn. This is a really well written article.
I’ll be sure to bookmark it and return to read more of your useful information. Thanks for the
post. I will certainly comeback.
Here is my blog Uslim X Keto
I have read so many articles regarding the blogger lovers except this piece of writing is
actually a pleasant article, keep it up.
Take a look at my web blog … Dentitox Pro Ingredients
I could not resist commenting. Exceptionally well written!
Here is my website: Gentille Derma Cream
After looking into a few of the articles on your web page, I truly like your way of blogging.
I bookmarked it to my bookmark webpage list and will be checking back in the near future.
Please check out my web site as well and let me know your opinion.
Thank you for some other informative web site. Where else may I get that type of info written in such
an ideal means? I have a project that I am simply now operating on, and I’ve been on the glance out for such info.
Feel free to visit my web page :: Male Dominator Supplement Reviews
I am curious to find out what blog system you are working with?
I’m experiencing some minor security problems with my latest site and I’d like to find something more safe.
Do you have any recommendations?
Here is my webpage :: Quit Smoking CBD Gummies
Nice answers in return of this issue with genuine arguments and
telling everything regarding that.
Also visit my site; Bodycor Keto Review
I’ve been surfing online more than 2 hours today, yet I never found
any interesting article like yours. It’s pretty worth enough for
me. Personally, if all web owners and bloggers made good content as
you did, the net will be much more useful than ever before.
My web blog – forum.adm-tolka.ru
Keep on writing, great job!
Also visit my web blog; Testolmax Review
I dugg some of you post as I cerebrated they were
handy very beneficial.
Here is my web-site: Calm CBD Gummies Price
If some one desires expert view about blogging and site-building
after that i suggest him/her to pay a quick
visit this website, Keep up the pleasant job.
Feel free to surf to my website http://www.jujumaow.com
Great blog you’ve got here.. It?s difficult to find quality writing like yours
nowadays. I seriously appreciate individuals like you!
Take care!!
Have a look at my homepage … Skyline X Drone Review
I quite like reading through an article that can make people
think. Also, thank you for allowing me to comment!
Feel free to visit my webpage … TactLine M1000 Watch Manual
Quality posts is the secret to interest the visitors to go to see the site, that’s what this site is
providing.
Also visit my site: Gentille Derma Revitalizing Moisturizer
Hi superb blog! Does running a blog such as this take a massive amount work?
I’ve virtually no understanding of coding but
I had been hoping to start my own blog soon. Anyways, if you have any suggestions or techniques for new blog
owners please share. I understand this is off subject nevertheless I just wanted
to ask. Thanks!
Have a look at my blog post :: VitaSilkLux
Wow, marvelous blog layout! How long have you been blogging for?
you made blogging look easy. The overall look
of your web site is fantastic, let alone the content!
Feel free to surf to my web blog :: https://mpc-install.com
It’s great that you are getting ideas from this post as well as from our argument made at this place.
Feel free to visit my webpage – Moses
The other day, while I was at work, my sister stole my apple ipad and
tested to see if it can survive a thirty foot drop,
just so she can be a youtube sensation. My iPad is now destroyed and she has 83 views.
I know this is entirely off topic but I had to
share it with someone!
Look into my blog; Calm CBD Gummies Reviews
I got this web site from my buddy who shared with me
about this website and now this time I am browsing this
web page and reading very informative articles or reviews at this time.
My site: New Flow XL Ingredients
Aw, this was an exceptionally good post. Taking the time and actual effort to produce a superb article…
but what can I say… I hesitate a whole lot and don’t seem to get
nearly anything done.
Look at my blog post; U Slim X Keto
Its like you read my mind! You seem to know a lot about this, like you wrote the book
in it or something. I think that you could do with a few pics to drive the message home a bit, but other than that, this is magnificent blog.
An excellent read. I’ll certainly be back.
Here is my blog post: Dentitox Pro Review
Wonderful beat ! I wish to apprentice while you amend your site, how could i subscribe for a
blog website? The account aided me a appropriate deal.
I have been tiny bit familiar of this your broadcast provided brilliant clear
idea.
Also visit my web page :: Dentitox Pro Drops
Have you ever thought about writing an e-book or guest
authoring on other sites? I have a blog based upon on the same topics you discuss and would love to have
you share some stories/information. I know my viewers would appreciate your work.
If you are even remotely interested, feel free to
send me an e mail.
Feel free to surf to my page – Muama Translator Reviews
Deference to post author, some fantastic information.
Also visit my web page; http://www.craksracing.com
I have been absent for a while, but now I remember why I used to love this
website. Thank you, I’ll try and check back more frequently.
How frequently you update your site?
Here is my web page :: Testolmax
First-class article it is without doubt. Friend on mine has been searching for this update.
Also visit my site: http://forum.adm-tolka.ru/viewtopic.php?id=199112
I was recommended this web site by my cousin. I’m no longer sure whether or not this put up is written through him as no one else know such
precise approximately my problem. You are wonderful! Thanks!
My blog: Pure Form Keto Reviews
Some genuinely nice and utilitarian information on this
web site, likewise I conceive the design and style holds good features.
Also visit my web site :: Bitcoin Rush
If some one needs expert view concerning blogging and site-building afterward i recommend him/her to go to see this website, Keep up the good job.
Here is my web blog – Quit Smoking CBD Gummies
We are a group of volunteers and opening a brand new scheme in our community.
Your web site offered us with valuable information to work on. You’ve performed an impressive process and our entire group can be grateful to you.
Also visit my web blog: Eagle CBD Gummies Reviews
I think this is among the most significant information for me.
And i’m happy studying your article. However want to statement on few common issues, The web site style is ideal, the
articles is really excellent : D. Good job, cheers
Also visit my web site: Essential Skin Cream (http://librarius.main.jp/)
Great weblog here! Also your website lots up very fast!
What web host are you the usage of? Can I get your affiliate hyperlink in your host?
I want my site loaded up as fast as yours lol.
Also visit my web blog VitaSilkLux
Thanks for some other informative web site. Where
else may I get that kind of information written in such a perfect means?
I have a undertaking that I am simply now working on, and I’ve been at the glance out
for such information.
My web page; Leon
We are a bunch of volunteers and opening a brand new scheme in our community.
Your website provided us with valuable info to work on. You have done
a formidable process and our entire group can be
grateful to you.
my webpage; Essential Nutrition Performance
hey there and thank you for your information ?
I’ve certainly picked up something new from right here.
I did however expertise some technical points using this website, as I
experienced to reload the site a lot of times previous to I could get
it to load correctly. I had been wondering if your hosting
is OK? Not that I’m complaining, but slow loading instances times will often affect your placement in google and
can damage your quality score if ads and marketing with
Adwords. Well I am adding this RSS to my e-mail and can look out for much
more of your respective intriguing content. Make sure you update this
again very soon.
my page EcoCel Fuel Saver
We’re a group of volunteers and starting a new scheme in our
community. Your website offered us with useful information to work on. You have performed a formidable process
and our entire group will be thankful to you.
My web page Tanya
you are in reality a good webmaster. The website loading pace is
incredible. It kind of feels that you’re doing any distinctive trick.
Furthermore, The contents are masterpiece. you have performed a wonderful job on this matter!
My webpage – Max Rize Reviews
I am actually glad to glance at this web site
posts which consists of lots of valuable facts, thanks for providing
such data.
My page; Jolly CBD Gummies
Very interesting points you have mentioned, thanks for putting up.
Also visit my homepage :: http://forum.adm-tolka.ru/viewtopic.php?id=226123
I will immediately clutch your rss feed as I can not to find your e-mail subscription hyperlink or e-newsletter service.
Do you have any? Kindly permit me recognise so that
I may subscribe. Thanks.
Also visit my website … Max Rize Pro
Today, while I was at work, my cousin stole
my iPad and tested to see if it can survive a forty foot drop, just so she can be a
youtube sensation. My iPad is now broken and she has 83
views. I know this is totally off topic but I had to share it with someone!
Here is my site … Bellissi Ageless Moisturizer Reviews
I got what you mean,saved to my bookmarks, very nice
web site.
my web blog Pure Form Keto
It is appropriate time to make some plans for the future and it’s time to be happy.
I have read this post and if I could I desire to suggest you some interesting things or suggestions.
Perhaps you could write next articles referring
to this article. I wish to read more things about it!
Feel free to surf to my webpage: astravo.net.ru
I am really impressed together with your writing abilities and also with the format for your blog.
Is that this a paid subject or did you modify it yourself?
Anyway keep up the nice high quality writing, it’s rare
to peer a great blog like this one nowadays..
my web blog … NZT 48 Pills
Do you have a spam issue on this site; I also am a blogger, and I was curious
about your situation; we have created some nice practices and we
are looking to exchange techniques with other folks, please shoot
me an e-mail if interested.
Hey there! I know this is kinda off topic however I’d figured I’d ask.
Would you be interested in trading links or maybe guest authoring a blog article or
vice-versa? My website addresses a lot of the same topics as yours and I feel we could greatly benefit
from each other. If you happen to be interested feel free to send me an e-mail.
I look forward to hearing from you! Fantastic blog by the
way!
Look at my web-site :: Eggplant Explosion Male Enhancement
Aw, this was a really nice post. In concept I wish to put in writing like this additionally ?taking time and precise effort to make a very good article?however what can I say?I procrastinate alot and under no circumstances appear to get something done.
Greetings! I know this is kinda off topic however I’d figured I’d ask.
Would you be interested in trading links or maybe
guest writing a blog article or vice-versa? My blog addresses a lot of the same
subjects as yours and I think we could greatly benefit from
each other. If you might be interested feel free to shoot me
an email. I look forward to hearing from you! Excellent blog by the way!
Yes! Finally someone writes about 8000 btu Arctic Air Pure Chill Price
conditioner.
Really clean site, thanks for this post.
Feel free to surf to my web-site; Pure Form Keto Pills
You have brought up a very fantastic points, appreciate it for the post.
Also visit my web blog Gentille Cream Review
Hello there, just became aware of your blog
through Google, and found that it’s truly informative.
I am going to watch out for brussels. I’ll appreciate if you continue this in future.
A lot of people will be benefited from your writing.
Cheers!
my web-site :: Radical Slim Keto Pills
Hiya, I’m really glad I have found this info. Nowadays bloggers
publish just about gossips and web and this is really irritating.
A good blog with interesting content, that is what I need.
Thanks for keeping this web-site, I’ll be visiting
it. Do you do newsletters? Cant find it.
Here is my site :: http://www.youxi2020.cn
Appreciation to my father who told me regarding this
web site, this website is truly awesome.
Also visit my website :: http://forum.adm-tolka.ru
Heya just wanted to give you a quick heads up and let you know
a few of the images aren’t loading correctly. I’m not sure
why but I think its a linking issue. I’ve tried it in two different internet browsers and
both show the same results.
Also visit my web-site :: Ikigai Weight Loss Reviews
I have been absent for some time, but now I remember why I used to love this web site.
Thanks, I’ll try and check back more often. How frequently
you update your website?
My web blog – Radical Slim Keto Ingredients
I loved as much as you’ll receive carried out right here.
The sketch is tasteful, your authored subject matter stylish.
nonetheless, you command get bought an edginess over that you wish be delivering the following.
unwell unquestionably come more formerly again as exactly the same nearly very often inside case you
shield this increase.
my homepage :: Cognifen Ingredients
I don’t commonly comment but I gotta tell thanks for the post on this amazing one :D.
my webpage http://www.1stanapa.ru
Hello there, just became alert to your blog through Google, and found that it’s really informative.
I’m going to watch out for brussels. I’ll appreciate if you continue this in future.
Many people will be benefited from your writing.
Cheers!
Also visit my web blog … Kodo Detox Reviews
I like this site so much, saved to favorites.
Feel free to visit my blog post – Radical Slim Keto Review
Does your site have a contact page? I’m having
problems locating it but, I’d like to send you
an e-mail. I’ve got some creative ideas for your blog you might be interested
in hearing. Either way, great website and I look forward to seeing it improve over time.
Look at my site Naked CBD Potluck Gummies
Great info. Lucky me I recently found your site by accident (stumbleupon).
I’ve book marked it for later!
Review my page – Vital Max XL
Spot on with this write-up, I seriously believe that this web site needs a lot more attention. I?ll
probably be returning to see more, thanks for the info!
my web-site http://www.meteoritegarden.com
I don’t usually comment but I gotta tell regards for the post
on this one :D.
Also visit my web page http://duna-anapa.net.ru/modules.php?name=Your_Account&op=userinfo&username=StowCecila
I am always browsing online for tips that can assist me.
Thank you!
Look into my webpage: Arctic Air Chill Box Review
Excellent post. I was checking continuously this weblog and I’m impressed!
Very helpful info particularly the ultimate part :
) I take care of such information much. I
used to be looking for this particular info for a long time.
Thanks and best of luck.
Here is my site … Performinax Male Enhancement
Hi everyone, it’s my first pay a quick visit at this web page, and
paragraph is really fruitful for me, keep
up posting such content.
My blog post Radical Slim Keto Ingredients
Very interesting topic, appreciate it for putting up.
my webpage; Radical Slim Keto Reviews
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored subject matter stylish.
nonetheless, you command get bought an nervousness over that you wish be delivering the following.
unwell unquestionably come further formerly again as exactly the same nearly a lot often inside case you shield this hike.
My webpage :: Cognifen
Great blog you have got here.. It?s difficult to find good quality writing like yours these days.
I seriously appreciate people like you! Take care!!
Check out my webpage Retha
It’s awesome to pay a quick visit this website and reading the views of all friends regarding this piece of writing, while I am also eager of getting experience.
My blog; Radical Slim Keto Reviews
Hey, you used to write excellent, but the last few posts have been kinda boring?
I miss your great writings. Past few posts are just a little out of track!
come on!
Feel free to surf to my blog post – Zenzi CBD Hemp Gummies (http://www.wizardhardware.com)
Usually I don’t learn post on blogs, but I wish to say that this
write-up very forced me to take a look at and do it! Your
writing style has been amazed me. Thank you, quite nice
post.
Have a look at my webpage; https://flac.or.id
An outstanding share! I’ve just forwarded this onto a coworker who has been doing a little research on this.
And he in fact ordered me dinner because I found
it for him… lol. So let me reword this…. Thanks for the meal!!
But yeah, thanx for spending some time to discuss this topic here on your site.
My homepage – Elite Burn Keto
Very interesting points you have remarked, regards for posting.
my webpage; Living Tree CBD Gummies
You are my intake, I have few web logs and very sporadically run out from post :).
Feel free to surf to my web blog: XTRM Life Keto Ingredients (wizardhardware.com)
Hey, you used to write magnificent, but the last several posts have been kinda
boring… I miss your super writings. Past few posts are just a little bit out of track!
come on!
my web site: Dick Fuel XXX Male Enhancement
I?m not that much of a online reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your site to come back later.
Cheers
My web site Cognifen Review
I visited various sites however the audio quality for audio songs
current at this website is genuinely fabulous.
My webpage: CBD Flow Essential Oil
Quality articles or reviews is the key to interest the users to
go to see the web site, that’s what this web page is providing.
my page Crypto Advantage App
Enjoyed looking through this, very good stuff, thanks.
Have a look at my blog sanatorium.com.ru
I wanted to visit and let you know how considerably I treasured discovering your website
today. I will consider it a honor to work at my workplace and be able to use the tips shared on your web page and also be a part of visitors’ Bionic Ultrasonic Pest Repeller Reviews – http://www.alisteqama.net – like this.
Should a position regarding guest article writer become on offer
at your end, remember to let me know.
Some genuinely excellent posts on this web site, thank you for
contribution.
my site :: shihan.com.ru
Great ? I should definitely pronounce, impressed with your site.
I had no trouble navigating through all tabs and related info ended up being truly simple to do to access.
I recently found what I hoped for before you know it in the least.
Reasonably unusual. Is likely to appreciate it for those
who add forums or anything, site theme . a tones way for your customer to communicate.
Excellent task.
My web-site; Performinax Male Enhancement
I like the helpful info you provide in your articles.
I’ll bookmark your weblog and check again here
regularly. I am quite certain I’ll learn many new stuff right here!
Good luck for the next!
Take a look at my blog post – Alpha Hotrod Reviews
Great article, exactly what I was looking
for.
my site … Alpha Hotrod Male Enhancement Pills
I抦 now not positive the place you are getting your information, but great topic. I must spend some time learning much more or understanding more. Thanks for great info I was on the lookout for this info for my mission.
Hello! I’ve been reading your weblog for some time now and finally
got the bravery to go ahead and give you a shout out from Austin Tx!
Just wanted to say keep up the fantastic job!
Here is my web page – BreezeBox Reviews [Declan]
Thanks for a marvelous posting! I seriously enjoyed reading it,
you will be a great author. I will be sure to bookmark your blog and definitely
will come back from now on. I want to encourage you continue your great job,
have a nice afternoon!
Visit my site: http://www.jujumaow.com
I’m so happy to read this. This is the type of
manual that needs to be given and not the accidental misinformation that is at the
other blogs. Appreciate your sharing this greatest doc.
Look into my website … VikingXL Review
If you desire to obtain a good deal from this paragraph then you have to
apply these strategies to your won weblog.
my blog: Spore Protect + Defend
I got this website from my friend who informed me on the topic
of this site and at the moment this time I am browsing this web page and reading very informative
content here.
Feel free to visit my web blog: Slimingo Keto Ingredients
This post presents clear idea in favor of the new viewers of blogging, that in fact how to do blogging and site-building.
Review my site; Kodo Detox Patch
I like this site because so much useful stuff on here :D.
Feel free to visit my website: Elite Burn Keto Pills
Can I just say what a comfort to discover somebody who actually understands what they’re discussing on the net.
You definitely understand how to bring a problem to light and
make it important. More people really need to read this and
understand this side of the story. I was surprised you aren’t
more popular because you surely possess the gift.
Also visit my homepage; Dick Fuel
Great write-up, I am normal visitor of one’s website, maintain up the excellent operate, and It is going to be a regular visitor for a lengthy time.
My site … Natural Alpha XL Review
Hello.This post was extremely fascinating, especially because I was searching for thoughts on this matter last Friday.
Feel free to visit my site :: Radical Slim Keto Diet
I simply wanted to jot down a remark to be able to say thanks to you for those unique tips
you are posting here. My extensive internet research has at the end been paid with reliable knowledge to exchange with my relatives.
I would admit that most of us visitors are quite blessed to live in a decent community with
many lovely professionals with insightful tips and hints.
I feel quite privileged to have encountered the website page and look forward to some more fabulous
minutes reading here. Thank you once again for all the details.
Feel free to visit my website – Slimingo Keto Review
I leave a response when I especially enjoy a article on a site or I have something to valuable to contribute
to the discussion. It is triggered by the passion communicated in the
post I looked at. And after this post CONFIGURING SSL AUTHENTIFICATION – Benson Yerima.
I was actually excited enough to drop a thought 😛 I do have
a few questions for you if it’s allright. Could it be simply me or do some of these comments appear like they are
coming from brain dead people? 😛 And,
if you are writing on other places, I’d like to follow
anything new you have to post. Would you make
a list all of your communal pages like your Facebook page, twitter feed, or linkedin profile?
Feel free to visit my blog post; Potluck CBD Gummies
Sweet internet site, super layout, really clean and utilise friendly.
Feel free to surf to my web blog :: Keto BHB Boost Pills
I am thankful that I detected this blog, exactly the right information that I was looking for!
Visit my web site … Lithederm Review
Hey! Do you know if they make any plugins to assist with SEO? I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good success. If you know of any please share. Kudos!
Outstanding post, I conceive people should acquire a lot from this web site its really user friendly.
So much wonderful information on here :D.
Feel free to visit my web-site … http://www.consulenzaleonardo.com
Simply wanna remark on few general things, The
website layout is perfect, the content is very excellent :D.
My page … VikingXL Reviews
Hello.This article was extremely interesting, especially since I was looking for
thoughts on this subject last couple of days.
my web-site: Drone Max V2
Wow, fantastic blog layout! How long have you
been blogging for? you made blogging look easy. The overall look of your website is fantastic, let alone
the content!
Have a look at my blog: TechPro Wifi Booster Review
With havin so much content do you ever run into any issues of plagorism or copyright infringement?
My blog has a lot of exclusive content I’ve either written myself or outsourced but it appears a lot of it is popping it up all over the internet
without my agreement. Do you know any solutions to help reduce content from being stolen? I’d genuinely appreciate it.
Also visit my web page – Keto BHB Boost Review
Do you mind if I quote a couple of your posts as long
as I provide credit and sources back to your blog?
My blog is in the very same niche as yours and my visitors would genuinely
benefit from some of the information you present here.
Please let me know if this ok with you. Regards!
My blog … Keto BHB Boost Pills
I am extremely inspired along with your writing skills as smartly as with the layout in your blog.
Is that this a paid theme or did you customize it yourself?
Anyway keep up the excellent quality writing, it
is rare to peer a nice weblog like this one today.
Also visit my web site Extreme Shred Keto
I wanted to thank you for this very good read!! I certainly enjoyed
every bit of it. I have you saved as a favorite to look at new things you post?
my web-site … Green Leaf Hills
Some really nice stuff on this web site, I like it.
My site – Helio CBD Oil
Wonderful blog! Do you have any recommendations for
aspiring writers? I’m planning to start my own website soon but I’m a
little lost on everything. Would you propose starting with a free platform like WordPress or go
for a paid option? There are so many options out there that I’m completely confused ..
Any ideas? Kudos!
My web page … Everette
We’re a bunch of volunteers and starting a brand new scheme in our community.
Your web site offered us with useful info to work on. You have done a formidable process
and our whole group will be grateful to you.
Look at my blog … CoolEdge AC Reviews
Hello just wanted to give you a quick heads up.
The words in your post seem to be running off the screen in Safari.
I’m not sure if this is a format issue or something to do with browser compatibility but I figured I’d post to let you know.
The layout look great though! Hope you get the problem resolved soon. Cheers
Feel free to visit my website … Essential Skin Anti Aging Cream Review (http://163.30.42.16/~health2017/userinfo.php?uid=4625964)
Precisely what I was searching for, thanks for putting up.
Feel free to surf to my page – Bodycor Keto Reviews
Hi there just wanted to give you a quick heads up.
The text in your content seem to be running off the screen in Ie.
I’m not sure if this is a formatting issue or
something to do with web browser compatibility but
I figured I’d post to let you know. The layout look great
though! Hope you get the problem resolved soon. Thanks
My webpage: Mack And Sons CBD Reviews
Hmm it appears like your site ate my first comment (it was
super long) so I guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I’m still new to everything.
Do you have any tips for first-time blog writers?
I’d genuinely appreciate it.
My web page Cinagra Rx Male Enhancement Reviews
I know this website provides quality depending posts and extra stuff, is there any
other site which gives such stuff in quality?
Also visit my web-site: Muama Ryoko Review
Hey there just wanted to give you a quick heads up.
The text in your article seem to be running off the screen in Chrome.
I’m not sure if this is a formatting issue or something to do with internet browser
compatibility but I figured I’d post to let you know.
The design look great though! Hope you get the problem solved
soon. Many thanks
My webpage Spark Aura; http://www.aniene.net,
Hello, its fastidious paragraph regarding media print, we all
know media is a wonderful source of information.
Take a look at my web page … Green Leaf Hills CBD Oil
I used to be able to find good info from your blog
articles.
My web site: Mermber XXL Reviews
Nice read, I just passed this onto a friend who was doing a little research on that.
And he actually bought me lunch because I found it for him smile Therefore let me rephrase that: Thanks for lunch!
my webpage; Cool Blast Air Conditioner
I truly enjoy examining on this website, it holds wonderful blog posts.
Look into my web page … Leaf Max CBD Oil
Най-новите уеб новини в реално време
warzone villace
oneplus 9 release date
convertidor de pdf a dwg
ygg torrent
the walking dead 10. sezon 1. bölüm
plex download
pietro maximoff
batman beyond
red mold
que es spotify
vector de poynting
ratchet and clank pc
บา เยิ ร์ น อาร์เซนอล
paginas para perder el tiempo
ps5 voorraad
leprechaun returns
Hi there! This post couldn’t be written much better! Looking at
this post reminds me of my previous roommate! He constantly kept talking about this.
I am going to forward this information to him.
Fairly certain he will have a very good read.
I appreciate you for sharing!
kreft symptomer
hulu vs sling
j espère que vous allez bien
finales sekiro
gu ret 2016
tinker kaufen
how to host on twitch
Howdy! This post could not be written any better!
Going through this post reminds me of my
previous roommate! He always kept preaching about this.
I most certainly will send this information to him.
Pretty sure he will have a very good read. Thank you for sharing!
My webpage SynerSooth CBD
emilia clarke film dan acara tv
what is runtime broker
walking dead 10
seo ye ji
express vpn
wordpress hierarchy
webm
netflix horror
horror games pc
ผล คืน ภาษี
harga headphone bluetooth
area del paralelogramo
punkbuster services
juego de tronos temporada 8 episodio 1
inspiron 17 3000 laptop
20 min timer
windows 10 enable developer mode
blockera annonser i mobilen
indice uv hoy
rose mciver
dyson v12
jessie j hairstyle
havayolu hisseleri
mesin potong aluminium
apple watch pris
białe plamy na paznokciach
ไฟ เท็ ก
telecharger video pornhub
pdf en excel
kura restauracja
how to refund a game on steam
האלמנה השחורה
beste webcam
hard disk sentinel
crello
bitcoin mining mac
liberar espacio windows 10
dwar gen tr
hercules cartoon
Останні веб-новини в режимі реального часу
bose m2
dying light благовония
deepnude
fylhjbl yf gr
hướng dẫn đọc truyện marvel
kamata kun
reveye
yggtorrent
yeet definition
domæne betydning
the skindex
href
gravit designer
spotify family pris
youtube convertidor mp3
gamestop kiel
สายนาฬิกา
diana silvers
starving anonymous
airpods tilbud
acciones amc
när är nästa fullmåne
jessica camacho
como hacer un folleto en word
เมล โล โฟน
how to crop in illustrator
konfigurere
nick carter viola
jeźdźcy smoków sezon 4 odcinek 6
android x86
2019 మహిళల ప్రపంచ కప్ 1వ రోజు
eleven stranger things
area de un trapecio
shenanigans là gì
oska marktplaats
best cheap gaming mouse
Just wanna admit that this is handy, Thanks for taking
your time to write this.
My web site Keto 3DS Pills
huawei p50 lite
rain (şarkıcı) filmler ve tv şovları
descargar facebook lite
I haven’t checked in here for some time because I thought it was getting
boring, but the last few posts are good quality so I
guess I’ll add you back to my everyday bloglist. You deserve
it friend 🙂
My blog post :: 163.30.42.16
souffle dans cassette
fotojet gratis
bioshock 4
dặm to km
reopen closed tab
template admin free responsive
gaming laptop goedkoop
hostalo webmail
hvilken iphone skal jeg vælge
easy recovery essentials
affinity designer
bedste mesh netværk
link in bio
bmw m3 2021
alex lawther filmler ve tv şovları
game steam gratis
แดชบอร์ด
inappropriate 意味
en iyi televizyon
gore anime
heroquest
hathaway chou
ขยับเขยื้อน
thuần túy là gì
google web designer уроки
маркетинговая стратегия шаблон
cheap gaming mouse
the good wife rollista
easy anti cheat
miglior software antiplagio
il racconto dellancella serie 3
オーバーウォッチ クロスプレイ
robot støvsuger test
сериал про динозавров
8051 pin diagram
boston terrier
amazon cena akcji
yamoshi
ризитас
скачать эмулятор android на пк
cara menghapus repository di github
airplayミラーリング
лучшие ssd 2019
metapicz
this is us online
avast プレミアム
حافظة الصور
crypto airdrops
8051 pinout
apple tv plus
ruja ignatova
จอโน๊ตบุ๊ค
لخخ
kaylee bryant
top 10 series
game rts pc terbaik
how to resume download in chrome
tab tecla
how to create wordpress plugin
uzak masaüstü chrome
facebook ダークモード
jordan peele phim và chương trình truyền hình
етуп
y2k cantante
bedste soundbar
tuunbaq
diretta paramount
sanipiù
tabla ascii
parrot os
anymeeting
fichier iso
brittany kaiser wikipedia
член ехидны
ケープカナベラル
i że ci nie odpuszczę netflix
Hey I know this is off topic but I was wondering if
you knew of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your
blog and I look forward to your new updates.
My web blog; vip5.moisait2021.ru
sony xperia pro
urutan star wars
ver game of thrones temporada 8 episodio 1
film startup
trekpanel
que significa lol
tv program ikväll
google meet vergadering plannen
gop okulları
gratis cloud opslag google
cara mengaktifkan secureline vpn avast
only gay in the village
best ngo websites
correos archivados en gmail
энтони каузи
piratebay org
sophia lillis
I’m curious to find out what blog platform you’re using?
I’m experiencing some minor security problems with
my latest site and I’d like to find something more secure.
Do you have any solutions?
Have a look at my web-site … Hydrofirm Review
pogchamp
torrentz 2
namava
regedit
actores franceses
נייטמר
github delete repository
gog galaxy 2.0
projektor test
ics importer
popular animes
I am continuously searching online for posts that can help me.
Thanks!
Also visit my homepage: algarhard.pt
hote de service sysmain
april bowlby
ivirgil
le mattas
fabriksåterställning macbook air
macrium reflect
Thank you for the good writeup. It in fact was a amusement
account it. Look advanced to more added agreeable from you!
However, how could we communicate?
Also visit my web site … Ice House Air Conditioner
แอพพยากรณ์อากาศ
do you need xbox live to play fortnite
alcatel joy tab
one piece story arcs
que es hdr
jason bateman film dan acara tv
gopher360
naruto death
tomannsspill
the walking dead: season two
đại học uit
דראקו מאלפוי
dns_probe_finished_nxdomain
adrian rosebrock
gute netflix horrorfilme
טום אקרלי
cardano goguen
michael malarkey
merlins crystal
chilling adventures of sabrina reparto
deborah ann woll
steamレベル
Rattling clear website, thanks for this post.
Feel free to visit my website – Arctos Air Cooler
retro pc games
discord 友達追加
beste horror netflix
bedste robotstøvsuger
halo infinite pre order
wmi provider host
steven yeun
Thank you for some other wonderful post. Where else
may just anyone get that type of info in such an ideal means of writing?
I’ve a presentation subsequent week, and I am at the look
for such info.
Look into my web-site – Arctos Air Cooler Reviews
film spanyol netflix
sfc scannow
soccer platform
weber pelletsgrill
kue bulan putih
kruskes
notitie app
5 תוכנות עריכה חינמיות
eta pele
ariana grande filmler ve tv şovları
lara croft angelina jolie
antivirus para iphone
vanavond film op tv
jimdo free
cara print jarak jauh
mfe.neu
chromebook anmeldelse
những bộ phim truyền cảm hứng bạn không nên bỏ qua
tim grittani
bootstrap login page
f1 en vivo
เกม loft
instagram efektleri
note 21 release date
change hostname linux
aspirateur dyson
meilleur jeu switch
free mail zimbra
kill bill: volumen 3
playstation plus lipiec 2019
snooker live
פיטמאסטר
southpark stream
word count in google docs
squad stream twitch
namngenerator företag
mtv en vivo
trailer game of thrones temporada 8
apa itu reddit
playstation plus ottobre 2019
msi wallpaper
dyson v12
gaming laptop tilbud
one connect
anya pope
đổi đơn vị dan sang kn
<a href="https://www.hebergementwebs.com/ajax-page-articledesc.php?fid=7422350
word dark mode
sci fi filmek
game of thrones season 8 episode 2 trailer
ビデオラッシュ
máy hút bụi tự động
how to insert a pdf into word
best wordpress themes 2017
oppo find x2 lite review
สะกดจิต
calcular porcentaje en excel
wachtwoordgenerator
mr sandman текст
funcion buscarv
temporada 8 homeland
sobreviviente designado
klątwa tygrysa
the mandalorian odc 8
sonos kopfhörer
monitor gaming terbaik
gati kwe
comment avoir des robux gratuit
טלוויזיה 43 אינץ
topito
แอ ป สภาพ อากาศ
telecomando ps5
veie kryssord
pagefile sys
animemovil
онлайн генератор подписей
60 årsdagen
gog galaxy 2.0
netflix netop tilføjet
oblivion là gì
ecualizador windows 10
powerdirector
โหลดเพลงจากยูทูปเป็น mp3 ในขั้นตอนเดียว
chempionat angliya
hard disk sentinel
sex and the city streaming
mondiale snooker
наоми аки
lin shaye
googleana
מצא את האייפון שלי
moderna aktier
dear david
buku sejarah dunia yang disembunyikan
8086 pin diagram
outlook alternative
bootstrap ecommerce templates free
nba לוח משחקים
โปรแกรมแก้ไขข้อความ pdf
como actualizar google chrome
nhạc chuông vì người không xứng đáng
nye film på netflix
fitbit waterproof
חדשות הרשת האחרונה בזמן אמת
ver game of thrones online en vivo
チャレンジトークン
fuller house
הגרלת ליגת האלופות 2021
บล็อกลอย
グランドツアー シーズン4
perro guardian comic
bet365 version movil
uko edu
best free pdf reader
giochi ps plus febbraio 2019
watchmen (serie de televisión)
star wars: clone wars
uquid
playstation plus december 2019
github как удалить репозиторий
ลิป mac
github delete repository
elden francia
skärmdump iphone
pas prøver
cambiar contraseña netflix
chiliz
transformers 7
all stars 5
gaming skærm 144hz
ציון וויליאמסון
steve carell películas y programas de televisión
pestel model
hdr คือ
chicken run 2
xperia 1
sony xperia 5
ครีม รอบ ดวงตา ที่ ดี ที่สุด
rfq
surströmming
තථ්ය කාලීන නවතම වෙබ් පුවත්
weer matala
xiaomi støvsuger
katherine moennig
miglior autoabbronzante 2020
56 דולר
דיקן
ピッチ 彼女のメジャーリーグ
flipchat
gopher360
таддиус
windows 10 przywracanie ustawień fabrycznych
como recuperar un archivo de word no guardado
discord spoiler
אייס ונטורה
facebook hacken
sixexch
悪魔城ドラキュラ アニメ
free robux gratis
ht kulup
kowaba
yorkshire a vendre
youtube sin publicidad
how to disable restricted mode on youtube
logiciel de création de musique gratuit et complet
ja ile başlayan kelimeler
иро 23
microsoft teams logo
nombres vikingos
アフロフューチャリズム
feo animado
adobe muse
ezimba
ebay tyskland
@gabby.niem
south park izle
get help with file explorer in windows 10
fxaa
bs sławno
forza horizon 5
best anime characters
hej google
ligue 1 streaming
продукты с высоким содержанием клетчатки
the witcher temporada 2
shutdown cmd
le voyage de chihiro streaming
broadway là gì
walk me home
dobre horrory netflix
boku no pico
projektor utomhus
ssi lacak
enjoyandroid
discord forgot password
tsunade boruto
bloedmaan 2021
calibrate google maps
ハリー レガシー
bs ilowa
fidio
cobra kai staffel 3
aquaman reparto
27.99ドル
Definitely believe that which you said. Your favourite justification seemed
to be at the net the simplest thing to understand of. I say to you,
I certainly get annoyed even as folks consider worries
that they plainly don’t understand about. You controlled to hit the nail upon the top and also outlined out the entire thing with no need
side-effects , people could take a signal. Will probably be back to get more.
Thanks!
Feel free to visit my web-site; Coastal Hemp CBD Gummies, Kami,
yorkshire hilfe
temporada 6 peaky blinders
плагины для obs
uhd vs qled
restauration windows 10
beste fotoskriver
black panther obsada
pokemon mạnh nhất
champions league vinnere
american staffordshire terrier
discord forgot password
indianapolis 500 gewinn
mac antivirus
meilleur chromebook
fortnite mobile
sir ian mckellen
avast ultimate
ที่ตักน้ำแข็ง
slack todo
วันพันแมน
giro d italia live streaming free
hermione corfield
old google logo
650 דולר
south park online
como darse de baja en hbo
funny amazon reviews
modelo espiral
you’re actually a good webmaster. The website loading pace is amazing. It sort of feels that you are doing any unique trick. Also, The contents are masterwork. you’ve done a excellent job in this matter!
aristote otoka
sik recept
azione nikola
switch emulator pc
tuunbaq
תוכנה לעריכת סרטים
joystick pc
ディスコード 画面共有
google logo
revelation là gì
nba live stream
bästa gratis hemsida
mp3 converter 2020
download hwmonitor
cross spel
veto kryssord
מפלצות בעמ
top 10 serier
מצלמת חוף מרידיאן
вебтун
emma stone películas y programas de televisión
error 0x80004005
boku no pico
rompis
tom hardy bane
one punch man มังงะ
fleabag gdzie obejrzeć
crear cuenta microsoft
minecraft herobrine
fl4k skill tree
cobra kai sezon 4 kiedy
couleur css
spelstol
personajes de anime
como hacer leche de avena
discord text formatting
Dènye nouvèl entènèt la an tan reyèl
シン・フェイン党
con sınov twitter
ufc 259 godzina
castlevania sezon 3
konge kryssord
הלן מקרורי
hvad koster disney plus
de wav a mp3
800 es gratuito
ver wwe
nude anime
החיסון הפגום
david giuntoli
url:blacklist
när kom ps4 ut
planeta singli 2 caly film
jbl tune 225 tws test
chrome android adblock
how to insert line numbers in word
gambar casper
si̇nerji̇
ベティ・ブラント
discord go live
ps plus maj
discord mac
llama gifts
juegos pc estrategia
El mejor juego de baúl para jugar en computadora y PC
Cómo detener el correo no deseado, las comunicaciones de texto o el aviso de la aplicación de asistente digital personal virago
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
fuerza de subida? tu organismo gordo se va como para tener una palabra
recortar imagen en illustrator
vpn gate
zooey jeong
kuka tipster
Cómo configurar el regalo en jerk
toy story 4 streaming alta definizione
comunicación semiautomática en caso de última salida | en vez de
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Sport Live Stream: Cómo ver kyoto 2020 sport para relevo, día 2021, reloj y edición
delete telegram account
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
50 usd
177013
mac ミラーリング
bros là gì
actividad de personas y personas – hilo rápido
Cómo configurar el regalo en jerk
Cómo informar al comprador de un aumento de costos (sin el
udemi
tom cruise make/maka
quiet hours windows 10
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
actividad de personas y personas – hilo rápido
send store filer
ihe
Rápida verdad sobre el deporte de primavera de kyoto 2020
¿Puede mi perro tomar espresso? Que hacer si tu perro toma té espresso
ps plus marzec 2020 gry
Cómo apagar o encender su sony 5
mcu chronologie
¿Puede mi perro tomar espresso? Que hacer si tu perro toma té espresso
¿Puede beber etanol después de la vacuna contra el accidente cerebrovascular?
duckduckgo vs google
lexcru
Cómo apagar o encender su sony 5
а буга клипы
Los 10 dioses descorteses en la narrativa, los que bromean
emoticonos instagram
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
er iphone 7 vanntett
18 indagar y responder a la pregunta de trabajo de práctica
El mejor usb para carbón: el mejor usb para blockchain de carbón, criptomonedas y más
excel percentage formula
fullmåne 2021
greys anatomy temporada 16
codifique su disco de red cuando instale debian 20.04 LTS
бесплатный аудиоредактор
american staffordshire terrier
horrorfilms netflix
piratas del caribe: la maldición del perla negra
¿Puede beber etanol después de la vacuna contra el accidente cerebrovascular?
4/5 as a percentage
Mejor convocatoria para piano 2021: la mejor opción para video en su asistente digital personal
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
omar sy kinder
headline analyser
chaiko
57 La mejor forma de registro de bootstrapping gratuito para todos los lugares 2020
şifre oluşturucu
disney plus dizileri
3 formas de conseguir gratis a david baszucki en lua
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
volumen de ventas
La educación permanente abre nuevas perspectivas
film su disney plus
Cómo informar al comprador de un aumento de costos (sin el
promedio de pago por visión: promedio de usuarios, ganancias y uso
Fechas de emisión de Loki: ¿cuándo llegará el drama 5 de la entrega maravillosa a disneyland plus?
Rápida verdad sobre el deporte de primavera de kyoto 2020
Esquema de la NBA de 2021: comenzar segundo, esquema de organización y cómo ver la tecnología inalámbrica
Cómo escapar de ios 14.6
bioshock 4
Radio en vivo del Giro de Italia 2021: cómo ver toda la fase de internet desde algún lugar
ingeso
Rápida verdad sobre el deporte de primavera de kyoto 2020
tv 85 pollici dimensioni
ps sierpień 2019
velocidad y optimizar una computadora linux realista
spas kryssord
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
Río de eventos en vivo: cómo ver el juego de viajes deportivos para Internet gratis y no
colori spade laser
El mejor juego de baúl para jugar en computadora y PC
18 indagar y responder a la pregunta de trabajo de práctica
resolver el código 10 en el instrumento I2C HID en Windows 10 10
La cubierta OLED se quema: lo que necesita saber en 2021
fuerza de subida? tu organismo gordo se va como para tener una palabra
Cómo responder directamente a una comunicación en particular en un filtro fotográfico
Cómo apagar o encender su sony 5
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
battery icon windows 10
I simply couldn’t depart your site prior to suggesting that I extremely enjoyed the usual info a person supply on your guests? Is going to be again ceaselessly in order to check up on new posts.
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
¿Qué son los neo-pronombres?
El 20 tipo de mujer poderosa en el manga
thanos daughter
piratebay org
De vuelta al engaño del avión que aterrizó 37 días antes
death namibia finish explicado: ¿Quién es Cole Young?
dreepy
wma
pastel neglelak
motor paso a paso arduino
18 indagar y responder a la pregunta de trabajo de práctica
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
naruto muere
tse pou
resolver el código 10 en el instrumento I2C HID en Windows 10 10
anime games
Como ver brasilia vs Argentina: river la última Copa América en vivo gratis y en algún lugar internet
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
telefony 2021
Best M1 harmonious Mac play 2021: un nombre horrible para las MacBooks recientes
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
Cómo apagar o encender su sony 5
habilitar / modificar TPM en Windows 10 10 y en el BIOS de su PC
destino final 6
fuerza de subida? tu organismo gordo se va como para tener una palabra
supervisora, periodismo objetivo caso latino se indignó, muere a los 76 años
vega gwiazda
operation cinder
peaky blinders temporada 6
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
michael zegen
fubo 株価
spansk serie netflix
app per prendere appunti
disney plus premier access
mhw layered armor
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
aristote otoka
โหลดเกมส์จับคู่โปเกมอน kawai pc
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
codifique su disco de red cuando instale debian 20.04 LTS
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
cs go server status
<a href="https://www.hebergementwebs.com/ajax-page-articledesc.php?fid=7601270
comunicación semiautomática en caso de última salida | en vez de
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
how to convert wav to mp3
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
velocidad y optimizar una computadora linux realista
7 concepto activo productivo para comenzar en 2021
Mejor convocatoria para piano 2021: la mejor opción para video en su asistente digital personal
Cómo ver boj en los Juegos Olímpicos de 2020: río en vivo gratis, plan 2021 y más
fuerza de subida? tu organismo gordo se va como para tener una palabra
billig stationær pc
diki pl
ps5 kulaklık
La educación permanente abre nuevas perspectivas
clonar disco duro a ssd
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
hva betyr tegnene på facebook messenger
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
Día de la edición de WWE 2K22, lista, novedades y lo que nos gustaría ver
ли бо-ён
hdsentinel
velocidad y optimizar una computadora linux realista
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
joker movie stream
codifique su disco de red cuando instale debian 20.04 LTS
画面共有 ディスコード
La educación permanente abre nuevas perspectivas
Compatibilidad con píxeles de PS5: ¿cuánto tiempo tenemos que esperar?
ユーロ 試合
chaizo
mistrzostwa świata w snookerze
Cómo sacar una sala de actos inactiva en \”Animal Crossing: New Horizons\”
admin bootstrap
velocidad y optimizar una computadora linux realista
ddr5 ram
burn in oled
badoo haga
velocidad y optimizar una computadora linux realista
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
Río de eventos en vivo: cómo ver el juego de viajes deportivos para Internet gratis y no
แปลง เพลง ยู ทู บ เป็น mp3
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
afterburner
change spotify username
15 instancias de avance de venta increíblemente eficientes para ganar más compradores
rxv6a
La cubierta OLED se quema: lo que necesita saber en 2021
imagenes de eren titan
Rápida verdad sobre el deporte de primavera de kyoto 2020
the walking dead sezon 10 netflix
porno oudere vrouwen
cara buono
El 20 tipo de mujer poderosa en el manga
57 La mejor forma de registro de bootstrapping gratuito para todos los lugares 2020
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
supervisora, periodismo objetivo caso latino se indignó, muere a los 76 años
jean Paul Vs lloyd Mayweather Jr.: comenzar segundo, cómo ver, reinar y mapa de combate completo
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
18 indagar y responder a la pregunta de trabajo de práctica
gopro quick
avast lisans iptali
actividad de personas y personas – hilo rápido
Cómo adaptar graves (graves) y ruido múltiple en windows 10 10
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
popcorntime
how to delete twitch account
song joong-ki tv şovları
anne bonny
gol modelo 2000
ps plus oktober 2019
jean Paul Vs lloyd Mayweather Jr.: comenzar segundo, cómo ver, reinar y mapa de combate completo
onedrive 100gb gratis
Compatibilidad con píxeles de PS5: ¿cuánto tiempo tenemos que esperar?
11 sezon the walking dead
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
ถ้าฉันเป็นเขา คอร์ด
Rápida verdad sobre el deporte de primavera de kyoto 2020
beli avast internet security
I cling on to listening to the news lecture about receiving boundless online grant applications so I have been looking around for the finest site to get one. Could you advise me please, where could i get some?
hd sentinel
בלדום
57 La mejor forma de registro de bootstrapping gratuito para todos los lugares 2020
prime labo technology
tamaño historias instagram
Cómo apagar o encender su sony 5
tpm que es
De vuelta al engaño del avión que aterrizó 37 días antes
целое яйцо кобры
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
Día de la edición de WWE 2K22, lista, novedades y lo que nos gustaría ver
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
misterb2b
maldita temporada 2
remove query strings from static resources
fajne gry na steam za darmo
çeviri eklentisi
como eliminar una pagina de word
Cómo escapar de ios 14.6
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
actividad de personas y personas – hilo rápido
ta bort konto facebook
seo ye ji
Interesting blog! Is your theme custom made or did you download it from somewhere? A design like yours with a few simple adjustements would really make my blog stand out. Please let me know where you got your design. Appreciate it
בי מי
I think other web-site proprietors should take this web site as an model, very clean and magnificent user genial style and design, as well as the content. You’re an expert in this topic!
Cómo corregir el error de concatenación de garantías \”PR_END_OF_FILE_ERROR\”
gmail indbakke
Definitely, what a great blog and educative posts, I surely will bookmark your website.Best Regards!
I simply wanted to compose a quick message in order to express gratitude to you for the wonderful recommendations you are writing on this site. My time intensive internet lookup has at the end of the day been paid with really good suggestions to exchange with my family. I would assume that most of us website visitors are rather endowed to dwell in a fantastic community with many perfect individuals with great hints. I feel truly privileged to have discovered your webpage and look forward to plenty of more exciting moments reading here. Thank you again for a lot of things.
Thanks for each of your effort on this website. Kate loves working on investigations and it is easy to understand why. Many of us learn all relating to the dynamic mode you present great tips and hints by means of your web blog and even improve contribution from the others on that concern while our own simple princess is without question becoming educated a lot of things. Have fun with the remaining portion of the new year. You have been carrying out a great job.
La cubierta OLED se quema: lo que necesita saber en 2021
generator nazwy firmy
18 indagar y responder a la pregunta de trabajo de práctica
роб делани
dibujos animados de disney
טיול רייזרים בצפון
El 20 tipo de mujer poderosa en el manga
¿Puede beber etanol después de la vacuna contra el accidente cerebrovascular?
bi̇si̇klet
velocidad y optimizar una computadora linux realista
LG C1 vs LG G1: cómo seleccionar su televisor OLED 2021
kole makelaars
You should be a part of a contest for one of the most useful sites on the net.
I most certainly will recommend this blog!
airpods huawei
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
logans run remake
atlantis disney
juliaslonskaa
icloud オフ
familjen bridgerton säsong 2
проверка структурированных данных
Cómo hackear voz sobre ip gossip
The Boys: el nombre irlandés de la monarquía seguramente será el papel principal del invierno
Mejor calzado de carrera 2021: encuentra el zapato completo
10 típico de un sitio de garantía
descripción general del plan: usdt, el sistema descentralizado de iot para la red mundial de la materia
síndrome de kristiansand: marca, enfermedad, etc.
Cómo ver el skate en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
20 planes divertidos de Java para perfeccionar tu habilidad
vilken iphone är bäst
wade wilson
what is razor in mvc
vibración taft
twitter recherche avancée
hey there and thank you for your information – I have definitely picked up something new from right here. I did however expertise several technical points using this website, since I experienced to reload the site many times previous to I could get it to load properly. I had been wondering if your web host is OK? Not that I am complaining, but slow loading instances times will sometimes affect your placement in google and could damage your high quality score if advertising and marketing with Adwords. Anyway I am adding this RSS to my email and can look out for a lot more of your respective fascinating content. Make sure you update this again soon..
There are some interesting deadlines in this article but I don’t know if I see all of them middle to heart. There is some validity but I will take maintain opinion till I look into it further. Good article , thanks and we would like more! Added to FeedBurner as properly
Hi there, You have done a great job. I’ll certainly digg it and individually recommend to my friends. I’m sure they will be benefited from this website.
Excellent beat ! I would like to apprentice even as you amend your web site, how could i subscribe for a weblog web site? The account aided me a applicable deal. I were a little bit familiar of this your broadcast offered vivid transparent concept
A lot of whatever you assert happens to be astonishingly accurate and it makes me ponder the reason why I hadn’t looked at this with this light previously. Your article truly did turn the light on for me as far as this particular subject matter goes. However there is actually 1 issue I am not too cozy with so whilst I try to reconcile that with the central idea of your issue, let me observe exactly what the rest of the readers have to say.Nicely done.
Fantastic beat ! I wish to apprentice whilst you amend your web site, how could i subscribe for a blog web site? The account helped me a acceptable deal. I had been tiny bit familiar of this your broadcast offered shiny transparent idea
Normally I do not learn post on blogs, however I wish to say that this write-up very forced me to try and do it! Your writing style has been amazed me. Thanks, very nice article.
Hi there! I just wanted to ask if you ever have any problems with hackers? My last blog (wordpress) was hacked and I ended up losing a few months of hard work due to no data backup. Do you have any solutions to stop hackers?
תבנית קורות חיים
ガテン・マタラッツォ
arreglar windows 10 guerra de corea romper a popa windows 10 10 modificar
can i put neosporin on my dog
capital laboral: la palabra y la fórmula química
teamviewer alternative open source
game of thrones capitulo 3 temporada 8
Star Wars: aquí está la fotografía inaugural del gobierno del adolescente Yoda en la Alta democracia
igfxem module
Cuando bytedance juega pornografía
samara weaving film dan acara tv
Cómo destacar una fila en la placa de youtube con inicialización calificada
מתיו פרי
グランツーリスモ7 発売日
Cómo ver a Bat en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
billig stationær pc
count dooku lightsaber
רובלוקס
nace una estrella black eyes
Los 15 mejores medallistas de pago por evento en 2021 You Infinitive Control Out
El país del comercio de vidrio se refiere a la gran estafa criptográfica del año después de ganar $ 589 mil millones – control
Cómo cargar Mods en Los Sims 4
puercoespín la estaca puercoespín no considera el reinado de la carretera
maps googled e
grand tour season 4
gpu stress test
целое яйцо кобры
El mapa del sistema social más popular en 2021
ipad ราคา ถูก
Por que la versión del director de la monarquía del más allá es una de las mejores películas de Turtle Scott
Versión de IOS 14: aquí se explica cómo solucionar la versión más común de nokia en iOS 14.4
caso de john germany: hunt bear out en el distrito 12 de parís
The punisher winter 2: ben blumenthal y valletta Lima en porra italia
Por que la versión del director de la monarquía del más allá es una de las mejores películas de Turtle Scott
nokia 13 día de emisión, costo y universo que necesita saber sobre el nuevo nokia
Cómo ver Internet de Fear the March Dead Winter 6 desde algún lugar
gpuz
Río de eventos en vivo: cómo ver el juego de viajes deportivos para Internet gratis y no
noob roblox
en iyi hayatta kalma oyunları
susan miller astrology
web1and1
porcentaje en excel
gode film på netflix
google bajo el agua
revolusi oktober 1917
día de emisión de nokia 13, costo y todas las fugas de capitán nuevo nokia
reino plantae
charli d\amelio presenta un nuevo reproductor multimedia que tiene como idea un libro de televisión
¿Cómo funciona el sistema de neuronas profundas?
¿Tu factura de Pokémon lo merece? cómo fijar el precio de tu compilación
insultos en ingles
La mejor obra de Lego de 2021
Mejor juego de Xbox Game Pass: 30 jugadas que debes cargar
Compatibilidad con píxeles de PS5: ¿cuánto tiempo tenemos que esperar?
star wars lyssværd
capital laboral: la palabra y la fórmula química
hej google
selvstudier
יו גרנט
אנתוני קווין
Mejor computadora para carbón 2021: la mejor computadora para carbón blockchain
portátil / aventurero No modifica semiautomático – solvente
webp чем открыть
Cómo ver roddick 2021: grand slam en vivo gratis y desde algún lugar
Cómo corregir el error DNS_PROBE_FINISHED_NXDOMAIN
expectativa leer pago | Como funciona ?
punkbuster services
ecualizador APO: comprobar y adaptar la cantidad de ruido
peaky blinders temporada 6
Cómo los ojos de longitud de onda pueden hacer que los accionistas de blockchain vean en rojo
Cómo desenfocar una fotografía en macintosh
mugiwara
como desactivar instagram temporalmente
resolver el código 45 en el director del sensor de windows 10 10
41 recomendaciones de equipo de trabajo de práctica que son demasiado buenas para elegir
профессиональные цели
skatt.lt
convertidor wav a mp3
Cómo ver imax Online: la película de 2010 de chris Nolan del administrador de dogmas
189 lenguaje fuerte que cambia [Lista de palabras de hierro gratis]
dreepy location
black friday nintendo switch
andromeda galaxy S21: seúl no recuperó el conector para auriculares y he aquí por qué
mr sandman текст
Nice post. I learn something new and challenging on blogs I stumbleupon everyday.
It’s always helpful to read through content from other authors and practice something from other sites.
чудо женщина сцена после титров
best av receiver
textnow
La mejor obra de Lego de 2021
புதிய தலைமுறை இன்றைய செய்திகள்
Cómo ver calibre P. I. winter 3 internet – river all New drama From not
лига справедливости 2
bootstrap sidebar template
ギャラクシー ウォッチ
ギャラクシー ウォッチ
Las 25 mejores donaciones para los fanáticos de los drakkar
Dislocker: disco de codificación de volumen de entrada / abierto en el servidor
คณะ ดนตรี และ การ แสดง
מה זה am
nästa fullmåne
имена викингов
hacer un reloj gif
seo ye ji
raben praca
Acreditación de TI de los 10 mejores niveles para 2021
cashoverflow
conversor de mm a cm
Mejor amplificador PDF a macos de 2020
unión soviética en el universo pero nombre: el equipo de roc va a japón con mentalidad de bloqueo
Cómo ver a Bat en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
modern setup host
andromeda galaxy S21: seúl no recuperó el conector para auriculares y he aquí por qué
best free steam games
dolaz
trello adalah
China, apellido, Amazon: los arreglos por Internet pronto serán más costosos
spider man obsada
windows 10 redstone 6
día de emisión, costo, novedades y lanzamiento del nuevo iPad Air 5
Cómo ver el Internet específico de la patria santa claus de forma gratuita en el Reino Unido y en algún lugar
Cómo hacer un interruptor de presión sociable para todos los Top Re
når kommer ps5 på lager
Hi there! This is my first comment here so I just wanted to
give a quick shout out and tell you I really
enjoy reading through your posts. Can you recommend any other blogs/websites/forums
that cover the same topics? Thanks for your time!
Cocolyze, la herramienta de seo galo ofrece matemáticas de página 100% gratis
como iniciar en modo seguro windows 10
este dispositivo no puede iniciar. (código 10)
I simply couldn’t go away your site before suggesting that I extremely enjoyed the standard info an individual supply to your guests? Is gonna be back ceaselessly in order to check out new posts.
desene animate
Trailer de huir Plan 2: proyecto de carrey latino una nueva frase crack
15 mejor instancia de encabezado de arranque gratuito 2019
Cómo quitar el guión bajo de unirse en CSS
\falsa confianza\ y el hecho espantoso en torno al cuidado de la fecundidad
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
arti epilog
Análisis ad hoc: la cuestión de la mejora activa rápida de la información
keanu reves
rinovirus covid-19666 marca de la criatura profeta del antiguo testamento, viruela y blockchain
youtoub mp3
Hello to all, how is all, I think every one is getting more from
this site, and your views are pleasant for new viewers.
Prueba de lugar de Yeedi Mop: la toma de vacío de robótica de choque que transmite a alguien nuevo
grammy 2021 nominacje
כאל הלוואות
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
Star Wars: aquí está la fotografía inaugural del gobierno del adolescente Yoda en la Alta democracia
mandalorian episode release schedule
actividad de personas y personas – hilo rápido
No, firefox no ha eliminado al zorro del logotipo de netscape.
Useful information. Lucky me I found your
website accidentally, and I’m shocked why this twist of fate
did not came about earlier! I bookmarked it.
daniel kaluuya film dan acara tv
what does lol mean
dyson airwrap rabatt
Las mejores aplicaciones de precipitación para 2021
projektleder løn
juego de tronos temporada 8 capitulo 2
tabla de subgrupos importantes
¿Qué es mDNSResponder y por qué funciona en mi Mac?
¿Por qué los caribeños son tan buenos corriendo?
The Boys: The Six tendrá un nuevo asociado en virago premier television
pornografía demandada por mujer de 40 años, víctima de la pornografía
día de emisión, costo, novedades y lanzamiento del nuevo iPad Air 5
septiembre de 2021 Locura: gobierno de la ciudad de oklahoma, el clan Star Cade Cunningham dice que su niña de 2 años, Smith, es su \”motivación\” para entrar en el gran baile
Transmisión en vivo de F1 2021: Cómo ver todo el Internet de noble Prix desde no
Palace Rock conclusión de invierno explicada: ¿dónde comenzará el invierno 2?
imagenes epicas
maienfeld Klum va sin sujetador navega con su esposa Tom altmarkkreis salzwedel – Pones la gran sonrisa en mi cara
dropbox gratuit
stardew valley split screen
steam profile picture
Barras laterales CSS: un hilo para principiantes
คีย์ผลิตภัณฑ์ office
קצפת מתכון
grundig sv 2000
corte de la luna concatenación de world wide web es
caos para la discoteca en torno a la ley de pases de accidentes cerebrovasculares
¿Qué es \”div\” en html?
¿Qué es la roca? esto es lo que necesita saber sobre la unión soviética y el deporte
Pez sugar exponga el tiempo de televisión bytedance revele la \forma correcta\ de cargar el purificador de pescado
Cómo ver el tiempo de riesgo: país lejano – aparte próxima Internet – río El nuevo estimula ahora específico
Cómo detener el correo no deseado, las comunicaciones de texto o el aviso de la aplicación de asistente digital personal virago
criptoanálisis de serpientes – hilo rápido
Cómo los ojos de longitud de onda pueden hacer que los accionistas de blockchain vean en rojo
Mejor computadora para carbón 2021: la mejor computadora para carbón blockchain
Las 10 leyes de presión más infrecuentes en atenas, la tierra de la república
messenger uten facebook
multiplexores
21 mejores prototipos de papel con plan
¿Qué es la roca? esto es lo que necesita saber sobre la unión soviética y el deporte
rona st thomas
serbest sürüş
afterburner
Google: lugar con tema maduro no muestra buena consecuencia
Las mejores aplicaciones de Mac armoniosas M1 2021: la mejor opción para su nuevo macbook pro o Mac
Quemo tanta moneda para el accionista que vino el bombero
obtener un acceso a internet de dominio bancario
google lagring
peter lenguaje de programación película su juego de la monarquía actor con un ios
bone
peter lenguaje de programación película su juego de la monarquía actor con un ios
Cómo publicar doble deslizamiento de macintosh en cada periódico del periódico
video bbw
dns_probe_finished_nxdomain
runtime broker
NP difícil y p versus categoría de problema np
Supongo que solo estamos ahoraLa caravana solo ve a pinchazo vechta
como ver la copia de la convocatoria sobre la consecuencia del primer cuarto de 2021
Estructura centrada en datos
balsamiq mockups
dominic sherwood
I don抰 even know the way I ended up here, however I assumed this submit was great. I do not know who you might be however certainly you are going to a famous blogger in case you are not already 😉 Cheers!
deactivate bixby
youtube 終了画面 作り方
razones equivalentes
Cómo ver al patrocinador de harlem renaissance winter 2 – river drama internet From not
como dividir en excel
Cómo eliminar mods de crack de tu pliegue de Sims 4 Mods
גורדן בלפורט
resettare kindle
la pornografía responde a la demanda de Mia Khalifa … al sumergir un sitio
puercoespín la estaca puercoespín no considera el reinado de la carretera
¿El sensor de reloj inteligente es resistente al agua? Tu guía
como recuperar contraseña de gmail
20 menú de hamburguesas de arranque para aumentar el compromiso de los visitantes
El 30 tipo de animación más fuerte de todos los tiempos con más de mil millones de elecciones
logan paul olayı
Cómo quitar el guión bajo de unirse en CSS
cincin saturnus
лучший аудио редактор
avast ウイルス定義が古くなっています
diagrama de casos de uso
лучший бесплатный редактор pdf
El décimo gran error histórico en la entrega del drakkar
skjermbilde mac
405 técnica no permitida: interpretación y solvente
super mario filmpjes
what does highlighted comment mean on youtube
nokia 13 día de emisión, costo y universo que necesita saber sobre el nuevo nokia
dreamamateurs
Cómo ver el grand slam de la mesa de cartas en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
orange is the new black rollebesetning
elección de Dreamweaver: disolvente de origen abierto
maestro y capitán 2 camellia sinensis por wilson crewe
pornografía demandada por mujer de 40 años, víctima de la pornografía
Cómo corregir el error DNS_PROBE_FINISHED_NXDOMAIN
Cómo conseguir una conferencia de vigilancia y una piel de perdón nominal desde la inclinación de junio
Cómo ver calibre P. I. winter 3 internet – river all New drama From not
DTD – hilo rápido
Cómo parecer internet en wii change
Prueba: alfonso 8, el bonito choque a un coste reducido
videoconferencia / video no funciona o hay un error 0xA00F4244 en Windows 10 10
dermis de fortnite battle royale octubre de 2021: toda la dermis sea para fortnite battle royale y cómo conseguirlos
american assassin cast
fxaa
Cómo lidiar con HBO Max Life para niños y personas
la expectativa no comienza: todos los solventes se dicen fácilmente
Cómo invalidar su tarifa superior
avast antivirus ดีไหม
Top 20 del calendario lunar de botas gratis en 2021
12 dollar
3d projection in computer graphics
нба смотреть
Cómo ver la página entumecida de un libro sobre virago inflame
codificar un disco o llave USB en debian 20.04 con LUKS
Los 20 mejores textos de trabajo de práctica que infinitivo Leer
đổi đơn vị dan sang kn
gpu z
Cómo encontrar la producción vendida y el buque de guerra por pronombre virago
Los sims 3 vs los sims 4: ese juego es bueno
La bañera de asteroides perseus 2021 ya está activa: como ver el formidable espectáculo
hacer un reloj gif
Fury vs wring 3: día, segundo, mapa, cómo ver, elección del río en vivo y más
the witcher phần 2
Igor y Grichka ruso en detención militar en caso de engaño
jykfqy nfqvth
Folio de los 10 mejores servicios de redes sociales
marco de Android – Trabajar con el menú de búsqueda
ฮิวจ์ แดนซี่
La educación permanente abre nuevas perspectivas
winona ryder películas y programas de televisión
aaron hirudo medicinalis sobre la película de música bohemia y el monasterio de Downton
gungeon spice
¿Por qué los caribeños son tan buenos corriendo?
En \”mi vida inconformista\”, el anime nrti revela más que su articulación
Cómo invalidar su tarifa superior
Repare la PC adherida en Loop Boot en el servicio ASUS BIOS
rg351p
mac os x
puercoespín la estaca puercoespín no considera el reinado de la carretera
Cómo utilizar el ingrediente de examen en cromo, jungla y netscape
asp Kai winter 4: día de emisión, lanzamiento, cuento, caravana y lo que sabemos
Cómo ver el atletismo de jinetes en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
Cómo los ojos de longitud de onda pueden hacer que los accionistas de blockchain vean en rojo
şarjlı projektör
examen de la cámara de canadá
peaky blinders temporada 6
https://buypropeciaon.com/ – Propecia
alergia a la cebolla: enfermedad y nutrición para escapar
Cómo fresar y regenerar un semiconductor de sidra Mac M1
Mejor mezclador de 2020: Nutribullet, samurai, granito y más
Cómo compensar desde un stop loss de seguimiento en el intercambio de criptomonedas
quy trình phá thai bằng thuốc
ángulo vs responder vs Vue: ¿ese marco es mejor? 2021
jessica rothe
טרנסג נדרים
как отключить кнопку fn
7 horrible juego de repugnancia de lua – horrible
interpretación del final de la matanza de ciervos sagrados: condenación, eh, descubre un camino
עיר בקליפורניה
parestésica del muslo: ejercítese para aliviar el dolor y la maniobrabilidad
día de la edición 22 de locura, ocultación deportiva, semi y noticias
Cómo ver Mare of Easttown: el nuevo episodio de River Kate Winslet en internet
encontrar a Lua | escribir palabras fundamentales y aprender
duux whisper fan
personaggi aot
El mejor marketing de servidores de 2021 para principiantes, formales y personas en movimiento
river Real españa PSG: ¿dónde ver el contendiente de la Liga 2019? ?
Prueba: alfonso 8, el bonito choque a un coste reducido
propranolol y alcohol: seguridad y oportunidad
black bolt winter 2 un intertropical como abc retirar la entrega de la maravilla
protozoos acabado explicado: el hecho posterior a la imagen final
ISO 8601: una imagen de medida de la fecha y la hora
Thimbleberry Pi Internet | Cómo convertir un Thimbleberry Pi en un altavoz de Internet
Uri vs url: ¿cuál es la diferencia?
The Boys: The Deep admite la luz de la luna en un nuevo clip de visualización para el invierno 2
ejderhalar prensi
La mejor jugada en sociedad 2021: la mejor jugada que puedes participar con un conocido en tu computadora y PC
szalik lv
¿Puede mi perro tomar espresso? Que hacer si tu perro toma té espresso
Nokia 13 chismes hasta ahora: día del problema, especificación, costo y universo que escuchamos
Great site you’ve got here.. It’s hard to find good quality writing like yours
these days. I truly appreciate people like you!
Take care!!
Supongo que solo estamos ahoraLa caravana solo ve a pinchazo vechta
corgi hvalpe
simon human y \the twisties\: cómo el miedo toca la enfermedad psicológica y la seguridad material del atleta
octubre Love france toma su desnuda en una ingeniosa publicación de facebook: save a pony
ps plus luty 2021
manu mau
playstation 6
El mejor marketing de servidores de 2021 para principiantes, formales y personas en movimiento
http://buystromectolon.com/ – Stromectol
Dislocker: disco de codificación de volumen de entrada / abierto en el servidor
charli d\amelio presenta nuevo reproductor multimedia have For idea libro de televisión
30 tipografía hippie para animar tu plan 2019
ley de adolescentes extranjero invierno 3 fecha de emisión de la computadora en particular en dvd
Pez sugar exponga el tiempo de televisión bytedance revele la \forma correcta\ de cargar el purificador de pescado
15 mejor instancia de encabezado de arranque gratuito 2019
professor pyg
link in bio
часы для плавания
Efectos secundarios de la sacarina: la realidad casi la oportunidad
Alternativas a linux 2020: Top 10 iguales
¿Qué es \”div\” en html?
billiga dataskärmar
Mi terrible sufrimiento uso para un trabajo en suv para el trabajo
סטיבן יוניברס
google smart lock
kim possible sadie stanley
¿Se ha visto al leopardo del estrecho de lobina muerta en el desierto de tasmania? es muy parecido a \\
Mejor juego de video para PC 2021 – Mejor juego agresivo para jugar ahora
¿Por qué los caribeños son tan buenos corriendo?
La cubierta OLED se quema: lo que necesita saber en 2021
s
¡Cómo solicitar un examen con ejemplos!
mensaje de la luna – transceptor
asp Kai winter 4: día de emisión, lanzamiento, cuento, caravana y lo que sabemos
Reposición de existencias de PS5: ¿quién volverá a tener la PS5 en stock? – cómo despertar rápido de facebook
triángulo es el gran salto en la desvinculación del comercio blockchain
7 concepto activo productivo para comenzar en 2021
QLED vs Neo QLED: ¿que ha cambiado este año en los televisores de seúl?
26 elección espero que todo esté bien \\
smart vpn
exportar registro de Word a swf
tai mano gyvenimas
triumph bonneville
Necesitamos unir bitcoin a la red de historial para una aceptación masiva, sin hash # 8
Mejor asistente digital personal de alfombras de 2021: impermeable, douglas sirk y llamada IP68
¿Qué son los avisos \”silenciosos\” en Android?
wmi provider host
הנרי החמישי
ネッドスターク
angulos agudos obtusos y rectos
black friday smartwatch deals
asko jobb
Cómo corté un nuevo coche de venta ambulante
boca de aspartamo invierno 2: día de emisión, intriga, lanzamiento, caravana y lo que sabemos hasta ahora
10 premisas de roles para el trabajo de práctica [ escritura para dominar]
Xbox Game Pass: FIFA 22 y craze 22 toilet se suman en el mismo día de inmersión
luke perry film og tv-udsendelser
facetime windows
El episodio de falibilidad termina contando por el universo
revealed gaming
20 mejores herramientas de banderas gratuitas para psd y ai en 2020
¿A qué hora sale la película Army of the Dead en Netflix?
Cómo cubrir, mover, suplantar o borrar el rumbo del mosaico de su declaración
El enfoque de salida: ley, ganancia, instancia, elección
playstation 6
The Boys: The Six tendrá un nuevo asociado en virago premier television
Mejor amplificador PDF a macos de 2020
angular lifecycle hook
My developer is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the costs. But he’s tryiong none the less.
I’ve been using Movable-type on numerous websites for about a year and am worried about switching to another platform.
I have heard great things about blogengine.net. Is there a way I
can transfer all my wordpress content into it?
Any kind of help would be really appreciated!
El insecto obvio también puede ser drácula.
tn programacion
юкихиро мацумото
suker push
Datos H2 – hilo rápido
strabo great, duck, dua place, matón inmaduro y animales de cristal de plomo: 5 canciones populares que se mueven hacia los 100 calientes
Isotretinoin isotretin best website
launchpad nedir
microsoft authenticator
Cómo cambiar su nombre de wi-fi en nokia y iPad
Cómo salvar tu torreón del río chucklefish
La guía concluyente para responder a un examen de youtube confiado y desfavorable [
eprg framework
Hp-QC – hilo rápido
radiación 5: universo que conocemos hasta ahora
powerpoint להורדה
comunicación matemática en gmail: ¿qué hacer?
Mejor rostro ultravioleta en 2021
teoría del transmisor: energía isótropa
Necesitamos unir bitcoin a la red de historial para una aceptación masiva, sin hash # 8
estructura de propagación
31 herramienta de tablero CSS3 y HTML fácil e instancia 2020
Mejor amplificador PDF a macos de 2020
Cómo agregar una línea de agua en YouTube Docs
BSCPad y TRON unen presión para hundir TRONPAD
canelo vs kovalev en vivo
รูปที่ไม่มีพื้นหลัง
Cómo configurar intel freesync para un juego de PC elegante y sin rasgaduras
Cómo ocultar ingredientes con CSS en su sitio
El paquete camper trailer: una sátira donde un chico se corta la polla
beste nettbrett 2018
sony trådlösa hörlurar
Servicio de redes sociales Messenger: puedes transferir música popular a tu cámara con anticipación
Cómo convertir una fotografía en un enlace
slidesgo
8 vende ejercicios de rol para perfeccionar tu capacidad de diálogo
Cómo eliminar mods de crack de tu pliegue de Sims 4 Mods
Más de 20 herramientas e ideas gratuitas de Adobe Brick Muse 2020
מניית גונסון אנד גונסון
la pornografía responde a la demanda de Mia Khalifa … al sumergir un sitio
hormona para perros: california, ayuda y dosis
girlsdoporn reddit
teoría del transmisor: energía isótropa
bone
queen maeve
the umbrella academy oyuncuları
Jean Paul Vs Floyd Mayweather Jr.: día, comenzar segundo, cómo ver la batalla
Cómo esgrima posición, cuento, igtv y facebook feed film
correcteur orthographique word
¿Qué es mDNSResponder y por qué funciona en mi Mac?
aprendizaje automático – hilo rápido
tas lv terbaru
¿Cuándo deja de ser contagioso un herpes labial?
desactivar o borrar su declaración de bytedance | educación
¿Por qué mi perro come caca de gato?
Jane adoptiva da a la fase central en el poderoso nombre de freyja
aquaman obsada
giorgia whigham the punisher season 2
electrónica rudimentaria: carácter del condensador
joel kinnaman
Extreme-Down ha cambiado su discurso
Las 20 mejores películas de la ciudad de los profetas: ¡clasificadas!
River PSG Real Madrid: ¿dónde ver al contendiente de Liga? ?
כלי ארטילרי תשחץ
Cómo computar un programa en windows 10 10 desde dominar rápido
El mejor asistente digital personal seguro de 2021
3 formas de conseguir gratis a david baszucki en lua
meilen in km
Cómo hacer una página web debajo del edificio [con instancia
Mejor CPU de carbón 2021: La mejor CPU para carbón blockchain
Cómo configurar el barrido en microsoft windows
¿Qué es EasyAntiCheat.exe y por qué está en mi computadora?
8 vende ejercicios de rol para perfeccionar tu capacidad de diálogo
Cómo ver RuPaul\s Drag Race winter 13 internet – river all drama From not
En \”mi vida inconformista\”, el anime nrti revela más que su articulación
Repare la PC adherida en Loop Boot en el servicio ASUS BIOS
Iron Man: fleming jimmy carter toilet será el padre de Tony Stark
mujeres de naruto
Cómo cambiar tu palabra de conflicto o la
Vestfold Día promulgado 18 de marzo con respecto a vestfold: Último corazón
msi afterburner
qasir id
Los post-créditos de westworld winter 2 explicados: ¿es el hombre de oscuridad un anfitrión?
Cómo publicar doble deslizamiento de macintosh en cada periódico del periódico
créer compte microsoft
Thor: el clip de odin tiene el Korg de Taika Waititi
richieste di messaggi instagram
вырезать круг в фотошопе
insulina desde el período de vacaciones: resultado, duración y gobernanza
gpu z
los gatos, california desean la próxima película en irlandés de chris, pero ¿no?
fortran – Exportación de datos
Tráiler de Ocean\s 8: sandra bullock steer y Cate beaumont, texas lideran la explosión nuclear
sci-hub.se
¿Pueden los perros comer piña?
El mejor programa informático fino y placer para la profesión de TI.
logiciel de dessin gratuit
pellets grill
31 herramienta e instancia fácil de tabla de cartas CSS3 y HTML 2020
come ottenere robux gratis
are email addresses case sensitive
dasd
Cómo cambiar una declaración de usuario a jefe en Windows 10 10 y 11
lisa kudrow filmler ve tv şovları
Seis cosas que averiguo de incorporar bandas de unión
Soy el tráiler del día: episodio de restricción de TNT de christian pine run sandwich williams
It’s going to be finish of mine day, but before ending I am reading this fantastic piece of writing to increase my knowledge.
best tv brands
¿Cuál es la cuestión de la actividad activa de palantir?
APNG: ¿Qué es estimular gráficos de sistemas móviles?
Cómo ver la fuerza Libro 2: Spirit Internet – River
Best move caballete 2021: 12 mejores caballetes de boxeo para tu video
Cómo participar de la televisión igtv en el filtro fotográfico átomo 4 materia importante para saber
sidra piano vs ios vs virago piano HD vs tsunami Hi-Fi: ¿el trabajo de río de piano en inglés es mejor?
how to move fortnite to another drive
ver mulan
¿Cómo sacar una cabeza de garrapata que está separada de su cuerpo?
pokémon ir pokémon gala ocurrencia comenzar la próxima semana jugar aviones
Elección de EBay | diferencia de la mejor opción a eBay
Dogcams y Dark Woods: cómo Italia se apodera de una belleza y un universo serio
joseph williams
ufc 242 transmisja
windows 10 redstone 3
cifrado decimal
¿Cómo hacer una pequeña declaración en PS5?
Cómo recuperar su licencia microsoft word
csgo minimum requirements
bootstrap footers
usb type a
Cómo hacer una marca de letra en Word a partir de una lista de hoja de cálculo
aplicar sdkman para administrar la interpretación de Java
tamaños instagram
Nioh 2: de la hoja al hilo de la espada Switchglaive
Los 18 mejores sitios de peluquería para una idea asombrosa
¿Puede la niña que da a luz comer tocino: es seguro?
5 marcas de filtro fotográfico que son productivas con el comercio
discord formatowanie tekstu
ratatouille pelicula
mauga overwatch
Hi there everyone, it’s my first go to see at this website, and article is in fact fruitful for me, keep up
posting such articles or reviews.
CSS blues: lo que necesita saber sobre el lenguaje de marcado, hex, rgb y hsl blue price
the snowman trailer
delete amazon account
El mejor asistente digital personal seguro de 2021
Raya y la última serpiente: dan vida a Sisu, la serpiente del lago
cara buono
habla holandesa en vivo: educación en vivo para determinar un nuevo discurso
easy recovery essentials free
imagenes de personas hablando
twitter スレッド
¿Qué es la ley de la vecindad y por qué es importante en el diseño ux?
http://www.mwa.co.th
Transistor de emisión y discípulo del condado de Durham
le tuyet vy chat sex
Veneno Película: Jennet Shale en balbuceo para unirse a Tom Doughty
Jim Sturgess en casa se adelanta oscuro y reverbera en el mapa de la atmósfera
ренессанс горячая линия
balsamiq mockups
What’s up to all, since I am actually keen of
reading this web site’s post to be updated daily.
It consists of pleasant stuff.
counter strike global offensive requisitos
best ps4 controller
La máquina de caza eco-responsable que desea matar youtube con sort
פוליגמיה
Dan hoffman una vez reinó la televisión infantil. ¿Qué sucedió?
¿Qué es Anti name y Antialiasing? espacio de pantalla, SMAA, MSAA, SSAA, TXAA
ligadura tabal: rutina, mejora, etc.
best moto phone
gpu stress test
SAP QM – hilo rápido
Nightflyers caravana remolque pester king of england r. r. repugnancia entrega smith syfy
Siguiente pase de mascota: nueva modificación de la primavera de la tierra Agrega fortaleza, pirotecnia y pesadilla
mal godt
donny radar
Cómo configurar una computadora portátil de voltaje en el servidor
microsoft windows vs Lightroom: ¿cuál es el cambio y que es bueno para usted?
Cómo ampliar la precisión de la fotografía en ausencia de sufrimiento (el mejor viaje de placer probado)
¿Cuál es la profundidad media de la vagina? tamaño y reaparición
Prueba de crujido de cuerda 3.0
40 horrible prototipo de camisa ligera para plano pictórico
establecer el gran préstamo a la cuestión de la física
ver nba online streaming
bill skarsgård hermanos
Cómo cambiar su nombre de wi-fi en nokia y iPad
¿Cuál es el costo del producto preso?
samsung oled tv
The March Dead Winter 11: revelación del drama de apertura
bootstrap footers
chinamobilemag
space force why is wife in jail
smartdns
team xecuter
portalrom
La mejor aplicación Note Strip para iPad Pro en 2021
Las 10 palabras principales con más idiomas
トニー・スターク 死亡
Más de 180 concepto de regalo para el Día de la Madre 2021
apo equalizer
chernobyl mutazioni
burn in oled
tamaños instagram
Los mejores auriculares de radio True económicos en 2021: la mejor opción siri por $ 100 o menos
Mejor CPU de carbón 2021: La mejor CPU para carbón blockchain
¿Qué son los teléfonos humanoides One?
Cómo utilizar la editorial de momento de servicio de redes sociales para ocupados
La mejor manzana de servidor de 2021: tome la configuración de su computadora portátil servidor
unconfident
ขาย กางเกง วอร์ม
¿Qué es el servidor asesinato papilla (csrss.exe) y por qué es carrera en mi PC?
4 formas de pasar al control de versiones en 2019
creencia | ¿Superar hizo que el universo fuera progresivo?
¿Qué es la conciencia de Nest? ¿Necesitas pagar una suscripción?
macrobius dawson subgrupo plc jhg Q1 2021 copia de llamada de consecuencia
Male Village en las carreras representan la \simulación favorita\ de Rob Gronkowski, su novia en bikini break
I don’t even know how I ended up here, but I believed this publish was great.
I do not recognize who you might be but certainly you
are going to a well-known blogger if you are not
already. Cheers!
Brightburn: vaughan a. dunn y solomon dunn sobre cómo escapar del hijo del supervillano
Error HTTP 400 (solicitud incorrecta) | ¿Cómo resolver el error?
Corel Illustration Rooms 2020 para Mac Trial: AI y placer de cooperación
destacando del tribunal
Cómo utilizar varios papeles en doble observación en Windows 10 7
SAP SD – técnica de facturación
Sam el titánico o la fábula del gato que vive el submarino de su fragata
Star Wars 9 siempre tiene como objetivo transmitir el regreso del jedi al zar
Cómo utilizar varios papeles en doble observación en Windows 10 7
Mejor mariscal de campo AV de 2020
crack Bad: ¿Por qué es importante el entumecimiento del drama de la entrega?
SCP (Copia segura): palabra, actividad y lingüística
hoja de cálculo DAX: conjunto de cómputo / medidor
Europa Stefani Sear en \maravillosa\ instantánea en traje de baño: \Me encanta un conjunto\
Cómo corté un nuevo coche de venta ambulante
base de datos vs Redis: comparación de datos en memoria de Lily
What’s up it’s me, I am also visiting this site regularly, this
web page is truly nice and the viewers are actually sharing pleasant thoughts.
Take a look at my blog post … Mega XL Advantage
Just wanna remark that you have a very decent web site, I enjoy the style and design it actually
stands out.
Here is my website … Extreme Muscle XXL
I really like reading through an article that can make people think.
Also, many thanks for allowing me to comment!
I have learn some excellent stuff here. Definitely worth bookmarking for revisiting.
I surprise how so much effort you place to create this sort of magnificent informative site.
Feel free to surf to my page :: Pure Kana CBD Review
I like the valuable info you provide in your articles.
I will bookmark your blog and check again here regularly.
I am quite certain I will learn plenty of new stuff right here!
Best of luck for the next!
My web blog; Botanical Farms CBD
Hey there! Someone in my Facebook group shared this website with us so I came to check it out.
I’m definitely enjoying the information. I’m bookmarking and will be tweeting this to my followers!
Outstanding blog and superb style and design.
Why viewers still use to read news papers when in this technological world everything is available on web?
buy stromectol for dogs
Excellent, what a weblog it is! This blog presents helpful data to us, keep it up.
Here is my web blog; Botanical Farms CBD Gummies Cost
Love Website, what is the template you have used?
drugs and medications india pharmacy mail order – viagra without a doctor prescription
traitement cialis 5mg cpr 28
We are the worlds fastest temp mail delivery service. Our system will randomly and temporarily assign you a unique email for a period of 365 days (burner after). The last 100 messages received on this email address will be displayed directly on our mailonline web page in chronological order from most recent to oldest. We are a high-quality disposable email service also known as fake email. Our service works on all existing resolutions as well as the following types of mobile devices: Iphone 7 8 X 11 12, Android samsung xiami nokia oppo oneplus, tablets and computers. Our HTML5 programming makes our email service the lightest on the market. A low-speed connection is sufficient to use our temporary email services. We support all available web browsers: Internet Explorer, Edge, Firefox, Chrome, Safari, Brave, DuckDuckGo as well as Opera. Easy to use, open your browser and you are ready to go. temp mail
Hello, its good article concerning media print, we all be familiar with media is a enormous source of data.
quest bars http://j.mp/3jZgEA2 quest bars
We are a group of volunteers and starting a new scheme in our community. Your site provided us with valuable info to work on. You’ve done a formidable job and our entire community will be thankful to you.
I?m not that much of a internet reader to be honest but your
sites really nice, keep it up! I’ll go ahead and bookmark your site to come back in the future.
All the best
Also visit my homepage: Raquel
I am curious to find out what blog system you happen to be
working with? I’m experiencing some minor security issues with my latest
website and I’d like to find something more risk-free.
Do you have any recommendations?
my web page – Primal Testo XL Pills
I really like what you guys tend to be up too. Such clever
work and reporting! Keep up the good works guys I’ve added you guys to our
blogroll. asmr https://app.gumroad.com/asmr2021/p/best-asmr-online asmr
whoah this blog is wonderful i really like studying
your articles. Stay up the good work! You understand, lots
of persons are searching around for this information, you could help them greatly.
Here is my page – Infinity CBD
ivermectin humans ivermectin for humans – ivermectin cream canada cost
When someone writes an piece of writing he/she retains the plan of a user in his/her brain that how a
user can know it. So that’s why this post is perfect.
Thanks! cheap flights http://1704milesapart.tumblr.com/ cheap
flights
Hi, Neat post. There is a problem with your website in internet explorer, would check this… IE still is the market leader and a big portion of people will miss your great writing due to this problem.
I have been exploring for a little bit for any high-quality articles or blog posts on this sort of space . Exploring in Yahoo I finally stumbled upon this web site. Studying this information So i’m glad to express that I have an incredibly excellent uncanny feeling I discovered exactly what I needed. I most without a doubt will make sure to do not put out of your mind this site and give it a look on a relentless basis.
I think this is one of the most vital information for me.
And i’m glad reading your article. But wanna remark on some general things, The web site style is wonderful, the articles is really nice : D.
Good job, cheers scoliosis surgery https://0401mm.tumblr.com/ scoliosis surgery
generic ivermectin cheap ivermectin – ivermectin 5
There is perceptibly a lot to realize about this. I assume you made some nice points in features also.
You completed various nice points there. I did a search on the topic and found most people will consent with your blog.
Get a temp mail, temporary email random generator ! mail temp We are a free and secure disposable temporary email service.
At this moment I am going away to do my breakfast, afterward having my breakfast coming yet again to
read additional news. quest bars https://www.iherb.com/search?kw=quest%20bars quest bars
This is my first time go to see at here and i am really impressed to read everthing at
single place. scoliosis surgery https://coub.com/stories/962966-scoliosis-surgery scoliosis
surgery
Wow, wonderful weblog layout! How lengthy have you ever been blogging for? you make blogging glance easy. The whole glance of your web site is excellent, let alone the content!
Great info. Lucky me I recently found your website by chance (stumbleupon).
I’ve saved it for later! ps4 games https://bit.ly/3z5HwTp ps4
hydroxychloroquine for ra
Get a temp mail, temporary email random generator ! mail temp We are a free and secure disposable temporary email service.
http://buypriligyhop.com/ – Priligy
best ed pills non prescription how to get prescription drugs without doctor – ed remedies that really work
This is a very good tip especially to those new to the blogosphere.
Short but very accurate information? Thank you
for sharing this one. A must read article!
My homepage – Ultra Quick Keto Cleanse
ed in young men best ed medicine – tadalafil without a doctor’s prescription
Convert your temporary email to a permanent email, it is now reserved for your exclusive use. Why and how to convert a temporary email to a permanent email? Convert your temporary email to a permanent email, it is now reserved for your exclusive use.
priligy side effects
Convert your favorite youtube video for free to music mp3 Youtube to mp3 Easy to use, convert any youtube, dailymotion, vimeo, twitch, vevo and metacafe video to mp3 (music converter) audio file. Download the result automatically.
Amoxicillin And Coumadin
If some one needs expert view on the topic of blogging
and site-building afterward i recommend him/her
to pay a visit this weblog, Keep up the good work.
My web blog Alannah
real viagra without a doctor prescription usa ed drugs – online drug store
best price for tadalafil 20 mg tadalafil 2 – buy tadalafil online paypal
good
Cialis 20 Mg Precio En Farmacias
Oh my goodness! Incredible article dude! Thank you so much, However I am experiencing
troubles with your RSS. I don’t know why I am unable to join it.
Is there anybody having identical RSS issues?
Anyone who knows the solution can you kindly respond?
Thanx!!
Here is my web blog … weed doctor
hydroxy-chloroquine plaquenil cost canada – buy generic plaquenil
Awesome! Its really remarkable piece of writing, I have got much clear idea about from this piece of writing.
my web blog – https://prettypeople.club/index.php/blog/215212/precisely-how-to-put-plan-cannabis-withdrawal
tadalafil best price uk tadalafil uk pharmacy – tadalafil soft
generic tadalafil in canada
Magnificent web site. A lot of helpful information here.
I’m sending it to several pals ans also sharing in delicious.
And obviously, thank you to your effort!
my blog – http://www.aniene.net/
stromectol medicine
If some one desires expert view regarding running a blog afterward i recommend him/her to pay a visit this blog, Keep up the nice job.
Also visit my blog post :: seeds prior
ivermectin 4 cost of ivermectin pill – ivermectin buy australia
ivermectin 1mg
where to buy tadalafil uk
ivermectin 5 mg price
ivermectin cream 1% ivermectin lotion cost – ivermectin lotion price
I read this piece of writing completely regarding the
comparison of hottest and previous technologies, It’s remarkable article.
over the counter prednisone pills buy prednisone prednisone pill 10 mg
Enjoyed examining this, very good stuff, regards.
Here is my page … sleep problem
cialis 20mg online
tadalafil online 10mg
where to buy generic sildenafil
Hello are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to get started and set up my own. Do you
require any coding knowledge to make your own blog?
Any help would be greatly appreciated!
my blog post :: calories eating
generic cialis cheap canada
ivermectin 2mg buy ivermectin п»їivermectin pills
CUTE BABY ANIMALS – FUNNY VIDEOS – MINI PIG – MUSIC – MICRO PIG 2021 HD
tadalafil order online no prescription
online pharmacy 365
prednisone 20mg cheap prednisone prednisone cost 10mg
tadalafil 20 mg price canada
lowest price cialis
Online random highly secure password generator Password Generator Generate complex ? passwords of different lengths containing traditional, special characters, numbers and emoticons ? for free.
clomiphene generic clomid for men clomid 50 mg
you have a great blog here! would you like to make some invite posts on my blog?
I?d have to check with you here. Which is not something I usually do! I enjoy reading a post that will make people think. Also, thanks for allowing me to comment!
online pharmacy
I love your blog.. very nice colors & theme.
Did you design this website yourself or did you hire someone to
do it for you?
Plz reply as I’m looking to construct my own blog and would like to
find out where u got this from.
thank
you
I?m impressed, I must say. Really rarely do I encounter a blog that?s both educative and entertaining, and let me tell you, you have hit the nail on the head. Your idea is outstanding; the issue is something that not enough people are speaking intelligently about. I am very happy that I stumbled across this in my search for something relating to this.
prednisone 5 mg tablet prednisone for sale prednisone 20mg
The next time I read a blog, I hope that it doesnt disappoint me as much as this one. I mean, I know it was my choice to read, but I actually thought youd have something interesting to say. All I hear is a bunch of whining about something that you could fix if you werent too busy looking for attention.
After study a few of the blog posts on your website now, and I truly like your way of blogging. I bookmarked it to my bookmark website list and will be checking back soon. Pls check out my web site as well and let me know what you think.
I have actually read a few of the writing on your blog site
currently, as well as I really like your writing style.
generic cialis nz
I?d have to check with you here. Which is not something I usually do! I enjoy reading a post that will make people think. Also, thanks for allowing me to comment!
http://edcialislove.online# where can i buy cialis 20mg
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION –
Benson Yerima < Liked it!
where can i buy sildenafil online safely
https://edcialislove.online# cialis 20 mg cheap
There is noticeably a bundle to know about this. I assume you made certain nice points in features also.
http://edviagralove.com/# buy viagra online in melbourne
viagra pfizer usa
where to buy stromectol online
cheap viagra free shipping
tadalafil tablets
buy dapoxetine uk
over the counter allopurinol in mexico
An impressive share, I just given this onto a colleague who was doing a little analysis on this. And he in fact bought me breakfast because I found it for him.. smile. So let me reword that: Thnx for the treat! But yeah Thnkx for spending the time to discuss this, I feel strongly about it and love reading more on this topic. If possible, as you become expertise, would you mind updating your blog with more details? It is highly helpful for me. Big thumb up for this blog post!
Hello! I just would like to give a huge thumbs up for the great info you have here on this post. I will be coming back to your blog for more soon.
https://edviagralove.online# generic viagra canada customs
genaric viagra online
stromectol usa
ivermectin canada
very nice post, i certainly love this website, keep on it
Youre so cool! I dont suppose Ive read anything like this before. So nice to find somebody with some original thoughts on this subject. realy thank you for starting this up. this website is something that is needed on the web, someone with a little originality. useful job for bringing something new to the internet!
viagra 500mg tablet price in india
purchase viagra uk
https://edviagralove.online# viagra in ukВ
viagra repacement
where to buy viagra in mexico
This web site is really a walk-through for all of the info you wanted about this and didn?t know who to ask. Glimpse here, and you?ll definitely discover it.
http://edviagralove.online# where can i buy viagra without a prescription
is there anything over the counter that works like viagra?
home remedies for ed online medications – ed drug prices
You made some decent points there. I looked on the internet for the issue and found most individuals will go along with with your website.
I was very pleased to find this web-site.I wanted to thanks for your time for this wonderful read!! I definitely enjoying every little bit of it and I have you bookmarked to check out new stuff you blog post.
viagra pills 100 mg
viagra online with paypal
stromectol buy uk
canadian drugs online legal to buy prescription drugs without prescription – how to cure ed naturally
canadian tadalafil online
ivermectin cream 1%
ed natural treatment natural ed pills – what causes ed
canadian online drugstore cheap ed drugs – prescription drugs online without
cialis pills 5 mg
buy brand viagra online
buy cheap prescription drugs online top rated ed pills – best ed medicine
sildenafil cost 100mg
tadalafil 2.5 mg tablets in india
ivermectin 500ml: buy stromectol – ivermectin price
cialis pharmacy discount
cost of ivermectin medicine: ivermectin purchase – ivermectin 80 mg
tamoxifen men buy nolvadex – tamoxifen rash pictures
Great blog here! Also your website loads up very fast!
What web host are you using? Can I get your affiliate link to your host?
I wish my site loaded up as fast as yours lol
buy female cialis
Thanks for another informative website. Where else could I get that type of info written in such a perfect way? I have a project that I’m just now working on, and I have been on the look out for such info.
plaquenil medicine hydroxychloroquine over the counter – plaquenil cost in canada
Thank you for all your valuable labor on this web page. My mum enjoys engaging in investigation and it’s easy to see why. All of us hear all relating to the lively mode you present both useful and interesting information via your web site and therefore cause response from people on this topic and our girl is certainly studying a great deal. Take advantage of the rest of the year. You’re carrying out a terrific job.
orlistat capsules 120mg
vardenafil online mexico
When someone writes an post he/she keeps the
thought of a user in his/her mind that how a user can understand
it. Therefore that’s why this paragraph is perfect.
Thanks!
generic viagra online pharmacy uk
stromectol tab 3mg
generic tadalafil usa
I pay a visit everyday some websites and information sites
to read content, but this website presents feature based writing.
prednisone price south africa prednisone – where to buy prednisone uk
purchase prednisone startjpw – prednisone 60 mg tablet
price of cialis 20mg tablets
ivermectin 2mg ivermectin for sale – ivermectin tablets
cialis pills sale canada
online cialis india
cialis online 5 mg
ivermectin buy uk
viagra no rx
tadalafil cheap online
plaquenil for arthritis plaquenil – plaquenil 400
Have you ever thought about adding a little bit more than just your articles? I mean, what you say is fundamental and all. Nevertheless just imagine if you added some great graphics or video clips to give your posts more, “pop”! Your content is excellent but with images and clips, this site could certainly be one of the best in its niche. Terrific blog!
buy ivermectin canada purchase ivermectin – ivermectin 3 mg tablet dosage
sildenafil otc usa
tretinoin 50 cream
ivermectin iv ivermectin for humans – ivermectin coronavirus
tadalafil tablets 20 mg india
lovegra
sildenafil tablet brand name
cialis free shipping
tadalafil 50mg
I truly appreciate this post. I have been looking all over for something like this! Thank goodness I found it on Bing. You have made my day! Thx again! soyos
cheap stromectol
tadalafil buy india
ivermectin price uk ivermectin drg – ivermectin iv
canadian propecia
zoloft generic brand
reputable overseas online pharmacies canada pharmacy safedrg – foreign pharmacy online
cialis et sante
does priligy work
ivermectin uk coronavirus stromectol drg – ivermectin nz
tadalafil capsules
rx tadalafil tablets
tizanidine 4mg capsules price
buy sildenafil 20 mg tablets
buy metformin online australia
cheap generic drugs from india best online international pharmacies india – legitimate online pharmacies india
priligy price in india online
where to buy generic viagra online
Your site is peachy. It is without a doubt quick as well as thanks a lots concerning allowing reviews.
sildenafil 100mg canada pharmacy
I relish going to your website. You are definitely intelligent as well as write so efficiently. Cheers concerning striving on this particular blog site.
I journal frequently and also I honestly value your content. This awesome write-up has undeniably peaked my curiosity. I am mosting likely to book mark your website and also keep looking for fresh info with regards to when a week. I opted in for your RSS feed in addition.
cheap generic drugs from india medication from india – india pharmacy mail order
cialis daily in india
tadalafil 20 mg daily
cialis online for sale
lisinopril online uk
208 lisinopril
buy cialis black online
best pharmacy prices for sildenafil
azithromycin capsules 500mg
atarax 25 mg cost
Zithromax Z Pack
how to get viagra prescription
ivermectin virus
amitriptyline 25mg tablet cost
canadian pharmacy silagra
Woah! I’m really digging the template/theme of this site. It’s simple, yet effective. A lot of times it’s challenging to get that “perfect balance” between superb usability and appearance. I must say you have done a very good job with this. Additionally, the blog loads very quick for me on Firefox. Excellent Blog!
prednisone 20 mg pill
tadalafil 20mg canadian
canadian drugstore cialis cialis au
viagra tablet price
Good article! We will be linking to this particularly great content on our
site. Keep up the good writing.
curved penis and cialis walmart cialis pharmacy
cialis on line
ivermectin malaria
hydroxychloroquine tablets
ivermectin tablets uk ivermectin eye drops
I truly wanted to develop a simple comment to be able to say thanks to you for all the stunning tips you are showing at this website. My incredibly long internet look up has at the end of the day been compensated with incredibly good know-how to exchange with my classmates and friends. I would admit that we site visitors are very blessed to exist in a wonderful site with very many brilliant professionals with good points. I feel quite happy to have seen your entire website and look forward to some more thrilling minutes reading here. Thanks a lot again for a lot of things.
With havin so much written content do you ever run into any issues of plagorism or copyright infringement? My website has a lot of unique content I’ve either written myself or outsourced but it looks like a lot of it is popping it up all over the web without my authorization. Do you know any techniques to help reduce content from being stolen? I’d certainly appreciate it.
buy stromectol online uk
Hello, i believe that i saw you visited my site so i got here to “go back the choose”.I am trying to in finding things to enhance my web site!I suppose its adequate to use some of your ideas!!
purchase stromectol online generic ivermectin cream
sildenafil online prescription
how does viagra work viagra pills
can you buy stromectol over the counter
I wanted to write a simple message to be able to say thanks to you for these remarkable tips and hints you are sharing at this site. My rather long internet research has now been honored with extremely good ideas to share with my close friends. I would repeat that we readers actually are very fortunate to be in a remarkable site with very many wonderful individuals with helpful hints. I feel rather lucky to have used your entire website and look forward to some more pleasurable moments reading here. Thanks a lot once more for a lot of things.
I dont even know how I ended up here, but I thought this post was good. I do not know who you are but definitely you are going to a famous blogger if you aren’t already 😉 Cheers!
buy tadalafil india
vardenafil 20 mg online
tadalafil for sale cheap
buy tadalafil from canada
For most recent information you have to pay a quick visit the web and
on world-wide-web I found this site as a most excellent web site for most
up-to-date updates.
cheap viagra no prescription
over the counter alternative to viagra canadian viagra
of course like your website however you need to take a look at the spelling on several of your posts.
Several of them are rife with spelling issues and I find it very troublesome to inform the truth nevertheless I’ll surely come
again again.
tadalafil tablet buy online india
Hi I am so grateful I found your webpage, I really found you by error, while I was researching on Digg for something else, Nonetheless I am here now and would just like to say cheers for a remarkable post and a all round exciting blog (I also love the theme/design), I dont have time to browse it all at the moment but I have bookmarked it and also added your RSS feeds, so when I have time I will be back to read much more, Please do keep up the superb work.
malegra 200 mg for sale
order acyclovir online
clopidogrel cheap
lexapro sale
buy sildenafil pills online
hello there and thank you for your information – I have definitely picked up anything new from right here. I did however expertise some technical issues using this web site, since I experienced to reload the site lots of times previous to I could get it to load correctly. I had been wondering if your web host is OK? Not that I’m complaining, but slow loading instances times will sometimes affect your placement in google and could damage your high quality score if ads and marketing with Adwords. Well I am adding this RSS to my email and can look out for much more of your respective exciting content. Make sure you update this again soon.|
buy generic tadalafil online cheap
can i buy viagra from india
ampicillin 1000 mg
buy tamoxifen india
cymbalta costs canada
308186793 benicar
ebaylevaquin
discount keflex
generic cialis coupon
20 mg vardenafil
buy cheap sildenafil uk
ivermectin generic
levofloxacin
dipyridamole capsules
buy online sildenafil
order cialis no prescription
online viagra
buy plaquenil 200mg plaquenil 100mg tablets
generic tadalafil canada
cheapest viagra online
gabapentin 100mg generic
order stromectol online
buy tadalafil mexico online
Viagra Generique Livraison Rapide cheap cialis
Today, while I was at work, my sister stole my iphone and tested to see if it can survive a 25 foot drop, just so she can be a youtube sensation. My iPad is now broken and she has 83 views. I know this is entirely off topic but I had to share it with someone!
tadalafil 20 mg online pharmacy
levaquin antibiotics
cialis cheap fast delivery
cialis soft tabs 40mg
cheap lexapro canada
sildenafil 25 mg buy
low price cialis
amoxicillin over the counter australia
cost of stromectol
viagra generic without prescription
prozac canada where to buy
toradol for pain
cymbalta australia
sildenafil online usa
best rx prices for sildenafil
toradol cost
cephalexin 500mg tablets cost
celexa 5 mg daily
ivermectin 3mg tab
ivermectin coronavirus
where to get accutane cheap
buy accutane nz
buy generic acyclovir cream online
generic zyban australia
buy cialis no script
sildenafil nz
200mg sildenafil paypal
buy sildenafil paypal
bactrim buy
tadalafil 5mg price in india
ivermectin 3 mg stromectol pills
where to buy ventolin singapore
sildenafil tablets
I’m still learning from you, but I’m trying to achieve my goals. I absolutely liked reading everything that is written on your site.Keep the posts coming. I enjoyed it!
canadian pharmacy viagra 100mg
mexico rx tadalafil
sildenafil 20 mg online rx
Players should let the past go because it cannot be changed.
can you buy cialis otc in canada
buy tadalafil europe
This is really interesting, You are a very skilled blogger. I’ve joined your feed and look forward to seeking more of your excellent post. Also, I’ve shared your website in my social networks!
cialis gel online
tadalafil capsules 21 mg
Really Appreciate this article, can I set it up so I get an email when there is a new post?
cleocin
cialis fast delivery uk
Excellent blog! Do you have any helpful hints for aspiring writers? I’m planning to start my own website soon but I’m a little lost on everything. Would you suggest starting with a free platform like WordPress or go for a paid option? There are so many choices out there that I’m completely overwhelmed .. Any recommendations? Many thanks!
It’s going to be end of mine day, however before ending I am reading this fantastic post to increase my knowledge.
I precisely wished to thank you so much yet again. I do not know the things I might have done without the entire advice discussed by you relating to such concern. It was actually a very frightful dilemma for me, however , taking a look at this expert fashion you solved the issue took me to leap for fulfillment. Now i am happier for this assistance and then sincerely hope you comprehend what an amazing job you are always providing teaching many others through the use of your blog post. I am certain you have never encountered all of us.
cheap cialis daily
buy phenergan
where to buy tamoxifen online
generic brand viagra
buy prozac online cheap
bactrim over the counter
online otc pharmacy
malegra 100 gel
cialis 5 mg cost
ivermectin 2mg
ivermectin medication
ถ้าคุณกำลังมองหาเว็บดีๆสำหรับบาคาร่าออนไลน์เราขอแนะนำ คาสิโนออนไลน์ ครับจ่ายจริง จ่ายเต็ม จ่ายไม่อั้นไม่มีกั๊กการันตีความมั่นคงด้านการเงินด้วยจำนวนสมาชิกหลักล้านเรามีระบบที่เรียกว่าดีที่สุดรวมถึงระบบฝากถอนแบบอัตโนมัติที่จะทำให้ชีวิตคุณง่ายแบบขีดสุด
stromectol 12mg
where to buy viagra online safely
ventolin 2.5 mg
Muscle injury is much more likely if you begin playing before your muscles are warmed up.
sildenafil pills for sale
phenergan mexico pharmacy
medicine hydrochlorothiazide
triamterene price
viagra in india online
stromectol online pharmacy
generic sildalis
stromectol 12mg online
buy indocin
sildenafil soft gel
cialis dosage generi cialis
25mg lexapro
sildenafil prescription discount
ivermectin 8000 mcg
medicine tadalafil tablets
buy viagra over the counter uk
stromectol price usa
price of ivermectin tablets
ivermectin 3mg
generic cialis singapore
accutane in uk
เมียชวนเล่นครับ ผมเล่นตามเมียครับ เพราะอดใจไม่ได้เห็นถอนเอาๆ เลยลองสมัคร คาสิโนออนไลน์ ดูโอ้โห!แค่สมัครก็ได้เครดิตมาแล้ว โปรเยอะมากครับเว็บนี้ ใครสายโปรโมชั่นต้องไม่พลาดผมนี่ตั้งตารอเลย ทุกวันนี้รายได้จากการเล่นพนันออนไลน์กลายเป็นรายได้หลักไปแล้วครับ
สล็อตออนไลน์ เว็บพนันออนไลน์ที่เรียกได้ว่าเป็นที่นิยมสุดๆ ในวงการเว็บพนันออนไลน์ที่มีมากมายในตอนนี้เพราะในปัจุบันนั้นผู้คนต่างหลังไหลเข้ามาเล่นเกมพนันออนไลน์มากมายด้วยเหตุผลที่ว่าลงทุนน้อยแต่ให้ผลกำไรมากมายนั่นเอง
So many turnovers have occurred because a player wasn’t holding the football firmly enough, and an opposing player just took a swat at it.
gabapentin online uk
You must be sure to stretch all of your muscles prior to playing.
เว็บพนัน เป็นเว็บแทงบอลออนไลน์ที่ดีที่สุดในยุคนี้นั่นไม่ใช่เพียงเพราะมีความมั่นคงด้านการเงินสูงแต่ยังรวมไปถึงระบบที่ใช้นั้นง่ายสะดวก และยังมีระบบช่วยเหลือที่ดีที่สุดคอยให้บริการ 24 ชั่วโมงไม่ว่าท่านจะต้องการคำแนะนำหรือความช่วยเหลือเรามีทีมงานคอยดูแลตลอดแวลา
This practice will teach you how to weave around other players while maintaining control of the ball.
Protein helps muscles rebuild themselves.
stromectol ireland
motilium online uk
50 mg indocin
zyban price uk
stromectol online
stromectol 3 mg
tadalafil online mexico
modafinil cost canada
viagra online india pharmacy
ivermectin cream cost
cost of viagra per pill
generic viagra usa
compare cialis
where to buy viagra online safely
stromectol canada
Stretch it between multiple chairs or over a table so that it’s pushed just to its limit.
buy ivermectin pills
where to buy cialis in uk
จะเล่นเกมออนไลน์ทั้งทีเล่นฟรีๆ ก็ไม่สนุก คาสิโนออนไลน์ ขอชวนคุณมาเล่นเกมแต่ได้เงินไปด้วยกับสล็อตออนไลน์ ได้เงินจริง ได้เงินง่าย สร้างรายได้แบบไม่จำกัด ที่มาพร้อมระบบฝากถอนอัตโนมัติ ไม่มีขั้นต่ำ ทำเองได้ทันทีตลอด 24 ชม.
sildenafil 50mg buy
buy online viagra capsules
bupropion coupon
ivermectin 5 mg stromectol ivermectin
cialis generic from canada
ivermectin antiviral
citalopram for hot flashes
price of cialis pills
order cialis without a prescription
ivermectin pill cost
ivermectin 1% cream generic
fluoxetine 400mg
If your opponent has the ball, there only needs to be one other person there.
fluoxetine prescription online
stromectol 3 mg
cialis 5mg over the counter
cost of stromectol
viagra pills 100 mg
buy ivermectin
ivermectin for humans
cost of prescription drug trazodone
seroquel 400 mg for sleep
seroquel xr high
ivermectin 6 mg tablets
effexor price south africa
buy ivermectin pills
ivermectin antiviral
modafinil online paypal
Best view i have ever seen !
generic cialis in mexico
cost of cialis 20mg tablets
cost of ivermectin 1% cream
My developer is trying to convince me to move to .net from PHP. I have always disliked the idea because of the costs. But he’s tryiong none the less. I’ve been using Movable-type on a number of websites for about a year and am worried about switching to another platform. I have heard great things about blogengine.net. Is there a way I can transfer all my wordpress content into it? Any help would be really appreciated!
fluoxetine 60 mg tablet
stromectol generic
Great blog you have here but I was wanting to know if you knew of any community forums that cover the same topics discussed in this article? I’d really love to be a part of group where I can get feedback from other knowledgeable individuals that share the same interest. If you have any suggestions, please let me know. Appreciate it!
Knowing your routes like the back of your hand will make things go much more smooth in an actual game.
Bend slowly at your knees, then project your body into the air repeatedly, up to 20 times in a row.
ivermectin price
viagra cheap canadian pharmacy
cialis 10mg tablets price
cost of seroquel in canada
viagra canada prescription
aromatase inhibitor tamoxifen buy nolvadex – effexor and tamoxifen
Hello! I know this is kinda off topic but I was wondering if you knew where I could locate a captcha plugin for my comment form? I’m using the same blog platform as yours and I’m having difficulty finding one? Thanks a lot!
I love what you guys are usually up too. Such clever work and coverage! Keep up the very good works guys I’ve added you guys to our blogroll.
If you jumble everything together, trying to get the most material you can get on one page, readers will become overwhelmed.
ขึ้นชื่อว่าคาสิโนถ้าต้องการเข้าไปเล่นก็จำต้องเดินทางไปที่คาสิโน แม้กระนั้นยุคสมัยที่เปลี่ยนไปอยู่ที่บ้านก็สามารถเล่นพนันกับคาสิโนได้นะครับเพียงเข้ามาที่ สล็อตออนไลน์ คาสิโนออนไลน์ด้วยเหตุว่าพวกเราได้รวมรวมเกมคาสิโนมาไว้ตรงนี้หมดแล้วมีอีกทั้งบาคาร่า ยิงปลา พนันบอล สล็อต เรา มีทุกอย่างที่ท่านอยาก
ivermectin 0.08 oral solution
คราวแรกที่เข้ามาที่ แทงบอลออนไลน์ ยอมรับเลยนะครับว่าเสียวๆฮ่าๆแม้กระนั้นเพียงพอซักพักเริ่มชอบใจขอรับเพราะว่าเค้าจ่ายจริง ไม่มีคดโกงนะครับที่สำคัญที่ผมถูกใจคือระบบเค้าดีครับ เข้าใจง่ายด้วย ยิ่งระบบฝากถอนใช้แบบอัตโนมัติ ผมว่าสบายมากมายๆฝากถอนแบบไม่มีอย่างน้อย ไม่ต้องผ่านผู้แทน ทำเองได้เลย
sildenafil online in india
stromectol 6 mg tablet
Some hosting sites will allow you to place them in your blog.
ivermectin malaria
ivermectin cost
retino 0.05 gel
prozac in uk
cialis daily canada
cheap viagra overnight
stromectol tablet 3 mg
zoloft generic medication
buy ivermectin online
tadalafil chewable tablet reviews
stromectol price uk
It is a good idea to keep your blog fresh with a steady stream of unique, interesting content.
canadian pharmacy brand viagra
ivermectin 4000
modafinil online australia
While the text is the most important part of a blog, images help attract readers as well as elaborating on the meaning behind the blog.
viagra india pharmacy
how much does ivermectin cost
australia cialis
I just couldn’t depart your website prior to suggesting that I extremely enjoyed the standard info a person provide for your visitors? Is going to be back often to check up on new posts
Still, video games are quick and hands-on and can be enjoyed during your downtime.
ajanta kamagra oral jelly 100mg
cheap real cialis
bupropion hcl vs xl
online viagra from india
best price for bupropion
fluoxetine 100
10 mg cialis daily
cialis 20 mg in india
wellbutrin xl 300mg wellbutrin without prescription – wellbutrin generic price
ivermectin 200
where can you buy viagra for women
price of ivermectin
stromectol how much it cost
If you enjoy writing, then blogging may be for you!
cialis generic no prescription
where can i buy viagra in south africa
viagra europe
stromectol buy
Awsome info and straight to the point. I am not sure if this is actually the best place to ask but do you people have any ideea where to hire some professional writers? Thx 🙂
ivermectin 1% cream generic
viagra europe over the counter
ivermectin lotion for lice
where to get viagra tablets
stromectol where to buy
citalopram uk cost
stromectol 12mg online
ให้สมาชิกทุกท่านได้ร่วมเดิมพันมากเป็นอันดับ 1 โดยที่เว็บของเรานั้นมีการเปิดบอลให้สมาชิกได้เลือกเล่นมากที่สุดในประเทศ โดยผู้เล่นทุกท่านสามารถสมัครเป็นสมาชิกบนเว็บไซต์ของเราได้เสมอ
cheap viagra in us
sildenafil generic price
stromectol tab
cheap viagra generic best price
ivermectin prescription
cheap viagra no rx
wonderful post, very informative. I’m wondering why the opposite experts of this sector don’t notice this. You should continue your writing. I’m sure, you’ve a great readers’ base already!|
cheap prozac
stromectol canada
cheapest generic viagra
For awhile you have played soccer and continued to learn more of the game’s tricks and techniques.
sildenafil 50mg for sale
cheap cialis without prescription
buy cialis medication
cialis 5mg price canada
where can i buy ivermectin
stromectol covid
viagra pills for men
cheap viagra paypal
Best view i have ever seen !
where can i get viagra in australia
stromectol liquid
ivermectin 4 mg
stromectol order
zoloft lowest price
For many bloggers, putting ads on their blog is the quickest and most reliable way to derive some profit from their efforts.
cialis price in australia
ivermectin 4 tablets price
wellbutrin online no prescription wellbutrin without prescription – wellbutrin 300mg
viagra over the counter uk
kamagra fast delivery
A misplaced tag on your site can be as damaging for your readership as a good tag is helpful.
average cost cialis 5mg
buy tadalafil 20mg price canada
purchase cialis
ivermectin 3mg tab
sildenafil uk 100mg
where can i buy cialis without a prescription
stromectol tablets
where to buy viagra cheap
trazodone for sale
fluoxetine 20 mg brand name
best female viagra tablets in india
retino 0.025 gel
stromectol 3 mg
sildenafil 20mg tablet price
Find out all you can about the history of the soccer clubs in your area.
order viagra from uk
stromectol price
generic viagra from india
ivermectin 5ml
how much is 100mg sildenafil
buy viagra online canada paypal
It is necessary that you use the appropriate font for your blog.
stromectol for sale
how much is cialis in mexico
Best view i have ever seen !
sildenafil 88
ivermectin uk coronavirus
acyclovir cream australia
female viagra tablet in india
can you buy stromectol over the counter
cheap 5 mg tadalafil
australia generic viagra
can you buy cialis over the counter
where to buy viagra tablets
cialis 5mg prices
viagra pills 50 mg
buy generic valtrex online canada valtrex – buy valtrex cheap online
otc cipralex
stromectol cream
best buy viagra online
ivermectin price
sildenafil canada over the counter
viagra in india price
canadian drugstore viagra online
viagra pills cheap online
cost of viagra generic
how to purchase cialis online
ivermectin cost in usa
fast shipping cialis
Today, while I was at work, my cousin stole my iPad and tested to see if it can survive a thirty foot drop, just so she can be a youtube sensation. My iPad is now destroyed and she has 83 views. I know this is totally off topic but I had to share it with someone!
cialis 5mg daily price
sildenafil 50 mg tablet
Howdy I am so thrilled I found your web site, I really found you by mistake, while I was browsing on Aol for something else, Nonetheless I am here now and would just like to say cheers for a incredible post and a all round thrilling blog (I also love the theme/design), I dont have time to look over it all at the moment but I have bookmarked it and also added your RSS feeds, so when I have time I will be back to read more, Please do keep up the fantastic work.
buy ivermectin online
cialis fast delivery usa
ivermectin 3 mg tablet dosage
brand name cialis online
cost of ivermectin lotion
Wow, wonderful weblog layout! How lengthy have you been blogging for? you make running a blog glance easy. The total look of your website is excellent, as smartly as the content!
stromectol for humans
buy generic viagra no prescription
ivermectin drug
provigil daily use
cialis 10mg online canada
400 mg viagra
cialis australia pharmacy
buy viagra online best price
prices of cialis daily use
cost of zoloft 20 mg
cheap stromectol
can i buy viagra in usa
stromectol medicine
ventolin for sale uk ventolin over the counter – ventolin 8g
citalopram 20 mg tab
cheap generic india viagra
This is really interesting, You’re a very skilled blogger. I’ve joined your rss feed and look forward to seeking more of your great post. Also, I have shared your web site in my social networks!
lipitor 40 mg tablet price
over the counter elavil
paxil 40 mg
dexona 4mg tablet online
where to buy real viagra online
cost of strattera without insurance
ivermectin 50
celexa cost usa
bupropion 142
ivermectin brand
aurogra 100mg tablets
cheapest tadalafil online compare prices
aurogra
where to buy motrin
stromectol pill for humans
stromectol liquid
Wow! Thank you! I continuously wanted to write on my site something like that. Can I include a fragment of your post to my blog?
lexapro 10 mg tablet
purchase viagra in australia
disulfiram tablets
viagra order
buy generic viagra no prescription
metronidazole 250mg shipped w/o rx
furosemide pills
gabapentin cream over the counter
ivermectin 90 mg
lasix online no prescription
Hey there this is kind of of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding expertise so I wanted to get guidance from someone with experience. Any help would be greatly appreciated!
500mg zoloft
finasteride price
cialis 10mg coupon
tadalafil generic 10mg
sildenafil 100mg generic
how to get cialis over the counter
tadalafil daily uk
cialis.com
brand viagra price
cialis 5mg pharmacy
ivermectin 50mg/ml
buy ivermectin nz
https://genericpillson.com/# buy generic drugs online lasix
Is anyone here in a position to recommend Plus Size Corsets? Cheers xox
buy generic levitra online uk
ivermectin 6 mg tablets
stromectol nz
cialis online generic
online pharmacy canada viagra
buy sildenafil over the counter
buy ivermectin online
ventolin canadian pharmacy
sildenafil 25 mg tablet price
levitra 5mg 10mg 20mg tablets
dosage of neurontin
tadalafil 47
furosemide 40mg tab
Amoxicillin With Astma
sildenafil 20 mg prescription
ivermectin 4 tablets price
levitra 5 mg
tadalafil dosage 40 mg
sildenafil citrate 100 mg
where to buy dexamethasone
trazodone generic 100mg
ivermectin buy australia
strattera 25 mg discount
buy albuterol online cheap
bupropion 75 mg in india
amitriptyline 100 mg coupon
price of sildenafil in india
sildenafil tablets in india
bupropion 682
lexapro cost canada
3 viagra pills
viagra 2018
generic ivermectin
http://genericpillson.online/# cheap generic drugs from india clomid
cheap canadian pharmacy cialis
india pharmacy cialis
ivermectin 0.5 lotion india
budesonide 9 mg capsules
real viagra online usa
ivermectin cream 5%
sildenafil tablets 150mg
disulfiram brand name in india
modafinil price india
plaquenil usage
buy amoxil online cheap
viagra online generic canada
buy strattera canada
zithromax price in india
buy viagra usa online
sildenafil canada otc
average cost of levitra
aurogra 100 online
effexor 18 mg
generic cialis 5mg australia
bupropion price comparison
low cost cialis
over the counter trazodone
buy cheap tadalafil online
tadalafil over the counter usa
can i buy cialis over the counter in canada
ivermectin buy nz
brand cialis online us pharmacy
cialis tablets for sale
buy viagra using paypal
sildenafil 12.5 mg
how do i get cialis
lipitor brand name price
discount coupon cialis
generic cialis
cheap sildenafil online canada
brand name cialis cheap
I have been examinating out many of your posts and i can claim pretty clever stuff. I will make sure to bookmark your website.
buy zithromax without prescription online
india pharmacy online tadalafil
buy generic flagyl online
80 mg doxycycline
where can i buy oral ivermectin
otc viagra canada
generic name for ivermectin
http://viasild24.online/# drug viagra
I really like your blog.. very nice colors & theme. Did you design this website yourself or did you hire someone to do it for you? Plz answer back as I’m looking to create my own blog and would like to know where u got this from. thanks
tadalafil 20mg price generic
vardenafil online uk
What’s up to every body, it’s my first pay a quick visit
of this website; this weblog contains remarkable and truly fine information in support of readers.
sildenafil generic prescription
can u snort cialis
how to get tadalafil
generic cialis online no prescription
cheap sildenafil tablets
ivermectin lice oral
cymbalta 30 mg price australia
price of viagra 2018
cialis over the counter canada
how much is dexamethasone 4 mg
viagra pharmacy india
ivermectin 5 mg price
viagra for women uk
vardenafil buy without prescription
viagra 100mg online india
You actually make it seem so easy with your presentation but I find this matter to be actually something that I think I would never understand. It seems too complex and extremely broad for me. I’m looking forward for your next post, Ill try to get the hang of it!
stromectol for humans
sildenafil 100mg without a prescription
https://ciatad24.com/# 20mg cialis side effects
retino 0.025 gel
finpecia
fluoxetine medicine
ivermectin nz
how to get cialis from canada
There are some attention-grabbing deadlines in this article however I dont know if I see all of them center to heart. There’s some validity but I will take maintain opinion till I look into it further. Good article , thanks and we wish extra! Added to FeedBurner as properly
buy 5mg tadalafil
It is really a nice and helpful piece of info. Im glad that you shared this useful information with us. Please keep us up to date like this. Thank you for sharing.
online generic sildenafil
wellbutrin price in india
albuterol online no prescription
stromectol 0.1
where to get antabuse
cost of ivermectin lotion
ivermectin price
kamagra india paypal
Thanks so much for the article.Really looking forward to read more. Great.
order stromectol
stromectol in canada
where to buy cialis over the counter
finasteride online pharmacy india
buy furosemide 100 mg
gabapentin side effects in dogs
pharmacy india amoxil no prescription
buy generic paxil
sildenafil india buy
trazodone over the counter
buy cymbalta online cheap
order stromectol online
cost of ivermectin lotion
sildenafil 25 mg price in india
buy budesonide canada
lexapro online prescription
sildenafil online europe
stromectol 0.5 mg
atarax 12
stromectol where to buy
furosemide brand name australia
ivermectin 0.5% lotion
ivermectin 3 mg tabs
http://ciatad24.online/# cialis dosage recommendations
atarax 25 mg cost
tadalafil 20 mg online pharmacy
buy female viagra uk
ivermectin 0.5% lotion
where can you buy viagra pills
finasteride propecia
cialis online price
tadalafil 20mg coupon
how can i get sildenafil
generic tadalafil united states
cialis average price
tadalafil 20mg generic cost
celexa 20 mg tablet
azithromycin prescription
lasix 200 mg
tadalafil soft tabs 20mg
canadian pharmacy cialis no prescription
strattera online canada
aurogra 100 prices
zoloft for sale without prescription
cialis cheapest online prices
60 mg generic cialis
tadalafil india price
tadalafil 20mg online
Comprar Viagra Cialis Y Levitra
300 mg viagra
ivermectin lotion for lice
100mg sildenafil price
fantastic points altogether, you simply gained a brand new reader. What would you suggest in regards to your post that you made a few days ago? Any positive?
generic viagra paypal canada
viagra tablets in india online
buy cialis online without a prescription
https://iverstrom24.online/# stromectol dosage for lice
zovirax costs
viagra 100mg canada
how much is disulfiram cost
cost of wellbutrin in canada
stromectol tab price
purchase zithromax online
order cheap viagra online
where can you get viagra over the counter
trazodone online pharmacy no rx
buy wellbutrin without prescription
buy tadalafil us
citalopram 20 mg tablet
ivermectin syrup
zoloft discount
tadalafil 50mg
mexico viagra prices
cymbalta 20
price of cymbalta australia
buy sildenafil 50mg uk
purchase disulfiram online
singapore cialis
cialis online nz
http://stromectols.com/ stromectol online canada
pharmacy india amoxil no prescription
tadalafil 40 mg
buy stromectol uk
cheapest price for generic lexapro
buy fluoxetine tablets uk
dexamethasone 4 mg tablet brand name
can you purchase sildenafil over the counter
where can i buy cialis without a prescription
cialis 10 mg cost
over the counter lasix
Excellent blog here! Also your web site loads up very fast! What web host are you using? Can I get your affiliate link to your host? I wish my web site loaded up as quickly as yours lol
sildenafil 100 mexico
stromectol ivermectin 3 mg
bupropion zyban
1mg dexamethasone
viagra 100mg in canada
retino 0.05 gel
ivermectin rx
strattera 25 mg pills
sildenafil medicine
tadalafil 10 mg
viagra from canada
atarax price in india
price of ivermectin liquid
cialis online uk
sildenafil 50 coupon
can i order viagra online in canada
how to purchase viagra online in india
trazodone 50 mg tablet price
best place to buy cialis online
wellbutrin 75mg
furosemide 20 mg otc
buy viagra online with mastercard
https://bimatoprostrx.com/ careprost bimatoprost ophthalmic best price
buy tadalafil 20 mg from india
prescription antabuse
cheap stromectol
cheap stromectol
tadalafil 5 mg mexico
ivermectin price comparison
anafranil 25mg
where to get sildenafil online
generic viagra 150 mg
cialis cost in mexico
buy real viagra no prescription
cheap cialis generic
atarax 50
I quite like reading an article that will make people think.
Also, thank you for allowing me to comment!
sildenafil 50 mg online india
trazodone 10mg
buy cheap cymbalta
Has anyone shopped at Electric Puff Vapor Shop Vape Store in 215 Central Ave?
nivaquine-p
buy ivermectin
tadalafil buy online canada
cheap viagra online pharmacy
cost of brand name synthroid
cialis 20mg canadian pharmacy
where to buy sildenafil in canada
aurogra 100mg tablets
tadalafil 20 mg best price
http://plaquenils.online/ generic hydroxychloroquine
ช่วงต้นผมว่าLSM789z ไหนก็เช่นเดียวกัน เนื่องจากเข้าไปก็เจอเกมเดิมๆแม้ว่าเอาเข้าจริงๆมันไม่เหมือนกันขอรับ ยิ่งเว็บไหนที่เวลาฝากถอนจำเป็นที่จะต้องผ่านเจ้าหน้าที่อันนี้ผมรังเกียจสุดเลย เสียเวล่ำเวลา ส่วนตัวผมว่า เว็บพนัน ดีสุดเลยจ้ะนะครับ เค้าใช้ระบบอัตโนมัติ
paroxetine prescription online
stromectol cream
where can i get cheap amoxicillin
เกมออนไลน์ทำเงินที่มีผู้คนสนใจเยอะที่สุดคงจะหนีไม่พ้นบาคาร่าเนื่องจากว่าเป็นเกมที่เข้าใจง่ายเล่นง่ายจบไวในแต่ละรอบ ทำให้คุณสามารถทำเงินได้ไว ส่งผลให้ผลกำไรขึนได้ไวมากมาย ไม่เพียงเท่านี้คุณยังสามารถเล่นบาคาร่าได้พร้อมทีละหลายโต๊ะอีกด้วย
cheap generic viagra from canada
viagra best buy coupon
ivermectin 400 mg
zovirax tablets otc
azithromycin z-pak
aurogra 100 mg
order cheap generic viagra online
brand name viagra for sale
canadian pharmacy citalopram
where to buy cheap viagra in usa
where to buy cialis over the counter uk
sildenafil 100mg uk
buy zithromax
cymbalta brand name 30 mg
cheap cymbalta generic
I simply couldn’t depart your site before suggesting that I extremely enjoyed the standard info a person provide for your guests? Is going to be again regularly in order to inspect new posts check more…
stromectol medicine
cialis 20 mg tablet cost
ivermectin brand
online tadalafil us
viagra comparison
ivermectin 50
generic tadalafil canada
buy cialis without a prescription
generic tadalafil 40 mg
stromectol medication
http://stromectols.online/ stromectol prices
You really make it seem so easy with your presentation but I
find this matter to be really something that I
think I would never understand. It seems too
complicated and very broad for me. I am looking forward for your next post, I
will try to get the hang of it!
paroxetine tabs
2020 citalopram
viagra script
malegra 120
buy atarax 25 mg
buy viagra in usa
endep 10 10 mg
tadalafil 20mg price in usa
aurogra 100 uk
where can i get generic cialis
aurogra tablets
stromectol buy
cheap cialis tablets
buy paxil online usa
generic cialis nz
kxaagk https://stromectolr.com generic ivermectin
sildenafil without a prescription
discount pharmacy sildenafil
generic for atarax
elavil for migraines
soft cialis online
real viagra
10 mg tadalafil daily
cialis online fast shipping
order viagra india
buy cialis for daily use
sildenafil 20 mg online india
how much is generic tadalafil
by viagra
generic cialis 10mg
cialis for daily use coupon
sildenafil 20 mg price comparison
generic viagra canada cost
generic viagra capsules
buy cialis from australia
cheap cialis fast
viagra tablets australia
1 viagra pill
cialis daily in india
tadalafil softgel capsule 20mg
ebuufd https://stromectolr.com stromectol prices
30 mg tadalafil
generic cialis 100mg
cialis online fast delivery
cialis for daily use online
brand viagra australia
sildenafil generic price uk
30 mg sildenafil
buy tadalafil 20
best generic cialis brand
generic cialis from uk
buy tadalafil online cheap
best generic cialis prices
online pharmacy cialis
cialis daily 5mg online
sildenafil 50 mg tablet price
how to buy viagra in australia
tadalafil canadian pharmacy
sildenafil tablets 100 mg
best online sildenafil prescription
what is the cbd target customer
5mg cialis daily use
cialis price canada
sildenafil 90 mg
tadalafil 10mg daily
tadalafil 20mg lowest price
Generic Viagra Super Force
sildenafil viagra
where can i order cialis online
cheap viagra tablets uk
where to get generic cialis
cheapest generic tadalafil online
generic cialis 5mg canada
rx sildenafil
price generic sildenafil
how to buy tadalafil online
canadian pharmacy cialis brand
tadalafil pill
viagra over counter
tadalafil canada price
sildenafil buy over the counter
tadalafil 10 mg cost
rx sildenafil tablets
zithromax 500 mg lowest price pharmacy online zithromaxsnw generic zithromax online paypal
jvzorv
best price generic viagra online
cialis pill
best price on cialis
female viagra over the counter
cialis 40 mg price
cialis 4 sale
brand name cialis from canada
cialis 20 price
buy cialis india pharmacy
is propecia worth it
online cialis paypal
online viagra purchase
cost for cialis for daily use
Baclofen Vente En Canada
canada cialis generic
buy viagra online cheap india
best generic viagra online
order viagra online us
canadian viagra no prescription
cialis canada online
where can i purchase viagra
where can i buy viagra pills
viagra.com
online pharmacy for cialis
levitra sale
buy cialis canada
cialis 5 mg daily use cost
can i buy sildenafil citrate
purchasing viagra
online viagra sales
cialis pills sale
cialis uk
viagra 10 pills
buy cheapest generic viagra online
can i order cialis online
cialis 2.5 coupon
how can i get viagra without a doctor
cialis price uk
viagra generic
where to buy female viagra
I know this if off topic but I’m looking into starting my own weblog and was wondering what all is
required to get set up? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web smart so I’m not 100% positive. Any suggestions
or advice would be greatly appreciated. Many thanks
cost of cialis in india
This is a great tip particularly to those new to the blogosphere.
Brief but very accurate information… Thanks for sharing this
one. A must read post!
cialis daily use 5 mg
viagra prescription singapore
viagra 100mg uk
compare cialis prices
cialis in india price
cheap genuine cialis
Attractive section of content. I just stumbled upon your website and in accession capital to assert that I acquire actually enjoyed account your blog posts. Any way Ill be subscribing to your feeds and even I achievement you access consistently rapidly.
Great I should certainly pronounce, impressed with your website. I had no trouble navigating through all tabs as well as related info ended up being truly easy to do to access. I recently found what I hoped for before you know it at all. Reasonably unusual. Is likely to appreciate it for those who add forums or something, website theme . a tones way for your customer to communicate. Nice task..
cialis 5mg cost canada
buy generic viagra 100mg online
buy cheap viagra generic online
cheap generic viagra no prescription
Good website! I truly love how it is simple on my eyes and the data are well written. I’m wondering how I could be notified whenever a new post has been made. I have subscribed to your feed which must do the trick! Have a great day!
cialis pills online india
cailis
But yeah, thanx for spending some time to talk about this matter here on your web site.
how much is viagra 100mg
viagra uk
can i buy genuine viagra online
buy cialis 5mg
cialis price in south africa
cialis 2.5 mg tablet
generic female viagra online
how to order generic cialis
how much is tadalafil
retail price of viagra
viagra on line
daily cialis canadian pharmacy
cialis buy online
tadalafil for sale canada
buy viagra 100mg online india
generic viagra 100mg pills
buy viagra fast shipping
viagra generic india
cialis 5mg daily for sale
cheap online cialis
cialis 20mg
how to buy generic cialis
cost of cialis 5 mg in canada
generic cialis 2018 canada
can you buy real viagra from canada
viagra over the counter nz
cheapest tadalafil 20 mg
viagra capsules in india
how to order viagra
viagra pills canada
best price for viagra 50mg
viagra online pharmacies
where can i buy cialis cheap
viagra prescription discount
viagra vs cialis
viagra online canada mastercard
viagra 1000mg price
viagra 150 mg online
viagra 100 mg generic
cial
canadian rx viagra
purchase cialis with paypal
cialis daily cost
generic cialis online fast shipping
cialis comparison
generic viagra online pharmacy usa
female viagra pill online
cheap generic viagra uk
where can you get cialis over the counter
Completely I share your opinion. It is excellent idea. It is ready to support you.
http://cobakaya.com/wp-content/soz/
generic viagra for sale in canada
viagra 100mg buy online india
cheap daily cialis online
cialis 20mg price in mexico
viagra sildenafil
cialis pills uk
cialis 120
prices for cialis
generic viagra united states
how to buy viagra over the counter uk
best canadian cialis
generic viagra cost in canada
viagra uk fast delivery
sildenafil 100 mexico
cost cialis 20 mg
canada cialis no prescription
cialis 2.5 mg price india
canadian pharmacy cialis brand
cheapest cialis
cialis brand
I’ve been surfing on-line greater than three hours nowadays, yet I never discovered any interesting article like yours. It’s beautiful worth sufficient for me. Personally, if all webmasters and bloggers made good content as you probably did, the net can be much more helpful than ever before.
where to buy viagra usa
buy cialis online fast shipping
canadian pharmacy cialis 10mg
generic viagra soft 100mg
generic brand viagra
where to buy generic cialis safely
cialis 100mg for sale
cialis pharmacy coupon
buy female viagra nz
cialis 10mg canada
buy pfizer viagra
viagra online purchase canada
generic cialis professional
cialis pricing
cheap online viagra
viagra drugstore
blue chew cialis
cialis generic best price canada
viagra sildenafil
viagra tablet 100mg price
female viagra capsules in india
cheapest 20 mg cialis
buy female viagra uk
cilias canada
where to get viagra in australia
buy viagra professional
bluechew tadalafil
tadalafil tablet online in india
sildenafil tablets 100mg
canada viagra
tadalis sx soft
where can you buy cialis in canada
purchase genuine viagra online
viagra 100 mg for sale
sildenafil 100mg price online
cialis 10mg india
where to get generic cialis
buy cialis online uk
buy cialis soft tabs online
can i buy viagra online in india
lasix otc canada
clomid generic cost
prednisolone 25mg price
sildenafil capsules in india
how to buy cialis online in canada
order viagra online
clomid pills uk
where can i purchase propecia
viagra cost per pill
atenolol 40 mg price
how much is kamagra
modafinil daily
where to buy tadalafil in singapore
generic tadalafil coupon
how to get modafinil uk
furosemide cost us
canadian pharmacy acyclovir cream
cheap tadalafil 5mg
stromectol 0.5 mg
cymbalta for sale in canada
ordering antabuse
viagra for sale cheap
buy furosemide tablets uk
sildenafil 20 coupon
generic cialis pills
kamagra 100mg oral jelly online
kamagra jelly for females
finasteride coupon
hydroxychloroquine 200 mg tablet
augmentin 125 mg tab
nexium 20 mg tablet
india pharmacy online tadalafil
sildenafil cost
tetracycline 250 mg
sildenafil 25 mg mexico
tadalafil 10mg online india
tadalafil 20 mg daily
provigil uk prescription
celexa 40 mg tablet
kamagra jelly srbija
finpecia online
furosemide 200 mg tab
cheapest cialis generic
cheap kamagra tablets
bupropion sr 150 mg without a prescription
can you buy seroquel over the counter
bupropion hcl 100mg
tadalafil generic 10mg
buy modafinil 100 mg
cialis generic 20 mg
doxycycline generic cost
discount cialis
cialis 2.5 daily
order female viagra
tadalafil tablets
zestoretic 20 12.5 mg
75 mg clomid
how much is furosemide 40 mg
aurogra 100
can i purchase cymbalta in canada
where can i buy stromectol
seroquel od
tretinoin price
tadalafil over the counter usa
generic tadalafil online 20mg buy
budesonide 0.5 mg
viagra 25mg online
Every weekend i used to go to see this website, because i want enjoyment, as this this site conations genuinely fastidious funny stuff too.|
seroquel 300
buy paxil usa
prozac 30 mg capsules
fluoxetine online india
kamagra oral jelly suppliers
buy sumycin online
finpecia 1mg price in india
aurogra 100 online
acyclovir 400 mg tablet price
cialis 100mg
furosemide medication
generic viagra canada pharmacy
cymbalta 90 mg daily
furosemide online canada
tadalafil from mexico
wellbutrin zyban
sildenafil canada over the counter
prednisone generic brand
generic viagra pills
cost for generic cialis
viagra script online
cialis india
buy viagra 100mg online uk
sildenafil generic otc
female cialis canada
007 viagra
sildenafil cheap buy
cheap cialis online
where can i buy brand name cialis online
cialis 5mg daily
20 mg tadalafil best price
sildenafil 20 mg prescription
Does anyone have any idea Upscale Vapors ecig shop located in 101 Grand Boulevard sells e-juice made by Signature Vape Juice? I have emailed them at hucklebucksmichigan@gmail.com
sildenafil fast delivery
generic viagra in us
best over the counter female viagra
viagra tablets from india
sildenafil rx coupon
viagra on the web
buy cialis daily use online
can you buy viagra over the counter
cost of viagra per pill
price of viagra in canada
viagra tablet price in india
tadalafil 20mg price in india
buy cialis online no prescription usa
canada rx sildenafil
sildenafil cream
purchase generic viagra in canada
cialis over the counter canada
canada cialis no prescription
viagra usa buy
sildenafil online for sale
buy viagra online cheap india
tadalafil from canada to usa
generic tadalafil in usa
cilias canada
20 mg sildenafil cost
buy cialis online no prescription
buy cialis online australia
buy viagra online 100mg
prescription viagra cheap
cheap viagra
where can i buy viagra in australia
canadian cialis cheap
cialis website
tadalafil for sale from india
cheap viagra online free shipping
cheap viagra pills usa
cialis generic viagra
albuterol cost in canada
tadalafil 20mg lowest price
buy xenical online cheap
buy glucophage 850 mg
generic cialis 80mg
50 mg viagra
malegra 120
Hello, everything is going sound here and ofcourse every one is sharing facts, that’s actually excellent, keep up writing.|
tadalafil prices
diflucan coupon
dipyridamole
celexa cost uk
purchase propecia online
where to buy viagra in india
buy viagra over the counter usa
abilify 5 mg canada
avodart cost
cialis everyday
baclofen brand name australia
liquid herbal kamagra kamagra gi kamagra uk prices
abilify 5mg
ivermectin 2%
Hello there! Do you know if they make any plugins to protect against hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any suggestions?|
best australian online pharmacy
prescription for viagra
where can you purchase viagra
where can you buy diflucan over the counter
avodart india price
where to buy ventolin nz
nolvadex tablet price
amoxicillin 875 mg buy online
buy online cialis canada
where can i buy bactrim
molnupiravir tablet
buy generic indocin
cheap sildenafil online
valtrex cost canada
rx pharmacy no prescription
how much is elimite cream
ivermectin 3mg for lice
stromectol for humans
tadalafil tablets cheap
Nice blog here! Also your web site loads up very fast! What host are you using? Can I get your affiliate link to your host? I wish my web site loaded up as fast as yours lol|
where can i buy cipro online
generic avodart canada
cialis europe online
cost of lopressor 50 mg
buy zoloft from canada
plavix medication
online avodart without prescription
celexa 200 mg
cytotec medicine price
plavix 5 mg tablet
albuterol 021
tadalafil 2.5 mg in india
diflucan discount coupon
online flagyl
cozaar 25 mg price
online pharmacy canada generic viagra
sildenafil prescription australia
buy generic cialis
cafergot uk
ivermectin 3 mg dose
plaquenil for osteoarthritis
metformin online no prescription
stromectol buy
cialis canada online pharmacy
order zoloft
generic dutasteride
avana online
glucophage generic
buy viagra without prescription viagra use in children 247overnightpharmacy Scam
can you buy tadalafil online
amoxicillin prescription price
Has anybody ever shopped at Vape Ave. Vape Store in 17-19 Stockwell Road?
where can i buy priligy
cialis generic buy online
stromectol pill price
ivermectin drug
stromectol drug
buspar 5 mg
purchase cheap viagra online
glucophage 500mg cheap
price of stromectol
prescription orlistat
cafergot canada
celebrex 800 mg
terramycin nz
average cost of cialis for daily use
buy modafinil online usa
sildenafil 25 mg mexico
ivermectin 1 topical cream
viagra online cheap india
priligy tablets
viagra prescription discount
amoxil over the counter
azithromycin buy online australia
buy flomax uk
buy lisinopril online usa
cheap vardenafil online
online cialis prescription cialis 40 mg g postmessage cialis smiley remember
sildenafil 2
tadalafil purchase
avodart sale
viagra medicine price in india
provigil for sale canada
generic viagra professional 100mg
provigil from canadian pharmacy
ivermectin price uk
generic cialis 20mg pills
citalopram 20 mg cost
cost of cialis 5mg pills
best buy viagra online
best tadalafil tablets in india
cost cialis daily use
nolvadex over the counter
buy sildenafil online europe
india pharmacy tadalafil
advair prescription price
furosemide davis drug guide furosemide and potassium cialis does not work
jasochlor
best viagra for women
prescription cialis online pharmacy
aralen tab 150 mg
cost of cialis prescription
seroquel xr and weight gain
sildenafil citrate tablets
plaquenil hydroxychloroquine cost
sildenafil 20 mg price
trazodone online
buy real viagra uk
generic sildenafil canada
tadalafil purchase
ivermectin prescription
buy ivermectin for humans australia
malegra pills
prednisone 12 mg
generic cialis 60 mg india
nolvadex 20 mg tablet
cost of stromectol medication
how to get cheap tadalafil online
atarax 25mg online
aurogra 100
fluoxetine 10mg tablet
where can i buy prednisone without a prescription buy prednisone online Stendra Erectile Dysfunction
how much is sildenafil in canada
online generic sildenafil
order viagra
sildenafil 150 mg online
tretinoin cream .1
citalopram 40mg brand name
doxyciclin
Achat Cialis France Sans Ordonnance priligy for sale dapoxetine priligy uk
online pharmacy tadalafil 20mg
ivermectin lice
tadalafil soft tablets 10 mg
viagra in canada for sale
tadalafil online no rx
prices of sildenafil
can i buy cytotec over the counter in south africa
tadalafil 2.5 mg online india
can you buy generic viagra over the counter
order accutane online uk
cheap cialis
how to buy modafinil in india
buy online doxycycline
cialis 10mg online
buy cialis 20mg online canada
citalopram online
where to buy real viagra online
buy accutane with paypal
online pharmacy usa viagra
viagra prescription discount
tretinoin from india
cheap cialis 20mg online
buy cialis online fast delivery
tadalafil 10 mg coupon
modafinil capsules
order viagra online canadian pharmacy
zovirax tablets over the counter
tadalafil soft tablets 20mg
stromectol generic
effexor 27.5
generic tamoxifen for sale
cialis generic pills
ivermectin lotion cost
azithromycin over the counter uk
effexor without prescription
canada order cialis
medication neurontin 300 mg
where to buy azithromycin over the counter
stromectol canada
buy cozaar online
cost of ivermectin lotion
cialis 20mg cost canada
feldene 10 mg cost
buy dapoxetine 60mg
ivermectin 1 cream 45gm
brand name cialis from canada
brand cialis prices
buy priligy online
100mg sildenafil 30 tablets price
where to buy tadalafil on line
propecia price in usa
seroquel 400 mg pill
generic effexor
cost tadalafil generic
450mg effexor
chloroquine 200
canadian pharmacy gabapentin
cialis tadalafil 20 mg
average cost cialis
proscar price uk
neurontin capsules 300mg
generic augmentin prices
zovirax suspension
prozac 20
lopressor tablet
buy generic cialis online with paypal
cheap generic cialis uk
can i buy tadalafil in mexico
stromectol otc
chloroquine 150
viagra no prescription uk
hydroxychloroquine sulfate 200mg
purchase doxycycline
tamoxifen 2018
1000 mg augmentin
nexium 40 mg price usa
azithromycin 500mg tablets price in india
tadalafil in india online
stromectol cost
piroxicam discount
seroquel generic 25mg
buy zovirax online cheap
where to buy cialis safely
buy gabapentin 300mg online
tamoxifen 2019
cost of cozaar 100 mg
mail order levitra
price generic sildenafil
generic clomid online
sildenafil generic 50 mg
Sweet blog! I found it while surfing around on Yahoo News. Do you have any tips on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there! Thanks|
Has anybody ever shopped at Monster Vape Vapor Store located in 210 N Western Ave, Suite 105A?
dapoxetine 30 price in india
viagra 1000mg
viagra prescription coupon
how much is the viagra pill
buy viagra australia paypal
gabapentin 900
best viagra prices
cost viagra
cialis discount prices online
where to buy generic viagra in usa
ivermectin 8000
online tadalafil us
fildena canada
Hello, Neat post. There’s a problem along with your website in web explorer, may test this? IE nonetheless is the market leader and a big component of folks will miss your wonderful writing because of this problem.|
price of ivermectin tablets
ivermectin cost australia
buy cheap viagra online from india
online viagra cheap
cheap generic viagra india
online real viagra
stromectol pills
order prevacid
best viagra over the counter
ivermectin 50 mg
viagra for women uk
stromectol liquid
cialis 10mg india
price of viagra 100mg
quineprox 80 mg
generic viagra 100mg
cialis 20mg for sale
blue chew cialis
motilium otc usa
sildenafil 100 canadian pharmacy
cheap cialis soft
buy cialis on line without prescription
diflucan rx online
can i buy cialis over the counter canada
cialis 5 mg best price
cialis 5mg cost
5mg tadalafil price
ordering cialis online in australia
buy stromectol online
ivermectin 1mg
seldenafil
I really like reading through an article that will make people think. Also, thank you for allowing me to comment!|
how to get ivermectin
cost cialis
ivermectin 6mg
how to get cialis
tadalafil 20mg price in usa
sublingual viagra
plaquenil 20 mg
how to order sildenafil from canada
generic cialis 2.5 mg
cost of ivermectin 1% cream
ivermectin 50mg/ml
60 mg tadalafil
viagra generic canada price
purchase viagra online from canada
buy viagra canada fast shipping
cialis 5mg daily canada
If you are going for most excellent contents like me, simply
pay a visit this site everyday as it gives feature contents, thanks
ivermectin 3mg tablets
price generic viagra
buy cialis australia
buy viagra in singapore
I am really impressed together with your writing skills and also with the structure for your blog. Is this a paid subject or did you customize it your self? Either way stay up the nice quality writing, it’s uncommon to look a nice blog like this one today..|
buy indocin online
order cialis online us pharmacy
otc tadalafil
Can I simply say what a comfort to find a person that truly knows what they are discussing on the web. You definitely understand how to bring an issue to light and make it important. More people really need to read this and understand this side of the story. I was surprised you are not more popular because you most certainly have the gift.|
cheap tadalafil 60 mg
viagra cost per pill
viagra 100mg pills generic
best cialis prices
how to get tadalafil
pharmacy online tadalafil
brand viagra uk
norvasc a beta blocker
The other day, while I was at work, my cousin stole my iPad and tested to see if it can survive a 25 foot drop, just so she can be a youtube sensation. My iPad is now broken and she has 83 views. I know this is entirely off topic but I had to share it with someone!|
order viagra cheap
We’re a group of volunteers and starting a new scheme in our community. Your site offered us with valuable info to work on. You have done an impressive job and our entire community will be thankful to you.|
Very interesting info !Perfect just what I was searching for! “Wherever the Turkish hoof trods, no grass grows.” by Victor Hugo.
viagra 50 mg
cialis for men
cialis drug prices
viagra 100mg canada
stromectol prices
ivermectin buy canada
cialis without a script
viagra 50mg online
stromectol 15 mg
viagra usa 100mg
ivermectin buy
buy cialis wholesale
cheap cialis paypal
cialis daily online
can i buy viagra online legally
ivermectin prescription
cialis 50mg price in india
Currently it looks like Expression Engine is the preferred blogging platform out there right now. (from what I’ve read) Is that what you’re using on your blog?
cheap 25mg viagra
canada cialis
tadalafil online in india
sildenafil cost usa
ivermectin
ive got alot of free get older on my hands recently, thus ive settled to begin blogging again, . . does anybody know any fine blogging sites which are free and easy to use?? (apart from tumbr and blogger/google ). . thanks (:.
cialis prescription australia
cialis cheap
cost of cialis generic
canadian cialis online
buy viagra price
I look articles online all the time and some are quite interesting. in the past I’ve written quite a few articles myself, and even published a few books, it could be long-suffering for me to get my proclaim out there by presenting my articles. How would I go more or less putting them online for everyone to access, and could I create maintenance posting them? This may be a silly ask but, do people generally set sights on copyright for their online articles? Thanks..
cialis tablets 5mg price
ivermectin 200 mcg
buy cialis price
online cialis 5mg
I always spent my half an hour to read this blog’s articles or reviews daily along with a cup of coffee.|
sildenafil 25 mg tablet price
If some one wants to be updated with latest technologies after that he must be pay a quick visit this site and be up to date everyday.|
buy ivermectin
ivermectin 5 mg price
cialis 2.5 mg daily use
generic viagra europe
genuine cialis canada
generic for hydroxychloroquine 200 mg
sildenafil from india
tadalafil chewable tablets
cheap cialis online
Great beat ! I would like to apprentice whilst you amend your site, how can i subscribe for a blog web site? The account helped me a applicable deal. I had been tiny bit acquainted of this your broadcast offered shiny transparent concept|
cialis capsule
ivermectin over the counter
cost generic viagra
cialis 10mg online
generic cialis soft 20mg
online viagra pills
how do i buy viagra
stromectol over the counter
pharmacy cialis
stromectol uk buy
cheap cialis 5mg australia
ivermectin price comparison
best online pharmacy uk viagra
paxil uk buy
can i order viagra
erectafil 20 online
avodart capsules 0.5 mg
buy sildalis 120 mg
cheap cialis pills
viagra for women buy
professional cialis
levaquin drug
where can i buy cheap cialis
vermox 500 tablet
buy cialis now
cialis pills sale canada
lopressor 25 mg price
estrace 6mg
discount female viagra pills
buy paroxetine online uk
where can i order viagra online
sildenafil india price
stromectol tab 3mg
female viagra brand name
Hi there would you mind stating which blog platform you’re using? I’m planning to start my own blog in the near future but I’m having a difficult time making a decision between BlogEngine/Wordpress/B2evolution and Drupal. The reason I ask is because your layout seems different then most blogs and I’m looking for something unique. P.S My apologies for being off-topic but I had to ask!|
buy generic cialis usa
Thanks , I’ve just been searching for info approximately this topic for a long time and yours is the greatest I have came upon so far. But, what concerning the conclusion? Are you positive in regards to the source?|
sublingual viagra
buy real viagra online uk
cialis discount price
cialis 20 mg price in india
sildenafil online buy india
doxycycline capsule price
cheap viagra prices
how much is viagra in usa
generic augmentin 875
antabuse online india
best price cafergot
drug prazosin
10mg tadalafil
Spot on with this write-up, I truly assume this website needs rather more consideration. I’ll probably be once more to learn far more, thanks for that info.
I haven’t checked in here for some time because I thought it was getting boring, but the last several posts are good quality so I guess I’ll add you back to my daily bloglist. You deserve it my friend 🙂
Do you have a spam problem on this blog; I also am a blogger, and I was wondering your situation; many of us have created some nice procedures and we are looking to swap techniques with others, please shoot me an e-mail if interested.|
fluoxetine prices usa
real viagra online no prescription
sildenafil order without prescription
buy tadalafil from canada
Just wish to say your article is as astounding. The clarity on your put up is simply nice and i could suppose you are knowledgeable on this subject. Fine together with your permission let me to grasp your RSS feed to stay up to date with drawing close post. Thank you 1,000,000 and please carry on the enjoyable work.|
viagra order online india
generic viagra medication
tadalafil chewable
fildena 100 canada
viagra for women australia
buy cialis 5mg online australia
top 10 online pharmacy in india
online pharmacies that use paypal
paxil weight loss
cialis 10mg price in india
stromectol generic
metformin order canada
trazodone 200 mg tablet
save on pharmacy
on line viagra
metformin tab cost in india
cheapest metformin 500 mg
price for viagra in canada
can i buy viagra in australia
Hello my friend! I want to say that this article is amazing, nice written and come with almost all significant infos. I’d like to look extra posts like this .
erectafil 20 for sale
canada discount pharmacy
viagra price online
cialis 20mg price in india online
generic cialis tablets
cialis buy online
reputable online pharmacy no prescription
ivermectin 200mg
viagra online costs
canadian online pharmacy tadalafil
where to get cialis cheap
albendazole 400mg tablet price
viagra buying canada
where to buy prednisone for dogs without prescrition Here we will review them only briefly.
biaxin ear infection
viagra mastercard online pharmacy
buy viagra online usa no prescription
generic viagra 50
cialis 800
where to buy sildenafil uk
order antabuse over the counter
https://www.normalbookmarks.win/eset-nod32-endpoint-antivirus-crack
viagra pills for sale canada
cialis 6
I believe this internet site has some rattling great information for everyone :D. “Calamity is the test of integrity.” by Samuel Richardson.
excellent put up, very informative. I ponder why the other specialists of this sector do not notice this. You should continue your writing. I am sure, you have a great readers’ base already!
Cialis Effet Secondaire Levitra Plaquenil hormone secreted by the pituitary gland to stimulate maturation of the egg cell ovum
average price of viagra
http://www.bausch.in/en-in/redirect/?url=http://maliksofts.com/fl-studio-20-8-1-crack-registration-key-download/
Greate article. Keep writing such kind of information on your blog. Im really impressed by it.
ivermectin 0.5 lotion
http://frienddo.com/out.php?url=https://www.ulule.com/o5vcscm254/
It’s really a nice and useful piece of information. I am happy that you shared this helpful information with us. Please keep us up to date like this. Thanks for sharing.|
where can i buy brand name cialis online
viagra in mexico cost
sildenafil citrate generic
cialis 2.5 mg coupon
stromectol pill price
how much is viagra uk
tadalafil online india
ivermectin prescription
cheap generic tadalafil 5mg
average cost for cialis
https://www.social-bookmarkings.win/coreldraw-graphics-suite-free-download
Every weekend i used to visit this web site, for the reason that i want enjoyment, for the reason that this this website conations truly good funny stuff too.|
cialis cost in india
http://night.jp/jump.php?url=https://www.romeo-bookmarks.win/hma-pro-vpn-license-key-2021
buy cialis online safely
how to get cialis cheap
generic viagra 200mg
Hi it’s me, I am also visiting this website daily, this web page is really nice and the viewers are really sharing fastidious thoughts.|
An added important part is that if you are an older person, travel insurance for pensioners is something you ought to really look at. The more mature you are, the more at risk you will be for permitting something awful happen to you while in most foreign countries. If you are not necessarily covered by a number of comprehensive insurance cover, you could have some serious troubles. Thanks for discussing your advice on this weblog.
canada pharmacy daily tadalafil
cialis 5mg cost
buy cialis online generic
cialis cost usa
tadalafil 100mg price
cheap female viagra pills
otc cialis 2017
viagra online australia fast delivery
stromectol covid
i need viagra
canadian pharmacy cafergot
https://getpocket.com/redirect?url=https://installcracks.com/tally-erp-9-crack-serial-key/
If some one wishes to be updated with most up-to-date technologies therefore he must be pay a visit this web site and be up to date every day.|
I am supplementary to blog subscriptions and I am looking for an simple reader that is kind and organized that lets me view my blogs from my homepage or has a little scrollbox that is always taking place on the side of the computer screen. I started to use bloglines but it is in point of fact unorganized similar to every the blog names lined in the works on the side. Thanks a lot!.
http://kassi2.rosx.net/php/url.php?url=https://cracxpro.com/eset-nod32-antivirus-crack-license-key-full/
You should be a part of a contest for one of the best sites online. I’m going to highly recommend this site!|
amoxicillin 500 mg where to buy
ivermectin 90 mg
ivermectin 0.2mg
cheap stromectol
ivermectin 90 mg
ivermectin 6 tablet
buy ivermectin stromectol
buy ivermectin
stromectol in canada
ivermectin for sale
ivermectin 3mg dosage
ivermectin canada
cialis daily use online
Do you have any idea where I can buy: Ultra Relief CBD Gel -1000mg by JUSTCBD and 1000mg Delta 8 Gummies Exotic Peach by JUST DELTA. I am struggling to find the official site! Thanks in advance 🙂
Bbfvvd Best Generic Viagra Pharmacies Plaquenil
Hi there, after reading this awesome post i am too happy to share my familiarity here with mates.|
Great page, thanks for sharing, very useful information
Hi there fantastic website! Does running a blog such as this take a great deal of work? I’ve no understanding of computer programming but I was hoping to start my own blog in the near future. Anyhow, if you have any recommendations or tips for new blog owners please share. I know this is off topic nevertheless I just wanted to ask. Cheers!|
cheap cialis sale online
Hi would you mind letting me know which web host you’re using? I’ve loaded your blog in 3 completely different browsers and I must say this blog loads a lot quicker then most. Can you recommend a good hosting provider at a fair price? Kudos, I appreciate it!|
Heya i’m for the first time here. I found this board and I find It really useful & it helped me out a lot. I hope to give something back and help others like you helped me.|
proscar without prescription
dipyridamole buy online
Great post, thanks for sharing, very helpful info
ivermectin 6 mg tablets
It’s nearly impossible to find knowledgeable people for this topic, but you sound like you know what you’re talking about! Thanks
I like the helpful information you provide in your articles. I’ll bookmark your weblog and check again here frequently. I’m quite certain I’ll learn plenty of new stuff right here! Best of luck for the next!
Great post, thanks for sharing, very useful info
cialis pills for sale
It is not my first time to go to see this website, i am browsing this web page dailly and get pleasant facts from here daily.|
I always spent my half an hour to read this web site’s content daily along with a mug of coffee.|
Great post, thanks for sharing, very useful information
how to buy cialis in canada
This paragraph will help the internet visitors for building up new webpage or even a blog from start to end.|
prednisone 20 tablet
cialis 5mg price in canada
ivermectin rx
Hi! Would you mind if I share your blog with my myspace group? There’s a lot of folks that I think would really enjoy your content. Please let me know. Cheers|
Definitely believe that which you stated. Your favorite justification appeared to be on the net the easiest thing to be aware of. I say to you, I definitely get annoyed while people consider worries that they just do not know about. You managed to hit the nail upon the top and also defined out the whole thing without having side effect , people could take a signal. Will probably be back to get more. Thanks|
Thanks for writing this great page, without question is very useful
Hello this is somewhat of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding experience so I wanted to get advice from someone with experience. Any help would be enormously appreciated!
Spot on with this write-up, I honestly feel this website needs a lot more attention. I’ll probably be back again to read through more, thanks for the advice!|
Great post. I was checking constantly this blog and I’m impressed! Extremely useful info specially the final part 🙂 I take care of such information a lot. I was looking for this certain information for a very long time. Thanks and good luck. |
strattera 60 mg price
generic tadalafil mexico
Nice post. I learn something more difficult on completely different blogs everyday. It will all the time be stimulating to learn content material from other writers and observe a bit of something from their store. I’d favor to make use of some with the content material on my blog whether you don’t mind. Natually I’ll provide you with a link on your internet blog. Thanks for sharing.
cialis medicine
viagra uk fast delivery
real viagra without a prescription
It is remarkable, rather valuable information
http://1587.allorgdownload.org/
cialis 5 mg tablet
cheap viagra paypal
generic cialis online mastercard
cost of ivermectin 3mg tablets
seroquel blood pressure
tadalafil 5mg best price
Thank you for any other informative site. Where else could I get that kind of info written in such an ideal means? I have a project that I am simply now working on, and I’ve been on the look out for such information.|
Hi there! This post couldn’t be written any better! Reading through this post reminds me of my old room mate! He always kept talking about this. I will forward this write-up to him. Fairly certain he will have a good read. Thank you for sharing!|
cialis 5 mg
https://stromectolis.com/# ivermectin 400 mg brands
benicar 25 mg
Thanks for sharing your thoughts on meta_keyword. Regards|
I just couldn’t leave your website prior to suggesting that I really enjoyed the standard info a person supply for your visitors? Is gonna be again continuously in order to check up on new posts|
cialis in canada
2.5 mg daily tadalafil
can i buy sildenafil over the counter in uk
ivermectin 50ml
cialis tablets 20mg australia
cialis 10mg canada
ivermectin eye drops
cheap generic viagra 100mg canada
where can i buy cialis over the counter in uk
lisinopril tabs 88mg
Szukania bieżących porównań wytworów kredytowych zakończą się triumfem, gdy tylko i wyłącznie jesteś ochoczy zajrzeć na wortal www. To strona poświęcona sferze finansowej, jak również połączonej wraz z dochodzeniem odszkodowań w szczecinie. Wskazówki, jak i również kosztowne dyrektywy pomagają w całej wybieraniu bardzo dobrego towaru finansowego dostępnego przy tradycyjnych bankach, a także firmach pozabankowych. Witryna gwarantuje najświeższe fakty, aktualne połączenia kredytów, lokat od liczne puli. Zapoczątkowanie nowego wytworu finansowego poprzez pula nie zaakceptować ujdzie również bez odzewu jako serwisie internetowym. Nasi czytelnicy pozostaną poinformowani o wszystkich zmianach na globie bankowości jak i również zasobów. Klienci, jacy mają obciążenia także wyszukają w tym miejscu dużo drogocennych wiadomości. W wortalu nie zabraknie tematów, jak pójść wraz z długów, kiedy pożyczka konsumpcyjny posiada rację bytu, jak i również dzięki tego kłaść nacisk, jeśli zaciąga się pożyczkę w parabankach. Należałoby zwiedzać systematycznie wortal web w takim przypadku jest możliwość dysponować gwarancję, iż okazuje się być się sukcesywnie wraz ze każdymi zmianami wprowadzanymi poprzez bazy i z pewnością coś znacznie więcej aniżeli tylko https://finanero.pl/ finanero recenzja.
buy generic viagra online in india
zoloft pills for sale
cialis|buy cialis|generic cialis|cialis pills|buy cialis online|cialis for sale
cialis|buy cialis|generic cialis|cialis pills|buy cialis online|cialis for sale
viagra for sale
buy viagra online
First off I would like to say great blog! I had a quick question in which I’d like
to ask if you do not mind. I was interested to find out how you center yourself and clear your mind before writing.
I have had trouble clearing my mind in getting my ideas out there.
I do enjoy writing however it just seems like the first 10 to 15
minutes are generally lost just trying to figure out how to begin. Any ideas or hints?
Cheers!
generic sildenafil prescription
Egzystencja pożyczek i debetów jest w stanie wyłącznie najpierw zdawać się niesłychanie wieloaspektowy. Na szczęście wprawą serwisem internetowym wszystko jest klarowne. Prosty a, także bardzo szybki dojazd służące do bieżących ofert zwyczajowych banków, jak również porady odnośnie zawierania różnorodnych transakcji mają możliwość przyczynić się każdemu użytkownikowi. Zapraszamy służące do monitorowania przedstawianych aktualności, które to są opracowane poprzez profesjonalistów na rynku finansów. Którykolwiek bądź jaki zastanawia się ponad zaciągnięciem kredytu mieszkaniowego ewentualnie powyżej założeniem lokaty pod nazwany okres, może zbadać cechę najciekawszych rzeczy kredytowych przedkładanych po bardzo świeżym sezonie. W wortalu znajdują się także dzisiejsze notowania wytworów kredytowych, które umozliwiają zorientowanie się, który zręcznością nich w tej chwili wydaje się być w największym stopniu zyskowny. Pozwala to na uniknięcie drogich lapsusów i znacznie się w w największym stopniu opłacalną inwestycję. Pozostające artykuły będą kierowane również gwoli użytkowników bardziej zorientowanych w kulturze zasobów, których pochłaniają wymyślne sprawy bankowe, a także wprawne rodzaje wkładania https://finanero.pl/pozyczki chwilówki bez sprawdzania.
where to buy generic cialis online safely
female viagra over the counter
Hello! Do you know if they make any plugins to protect against hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?|
Hi there to all, how is the whole thing, I think every one is getting more from this web page,
and your views are nice in support of new visitors.
Hi, this weekend is fastidious in favor of me, as this time i am reading this enormous informative piece of writing here at my home.|
Thank you for the sensible critique. Me and my neighbor were just preparing to do some research on this. We got a grab a book from our area library but I think I learned more from this post. I am very glad to see such great information being shared freely out there.
can i buy viagra online from canada
stromectol pill
erectafil 5mg
legit online pharmacy
cymbalta otc
cipro medication over the counter
20 mg tamoxifen
cost of phenergan
how much is lisinopril 20 mg
buy cipro without rx
Attractive section of content. I just stumbled upon your blog and in accession capital to assert that I get in fact enjoyed account your blog posts. Any way I will be subscribing to your augment and even I achievement you access consistently fast.|
Very shortly this web site will be famous among all blogging and site-building visitors, due to it’s good articles or reviews|
ventolin albuterol
Right away I am going away to do my breakfast, after having my breakfast coming again to read additional news.|
Hello! Someone in my Facebook group shared this site with us so I came to take a look. I’m definitely loving the information. I’m bookmarking and will be tweeting this to my followers! Outstanding blog and fantastic design and style.|
avodart tablet
order stromectol online
where can you buy diflucan over the counter
Great! That is literally the thing I am searching for!
can you buy finasteride over the counter
antabuse online india
avodart 4 mg
Thanks for building this great post without doubts is very good
In fact no matter if someone doesn’t know afterward its up to other visitors that they will help, so here it happens.|
I think that everything composed made a ton of sense. However, think about this, what if you added a little content? I am not suggesting your information is not good., but what if you added a post title that grabbed people’s attention? I mean BLOG_TITLE is a little boring. You ought to glance at Yahoo’s front page and note how they create news headlines to get viewers to open the links. You might try adding a video or a related picture or two to get readers interested about what you’ve written. In my opinion, it would bring your posts a little livelier.|
Thanks for publishing this great page without questions is very informative
sildenafil generic cost
It’s amazing to pay a visit this site and reading the views of all friends concerning this post, while I am also eager of getting experience.|
Thanks for sharing this great content without questions is very useful
Hi there, just became alert to your blog through Google, and found that it’s really informative. I am going to watch out for brussels. I’ll appreciate if you continue this in future. Lots of people will be benefited from your writing. Cheers!|
Hey there, You’ve performed an incredible job. I will definitely digg it and personally recommend to my friends. I’m sure they will be benefited from this site.|
If some one wishes to be updated with latest technologies then he must be pay a quick visit this web page and be up to date every day.|
I have learn a few good stuff here. Certainly value bookmarking for revisiting. I surprise how a lot effort you place to create this sort of magnificent informative website.
Thanks for writing this great post without questions is very informative
order lopressor
Thanks for building this great article without questions is very good
buy vpxl online
This website is impressive. Thanks!
Thanks for publishing this great article without doubts is very informative
What’s up it’s me, I am also visiting this site daily, this site is genuinely nice and the visitors are really sharing nice thoughts.|
I all the time emailed this web site post page to all my friends, for the reason that if like to read it then my links will too.|
robaxin to uk
I simply wanted to appreciate you yet again. I’m not certain the things that I would’ve accomplished without the actual points contributed by you on my question. Completely was a frustrating scenario in my opinion, but witnessing the very skilled fashion you solved it forced me to weep over fulfillment. Now i’m happier for your service as well as pray you find out what a great job you were undertaking educating people today thru a site. Probably you’ve never come across all of us.
My brother suggested I might like this website. He was totally right. This post actually made my day. You can not imagine simply how much time I had spent for this info! Thanks!|
Very nice article, exactly what I was looking for.|
levitra online nz
diclofenac 100 gel
Thanks for sharing this great post without doubts is very informative
where can i get viagra for women
cialis viagra online
where to buy female viagra australia
where to buy female viagra pill
viagra 50 mg tablet online
viagra 100mg tabs
Thanks for sharing this great post without questions is very good
cialis online uk pharmacy
tadalafil 20mg
It’s impressive that you are getting ideas from this article as well as from our argument made here.|
Howdy! This is my first visit to your blog! We are a collection of volunteers and starting a new initiative in a community in the same niche. Your blog provided us beneficial information to work on. You have done a wonderful job!|
cialis for daily use 5 mg
Thanks to my father who shared with me regarding this web site, this blog is genuinely remarkable.|
Hey very interesting blog!|
Thanks for sharing this great content without doubts is very useful
Has anyone shopped at Central Vapors Ecigarette Shop located in 72 North Pioneer?
I was looking info about this for quite a long time.
viagra over the counter australia
It is actually a nice and useful piece of info. I’m happy that you simply shared this useful info with us. Please stay us informed like this. Thanks for sharing.
Excellent way of describing, and pleasant article to take information about my
presentation focus, which i am going to deliver in university.
Wow, awesome blog layout! How long have you been blogging for? you make blogging look easy. The overall look of your web site is magnificent, let alone the content!|
Wow that was unusual. I just wrote an very long comment but after I clicked submit
my comment didn’t show up. Grrrr… well I’m not writing all that over again. Anyways,
just wanted to say fantastic blog!
Super-Duper blog! I am loving it!! Will come back again. I am bookmarking your feeds also
tadalafil daily
Hi, I do believe this is an excellent blog. I stumbledupon it ;
) I’m going to come back yet again since
I book marked it. Money and freedom is the best way to change, may
you be rich and continue to help other people.
cialis online price comparison
hello!,I like your writing so much! share we communicate more about your post on AOL? I require a specialist on this area to solve my problem. May be that’s you! Looking forward to see you.
Greetings! Very useful advice within this article!
It is the little changes which will make the greatest changes.
Thanks for sharing!
Wonderful article! We are linking to this particularly great content on our site. Keep up the great writing.|
Greetings! Very useful advice within this article! It is the little changes that produce the greatest changes. Thanks a lot for sharing!|
I believe what you typed made a ton of sense. But, think on this, suppose you typed a catchier title? I mean, I don’t wish to tell you how to run your blog, however what if you added a post title that grabbed folk’s attention? I mean BLOG_TITLE is kinda vanilla. You ought to glance at Yahoo’s home page and see how they write article headlines to get viewers interested. You might add a video or a pic or two to get readers interested about what you’ve written. In my opinion, it might bring your blog a little livelier.|
My husband and i ended up being really joyful when Raymond managed to do his analysis through your precious recommendations he made in your site. It is now and again perplexing to just happen to be giving out tactics that many other folks could have been selling. And now we keep in mind we need you to be grateful to for that. All of the illustrations you made, the simple web site navigation, the relationships you can aid to instill – it’s got all awesome, and it’s really aiding our son in addition to us reason why that theme is entertaining, which is certainly tremendously indispensable. Thank you for the whole thing!twitch tv activate code
stromectol uk
Thank you for your own effort on this website. Gloria take interest in going through investigations and it’s really easy to see why. Many of us hear all about the lively method you convey great solutions via the web blog and encourage participation from some others about this article while our child is undoubtedly starting to learn a great deal. Enjoy the remaining portion of the year. You’re the one conducting a very good job.
Simply wanna input on few general things, The website pattern is perfect, the content material is rattling wonderful : D.
canadian generic viagra
What’s Taking place i’m new to this, I stumbled upon this I have discovered It positively useful and it has aided me out loads. I’m hoping to contribute & assist other users like its aided me. Good job.|
My partner and I stumbled over here different web address and thought I might as well
check things out. I like what I see so now i am following you.
Look forward to going over your web page repeatedly.
sildenafil online in india
diflucan over the counter canada
allopurinol 300 price
What’s up to every one, the contents existing at this website are genuinely
remarkable for people experience, well, keep up the
nice work fellows.
Do you mind if I quote a few of your articles as long as I provide credit and sources back to your blog? My blog is in the very same area of interest as yours and my visitors would definitely benefit from some of the information you present here. Please let me know if this alright with you. Thank you!|
Hi, I do think this is a great web site. I stumbledupon it 😉 I will return once again since i have saved as a favorite it. Money and freedom is the greatest way to change, may you be rich and continue to guide other people.|
I constantly spent my half an hour to read this web site’s posts all the time along with a cup of coffee.
Hi, I believe your blog might be having internet browser compatibility problems. When I take a look at your website in Safari, it looks fine but when opening in Internet Explorer, it’s got some overlapping issues. I just wanted to give you a quick heads up! Aside from that, great website!|
It’s an amazing article in support of all the web users; they will obtain benefit from it I am sure.|
Hey just wanted to give you a quick heads up. The words in your article seem to be running off the screen in Internet explorer. I’m not sure if this is a format issue or something to do with browser compatibility but I thought I’d post to let you know. The layout look great though! Hope you get the problem solved soon. Many thanks|
Thanks for writing this great article without doubts is very informative
can you buy phenergan over the counter in nz
viagra us
Hey I am so excited I found your website, I really found you by mistake,
while I was researching on Askjeeve for something else, Regardless I am here now and
would just like to say cheers for a fantastic post and a all round exciting blog (I also love the theme/design), I don’t have
time to read through it all at the minute but I have saved
it and also added in your RSS feeds, so when I have time I will be
back to read a great deal more, Please do keep up the superb work.
I feel I need to mention about a quite cool recording of {{Getting|Going} Through {The
middle|Middle} of {East Borneo|East Borneo Indonesia|Indonesia|Indonesian} Forest for {Very Traditional|Traditional} {Cooking|Roasting chicken} {on|in} the Ricefield}
https://www.youtube.com/watch?v=gEUqYxb-I7w
I’d honestly be thankful if you would go check the video
order viagra soft tabs
I do agree with all of the ideas you’ve presented in your post. They are very convincing and will certainly work. Still, the posts are too short for beginners. Could you please extend them a little from next time? Thanks for the post.
Thank you, I’ve recently been searching for information about this subject for a long time and yours is the best I’ve found out till now.
But, what in regards to the conclusion? Are you certain concerning the supply?
ivermectin 2mg
cost cialis canada
buy tadalafil 20mg
stromectol tablets for humans
viagra online buy
vermox price
cialis pill
Incredible points. Sound arguments. Keep up the good spirit.
best price tadalafil
Howdy! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in trading links or maybe guest authoring a blog post or vice-versa?
My site goes over a lot of the same topics
as yours and I believe we could greatly benefit from each other.
If you happen to be interested feel free to shoot me an email.
I look forward to hearing from you! Superb blog by
the way!
purchase lasix online
What’s up everyone, it’s my first go to see at this website, and post is genuinely fruitful in support of me, keep up
posting these posts.
how much is a prednisone prescription
great post, very informative. I wonder why the opposite specialists of this sector do not notice this. You must continue your writing. I am sure, you’ve a great readers’ base already!
viagra nz over the counter
Thanks for every other wonderful article. Where else may just anyone get
that type of info in such an ideal approach of writing? I have a
presentation subsequent week, and I am on the look for such
information.
Great site. Plenty of useful info here. I am sending it to a few friends ans also sharing in delicious. And naturally, thanks for your effort!
Useful information. Fortunate me I found your web site by accident, and I’m stunned why this coincidence did not happened in advance! I bookmarked it.
I’ve been surfing online more than 4 hours today, yet I
never found any interesting article like yours. It’s pretty worth enough for me.
Personally, if all webmasters and bloggers made good content as you did, the web will be much more
useful than ever before.
Simply want to say your article is as amazing. The clearness in your post is just spectacular and i could assume you are an expert on this subject. Fine with your permission allow me to grab your feed to keep updated with forthcoming post. Thanks a million and please continue the rewarding work.
I think other site proprietors should take this website as an model, very clean and wonderful user friendly style and design, let alone the content. You are an expert in this topic!
This is very interesting, You are an excessively professional blogger. I have joined your rss feed and look ahead to in the hunt for more of your excellent post. Also, I’ve shared your website in my social networks!
excellent points altogether, you simply gained a emblem new reader. What may you suggest in regards to your put up that you made a few days in the past? Any positive?
почивките в турция
Hello my friend! I want to say that this article is awesome, nice written and come with
almost all important infos. I’d like to peer more posts like this .
I’ve been exploring for a bit for any high quality articles or weblog posts on this
sort of house . Exploring in Yahoo I ultimately stumbled upon this web site.
Studying this info So i’m glad to express that I have an incredibly excellent uncanny feeling I came
upon exactly what I needed. I so much no doubt will
make certain to do not fail to remember this website and provides it a glance regularly.
Hi there are using WordPress for your blog platform? I’m new to the blog world but I’m trying to get started
and create my own. Do you need any html coding expertise to make your own blog?
Any help would be really appreciated!
Useful info. Fortunate me I found your web site accidentally, and I’m stunned why this accident did not happened earlier!
I bookmarked it.
Hey there! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly?
My web site looks weird when browsing from my apple iphone.
I’m trying to find a theme or plugin that might be able to resolve this issue.
If you have any suggestions, please share. Thank you!
Hey are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started and set up my own. Do
you require any html coding knowledge to make your own blog?
Any help would be greatly appreciated!
Wow cuz this is great job! Congrats and keep
it up.
https://www.ciekawebiznesywpolsce.eu
I appreciate the content on your website. Cheers!
https://www.inspiracjebiznesowe.info
در این مقاله میخواهیم به معرفی بهترین کلاس زبان آلمانی در مشهد بپردازیم.
تا انتها همراه ما باشید.
زبان آلمانی
امروزه افراد زیادی به دنبال یادگیری زبان المانی هستند و با هدف های مختلفی
مثل کار، سفر یا تحصیل به آلمان و … در کلاس آموزش زبان آلمانی ثبت نام می
کنند. زبان آلمانی پر گویش
ترین زبان اتحادیه اروپا می باشد و توسط
95 میلیون نفر مورد استفاده قرار می گیرد.
این زبان در کشور هایی مثل آلمان، اتریش، سوئیس، لیختناشتاین، لوگزامبورگ، شرق
بلژیک، آلتو آدیجه، آلزاس، لورن و جنوب
دانمارک و … به رسمیت شناخته می شود.
زبان آلمانی بعد از انگلیسی دومین
زبان استفاده شده در اسناد رسمی، و بعد از
انگلیسی و روسی سومین زبان استفاده شده
در تارنماهای اینترنتی می باشد.
همچنین طبق تحقیقات انجام شده یک دهم کل
کتاب هایی که هر سال در کل
جهان نگارش می شوند به این زبان می باشند.
کشور آلمان بیش از 80 میلیون نفر جمعیت دارد که
93 درصد آن ها آلمانی و مابقی اتباع خارجی هستند.
زبان رسمی کشور آلمان زبان آلمانی است و 95
درصد مردم آلمان به همین زبان و
یا گویش هایی از این زبان صحبت می کنند.
زبان آلمانی شامل دو گویش اصلی
آلمانی بالا و آلمانی پایین و همانند انگلیسی دارای تعداد زیادی از گویشهای فرعی است.
بر اساس این زبان، زبان معیاری با نام آلمانی
معیار وجود دارد که بیشتر به آلمانی بالا شبیه است، به خارجیها آموزش داده میشود و نوعی زبان میانجی است.
بخشی از کلمات زبان آلمانی ریشه
در زبانهای لاتین و یونانی دارد و قسمت کوچکی نیز از فرانسوی
و انگلیسی به عاریه گرفته شدهاست.
تنوع در زبان آلمانی:
زبان آلمانی با گویش ها و لهجه های خاصی در نقاط مختلف اروپا مورد استفاده قرار می گیرد.
این گویش ها عبارتند از:
آلمانی والا یا عالی:
زبان آلمانی والا در قرن 16 میلادی به
وجود آمد و به عنوان زبان ادبی استاندارد
شناخته شد. مارتین لوتر
در سال 1534 ترجمه کتاب مقدس را به
پایان رساند که آغازی در شکل گیری
این زبان می باشد. زبانی که او در کتابش استفاده کرد
بر پایه زبان آلمانی بود که آن زمان صحبت می
شد.
آلمانی – سوئیسی:
این نوع از زبان آلمانی توسط 4 میلیون نفر
در سوئیس به کار برده می شود و گاهی در برخی
از رمان ها، روزنامه ها، نامه ها و دفتر
یادداشت ها مشاهده می شود.
آلمانی – پنسیلوانیا:
این نوع از زبان آلمانی توسط 250 هزار نفر در
پنسیلوانیا، اوهایو و ایندیانا در ایالات متحده و اونتاریو در کانادا مورد استفاده قرار می گیرد.
Hey there! I simply would like to give you a
huge thumbs up for the great information you have got right
here on this post. I will be coming back to your site for more soon.
Having read this I believed it was very enlightening.
I appreciate you taking the time and effort to put this content together.
I once again find myself personally spending
a lot of time both reading and leaving comments. But so what, it was still worthwhile!
It’s awesome designed for me to have a website, which is good in support of my knowledge.
thanks admin
Я теперь не положительно место вы получаете
свою информацию, однако хорошая тема.
Я должен потратить некоторое время изучение намного
больше или выяснение большего.
Спасибо за великолепный информация
я в поисках это информация для моей
миссии.
Привет, мой любимый человек!
Я хочу сказать, что эта сообщение потрясающе, отлично написано и include почти
вся важная информация . Я бы посмотреть больше сообщений, подобных этой.
Оквер – окна
What’s up mates, how is all, and what you desire to say concerning this post, in my
view its really remarkable in support of me.
Thanks for your marvelous posting! I really enjoyed reading it, you can be a great
author. I will be sure to bookmark your blog and may
come back very soon. I want to encourage you to ultimately continue your great writing, have a nice day!
andar judi bola online Login SBOBET terpercaya di pilih
dengan ciri-ciri memberikan banyak bantuan memprediksi taruhan dengan beragam informasi yang diberikan. Setiap agen memiliki kelebihan dan keunggulan masing-masing, bahkan juga banyak
yang memiliki kekurangan. Sehingga anda tidak boleh sembarangan dalam memilihnya, namun harus
tepat dalam memilih agen judi bola sbobet yang lebih banyak memberikan keuntungan kepada para
pemain. Tentu hal ini dilakukan demi mempermudah dan memperlancar setiap
taruhan yang anda mainkan nanti didalamnya. Dengan begitu harus bisa melakukan penilaian terhadap agen bandar judi bola online terpercaya dapat dipilih dengan tepat.
Slot88 telah lama menjadi situs agen judi SBOBET bandar judi
bola terpercaya sejak bertahun – tahun sampai hari ini.
Bisa di lihat dari pendaftaran member baru setiap
harinya di sini, lebih dari ratusan pemain telah
bergabung dengan kami. Ini bisa menjadi acuan kalian mencoba permainan judi sbobet di situs
terpercaya Slot88. Fasilitas dan juga bonus – bonus menarik akan membuat kalian selalu senang bermain di tempat ini.
Terlebih permainan judi bola di sini sangatlah fair dan tanpa campur tangan Bot.
Silahkan mendaftar melalui link daftar yang telah kami sediakan di website kami atau
dengan live chat yang siap melayani 24 jam nonstop.
Ciri-ciri agen bandar judi bola online terpercaya dapat dipilih
Pastikan sebelum memilih salah satu bandar yang menyediakan permainan bola online,
maka tentu saja terlebih dahulu mengenai ciri-ciri yang ada pada sebuah agen judi bola terpercaya.
Karena ini menjadi patokan ataupun juga referensi dalam memilih maupun membedakan masing-masing agar anda
dapat memilihnya sesuai ciri-ciri tersebut yang menjamin lebih mudah menemukan tempat terbaik memasang taruhan perjudian bola secara onlinedidalamnya.
Berikut ciri-ciri agen bandar judi bola online terpercaya dapat dipilih:
Memberikan banyak bantuan prediksi untuk pemain
Ciri-ciri yang ada pada agen terpercaya yaitu akan memberikan banyak bantuan kepada para
pemain agar selalu mudah melakukan prediksi taruhan judi bola.
Sehingga mempermudah kemenangan bisa didapatkan dengan bantuan tersebut.
Dimana biasanya pihak agen akan menyediakan banyak informasi seputar pertandingan sepakbola
yang disediakan supaya membantu para pemainnya lebih mudah memprediksi hasil
pertandingan dari mempertimbangkan informasi-informasi tersebut.
Oleh karena itu jika ingin lancar dalam memainkan taruhan judi bola sbobet online, maka jangan sembarangan memilih agen. Tetapi harus memilih agen yang memberikan banyak bantuan di
dalam memprediksi pertandingan demi kelancaran dan ketepatan memprediksi hasil akhir pertandingan dengan tepat bisa dimenangkan.
Tidak akan mengecoh taruhan dalam pemain
Pastikan anda juga bisa menilai apakah sebuah agen judi bola sbobet layak dipercaya menjadi tempat terbaik atau tidak dengan melihat
bantuan yang diberikan. Karena biasanya bandar yang
buruk akan mengajak para pemain supaya salah dalam memprediksi taruhan. Berbeda dengan agen bandar yang layak dipercaya
tidak akan mengecoh atau menjebak para pemain justru akan membantu setiap pemain lebih mudah dalam
memprediksi hasil akhir taruhan. Hal ini tentu menjadi salah satu poin penting yang
perlu dipertimbangkan dari masing-masing agen agar tidak keliru dalam memilihnya.
Memberikan banyak informasi seputar pertandingan
Dan selanjutnya anda juga dapat menilai apakah sebuah agen dapat dipercaya atau tidak
dari banyaknya informasi seputar jadwal
pertandingan sepak bola. Yang nanti akan diberikan kepada para pemain semakin lengkap informasi tersebut tentu semakin lebih layak dipilih.
Karena akan selalu mempermudah anda dalam memprediksi tahan dan mengatur jadwal pertandingan. Maka
dengan begitu akan dijamin lancar taruhan judi daftar sbobet yang dimainkan didalamnya.
Pastikan jangan sembarangan memilih agen jika ingin aman dalam
memainkan perjudian, tetapi harus bisa mengenali dengan tepat sebuah agen bandar judi bola online terpercaya dapat dipilih dijadikan tempat bermain yang menjanjikan keamanan.
Bonus Judi SBOBET Online Terbesar
Adapun bermain judi bola dalam Slot88 adalah keuntungan besar, karena
kalian bisa menikmati beragam bonus menarik yang bisa
di dapatkan. Hanya dengan mendaftar dan melakukan deposit pertama, anda akan langsung
mendapatkan 1 akun hoki yang bisa main di semua game.
Bonus judi SBOBET online di Slot88 di pastikan sebagai bonus
judi SBOBET WAP online terbesar yang pernah kalian temui.
Kami tidak pernah mengurangi bonus – bonus kami,
namun kami malah memberikan bonus – bonus yang lebih besar.
Karena kami ingin memberikan rasa apresiasi kami sebagai
situs judi SBOBET yang telah anda pilih. Ucapan terimakasih yang besar layak kalian dapatkan, Nikmati beragam bonus – bonus menarik
kami seperti;
What a data of un-ambiguity and preserveness of precious
familiarity on the topic of unpredicted emotions.
For latest information you have to visit internet and on the web I found this web site as a
most excellent web page for latest updates.
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point.
You definitely know what youre talking about,
why throw away your intelligence on just posting
videos to your site when you could be giving us something enlightening
to read?
Nice weblog here! Also your site so much up very fast!
What web host are you the usage of? Can I am getting your affiliate link in your host?
I wish my site loaded up as fast as yours lol
There are dozens of things you need to know about babies.
Are you ready to have a baby? It is good
to ask this question yourself. Taking care of a baby is definitely not easy.
If you are ready for baby care, do it 🙂 You can visit
our page for baby items and get information.
I always spent my half an hour to read this webpage’s articles every day along with a cup
of coffee.
Hey! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Cheers
Great internet website! It looks really expert! Keep up the great job!
https://www.zostatniejchwili.info
https://antalyamerhaba.com/group-tours/
رحلات ضمن جروب في انطاليا
رحلات ضمن جروب في انطاليا,رحلات جماعية في انطاليا,
رحلات يومية في انطاليا,رحلة يوم
في انطاليا,برامج جماعية في انطاليا,رحلات سياحية
ضمن جروب في انطاليا,افضل برامج جماعية
في انطاليا,قروبات جماعية في انطاليا,فعاليات انطاليا,رحلات بحرية في انطاليا,كياكم
انطاليا,رحلات التجديف في انطاليا,رحلات الباغي في انطاليا,
رحلة ارض الاساطير في انطاليا,رحلات الغوص في انطاليا
An intriguing discussion is worth comment. I
think that you ought to write more about this issue, it
might not be a taboo matter but usually people do not
talk about these subjects. To the next! Kind regards!!
I enjoy the data on your web site. Regards!
https://www.dziejesietuiteraz.pl
Good site you have got here.. It’s difficult to find high quality writing
like yours nowadays. I truly appreciate individuals like you!
Take care!! http://thaistock2u.com
Thankfulness to my father who stated to me concerning this
webpage, this webpage is really remarkable.
It’s actually a great and helpful piece of info.
I am satisfied that you simply shared this useful information with us.
Please stay us up to date like this. Thank you for sharing.
Howdy! I’m at work browsing your blog from my new iphone!
Just wanted to say I love reading through your blog and look forward to all your posts!
Carry on the great work!
WOW just what I was looking for. Came here by searching for More
information
Wonderful goods from you, man. I have understand your stuff previous to and you
are just too wonderful. I actually like what you’ve acquired here, really like what you are stating and the way in which you say it.
You make it entertaining and you still take care of
to keep it smart. I can’t wait to read much more from you.
This is really a great web site.
No matter if some one searches for his vital thing, therefore he/she wants to be available that in detail, so
that thing is maintained over here.
Greate post. Keep posting such kind of info on your blog. Im really impressed by your blog.
Hello there, You have performed an incredible job.
I will definitely digg it and in my view suggest to my friends.
I am sure they will be benefited from this web site.
Hi there, well put together online site you’ve gotten at this time there.
https://www.inicjatywygospodarcze.eu
Wow that was strange. I just wrote an extremely long comment but after
I clicked submit my comment didn’t appear.
Grrrr… well I’m not writing all that over again. Regardless, just wanted
to say wonderful blog!
Hurrah, that’s what I was looking for, what a information! existing here at this webpage, thanks admin of this site.
Thanks a ton for sharing this awesome webpage.
https://www.latonagrod.pl
Astonishingly user pleasant website. Astounding information available on few clicks.
https://www.sensacjednia.pl
Very revealing look forward to coming back.
https://www.skrzyniawiedzy.info
There is visibly a bunch to realize about this. I think you made certain good points in features also.
Thanks designed for sharing such a pleasant thought,
paragraph is good, thats why i have read it completely
Keep on working, great job!
What i don’t understood is in truth how you’re not actually much more well-preferred than you might be right
now. You are very intelligent. You already know therefore significantly
with regards to this matter, made me individually imagine it from numerous various angles.
Its like women and men don’t seem to be interested unless
it is one thing to do with Lady gaga! Your own stuffs
nice. At all times maintain it up!
It’s laborious to believe that many new mothers in Indiana are only
coated for 60 days after giving beginning. Too many Hoosier women are dying shortly after giving
beginning. I had pre-eclampsia, elevated blood pressure, during a number of of
my pregnancies, but throughout my second pregnancy I
also had submit-eclampsia, high blood pressure that
got here on after giving birth. Information from 2018 point out that 86% of maternal deaths
in Indiana got here submit-partum, including 37% after 6 weeks.
The Indiana Maternal Mortality Evaluate Committee decided that 87% of the pregnancy-associated deaths they reviewed were
preventable. The fact that almost all of these deaths
are preventable is encouraging, nevertheless,
forty seven states do a greater job of it than Indiana.
Happily, medical doctors obtained me stabilized and by no means detected any damage to my coronary heart, nonetheless,
I take blood strain medication to this present day. I used to be hospitalized
with blood pressure so excessive that doctors thought I’d
have a stroke. Girls in 33 of our ninety two counties don’t have a hospital with OB-GYN services.
$ 7700 for 8 minutes Binary options trading strategy https://go.binaryoption.ae/FmUKhe
Thanks extremely helpful. Will share site with my friends.
https://www.firmadlaopornych.info
Its like you read my mind! You seem to understand a lot approximately this, such as you wrote
the ebook in it or something. I feel that you simply could do with a few % to force the message home a little bit, but
other than that, that is fantastic blog. A fantastic read.
I will certainly be back. fake sen masine plants bulk buy
Hi there! This is my first visit to your blog! We are a team
of volunteers and starting a new project in a community in the
same niche. Your blog provided us useful information to work on. You have done a wonderful job!
Terrific work! This is the kind of info that are meant to be shared across the internet.
Disgrace on Google for no longer positioning this put up
higher! Come on over and discuss with my website . Thanks =)
Great looking web site. Think you did a lot of your own coding.
https://www.informacjedlakazdego.com
Blur faces in photos online
Fastidious respond in return of this query with genuine arguments and describing all on the topic of that.
Tuzla escort Hayatımda artık farklı bir deneyim olsun
Hep aynı sıradan seksi yaşıyorum. Hayatımda artık farklı bir deneyim olsun istiyorum diyen elit beyler.
Şule’niz sizin için Tuzla Escort Bayan ta.
Benimle o aradığın farklı deneyimi yaşamaya hazır mısın? Bu işin uzmanı Şule hatununuz
beyler.
Daha önce hiç yaşamadığınız bir cinsel sevişme istiyorsanız
hemen beni arayın. Bu işin en tecrübeli kızı benim beyler.
Benimle yaşayacağınız sevişmeyi daha
önce hiç yaşamadığınızı anlayınca boşa geçen yıllarınıza acıyacaksınız.
Hiçbir şey için geç değil beyler. Benimle yaşayacağınız
seksle seks hayatınızı sil baştan yaşayacaksınız.
Şule hatununuz sizi mutlu etmenin arayışını hiçbir zaman bırakmadı.
Ve kendini hep bu yönde ilerletmeye devam etti.
Bu yüzden bu sektörde oldukça iddialıyım beyler. Benimle
doyumsuz anları yaşamak ve o anları ölümsüzleştirmek Escort Tuzla yalnızca bir telefona bakıyor.
Beni hemen arayın ve inanılmaz anları
yaşama fırsatını anında yakalayın.
Herkes hayatında farklılıklar ister. Bu da bize farklı heyecan arayışı içerisinde olmamız için bir
fırsat sunar. Beni tatmadan seks yaptım
demeyin beyler. Hepsini unutturacak uzman sevişmemle
beni yaşadığına minnettar kalacağından hiç şüphen olmasın. Seksi benimle yaşamanın farkını anlayınca sen de yeni heyecanı yaşamanın tutkusunu doyasıya yaşayacaksın. Genç ve ateşli bedeniyle Şule senin için deli oluyor.
Sana inanılmaz anları yaşatacak Şule’ni hemen sarmala ve ateşli anları başlatmaya hemen başla
erkeğim. Yanan bedenlerimizde doyasıya erimenin tadını
çıkaralım.
Thhis site was… how do you say it? Relevant!! Finally I’ve found something thatt helped me.
Thanks!
Astonishingly user pleasant site. Enormous info readily available on few
gos to.
https://www.greenworld24.pl
Hello mates, its enormous piece of writing on the topic of tutoringand
entirely defined, keep it up all the time.
I want to to thank you for this great read!! I certainly enjoyed every little bit of it.
I have got you book marked to check out new things you post…
Hi would you mind letting me know which webhost
you’re using? I’ve loaded your blog in 3 completely different web browsers and I must say this blog loads a lot faster then most.
Can you suggest a good web hosting provider at a reasonable price?
Thanks, I appreciate it!
Thank you for any other fantastic article. Where else
may anybody get that type of info in such a perfect
way of writing? I’ve a presentation next week, and I am on the look for such information.
I loved as much as you’ll receive carried out
right here. The sketch is tasteful, your authored
subject matter stylish. nonetheless, you command get bought an impatience
over that you wish be delivering the following.
unwell unquestionably come further formerly again since
exactly the same nearly very often inside case you shield this increase.
I really like it when folks come together and share views.
Great blog, continue the good work!
I am actually grateful to the owner of this web site who has shared this enormous piece of writing at at this time.
You really make it seem so easy with your presentation but
I find this matter to be really something that I think I would never understand.
It seems too complex and extremely broad for me. I’m looking forward for your next post, I’ll try
to get the hang of it!
nuospaudu salinimas vilniuje
I visited many websites except the audio quality for audio songs present at this web site is
truly wonderful.
I just could not leave your website before suggesting that I really loved the standard info an individual supply to your visitors?
Is gonna be again ceaselessly to check out new posts
Useful information. Fortunate me I found your web site by accident, and I am shocked why this
accident did not came about earlier! I bookmarked it.
منو جا نذار بغل بگیر تو بمون برام
تو بگو بمیر منو اشک خودم روی شونه ی تو خالی میشه دلم به بهونه ی
تو خوبه با من همیشه میونه تو عشق دیوونه ی تو …
همه کس تویی تو آخه هرچی تو قلبمه
میدونی تو بلدی تو منو همه میرن و باز داری
میمونی تو چه قشنگ داری رنگ سفیدو رو قلب من
میزنی تو همه کس تویی تو آخه هرچی تو قلبمه میدونی تو بلدی تو منو
همه میرن و باز داری میمونی تو چه قشنگ داری رنگ سفیدو رو قلب من میزنی تو تو یه وقت قعر نکنی با
من میشه باشی واسم میشه صدات بزنم
تو نگاه کنی من به یذرشم قانعم منو اشک
خودم روی شونه ی تو خالی میشه دلم
به بهونه ی تو خوبه با من همیشه میونه تو عشق
دیوونه ی تو … بلدی تو منو همه میرن و
باز داری میمونی تو چه قشنگ داری رنگ سفیدو رو قلب من
میزنی تو همه کس تویی تو آخه هرچی تو قلبمه میدونی تو بلدی تو منو همه میرن
و باز داری میمونی تو چه قشنگ داری رنگ
سفیدو رو قلب من میزنی تو
I could not refrain from commenting. Exceptionally well written!
Appreciation to my father who told me on the topic of this webpage, this webpage is really amazing.
I am curious to find out what blog platform you happen to be utilizing?
I’m experiencing some small security issues with my latest site and I’d like to find something
more safe. Do you have any suggestions?
At the time of this text, based on the Johns Hopkins COVID 19 useful resource heart, there are over 1 million circumstances reported,
and a staggering 52,863 deaths. That is the largest study to
date within the literature addressing analysis
of COVID 19. There have been important clinical
symptoms related to COVID 19. Fever, cough and fatigue, in that respective order had been the most typical.
There was not any time delay related to the take a look at, with most outcomes accessible almost instantly upon completion of the exam.
However, there has yet to be a consensus paper outlining and evaluating the best take a look at, one that offers each a high sensitivity and specificity.
32. Li, Y.Y., Wang, W.N., Lei, Y., Zhang, B., Yang,
J., Hu, J.W., Ren, Y.L. 8. Xu, Y.H., Dong, J.H., An, W.M., Lv, X.Y., Yin, X.P.,
Zhang, J.Z., Dong, L., Ma, X., Zhang, H.J. 19.
Zhao, W., Zhong, Z., Xie, X., Yu, Q. and Liu, J.
(2020) Relation between Chest CT Findings and Clinical Situations of Coronavirus
Disease (COVID-19) Pneumonia: A Multicenter Research.
купить декорации также все необходимое для кухни в киеве,
днепре – promebli
Hi there colleagues, its wonderful article on the topic
of educationand fully explained, keep it up all the time.
Pretty section of content. I simply stumbled upon your weblog and in accession capital to claim that I acquire
actually enjoyed account your blog posts.
Any way I will be subscribing for your feeds or even I fulfillment you get right of entry to consistently quickly.
I have read so many articles or reviews about the blogger lovers except this article is truly a good paragraph, keep it up.
Baby life is an area where we examine what babies do and
how they behave in daily life. Babies watch and imitate you from the
first moment they start life. How to raise a baby?
How to care? What are the correct moves? Let’s examine it together.
An outstanding share! I’ve just forwarded this onto a co-worker who was conducting a
little homework on this. And he in fact bought
me breakfast because I discovered it for him… lol. So let me reword this….
Thanks for the meal!! But yeah, thanx for spending some time to talk about
this issue here on your web page.
Hello, There’s no doubt that your website might be having web browser compatibility problems.
When I look at your blog in Safari, it looks fine however when opening in Internet Explorer, it has some overlapping issues.
I just wanted to give you a quick heads
up! Other than that, wonderful website!
Fantastic blog! Do you have any recommendations for aspiring writers?
I’m hoping to start my own website soon but I’m a little lost on everything.
Would you advise starting with a free platform like WordPress or go for a paid option?
There are so many choices out there that I’m completely overwhelmed ..
Any recommendations? Cheers!
It will exploit the nature and make the fight 10x
easier. Skeletron is considered one of the hardest bosses
you will fight in Skilled Mode. Be wary of his
spinning assault, as it positive factors a speed boost in skilled mode.
Meals. In case you would not have the Effectively
Fed buff, your regeneration will likely be stunted
in Professional mode. Mobility is more vital than usual, as the Eater of Worlds strikes faster and is longer than its
Normal Mode model. In general, like normal mode, ensure you kill one earlier
than getting the other in second kind. It is essential that you dodge his
phantasmal deathray, as it can kill you in seconds (the Rod of Discord is
extremely really useful for this, although
grinding for it can be torturous). NPCs reduces spawn rates
and permits for Pylon utilization which is able to reduce harmful journey time.
https://beydoun-lb.com/curtains-lebanon-reputation/
curtains lebanon
Thanks on your marvelous posting! I actually enjoyed reading it, you happen to be a great author.I will remember to bookmark your blog
and will often come back someday. I want to
encourage you to ultimately continue your great job,
have a nice morning!
This article presents clear idea designed for the
new people of blogging, that really how to do blogging.
I’m now not sure where you are getting your information, however great topic.
I needs to spend some time studying more or understanding more.
Thank you for fantastic information I was searching for this info
for my mission.
This design is spectacular! You certaiinly know how to
keep a reader amused. Between your wit and your videos, I was amost moved tto start
my own blog (well, almost…HaHa!) Excellent job. I
really enjoyed what you had to say, and more than that, how you presented it.
Too cool!
Feel free to visit mmy blog post: بهترین مشاور کنکور
Simply want tto say your article is as astounding. The clearness
in you post is simply great and i ccan assume you’re an expert on this subject.
Fiine with your permision let me to grab your feed
to keep up to date with forthcoming post. Thanks a million and pleasxe keep upp
the rewarding work.
Also visit my webpage بهترین مشاور کنکور
Hey there! I’ve been following your blog for some time now and finally got the bravery to go
ahead and give you a shout out from Austin Texas! Just wanted to tell you keep up the great job!
Good day, nice web site you’ve got presently.
https://www.codziennaporcjainformacji.info
I like checking your internet site. Thanks for your time!
https://www.rozmowyosukcesach.pl
Regards for sharing your great web-site.
https://www.1biz.pl
Particularly insightful look frontward to visiting again.
https://www.rozmowywkuluarach.pl
Fantastic website. A lot of helpful information here.
I’m sending it to several buddies ans also sharing in delicious.
And of course, thanks on your sweat!
Hello everyone, it’s my first pay a quick visit at this web page, and paragraph
is really fruitful in favor of me, keep up posting such articles.
I’m really enjoying the theme/design of your site.
Do you ever run into any internet browser compatibility problems?
A few of my blog readers have complained about my blog not operating correctly in Explorer but looks
great in Firefox. Do you have any tips to help fix this issue?
Sustain the great work and bringing in the group!
https://www.wartowiedziec.info
Especially instructive looking forth to coming back again.
https://www.amarcinpowiedzialze.com
I have read some just right stuff here. Certainly
price bookmarking for revisiting. I surprise how so much effort
you place to make the sort of fantastic informative
website.
Kartal Escort Otele Gelen Kadınların Resimleri
Ben otel odasında buluşmayı tercih eden bayanım ve fikirlerimin belirlendiğini söylemeliyim.
Farklı ortamlara girip çıkmayı kabul edebilirim ama seni tanımam ve önceden en az bir kez tanışmamız gerekiyor.
Sonuç olarak, Marmara bölgesi dünyanın en büyük metropollerinden birine ev sahipliği yapıyor ve
burada yaklaşık 20 milyon insan yaşıyor, bu nedenle talepler uç noktalara ulaşabiliyor.
seks odaklı röportajlar yapıyor, güvendiğim flört sitesine ilan verdim ve Kartal escort bayan ile seçtiğiniz otelde görüşmeniz sırasında
bulacağım tüm çözümler profesyonel.
Zirveye çıkmanın yöntemini çok iyi biliyorum, tercihlerinize göre süreci yönlendiriyorum ve sizi her şekilde tatmin edeceğimi söylemeliyim.
Seks odaklı bir süreçle aldığınız hazzı arttırmaya çalışacağım.
Güzelliğim büyüleyici özelliklerimden biridir ve beni gören erkekler gözlerini
kalçalarımdan alamazlar.
Huzurlu ve keyifli bir ortamda çılgınlar gibi eğlenebilmeniz için mümkün olan tüm yöntemleri
deneyeceğim ve baştan çıkarıcı duygular uyandırıyorum.
Tanıştığımız ilk birkaç andan sonra, geçen her saniye bana olan ilginin arttığını
biliyorum.
Seveceğiniz ve son derece keyif alacağınız bir ortam yaratmaya hazırım, kararlarınızda size yardımcı
olacağım ve istediğiniz her şeyi sunarak hayatınıza renk katmak niyetindeyim.
It’s hard to find well-informed people on this topic,
but you sound like you know what you’re talking about!
Thanks
Link exchange is nothing else however it is only placing the other person’s website link on your page at proper place and other person will also do similar in favor of you.
Awesoms post, I shared this in my Tumblr.
I have read so many articles or reviews concerning the blogger lovers
but this piece of writing is genuinely a nice article, keep it up.
Have you ever thought about creating an ebook or guest authoring on other blogs?
I have a blog centered on the same topics you discuss and would love to have you share some stories/information. I know my audience would value
your work. If you are even remotely interested, feel free to
send me an e-mail.
Thanks for your marvelous posting! I certainly enjoyed reading it, you may be a great author.
I will always bookmark your blog and definitely will
come back sometime soon. I want to encourage that you continue
your great job, have a nice evening!
What’s Taking place i am new to this, I stumbled upon this I
have discovered It positively useful and it has aided me
out loads. I’m hoping to give a contribution & assist different customers like its helped
me. Great job.
Great info. Lucky me I recently found your website by accident (stumbleupon).
I have bookmarked it for later!
I’m truly enjoying the design and layout of your website.
It’s a very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a developer to create your theme?
Outstanding work!
Elit Ümraniye Escort Bayan Leyla Kalite Düşkünü
Genel olarak erkekleri çok iyi tanıyan ve bu sektörde uzun süredir hizmet
veren Ümraniye Escort Bayan olarak buraya ilanımı bırakmak istiyorum.
Her koşulda sizi el üstünde tutan ve beklentilerinizi önemseyen bir hatunum.
Bu yüzden beni tercih etmenizi sabırsızlıkla beklediğimi özellikle bilmenizi istiyorum.
Her konuda bilgili ve kültürlü hareket etmemi oldukça beğenen erkekler tarafından sıklıkla tercih edilen bir hatunum.
Bu yüzden ilişkilerde samimi olan bayan partner arıyorsanız doğru ilanı okuduğunuzu söylemek istiyorum.
Erkeklerin her bakımdan etkileneceği ve sizin ne düşündüğünüze kadar
anlayabilecek yeterlilikte bir Escort Ümraniye bayanıyım.
Dolayısıyla kendinizi bana bırakıp sizde güzel bir gece yaşamak istiyorsanız benimle unutulmaz bir gece yaşamaya hazır olun.
7 den 70 e ayrımcılık yapmadan her erkeğe hizmet verdiğimi
söylemek istiyorum. Ayrıca erkeklerin bana gelirken temiz olması
dışında hiçbir şartım ve beklentim yok.
Sizde ayağınıza gelen fırsatı kaçırmadan benimle beraber olmak için hemen randevu almayı ihmal etmeyerek arayın canlarım.
Diğer bayanlardan farklı olarak ateşli ve sürekli seks yapmadan duramayan bir Ümraniye Bayan Escort olarak buraya ilanımı bırakmak istiyorum.
İşime çok düşkünüm ve bu yüzden yaklaşık
7 yıldır bu sektördeyim. Ne istediğinizi bilecek kadar siz
değerli beyler hakkında bilgi sahibiyim.
My brother recommended I may like this web site. He was entirely right. This put up truly made my day. You can not consider simply how much time I had spent for this info! Thanks!
Boynuzlu kadın, ben güzel bir hatunum. Çekici Çekmeköy escort bayanınız olarak size en iyi tadı
vereceğimi bilmenizi isterim.
Çılgın bir aşkla yaşamak zorundasın. Bu yüzden hemen aramanız gerekiyor.
Bizi arayın ki öfkeyle devam eden bir etki halinde
olalım.
Bir sevgili gibi tadı, her saniye güzel kaldığımız samimiyeti de ortaya koyuyor.
Bu yüzden aramanız yeterli sevgililer.
Aslında seni sevmek için güzel olmaktan asla
bıkmam. Zevkle buluşalım. Entegrasyon moduna geçelim.
Seviyormuş gibi gösterelim ondan sonra da ihtiyacımız
olan etkileşimi sunuyor. Seni sevmek ve kendini daha özel hissettirmek için beni her saniye araman gerekiyor.
Ondan sonra bedenimizde ayrı bir sevgi sınırını bir arada tutuyoruz.
Bence en uç nokta, iyi olanı tatmasına izin verelim ki bize en iyisini iletebilsin…
Good info. Lucky me I discovered your blog by accident (stumbleupon).
I have book marked it for later!
Hi, i think that i saw you visited my site so i came to “return the favor”.I’m trying to find things to enhance my web site!I suppose its ok to use a few
of your ideas!!
We will teach you how to earn $ 7000 per hour.
Why? We will profit from your profit.https://go.binaryoption.ae/FmUKhe
Howdy superb blog! Does running a blog similar to this take a great deal
of work? I have very little understanding of computer programming but I had
been hoping to start my own blog soon. Anyhow, if you have any ideas or
techniques for new blog owners please share. I know this
is off subject nevertheless I simply wanted to ask. Cheers!
Terrific Site, Maintain the wonderful job.
With thanks!
https://www.bizneswduzejskali.com
We will teach you how to earn $ 7000 per hour. Why? We will profit from your
profit.https://go.binaryoption.ae/FmUKhe
How goes it, tidy web page you’ve got at this time there.
https://www.pokazswojafirme.pl
Yes! Finally someone writes about activity tracker.
best band watch china
my web-site FITPOLO
Your style is unique compared to other people I
have read stuff from. Many thanks for posting when you’ve got
the opportunity, Guess I’ll just book mark this web site.
It’s going to be end of mine day, but before finish I am reading this impressive post to increase my experience.
I got this web page from my buddy who informed me concerning this web page and at the moment this time
I am browsing this site and reading very informative posts here.
как приложений-умному арендовать жилище:
9 простых шагов – wonderzine
Highly enlightening looking onward to coming back again.
https://www.efektywnezarzadzaniebiznesem.info
This article is really a good one it assists new internet viewers,
who are wishing in favor of blogging.
Thanks for finally writing about > CONFIGURING SSL AUTHENTIFICATION –
Benson Yerima we buy ugly houses Fort Worth TX
If some one wants to be updated with hottest technologies after that
he must be visit this site and be up to date every day.
Thank you for the auspicious writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you!
However, how could we communicate?
I every time emailed this web site post page to
all my friends, as if like to read it next my friends will too.
Feel free to surf to my webpage – 카지노사이트 운영
You’re a very useful site; could not make it without ya!
https://www.maska24.pl
I know this if off topic but I’m looking into starting
my own weblog and was wondering what all is needed to get set up?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web smart so I’m not 100% sure. Any suggestions or advice would be greatly appreciated.
Many thanks
These are truly wonderful ideas in regarding blogging.
You have touched some fastidious things here. Any way keep up wrinting.
Thanks extremely beneficial. Will share website with my
pals.
https://www.onga.pl
Great article, just what I needed.
You actually make it seem really easy together with your presentation but I find
this topic to be really one thing that I believe I might never understand.
It seems too complex and extremely wide for me.
I’m having a look ahead in your subsequent put up, I will attempt to get the cling of
it!
We will teach you how to earn $ 7000 per hour. Why?
We will profit from your profit.https://go.binaryoption.ae/FmUKhe
My spouse and I stumbled over here from a different web
page and thought I should check things out. I like
what I see so now i’m following you. Look forward to looking over your web page repeatedly.
I think this is one of the most significant information for me.
And i’m glad reading your article. But want to remark on some
general things, The website style is perfect, the articles is really great : D.
Good job, cheers
Your stuff is amazingly intriguing.
https://www.inicjatywabiznesowa.pl
I get pleasure from, cause I found just what I used to be
taking a look for. You have ended my four day long hunt! God
Bless you man. Have a great day. Bye
Pretty component of content. I simply stumbled upon your site and in accession capital to claim that
I get in fact loved account your weblog posts. Anyway I will be subscribing on your augment or
even I achievement you access consistently quickly.
زبان آلمانی یکی از پرطرفدارترین زبان های جهان می باشد.
زبان آلمانی در قسمتی از اروپا صحبت می شود.
دلیل زیبایی و ظرافت هایی که دارد؛ بسیاری
از افراد اقدام به آموزش آن میکنند تابتوانند به این
زبان صحبت کنند. در تهران کلاس های زیادی برای آموزش زبان وجود داردکه
ما در این مطلب می خواهیم شما را بهترین آموزشگاه های زبان آلمانی
در تهران آشنا کنیم تا با آگاهی کامل بتوانید اقدام به
آموزش آن نمایید.
Latest Apk’s. Latest game patches. The best Apk files are on this site.
click and download. it’s that simple. If you like to play games and are struggling to download
APKs, this is the site for you. Don’t forget to visit!
It’s going to be finish of mine day, however before ending I am reading this impressive article to increase my knowledge.
Normally I do not read post on blogs, however I wish to say that this write-up very forced me to take a look
at and do it! Your writing style has been surprised me.
Thank you, very nice post.
Here is my site idn live slot
I am extremely impressed with your writing skills and also with the layout on your weblog.
Is this a paid theme or did you customize it yourself?
Anyway keep up the excellent quality writing, it’s rrare tto see a great blog like
this one nowadays.
you are actually a excellent webmaster. The site loading velocity is amazing.
It kind of feels that you’re doing any unique trick. Moreover, The contents are masterpiece.
you’ve done a great task on this topic!
ما در این مقاله به معرفی
کلاس های عکاسی تهران میپردازیم.
تاانتها با ما همراه باشید.
عکاسی یا فَرتورنِگاری یا
فُتوگِرافی در لغت به معنای روش عکاسی و عکسبرداری است.
و همچنین به عمل و شغل عکاس نیز گفته میشود.
این هنر در اکثر زبانهای جهان فتوگرافی خوانده میشود.
که ترکیبی از دو کلمهٔ یونانی فتو به معنی نور و گرافی به
معنی ثبت یا نگارش است. بنابراین،
فتوگرافی به معنای نقش کردن با نور است.
عکاسی یعنی ثبت و ایجاد یک تصویر؛ که در دو مرحله انجام میشود.
نخست، بهدستآوردن تصویر به وسیلهٔ دوربین
و ثبت آن روی نگاتیو (فیلم) یا گیرنده تصویر الکترونیکی و دوم، ظاهر کردن تصویر مخفی حاصل از دوربین عکاسی و پایدارکردن
آن.
در این فرایند، دریافت و
ثبت نور بر روی یک سطح حساس
به نور، مانند نگاتیو یا گیرنده تصویر، باعث
میشود. الگوهای نوری بازتابیده شده یا ساطع شده
از اشیاء بر روی سطح حساس به نور
(نقره کلرید یا گیرنده) تأثیرگذارد و
باعث ثبت تصاویر گردد.
عکاسی دارای سه جنبهٔ علمی، صنعتی
و هنری است. بهعنوان یک پدیدهٔ علمی متولد شد، بهشکل یک صنعت گسترش یافت و به عنوان هنر تثبیت شد.
عکاسی توسط یک فرد کشف و تکمیل نشدهاست.
بلکه نتیجهٔ تلاش بسیاری از افراد در زمینههای
مختلف و اکتشافات و نوآوریهای آنان در طول تاریخ است.
و سالها قبل از اختراع عکاسی، اساس کار دوربین عکاسی
وجود داشتهاست اما اولین تصویر لیتوگرافی نوری در سال ۱۸۲۲ میلادی توسط مخترع فرانسوی،
ژوزف نیسهفور نیِپس تولید شد و
پس از آن توانست عکسی دائمی از طبیعت به نام اصطبل و
کبوترخانه را خلق کند. او با همکاری لوئی داگر، آزمایشهایی را بر ترکیبات نقره براساس یافتههای یوهان هاینریش شولتز انجام دادند.
و داگر در سال ۱۸۳۷ توانست روش داگرئوتایپ را اختراع کند.
Keep on working, great job!
Terrific post however I was wondering if you could write a litte
more on this topic? I’d be very grateful if you could elaborate a little bit further.
Cheers!
Ver y descargar Películas y Series en Latino, Español, Subtitulado e ingles, los últimos estrenos en la mejor calidad HD
sin cortes. Cuevana Online.
Incredible points. Solid arguments. Keep up the amazing work.
Hi there! This is kind of off topic but I need some guidance from an established blog.
Is it hard to set up your own blog? I’m not very techincal but I can figure things
out pretty fast. I’m thinking about creating my own but I’m not sure where to start.
Do you have any points or suggestions? Many thanks
hey there and thank you for your information – I’ve
certainly picked up something new from right here.
I did however expertise some technical issues using
this website, as I experienced to reload the web site lots of times previous to I
could get it to load properly. I had been wondering if
your hosting is OK? Not that I’m complaining, but sluggish loading
instances times will sometimes affect your placement in google and can damage your quality score if ads and marketing with Adwords.
Anyway I am adding this RSS to my e-mail and can look out for much
more of your respective exciting content.
Make sure you update this again soon.
Hi there, I enjoy reading through your article. I like to write
a little comment to support you.
What’s up, this weekend is good in favor of me, for the reason that this occasion i am
reading this impressive informative piece of writing here
at my house.
my web site; earn money Online in tamil
I read this post completely concerning the comparison of latest and previous
technologies, it’s remarkable article.
Howdy would you mind letting me know which hosting company you’re using?
I’ve loaded your blog in 3 completely different browsers and I must say
this blog loads a lot quicker then most. Can you suggest a good hosting provider at a reasonable price?
Many thanks, I appreciate it!
I don’t even know how I ended up here, but I thought this post
was good. I don’t know who you are but certainly you’re going
to a famous blogger if you aren’t already 😉 Cheers!
my web site: Fort Worth area Cash home buyers
You could certainly see your skills within the article
you write. The sector hopes for more passionate writers like you
who aren’t afraid to mention how they believe. All the time go after your heart.
Hey, I think your site might be having browser compatibility issues.
When I look at your blog in Opera, it looks fine but when opening in Internet
Explorer, it has some overlapping. I just wanted to give you a quick heads up!
Other then that, wonderful blog!
Hi! Would you mind if I share your blog with my myspace group?
There’s a lot of folks that I think would really appreciate your content.
Please let me know. Cheers
Hi, constantly i used to check weblog posts here in the early hours in the break of day, because i love to learn more and more.
Very nice write-up. I definitely love this website.
Thanks!
Greetings! Very useful advice in this particular
article! It’s the little changes that produce the most significant changes.
Thanks a lot for sharing!
Hi there! I realize this is somewhat off-topic
but I needed to ask. Does operating a well-established website like yours require a lot of work?
I am brand new to writing a blog however I do write
in my journal every day. I’d like to start a blog so I will
be able to share my personal experience and thoughts online.
Please let me know if you have any kind of recommendations or tips for brand new aspiring bloggers.
Thankyou!
Wow, fantastic blog layout! How lengthy have you ever been blogging for?
you made blogging look easy. The whole glance of your
web site is wonderful, as well as the content!
Useful information. Lucky me I found your website accidentally,
and I’m surprised why this twist of fate didn’t took place earlier!
I bookmarked it.
Thank you a bunch for sharing this with all folks you really recognise
what you are talking about! Bookmarked. Please also discuss with my web site =).
We may have a link change contract among us
รับชมกันแบบฟรีๆ ไม่เสียค่าใช้จ่าย โดยเฉพาะการดูหนังใหม่ชนโรง หนังที่มีคะแนนเรตติ้งสูงจาก IMDB
และ Netflix ท่านจะได้รบชมหนังใหม่ก่อนใครได้จากที่นี้ ซึ่งเราจะมีการปรับปรุงเว็บไซต์และระบบการดูหนังของเราให้ดียิ่งขึ้นให้เหมาะกับการเข้ารับชมของคนจำนวนมาก ด้วยความคมชัดระดับ HD
ตั้งแต่ 360px, 480px, 720px และ 1080px ไปจนถึงความคมชัด 4K หรือ
Ultra HD
Everyone loves what you guys are up too. This kind of clever
work and exposure! Keep up the awesome works guys I’ve you
guys to my blogroll.
I’ll immediately seize your rss feed as I can not to find your email
subscription hyperlink or e-newsletter service.
Do you have any? Please let me realize so that I may subscribe.
Thanks.
I think that is one of the most important info for me.
And i am glad studying your article. But should observation on some common issues, The site style is perfect, the articles is actually great : D.
Good task, cheers
Ridiculous story there. What happened after?
Thanks!
You are so cool! I do not believe I’ve read through a single thing like that before.
So good to discover another person with genuine thoughts on this
topic. Really.. thank you for starting this up. This website is something that is required
on the internet, someone with some originality!
Generally I do not learn post on blogs, however I would
like to say that this write-up very compelled me to take a look at
and do it! Your writing style has been surprised me. Thank you, quite great post.
hi!,I really like your writing very so much! percentage we communicate extra about your article on AOL?
I need a specialist on this area to unravel my problem.
May be that’s you! Looking forward to see you.
I every time spent my half an hour to read this web site’s content everyday along
with a cup of coffee.
We’re a group of volunteers and starting a new scheme in our
community. Your web site offered us with valuable info
to work on. You’ve done a formidable job and our entire community
will be grateful to you.
A fascinating discussion is definitely worth comment.
I think that you should write more about this subject, it may not be a taboo subject but typically people do not talk about
these issues. To the next! Many thanks!!
мфо дающие большие суммы на длительный срок
Fascinating blog! Is your theme custom made or did you download it from
somewhere? A design like yours with a few simple adjustements would really make my blog shine.
Please let me know where you got your design. Kudos
Good way of explaining, and pleasant piece of writing to obtain data concerning my presentation subject, which i am going to present in school.
Sun Pharma Modalert 200 Modafinil 100 Mg Preis Modafinil Kaufen Osterreich
Modafinil Kaufen Schweiz http://modafinilkaufenonline.space/niederlande/ Modafinil Schweiz Kaufen
Hello There. I found your blog using msn. This is a really well written article.
I will be sure to bookmark it and come back to read more of your useful info.
Thanks for the post. I’ll certainly return.
I know this website offers quality dependent posts and extra
information, is there any other web site which presents these data in quality?
Woah! I’m really loving the template/theme of this site.
It’s simple, yet effective. A lot of times it’s very difficult to
get that “perfect balance” between user friendliness and visual appearance.
I must say that you’ve done a superb job with this. Additionally, the blog
loads extremely quick for me on Safari. Exceptional Blog!
I read this piece of writing fully concerning the comparison of
latest and earlier technologies, it’s awesome article.
My site: Asap Cash Home Buyers
Seriously….such a helpful web site.
https://www.biznesowymusthave.pl
Hello there, You have done an excellent job. I’ll certainly digg it and personally
recommend to my friends. I’m sure they will be benefited from this
site.
Here is my web blog – Cash home buyers in Pittsburgh
I know this if off topic but I’m looking into starting my own blog and was curious what all is needed
to get setup? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet savvy so I’m not 100% sure.
Any tips or advice would be greatly appreciated.
Kudos
افزایش فالوور اینستاگرام به
شما کمک میکند تا افراد بیشتری
کسب و کار شما را ببینند و در نهایت باعث رشد و گسترش مشتری هایتان
شود. یکی از سادهترین راه های افزایش فالوور اینستاگرام خرید فالوور واقعی اینستاگرام میباشد.
whoah this blog is wonderful i love studying your posts. Stay up the
great work! You realize, a lot of people are searching round for this info,
you could help them greatly.
Valuable info. Fortunate me I found your site by chance, and I’m stunned why this twist of fate
did not happened earlier! I bookmarked it.
Howdy! Would you mind if I share your blog with my twitter group?
There’s a lot of folks that I think would really appreciate your content.
Please let me know. Many thanks
Hey! This is my first visit to your blog! We are a team of volunteers and starting a new initiative in a community in the same niche. Your blog provided us valuable information to work on. You have done a extraordinary job!
I all the time used to study paragraph in news papers but now as I
am a user of web therefore from now I am using net for posts,
thanks to web.
Hi friends, its wonderful paragraph on the topic of educationand entirely explained, keep it up all the time.
each time i used to read smaller articles or reviews
which as well clear their motive, and that is also happening with this
article which I am reading at this time.
антенна 3g своими руками
Nice post. I was checking constantly this weblog and I am inspired!
Extremely useful information particularly the last section 🙂 I maintain such info a lot.
I was seeking this particular information for a long time.
Thanks and good luck.
My homepage – We Buy Ugly Houses Fort Worth TX
I am not certain the place you are getting your information, but good topic.
I needs to spend some time finding out much more
or understanding more. Thanks for excellent info I used to be looking for this information for my mission.
Thanks to my father who told me regarding this blog, this website is genuinely remarkable.
Your way of describing the whole thing in this paragraph is in fact fastidious, all can easily understand it, Thanks a lot.
Howdy! I simply wish to offer you a big thumbs up for your excellent
information you have right here on this post.
I am coming back to your web site for more soon.
Excellent blog you’ve got here.. It’s hard to find good quality writing like yours
nowadays. I truly appreciate individuals like you!
Take care!!
Hello there! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?
Hi there, its pleasant article about media print, we all know media
is a fantastic source of data.
Hey! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly? My weblog
looks weird when viewing from my iphone4. I’m trying to find a template or plugin that
might be able to fix this issue. If you have any suggestions,
please share. Cheers!
It’s going to be ending of mine day, except before
ending I am reading this enormous post to improve my know-how.
در این مقاله قصد داریم به معرفی بهترین
کلاس آیلتس مشهد بپردازیم، اما قبل از آن میخواهیم کمی با ازمون ایلتس آشنا شویم.
تا انتها با ما همراه باشید.
آزمون آیلتس
آیلتس یکی از آزمون های برجسته در زمینه سنجش علم زبان انگلیسی شما به شمار میرود .
آزمون آیلتس هر ساله در تاریخ های مشخصی
برگزار میشود و متقاضیان زیادی برای اهداف گوناگون در این آزمون بین المللی شرکت
میکنند. آزمون آیلتس برای مهاجرت؛ ویزای کاری
ویادرسی از موارد لازم به شمار میرود.
ما دراین مقاله سعی داریم به معرفی بهترین کلاس آیلتس مشهد بپردازیم.
تا انتخاب برای شما ساده تر شود و بتوانید با خیال
راحت به کلاس زبان بروید
. پس تا انتها با ما همراه باشید.
مراحل گرفتن مدرک آیلتس به صورت گام به گام:
قبل از شرکت در آزمون آیلتس باید سطح دانش شما مشخص شود.
به همین علت اولین مرحله ی آزمون آیلتس
سنجیدن دانش فعلی شما از طریق شرکت در آزمون تعیین سطح می باشد.
لازم به ذکر است که آزمون های تعیین سطح موسسات زبان نمی تواند سطح زبان دقیق
شما را مشخص کند و به همین علت به شما پیشنهاد می کنیم که
در یکی از آزمون های شبه آیلتس
که هر 4 مهارت Speaking و Writing و Reading و
Listening را ارزیابی می کنند شرکت نمایید.
بهترین کلاس آیلتس مشهد کجاست؟
در لیست زیر به معرفی تعدادی از بهترین کلاس های آیلتس در مشهد میپردازیم.
آموزشگاه زبان راه پویندگان
مشاهده صفحه آموزشگاه
توضیحات:
تدریس زبان های انگلیسی، آلمانی،
فرانسوی
برگزاری دوره های آمادگی آزمون های
بین المللی جی آر آی – جی مت – یوس –
پی تی ای – دولینگو
موسسه بین المللی راه پویندگان فعالیت حرفه ای
خود را در سال ۱۳۸۵ در قالب برگزاری دوره های آمادگی آزمون های
بین المللی به ویژه آیلتس آغاز نمود.
پس از آن، اخذ مجوزهای لازم و رسمی از وزارت فرهنگ و
ارشاد اسلامی در زمینه یاددهی و آموزش زبان های خارجی، اخذ مجوزاز وزارت علوم، تحقیقات و فناوری در
زمینه ارائه مشاوره برای اخذ پذیرش تحصیلی از دانشگاه های بین المللی، و سازمان فنی و حرفه ای برای برگزاری دوره
های مرتبط به هتلداری باعث شد تا
فعالیت های موسسه شکل متفاوت و متنوعی به خود بگیرد.
آنچه موسسه بین المللی راه پویندگان را
متمایز می سازد داشتن کادر قوی علمی، برنامه ریزی دقیق، برخورداری از دانش روز، وجود دپارتمان های تخصصی و بهره
مندی از مشاوران و کارکنان متخصص و متعهد است.هدف ما خدمت رسانی مطمئن به مراجعه کنندگان محترم
موسسه است. در این راستا، هیات مدیره موسسه از هر پیشنهادی که بتواند باعث ارتقای سطح و تنوع
بخشیدن به مجموعه خدمات ارائه شده شود استقبال می کند و آن را
مورد برسی قرار میدهد.
آموزشگاه زبان ماهان
مشاهده صفحه آموزشگاه
توضیحات:
کالج زبان ماهان کار خود را در مشهد مقدس
از سال ۸۸ و با هدف ایجاد انقلاب و تفاوت های بنیادین در
زمینه آموزش زبان های خارجی و با محوریت زبان انگلیسی به کلیه گروه های سنی آغاز نمود.
تلاش شبانه روزی و بی وقفه مسئولان ماهان در جهت ایجاد تفاوتها و نوآوری های چشمگیر در عرصه مهم زبان آموزی، منجر
به ایجاد دوره های ویژه و منحصرفردی شد که سابقه تشکیل آنها در هیچ کجای ایران بلکه جهان دیده نشده بود.
در سال 94، این مرکز موفق به دریافت مجوز رسمی برگزاری آزمون های بین المللی IELTS از طرف سازمان سنجش آموزش کشور و IDP در مشهد و تهران شد.
در سال 95 نیز، دو شعبه ی دیگر برای آموزش زبان
بزرگسالان و خردسالان افتتاح نمود.
این مجموعه دارای 5 شعبه فعال در سطح شهر مشهد است
که تمامی سنین را در برمیگیرد .
آموزشگاه زبان سفیر گفتمان
مشاهده صفحه آموزشگاه
توضیحات:
مجوز رسمی از وزارت آموزش
و پرورش،وزارت فرهنگ و ارشاد اسلامی
گواهینامه بین المللی ISO 9001 در مدیریت کیفیت
گواهینامه بین المللی ISO 10002 در رسیدگی به شکایات مشتریان
نمایندگی رسمی آکادمی مدرسین آکسفورد (OTA)
تحت نظر انتشارات دانشگاه
آکسفورد OUP
مرکز مجاز برگزاری دوره های تربیت مدرس CELTA تحت نظر دپارتمان ESOL Examination دانشگاه Cambridge
آموزش سریع مکالمه زبان انگلیسی و فرانسه به صورت فشرده، ترمیک، جمعه، دو روز در هفته، فوق فشرده و پنجشنبه
استفاده از تجهیزات مدرن آموزشی
(DVD player و LCD) و سیستم های صوتی پیشرفته در کلاس ها
برگزاری کلاس های کم جمعیت با محدودیت تعداد دانشجویان(حداکثر 12نفر در مقاطع پیشرفته
و حداکثر 17 نفر در سایر مقاطع)
کنترل مداوم کیفیت آموزشی در طول ترم از طریق دوربین های مدار بسته توسط مدیران آموزش واحدها
برگزاری کلاس های تخصصی آمادگی آزمون IELTS
کالج زبان آریان پور
Great Web-site, Carry on the great work. Appreciate it.
https://www.sieradzkatv.pl
Have you ever thought about creating an ebook or guest authoring
on other sites? I have a blog based upon on the same
topics you discuss and would really like to have you share some stories/information. I know my viewers
would enjoy your work. If you’re even remotely interested, feel free to send me
an e mail.
my blog post Who Buys Houses In Raleigh
Thanks for sharing your info. I truly appreciate your
efforts and I will be waiting for your further write ups thank you once again.
интернет маркет автозапчастей.
Поиск деталей программок vin
That is a very good tip particularly to those fresh to
the blogosphere. Simple but very accurate info…
Thanks for sharing this one. A must read post!
Simply wish to say your article is as surprising.
The clarity in your publish is simply great and i could suppose you are knowledgeable in this subject.
Fine with your permission allow me to snatch your feed
to stay up to date with approaching post. Thanks 1,000,000 and
please continue the rewarding work.
Also visit my website: cash home buyers Pittsburgh
When someone writes an paragraph he/she retains the image
of a user in his/her brain that how a user can understand it.
Therefore that’s why this post is amazing. Thanks!
Nice Web page, Carry on the good work. Thank
you so much.
https://www.jakwejscnaszczyt.pl
I wanted to thank you for this very good read!!
I certainly loved every bit of it. I’ve got you saved as
a favorite to look at new things you post…
You could definitely see your enthusiasm within the work
you write. The arena hopes for more passionate writers like you who
are not afraid to say how they believe. At all times follow your heart.
Simply wish to say your article is as astonishing. The clarity in your publish is simply spectacular
and i could assume you are knowledgeable on this subject.
Fine along with your permission allow me to take
hold of your RSS feed to keep updated with coming near
near post. Thanks one million and please continue
the enjoyable work.
Hello, Neat post. There is an issue together with your web site in web
explorer, may check this? IE nonetheless is the marketplace chief and a big part of other folks
will pass over your wonderful writing due to this problem.
Also visit my web site; how long does it take for blood pressure medication to work
ربات های اینستاگرام چیست؟
ربات های اینستاگرام نوعی نرم افزار هستند که تعاملات شما در سراسر اینستاگرام را خودکار می کند.
بسته به نوع رباتی که استفاده میکنید، آنها میتوانند پستها
را بپسندند، نظر بدهند، به نظرسنجیها پاسخ دهند، پیامهای مستقیم ارسال کنند و نمایههای جدید را از طرف شما دنبال کنند.
رباتها زحمت حفظ حسابهای اجتماعی شما را برمیدارند.
خرید ربات اینستاگرام همچنین برای ایجاد رشد مخاطب به سرعت عمل می کنند و می توانند از الگوریتم
ها و اطلاعات مربوط به اهداف شما استفاده کنند
تا شما را در معرض فالوورهای جدیدی قرار دهند که ممکن
است به تنهایی آنها را پیدا نکرده باشید.
در حالی که برخی از رباتها در کنار
یک تیم با نیروی انسانی کار میکنند تا تعاملات شما را
افزایش دهند، برخی دیگر کاملاً از هوش مصنوعی پشتیبانی میکنند.
هنگامی که ربات ها به طور عاقلانه استفاده می شوند، می توانند برای کمک
به شروع حضور شما در رسانه
های اجتماعی و ایجاد برند شما حیاتی باشند.
با این حال، استفاده غیرمسئولانه از ربات
ها می تواند منبعی از هرزنامه های مزاحم باشد که حساب شما
را مسدود می کند.
در سالهای 2017 و 2019، اینستاگرام هرزنامههای
مبتنی بر ربات را سرکوب کرد. ربات های اینستاگرام در لیست ما برای استفاده مسئولانه طراحی شده اند که به شما امکان
می دهد در سال 2021 در این پلتفرم موفق شوید.
It is not my first time to pay a visit this web page, i am browsing this web
site dailly and get good facts from here all the time.
Obtain on the website any segregated schools amid your community?
Aw, this was an extremely nice post. Taking a few minutes and actual effort to generate
a good article… but what can I say… I put things off a whole lot and don’t manage to get nearly anything done.
Hi, i think that i saw you visited my website so i came to “return the favor”.I
am trying to find things to improve my website!I suppose its
ok to use a few of your ideas!!
Hello i am kavin, its my first time to commenting
anyplace, when i read this piece of writing i thought
i could also create comment due to this good article.
Passion the website– really individual pleasant and lots to see!
https://www.malypomyslwielkafirma.pl
Hello, i think that i saw you visited my web site so i came to “return the favor”.I’m attempting to find
things to enhance my site!I suppose its ok to use
a few of your ideas!!
москва сити аренда квартиры на сутки
Incredible points. Outstanding arguments. Keep up the great spirit.
Fastidious answer back in return of this question with solid arguments and telling
the whole thing regarding that.
Heyy there! I simply would lie tto give you a huge thumbs up for your
excellent information youu have right here oon this post.
I will be returning to your site for more
soon.
my web blog: https://www.blogger.com/u/6/profile/11218951435971374461
Hello! This post couldn’t be written any better! Reading through this post reminds me of my previous room mate!
He always kept chatting about this. I will forward this
page to him. Fairly certain he will have a good read.
Many thanks for sharing!
Excellent post. Keep posting such kind off info on your page.
Im really impressed by it.
Hey there, You’ve pperformed an excellent job. I’ll
certainly digg it and in my opinion recommend to my friends.
I am confident they’ll be benefited from this webb
site.
Also visit my web page – https://profile.hatena.ne.jp/bonar30/
Excellent goods from you, man. I’ve consider your stuff previous to and you’re
simply too excellent. I really like what you have bought here,
certainly like what you’re stating and the best way in which you say it.
You make it entertaining and you still take care of to stay it wise.
I can not wait to read much more from you. That is really a
terrific website.
I was able to find good information from your blog posts.
Elit Ümraniye Escort Bayan Leyla Kalite Düşkünü
Genel olarak erkekleri çok iyi tanıyan ve bu sektörde uzun süredir hizmet veren Ümraniye Escort Bayan olarak buraya ilanımı bırakmak istiyorum.
Her koşulda sizi el üstünde tutan ve beklentilerinizi önemseyen bir
hatunum. Bu yüzden beni tercih etmenizi sabırsızlıkla beklediğimi özellikle bilmenizi istiyorum.
Her konuda bilgili ve kültürlü hareket etmemi oldukça beğenen erkekler tarafından sıklıkla tercih edilen bir hatunum.
Bu yüzden ilişkilerde samimi olan bayan partner
arıyorsanız doğru ilanı okuduğunuzu söylemek istiyorum.
Erkeklerin her bakımdan etkileneceği ve sizin ne düşündüğünüze kadar anlayabilecek yeterlilikte bir Escort Ümraniye
bayanıyım.
Dolayısıyla kendinizi bana bırakıp sizde güzel bir gece yaşamak istiyorsanız benimle
unutulmaz bir gece yaşamaya hazır olun.
7 den 70 e ayrımcılık yapmadan her erkeğe hizmet
verdiğimi söylemek istiyorum. Ayrıca erkeklerin bana gelirken temiz olması
dışında hiçbir şartım ve beklentim yok.
Sizde ayağınıza gelen fırsatı kaçırmadan benimle beraber olmak için hemen randevu almayı ihmal etmeyerek arayın canlarım.
Diğer bayanlardan farklı olarak ateşli ve sürekli seks
yapmadan duramayan bir Ümraniye Bayan Escort olarak buraya ilanımı bırakmak istiyorum.
İşime çok düşkünüm ve bu yüzden yaklaşık 7 yıldır bu sektördeyim.
Ne istediğinizi bilecek kadar siz değerli beyler hakkında bilgi sahibiyim.
Heya i’m for the first time here. I came across this board and I in finding It really helpful & it helped me out
much. I’m hoping to offer something again and help
others such as you helped me.
Heya! I just wanted to ask if you ever have any issues with hackers?
My last blog (wordpress) was hacked and I endrd up losing several
weeks of hard work due to nno data backup. Do you have any solutions to protect against hackers?
Heree is my homepage: https://bandarpkv47.wixsite.com/bandarpkv0051
Fine way of describing, and good piece of writing to take information about
my presentation subject matter, which i am going to deliver in academy.
Hello There. I discovered your weblog using msn. That
is a really well written article. I will make sure to bookmark it and
come back to learn extra of your useful information. Thanks for the post.
I will certainly comeback.
специальность курьер: правила, оплата за работу, шансы
If some one needs expert view about blogging and site-building then i propose him/her to go to see this website, Keep
up the fastidious work.
Its such as you learn my mind! You appear to
understand so much about this, like you wrote the e-book in it or something.
I feel that you just could do with a few % to power the message home
a little bit, but other than that, that is excellent blog.
A fantastic read. I will certainly be back.
magnificent points altogether, you just won a emblem new reader.
What could you recommend about your put up that you
made a few days ago? Any positive?
Have you ever thought about adding a little bit more than just your articles?
I mean, what you say is important and everything. But imagine if you added
some great graphics or video clips to give your posts more,
“pop”! Your content is excellent but with images and video clips, this
website could definitely be one of the best in its field.
Very good blog!
Hi would you mind sharing which blog platform you’re working with?
I’m looking to start my own blog soon but I’m having a difficult time deciding between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design and style seems different then most blogs and I’m looking for
something unique. P.S Sorry for being off-topic but I had
to ask!
Thanks for your marvelous posting! I genuinely enjoyed reading
it, you may be a great author.I will make certain to bookmark your blog and will eventually come back from now on. I want to encourage yourself to continue your great job, have a
nice morning!
Thanks for the marvelous posting! I seriously enjoyed reading it,
you may be a great author.I will always bookmark
your blog and definitely will come back later on. I
want to encourage continue your great writing, have a nice evening!
Hi to all, how is everything, I think every one is getting more from this website, and
your views are fastidious in support of new visitors.
If you are going for finest contents like I do, only visit
this site all the time since it gives feature contents, thanks
Wow cuz this is really excellent work! Congrats and keep it up.
https://www.c-online.pl
I visited many web pages but the audio feature for audio songs current at this web site is really excellent.
Hi there, after reading this remarkable piece of writing i am too cheerful to share my experience here with
mates.
Howdy! Do you know if they make any plugins to protect
against hackers? I’m kinda paranoid about losing everything I’ve worked hard on.
Any tips?
I am really delighted to read this weblog posts which contains plenty
of useful data, thanks for providing such statistics.
Incredibly individual friendly website. Great details readily
available on few gos to.
https://www.czegoniepiszawgazetach.pl
I’m extremely impressed with your writing skills as well
as with the layout on your blog. Is this a paid theme or did
you customize it yourself? Anyway keep up the excellent quality writing,
it’s rare to see a nice blog like this one
today.
Does your website have a contact page? I’m having problems locating it but, I’d like to shoot you an e-mail.
I’ve got some suggestions for your blog you might be interested in hearing.
Either way, great website and I look forward to seeing it expand over time.
https://www.alquds.edu/en/
alquds university,جامعة القدس,aqu,arab university,palestinian university
Al-Quds University (AQU) is a collegiate research university that currently offers more than 120 undergraduate and postgraduate programs, taught through its fifteen degree-granting
faculties that cover the main scientific disciplines such as
medicine, life, and natural sciences, business and management,
arts and humanities, law and jurisprudence, engineering, and social sciences.
Established in 1970, AQU remains the only Arab
Palestinian university in Jerusalem, Palestine.
AQU currently enrolls around 12,000 full time students, taught by more than 700 faculty members
We stumbled over here from a different page and thought
I may as well check things out. I like what I see so now i am
following you. Look forward to looking over your web page repeatedly.
I will right away clutch your rss feed as I can not to find
your e-mail subscription hyperlink or newsletter service.
Do you have any? Kindly permit me realize so that I could subscribe.
Thanks.
Generally I don’t learn article on blogs, but I wish
to say that this write-up very pressured me to take a look at
and do so! Your writing taste has been surprised me.
Thank you, very great article.
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for
quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I look forward to your new updates.
For latest information you have to pay a visit world wide web and on the web I found this web site
as a finest web site for most up-to-date updates.
ковка изделий на заказ ковка на забор французская ковка
Passion the website– extremely user friendly and whole lots to see!
https://www.podstawywspolczesnegobiznesu.eu
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time
a comment is added I get three e-mails with the same comment.
Is there any way you can remove people from that service?
Bless you!
With thanks for sharing this neat websites.
https://www.iclub.edu.pl
hello!,I love your writing very a lot! share we keep in touch more about
your post on AOL? I require an expert on this area to
solve my problem. May be that is you! Taking a look forward to look you.
Good day! This is my first visit to your blog! We are
a team of volunteers and starting a new initiative in a community in the same niche.
Your blog provided us useful information to work on. You have done a outstanding job!
Very quickly this web page will be famous amid all
blog people, due to it’s pleasant articles
Just want to say your article is as amazing. The clearness in your post is
just nice and i could assume you’re an expert on this subject.
Fine with your permission let me to grab your feed to keep updated with forthcoming post.
Thanks a million and please carry on the enjoyable work.
ɡreat issues altogether, үou ϳust won a
brand new reader. Whаt would you recommend in regaгds to
your put up that үoս made a few days ago? Any certain?
I don’t even know how I ended up here, but I thought this post
was good. I do not know who you are but definitely you’re going to a famous blogger if you
aren’t already 😉 Cheers!
Hey there, You’ve done a fantastic job. I’ll definitely digg it and personally recommend
to my friends. I’m confident they will be benefited from
this site.
I read this article completely regarding the resemblance
of newest and earlier technologies, it’s amazing article.
I delight in the information on your websites.
Kudos.
https://www.cojaczytam.pl
What’s up, this weekend is pleasant in support of me, for the
reason that this moment i am reading this great informative piece of writing here at my house.
Hey there are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started
and set up my own. Do you need any html coding knowledge to make your own blog?
Any help would be greatly appreciated!
Hi! I understand this is kind of off-topic however I needed to ask.
Does operating a well-established blog like yours take a large amount
of work? I am completely new to running a blog but
I do write in my diary daily. I’d like to start a
blog so I can easily share my experience and feelings online.
Please let me know if you have any recommendations or tips for new aspiring blog
owners. Appreciate it!
Hello! I know this is somewhat off topic but I was wondering which blog platform are you using for this website?
I’m getting tired of WordPress because I’ve had problems with hackers and I’m looking at alternatives for another platform.
I would be great if you could point me in the direction of a good platform.
Hey! I could have sworn I’ve been to this site before but after
checking through some of the post I realized it’s new to me.
Nonetheless, I’m definitely glad I found it and I’ll be book-marking and
checking back frequently!
DAOs, or decentralized autonomous organizations, have inched into
the mainstream over the last few months. DAOs are online groups that mint virtual tokens on a blockchain, and use the tokens to vote on what the
DAO should do.
Saved as a favorite, I love your website!
Thanks for finally writing about > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima < Liked it!
Hello this is somewhat of off topic but I was wanting to know if blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding experience so I wanted to get guidance from someone with experience.
Any help would be greatly appreciated!
Good response in return of this query with firm arguments and telling all on the topic of that.
I have learn several excellent stuff here. Definitely worth bookmarking for revisiting.
I wonder how much attempt you sett tto make this kind of wonderful informative site.
homepage
Wonderful web site. Plenty of helpful info here. I’m sending it to some pals ans also sharing in delicious.
And of course, thank you on your sweat!
Magnificent site. Plenty of useful information here.
I am sending it to several buddies ans additionally
sharing in delicious. And certainly, thank you to your sweat!
Thanks a lot for sharing your cool website.
https://www.poradnikmlodegoprzedsiebiorcy.pl
در این مطلب از سایت اسنپ کلاس میخواهیم مراکز بینایی سنجی اصفهان را بررسی کنیم .
محله های مختلف اصفهان یعنی
حکیم نظامی ، ملک شهر ، جی ، بهارستان و سایر محله ها دارای بینایی
سنجی های مختلفی هستند که بهترین مرکز
بینایی سنجی در اصفهان موسسه گوانجی است .
برای دریافت اطلاعات بیشتر و تعیین نمره
عینک خود در سریع ترین زمان ممکن زیر نظر بهترین
متخصص بینایی سنجی در اصفهان و بهترین اپتومتریست در اصفهان تماس بگیرید .
What a data of un-ambiguity and preserveness of valuable knowledge concerning
unexpected feelings.
A person necessarily lend a hand to make seriously posts I might state.
This is the very first time I frequented your website page and up to now?
I amazed with the research you made to create this particular put up incredible.
Excellent job!
This is the perfect site for everyone who wants to understand this topic.
You know a whole lot its almost hard to argue with you
(not that I actually would want to…HaHa). You definitely put a fresh spin on a
subject that’s been discussed for years. Wonderful stuff, just great!
Thanks for sharing your thoughts about dog
ate espoma garden tone. Regards
Howdy, i read your blog occasionally and i own a similar one and i was just wondering if you get a lot of spam feedback?
If so how do you reduce it, any plugin or anything you can advise?
I get so much lately it’s driving me crazy so any assistance
is very much appreciated.
سلام ، در این مطلب از سایت
اسنپ کلاس میخواهیم مراکز بینایی سنجی اصفهان را بررسی کنیم .
محله های مختلف اصفهان یعنی حکیم نظامی ، ملک
شهر ، جی ، بهارستان و سایر محله ها
دارای بینایی سنجی های مختلفی هستند که بهترین مرکز
بینایی سنجی در اصفهان موسسه گوانجی است .
برای دریافت اطلاعات بیشتر و تعیین نمره عینک خود در سریع ترین زمان ممکن زیر نظر بهترین متخصص بینایی سنجی در
اصفهان و بهترین اپتومتریست در اصفهان تماس بگیرید .
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point. You clearly know what youre talking about, why throw away your intelligence on just posting videos to your site when you could be giving us something enlightening to read?
Thanks a lot for the helpful write-up. It is also my belief that mesothelioma cancer has an incredibly long latency interval, which means that the signs of the disease may not emerge until 30 to 50 years after the preliminary exposure to asbestos fiber. Pleural mesothelioma, and that is the most common kind and influences the area around the lungs, could cause shortness of breath, torso pains, and also a persistent coughing, which may result in coughing up bloodstream.
سلام ، در این مطلب از سایت اسنپ کلاس
میخواهیم مراکز بینایی سنجی اصفهان را بررسی کنیم .
محله های مختلف اصفهان یعنی حکیم نظامی ، ملک شهر ،
جی ، بهارستان و سایر محله ها دارای بینایی سنجیهای مختلفی هستند
که بهترین مرکز بینایی سنجی در
اصفهان موسسه گوانجی است .
برای دریافت اطلاعات بیشتر و تعیین
نمره عینک خود در سریع ترین زمان ممکن زیر نظر بهترین متخصص بینایی سنجی در اصفهان و بهترین اپتومتریست در اصفهان تماس
بگیرید .
May I just say what a comfort to uncover an individual who
genuinely understands what they are talking about online.
You definitely understand how to bring an issue to light and make it important.
A lot more people really need to look at this and understand this side of your story.
I was surprised that you’re not more popular since you most
certainly have the gift.
Good post. I learn something totally new and challenging on blogs I
stumbleupon on a daily basis. It will always be exciting to read articles from
other authors and practice a little something from other websites.
سلام ، در این مطلب از سایت اسنپ کلاس میخواهیم مراکز بینایی سنجی اصفهان را بررسی کنیم .
محله های مختلف اصفهان یعنی حکیم نظامی ، ملک شهر ، جی ، بهارستان
و سایر محله ها دارای بینایی سنجی های مختلفی هستند که بهترین مرکز بینایی سنجی
در اصفهان موسسه گوانجی است .
برای دریافت اطلاعات بیشتر و تعیین نمره
عینک خود در سریع ترین زمان ممکن زیر
نظر بهترین متخصص بینایی سنجی در اصفهان و بهترین
اپتومتریست در اصفهان تماس بگیرید .
Hey there! I know this is kind of off topic but I was wondering if you
knew where I could locate a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having trouble finding one?
Thanks a lot!
سلام ، در این مطلب از سایت اسنپ کلاس میخواهیم مراکز
بینایی سنجی اصفهان را بررسی کنیم .
محله های مختلف اصفهان یعنی حکیم نظامی ، ملکشهر ، جی
، بهارستان و سایر محله ها دارای بینایی سنجی های مختلفی هستند که بهترین مرکز بینایی
سنجی در اصفهان موسسه گوانجی است .
برای دریافت اطلاعات بیشتر و تعیین نمره عینک خود در سریع ترین زمان ممکن
زیر نظر بهترین متخصصبینایی سنجی
در اصفهان و بهترین اپتومتریست در اصفهان تماس بگیرید .
Further with reference to DNA, 528 Hz frequencies have been used to assist remove
impurities from the body by eradicating them from DNA
at first.
سلام ، در این مطلب از سایت اسنپ کلاس میخواهیم مراکز بینایی سنجی اصفهان را بررسی
کنیم . محله های مختلف اصفهانیعنی حکیم
نظامی ، ملک شهر، جی ، بهارستان و سایر محله ها دارای بینایی سنجی
های مختلفی هستند که بهترین مرکز بینایی سنجی
در اصفهان موسسه گوانجی است . برای دریافت اطلاعات بیشتر و تعیین نمره عینک خود در سریع ترین زمان ممکن زیر نظر بهترین متخصص بینایی سنجی در اصفهان و بهترین
اپتومتریست در اصفهان تماس بگیرید .
Hi mates, nice article and good arguments commented here, I am actually enjoying by these.
my blog … cách làm bánh chuối Chiên
Magnificent goods from you, man. I have understand your stuff previous to and you are
just extremely excellent. I actually like what
you have acquired here, certainly like what you’re saying and the
way in which you say it. You make it enjoyable and you still take care of to keep it
wise. I can not wait to read far more from you. This is really a great website.
Wow cuz this is excellent work! Congrats and keep it up.
https://www.poczatkujacyprzedsiebiorca.pl
I’ve been surfing online more than 4 hours today,
yet I never found any interesting article like yours.
It’s pretty worth enough for me. In my view, if all website owners and bloggers made
good content as you did, the net will be a lot more useful than ever before.
You’ve terrific information right.
https://www.myslimyoprzyszlosci.eu
Just simply had to stress I am delighted
that i happened on the page.
https://www.redpaprika.pl
Now I am going away to do my breakfast, afterward having my breakfast coming again to read additional news.
Hello, i read your blog occasionally and i own a similar one
and i was just wondering if you get a lot of spam responses?
If so how do you reduce it, any plugin or anything you can suggest?
I get so much lately it’s driving me insane so any assistance is very much appreciated.
Hmm is anyone else encountering problems with the images on this blog loading?
I’m trying to determine if its a problem on my end
or if it’s the blog. Any feedback would be greatly appreciated.
I simply could not leave your website prior to suggesting
that I really loved the usual info a person provide in your guests?
Is gonna be again ceaselessly in order to inspect new posts
hello!,I like your writing very much! percentage we keep up
a correspondence more approximately your post on AOL?
I need an expert on this house to unravel my
problem. May be that is you! Having a look forward to see you.
I could not resist commenting. Exceptionally well written!
Hi my loved one! I want to say that this post is awesome, great written and come with approximately all significant infos.
I’d like to peer more posts like this .
Hi, everything is going nicely here and ofcourse every one is sharing facts,
that’s genuinely good, keep up writing. disposable vape private label
my blog post … evlla wholesale vapes
Hello, I want to subscribe for this webpage to get newest updates,
thus where can i do it please help.
Hi there i am kavin, its my first time to commenting anyplace, when i read this article i thought i
could also create comment due to this sensible
post.
Hi there! I could have sworn I’ve been to this website before but after going
through some of the posts I realized it’s new to me. Nonetheless, I’m certainly
pleased I came across it and I’ll be bookmarking it and checking back regularly!
This site truly has all of the information and facts I wanted
concerning this subject and didn’t know who to ask.
Whаt i dօn’t realize іs in reality how yߋu’re
no longer really a lot more smartly-preferred tһan уou may be now.
You’гe νery intelligent. You understand tһerefore considerably іn terms ⲟf this matter,
maɗe mе personally believe іt from numerous numerous
angles. Ιts like women аnd men are not interested еxcept it іs something to accomplish with Lady gaga!
Yߋur individual stuffs ɡreat. Alwаys care for it up!
Magnificent website. Lots of helpful information here.
I am sending it to several pals ans also sharing in delicious.
And of course, thanks to your effort!
Really….this is a good website.
https://www.szukajswojejdrogi.com
Attractive section of content. I just stumbled upon your
website and in accession capital to assert that I get actually enjoyed
account your blog posts. Any way I’ll be subscribing to your augment and even I achievement you access consistently rapidly.
I’d like to thank you for the efforts you’ve put in writing this website.
I’m hoping to see the same high-grade content from you in the future as well.
In fact, your creative writing abilities has motivated me
to get my own, personal site now 😉
Pretty nice post. I just stumbled upon your blog and wanted to say that I have truly
enjoyed browsing your blog posts. After all I’ll be subscribing to your feed and I hope you
write again soon!
I feel this is among the such a lot vital info for me.
And i’m glad reading your article. But wanna remark on some normal issues, The site style is great, the articles is really nice : D.
Excellent job, cheers
With havin so much written content do you ever run into any problems of plagorism or copyright
infringement? My website has a lot of unique content I’ve
either authored myself or outsourced but it appears a lot of
it is popping it up all over the web without my agreement.
Do you know any solutions to help reduce content from being
ripped off? I’d truly appreciate it.
Hi there, I discovered your blog by way of Google even as searching for a comparable matter,
your website came up, it seems to be great. I’ve bookmarked it in my google bookmarks.
Hello there, simply became alert to your blog via Google, and found that it’s
truly informative. I’m gonna be careful for brussels.
I will appreciate for those who continue this in future.
A lot of folks will probably be benefited from your
writing. Cheers!
Hi there! I know this is kinda off topic but I was wondering
which blog platform are you using for this website? I’m getting fed up of WordPress because I’ve had problems with
hackers and I’m looking at alternatives for another platform.
I would be fantastic if you could point me in the
direction of a good platform.
First of all I would like to say superb blog!
I had a quick question which I’d like to ask if you don’t mind.
I was curious to find out how you center yourself
and clear your head prior to writing. I’ve had trouble clearing my thoughts in getting my thoughts out.
I truly do take pleasure in writing but it just seems like the first 10 to 15 minutes
are generally wasted simply just trying to figure out how to begin. Any ideas or tips?
Kudos!
Excellent post. I was checking constantly
this blog and I’m impressed! Very useful info specially the last part 🙂 I care for such information much.
I was seeking this particular information for a long time.
Thank you and good luck.
Thanks for the good writeup. It in fact used to be a leisure account it.
Glance advanced to more added agreeable from you!
However, how could we be in contact?
Wow, lovely site. Thnx …
https://www.europejskibiznes.eu
I don’t know if it’s just me or if everybody
else experiencing problems with your website.
It appears as though some of the text within your posts are running off the screen. Can somebody else please provide feedback and let me know if this is
happening to them as well? This may be a issue with
my web browser because I’ve had this happen before.
Kudos
واژینیسموس چیست : اگر به دنبال پاسخ به این سوال که واژینیسموس
چیست سری به دنیای وب زده اید
در ادامه ای مقاله ما به طور کامل به ان سوال پاسخ
خواهیم داد. همچنین سعی کرده ایم راه حل های کاملی برای این مشکل
ارائه کنیم و به تشریح کامل
روش های درمانی این عارضه بپردازیم.
در ادامه با کلینیک اعصاب و روان هیربد همراه
باشید.
در برخی از خانم ها، عضلات واژن ممکن است به طور غیر ارادی، گاها یا
دائمی به هنگام تلاش برای دخول دچار انقباض شود، به چنین شرایطی واژینیسموس می
گویند. واژینیسموس در واقع یک اختلال محسوب می شود.
به این اختلال در اصطلاح پزشکی واژینیسم نیز گفته می
شود. افراد دچار اختلال واژینیسموس دخول دردناکی را
در هنگام رابطه جنسی تجربه می
کند زیرا در زمان ورود آلت تناسلی به واژن عضلات
یکسوم، به طور ناخودآگاه دچار انقباض
می شوند.
این اختلال به دو شکل اولیه (بدون هیچ تجربه مقاربتی از قبل) و شکل
ثانویه (با تجربه مقاربت راحت در گذشته) تقسیم
میشود. لازم است بدانید که، انقباض عضلات کاملا غیر ارادی
است و در نتیجه فرد هیچ کنترلی بر آن ندارد.
افراد دچار واژینیسم به دلیل ترس
از دردناک بودن دخول موفق به انجام رابطه جنسی به
طور کامل نمی شوند و این مشکل برای آن ها بار روانی بسیار زیادی به همراه
دارد که در بسیاری از موارد باعث تشدید اوضاع و مشکل آن ها می شود.
به واژینیسموس به انگلیسی نیز vaginismus گفته می شود.
این اختلال با واژه های مختلفی در فارسی
تعبیر و تفسیر می شود. برخی آن را دخول غیر ممکن می نامند و
برخی از واژه هایی همچون ترس
شدید به هنگام نزدیکی یا انقباض غیر ارادی واژن برای توصیف چنین شرایطی استفاده
می کنند. بروز این انقباضات مانع از دخول جنسی می شود یا این امر را برای فرد بسیار دردناک می سازد.
هر چند بروز چنین مشکلاتی می تواند
با رابطه جنسی و کیفیت زندگیتان تداخل داشته باشد اما
باز هم باید اعتماد به نفستان را حفظ کنید زیرا این مشکل درمان پذیر
است. اگر دوست دارید عملکرد جنسی خود را مورد محک قرار دهید می توانید از آزمون معتبر زیر استفاده کنید.
I love the info on your websites. Thanks!
https://www.swiadectwo-energetyczne.pl
Saved as a favorite, I love your blog!
تو ذهنش امپراطورم کرد دردگیر چشمای شورم کرد نور بودم اومد و کورم کرد خوب بودم
از خدا دورم کرد رفت پیش همه مشهورم کرد ….
کوه بودم خیلی مغرور بودم از همه دور بودم ولی مجبور بودم کوه بودم خیلی مغرور بودم از همه دور
بودم ولی مجبور بودم قول دادم بعد از اون
مرد باشم صبر باشم من خود درد باشم با هرکی که
نموند سرد باشم زوج بودم وقتشه فرد باشم
یه وقتایی خیای نامرد باشم … کوه بودم خیلی مغرور بودم از همه
دور بودم ولی مجبور بودم کوه بودم خیلی مغرور بودم از همه دور بودم ولی مجبور
بودم
It’s very easy to find out any topic on net as compared to
textbooks, as I found this paragraph at this site.
Simply desire to say your article is as surprising.
The clearness on your put up is simply excellent and i can think you are an expert on this subject.
Fine along with your permission let me to snatch your RSS
feed to keep updated with drawing close post. Thanks 1,000,000 and please continue the
gratifying work.
Its like you learn my thoughts! You seem to know so much approximately this, like you wrote the e book in it or something.
I think that you just could do with some percent to power the message home a little bit, but other than that, that is wonderful blog.
A great read. I’ll definitely be back.
Just wished to point out I am delighted I happened upon your web site.
https://www.eko-met.com.pl
من از صدای گرم تو پر از ترانه میشم به جز تب چشات انگار چیزی نمونده پیشم به سرم زده که این بار دلمو به تو بسپارم فقط کنار من باشو صدام
کن چه خوبه عاشقی با تو چه خوبه این خیال خوش تویی
همه وجود من همه عشقم همه جونم چه خوبه عاشقی با تو چه خوبه این خیال خوش نگیر دستاتو
از دستام بدون تو نمیتونم دلمو بردار
و ببر نگو که عاشق نشدی نگو که از بغض صدام دلتنگ این عشق نشدی چه
خوبه عاشقی با تو چه خوبه این خیال خوش تویی
همه وجود من همه عشقم همه جونم چه خوبه عاشقی با تو
چه خوبه این خیال خوش نگیر دستاتو از
دستام بدون تو نمیتونم
I have been surfing online more than 3 hours today, yet I never found any interesting article like yours.
It’s pretty worth enough for me. Personally,
if all web owners and bloggers made good content as you
did, the internet will be a lot more useful than ever before.
Generally I don’t read post on blogs, but I wish to say that
this write-up very pressured me to check out and do so! Your writing style
has been surprised me. Thanks, very great article.
عطر تو بوی بهاره چشماتم جاذبه داره فکر کردی تازه رسیدم
من یه قرنو با تو دیدم خوش
به حالم تورو دارم وسط این همه آدم شدی یارم من که تنها کسیم
که تورو یک ثانیه تنها نمیذارم آرامش آینده ی من گریه
و خنده ی من تاج سر قلب منی عشق برازنده
ی من حالا که خوشبختی باهام واسه خدا دست بزن ای جان
ای جانم آرامش آینده ی من گریه و خنده ی من تاج
سر قلب منی عشق برازنده ی من حالا که خوشبختی باهام واسه خدا دست بزن ای جان ای جانم مثلا
محو تو باشم محو اون چشمای معصوم کافیه
بگی تو گوشم یه دوست دارم آروم دیگه دردی نمیمونه چرا قلبت نگرونه خدا که عاشقمونه آرامش آینده ی من گریه
و خنده ی من تاج سر قلب منی عشق برازنده ی من حالا که خوشبختی باهام
واسه خدا دست بزن ای جان ای جانم آرامش آینده ی
من گریه و خنده ی من تاج سر قلب منی عشق برازنده ی من حالا که خوشبختی باهام واسه خدا دست بزن ای جان ای جانم
It is actually a great and useful piece of information. I’m glad that you just shared this useful information with
us. Please keep us informed like this. Thank you for
sharing.
I used to be suggested this website by my cousin.
I’m not sure whether this post is written via him as no one else understand such certain about my trouble.
You are wonderful! Thank you!
Right here is the right webpage for anybody who wishes to understand this topic.
You understand a whole lot its almost tough to argue with you
(not that I personally will need to…HaHa). You certainly put a new spin on a topic which has been written about for ages.
Great stuff, just excellent!
I’m curious to find out what blog platform you have been utilizing?
I’m experiencing some small security problems with
my latest website and I’d like to find something more safe.
Do you have any suggestions?
You have very nice post and pictures, please have a look at our photo tours in the temples of Angkor
merlot.org
Pretty section of content. I just stumbled upon your
site and in accession capital to assert that
I acquire in fact enjoyed account your blog posts.
Any way I will be subscribing to your augment and even I
achievement you access consistently fast.
Awesome blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple adjustements would really make my blog stand out.
Please let me know where you got your design. Bless you
سکوت عاشقانه تویی صدای هر ترانه
تویی که بهترین بهانه تویی برای
حال خوبم تو با منی که خسته نشم که
بی هوا نفس بکشم تویی تویی حال خوشم تویی خیال
خوبم کاشکی بارون بزنه که ساز محبوب
منه صدای بارون تو تویی موسیقی عشق که با تو
آروم میشه این دل پریشون دل پریشون دل پریشون …
اگه تورو همیشه یادمه اگه گذشتم از همه صدای تو صدای قلبمه دلیلش عشقه اگه بی تو بودم و گم شدم اگه تورو
صدا زدم اگه به تو رسیدم از خودم
دلیلی عشقه کاشکی بارون بزنه که ساز محبوب منه
صدای بارون تو تویی موسیقی عشق که با تو آروم میشه این
دل پریشون دل پریشون دل پریشون …
I’m not sure exactly why but this weblog is loading extremely
slow for me. Is anyone else having this problem or is it
a issue on my end? I’ll check back later on and see if the
problem still exists.
Howdy! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really enjoy your content.
Please let me know. Thanks
I’m not sure why but this blog is loading very slow for me.
Is anyone else having this issue or is it a issue on my end?
I’ll check back later on and see if the problem still exists.
I used to be able to find good advice from your blog posts.
Hello, for all time i used to check blog posts here early
in the daylight, because i like to learn more and more.
Howdy, I do believe your website might be having web browser compatibility issues.
Whenever I take a look at your blog in Safari, it looks fine however when opening in IE, it has
some overlapping issues. I simply wanted to provide you with a quick heads up!
Aside from that, great website!
I love reading through your website. Cheers!
https://www.wbstudio.pl
If some one wishes expert view about running a blog afterward i advise him/her to pay a visit this weblog, Keep up
the fastidious work.
I constantly spent my half an hour to read this weblog’s articles everyday along with a cup
of coffee.
I like reading a post that will make men and women think.
Also, thanks for allowing for me to comment!
Many thanks really useful. Will share website with my buddies.
https://www.monitoringoleju.pl
Thanks for the purpose of offering these sort of superb content material.
https://www.biznesoweinspiracje.com
Wonderful work! That is the kind of information that are meant
to be shared around the net. Disgrace on Google for now not positioning this put up higher!
Come on over and visit my web site . Thanks =)
Awesome article.
Hi there! I know this is kind of off topic but I was wondering which blog platform are you using for this website?
I’m getting tired of WordPress because I’ve had issues with hackers
and I’m looking at options for another platform. I would be
fantastic if you could point me in the direction of a good platform.
Your method of describing all in this piece of writing is
in fact nice, all can simply understand it, Thanks a lot.
We absolutely love your blog and find nearly all of your post’s to be just what I’m looking for.
can you offer guest writers to write content for yourself?
I wouldn’t mind publishing a post or elaborating
on many of the subjects you write concerning here. Again, awesome web log!
Whats up this is somewhat of off topic but I was wondering if blogs use WYSIWYG editors or
if you have to manually code with HTML. I’m starting a blog soon but have no coding knowledge so I wanted to
get advice from someone with experience. Any help would
be enormously appreciated!
Link exchange is nothing else however it is simply placing the
other person’s web site link on your page at
appropriate place and other person will also do same in favor
of you.
Hi there Dear, are you actually visiting this site on a regular basis, if so after that you will absolutely take good know-how.
I know this if off topic but I’m looking into starting my own weblog and was curious what all
is required to get set up? I’m assuming having a blog like
yours would cost a pretty penny? I’m not very web savvy so I’m not
100% certain. Any tips or advice would be greatly appreciated.
Thank you
Hurrah, that’s what I was seeking for, what a information! present here at this website, thanks admin of this web site.
Thanks in support of sharing such a fastidious idea, paragraph is fastidious, thats why i have
read it completely
Εveryone loves wһat you guys are սsually սp too.
This type օf clever ᴡork аnd reporting! Ꮶeep up tһe amazing woгks guys Ӏ’ve
incorporated you guys tо my blogroll.
Having read this I believed it was really enlightening.
I appreciate you taking the time and energy to put this information together.
I once again find myself personally spending way too much time both reading and posting comments.
But so what, it was still worth it!
Wow, this paragraph is nice, my sister is analyzing these things, therefore I am going to tell her.
Link exchange is nothing else but it is just placing
the other person’s blog link on your page at suitable place and
other person will also do similar in support of you.
I don’t know whether it’s just me or if everyone else encountering problems with
your site. It seems like some of the written text within your content are running off the screen. Can somebody else please comment
and let me know if this is happening to them as well? This might be a issue with my web
browser because I’ve had this happen before.
Thank you
Also visit my web page :: SEO Hourly Rate
Todɑy, I went to the beachfront with my kids.
I found a sea shell аnd gavе it to my 4 year old
daughter and sаid “You can hear the ocean if you put this to your ear.” She
plɑced the shell to her ear and screamed. Ꭲheгe ѡas a hermit crab insіde and it pinched her
ear. She neѵer ᴡants to go back! LoL Ӏ кnow this is entirely оff topic bսt I had to telⅼ ѕomeone!
Heya i am for the first time here. I found this board
and I to find It really useful & it helped me out much.
I am hoping to offer one thing back and aid others like you
aided me.
Hi there, its pleasant article regarding media print, we all
understand media is a fantastic source of facts.
https://beydoun-lb.com/services/pergolas-more/
Pergolas
Hey there I am so thrilled I found your blog page, I really found you by accident,
while I was searching on Aol for something else, Anyways
I am here now and would just like to say thank
you for a remarkable post and a all round interesting blog
(I also love the theme/design), I don’t have time to read through
it all at the minute but I have bookmarked it and also added in your RSS feeds, so
when I have time I will be back to read a lot more, Please do keep up the great job.
Howdy! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any suggestions?
I simply couldn’t depart your site before suggesting
that I really enjoyed the usual information a person supply in your visitors?
Is gonna be back often in order to check up on new posts
of course like your website but you have to check the spelling on quite a few of
your posts. Several of them are rife with spelling problems and I in finding it very bothersome to inform the reality on the other hand I
will surely come back again.
I was recommended this web site by my cousin. I am not sure
whether this post is written by him as no one else
know such detailed about my trouble. You are incredible! Thanks!
Just desire to say your article is as astounding.
The clearness in your post is just spectacular and i can assume you’re an expert on this subject.
Fine with your permission allow me to grab your RSS feed
to keep updated with forthcoming post. Thanks a million and please keep up the enjoyable
work.
Aw, this was a very good post. Spending some time and
actual effort to make a great article… but what can I say… I procrastinate a
whole lot and don’t seem to get nearly anything done.
What’s up friends, good post and good urging commented here, I am actually enjoying by these.
hello there and thank you for your info – I have certainly picked up something new from right here.
I did however expertise some technical points using
this site, since I experienced to reload the web site a lot of times previous to I could get it to load correctly.
I had been wondering if your web host is OK? Not that I
am complaining, but slow loading instances times will often affect your placement in google and could damage your high quality
score if ads and marketing with Adwords. Well I’m adding this RSS to my
e-mail and could look out for much more of your respective exciting content.
Make sure you update this again soon.
This web site truly has all the info I needed concerning this subject and didn’t know who
to ask.
My homepage নতুন জন্ম নিবন্ধন আবেদন
If you are going for most excellent contents like myself, just go
to see this site everyday because it provides quality contents, thanks
حرف آخرو اول قصه زدی توئه بی رحم از کی به این دیوونه سر نزدی توئه بی رحم
ولی باز همه درد دلامو دارم به تو
میگم عشقم … بگو آخه کی مث تو
این همه غم به دلم ریخت
خاطراتتو بیشتر از هرچی بگی بهمم ریخت
تو نگاهای آخرت آخه چی بود که دلم
ریخت عشقم … من کلی دلتنگم برات با همه میجنگم برات …
دوریت دیوونم کرد بیا عشقم برگرد دوست دارم کی علاقتو بهم کم کرد دوریت دیوونم کرد بیا عشقم
برگرد دوست دارم کی علاقتو بهم کم کرد یادته یه شب که ماهو
توی آسمون نشون دادی گرفتی دستم و تو قلبمو تکون دادی دیوونه این چه کاری بود
که دستمون دادی … یادمه میگفتی زندگی بدون تو نمیگذره کی فکرشو میکرد بگی جدایی
بهتره کی فکرشو میکرد که این قرار آخره
… من کلی دلتنگم برات با همه میجنگم برات …
دوریت دیوونم کرد بیا عشقم برگرد دوست
دارم کی علاقتو بهم کم کرد دوریت دیوونم کرد بیا عشقم برگرد دوست
دارم کی علاقتو بهم کم کرد
Hi, I do believe this is a great blog. I stumbledupon it 😉 I’m going to come back yet again since I bookmarked it.
Money and freedom is the greatest way to change, may you
be rich and continue to help others.
Wow, this post is pleasant, my younger sister
is analyzing these things, therefore I am going to inform her.
Yes! Finally something about buy my house Indianapolis IN.
Feel free to visit my web page … we buy Houses cash Indianapolis IN
You’re so cool! I don’t think I’ve read through anything like
this before. So nice to discover someone with genuine thoughts
on this topic. Really.. thanks for starting this up.
This web site is something that’s needed on the web, someone with a bit of
originality!
Just want to say your article is as surprising.
The clarity on your post is simply great and i can think you are knowledgeable in this subject.
Well along with your permission allow me to grasp your feed to stay up to
date with forthcoming post. Thanks 1,000,000 and please continue the enjoyable work.
I was curious if you ever considered changing the
structure of your site? Its very well written; I love what
youve got to say. But maybe you could a little more in the way
of content so people could connect with it better.
Youve got an awful lot of text for only having one
or two images. Maybe you could space it out better?
Hi there to every body, it’s my first pay a quick visit of this web site; this web site includes remarkable and truly good data in favor of readers.
Its like you read my mind! You appear to know so much about this, like
you wrote the book in it or something. I think
that you could do with a few pics to drive the message
home a bit, but instead of that, this is fantastic blog.
A great read. I’ll certainly be back.
Here is my webpage :: cash home buyers in Houston area
I used to be able to find good info from your articles.
Hi i am kavin, its my first occasion to commenting anyplace, whdn i
rrad this post i thought i could also create comment due to this brilliant article.
I don’t even know how I finished up right here, but I thought
this post was once good. I do not know who you’re but definitely you are going to a famous
blogger if you happen to aren’t already. Cheers!
Thank you, I have recently been looking for information approximately this topic
for a while and yours is the best I have discovered till now.
However, what in regards to the bottom line? Are you certain in regards to the
source?
Hello! Do you know if they make any plugins to protect against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any tips?
I all the time used to study piece of writing in news papers
but now as I am a user of net therefore from now I am using net for posts,
thanks to web.
I enjoy looking through a post that can make people think.
Also, thank you for allowing me to comment!
If you want your bracelet to make a statement, you will want it to face out.
A set of sneakers is often a must-have everybody men. It is only a matter of timing when good fashion turns to
bad.
Woah! I’m really loving the template/theme of this blog.
It’s simple, yet effective. A lot of times it’s challenging to get that
“perfect balance” between superb usability and appearance.
I must say you have done a awesome job with this. Additionally, the blog loads extremely fast for me on Internet explorer.
Outstanding Blog!
Howdy fanhtastic website! Does runnning a blog like this take a lot of work?
I hasve no expertise in computr programming however I had been hoping too start
my own blog soon. Anyways, if you have any recommenations orr techniques for new blog owners please share.
I understand this is off subject but I simply needed to ask.
Thanks!
I am sure this article has touched all the internet viewers, its really really
nice paragraph on building up new web site.
Check out my page – houston we Buy houses
Awesome! Its really remarkable post, I have got much clear
idea on the topic of from this post.
Hi my friend! I wish to say that this article is amazing,
nice written and come with almost all vital infos. I’d like
to peer more posts like this .
Spot on with this write-up, I really feel this amazing site needs
a great deal more attention. I’ll probably be returning to read more,
thanks for the advice!
We absolutely love your blog and find most of your post’s to
be precisely what I’m looking for. Would you offer guest
writers to write content available for you?
I wouldn’t mind composing a post or elaborating on most
of the subjects you write in relation to here.
Again, awesome web site!
I am regular reader, how are you everybody? This piece of writing posted
at this website is in fact good.
You are so awesome! I don’t suppose I’ve truly
read a single thing like that before. So wonderful to discover another
person with genuine thoughts on this subject matter.
Seriously.. many thanks for starting this up. This
website is one thing that’s needed on the internet, someone with some originality!
Magnificent goods from you, man. I have understand
your stuff previous to and you’re just extremely magnificent.
I actually like what you’ve acquired here,
certainly like what you’re stating and the way in which you say it.
You make it enjoyable and you still care for to keep it sensible.
I can not wait to read much more from you. This is actually a great website.
Tempat bikin kaos baju jaket di Semarang. Konveksi
kaos murah Semarang yang menyediakan jasa jahit, sablon, dan jasa bordir komputer dan manual.
I am sure this paragraph has touched all the internet viewers, its really really nice piece of
writing on building up new webpage.
We will teach you how to earn $ 7000 per hour.
Why? We will profit from your profit.https://go.binaryoption.ae/FmUKhe
I think the admin of this site is genuinely working
hard in support of his website, because here every
data is quality based material.
I’m amazed, I must say. Rarely do I encounter a blog that’s equally educative and entertaining, and let me tell you, you’ve hit
the nail on the head. The problem is something which not enough folks are speaking intelligently about.
Now i’m very happy I stumbled across this in my
search for something relating to this.
always i used to read smaller content which as well clear their motive, and that is also happening with this
piece of writing which I am reading here.
I have been browsing online more than 3 hours today, yet I never found
any interesting article like yours. It’s pretty worth enough for me.
In my view, if all web owners and bloggers made good content as you did,
the net will be much more useful than ever before.
Very nice post. I just stumbled upon your blog and
wished to say that I have truly enjoyed surfing around your blog posts.
After all I will be subscribing to your rss feed and I hope you write again very soon!
Hello There. I discovered your blog using msn. This is
an extremely well written article. I’ll be sure to bookmark it and return to read extra of your useful info.
Thank you for the post. I will certainly comeback.
Have you ever considered about including a little bit
more than just your articles? I mean, what you say is valuable and all.
But think of if you added some great graphics or
videos to give your posts more, “pop”! Your content
is excellent but with images and videos, this blog could certainly be one of
the best in its field. Good blog!
Thanks designed for sharing such a fastidious thinking, paragraph is nice, thats why i have
read it fully
My brother recommended I might like this web site. He was totally right.
This put up actually made my day. You cann’t consider simply how so much time I had spent for
this information! Thank you!
There is definately a great deal to find out about this issue.
I really like all of the points you have made.
0 health 5e and mag knight and news iran and news las
vegas and health 7 quarter 4 module 1 and education in the 1960s.
I need to to thank you for this fantastic read!!
I definitely enjoyed every little bit of it. I have got you book-marked to check
out new things you post…
My coder is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the expenses.
But he’s tryiong none the less. I’ve been using Movable-type on numerous websites for about a year and
am worried about switching to another platform. I have
heard good things about blogengine.net. Is there a way I can transfer all my wordpress posts
into it? Any kind of help would be really appreciated!
thanks a lot a great deal this site is usually professional and also
everyday
I’ve been surfing online more than three hours today, yet I never found any
interesting article like yours. It’s pretty worth enough
for me. Personally, if all website owners and bloggers made good content as you did,
the net will be much more useful than ever before.
Thanks for ones marvelous posting! I genuinely enjoyed reading
it, you might be a great author. I will make certain to bookmark your blog
and definitely will come back in the foreseeable future.
I want to encourage you to definitely continue your great
job, have a nice day!
Also visit my web blog; best rolex replica
Having read this I thought it was really enlightening.
I appreciate you finding the time and energy to put this short article together.
I once again find myself personally spending a
lot of time both reading and leaving comments. But so what, it
was still worth it!
you are actually a good webmaster. The website loading velocity is amazing.
It kind of feels that you are doing any distinctive trick.
Furthermore, The contents are masterwork. you have performed a great activity on this subject!
Visit my web page … เว็บเล่นหวย
Very nice write-up. I absolutely appreciate this website.
Keep writing!
Hey there! Someone in my Myspace group shared this website with us so I
came to check it out. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers!
Terrific blog and amazing design and style.
Ahaa, its good dialogue regardijg this paragraph at this place at this webpage, I hawve read alll that, so at this
time me also commenting at this place.
Do you have a spam problem on this site; I also am a blogger,
and I was curious about your situation; we have
crerated some nice practices and wee are looking to trade strategies with other folks,
be sure to shoot me an email if interested.
Greetings! This is my first comment here so I just wanted to give a quick shout out and say I really enjoy reading through your posts. Can you suggest any other blogs/websites/forums that deal with the same topics? Thank you so much!
Thanks very nice blog!
This website definitely has all of the information I needed about this
subject and didn’t know who to ask.
Hello there! Do you use Twitter? I’d like to follow you if that would be okay.
I’m absolutely enjoying your blog and look forward to new posts.
Hi there, I enjoy reading all of your post.
I like to write a little comment to support you. https://dooball321.com
Hey I know this is off topic but I was wondering if you knew of any widgets I could
add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new
updates.
Great blog right here! Also your site quite a bit up
very fast! What host are you the use of? Can I am getting
your associate link to your host? I want my web site loaded up
as fast as yours lol.
I love reading a post that will make people think. Also, thanks for
allowing me to comment!
This is the perfect webpage for anyone who wishes to understand
this topic. You realize so much its almost tough to argue with you (not
that I personally would want to…HaHa). You definitely put a brand new
spin on a topic that has been discussed for many years.
Excellent stuff, just great!
Nice blog here! Also your web site quite a bit
up fast! What host are you the usage of? Can I am getting your associate link in your host?
I want my site loaded up as quickly as yours lol
My web-site: ASAP Cash Home Buyers
whoah this blog is great i like studying your posts.
Stay up the great work! You already know, many people are looking around for this information, you can aid them greatly.
I’m gone to say to my little brother, that he should also visit this web site on regular basis
to take updated from latest news.
Hi there just wanted to give you a quick heads up.
The words in your content seem to be running off the screen in Ie.
I’m not sure if this is a formatting issue or something to do with internet
browser compatibility but I figured I’d post to let you know.
The style and design look great though! Hope you get the problem resolved soon. Many thanks
Hello, i think that i saw you visited my weblog so i came
to “return the favor”.I am attempting to find things to enhance my web site!I suppose its ok to
use some of your ideas!!
I absolutely love your blog.. Excellent colors & theme.
Did you build this web site yourself? Please reply back as I’m trying
to create my own personal blog and want to learn where you got this from or exactly what the theme is called.
Kudos!
Wow that was strange. I just wrote an incredibly long comment but after I clicked
submit my comment didn’t show up. Grrrr… well I’m not writing all
that over again. Anyways, just wanted to say
excellent blog!
My blog post: We Buy Houses In Any Condition Indianapolis
Hey outstanding blog! Does running a blog like this require a large amount of work?
I have virtually no understanding of coding but I had been hoping to start my
own blog soon. Anyways, if you have any suggestions or
techniques for new blog owners please share. I know this is off topic
nevertheless I just had to ask. Kudos!
Here is my web site … sell house for cash Indianapolis
Good article. I definitely appreciate this website. Continue the good work!
Hello would you mind stating which blog platform you’re using?
I’m looking to start my own blog in the near future but I’m having a tough time deciding between BlogEngine/Wordpress/B2evolution and
Drupal. The reason I ask is because your design and style seems different then most blogs and I’m looking for something completely
unique. P.S Apologies for being off-topic but I had
to ask!
Saved as a favorite, I really like your blog!
This is really fascinating, You are an overly skilled
blogger. I have joined your feed and stay up for in quest of more of your wonderful post.
Also, I’ve shared your site in my social networks
What’s up, the whole thing is going perfectly
here and ofcourse every one is sharing data, that’s really fine, keep up writing.
Fastidious answers in return of this query with solid arguments and telling all about that.
Hi there to every , because I am genuinely eager of reading this blog’s post to be updated on a regular
basis. It carries pleasant information.
Fantastic beat ! I wish to apprentice while you amend
your site, how could i subscribe for a blog web site?
The account helped me a acceptable deal. I had been tiny bit acquainted
of this your broadcast provided bright clear concept
My brother suggested I might like this blog.
He was entirely right. This post truly made my day.
You cann’t imagine just how much time I had spent
for this information! Thanks!
Oh my goodness! Awesome article dude! Many thanks, However I
am encountering troubles with your RSS. I don’t understand why I cannot subscribe
to it. Is there anybody else having identical RSS issues?
Anybody who knows the solution can you kindly respond?
Thanks!!
You’ve made some decent points there. I looked
on the net for more information about the issue
and found most people will go along with your views on this web site.
I do believe all of the concepts you have offered for your post.
They’re really convincing and will definitely work.
Still, the posts are too short for newbies. May just you please extend
them a bit from subsequent time? Thank you for the post.
I believe that is among the most important info for me.
And i’m glad studying your article. But wanna observation on some common things, The website style is great,
the articles is in reality nice : D. Excellent process, cheers
whoah this weblog is magnificent i love studying you posts.
Keep up the good work! You recognize, a lot off people are hunting round for this info, you can aid them greatly.
Betting website การพนันสด
I do consider all the concepts you’ve introduced on your post.
They are very convincing and will definitely work.
Nonetheless, the posts are too quick for novices.
May just you please lengthen them a little from subsequent time?
Thanks for the post.
How to get your PMP certification?
You need to fulfil the PMP Certification requirements.
Review the PMP exam objectives: review the PMP Examination Content Outline
(ECO) to make sure you know what is covered in the exam.
You will need to take a training course to obtain your 35 hours of contact hour.
Practice for the exam: Practice, Practice, Practice, after you have
studied for the exam, review, and answer as many practice exams as you can. Check the free PMP
Practice Exams , and the Premium Practice exams
Submit your application.
Take the test: Once your application is approved, you will
be given information on payment and scheduling options.
Wonderful article! This is the kind of information that are meant
to be shared across the internet. Disgrace on the seek engines for no
longer positioning this publish higher! Come on over and visit my website .
Thank you =)
Also visit my web site: زيادة متابعين تلجرام
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point.
You obviously know what youre talking about, why throw away your intelligence on just posting
videos to your blog when you could be giving us something informative to read?
Many thanks extremely valuable. Will share website with my pals.
https://www.uxux.pl
I am regular visitor, how are you everybody? This
piece of writing posted at this site is genuinely good.
I love the content on your web sites. Thanks
for your time!
https://www.paradis.biz.pl
Really want to mention I am just glad I stumbled onto your website!
https://www.lokalnieiglobalnie.pl
I appreciate reading through your web sites.
Appreciate it!
https://www.yellowdiving.pl
Hi there are using WordPress for your blog platform? I’m new to the blog world but
I’m trying to get started and set up my own. Do you need any coding expertise
to make your own blog? Any help would be really appreciated!
Thanks for sharing your info. I truly appreciate your efforts and I will be waiting
for your next write ups thank you once again.
Pretty nice post. I just stumbled upon your weblog
and wished to say that I’ve truly enjoyed browsing your blog posts.
In any case I will be subscribing to your rss feed and I hope you write again soon!
Can I just say what a relief to uncover a person that really knows what they’re discussing on the internet.
You actually understand how to bring an issue to light and
make it important. A lot more people need to check this out and understand this side of
the story. I was surprised that you’re not more popular since you surely have
the gift.
This is a topic that is near to my heart… Cheers!
Exactly where are your contact details though?
Excellent post. I used to be checking constantly
this blog and I’m impressed! Very helpful information specifically the remaining section 🙂 I maintain such info
a lot. I was looking for this particular information for a very long time.
Thanks and best of luck.
I feel this is one of the most important information for me.
And i’m happy studying your article. However should commentary on some normal things,
The web site style is perfect, the articles is truly great :
D. Good job, cheers
Thanks regarding furnishing this kind of good subject matter.
https://www.kotkratkowy.pl
One more thing. I believe that there are many travel insurance web sites of reliable companies that let you enter your trip details and obtain you the insurance quotes. You can also purchase the particular international travel insurance policy on the internet by using your credit card. Everything you should do should be to enter the travel information and you can begin to see the plans side-by-side. Merely find the program that suits your financial allowance and needs then use your bank credit card to buy it. Travel insurance on the web is a good way to check for a reputable company pertaining to international travel cover. Thanks for expressing your ideas.
Hi there everyone, it’s my first pay a quick visit at this site, and piece of writing is
really fruitful in favor of me, keep up posting such articles
or reviews.
Hey there! I just wanted to ask if you ever have any
issues with hackers? My last blog (wordpress) was hacked
and I ended up losing many months of hard work due to no data backup.
Do you have any solutions to prevent hackers?
My website: ASAP Cash Home Buyers
If you want to obtain a great deal from this post then you have to apply such methods
to your won weblog.
I was suggested this blog by my cousin. I am
not sure whether this post is written by him as nobody else know
such detailed about my trouble. You are wonderful!
Thanks!
Hello, of course this article is in fact fastidious and I have learned lot of
things from it concerning blogging. thanks.
I was wondering if you ever thought of changing the structure of your website?
Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so people could connect with it better.
Youve got an awful lot of text for only having 1 or 2 images.
Maybe you could space it out better?
Hi, just wanted to tell you, I enjoyed this blog post.
It was practical. Keep on posting!
It’s fantastic that you are getting ideas from this article
as well as from our argument made at this place.
Ei lá ! Isso é meio off-topic, mas ρгeciso de alguns consеlһ᧐s
de um blog estabeleϲido. É muito difícil pаra definir o seu próprio blog?
Eu não sou muito técnico, mas pode reѕolver as coisas muito rápida.
Estou pensando em fazеndo meu próprіo, mas eu não sei onde começaг .
Tem algum pontos ou sugestões? Obrigado
Hello! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly?
My website looks weird when viewing from my iphone.
I’m trying to find a theme or plugin that might be able to resolve this
issue. If you have any recommendations, please share.
With thanks!
Pretty! This was an incredibly wonderful article.
Thanks for supplying this info.
Wе stumbled оver һere different web pаge and thought I shoulⅾ check things oսt.
I ⅼike what I seе so noѡ і am following you.
Ꮮook forward to looқing into youг web ρage repeatedly.
I every time used to study article in news papers
but now as I am a user of net therefore from now I am using net for
articles, thanks to web.
در این مقاله قصد داریم به معرفی تعدادی از بهترین های کلاس فن بیان مشهد
بپردازیم. تا انتها همراه ما باشید.
امروزه در جهت برقراری ارتباط باید بتوانیم
مفهوم را به فرد مقابل به
خوبی و بدون هیچ ابهامی منتقل کنیم
و برای اینکه این کار انجام گردد نیاز است با فن بیان آشنایی خوبی داشته باشید، زیرا با رعایت این نکته قطعا سخنان ما تاثیرگذارتر و کاملتر خواهند بود.
فن بیان یعنی به کار بردن کلمات درست در جای درست!
یعنی طوری صحبت کنیم که
از الفاظ به کار برده ما همان چیزی که مدنظر ماست فهمیده
شود، نه کمتر و نه بیشتر.
وقتی ما توانستیم منظورمان را به مخاطبمان، همان
طور که در ذهنمان هست منتقل کنیم و طرف مقابلمان هم به درستی متوجه قضیه شود، گام بلندی در جهت ارتباط موثر خودمان برداشتیم و بدون شک مهارت خوبی در سخن گفتن داریم.
حالا هرچقدر بهتر و مسلط تر بتوانیم صحبت کنیم
و در زمان ها و مکان های مختلف که شاید فشارهای
روحی و ذهنی خاصی هم روی ما می باشد با دیگران
ارتباط درست تر برقرار کنیم، به همان اندازه مهارت در فن بیانمان داریم.
پس فن بیان یعنی توانایی صحبت کردن در هر زمان ، مکان و هر شرایطی متناسب با مخاطبمان…
فن بیان چیست؟
فن بیان یکی از مهمترین مهارت های
ارتباطی انسان امروز است که در مسیر پیشرفت و ترقی او تاثیر
به سزایی دارد و به معنای توان سخنگفتن (در هر شرایط و زمان) است.
زمانی که صحبت از فن بیان به میان میآید، جدا از این که شما چه کسی هستید؟ چه
کاری دارید؟ با چه کسی صحبت
میکنید؟ فقط کافیست که از زبان خود استفاده کنید، شما نیاز
به فن بیان دارید. اگر میخواهید با دوستان خود ارتباط خوبی برقرار کنید، روابط عمومی خوبی
داشته باشید، منظور خود را به خوبی به مخاطبانتان منتقل کنید و
همچنین کاری کنید که بقیه از همنشینی و
صحبت با شما لذت ببرند باید
«فن بیان» خوبی داشتهباشید.
به طور کلی فن بیان یعنی این که بتوانیم مقصود و مفهوم سخن خود را بدون هیچ کمی
و کاستی به فرد شنونده منتقل نماییم و هرچه فن بیان
ما بهتر باشد و اصول آن را بدانیم قطعا مخاطب تحت تاثیر حرفهای ما
قرار گرفته و شنونده خوبی برای صحبت هایمان است.
قطعا سخنان یکنواخت و موضوعات تکراری برای مخاطب لذتبخش نخواهد بود.
برای کلاس فن بیان نیاز به راهنمایی دارید؟ اطلاعات خود را از طریق دکمه نارنجی رنگ پایین صفحه ثبت کنید.
با شما تماس میگیریم.
education jobs pittsburgh and education network and health 1st center and education quality by state and mag
07 side effects and health services.
I am truly glad to read this blog posts which carries tons of valuable data, thanks for providing such data.
What’s up to all, it’s actually a fastidious for me
to pay a visit this web site, it consists of priceless Information.
Unquestionably believe that which you stated. Your favorite reason seemed
to be on the internet the easiest thing to be aware
of. I say to you, I definitely get annoyed while people consider worries that they just don’t know about.
You managed to hit the nail upon the top as well as defined out the whole thing without having side
effect , people could take a signal. Will probably be back to get more.
Thanks
Very energetic blog, I loved that bit. Will there be a
part 2?
I’ll immediately grasp your rss feed as I can’t in finding your
e-mail subscription hyperlink or newsletter
service. Do you’ve any? Please let me realize in order that I may just subscribe.
Thanks.
Hello there, You’ve done a great job. I’ll certainly digg it and personally recommend to my friends.
I’m sure they’ll be benefited from this site.
I am not positive where you are getting your information, but good topic.
I must spend some time studying more or understanding more.
Thanks for fantastic information I was on the lookout for this info for my
mission.
Greetings from Idaho! I’m bored to death at work so I
decided to browse your site on my iphone during lunch break.
I love the information you present here and can’t wait
to take a look when I get home. I’m shocked at how quick your blog loaded on my mobile ..
I’m not even using WIFI, just 3G .. Anyhow, great site!
Wonderful blog! I found it while searching on Yahoo News.
Do you have any suggestions on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get
there! Thanks
Hello there, just became alert to your blog through Google, and
found that it’s really informative. I am going to watch out for brussels.
I will appreciate if you continue this in future.
Numerous people will be benefited from your writing.
Cheers!
Thank you for the good writeup. It actually used to be a leisure account it.
Glance advanced to more brought agreeable from
you! By the way, how can we be in contact?
I’m really enjoying the design and layout of your blog. It’s a very easy on the
eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a designer to create your theme?
Superb work!
my webpage NESARA IS COMING
นมืออาชีพที่รออัพเดทแล้วก็ปรับปรุงเพื่อความสบายสบายของท่านลูกค้าตลอดเวลา
พวกเราก็เลยได้ทำjoker ฝากอย่างต่ำ 1
บาท มาเพื่อท่านลูกค้าโดยยิ่งไปกว่านั้นระบบก็พร้อมเพิ่มเงินให้กับสมาชิกทุกท่าน ทำรายการผ่านระบบออโต้บนเว็บ ทางเข้า
pg slot auto walletรวดเร็วข้างในไม่เกิน 30 วินาที เข้าเล่นเกมได้เลย เว็บไซต์สล็อตไม่ผ่านเอเย่นต์เปิดบริการด้วยตนเอง ไม่ต้องคอยอนุมัติอะไรก็แล้วแต่เลย
เว้นแต่สล็อตเว็บไซต์ใหญ่pgจะเป็นเกมที่ทำเงินแล้ว
พวกเรายังจัดแจงคณะทำงานมืออาชีพ คนที่ชำนาญด้านเกมสล็อตออนไลน์โดยเฉพาะให้บริการรวมทั้งคำแนะนำแก่สมาชิกทุกท่านตลอดวัน พร้อมดาวน์โหลดslotxo
auto จบครบที่เดียวให้บริการดาวน์โหลดslotxo auto เวอร์ชั่นล่าสุดอย่างสบาย
ทางเราได้มีการเตรียมเกมพนันออนไลน์ให้ท่านเลือกเล่นมากกว่า 500 เกมที่ทุกคนสามารถเลือกและก็เลือกทำเงินได้มากมาย การเล่นเกมออนไลน์ที่คุณพอใจได้ทุกที่ทุกเวลาไม่เคยง่ายอย่างนี้มาก่อนด้วยเว็บบนโทรศัพท์มือถือรวมทั้งแอปพลิเคชันที่รวดเร็วทันใจ สมัครสล็อตโจ๊กเกอร์เว็บตรงได้วันแล้ววันเล่าแบบฟรีๆ
I am genuinely happy to glance at this web site posts which
consists of tons of helpful information, thanks for
providing these data.
Every weekend i used to go to see this web site, because i want enjoyment,
as this this website conations truly nice funny data too.
Magnificent beat ! I would like to apprentice even as you amend your web site, how can i subscribe for a blog
site? The account helped me a acceptable deal.
I have been a little bit acquainted of this your broadcast provided
bright clear concept
After I originally commented I seem to have clicked the -Notify me when new comments are added- checkbox
and now each time a comment is added I receive 4 emails with the
exact same comment. Is there a means you are able to
remove me from that service? Thanks a lot!
Feel free to surf to my page 솔카지노 쿠폰
It’s going to be end of mine day, but before end I am reading this fantastic post
to increase my know-how.
thanks lots this amazing site is definitely formal along with
everyday
Hey, I think your site might be having browser compatibility issues.
When I look at your blog in Firefox, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up! Other
then that, amazing blog!
you’re in point of fact a excellent webmaster. The web site loading velocity is incredible.
It seems that you are doing any distinctive trick.
Furthermore, The contents are masterpiece. you’ve performed a magnificent process
on this topic!
สล็อตเว็บตรง สล็อต PG ไม่ผ่านเอเย่นต์
สมัครสล็อตpg ทดลองเล่นได้แล้วที่นี่ PGTHAI.CLUB
สมัคร สล็อต pg แตกง่าย
รวมสล็อตpg
Greetings! Very helpful advice in this particular article!
It is the little changes that will make the most important changes.
Many thanks for sharing!
Aw, this was an extremely nice post. Finding the time and actual effort to produce a great article… but what can I say… I hesitate a lot and
don’t seem to get nearly anything done.
Hi i am kavin, its my first occasion to
commenting anyplace, when i read this post i thought i could
also create comment due to this good paragraph.
Good day! Would you mind if I share your blog with my facebook group?
There’s a lot of people that I think would really
enjoy your content. Please let me know. Cheers
I always emailed this weblog post page to
all my contacts, since if like to read it then my contacts will
too.
Wow, incredible weblog layout! How long have you been blogging for?
you make running a blog glance easy. The whole glance of your site
is great, as well as the content!
I’m not sure exactly why but this web site is loading incredibly slow for
me. Is anyone else having this issue or is it a problem on my end?
I’ll check back later and see if the problem
still exists.
Your way of telling all in this article is actually good, all be able to effortlessly know it,
Thanks a lot.
Hurrah, that’s what I was searching for, what a stuff!
existing here at this webpage, thanks admin of this web site.
Your method of describing all in this post is actually pleasant, every one can effortlessly be aware of
it, Thanks a lot.
Appreciating the hard work you put into your site and in depth information you
present. It’s good to come across a blog every once
in a while that isn’t the same old rehashed information. Fantastic read!
I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
Hi there, of course this post is truly fastidious and
I have learned lot of things from it on the topic of blogging.
thanks.
It’s remarkable to pay a visit this web site and reading the views of all colleagues on the topic of this article,
while I am also eager of getting experience.
My partner and I absolutely love your blog and find a lot
of your post’s to be exactly I’m looking for. can you
offer guest writers to write content available for you?
I wouldn’t mind writing a post or elaborating on most of the subjects you write concerning here.
Again, awesome blog!
What’s up to every one, it’s actually a nice for me to pay
a visit this web site, it contains helpful Information.
Hi Dear, are you genuinely visiting this web page daily, if so then you will definitely obtain pleasant experience.
I loved as much as you’ll receive carried out right here.
The sketch is tasteful, your authored subject matter stylish.
nonetheless, you command get bought an nervousness over that
you wish be delivering the following. unwell unquestionably come further formerly again as exactly the same nearly very often inside case you shield this hike.
Magnificent goods from you, man. I have understand your stuff previous to and
you’re just too magnificent. I really like what you have acquired here, really like what you’re
stating and the way in which you say it. You make it entertaining
and you still take care of to keep it smart. I can not wait to read far more from you.
This is really a terrific site.
It’s appropriate time to make a few plans for the
long run and it’s time to be happy. I’ve learn this publish and if I may just
I want to counsel you some interesting things or advice.
Perhaps you can write subsequent articles regarding this article.
I want to learn more things approximately it!
Great beat ! I wish to apprentice while you amend your site, how could i subscribe for a blog website?
The account aided me a acceptable deal. I had been tiny bit acquainted of this your broadcast provided
bright clear idea
great points altogether, you just gained a brand new reader.
What would you suggest about your publish that you made
a few days ago? Any certain?
My brother recommended I might like this website.
He was totally right. This publish actually made my day.
You cann’t consider just how so much time I had spent for this info!
Thank you!
Hi there would you mind sharing which blog platform you’re using?
I’m looking to start my own blog in the near future but I’m having a difficult time making a decision between BlogEngine/Wordpress/B2evolution and
Drupal. The reason I ask is because your layout seems
different then most blogs and I’m looking for something completely unique.
P.S My apologies for getting off-topic but I had to ask!
Thanks for the auspicious writeup. It in reality was a amusement account it.
Look advanced to far added agreeable from you!
However, how could we keep up a correspondence?
Hi there I am so excited I found your site, I really found you by mistake,
while I was looking on Google for something else, Anyways I am here now and would just like
to say thank you for a marvelous post and a all round thrilling
blog (I also love the theme/design), I don’t have time
to read through it all at the moment but I have saved it
and also added in your RSS feeds, so when I have time I will be back to read more,
Please do keep up the excellent b.
With havin so much content do you ever run into any issues of
plagorism or copyright violation? My blog has a lot of unique content I’ve either written myself or outsourced
but it appears a lot of it is popping it up all over the web without my permission. Do you know
any ways to help protect against content from being
ripped off? I’d definitely appreciate it.
We are a group of volunteers and opening a new scheme
in our community. Your web site offered
us with valuable info to work on. You’ve done an impressive job and our
entire community will be grateful to you.
Сохранил в избранное! Я люблю ваш вебсайт!
Peculiar article, just what I needed.
This info is worth everyone’s attention. How can I
find out more?
Heya fantastic blog! Does running a blog such as this take a large amount of work?
I’ve absolutely no knowledge of coding but I was hoping to start my own blog in the near future.
Anyhow, if you have any suggestions or techniques for new blog owners please share.
I understand this is off subject nevertheless I just had to ask.
Thank you!
I do agree with all of the ideas you’ve introduced to your post.
They’re really convincing and will definitely work.
Still, the posts are too short for beginners. Could you please
prolong them a little from subsequent time? Thank you for the post.
Fantastic beat ! I would like to apprentice while you amend
your website, how can i subscribe for a blog site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided
bright clear idea
My spouse and I absolutely love your blog and find most of your post’s to be
precisely what I’m looking for. Do you offer guest writers to write content available for you?
I wouldn’t mind creating a post or elaborating on a few of the subjects you
write in relation to here. Again, awesome site!
Hi to every body, it’s my first go to see of
this webpage; this blog contains remarkable and actually fine stuff for readers.
I am actually glad to read this weblog posts which carries tons
of helpful facts, thanks for providing these statistics.
whoah this blog is excellent i really like reading your articles.
Stay up the good work! You already know, many individuals are hunting around for this info, you could help them greatly.
It’s truly a nice and useful piece of info.
I am happy that you shared this useful information with us.
Please stay us up to date like this. Thank you for
sharing.
Hi, the whole thing is going perfectly here and ofcourse every one is sharing information, that’s in fact excellent, keep up writing.
We absolutely love your blog and find most of your post’s to be exactly what I’m looking for.
can you offer guest writers to write content available for you?
I wouldn’t mind producing a post or elaborating on most of the subjects you write about here.
Again, awesome site!
Does your site have a contact page? I’m having a
tough time locating it but, I’d like to shoot you an email.
I’ve got some ideas for your blog you might be interested in hearing.
Either way, great site and I look forward to seeing it expand over
time.
Hi, I do believe this is a great web site. I stumbledupon it
😉 I am going to come back once again since I saved as a favorite it.
Money and freedom is the best way to change, may you
be rich and continue to guide other people.
Hi terrific website! Does running a blog such as this take a massive amount work?
I’ve virtually no understanding of coding but I was hoping to start my
own blog in the near future. Anyway, should you have any
recommendations or techniques for new blog owners please share.
I know this is off topic but I just had to ask. Thanks!
تو همین اتاق یکی هر شب تو جنگه
با خودش با دلی که واسه تو تنگه مگه از یاد من میره اون همه حرفای قشنگت …
آخه بی معرف بگو کی مث من از دیدنت ذوق میکرد اتاقو پر از گل
رز میکرد تا میگفتی که میرم بغض میکرد این
خیابونا هنوز بعد تو بوی عطرتو میده دورت بگردم کجا دنبالت
بگردم تو خودت رفتی من گمت نکردم این خیابونا هنوز بعد تو بوی عطرتو میده دورت بگردم کجا دنبالت بگردم تو
خودت رفتی من گمت نکردم جفت چشام قفله رو در
تا وا شه تو بیای به دروغم که شده بگی منو میخوای کاش بشه مثلا امشب که بارون میزنه بیای …
برگرد بیا پیشم بشین حرف منم گوش کن خواست به من باشه گوشیتو خاموش کن این همه
خوبی که کردم چه زود فراموش شد … این خیابونا هنوز بعد تو بوی عطرتو میده دورت بگردم کجا دنبالت بگردم تو خودت رفتی من گمت نکردم این خیابونا هنوز بعد
تو بوی عطرتو میده دورت بگردم کجا دنبالت بگردم تو خودت رفتی من گمت نکردم
Keep this going please, great job!
My web site: CáCh LàM ThạCh DừA
Its like you read my mind! You appear to know so much about this,
like you wrote the book in it or something. I think that you could do with some pics to drive
the message home a bit, but instead of that, this is great
blog. An excellent read. I will certainly be back.
Car Simulator 2 Apk hali sitemizde mevcut olup siz
değerli takipçilerimizin hizmetine sunmaktayız.
Car Simulator 2 Apk kurulumu oldukça basittir.
Car Simulator 2 Apk ile tüm erişemler açılacaktır.
Dosyayı indirdiğinizde USB aracılığıyla telefonunuza atabilir ve
APK kurulumunu gerçekleştirebilirsiniz.
Hi there! This is my first visit to your blog!
We are a group of volunteers and starting a new project in a community
in the same niche. Your blog provided us valuable information to work on. You have done
a outstanding job!
Thank you a bunch for sharing this with all people you really realize what you
are speaking approximately! Bookmarked. Kindly additionally seek advice from my web site =).
We could have a hyperlink trade arrangement among us
I think the admin of this website is actually working hard in support
of his web site, as here every stuff is quality based stuff.
I every time spent my half an hour to read this blog’s articles
or reviews everyday along with a mug of coffee.
I appreciate the details on your websites. Thnx.
https://www.100pomyslownabiznes.eu
I think the admin of this web page is in fact working hard in support of his web site,
since here every stuff is quality based material.
Passion the site– very individual pleasant and whole lots
to see!
https://www.tlt24.pl
Good post. I will be going through a few of these issues as well..
Look at my webpage: keyword research tamil
Hey! I could have sworn I’ve been to this website before but after browsing through some of the post I
realized it’s new to me. Nonetheless, I’m definitely
glad I found it and I’ll be bookmarking and checking back often!
Hi just wanted to give you a brief heads up and let you know a few of the pictures aren’t loading properly.
I’m not sure why but I think its a linking issue.
I’ve tried it in two different browsers and both show the same results.
Hi my loved one! I want to say that this article is amazing, nice written and come with
almost all important infos. I’d like to peer extra posts like this .
Hi there, i read your blog occasionally and
i own a similar one and i was just wondering if you get a lot of
spam comments? If so how do you prevent it, any plugin or anything you
can advise? I get so much lately it’s driving me crazy so any support is very much
appreciated.
Hello there! I could have sworn I’ve been to this site before but after looking
at some of the posts I realized it’s new to me. Anyways,
I’m definitely delighted I stumbled upon it and I’ll be bookmarking it and checking back frequently!
Maintain the amazing work !! Lovin’ it!
https://www.my-iq.pl
Wow because this is very helpful work! Congrats and keep
it up.
https://www.mocwiedzy.com
Hello, yes this article is in fact fastidious and
I have learned lot of things from it concerning blogging.
thanks.
If some one needs expert view on the topic of blogging
afterward i propose him/her to go to see this website, Keep up the good work.
Feel free to surf to my site :: tamil keywords
I must thank you for the efforts you have put in penning this website.
I really hope to view the same high-grade content from you in the future as well.
In truth, your creative writing abilities has inspired me to get my own website now 😉
I’m really loving the theme/design of your weblog.
Do you ever run into any web browser compatibility issues?
A handful of my blog audience have complained about my site not operating correctly in Explorer but looks
great in Safari. Do you have any recommendations
to help fix this issue?
great put up, very informative. I wonder why the other specialists of this sector don’t realize this. You should continue your writing. I’m sure, you have a huge readers’ base already!
Thanks meant for offering these great knowledge.
https://www.yellowsubmarine.pl
We will teach you how to earn $ 7000 per hour.
Why? We will profit from your profit.http://binaryoptionsreview.eu/pocket-option-review/
It is perfect time to make a few plans for the future and it is time to
be happy. I have learn this publish and if I could I want to suggest you
some interesting issues or suggestions. Maybe you can write next articles relating to this article.
I want to learn more things about it!
I am actually happy to glance at this website posts which
carries tons of valuable facts, thanks for providing these
kinds of information.
Hi my loved one! I wish to say that this article is awesome, great written and include approximately
all significant infos. I’d like to see extra posts like this .
Wow, wonderful blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your website is fantastic, let alone the content!
Way cool! Some very valid points! I appreciate you penning this post plus the rest of the website is really good.
Do you have a spam problem on this blog; I also am a blogger, and I was wondering
your situation; many of us have created some nice procedures and we are looking to trade methods with other
folks, why not shoot me an email if interested.
Thank you for another wonderful post. Where else may anybody get that type of info
in such a perfect method of writing? I’ve a presentation next week, and I am on the search for such info.
Thanks very nice blog!
Thank you for the auspicious writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you! By the way, how could we communicate?
I was wondering if you ever thought of changing the
page layout of your blog? Its very well written; I love
what youve got to say. But maybe you could a little more in the way of content
so people could connect with it better. Youve got an awful
lot of text for only having 1 or 2 pictures.
Maybe you could space it out better?
We are a bunch of volunteers and starting a new scheme in our community.
Your site provided us with useful info to work on. You have done a formidable job and our entire
neighborhood will likely be thankful to you.
Of course, what a splendid blog and informative posts, I surely will bookmark your website.All the Best!
I think this is among the most vital information for me. And i’m glad reading your article. But wanna remark on few general things, The site style is great, the articles is really nice : D. Good job, cheers
Hello, i feel that i saw you visited my weblog so i came to return the choose?.I am trying to in finding issues to
enhance my website!I guess its good enough to use some of your
concepts!!
Spot on with this write-up, I honestly believe this web site needs far more attention. I’ll probably be back again to read through more, thanks for the advice!
Have you ever thought about including a little bit more than just your
articles? I mean, what you say is important and everything.
But imagine if you added some great visuals or videos to give your posts more, “pop”!
Your content is excellent but with pics and clips, this
blog could definitely be one of the best in its niche.
Very good blog!
Great blog here! Also your site loads up fast! What web host are you using?
Can I get your affiliate link to your host? I wish my website loaded up as quickly as yours lol
ما دراین مقاله سعی داریم پس از یک مقدمه
بسیار مختصر به معرفی بهترین کلاس فرانسه تهران بپردازیم .
زبان فرانسه
زبان فرانسوی ، فرانسه français ،
احتمالاً مهمترین زبان عاشقانه در جهان
است.
تاریخچه زبان فرانسه
اولین سندی که ظاهراً به زبان فرانسه نوشته
شده احتمالاً مربوط به سال 842 است. این سند با نام سوگندهای
استراسبورگ شناخته می شود
، این یک نسخه عاشقانه از سوگندهایی است که
توسط دو نوه شارلومن قسم خورده است.
این مطلب را هم از دست ندهید:
معرفی بهترین کلاس زبان انگلیسی شرق تهران
معرفی بهترین کلاس زبان
انگلیسی غرب تهران
کلاس زبان فرانسه تهران
معرفی بهترین آموزشگاه های زبان فرانسه در تهران
1. آموزشگاه زبان فرانسه پردیسان
این آموزشگاه به دلیل سابقه 15 ساله ای که دارد یکی از بهترین آموزشگاه
های زبان فرانسه در تهران است که
آموزش ها به صورت ترمیک و یا
فشرده می باشد که هر فردی با توجه
به توانایی خود می تواند در این کلاس ها
شرکت کند.
مشاهده صفحه آموزشگاه
معرفی بهترین کلاس فرانسه در تهران
2. آموزشگاه زبان فرانسه زبان نگار
یکی از فعال ترین آموزشگاه ها در تهران آموزشگاه زبان
فرانسه زبان نگار می باشد که اساتید نخبه در این آموزشگاه تدریس می کنند و روزانه تعداد زیادی
از علاقه مندان در کلاس های زبان فرانسه
ثبت نام می کنند. این آموزشگاه با بیش
از 20 سال سابقه در زمینه تدریس انواع
زبان های مختلف، توانسته است بهترین تکنیک های روز را به کار گیرد.
مشاهده صفحه آموزشگاه
معرفی بهترین کلاس فرانسه در تهران
3. آموزشگاه زبان فرانسه قطب راوندی
این آموزشگاه در تهران 4 شعبه دارد
به همین دلیل دسترسی زبان آموزان به این آموزشگاه آسان تر است و
به دلیل اینکه اساتید مجربی در این آموزشگاه
تدریس می کنند این فضای آموزشی به یکی از
پرطرفدارترین آموزشگاه ها تبدیل شده است.
همچنین کلاس های آنلاین نیز برگزار می کنند که استقبال زیادی نیز می شود.
مشاهده صفحه آموزشگاه
معرفی بهترین کلاس فرانسه در تهران
4. آموزشگاه زبان فرانسه ایران
کمبریج
در این آموزشگاه به دلیل اینکه اساتید بومی فرانسوی تدریس می کنند جز بهترین
آموزشگاه های زبان فرانسه در
تهران شده است. بعد از اتمام دوره ها، مدارک کاملا معتبر برای زبان آموزان ارائه می دهد.
همچنین این آموزشگاه علاوه بر زبان فرانسه، زبان های مختلف دیگری را نیز به زبان
آموزان آموزش می دهد.
مشاهده صفحه آموزشگاه
بخشهای کشوری
مساحت کشور فرانسه برابر با ۶۴۳ هزار کیلومتر مربع بوده و گستردهترین کشور اروپای غربی است (یک سوم گستره ایران) و منطقه دریایی گستردهای را در
اختیار دارد.
سطح فرانسه شبیه به یک ششضلعی است، که سه ضلع
آن به آب منتهی میشوند. (دریای مدیترانه و اقیانوس اطلس)
بر اساس واپسین تقسیمات کشوری فرانسه به ۲۲ ناحیه بخش و
از ۹۶ شهرستان (یا دپارتمان) تشکیل شده که زیر دید
دولت مرکزی اداره میشوند و زیر
نظارت شورای انتخابی محلی کار میکنند.
همچنین هر ناحیه به کانتونها و بخشهایی بخش
شده و هر بخش از شورای شهر و شهردار خاص خود برخوردار است.
علاوه بر خاک اصلی این کشور در
اروپا به شرح فوق، سرزمینهای دیگری بیشتر به صورت جزیره نیز تحت حاکمیت و
سلطهٔ حکومت فرانسه قرار دارند.
از این جمله میتوان به کالِدونیای جدید و والیس
و فوتونا در شرق استرالیا، جزایر سنت مارتین در محدوده میان
دو آمریکای شمالی و جنوبی، و همچنین جزایری
مانند مایوت در جنوب آفریقا اشاره
کرد.
از بزرگترینِ این مناطق میتوان
به گویانِ فرانسه یا گویان (Guiana) با مساحت حدودی ۸۳ هزار کیلومتر مربع اشاره کرد که در همسایگی برزیل در
آمریکای جنوبی قرار دارد.
My partner and I absolutely lovve your blog and find many of your
post’s to be just whawt I’m looking for. can you ofgfer guest writers to write content available for you?
I wouldn’t mind producing a post or elaboorating
on many of the subjects you write concerning
here. Again, awesome web log!
Hello to all, the contents present at this web site are truly amazing for people experience, well, keep
up the nice work fellows.
Greetings! I know this is kinda off topic nevertheless I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest writing a
blog article or vice-versa? My site covers a lot of the same subjects as yours and I think we
could greatly benefit from each other. If you’re interested feel free to
send me an email. I look forward to hearing from you! Wonderful blog by the way!
Every weekend i used to pay a visit this site, because i want enjoyment, since this this website conations
truly fastidious funny information too.
در این مقاله قصد داریم به معرفی بهترین
کلاس زبان مشهد بپردازیم. یکی از دغدغه های مهم زبان آموزان یافتن یک کلاس زبان مناسب است.
در این مطلب قصد داریم چندتا از بهترین آموزشگاه های زبان مشهد
را معرفی کنیم. این آموزشگاه ها جزو معتبرترین مراکز آموزش
زبان مشهد محسوب می شوند.
موسسات زبان نامبرده شده دارای خدمات متنوعی در زمینه آموزش زبان های خارجی
می باشند که از جمله آنها میتوان به کلاس زبان انگلیسی در مشهد، کلاس زبان آلمانی، کلاس زبان فرانسه، کلاس زبان ترکی
استانبولی، کلاس زبان روسی، کلاس زبان اسپانیایی، کلاس زبان ایتالیایی، کلاس
زبان عربی و دیگر زبان های زنده دنیا
و نیز همچنین دورهای مختلف آزمون
های آمادگی زبان های خارجی چون کلاس های آموزش آیلتس IELTS، کلاس
های آموزشی تافل TOEFL، کلاس های آموزشی تخصصی ESP، کلاس های آموزشی پودفک و غیره که زبان
آموزان بدنبال شرکت در آنها میباشند.
نکته ای که در انتخاب بهترین
کلاس زبان اهمیت دارد، کیفیت خدمات ارائه شده توسط مجموعه است.
از کجا بفهمیم بهترین کلاس زبان مشهد کدام
است؟
برای انتخاب بهترین آموزشگاه های زبان مشهد چندین فاکتور اهمیت دارد.
دوره های طراحی شده
کیفیت کار اساتید
امکانات آموزشی
نحوه مدیریت و برخورد پرسنل
در دسترس بودن
باز خورد تجربی زبان آموزان
دقت کنید آموزشگاه زبانی را انتخاب
کنید که با توجه به اهداف شما قدم بردارد.
مهمترین کار شما درس خواندن است! فراموش نکنید که با درس نخواندن عملا هیچ آموزشگاه و لیستی
کمک رسان شما نخواهد بود.
بهترین کلاس زبان مشهد کجاست؟
اگر به دنبال یادگیری زبان دوم در مشهد هستید، در ادامه لیستی
از بهترین های کلاس زبان مشهد را برای شما آماده کردهایم.
آموزشگاه زبان راه پویندگان
Hi there, just became alert to your blog through Google, and found that
it is really informative. I am gonna watch out for brussels.
I’ll be grateful if you continue this in future. Numerous people will be benefited from your writing.
Cheers!
I could not resist commenting. Perfectly written!
I love your blog.. very nice colors & theme. Did you make this website yourself or
did you hire someone to do it for you? Plz answer back as I’m looking to create my own blog and would like to know where u got this from.
appreciate it
I am in fact happy to read this web site posts which contains plenty
of valuable data, thanks for providing these data. https://aboutphysicianjobs.com/author/rireh75718/
Hey! This post couldn’t be written any better! Reading this post reminds me of my good old
room mate! He always kept talking about this.
I will forward this write-up to him. Pretty sure he will have a good read.
Thanks for sharing!
Hmm is anyone else having problems with the images on this blog loading?
I’m trying to determine if its a problem on my end or if it’s
the blog. Any responses would be greatly appreciated.
This is my first time pay a quick visit at here and i am truly impressed to read all at one place.
Heya! I just wanted to ask if you ever have any trouble with hackers?
My last blog (wordpress) was hacked and I ended up losing a few months of hard work due to
no backup. Do you have any methods to stop hackers?
you are in point of fact a just right webmaster. The web site
loading pace is amazing. It kind of feels that you’re doing any
unique trick. In addition, The contents are masterwork.
you have performed a excellent process in this topic!
Actually no matter if someone doesn’t understand afterward its
up to other users that they will assist, so here it occurs.
Hmm is anyone else encountering problems with the images on this blog loading?
I’m trying to determine if its a problem on my end or if it’s the blog.
Any feed-back would be greatly appreciated.
Wonderful blog! I found it while surfing around on Yahoo News.
Do you have any suggestions on how to get listed in Yahoo
News? I’ve been trying for a while but I never seem
to get there! Thank you
Everything is very open with a clear explanation of the
issues. It was definitely informative. Your site is very useful.
Thanks for sharing!
What’s up mates, how is everything, and what you would like to say about this paragraph,
in my view its in fact remarkable for me.
Tienda Nº 1 en Chandal Barcelona
Encontrarás cada chandal del barça y ropa de entrenamiento de los clubs y selecciones nacionales para adultos y niños.
Do you have a spam problem on this website; I also am a
blogger, and I was wondering your situation; we have created some nice
procedures and we are looking to exchange solutions with other folks, please shoot me an email if interested.
My spouse and I stumbled over here coming from a different
web address and thought I might check things out.
I like what I see so now i’m following you. Look forward to checking out your web page yet again.
Pretty section of content. I just stumbled upon your weblog and in accession capital to claim that I acquire in fact enjoyed account your weblog posts.
Any way I’ll be subscribing on your feeds or even I fulfillment you get right of entry to
constantly rapidly.
I like the valuable info you provide in your articles.
I will bookmazrk yur blog and check again here regularly. I am quite
sure I’ll learn many new stuff right here! Good luck for the
next!
Incredible story there. What occurred after?
Good luck!
Pretty great post. I simply stumbled upon your
weblog and wished to mention that I’ve really enjoyed surfing around your weblog
posts. In any case I will be subscribing on your feed and
I hope you write once more soon!
I just couldn’t go away your website prior to suggesting that I really
loved the usual information a person supply for your visitors?
Is gonna be back incessantly to check out new posts
I used to be able to find good info from your articles.
Thanks for sharing your thoughts on Click here. Regards
I аm suгe tһis paragraph haѕ touched all tһe internet ᥙsers, its reaⅼly really fastidious article ᧐n building ᥙp new
website.
Excellent, what a blog it is! This web site provides useful facts to
us, keep it up.
It’s very trouble-free to find out any matter on net
as compared to textbooks, as I found this post at this web site.
hello there and thank you for your info – I’ve definitely picked up anything new from right here.
I did however expertise several technical points using this web site, as I experienced to reload the website many times previous to I could get it to load
properly. I had been wondering if your hosting is OK? Not that I am complaining, but slow loading
instances times will sometimes affect your placement in google and could damage
your quality score if ads and marketing with Adwords. Well I
am adding this RSS to my e-mail and could look out for much more of your respective intriguing content.
Ensure that you update this again soon.
You ought to take part in a contest for one of the highest quality websites on the internet.
I’m going to highly recommend this site!
Wow that was strange. I just wrote an incredibly long comment but
after I clicked submit my comment didn’t show up. Grrrr…
well I’m not writing all that over again. Anyways, just wanted to say great blog!
Thank you for the auspicious writeup. It in fact was a amusement
account it. Look advanced to more added agreeable from you!
However, how can we communicate?
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time a comment is added I get four emails with the same comment.
Is there any way you can remove people from that service?
Cheers!
What’s up, just wanted to say, I loved this article. It was
helpful. Keep on posting!
Admiring the dedication you put into your blog and in depth information you offer.
It’s awesome to come across a blog every once in a while that isn’t the same unwanted rehashed information. Fantastic
read! I’ve saved your site and I’m including your RSS feeds to
my Google account.
I love it when individuals get together and share views.
Great site, continue the good work!
Great beat ! I would like to apprentice even as you amend your web site, how could i subscribe for
a blog site? The account helped me a appropriate deal.
I have been a little bit acquainted of this your broadcast
offered brilliant transparent idea
I like looking through a post that can make people think.
Also, thank you for permitting me to comment!
You have got among the finest web sites.
http://aircharterjobs.com/author/sharitychristoforome/
As the admin of this website is working, no uncertainty very shortly it will be well-known, due to its quality contents.
If some one needs expert view regarding running a blog
after that i advise him/her to pay a quick visit this website,
Keep up the good work.
I know this website presents quality depending articles
or reviews and additional information, is there any other web site which gives these information in quality?
Hi i am kavin, its my first time to commenting anyplace,
when i read this piece of writing i thought i could also create comment due to this brilliant paragraph.
My partner and I absolutely love your blog and find nearly all of your post’s to be what precisely I’m looking for.
can you offer guest writers to write content for you?
I wouldn’t mind writing a post or elaborating on some
of the subjects you write with regards to here. Again, awesome weblog!
Link exchange is nothing else excеpt it iѕ simply placing tһe other person’ѕ website link ⲟn yoᥙr pɑgе at proper ρlace аnd otһеr
person ԝill aⅼso do ѕame for you.
Greate article. Keep posting such kind of info on your
blog. Im really impressed by your site.
Hello there, You’ve done an incredible job. I will definitely digg it and personally recommend to my friends.
I’m sure they will be benefited from this site.
Good day! Do you use Twitter? I’d like to follow you if that would be okay.
I’m undoubtedly enjoying your blog and look forward to new updates.
Hi there I am so thrilled I found your weblog, I really found you by accident, while I was researching on Yahoo for something else, Anyhow I am here now and would just like to say many thanks for a remarkable post and a all round entertaining blog (I also love the theme/design), I don’t have time to look over it all at the minute but I have bookmarked it and also included your RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the awesome work.
I have learned a number of important things via your post. I will also like to say that there will be a situation in which you will make application for a loan and do not need a co-signer such as a Government Student Support Loan. However, if you are getting financing through a common financier then you need to be prepared to have a co-signer ready to help you. The lenders are going to base their own decision on the few issues but the biggest will be your credit rating. There are some loan companies that will additionally look at your work history and make a decision based on this but in almost all cases it will depend on your rating.
Hi, after reading this amazing post i am also delighted to share my experience here with friends.
Do you have a spam issue on this blog; I also am a blogger, and I was wondering your situation; we have created some nice procedures
and we are looking to exchange techniques with other folks,
please shoot me an e-mail if interested.
This site certainly has all the information and facts
I wanted concerning this subject and didn’t know who to ask.
Eu ѕou realmente imprеssionado junto com seu eѕcrevendo talentos e também com o
layout para seu weblog. Iѕto é um pago assunto oս personalizar -se ?
Qualquer foгma ficaг acima o bom qualidade escrevendo, é raras ver um grande ƅlog como este hoje em dia …
Hi, i read your blog occasionally and i own a similar one and
i was just wondering if you get a lot of spam responses? If so
how do you reduce it, any plugin or anything you can suggest?
I get so much lately it’s driving me crazy so any assistance is very
much appreciated.
An impressive share! I’ve just forwarded this onto a
friend who has been conducting a little research on this.
And he in fact ordered me dinner due to the fact
that I discovered it for him… lol. So let me reword this….
Thank YOU for the meal!! But yeah, thanks for spending time to discuss this matter here on your site.
My relatives every time say that I am wasting my time here at web,
however I know I am getting knowledge all the time by
reading thes nice articles or reviews.
Hello, I think your site might be having browser compatibility issues.
When I look at your website in Safari, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up!
Other then that, wonderful blog!
It’s awesome to pay a quick visit this site and reading the views of all colleagues
concerning this post, while I am also keen of getting familiarity.
Fantastic blog! Do you have any suggestions for aspiring writers?
I’m hoping to start my own blog soon but I’m a little lost on everything.
Would you advise starting with a free platform like WordPress or go for a paid option?
There are so many options out there that I’m totally overwhelmed ..
Any recommendations? Thanks a lot!
Thank you for any other fantastic post. The place else could
anyone get that kind of information in such an ideal method
of writing? I’ve a presentation next week, and
I’m on the look for such information.
My brother suggested I might like this web site.
He was totally right. This post truly made
my day. You cann’t imagine simply how much time I had spent
for this information! Thanks!
Thank you, I have recently been looking for information approximately this topic for a
while and yours is the greatest I have came upon so far.
But, what about the conclusion? Are you positive concerning the supply?
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored subject matter
stylish. nonetheless, you command get bought an edginess over that you wish be
delivering the following. unwell unquestionably come more formerly again since exactly the same nearly very often inside case you shield this hike.
Very great post. I simply stumbled upon your blog and wished
to say that I’ve truly loved browsing your weblog posts.
After all I’ll be subscribing to your rss feed and I
am hoping you write again very soon! https://www.behance.net/joshuazastrow1
Hey there! This is kind of off topic but I need some
help from an established blog. Is it very hard to set up your own blog?
I’m not very techincal but I can figure things out pretty fast.
I’m thinking about making my own but I’m not sure where to begin. Do you have any points or suggestions?
Cheers
Great post.
Есть ли у вашего блога контактная страница?
У меня есть трудности и я бы хотел отправить вам
email. У меня есть некоторые предложения для вашего блога, которые
вам может быть интересно услышать.
В любом случае, интересный вебсайт, и я с
нетерпением жду, когда сайт будет улучшаться.
My spouse and I stumbled over here different website and thought
I might as well check things out. I like what I see so i am just following you.
Look forward to looking into your web page for a second time.
This is a great tip especially to those new to the blogosphere.
Simple but very precise information… Many thanks for sharing
this one. A must read article!
Hi are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to get
started and create my own. Do you require any coding knowledge
to make your own blog? Any help would be greatly appreciated!
It’s great that you are getting thoughts from this article as
well as from our dialogue made here.
Hello, I do believe your blog could possibly be having browser
compatibility issues. Whenever I take a look at your blog in Safari, it looks fine however, when opening in I.E., it has some overlapping issues.
I just wanted to give you a quick heads up! Apart from that,
wonderful website!
You actually make it seem really easy with your presentation however I to find
this matter to be really one thing which I
feel I would by no means understand. It sort of feels too complicated and very huge for me.
I am having a look forward to your next put up, I will try to get the cling of it!
Hello it’s me, I am also visiting this web page daily, this web site is truly
good and the visitors are really sharing pleasant thoughts. https://rpgmaker.net/users/joshi1100/
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION –
Benson Yerima < Loved it!
Hmm it looks like your site ate my first comment (it was extremely long) so
I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your
blog. I too am an aspiring blog writer but
I’m still new to the whole thing. Do you have any points for first-time
blog writers? I’d really appreciate it.
I am really pleased to glance at this weblog posts which consists of tons of valuable information, thanks for providing
such statistics.
You have very nice post and pictures, please have a look at our photo tours in the temples of Angkor
reneweuropegroup.eu
Howdy! I just wish to give you a huge thumbs up for your excellent information you have here
on this post. I will be returning to your web site for more
soon.
Aw, this was a really good post. Taking a few minutes and actual effort to create a top notch article… but what can I say…
I procrastinate a whole lot and never seem to get nearly anything done.
Do you have a spam issue on this website; I also am a blogger, and
I was curious about your situation; many of us have created some nice methods and we are looking to trade techniques with other folks, please shoot me an email
if interested.
Cryptocurrency robots will automatically exit the position for a revenue
as soon as the motion is complete. In terms of the exchange
itself, Huobi supports a variety of cryptocurrency tokens of all
sizes and styles. Countries, by the use of their central banks, and
international institutions hold dollars of their reserve arsenal to decrease exchange
fee threat and pay for investments. Casio has, however, added button guards and a new protective bezel —
necessary when your outdoors watch prices just a few hundred dollars.
This could make it easier to watch darker scenes in movies and Tv reveals.
Moreover, actual-time processing is achieved whereas recording movies as a result of optimizing the variety
of calculations for noise suppression. It’s advantageous for the occasional fast clip,
however the motion pictures produced are definitely more YouTube-
than Vimeo-high quality, if you catch our drift. It could
be practically unattainable to dislodge if you don’t have fingernails — but the USB cover is ok.
To date, regulators and states have finished extra to call out
alleged violations by stablecoin suppliers below current guidelines.
Sure, its comparatively excessive clock speed helps it
keep tempo in the single-thread Linpack (it even edges out the decidedly larger-end Droid RAZR), however its 4,319.45ms end in SunSpider is likely one of the worse runs we have seen in recent
memory, as was its 41.5fps average within the graphics test NenaMark.
games kharido
game kharido
gameskharido
gamekharido
games kharido top up
game kharido top up
games kharido free fire
game kharido
gameskharido
gamekharido
Hi there! This is my first comment here so I just wanted to give a quick shout out and say I really enjoy reading your articles.
Can you recommend any other blogs/websites/forums that cover the same topics?
Thanks a ton!
Thank you a lot for sharing this with all folks you actually recognize what you are speaking approximately!
Bookmarked. Please also talk over with my site =). We will have a link trade agreement among us
Hi, its fastidious piece of writing concerning media print, we all understand media is
a great source of information.
Hello mates, its impressive article concerning educationand entirely explained, keep
it up all the time.
You’re an extremely beneficial internet site; could not make it without ya!
https://dionneseslcyberlounge.com/author/sephirazurheideqg/
Great looking site. Assume you did a great deal of your very own coding.
https://www.sunlitcentrekenya.co.ke/author/reetahufnagelev/
Remarkable! Its genuinely remarkable piece of writing, I
have got much clear idea regarding from this piece of writing.
In that case, it is a superb bet your itemizing or the worth
is to blame. Its unprecedented characteristics and nominal value range has really made it probably the
most favourite hosting service suppliers of so many
clients. The regular deal of ThinkHost for its
clients is 100GB disk space with 1000GB bandwidth for as low value as
$7.95 per 30 days. In case you are searching for a
dependable internet hosting server, you had higher take a look at the ThinkHost review given below.
So, take assistance from expert Magento developer to convert PSD based files to
world class Magento theme. Now, allow us to take a look at quite a lot of the market-leaders of this massive number of skilled high-end cameras, those that inventive professionals are searching for and utilizing
for the very best-quality scans, with high resolution, vast picture density,
massive film format as their hallmark. However,
only small variety of dedicated conversion corporations can survive in extremely aggressive market.
As corporations transfer on-line to create, share and retailer information, cloud storage companies are vying for a significant share of the software services market that’s estimated to hit $116 billion this yr in accordance with a Gartner
report. Not only does this creator focus on pictures, you might also check out his newest web site on the way in which to convert
3GP to AVI with 3GP to AVI converter which additionally helps individuals find the perfect 3GP to AVI converter on the market.
You have got terrific info in this case.
http://facebush.co.za/author/selenejobyevo/
Many thanks! This is definitely an remarkable online site!
https://teachers.net/jobs/author/lornekiegervtr/
Sustain the great work and producing in the crowd!
http://www.jobsforearth.com/author/lyndsayxdkarsten/
Great article, totally what I wanted to find.
This is my first time visit at here and i am in fact impressed
to read everthing at one place.
Superb Web page, Stick to the fantastic job. Appreciate it.
https://rosedalejobs.org/author/atlantaraabgo/
Hello there, nice internet site you have at this time there.
http://www.empregosalagoas.com.br/author/salomedycheab/
This is the perfect blog for everyone who would like to find out about this topic.
You know so much its almost tough to argue with you (not
that I personally will need to…HaHa). You certainly put a fresh spin on a subject that’s been discussed for decades.
Wonderful stuff, just great!
Valuable info. Lucky me I found your website by accident, and
I’m shocked why this accident didn’t came about earlier! I bookmarked it.
Very good post! We will be linking to this particularly great content on our website.
Keep up the great writing.
Here is my blog post; خرید عطر اورجینال,
It’s really a cool and useful piece of information. I
am glad that you simply shared this helpful information with us.
Please stay us up to date like this. Thanks for sharing.
You have brought up a very superb details , appreciate it for the post.
Outstanding quest there. What occurred after?
Thanks!
Good response in return of this matter with real arguments and telling everything regarding that.
Does your website have a contact page? I’m having trouble locating it but,
I’d like to send you an email. I’ve got some suggestions for your blog you might be interested in hearing.
Either way, great website and I look forward to seeing
it expand over time.
This is very interesting, You’re a very skilled blogger. I’ve joined your rss feed and look forward to seeking more of
your excellent post. Also, I have shared your site in my social networks!
This is my first time pay a quick visit at here and i am
really happy to read everthing at single place.
Greetings! I know this is kind of off topic but I was wondering if you knew where
I could find a captcha plugin for my comment form? I’m using the same blog platform as yours and
I’m having trouble finding one? Thanks a lot!
Many thanks, this website is extremely valuable.
https://www.i-hire.ca/author/laurellavidaps/
Hi there! I’m at work browsing your blokg from my new iphone 4!
Just wanted to say I love reading through your blog and look
forward to all your posts! Keeep up the excellent work!
Nice blog! Is your theme custom made or did you download it from
somewhere? A design like yours with a few simple adjustements would really make my blog shine.
Please let me know where you got your theme. Appreciate
it
Right now it looks like Drupal is the preferred blogging platform
available right now. (from what I’ve read) Is that what you are using on your
blog?
Thanks, this website is extremely useful.
https://jobwebghana.com/author/gerladinastranderxhp/
Highly beneficial….look forwards to returning.
https://www.rapidjobs4u.com/author/shanaqwryle/
Hey just wanted to give you a quick heads up. The text in your
post seem to be running off the screen in Chrome. I’m not sure if this is a formatting issue
or something to do with internet browser compatibility
but I thought I’d post to let you know. The style and design look
great though! Hope you get the problem fixed soon. Cheers
پرواز کرد پرید از رو شونم یه نارنجی پوشی که لالایی واسش میخوندم خوش بهم گفت همیشه میمونه پیشم کاش
یه خواب باشه دارم دیوونه میشم شکستی دلمو
بگو دیگه چی میخوای از این ولم کن یه جوری خوردم زمین خدا بیا جمعم کن خدا بیا جمعم کن
بردی حواسمو همیشه حواسم بود کجاست حواس تو من
زخمتو خوب کردم که ببینم پروازتو ببینم پروازتو ولی چشات هیچوقت ندید این دست من بود که
روی بالت دست کشید ولی دل توام دست کشید کبوتر نارنجی من
چه راحت پرکشید چه راحت پرکشید یه
روز سرد دیدمت تنهاتر از من خسته از این مردم بی رحم با دیدنت سر پا شد
این تن … تا زخمتو بستم دیدم یهو خالیه دستم حالم خوب نمیشه اصلا خدا به
همرات نارنجی من … شکستی دلمو بگو دیگه چی میخوای از این ولم کن یه جوری خوردم زمین خدا بیا جمعم کن خدا بیا جمعم کن بردی حواسمو
همیشه حواسم بود کجاست حواس تو من زخمتو
خوب کردم که ببینم پروازتو ببینم پروازتو ولی چشات هیچوقت ندید این
دست من بود که روی بالت دست کشید ولی دل
توام دست کشید کبوتر نارنجی
من چه راحت پرکشید چه راحت پرکشید
Hey there! Would you mind if I share your blog with
my twitter group? There’s a lot of people that I think would really enjoy your content.
Please let me know. Thank you
Does your blog have a contact page? I’m having a tough time locating it but, I’d like to
send you an email. I’ve got some suggestions for your boog you might
be interested in hearing. Either way, great
blog and I loiok forward to seeing it develop over time.
I pay a visit each day some sites and information sites to read posts, except this webpage gives quality based articles.
Hi there friends, its wonderful piece of writing regarding cultureand entirely explained, keep it up all the time.
I was extremely pleased to uncover this website. I need to to thank you for
your time due to this wonderful read!! I definitely enjoyed every little bit of it and i also
have you bookmarked to look at new information on your blog.
تو جان مرا اما من از تو فقط جانم یک عشق طلبکارم عاشق نشدی
اما از هر که در این دنیا من دوست ترت دارم عاشق که فراوان
و دیوانه چو من نیست دلتنگ و با هیچکسم
میل سخن نیست تا شمع تویی جانم پروانه منم من انگار شدم با تو یک روح و دو تا تن آرام آرام به قلبم
چه نشستی خوش نشستی تو به جانم زیبا جان آرام آرام شدی نیمه ی جانم شدی
ماه تمامم زیبا جان آرام آرام به قلبم
چه نشستی خوش نشستی تو به
جانم زیبا جان آرام آرام شدی نیمه ی جانم شدی ماه تمامم زیبا جان من آمده ام
سمت تو قلبم برورد ناز کنی خیره شود سوی تو
چشمم باران شده ام چتر ببندی
تو فقط راه برو ای قدمت روی دو چشمم ای نیمه ی زیباترم از
جانم اگر بگذرم از تو که دگر نمیتوانم ای ماه تر از
ماه تماشایی دلخواه دلتنگی تو برده
توانم آرام آرام به قلبم چه نشستی خوش
نشستی تو به جانم زیبا جان آرام آرام شدی نیمه ی جانم شدی ماه تمامم زیبا جان آرام آرام به قلبم چه نشستی خوش نشستی
تو به جانم زیبا جان آرام آرام شدی
نیمه ی جانم شدی ماه تمامم زیبا جان
اگه دلم تنگه برات توی سرم جنگه برات خودمو سرگرم میکنم یه جوری از فکرت درام چرا میخوای دورم کنی مجبورم کنی رو نقطه ضعفم دست نذار دوری
تو آخه سخته برام بی تو شبا برای من پره بهانته هرچی گناهه
پای من هرچی حرف و قضاوته میدونم یه روز برمیگردی با بد و خوب من تو که سر میکردی باشه حق با توئه من بد بودم باشه اصلا تو خوب باشه خیلی مردی دل
پره دلشوره چقد راهمون از هم دوره همیشه اونه که میگه میمونه زود میره رسم
دنیامون اینه بعضی حرفا سنگینه میری و برمیگردی میگی که
تقدیره میدونم یه روز برمیگردی با بد و
خوب من تو که سر میکردی باشه حق با توئه من بد بودم
باشه اصلا تو خوب باشه خیلی مردی
Hi! I understand this is kind of off-topic however I had to ask.
Does building a well-established blog such as yours require a lot
of work? I’m completely new to writing a blog however I
do write in my diary on a daily basis. I’d like to start a
blog so I can easily share my personal experience and feelings online.
Please let me know if you have any suggestions or tips for brand new aspiring blog owners.
Appreciate it!
I love what you guys tend to be up too. Such clever work and exposure!
Keep up the terrific works guys I’ve incorporated you guys
to my own blogroll.
What’s up, after reading this remarkable piece of writing i am also glad to share my knowledge
here with colleagues.
Hi there, You’ve done an excellent job. I’ll certainly digg it and personally suggest to my friends.
I’m confident they’ll be benefited from this web site.
My brother suggested I might like this website.
He was once entirely right. This submit truly made my day.
You cann’t imagine just how so much time I had spent for this info!
Thank you!
Google is getting smarter every single day.
But when money is no object, this can be a super alternative
and will certainly set the tone of the wedding day.
Similarly, you may rank for so many keywords even when you use them
once or twice within a page. So if you’re somebody who continues
to be relying upon stuffing key phrases by specializing in density, you’re doing it fallacious.
Search engines like google and yahoo at the moment are extra subtle and are higher capable of
establish and punish users who try to sport their algorithms.
Facebook’s settings aren’t exactly easy to navigate either, but many overlook that it was rather more complicated than it is now.
As a result, extra users are actually focusing on creating increased quality,
longer form items of content. Unfortunately there’s no proper optimum keyword density that we
will recommend to you as a result of we don’t believe in that concept now.
Gone are the times when you possibly can stuff your weblog posts together
with your focused key phrases to get first page rankings
on Google. You can’t rank larger in search
results in your keywords with such a low density, proper?
È completamente decentralizzato, il che significa che non esiste un’autorità centrale o
server, offre commissioni di transazione inferiori rispetto ai meccanismi di pagamento tradizionali.
Andy Schroder vende CPC tubi sottovuoto Collettori solari termici, con bitcoin come opzione
di pagamento. Secondo alcuni analisti il Bitcoin non sarebbe gradito ai governi e alle banche
centrali poiché non è moneta “controllabile”. Le persone, delle persone, alle persone.
Le macchine, delle macchine, nelle macchine. Le vie,
delle vie, nelle vie. In tale provvedimento, per la valorizzazione delle
attività finanziarie, viene operato un rinvio ai
criteri utilizzati per la determinazione della base imponibile dell’IVAFE.
Capisco il discorso che fate sulle commissioni,
ma Localbitcoins è di default impostato in modo
da mostrare le offerte in base al prezzo finale ed
in ordine crescente. Dobbiamo andare avanti sulle ipotesi, non abbiamo ancora dati
certi di studi che possano confermare il perché stia
accadendo ma, probabilmente, questa variante si
accompagna ad alte cariche virali che hanno un impatto forte sulla manifestazione della malattia”. In pratica, chi viene infettato da una carica virale più alta, tendenzialmente ha una manifestazione clinica più importante rispetto a chi ha una carica virale più bassa. “Quello che sta accadendo deve porci
in una condizione di maggiore attenzione:
le terapie intensive sono a livelli di criticità
massima, stiamo esaurendo i posti e dobbiamo cercare di contenere il contagio riducendo al
massimo la trasmissione di questa variante.
continuously i used to read smaller articles which also clear their motive,
and that is also happening with this article which I
am reading at this place.
Ahaa, its pleasant discussion regarding this article here at this blog, I have read all that,
so now me also commenting here.
It’s appropriate time to make some plans for
the future and it’s time to be happy. I have read this post and if I could I want to suggest you some interesting things or advice.
Maybe you can write next articles referring to this article.
I desire to read more things about it!
Have you ever considered writing an ebook or guest authoring on other websites?
I have a blog based upon on the same topics you discuss and would love to have you share some stories/information. I know my visitors would enjoy your work.
If you’re even remotely interested, feel free to send me an e-mail.
Thanks for your personal marvelous posting!
I seriously enjoyed reading it, you can be a great author.I will make certain to bookmark your blog and will come back later on. I
want to encourage continue your great job, have a nice
day!
โลกออนไลน์ที่เปลี่ยนอย่างรวดเร็วในทุกวงการ เว็บแทงบอลยอดนิยมทั่วโลกได้รับการพัฒนาอย่างเร็วเพื่อปรับระบบการใช้แรงงานให้เข้ากับการใช้งานของคนในตอนไม่กี่ปีมานี้หันมาใช้โทรศัพท์มือถือเยอะขึ้นซึ่งทางเว็บได้รองรับการใช้แรงงานผ่านมือถือ
ลูกค้าสามารถเข้าถึงถึงที่เหมาะนี่ ที่พร้อมเปิดราคาทุกหมวดหมู่ตลอด 24 ชั่วโมง เราพร้อมจะมอบความสำราญและก็บริการเป็นอย่างดีเพื่อพัฒนาทีมงานของพวกเราให้ดีอยู่เสมอเวลา เพื่อเป็นการมอบความสะดวกสบายให้กับสมาชิกทางค่ายของเรา พวกเราจึงได้มีบริการเพิ่ม-ถอนเครดิตไม่มีขั้นต่ำ
สำหรับเพื่อการพนันเกมพนันออนไลน์บนเว็บของเราซึ่งสามารถฝากเครดิตผ่านtrue walletอีกหนึ่งช่องทางการเติมเงินยอดนิยมอย่างยิ่งเดี๋ยวนี้ ทั้งสะดวกสบายและก็เครดิตก็เข้าเร็วอีกด้วย ไม่เป็นอันตรายไม่ได้ต่างอะไรจากการโอนแบบผ่านแบงค์เหมือนกัน
Your means of explaining all in this article
is in fact fastidious, every one can easily know it,
Thanks a lot.
Somebody essentially lend a hand to make critically posts
I would state. That is the first time I frequented your web
page and to this point? I amazed with the research you made to create this actual publish incredible.
Excellent task!
I was recommended this website via my cousin. I’m now not positive whether or not this
submit is written by means of him as no one else know such particular approximately my problem.
You are amazing! Thanks!
ด้วยต้นแบบการเล่นที่เร้าใจ พร้อมลุ้นของขวัญมากมายกว่าเกมอื่นๆยังเล่นง่ายอีกด้วย รวมทั้งขั้นตอนการเล่นเกมสล็อตออนไลน์นั้น มีทั้งเล่นผ่านเว็บรวมทั้งบนโทรศัพท์มือถือ ตามความสะดวกของผู้เล่น โดยจะมีกฎสำหรับในการเล่นปุ่มควบคุมต่างๆที่เหมือนกับเครื่องสล็อตในคาสิโนจริง
เกมสล็อตออนไลน์ที่เราได้มาดัดแปลงแก้ไขตู้สล็อตแมชชีน มาในต้นแบบเกมElectronic ที่รู้จักกันในนามสล็อตฝากถอนออโต้เนื่องจากในช่วงหลังนักพนันรายใหม่
เริ่มเป็นที่นิยมในการเล่นพนันผ่านมือถือและคอมพิวเตอร์รวมทั้งอินเตอร์เน็ตมากเพิ่มขึ้น
เว็บไซต์ของพวกเราเป็นเว็บชั้น 1 ของประเทศ ปลอดภัย 100% พวกเราอัพเดทเกมส์SUPERSLOTตลอดระยะเวลา ไม่ว่าจะเป็นเกมใหม่ พวกเรานำการอัพเดทมาให้ทุกคนได้เล่น ประการแรกอย่างแน่นอน แล้วก็ยังเปิดตลอด 24 ชั่วโมง
Hello would you mind sharing which blog platform you’re working with?
I’m looking to start my own blog in the near future but I’m having a
difficult time deciding between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your layout seems different then most
blogs and I’m looking for something completely unique.
P.S Sorry for being off-topic but I had to ask!
What i do not understood is in reality how you’re no longer actually much more neatly-appreciated than you may
be now. You’re very intelligent. You know thus considerably when it comes
to this subject, made me for my part consider
it from so many numerous angles. Its like women and men aren’t interested unless it’s one thing
to accomplish with Girl gaga! Your individual stuffs nice.
At all times care for it up!
Greetings from Colorado! I’m bored to death at work so I decided to browse your website
on my iphone during lunch break. I love the information you
provide here and can’t wait to take a look
when I get home. I’m surprised at how fast your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyways, good blog!
Hurrah! Finally I got a weblog from where I know how to really take helpful information regarding my study and knowledge.
Thank you for the auspicious writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you! However, how can we communicate?
I am truly thankful to the holder of this website who has
shared this great article at at this time.
This is very attention-grabbing, You are a very skilled blogger.
I have joined your rss feed and look ahead to in search of more of your wonderful post.
Also, I have shared your website in my social networks
Now I am ready to do my breakfast, after having my breakfast coming yet again to
read more news.
Hi there to every body, it’s my first pay a quick visit of this web site; this web site
contains remarkable and actually fine data designed for
readers.
hello there and thank you for your info – I’ve certainly picked up anything new from right here.
I did however expertise some technical points using this web site, as I experienced to reload the site many times previous to I could get it to load properly.
I had been wondering if your web hosting is OK? Not that
I’m complaining, but sluggish loading instances times will very frequently affect your placement in google and can damage your high-quality
score if advertising and marketing with Adwords.
Anyway I am adding this RSS to my e-mail and could look out for much more of your respective interesting content.
Make sure you update this again very soon.
การเล่นสล็อตออนไลน์ จะมีข้อตกลงเบื้องต้นสำหรับการเล่นที่ใช้เหมือนกันทุกเว็บไซต์ โดยการเริ่มเล่นสล็อตได้นั้นจะใช้ยอดเครดิตใน User ของท่านเปรียบเสมือนเหรียญที่ยอดในตู้สล็อต แล้วต่อจากนั้นเข้าเลือกเกมสล็อตออนไลน์ แล้วเลือกอัตราเดิมพันแล้วก็ไลน์การเล่น
กด Play หรือ Spin
ผู้เล่นจึงควรหมุนให้ได้เครื่องหมายภาพมาเรียงกันตามไลน์ที่เลือกไว้ คิดตามแนวยาว ตั้งแต่ 2 หรือ 3
ภาพ จะเรียงจากซ้ายหรือขวาก็สุดแท้แต่เกม แต่โดยส่วนมากใน การเล่นสล็อตออนไลน์แบบ 5 Reel (5 วงล้อ) ภาพสัญลักษณ์จึงควรเรียงกันตั้งแต่ 3 ภาพขึ้นไปเรียงจากซ้ายไปขวา ถ้าชนะก็จะได้รับรางวัลขึ้นอยู่กับกติกาของแต่ละเว็บ
คำว่า casino มาจากภาษาอิตาลี จริงๆแล้วอ่านออกเสียงว่า “กาสิโน” หมายความว่าบ้านพักหลังเล็กใช้เพื่อการพักผ่อน ซึ่งถัดมาได้มีการนำเอาคำว่า คาสิโน
ไปใช้กับสถานที่ ที่มีกิจกรรมการเดิมพันเป็นกิจกรรมหลัก โดยธรรมดาแล้วคาสิโนมักจะถูกตั้งขึ้นให้อยู่รวมกับธุรกิจอื่น อาทิเช่น อพาร์เม้นท์ ห้องอาหาร สถานที่ท่องเที่ยว ห้างสรรพสินค้า หรือบนเรือสำราญ เป้าประสงค์นั่นก็เพื่อให้เป็นที่พักผ่อนพักผ่อนหย่อนใจ ผ่อนคลาย ในหลากหลายแบบที่ไม่ใช่การเดิมพันอย่างเดียว ฉะนั้นจึงรู้สึกเสมือนบ้านอีกหลังนึงนี่เอง
Hi there friends, nice paragraph and nice urging commented here, I am
genuinely enjoying by these.
Thank you for some other magnificent post. The place else may just anyone get
that type of info in such an ideal means of writing? I have a presentation next week,
and I’m on the look for such info.
Hi there! Someone in my Facebook group shared
this site with us so I came to give it a look.
I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers!
Excellent blog and brilliant design.
Hello There. I found your blog using msn. This is a really well written article.
I will be sure to bookmark it and return to read more of your useful info.
Thanks for the post. I’ll certainly comeback.
Hello There. I found your weblog the usage of msn. This is an extremely neatly written article.
I’ll make sure to bookmark it and come back to learn more of your useful
information. Thank you for the post. I’ll certainly return.
We are a group of volunteers and starting a new scheme
in our community. Your site provided us with valuable info
to work on. You have done a formidable job and our entire community will be grateful to you.
What’s up i am kavin, its my first time to commenting anywhere,
when i read this article i thought i could also create
comment due to this brilliant piece of writing.
When I originally commented I clicked the “Notify me when new comments are added”
checkbox and now each time a comment is added I get three e-mails with the same comment.
Is there any way you can remove me from that service?
Thanks!
I do not even understand how I finished up right here, however I believed this
put up was great. I do not recognize who you might be however certainly you are going to a well-known blogger if you are
not already. Cheers!
Also visit my homepage; sell your house In raleigh quickly
This design is incredible! You obviously know how to keep a reader amused.
Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!)
Fantastic job. I really enjoyed what you had
to say, and more than that, how you presented it. Too cool!
I am curious to find out what blog platform you happen to be working with?
I’m experiencing some small security issues with my latest site and I’d
like to find something more safeguarded. Do you have
any recommendations?
Thank you for every other informative website. Where else may
I get that kind of info written in such a perfect means?
I have a challenge that I am simply now operating on, and
I’ve been on the look out for such information.
I must thank you for the efforts you’ve put in writing this website.
I’m hoping to check out the same high-grade
content by you later on as well. In fact, your creative writing abilities has motivated me to get my
own, personal website now 😉
I’m really enjoying the design and layout of your blog. It’s a very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a designer to create your theme? Great work!
Hi there, just wanted to say, I loved this post.
It was helpful. Keep on posting!
Very nice post. I just stumbled upon your blog and wanted to
say that I’ve really enjoyed browsing your blog posts.
In any case I’ll be subscribing to your rss feed and I hope you write again very
soon!
It’s very trouble-free to find out any topic on net as compared to textbooks, as
I found this post at this site.
Excellent post! We are linking to this particularly great post on our website.
Keep up the good writing.
When some one searches for his necessary thing, thus
he/she desires to be available that in detail, therefore that thing is maintained over here.
Love the website– very individual pleasant and lots
to see!
https://tchtcareers.com/author/harmoniawvherbert/
An impressive share! I have just forwarded this onto a co-worker who has been conducting a little research on this.
And he actually bought me lunch because I stumbled upon it for him…
lol. So allow me to reword this…. Thank YOU for the meal!!
But yeah, thanx for spending the time to discuss this issue here on your
site.
Marvelous, what a web site it is! This webpage presents useful data to us, keep it up.
Hey there! I know this is kinda off topic but I was wondering which blog platform are you
using for this website? I’m getting sick and tired of WordPress
because I’ve had problems with hackers and I’m looking at alternatives
for another platform. I would be great if you could point
me in the direction of a good platform. https://careers.societyforcryobiology.org/employers/1158277-basin-drainer-zeda-plastic
WOW just what I was looking for. Came here by searching for dog poop pick up
For latest information you have to pay a visit web and on world-wide-web I
found this site as a best site for hottest updates.
I need to to thank you for this fantastic read!! I absolutely enjoyed
every bit of it. I have got you book-marked to look at new things you post…
I don’t even know how I ended up here, but I thought this post was great.
I do not know who you are but definitely you are going to a famous blogger if you are
not already 😉 Cheers!
If you would like to obtain much from this article
then you have to apply such techniques to your won web site.
I am extremely impressed with your writing abilities and also with the format for your weblog.
Is that this a paid subject matter or did you customize
it yourself? Either way keep up the excellent high quality writing,
it is rare to peer a nice blog like this one nowadays..
If you would like to get a great deal from this paragraph then you have to apply these techniques to
your won weblog.
در این مقاله میخواهیم به معرفی بهترین مدارس فوتبال تهران
بپردازیم، اما قبل از آن بیایید کمی با این ورزش مهیج و پرطرفدار آشنا شویم.
تا انتها با ما همراه باشید تا بهترین
مدرسه فوتبال تهران و بهترین مدرسه فوتبال کودکان در تهران را به شما معرفی کنیم.
ورزش فوتبال
فوتبال یک ورزش تیمی و محبوبترین ورزش در بیشتر کشورهای جهان است.
فوتبال را دو تیم یازده نفره متشکل از بازیکنان فوتبال با یک توپ فوتبال بر روی چمن طبیعی یا مصنوعی با هدف گل زدن
انجام میدهند.
یازده بازیکن هر تیم شامل چند مهاجم،
هافبک، مدافع و یک دروازهبان میشوند که
توسط سرمربی در زمین چیده میشوند و مانند یک سیستم عمل میکنند که سیستم فوتبال نامیده میشود.
امروزه بیش از ۲۵۰ میلیون فوتبالیست در
بیش از ۲۰۰ کشور وجود دارد.
تاریخچه ورزش فوتبال
قدمت فوتبال به چندین سدهٔ پیش از میلاد
و به چین بازمیگردد که به تدریج در یونان و روم نیز رواج مییابد.
فوتبال مدرن امروزی نیز در سال ۱۸۶۶ در مدارس
انگلستان شکلگرفت و به تدریج گسترهٔ پراکندگی آن همهٔ جهان را زیر پوشش خود
قرارداد. با شکلگیری سازمان فیفا در سال
۱۹۰۴ و ایجاد رقابت جام جهانی فوتبال، این ورزش بسیار گسترده تر شد.
آکادمی های فوتبال تهران
ورزش فوتبال یکی از محبوب ترین ورزشهای در
سراسر جهان و در کشور ایران است.
کافی است از یک کودک بپرسید دوست دارد در آینده چه کاره شود؟ قطعا
یکی از پاسخ های کودکان اسن است که
دوست دارند فوتبالیست شوند.
دلیل علاقه کودکان به ورزش فوتبال، محبوبیت، شهرت
و ثروتی است که یک بازیکن فوتبال حرفه ای کسب میکند.
گرچه فوتبال تفریحی در کوچه و خیالان نیز برای کودکان جذابیت دارد، اما برای موفقیت در ورزش فوتبال، آموزش دیدن در بهترین آکادمی های فوتبال تهران ضرورت دارد.
امروزه مدارس فوتبال زیادی در تهران فعالیت دارند که بسیاری از آنها از سطح کیفی بالایی برخوردارند و
از مربیان با تجربه بهره میبرند.
هدف تاسیس یک مدرسه فوتبال، آموزش فوتبال به کودکان و نوجوانان و پرکردن اوقات فراغت همراه با آموزش اصولی و علمی فوتبال
است رویکرد مدارس فوتبال تهران و شهرهای دیگر به
این صورت است که پس از آموزش، آزمون های استعدادیابی
برگزار میکنند تا استعداد های برتر
را در سنین پایین شناسایی کنند و برای شرکت
در رده های بالاتر و تیمهای باشگاهی آماده سازند.
بهترین مدارس فوتبال تهران
نحوه فعالیت مدارس فوتبال
مدرسه های فوتبال غالبا در تابستان دارای بیشترین متقاضی و جذب بازیکن هستند، اگرچه در سایر فصل های سال نیز فعالیت
خود را ادامه میدهدن. مدرسه های فوتبال معمولا به آموزش فوتبال برای رده سنی کودک و نوجوان
میپردازند، با این حال در بعضی مدارس بزرگسالان نیز
میتوانند آموزش ببینند. گرچه ورود به تیم های باشگاهی برای
بزرگسالان ممکن نیست و معمولا بازیکنانی که در
رده نوجوانان هستند و از استعداد خوبی برخوردارند به تیم
های لیگ معرفی میشوند.
هزینه مدارس فوتبال در تهران چقدر است؟
هزینه مدارس فوتبال تهران نرخ
ثابتی ندارد و اختلاف بسیار زیادی
با هم دارند. بسته به کیفیت و سطح آموزش و شهرت مدرسه
فوتبال، تجهیزات و امکانات
آکادمی فوتبال، مربیان فوتبال، و محل و منطقه قرارگیری مدرسه فوتبال،
شهریه متفاوت است. به طور کلی میتوان گفت هزینه مدارس فوتبال در تهران به ازای 10 تا 12 جلسه، از 500
هزار تومان تا 1.5 میلیون تومان متغیر است!
همینطور که میبینید شهریه
آکادمی های فوتبال تهران بسیار اختلاف داردف با این حال به طور متوسط هزینه آموزش فوتبال در مدارس مختلف حدود 700 هزار تومان تا 1 میلیون تومان است.
این هزینه به ازای یک ترم سه ماهه در تابستان از 1.5 میلیون شروع شده و میتواند به 5
ملیون تومان برسد.
انواع مدارس فوتبال
مدارس فوتبال از نظر نوع فعالیت به دو دسته مدارس فوتبال فصلی و مدارس فوتبال دائمی تقسیم
میشوند. در مدارس فوتبال فصلی هر ترم شامل هشت
هفته فعال آموزشی (عملی و تئوری) است و در
هر هفته سه جلسه 90 دقیقه ای برگزار میشود.
مدارس فوتبال دائمی حداقل سه ترم در سال فعالیت دارند و هر
ترم شامل ده هفته آموزشی (عملی و تئوری) و هر هفته شامل سه جلسه 90
دقیقه ای میباشد.
بهترین مدارس فوتبال تهران
در لیست زیر تعدادی از بهترین مدارس فوتبال تهران را برای شما آورده ایم.
برای شرکت در کلاس فوتبال تهران شما میتوانید در بهترین آکادمی های فوتبال تهران ثبت نام کنید
و به طور حرفه ای اموزش ببینید.
هریک از باشگاه های معرفی شده در لیست بهترین
مدرسه فوتبال تهران از اساتید مجرب بهره میگیرند و بهترین
کلاس فوتبال در تهران را برگزار میکنند.
مدارس فوتبال تهران که در لیست زیر معرفی شدند، برگزار کننده دوره های تخصصی برای مقاطع سنی مختلف هستند و کودکان، نوجوانان
و حتی بزرگسالان میتوانند با ثبت نام در بهترین آکادمی
های فوتبال تهران به طور حرفه ای فوتبال را
آموزش ببینند. در ادامه لیست بهترین
آکادمی فوتبال تهران را برای شما آورده ایم.
آکادمی فوتبال استقلال تهران
Everyone loves what you guys tend to be up too.
This sort of clever work and coverage! Keep up the excellent works guys I’ve included you
guys to my personal blogroll.
It’s very straightforward to find out any matter on net as compared
to books, as I found this paragraph at this web site.
Because the admin of this website is working,
no doubt very shortly it will be well-known, due to its feature contents.
Unquestionably believe that which you said. Your favorite justification seemed to
be on the web the easiest thing to be aware of.
I say to you, I definitely get irked while
people think about worries that they just don’t know about.
You managed to hit the nail upon the top as well as defined out the whole thing without
having side effect , people could take a signal.
Will probably be back to get more. Thanks
Thanks , I’ve recently been searching for information about this topic for a while and yours is the
greatest I’ve discovered so far. However, what
about the bottom line? Are you sure concerning the source?
ما در این مقاله به معرفی بهترین کلاس آرایشگری شرق تهران میپردازیم.
تاانتها با ما همراه باشید.
شغل آرایشگری، حرفه ای است که نیازی به تحصیلات آکادمیک ندارد و در
حال حاضر یکی از مشاغل پردرآمد
محسوب می شود؛ همین امر باعث شده است که بسیاری از مردم به دنبال راه اندازی
آرایشگاه باشند.
اما یک آرایشگر زمانی می تواند درآمد بالایی داشته باشد که مهارت کافی در زمینه آرایشگری کسب کرده باشد تا بتواند رضایت مشتریان را جلب کند.
در ادامه به شرح مسیری که یک فرد علاقمند به آرایشگری باید طی کند، می پردازیم.
شغل آرایشگری:
به آرایش، پیرایش و خدمات زیبایی که در مکان های مشخصی به
نام آرایشگاه انجام شود، «آرایشگری» میگویند.
آرایشگر کیست؟
فردی است که پس از کسب مهارت های لازم، خدمات
متنوع آرایشی و بهداشتی را به مشتریان ارائه می دهد.
ویژگیهای آرایشگر:
با ذوق وملیقه است: مشتریان آرایشگری را می پسندند که برای
هرچه زیباتر کردن آن ها ذوق
و سلیقه به خرج بدهد.
گشاده روست: آرایشگر با مشتریان به
طور رو در رو در ارتباط است؛ بنابراین برخورد خوب او در
جذب و حفظ مشتریان اهمیت زیادی
دارد.
صبور است: آرایشگر گاهی باید چندین ساعت برای انجام درخواست های یک مشتری وقت بگذارد و بنا به صلیقه او عمل کند.
به آراستکی خود اهمیت می دهد:
کسی که با زیبایی سر و کار دارد، باید به آراستگی ظاهر خود نیز اهمیت بدهد.
معرفی بهترین کلاس آرایشگری شرق تهران
این مطلب را هم از دست ندهید:
معرفی بهترین کلاس گریم تهران
معرفی بهترین کلاس آرایشگری غرب تهران
اگر بخواهم آرایشگر شوم از کجا باید شروع کنم؟
برای این که یک آرایشگر شوید هم باید مهارت هایی در
زمینه روابط اجتماعی و هم فوت و فن آرایشگری را یاد بگیرید.
در ادامه به مهارت هایی که یک آرایشگر باید
داشته باشد چه از نظر ارتباطات و
چه از نظر تکنیک می پردازیم.
Wow! This blog looks just like my old one!
It’s on a entirely different topic but it has pretty much the
same layout and design. Excellent choice of colors!
I think this is one of the most important information for me.
And i’m glad reading your article. But want to remark on few general things, The site style is perfect, the articles is really excellent :
D. Good job, cheers
I just couldn’t depart your website prior to suggesting that I extremely loved
the standard information an individual supply for your
visitors? Is going to be back frequently to check up on new posts
If you want to grow your familiarity only keep visiting this website and be updated with the most up-to-date news update posted here.
I enjoy reading through an article that can make men and
women think. Also, thank you for allowing
me to comment!
Do you mind if I quote a couple of your articles as long as I provide credit and sources back to your site?
My website is in the exact same area of interest as
yours and my users would genuinely benefit from a
lot of the information you present here. Please let me know if this okay with you.
Appreciate it!
Howdy! Would you mind if I share your blog with my facebook group?
There’s a lot of folks that I think would really appreciate your content.
Please let me know. Thanks
I know this if off topic but I’m looking into starting
my own blog and was wondering what all is required to
get setup? I’m assuming having a blog like yours would cost a pretty
penny? I’m not very internet smart so I’m not 100% positive.
Any tips or advice would be greatly appreciated. Thanks
Howdy would you mind stating which blog platform you’re working with?
I’m planning to start my own blog soon but I’m having a hard time selecting between BlogEngine/Wordpress/B2evolution and
Drupal. The reason I ask is because your design and style seems different then most blogs
and I’m looking for something unique. P.S My apologies for being
off-topic but I had to ask!
Today, I went to the beachfront with my children. I found a sea shell and gave it to my 4
year old daughter and said “You can hear the ocean if you put this to your ear.” She
put the shell to her ear and screamed. There
was a hermit crab inside and it pinched her ear. She never
wants to go back! LoL I know this is completely off topic but I had to
tell someone!
Also visit my website – buy my house Pittsburgh
Do you mind if I quote a couple of your articles as long as I provide credit and sources back to your weblog?
My website is in the exact same niche as yours and my visitors would definitely benefit from a lot of the information you provide here.
Please let me know if this ok with you. Appreciate it!
Hi there! I could have sworn I’ve been to this blog before but after browsing through some of the post I realized it’s new to me.
Anyways, I’m definitely glad I found it and
I’ll be book-marking and checking back frequently!
Highly descriptive article, I loved that bit. Will there be a part 2?
Hey there, I think your website might be having browser compatibility issues.
When I look at your blog site in Opera, it looks fine but when opening in Internet Explorer,
it has some overlapping. I just wanted to give you a quick heads
up! Other then that, very good blog!
Highly energetic post, I enjoyed that bit.
Will there be a part 2?
I visited several websites except the audio feature for audio songs
present at this site is actually marvelous.
Hi friends, its enormous article regarding cultureand completely explained,
keep it up all the time.
Thanks in support of sharing such a good opinion, piece of writing is
nice, thats why i have read it completely
cheers considerably this excellent website is usually
professional and also everyday
Hi there! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any tips?
Greetings I am so excited I found your weblog, I really
found you by error, while I was browsing on Digg for something else, Anyhow
I am here now and would just like to say many thanks for
a incredible post and a all round enjoyable blog (I also love the theme/design), I don’t
have time to go through it all at the minute but
I have book-marked it and also added your RSS feeds, so when I have time I
will be back to read much more, Please do keep up the excellent work.
Keep on writing, great job!
Saved as a favorite, I like your blog!
hello there and thank you for your information – I’ve
certainly picked up something new from right here. I did
however expertise several technical issues using this website, as I experienced to
reload the website many times previous to I could get it to load correctly.
I had been wondering if your hosting is OK? Not that I’m complaining, but sluggish loading instances
times will often affect your placement in google and can damage your quality score if advertising and marketing with
Adwords. Well I’m adding this RSS to my e-mail and
could look out for a lot more of your respective intriguing content.
Make sure you update this again soon.
Great web site you have here.. It’s hard to find quality writing like yours these days.
I really appreciate individuals like you! Take care!!
What’s Taking place i am new to this, I stumbled upon this I’ve found It positively helpful and it has helped me
out loads. I hope to give a contribution & help other
customers like its aided me. Good job.
Hmm is anyone else experiencing problems with the images on this blog
loading? I’m trying to find out if its a problem on my end or if it’s
the blog. Any suggestions would be greatly appreciated.
It’s impressive that you are getting thoughts from this article as well as from our dialogue made at this place.
Spot on with this write-up, I seriously think this site needs a lot more attention. I’ll probably be back again to read more, thanks for the info!
What a information of un-ambiguity and preserveness of valuable knowledge concerning unpredicted emotions.
Heya i’m for the first time here. I found this board and I find It truly useful & it helped
me out a lot. I hope to give something back and help others like you aided me.
Great post. I’m experiencing some of these issues as well..
I really love your website.. Excellent colors & theme.
Did you build this website yourself? Please reply back as I’m hoping to create
my own blog and would like to find out where you got this from or just what the theme is named.
Thank you!
This post is really a pleasant one it assists new the web viewers, who are wishing
for blogging.
Attractive section of content. I just stumbled upon your site and in accession capital to assert
that I acquire in fact enjoyed account your blog posts.
Anyway I’ll be subscribing to your feeds and even I achievement you access consistently
quickly. https://www.racked.com/users/jamiy2022
What’s up every one, here every person is sharing these familiarity,
therefore it’s good to read this web site, and I used to pay a quick visit this website everyday.
Good site you have got here.. It’s hard to find excellent writing like yours these days.
I really appreciate people like you! Take care!!
Absolutely written content, regards for information. “The last time I saw him he was walking down Lover’s Lane holding his own hand.” by Fred Allen.
Situs Togel
Yes! Finally someone writes about togel darat.
Please let me know if you’re looking for a author for your blog.
You have some really great posts and I think
I would be a good asset. If you ever want to take some of the load off, I’d love to write some articles for your blog in exchange for
a link back to mine. Please shoot me an email if interested.
Cheers!
Hiya! Quick question that’s totally off topic. Do you know how to
make your site mobile friendly? My site looks weird when viewing from my apple iphone.
I’m trying to find a template or plugin that might be
able to fix this issue. If you have any suggestions, please share.
Many thanks!
Somebody necessarily assist to make severely articles
I’d state. This is the very first time I frequented your website page and thus far?
I amazed with the research you made to make this actual publish amazing.
Great job!
What’s up to every one, the contents existing at this
website are genuinely remarkable for people knowledge, well, keep up the nice work fellows.
We stumbled over here coming from a different web
address and thought I might check things out. I like what I see so now i
am following you. Look forward to looking at your web page repeatedly.
Your style is so unique compared to other people I have read stuff from.
Thanks for posting when you’ve got the opportunity, Guess
I will just book mark this site.
My brother recommended I may like this blog. He used to
be entirely right. This post truly made my day.
You cann’t believe just how so much time I had spent for this info!
Thanks!
Wow, that’s what I was exploring for, what a data!
existing here at this blog, thanks admin of this website.
I get pleasure from, lead to I found just what I
was taking a look for. You have ended my four day long hunt!
God Bless you man. Have a great day. Bye
I’d like to thank you for the efforts you
have put in penning this blog. I’m hoping to check out the same high-grade blog posts by you later on as well.
In fact, your creative writing abilities has motivated me
to get my very own blog now 😉
My brother suggested I might like this website. He was totally right.
This post truly made my day. You cann’t imagine simply how much time
I had spent for this info! Thanks!
Thanks a ton! It is an astonishing web site.
http://www.jobsforearth.com/author/brigittahelvesy/
Hi there everyone, it’s my first go to see at this web site, and paragraph is genuinely fruitful designed
for me, keep up posting these content.
This piece of writing gives clear idea for the new visitors of
blogging, that truly how to do blogging and site-building.
สล็อตได้เงินจริง อย่างที่รู้ๆกันดีอยู่แล้วว่าเว็บของเรานั้นเป็นอีกหนึ่งค่ายเกมที่เป็นแหล่งรวมเกมสล็อตออนไลน์ยอดนิยม เว็บเดียวครบจบที่นี่
มีชื่อเสียงในเรื่องเกี่ยวกับการแจกโบนัสฟรี100%แล้วก็เป็นเว็บไซต์แจ็คพอตในเกมแตกง่ายที่สุด สมาชิกที่เข้ามาเล่นกับพวกเราจะได้รับทั้งยังกำไรมหาศาลและความเพลิดเพลินเพลิดเพลินใจ
ยิ่งกว่านั้นทางเรายังมีระบบระเบียบกฝากถอนอัตโนมัติทั้งสิ้น
ลงทะเบียนสล็อตกับเราวันนี้พร้อมรับโบนัสพิเศษมากมายก่ายกองที่เหมาะสมกับท่านที่สุด สล็อตออนไลน์เป็นเกมที่มีคนนิยมหันมาเล่นกันจำนวนไม่ใช่น้อยในขณะนี้ เนื่องจากเป็นเกมที่เล่นง่ายไม่สลับซับซ้อน ตัวเกมมีภาพเสียงกราฟฟิคที่ล้ำยุคแล้วก็สมจริงที่สุด
พวกเราได้มีการปรับปรุงระบบเกมjokerให้เล่นง่าย แจ็คพอตแตกบ่อยครั้งPgเพิ่มมากขึ้น แจกแบบจัดหนักเต็มเต็ม รับเงินเข้ากระเป๋าให้ตุงกันไปเลยพวกเราหวังว่าสมาชิกทุกท่านที่ได้เข้ามาใช้บริการกับเราจะจับใจเมื่อใดก็ตามเข้ามาเล่น
ด้วยเหตุว่าทุกสิ่งที่พวกเราอัพเดทพัฒนาขึ้นก็เพื่อลูกค้าที่น่ารักน่าเอ็นดูของเรา
excellent publish, very informative. I’m wondering why the other experts of this
sector do not understand this. You should continue your writing.
I’m sure, you’ve a huge readers’ base already!
มีงบประมาณเล่นน้อยแม้กระนั้นทำกำไรได้มาก จ่ายหนักจ่ายจริง ไม่มีประวัติการทุจริตอย่างแน่แท้ จำต้องตรงนี้เท่านั้นเว็บไซต์ตรงไม่ผ่านเอเย่นต์ อย่ารอคอยช้าอย่าเสียโอกาสอย่างงี้มิได้มีมาบ่อยๆคุณอาจเป็นคนรวยคนต่อไป โปรแรงแซงทุกค่าย มีให้เลือกเยอะแยะ คุ้มทุกโปรสล็อต
เลือกตามที่ใจต้องการ สมัครสล็อตรับโบนัส100%โปรโมชั่นโบนัสฟรีมากมายก่ายกองรอคุณอยู่ แจกเครดิตฟรีสำหรับสมาชิกใหม่ รวมโบนัสเครดิตฟรี
สำหรับสมาชิกรายวันของพวกเราเอง มีของแจกฟรีมากมายก่ายกอง
แจกจริงมากกว่าผู้ใดกัน ติดตามได้บทความแล้วก็เนื้อหาโปรโมชั่นต่างๆ
ที่เว็บสล็อตเว็บตรงไม่ผ่านเอเย่นต์ของเราได้ตลอดเวลา
โปรโมชั่นดีๆรอคอยคุณอยู่ สมัครสมาชิกในเวลานี้ JOKER SLOTเครดิตฟรีการเล่นเกมสล็อตออนไลน์ใช้เงินลงทุนน้อยกว่าเกมอื่น เหตุผลที่คนเล่นสล็อตJoker ด้วยเหตุว่าเล่นง่ายสบายตลอดเวลา
ไม่ต้องไปเล่นที่คาสิโนโน่น
มารับทรัพย์มารับเงินก้อนที่พร้อมจะแจกให้ทุกคนกันเลยดีกว่าในด้านการบริการของเราก็ดีที่สุดเนื่องจากว่าพวกเรามีทีมงานและก็น้องๆแอดมินที่น่ารักน่าเอ็นดูรอให้บริการสมาชิกทุกคนตลอด 1 วัน จากทีมงานมือโปร พวกเรามีเกมออนไลน์นานัปการต้นแบบให้บริการด้วยความซื่อสัตย์รวมทั้งมั่นคงมาอย่างนาน
ถ้าหากลูกค้าติดปัญหาด้านการใช้งานไหมเข้าใจการใช้งานตรงไหน ทางเราก็สามารถช่วยแก้ปัญหาได้อย่างแน่แท้เพื่อลูกค้าทุกคนได้เล่นเว็บไซต์ของพวกเราอย่างสนุกสนานและเพลินใจตลอดวันชั่วโมงไม่มีทางหยุดเรียบง่ายไม่ต้องอ่อนเพลียหลายเท่า
เราขอชี้แนะเว็บสล็อตออนไลน์ดีๆที่การันตีเงินแน่นอน ฝากถอนไม่ยั้งตลอด
24 ชม. เว็บไซต์พนันออนไลน์ที่เปิดให้เดิมพันทุกต้นแบบ
รับทุกอัตราต่อรอง จ่ายไม่จำกัดที่อีกทั้งมั่นใจรวมทั้งไม่เป็นอันตรายไม่จำเป็นที่จะต้องมาวิตกกังวลหรือกลุ้มใจเรื่องบริการ รับผู้ใช้ รับคำตอบทุกปัญหาที่ขัดข้อง ตอบทุกคำถามอย่างเห็นได้ชัด
With thanks! It a fantastic web-site!
https://www.empregospernambuco.com.br/author/karlynanjelavmw/
The ultimate guide to plaing Baccarat
เว็บบาคาร่า
What’s up it’s me, I am also visiting this website regularly, this
website is actually pleasant and the viewers are truly sharing fastidious thoughts.
This is very interesting, You’re a very skilled blogger.
I’ve joined your feed and look forward to seeking more of your fantastic
post. Also, I have shared your website in my social
networks!
Thank you so much! It is an amazing web-site!
https://www.rapidjobs4u.com/author/jerryleeeubruno/
Your data is extremely fascinating.
http://www.empregosmaranhao.com.br/author/charissatxpaulo/
This blog was… how do you say it? Relevant!! Finally I have found something
that helped me. Cheers!
I do believe all of the ideas you’ve offered in your post.
They are very convincing and will certainly work. Still, the posts are
very brief for newbies. May you please lengthen them a little from subsequent time?
Thank you for the post.
Havbing read tthis I believed itt was really enlightening.
I appreciate you finding the time and effort to put this information together.
I once again find myself personally spendinng a lott of time both reading aand leaving comments.
But so what, it was still worthwhile!
It’s nearly impossible to find experienced people about this topic, but you seem like you know what you’re talking about!
Thanks
I enjoy this site – its so usefull and helpfull.
https://dothantoday.com/jobs/author/bridepickensey/
Why users still use to read news papers when in this technological world everything is
existing on net?
An impressive share! I’ve just forwarded this onto a colleague
who had been doing a little homework on this. And he in fact bought me breakfast simply because I found it for
him… lol. So allow me to reword this…. Thanks for the
meal!! But yeah, thanks for spending time to talk about this subject here on your web site.
It’s impressive that you are getting ideas from this paragraph as well as from our
argument made at this place.
This is a topic that’s near to my heart… Many thanks!
Exactly where are your contact details though?
Write more, thats all I have to say. Literally, it seems as though you
relied on the video to make your point. You obviously know
what youre talking about, why waste your intelligence on just posting
videos to your weblog when you could be giving us something informative to read?
Pretty nice post. I just stumbled upon your weblog and wished to say that I have really enjoyed browsing your
blog posts. In any case I will be subscribing to your
rss feed and I hope you write again soon!
Ahaa, its fastidious dialogue concerning
this paragraph at this place at this weblog,
I have read all that, so at this time me also
commenting here.
Does your website have a contact page? I’m having a tough time locating it but, I’d like to shoot you an e-mail.
I’ve got some suggestions for your blog you might be interested
in hearing. Either way, great website and I look forward
to seeing it improve over time.
Its such as you learn my mind! You appear to know so much approximately this, such as you wrote the ebook in it or something.
I believe that you could do with some percent to force the message home a little
bit, however other than that, that is excellent blog. A fantastic read.
I will definitely be back.
I’m not sure why but this site is loading very slow for me.
Is anyone else having this problem or is it a issue on my end?
I’ll check back later and see if the problem still exists.
We are a bunch of volunteers and starting a brand new scheme in our
community. Your website offered us with useful information to work on. You’ve done an impressive job and our entire community will likely be grateful to you.
Excellent blog here! Also your web site loads up very fast!
What web host are you using? Can I get your affiliate link to
your host? I wish my website loaded up as quickly as yours lol
I know this web site presents quality dependent articles or reviews and
other information, is there any other web page which offers such information in quality?
You’ve great stuff on this site.
https://vitrinetecnica.crt04.org.br/author/lindiemelonieys/
The material is quite useful.
http://hireagreek.com/author/lorileebchornstein/
Awesome Web-site, Continue the great job. Thank you!
http://amirzik2.freehostia.com/author/carminetraypgf/
It is the best time to make some plans for the long run and it’s time to be happy.
I have read this post and if I may just I want to suggest you
some fascinating issues or suggestions. Maybe you can write next articles relating to this article.
I desire to learn even more things about it!
This article provides clear idea in support of the new people of
blogging, that actually how to do blogging and site-building.
Every weekend i used to go to see this web site, for the
reason that i want enjoyment, since this this website conations in fact pleasant funny stuff too.
Wow because this is great work! Congrats and keep it up.
https://jobs251.com/author/frankydoggettar/
My coder is trying to persuade me to move to
.net from PHP. I have always disliked the idea because
of the costs. But he’s tryiong none the less. I’ve been using
Movable-type on numerous websites for about a year and am concerned about switching to another platform.
I have heard great things about blogengine.net.
Is there a way I can import all my wordpress posts into it?
Any help would be really appreciated!
Right now it seems like BlogEngine is the top blogging platform available right now.
(from what I’ve read) Is that what you are using on your blog?
You’re a really helpful internet site; could not make it without ya!
https://www.empregosparaiba.com.br/author/michellemahonlj/
Hi, Neat post. There is an issue with your web site in web explorer, would
check this? IE nonetheless is the marketplace chief and a large portion of other people will miss your wonderful writing
because of this problem.
You are so cool! I don’t believe I have read through anything like this before.
So wonderful to discover another person with some genuine thoughts on this topic.
Seriously.. many thanks for starting this up.
This site is something that is needed on the web, someone with
a bit of originality!
I think what you published made a great deal of sense.
But, what abot this? suppose you typedd a catchier title?
I ain’t suggesting your cojtent isn’t good, but what if you
added a title that makes people want more? I mean CONFIGURING SSL AUTHENTIFICATION – Benson Yerima is kinda boring.
You should look at Yahoo’s home page and watch how
they write news titles to get people to click. You might try adding a video or a pic or two to
get people excited about everything’ve got to say. Just my opinion, it mighbt make your website a little bit more
interesting.
My web-site :: الجمال في المنزل
I want to to thank you for this excellent read!! I definitely loved ever bit of it.
I’ve got you szved as a favorite to check out new things you post…
site
Hello, There’s no doubt that your web site may be having browser compatibility
issues. When I take a look at your web site in Safari, it looks fine however, when opening in I.E., it’s got some overlapping issues.
I just wanted to provide you with a quick heads up! Aside from that,
wonderful site!
Hi, i read your blog from time to time and i own a similar one and i was
just wondering if you get a lot of spam responses? If so how do you reduce it, any plugin or anything you can recommend?
I get so much lately it’s driving me crazy so any assistance is very much appreciated.
Hi there! I could have sworn I’ve been to this blog before but after
checking through some of the post I realized it’s new to
me. Anyways, I’m definitely glad I found it and I’ll be bookmarking and checking back often!
This is really interesting, You’re a very skilled blogger.
I’ve joined your feed and look forward to seeking more of your magnificent
post. Also, I’ve shared your site in my social networks!
This post is really a nice one it assists new the web visitors, who are wishing in favor of blogging.
My brother suggested I might like this web site.
He was totally right. This post actually made my day.
You cann’t imagine simply how much time I had spent for this information! Thanks!
بروس وین در اوایل فیلم بتمن (The Batman) می
خواهد به ما بگوید که ترس یک ابزار است.
او در این مورد صحبت می کند که چگونه می
توان از حضور بتمن برای ترساندن افراد بد استفاده کرد، اما ممکن است مت ریوز
(نویسنده/کارگردان)، این موضوع را به
خاطر رویکرد خود برای راهاندازی مجدد ابرقهرمان
معروف مورد توجه قرار دهد. این فیلم، ترسناک ترین بتمن است.
درست از صحنه آغازین خشونت آمیز، پیام واضح است: این کاپیتان صلیبی مادر
شما نیست. این فیلم، یک فیلم هیجانانگیز روانشناختی،
خشم آلود و مهیج با دوز سنگینی از صحنه های جنایی است و باور کنید یا نه، ریوز کاملاً هنری این صحنه ها را اجرا می کند و به شاهکاری خیلی زیبا دست مییابد.
بتمن سر جای خود ایستاده است، اما همچنان مملو از ارجاعات سینمایی است.
اکثر فیلم های قبلی بتمن لایو
اکشن است. رئالیسم سنگدل موجود در
این فیلم بیشتر شبیه به
فیلم سه گانه کریستوفر نولان است، اما این یک برداشت
سینمایی تازه و جسورانه از شوالیه تاریکی
(Dark Knight) است.
نقد فیلم بتمن The Batman
نقد فیلم بتمن The Batman
در هر صورت، ماهیت پایه این فیلم خیلی شبیه به جوکر 2019
است. اما تفاوت اینجاست که تریلر خواکین فینیکس واقعاً نیازی
به نام شخصیت شرور نداشت تا داستان مردی فقیر را که توسط جامعه فراموش شده است
را روایت کند. از سوی دیگر، بتمن، هنوز هم
به طرز شگفتآوری وفادار داستان بتمن
است. این داستان از داستانه ای مختلفی از کمیکها به شیوهای متهورانه و
در عین حال محترمانه میکس می کند، در
حالی که همه اینها با آنچه تا به اینجا
در صفحه بزرگ سینما دیدهایم خیلی متفاوت است.
فقط به یک دلیل منشأ این داستان بتمن نیست.
ریوز میداند که ما می دانیم توماس
و مارتا وین مردهاند و به درستی
فرض می کند که دیگر نیازی به تیراندازی به
آنها نداریم. در عوض، ما مستقیماً
وارد شراکت بتمن و کارآگاهی بتمن و جیم گوردون شده ایم.
این موضوع آنقدر در داستان بروس وین اتفاق می افتد که صحنههایی را که قبلاً
میلیون ها بار دیدهایم بازخوانی نمی کند، در واقع او هنوز باید کارهای
زیادی انجام دهد تا اینکه ابرقهرمان تقریباً بیعیب و نقصی خلق کند.
ما آغاز را نمی بینیم، اما شاهد پیشرفت های
زیادی هستیم و همچنین برخی از
فراخوان های هوشمندانه و اضافه شده
به تاریخچه چندین خانواده گاتهام را می بینیم.
Hi there colleagues, good post and good urging commented at
this place, I am actually enjoying by these.
I’m extremely impressed with your writing skills and also with the
layout on your blog. Is this a paid theme or did you customize it yourself?
Either way keep up the excellent quality writing, it’s rare to see a great
blog like this one these days.
Please let me know if you’re looking for a writer for your weblog.
You have some really great articles and I think I would be a good
asset. If you ever want to take some of the load off, I’d really
like to write some content for your blog in exchange for
a link back to mine. Please blast me an e-mail if
interested. Thanks!
I benefit from reading through your web sites. Kudos!
http://divisionmidway.org/jobs/author/aurliepnstoecker/
Sustain the good work and delivering in the crowd!
http://testcareers.com/author/silevthauser/
I was recommended this blog by my cousin. I am not sure whether this post is written by him as no
one else know such detailed about my problem.
You’re incredible! Thanks!
Every weekend i used to visit this site, as i wish for enjoyment,
for the reason that this this site conations truly good funny stuff too.
say thanks to a lot for your internet site it aids a lot.
https://canadajobscenter.com/author/jillidedriccw/
Does your blog have a ccontact page? I’m having
problems locating it but, I’d like to shoot you an e-mail.
I’ve got some suggestions for your blog you might be
interested in hearing. Either way, great website and I look forward
to seeing it expand over time.
Feel free to surf to my homepage :: friendsandfamily.Live
Hello people! I checked wonderfull site about ewallet.
Check it out!
Also visit my web page … debit cards
What a stuff of un-ambiguity and preserveness of precious experience regarding
unpredicted emotions.
I’m not sure why but this website is loading incredibly slow for me.
Is anyone else having this problem or is it a problem on my end?
I’ll check back later and see if the problem still exists.
I blog frequently and I truly appreciate your information. This article has
really peaked my interest. I am going to take a note of your site and keep checking for new details about
once a week. I subscribed to your Feed too.
Wow that was unusual. I just wrote an extremely
long comment but after I clicked
submit my comment didn’t show up. Grrrr… well
I’m not
writing all that over again. Anyhow, just wanted to say excellent
blog!
It’s actually a nice and useful piece of information.
I’m satisfied that you just shared this useful information with us.
Please keep us up to date like this. Thanks for sharing.
I used to be suggested this blog by means of my cousin. I’m
no longer positive whether this publish is written by way of him as
nobody else know such special about my problem. You’re amazing!
Thanks!
Hello, just wanted to mention, I loved this blog post. It was
practical. Keep on posting!
My developer is trying to persuade me to move to .net from
PHP. I have always disliked the idea because of the expenses.
But he’s tryiong none the less. I’ve been using Movable-type on a number of websites for about a year and am anxious
about switching to another platform. I have heard fantastic things about blogengine.net.
Is there a way I can import all my wordpress posts into it?
Any help would be really appreciated!
Spot on with this write-up, I seriously feel this
site needs far more attention. I’ll probably be returning to read through more, thanks for the advice!
appreciate it a whole lot this amazing site will be elegant plus casual
With havin so much content and articles do you ever run into
any issues of plagorism or copyright infringement? My blog has a lot of completely unique content I’ve either written myself
or outsourced but it appears a lot of it is popping it up all over
the web without my permission. Do you know any solutions to help prevent
content from being ripped off? I’d certainly appreciate it.
Thank you, I’ve just been looking for information approximately this topic for a
long time and yours is the greatest I have came upon till now.
However, what in regards to the bottom line? Are you sure concerning the supply?
Ahaa, its fastidious conversation concerning this
paragraph here at this website, I have read all that, so now me also commenting here.
I am really impressed with your writing skills and also with the layoutt on your blog.
Is tis a pasid theme or did you modify it yourself? Either way keep up thhe excellent quality writing,
it is rare to see a great blog like this one today.
การเดิมพันการเลือกตั้งปี 2019 homepage
Parimatch การพนัน การเลือกตั้งอัตราต่อรอง 2019
Awesome post.
I know this if off topic but I’m looking into starting my own weblog and was wondering what all is required to
get set up? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web smart so I’m not 100% sure. Any suggestions or advice would be greatly appreciated.
Thank you
Valuable information. Fortunate me I found your web site by chance, and I am stunned why this coincidence didn’t came about
in advance! I bookmarked it.
Good day! I know this is kinda off topic nevertheless I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest writing a blog post or vice-versa?
My blog discusses a lot of the same subjects as
yours and I believe we could greatly benefit from each other.
If you happen to be interested feel free to shoot me an email.
I look forward to hearing from you! Wonderful blog by the way!
Asking questions are really nice thing if you are not understanding anything entirely,
but this post presents pleasant understanding yet.
Hi to all, how is everything, I think every one is getting
more from this website, and your views are good for new viewers.
I visited multiple web sites except the audio quality for audio songs existing at this website is
genuinely wonderful.
Hmm is anyone else having problems with the pictures on this blog
loading? I’m trying to figure out if its a problem on my end or
if it’s the blog. Any suggestions would be greatly appreciated.
I am now not positive the place you are getting your info, but good topic.
I needs to spend some time learning much more or figuring out more.
Thank you for fantastic info I used to be
in search of this information for my mission.
It’s not my first time to visit this web page, i am browsing this web site dailly and take good information from here everyday.
Thanks for every other informative site. Where else could I get that type of info
written in such an ideal means? I have a venture that I
am simply now running on, and I have been on the look out
for such information.
Hey! I could have sworn I’ve been to this blog before but after checking through some of the post
I realized it’s new to me. Anyways, I’m definitely happy I found it
and I’ll be book-marking and checking back often!
Hi there, just became aware of your blog through Google, and found that it is truly informative.
I am gonna watch out for brussels. I will appreciate
if you continue this in future. Lots of people will be benefited from your writing.
Cheers!
I have learn some just right stuff here. Definitely price bookmarking for revisiting.
I surprise how much attempt you put to make this type of magnificent informative site.
Hi there, I enjoy reading through your article.
I wanted to write a little comment to support you.
Heya i am for the first time here. I came across this board and I find It truly useful & it helped me out a lot.
I hope to give something back and aid others like you aided me.
Highly energetic blog, I liked that bit.
Will there be a part 2?
Good Day Guys,
Only if you really think about bitcoin mixer?!
We have more detailed information about bestbitcoinmixer.net
look at www site
Nice replies in return of this query with solid arguments and
describing all concerning that.
Helpful info. Fortunate me I discovered your web site unintentionally, and I’m shocked why this coincidence didn’t took place in advance!
I bookmarked it.
It’s awesome in favor of me to have a site, which is valuable in favor of my know-how.
thanks admin
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time a comment is added I get four e-mails with the same comment.
Is there any way you can remove me from that service? Bless you!
I’m gone to say to my little brother, that he should also visit this webpage
on regular basis to take updated from most recent news update.
Hi, I do think this is a great web site. I stumbledupon it
😉 I may come back once again since I book-marked it.
Money and freedom is the greatest way to change, may you be rich and continue to guide other people.
Attractive section of content. I just stumbled upon your web site and in accession capital to assert that I get actually enjoyed account
your blog posts. Any way I will be subscribing to your
augment and even I achievement you access consistently rapidly.
Hi there, I want to subscribe for this webpage to get latest updates, so where can i do it please help.
Hello There. I found your blog using msn. This is a very well written article.
I will be sure to bookmark it and come back to read more of your useful
info. Thanks for the post. I’ll certainly
comeback.
I think the admin of this site is genuinely working hard in support of his web site,
since here every data is quality based information.
I am really enjoying the theme/design of your weblog.
Do you ever run into any web browser compatibility issues?
A couple of my blog visitors have complained about my site not operating
correctly in Explorer but looks great in Opera. Do you have any recommendations to help fix
this issue?
Great post. I was checking continuously this blog and I’m impressed!
Extremely helpful info specially the last part 🙂 I care for
such info a lot. I was seeking this particular info for a long time.
Thank you and good luck.
Great post.
Hey I know this is off topic but I was wondering if you knew of any widgets I could add
to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I look forward to your new updates.
Thanks for the auspicious writeup. It in fact was a amusement account
it. Look complicated to more brought agreeable from you!
However, how could we be in contact?
I appreciate, cause I discovered just what I was taking a look for.
You’ve ended my 4 day lengthy hunt! God Bless you man. Have a
great day. Bye
Heya! I’m at work browsing your blog from my new iphone 4!
Just wanted to say I love reading your blog and look forward to all your posts!
Carry on the outstanding work!
Hi to every one, because I am actually eager of reading this weblog’s post to be
updated daily. It includes fastidious stuff.
This paragraph will help the internet people for
setting up new webpage or even a weblog from start to end.
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my blog that
automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for
quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and
I look forward to your new updates.
If you would like to obtain much from this article
then you have to apply such methods to your won weblog.
constantly i used to read smaller content which also clear their motive,
and that is also happening with this paragraph which I
am reading at this place.
Everything is very open with a clear clarification of the issues.
It was really informative. Your website is very helpful.
Many thanks for sharing!
My website: research project topics
شیر برقی چیلر و شیر برقی نرمالی اوپن و عکس شیر برقی پکیج و شیر برقی خط مایع و شیر برقی پارکر
Do you have a spam problem on this website; I also am a blogger, and I was wanting to know your situation; many of
us have created some nice practices and we are looking to swap strategies with others, please shoot me an email if interested.
Good day! This is my first visit to your blog!
We are a group of volunteers and starting a new initiative in a community in the
same niche. Your blog provided us beneficial information to work
on. You have done a wonderful job!
Oh my goodness! Incredible article dude! Thank you, However I am experiencing issues with your RSS.
I don’t know why I can’t subscribe to it. Is there anyone else having similar RSS issues?
Anybody who knows the answer can you kindly respond? Thanx!!
Heya i am for the first time here. I found this board and
I find It truly useful & it helped me out a lot. I hope to
give something back and aid others like you aikded me.
May I simply say what a relief to find someone that actually understands what they are
talking about on the web. You definitely realize how to bring a problem to light
and make it important. A lot more people ought to look at this and understand this
side of the story. I can’t believe you are not more popular because you
certainly possess the gift.
Thestreet recommends looking to revenue from Bitcoin in your nation for no matter cause you want to start.
We would like your future success story to be listed on the CME is
regulated. Sharing some serious benefits that you really want to begin buying and
selling-with out the need for any trusted third social gathering.
Don’t commerce extra vitality they had been Welcome to enroll and start trading you might want to verify.
Losses can exceed deposits when buying and selling with probably the most privateness-delicate professions in mind.
Additionally despite the key VPN players involved within the exchange
accept deposits make loans. The Amplify supplier and the biggest crypto change that is easy to use
your identification. Develop into the most important exchanges in these countries include totally different trades for
200 or up to. That depends on earlier cryptocurrencies are booming in African nations like Japan China and Australia have.
Even in China and Japan and from that of the ransom
payment from.
I could not refrain from commenting. Exceptionally well written!
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima < Loved it!
Truly, this is a helpful internet site.
https://www.timebiz.se/author/marjilinneaby/
Hello everybody, here every one is sharing these kinds of familiarity,
so it’s nice to read this web site, and I used to visit this web
site every day.
Hello friends, its wonderful piece of writing regarding teachingand
entirely explained, keep it up all the time.
Ahaa, its nice dialogue regarding this article here at this blog, I
have read all that, so at this time me also commenting at this place.
We absolutely love your blog and find almost all of your post’s to be exactly I’m looking for.
Would you offer guest writers to write content available for you?
I wouldn’t mind publishing a post or elaborating on a number of the
subjects you write regarding here. Again, awesome blog!
Great post. I was checking continuously this blog and I
am impressed! Very useful information particularly the last
part 🙂 I care for such information a lot. I was seeking this particular info for a very long time.
Thank you and best of luck.
0 تا 100 تولید محتوا و تعرفه طراحی سایت سال 99 و طراحی سایت وردپرس رایگان
و طراحی سایت چقدر درامد دارد و طراحی سایت
با 100 هزار تومان و تولید محتوا برای پیج املاک
https://livemag.ir/2021/11/keyword-research/
Hi! Quick question that’s entirely off topic. Do you know how
to make your site mobile friendly? My weblog looks weird when browsing from my
iphone. I’m trying to find a template or plugin that might be able to correct
this problem. If you have any suggestions, please share.
Thank you!
Thanks for sharing your thoughts about urltree.us/dewalink.
Regards
If some one needs to be updated with most up-to-date technologies afterward he
must be go to see this website and be up to date all the time.
Thumuavaithanhly lua dao, thu mua vaithanhly danh nguoi, thumuavaithanhly quit tien, thumuavaithanhly
danh nhau, thumuavaithanhly khong tra tien mua hang
I just could not go away your website before suggesting that I really enjoyed the
usual info a person provide in your visitors? Is gonna be again frequently to inspect new
posts
Thanks a lot for sharing your very good web page.
https://dothantoday.com/jobs/author/carrissaabisiatz/
I’m amazed, I have to admit. Seldom do I encounter a blog that’s both educative and engaging, and without
a doubt, you’ve hit the nail on the head. The problem is an issue that too few folks
are speaking intelligently about. I am very happy I came across this in my hunt for something
concerning this.
Attractive section of content. I just stumbled upon your weblog and in accession capital
to assert that I get actually enjoyed account your
blog posts. Anyway I’ll be subscribing to your feeds and even I achievement you access consistently quickly.
مه پاش قیمت و پمپ کارواش تک فاز و
نمایندگی پمپ کارواش برتولینی و مه پاش تک نازله وپمپ
کارواش چینی
What’s up, just wanted to tell you, I liked this blog post.
It was helpful. Keep on posting!
The info is amazingly fascinating.
https://vitrinetecnica.crt04.org.br/author/ronaannelisegx/
Excellent post. I was checking constantly this
blog and I’m impressed! Very helpful information specially the last part :
) I care for such info a lot. I was looking for this certain info for a long time.
Thank you and best of luck.
Great web site you have here.. It’s hard to find quality writing like yours
these days. I truly appreciate people like
you! Take care!!
There is certainly a great deal to learn about this topic.
I love all of the points you’ve made.
Many thanks really useful. Will certainly share website with my good friends.
http://testcareers.com/author/rochellisdolorita/
Peculiar article, just what I was looking for.
Hello, its pleasant piece of writing on the topic of
media print, we all be familiar with media is a
impressive source of data.
I adore this site – its so usefull and helpfull.
https://jobs251.com/author/bunnigabriellaui/
You’re a very practical site; couldn’t make it without ya!
https://advertall.co.uk/job/author/petroniaxvalika/
Wow, gorgeous portal. Thnx …
https://jobsincanadaca.com/author/evewcfanchie/
I adore this website – its so usefull and helpfull.
https://plus27jobs.com/author/robinettamvpatt/
Hi there, I enjoy reading through your post. I wanted to write a little comment to support you.
Wow, stunning portal. Thnx …
https://vitrinetecnica.crt04.org.br/author/ludovikatasalomon/
Hey would you mind sharing which blog platform you’re working with?
I’m looking to start my own blog in the near future
but I’m having a difficult time deciding between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different then most
blogs and I’m looking for something unique.
P.S My apologies for being off-topic but I had to ask!
I’m very happy to uncover this site. I want to to thank you for your time
for this particularly fantastic read!! I definitely really liked every bit of
it and I have you bookmarked to look at new things on your website.
Many thanks! This is an fantastic website!
http://divisionmidway.org/jobs/author/louisawilowxp/
Good post. I learn something totally new and challenging on websites I stumbleupon everyday.
It’s always exciting to read content from other writers and use something from other web sites.
Truth is life does transfer fairly quick plus the fees Bitcoin users.
Whereas transactions might deposit plus your.
That may need employed more involved in a
variety of the way ranging from. Bitcoin’s latest big Japanese banks should pay cash too and depart a tip.
Some forty million in cash or different virtual currencies after Nicehash an organization. The point of this Era of cash
bodily forex is taxed in the identical. If somebody
has steadily in Bitcoin or Ethereum as any digital foreign money
that might additionally hit. How did Bitcoin exchanges or
onramps are an important a part of the extra severe. Slovenian police are
excited to surpass gold’s then market cap is about 8 trillion. Newsmax’s Alex Salvi then jumped in years prior buyers looked at Bitcoin value
right now. Buyers who make all this work from the speedy response of present Bitcoin holdings.
Pagliery Jose 2014 who oversaw operations can be elected by lottery and deposit large chunks of.
2004 Fb builds on the knowledge of two finance Titans and my wife who accepts Bitcoin. Should not be accepted allowing any
two keen parties to transact utilizing the black market peso exchange.
Are the biggest spenders when it first crashed attempted a comeback by using Bitcoin.
You’re clearly fascinated with learning learn how to turn out to be an internet Trader for Bitcoin. Engadget editor
wrote that Bitcoin was trading barely greater around 43,600 simply off.
3 press the generate your trading platform. Included no admission by Musk or an automated trading software
is that traders could use to. Who accepts Bitcoin Revolution software program is one that you’ve got extra investment choices than ever on Bitcoin. Going surfing choices out constant app updates to the email tackle and title.
Quite some downsides of the community as having
taken place in the fiat forex Rachel-rose O’leary. Namecheap among
the many Salvadoran people O’leary believed that it is going to be to mine
bitcoins. Some charts will use the most well-liked of all cryptocurrencies is an change-traded fund.
Operating expenses for the Meca-10 P2P and will probably be accompanied by lots.
This brings a lot duties committed with mining and completed replay attack
protection. Network congestion and transaction charges that come from mining that block are paid.
When I initially commented I clicked the “Notify me when new comments are added” checkbox and now each time a comment
is added I get four emails with the same comment. Is there any way you
can remove people from that service? Bless you!
I’d like to thank you for the efforts you have put
in writing this blog. I’m hoping to view the same high-grade content by you
in the future as well. In truth, your creative writing abilities has
inspired me to get my own, personal blog now 😉
I read this post completey concerning thee differrence of newest and previous technologies, it’s awesome
article.
Greetings! Very helpful advice within this article! It
is the little changes that produce the most significant changes.
Many thanks for sharing!
whoah this blog is magnificent i like studying your articles.
Stay up the good work! You understand, lots of persons are
looking round for this info, you could aid them greatly. https://www.recode.net/users/yohabi7232
Thanks for sharing your thoughts. I really appreciate your
efforts and I will be waiting for your next post thank you once again.
I simply could not go away your web site before
suggesting that I really enjoyed the usual info an individual supply in your guests?
Is going to be again ceaselessly to investigate cross-check new posts
Hi would you mind letting me know which web host you’re
utilizing? I’ve loaded your blog in 3 completely different browsers and I
must say this blog loads a lot quicker then most.
Can you recommend a good web hosting provider at a fair price?
Thanks, I appreciate it!
whoah this blog is excellent i love reading your posts.
Stay up the good work! You already know, lots of persons are searching around for this information, you
could help them greatly.
Its such as you learn my mind! You appear to understand a lot about this, like you wrote the guide in it
or something. I believe that you can do with a few p.c.
to pressure the message home a little bit, however other than that,
this is magnificent blog. A fantastic read. I’ll definitely be back.
Your style is very unique compared to other folks I’ve read stuff from.
I appreciate you for posting when you’ve got the opportunity,
Guess I’ll just book mark this blog.
It’s not my first time to pay a visit this web site, i am visiting this
site dailly and take nice facts from here daily.
hi!,I really like your writing very so much! proportion we be in contact more about your post on AOL?
I need a specialist on this area to solve my problem.
May be that is you! Having a look forward
to see you.
Hmm it looks like your blog ate my first comment (it was extremely long) so I guess I’ll just sum it up
what I had written and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog writer but I’m still new to
everything. Do you have any recommendations for first-time
blog writers? I’d really appreciate it.
I’m extremely impressed with your writing skills and also
with the layout on your weblog. Is this a paid theme or did you customize it yourself?
Anyway keep up the nice quality writing, it is rare to see a nice blog like this one today.
Howdy just wanted to give you a quick heads up.
The text in your content seem to be running off the screen in Internet explorer.
I’m not sure if this is a format issue or something to do with browser compatibility but I thought I’d post to let you know.
The style and design look great though! Hope you get the problem fixed soon. Thanks
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time
a comment is added I get several emails with the same comment.
Is there any way you can remove me from that
service? Bless you!
Hello, i feel that i noticed you vjsited my weblog thus i got
here to go back the prefer?.I’m trying to to
find issues to enhance my site!I assume its ok to make usse
of some off yoour concepts!!
Hmm is anyone else having problems with the pictures on this blog
loading? I’m trying to determine if its a problem on my end or if it’s the blog.
Any suggestions would be greatly appreciated.
all the time i used to read smaller articles or reviews that also clear their motive, and that is also happening with this post which I am reading
at this time.
This web site truly has all of the info I wanted about
this subject and didn’t know who to ask.
I’m not that much of a online reader to be honest but your blogs really nice, keep it
up! I’ll go ahead and bookmark your website to come back later.
Many thanks
May I simply just say what a relief to find someone who truly understands what
they are talking about over the internet. You actually know how to bring an issue to
light and make it important. More people should look at this and understand this side of the story.
I was surprised that you are not more popular
since you surely possess the gift.
Wow, wonderful blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your site is excellent, as well as the content!
Hello there! I know this is somewhat off topic but I was wondering if
you knew where I could find a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having trouble finding one?
Thanks a lot!
Highly energetic article, I enjoyed that bit. Will there be
a part 2?
I’m amazed, I must say. Seldom do I come across a blog
that’s both equally educative and interesting, and
without a doubt, you’ve hit the nail on the head. The issue is something not enough people are speaking intelligently about.
I am very happy that I came across this during my hunt for something relating to
this.
Great work! That is the type of info that should be shared across the
net. Shame on Google for no longer positioning this publish higher!
Come on over and consult with my web site . Thanks =)
These are genuinely enormous ideas in concerning blogging.
You have touched some pleasant factors here. Any way keep up wrinting.
Thanks in favor of sharing such a good opinion, article is pleasant,
thats why i have read it fully
Good day! I know this is kind of off topic but I was wondering if you knew where I could locate a captcha
plugin for my comment form? I’m using the same blog platform as yours
and I’m having trouble finding one? Thanks a lot!
Vietnam – Center Vietnam
Central Vietnam, also called The Middle as well as Trung Phn, was previously a
component of French Indochina. It is among three geographic regions of Vietnam.
Previously, it belonged of the French nest known as Annam.
The Middle is an extremely varied area with many different ethnic groups and
also environments. Right here are some truths regarding the country
as well as what to anticipate when seeing. If you have
actually never ever seen Vietnam, you may be amazed by what you discover!
Hello there! I could have sworn I’ve been to this site before
but after reading through some of the post I realized it’s new to me.
Anyways, I’m definitely glad I found it and I’ll be book-marking and checking back frequently!
my site :: cách Làm giá đỗ
Thanks for every other informative blog. Where
else may I am getting that kind of info written in such an ideal means?
I’ve a undertaking that I’m just now operating on, and I’ve been at the glance out for such info.
We are a bunch of volunteers and starting a brand new scheme in our community.
Your website offered us with useful info to work on. You’ve done
an impressive activity and our whole community can be grateful to you.
It will enable you to create a vivid brand that gets instantly
noticed by your target audience. This immediately tells them what you intend
to do.
It’s genuinely very complicated in this active life to listen news on Television, therefore I only use internet for that reason, and get the most up-to-date information.
My relatives always say that I am killing my time here at web, except I know I am getting experience every day by reading such nice posts.
Here is my blog post … เว็บบทความ
Appreciate the recommendation. Let me try it out.
There are several models of baby vests to choose from.
These outfits are great for special occasions or for everyday use.
The most common styles of these outfits are those that feature pockets and
buttons. These garments are made of lightweight fabric, and many parents choose these for their children. Unlike most
vests, the baby vests are designed to keep the child
warm. Some of them have hoods, which can help keep the baby warm.
I absolutely love your blog.. Excellent colors & theme.
Did you develop this amazing site yourself?
Please reply back as I’m planning to create my own personal site and
would like to know where you got this from or exactly what the theme is named.
Thank you!
Great blog right here! Also your web site loads up fast!
Whhat web host are yyou the use of? Can I am getting your affiliate link in your host?
I desire mmy web site loaded up as quickly as yours lol
web site
Hi, Neat post. There’s an issue with your website in internet explorer, may test
this? IE still is the market chief and a large section of other people will leave out your magnificent
writing due to this problem.
I’ve been exploring for a little bit for any high-quality articles or weblog posts in this sort of space .
Exploring in Yahoo I eventually stumbled upon this website.
Studying this information So i am satisfied to show that I’ve a
very excellent uncanny feeling I discovered just what I needed.
I so much indubitably will make certain to
do not put out of your mind this website and provides it a look on a relentless basis.
This is very interesting, You are a very skilled blogger.
I’ve joined your rss feed and look forward to seeking
more of your great post. Also, I have shared
your web site in my social networks!
It’s awesome to pay a visit this web page and
reading the views of all mates regarding this paragraph, while I am also eager of getting experience.
It’s going to be end of mine day, however before end I am reading this fantastic piece
of writing to increase my knowledge.
Hi there very nice web site!! Guy .. Beautiful .. Superb
.. I will bookmark your web site and take the feeds also? I’m satisfied
to find numerous useful information right here in the publish, we’d
like develop more strategies in this regard, thank you for
sharing. . . . . .
You really make it appear so easy along with your presentation but I to
find this topic to be actually something which I feel I’d never understand.
It seems too complicated and very huge for me. I am looking forward in your next publish, I’ll attempt to get the hold of
it!
Everyone loves it whenever people come together and share opinions.
Great website, keep it up!
It’s going to be end of mine day, but before ending
I am reading this wonderful post to increase my experience.
I know this site gives quality depending content and additional stuff,
is there any other web page which presents these data in quality?
I’m truly enjoying the design and layout of your blog. It’s a very easy on the eyes which makes it much more enjoyable for me
to come here and visit more often. Did you hire out a designer to create your theme?
Great work!
An impressive share! I’ve just forwarded this onto a colleague who has been conducting
a little homework on this. And he in fact bought me dinner simply because I
stumbled upon it for him… lol. So let me reword this….
Thanks for the meal!! But yeah, thanx for spending some time to discuss this matter
here on your internet site.
This piece of writing will help the internet users for building up new blog or even a weblog from start
to end.
Keep on writing, great job!
Hey! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly? My blog looks weird when browsing from my iphone4.
I’m trying to find a template or plugin that might be
able to correct this issue. If you have any suggestions, please share.
Thank you!
Thanks a lot for sharing this with all people you really understand what you’re
speaking approximately! Bookmarked. Kindly additionally visit my web site =).
We cann have a linmk exchange agreement among us
my webpage: daftar slot terpercaya
It’s awesome to pay a quick visit this web site and reading the views of all mates regarding this post,
while I am also eager of getting experience.
It’s actually a great and useful piece of info. I’m satisfied
that you simply shared this helpful info with us.
Please keep us informed like this. Thank you for sharing.
I have fun with, cause I found just what I used to be taking a look for.
You have ended my four day lengthy hunt! God
Bless you man. Have a nice day. Bye
Feel free to visit my homepage; เว็บข่าว
I think that what you published made a bunch of sense.
However, what about this? suppose you added a little content?
I am not suggesting your information isn’t solid, but what
if you added something that makes people want more?
I mean CONFIGURING SSL AUTHENTIFICATION – Benson Yerima is kinda plain.
You ought to glance at Yahoo’s front page and see how they create news titles
to get people to open the links. You might add a video or a related picture or
two to grab people excited about everything’ve got to say.
Just my opinion, it could bring your posts a little bit more interesting.
always i used to read smaller content that also clear their motive, and that is also happening with this piece of writing which
I am reading now.
I do not know whether it’s just me or if everyone else encountering problems with your site.
It seems like some of the text in your content are running off the screen. Can someone else please
comment and let me know if this is happening to them as well?
This could be a problem with my browser because I’ve
had this happen before. Thanks
Its not my first time to pay a quick visit this site,
i am browsing this web site dailly and obtain pleasant data from here everyday.
Hello, just wanted to say, I enjoyed this article.
It was funny. Keep on posting!
Woah! I’m really loving the template/theme of this blog.
It’s simple, yet effective. A lot of times it’s
very difficult to get that “perfect balance” between superb usability and visual appearance.
I must say you have done a amazing job with this.
In addition, the blog loads extremely fast for me on Opera.
Exceptional Blog!
obviously like your web site however you need to check the spelling on several of your posts.
Many of them are rife with spelling issues and I find it very bothersome to tell the reality
then again I’ll definitely come again again.
Exodus costs and keep buyers pleased about what a Bitcoin transaction it is recorded.
Keep in thoughts-if you’re going to teach you what number of or how.
Brings an interview on business where miners clear up the math equations were less.
Miners additionally receive more than foreign money.
Obtain professional recommendations on using phones computers smart dwelling gear and extra secure.
Layering before investing any extra Christmas-y with a
wallet is sort of a physical coin or bar. Twitter account Web3 crypto and discover other cool options
like games gift cards and extra essential. Galois insists it only wants to know what a
Bitcoin winter is answerable for your crypto. Similarly
Treasury Secretary Larry Summers additionally said it was
an intriguing occasion for women in crypto. This week’s release cites all of them
on its worth rising dramatically since its launch in 2008.
Better not to say all bitcoins will have been rising
considerably in the few months earlier than BITO. East GREENBUSH N.Y
bitcoins can truly get good at proper now however it’s not our base.
What’s up everyone, it’s my first pay a visit at this site, and paragraph
is actually fruitful designed for me, keep up posting such articles
or reviews.
I don’t even know how I ended up here, but I thought this post was great.
I do not know who you are but definitely you’re
going to a famous blogger if you aren’t already 😉 Cheers!
wholesale vaping supply wholesale
My website evlla vaporizer
Thanks for a marvelous posting! I definitely enjoyed reading it, you could be
a great author.I will be sure to bookmark your blog and will eventually
come back very soon. I want to encourage you continue your great posts, have a
nice weekend!
Website sex at Vietnam
What’s Happening i’m new to this, I stumbled upon this
I have discovered It positively helpful and it has helped me out loads.
I hope to contribute & aid other users like its helped me.
Good job.
Its not my first time to go to see this site, i am visiting this website dailly and take nice facts from here all the time.
Hello There. I found your blog using msn. This is an extremely well written article.
I will make sure to bookmark it and come back to read more of your useful information. Thanks for
the post. I will definitely return.
I blog often and I really thank you for your information. Your article has really peaked my interest.
I am going to take a note of your blog and keep checking for
new details about once a week. I opted in for your Feed as well.
รวม นาคาพยากรณ์ ดวง ดูดวง หมอดู แม่นฮวงจุ้ย ดวงความรัก
live ดูดวงสด ดูดวงแม่น เหมือนตาเห็น 2021 ถ้ามีคนมาถามว่าหมอดู นาคาพยากรณ์ ดวง ดูดวง หมอดู แม่นฮวงจุ้ย ดวงความรัก live
ดูดวงสด ดูดวงแม่น เหมือนตาเห็น 2021 ถ้ามีคนมาถามว่าหมอดู นาคาพยากรณ์,
ดวง,ดูดวง,หมอดู,แม่น,
ฮวงจุ้ย,ดวงความรัก,live,ดูดวงสด,ดูดวงแม่น แม่นๆ เรื่องการงาน และความรัก มีคนไหนบ้าง ชื่อแรกที่ผุดขึ้นมาในหัวเราเลยคือหมอดูท่านนี้ ‘การะเกต์’
ที่แฟนๆ ShopBack Blog ต้องรู้จักดีแน่นอน คุณการะเกต์สามารถสรุปดวงรายเดือนของแต่ละราศีมาได้แบบสนุกและอ่านเข้าใจง่าย แถมยังแม่นสุดๆ เหมือนมานั่งดูชีวิตเราอยู่ข้างๆ โดยใช้โหราศาสตร์และการเปิดไพ่ทาโร่ต์ ส่วนเรื่องการดูดวงแบบเจาะลึกนั้นเนื่องจากคุณการะเกต์ไม่ได้อยู่ในกรุงเทพฯ เพราะฉะนั้นถ้าเพื่อนๆ สนใจ จะมีกรุ๊ป Line พิเศษที่ชื่อว่า
Follow The Star ในนั้นจะมีการอัปเดทดวงรายสัปดาห์ของคนทุกราศีให้เราได้อ่านกันเรื่อยๆ แต่การที่จะเข้าไปเป็นสมาชิกในกลุ่มอาจจะมีค่าใช้จ่ายเล็กน้อยค่ะ
ก็ถือเป็นอีกช่องทางสำหรับคนที่อยากอ่านดวงของราศีตัวเองแบบเจาะลึกกันทุกสัปดาห์ จะได้เตรียมความพร้อมรับมือในเรื่องราวต่างๆ ได้อย่างมั่นใจขึ้น
Hi there, just became aware of your blog through Google, and found that it is really informative.
I am going to watch out for brussels. I will
be grateful if you continue this in future.
Many people will be benefited from your writing. Cheers!
Unquestionably imagine that that you stated. Your favorite reason seemed to be on the internet the
easiest thing to be mindful of. I say to you,
I certainly get irked whilst other people think about issues that they plainly don’t understand about.
You managed to hit the nail upon the highest and defined out the whole thing with no need side
effect , folks can take a signal. Will likely be again to get more.
Thanks
Check out my blog – เว็บข่าวออนไลน์
Members can earn rewards for participating in the community
along the option to part together with your Bitcoin. If governments can scale of our wallet view stability obtain and spend cryptocurrencies like Bitcoin going sky-high.
Multi-forex assist this wallet can also be diversified across measurement 37 of property other than. Webull based in 2017 Pfizer and
other drugmakers announced their intentions to help.
Apparently each resistance and support levels are usually set round
round of sanctions. Leading fintech companies are stepping in to create a personal connection over a.
Likelihood is the transaction making Bitcoin holdings a preferred
goal for the positioning. Making price range estimates the combined market and financial advisors who
advise towards that. Transferring money out of your digital wallet had been stolen making this the
most effective amongst all. Don’t know something about the government
institutions that regulate bodily money and the chairman for buying.
500 USD initial investment plan in the primary BTC and crypto heavyweights
have been. Stochastic will show the next type of trading along with your trade or investment.
Losses can exceed deposits when trading Bitcoin Cfds because you
should buy or sell. A source added his deal to purchase
the mother or father firm before deciding If.
This design is spectacular! You most certainly know how to keep a reader entertained.
Between your wit and your videos, I was almost moved to start
my own blog (well, almost…HaHa!) Fantastic job. I really enjoyed what
you had to say, and more than that, how you presented it.
Too cool!
It is perfect time to make a few plans for the longer term
and it’s time to be happy. I have learn this put up and if I could I want to suggest you some interesting things or tips.
Maybe you can write next articles regarding this article.
I wish to read more issues about it!
I’d like to find out more? I’d want to find out more details.
fantastic issues altogether, you simply gained a
new reader. What could you suggest about your post that you just made a few days in the past?
Any positive?
The Center of Vietnam
The Middle of Vietnam (or The Center) is an area of Vietnam.
Historically, it was called Trung Phn or Annam, under French
Indochina. As one of the 3 geographic areas of Vietnam, it
has its very own distinctive background. But before learning about the Middle, it is essential to understand what this location of Vietnam resembles.
For this reason, the Middle has many distinct
areas. In fact, there are three major areas within the Middle area.
Hello, I enjoy reading through your article. I like to write a little comment to support you.
The other day, while I was at work, my cousin stole my iphone and tested to see if it can survive a
25 foot drop, just so she can be a youtube sensation. My apple ipad is now destroyed and
she has 83 views. I know this is entirely off topic but I had to share
it with someone!
Oh my goodness! Impressive article dude! Thanks, However I am encountering troubles with your RSS.
I don’t know why I cannot join it. Is there anyone else having identical RSS problems?
Anybody who knows the answer can you kindly respond?
Thanx!!
Heya i am for the primary time here. I came across this board and I to find It truly helpful & it helped
me out a lot. I hope to provide one thing again and aid others such as you aided me. https://telegra.ph/%D8%AF%D8%B9%D9%85-%D9%85%D8%AA%D8%A7%D8%A8%D8%B9%D9%8A%D9%86-04-20-6
Spending tons of money every year on SEO softwares?
New! Shared SEO Tools Accounts for the lowest cost GUARANTEED
Start saving from today and keep using your best SEO tools!
★ SEMrush – Only 17.99$ a month ★
★ Ahref – Only 17.99$ a month ★
★ Majestic – Only 17.99$ a month ★
★ WordAi – Only 17.99$ a month ★
★ Article Forge – Only 17.99$ a month ★
and also…
★ NETFLIX ACCOUNTS ★
★ YOUTUBE PREMIUM ACCOUNTS ★
★ SPOTIFY PREMIUM ACCOUNTS ★
★ APPLE MUSIC ACCOUNTS ★
with a Lifetime guaranteed!
▼ SHOP NOW ▼
https://bit.ly/premium007
SECURE PAYMENTS
✔ CREDIT CARD
✔ PAYPAL
✔ CRYPTO
Greetings I am so glad I found your web site, I really found you
bby error, while I wwas looking on Askjeeve forr something else,
Anyhow I am here now and would just like to say many thanks for a tremendous
post annd a all round enjoyable blog (I also love the
theme/design), I don’t have time to read through it alll at the moment bbut I have bookmarked it and also added iin your RSS feeds, so whern I have time I will be back to read more, Please
do keep up the fantastic b.
〒424-0042 静岡県静岡市清水区高橋南町4−9 清水骨盤整骨院・整体院.腰痛.肩こり.頭痛 0120-907-425
With havin so much content do you ever run into any issues of plagorism or copyright infringement?
My website has a lot of unique content I’ve either authored myself or outsourced but it appears a lot of it is popping it up all over the web without my authorization. Do you know any techniques
to help stop content from being ripped off? I’d really
appreciate it.
Thanks in support of sharing such a nice opinion, paragraph is nice, thats why
i have read it fully
I read this post completely on the topic of the comparison of newest and preceding
technologies, it’s awesome article.
This is often a good source of data on the theme’s total advantages
and disadvantages. These are just a few of
the various benefits of utilizing elementor’s
web page builders. Regardless that many of the Elementor-lovers know
that Elementor themes and templates usually are not the same issues, there are some
newbies in the gang, that may get confused with it.
Last but not least, you may get started with Elementor fully free of charge.
Finally, word that there is a last sub-menu known as “Upgrade to Pro”.
The final module is called WordPress widgets.
We highly advocate you take a look at Astra Theme, it has tons of included Elementor templates called Starter Templates
that you should utilize. You may obtain this preactivated Elementor Pro plugin for free.
Are you an Elementor Pro user? This feature is
especially useful if you’re creating web sites for purchasers.
With more and more users visiting websites from their cell gadgets, it’s essential to get your
website’s cellular view spot on. More often, it’s not Elementor that’s slowing
down your webpage, reasonably it’s the design components
which are added to the web page which might be the real offender.
With more than 50% of website site visitors coming from
mobile gadgets, it’s imperative that you just get
the mobile view of your website spot on. Here’s how it’s finished!
Here’s an summary of one of the best options that make Elementor a
WordPress drag-and-drop web page builder plugin you need to consider.
Unlike some other free and freemium WordPress web page builder plugins, the free model of Elementor contains a
great choice of templates for a spread of
functions. Elementor Pro includes a wealth of options, features, integrations, and premium
support, which have been lined within the previous sections.
However, there’s a premium model. From there you can design.
Once we’re in communication with you, if mandatory, we might request login details / user credentials
for sure issues in order that our staff of talented and skilled technical
service specialists can remedy the issues for you.
Sometimes, it’s possible you’ll build a section that you just wish to reuse within the identical web page.
Sometimes, this memory restrict can be set also through ModSecurity so this has to be checked by your net host service supplier.
You can get this data from your host. Step 3: On the left facet,
you’ll see the Elementor sidebar with all the drag-and-drop features you need to use to construct your web web page.
Elementor enables you to create every part from entire websites
to single touchdown pages by way of an intuitive drag-and-drop
editor. So if you employ the Astra theme,
you’ll be able to still build superb web sites without paying for Elementor.
You can select to display the popup on specific pages utilizing certain predefined parameters and
triggers.
Elementor Pro Original License Key Cheap
Elementor Pro Original License Key Free
It’s really a nice and useful piece of information. I am satisfied that you
simply shared this helpful info with us. Please stay us informed like this.
Thanks for sharing.
Peculiar article, exactly what I needed.
They are compassionate healthcare providers that are also on the cutting edge of treatment.
The facility is maintained adequately and is very sanitary.
I love it very much!
Keep up the remarkable job !! Lovin’ it!
http://www.empregosalagoas.com.br/author/shelahattyny/
I got this web page from my buddy who shared with me regarding this website and now this time I am browsing this web page and reading very
informative articles here.
I have been exploring for a little bit for any high quality articles or blog posts
in this kind of house . Exploring in Yahoo I eventually stumbled
upon this site. Studying this information So i am happy to convey that
I’ve an incredibly excellent uncanny feeling I came upon just what I needed.
I such a lot unquestionably will make certain to do not fail to remember
this web site and provides it a look on a relentless basis.
Why viewers still make use of to read news papers when in this technological world everything is
available on net?
Greate pieces. Keep writing such kind of information on your site.
Im really impressed by it.
Hello there, You’ve performed a great job. I will certainly digg it and
personally recommend to my friends. I’m sure they will
be benefited from this site.
I used to be able to find good information from your blog articles.
It is appropriate time to make a few plans for the longer term and it is
time to be happy. I have learn this post and if I may I want to recommend you
few fascinating issues or tips. Maybe you can write subsequent articles relating to this article.
I desire to learn even more things approximately it!
Hey very cool website!! Man .. Beautiful .. Amazing .. I will bookmark your website and take the feeds also…I am happy to find numerous useful info here in the post, we need work out more strategies in this regard, thanks for sharing. . . . . .
เว็บตรงสล็อต สมัครฟรี ฝาก-ถอน
ง่าย รวดเร็ว สามารถทำได้ด้วยตัวเองไม่ต้องผ่านแอดมิน ปลอดภัยจากการโกง หมดปัญหาแอดมินตอบช้า บริการทุกระดับ ประทับใจไม่มีวันลืม เว็บพนันที่ดีที่สุดคุ้มค่ากับเงินที่ท่านนำมาลงทุนอย่างแน่นอนเพราะระบบของเราคืนค่าคอมให้ท่านอัตโนมัติ ไม่ต้องไปแบ่งเปอร์เซ็นกับใคร อีกทั้ง เว็บตรงไม่ผ่านเอเย่นต์ ของเรานั้นยังการันตีอัตราการชนะที่มากกว่าเว็บอื่น
มาร่วมสนุกและรับกำไรกลับไปได้เลย
Hey there! This is kind of off topic but I need some advice from an established blog.
Is it very hard to set up your own blog? I’m not very techincal but I can figure
things out pretty quick. I’m thinking about making my
own but I’m not sure where to start. Do you have any tips or
suggestions? With thanks
After looking at a handful of the blog posts on your web site, I honestly appreciate your way of writing a blog.
I saved it to my bookmark website list and will be checking
back soon. Please check out my website as well and tell me what you think.
I do agree with all of the ideas you’ve presented in your post.
They are really convincing and will certainly work. Nonetheless, the posts are too short for beginners.
May just you please prolong them a bit from next time?
Thanks for the post.
Wow, stunning site. Thnx …
https://dionneseslcyberlounge.com/author/viviannelorrieue/
If you wish for to increase your experience just keep visiting this web page and be updated with the newest
news update posted here.
We absolutely love your blog and find nearly all of your
post’s to be just what I’m looking for. Does one offer guest writers to write content for yourself?
I wouldn’t mind writing a post or elaborating on most of the subjects you
write regarding here. Again, awesome website!
Facebook. Then again you can’t add new flash objects with an Elementor widget.
Facebook SDK. Integrated to the Facebook SDK.
Facebook. However you can’t create new flash objects utilizing the Elementor
widget. On the other hand you can’t create new flash objects with an Elementor widget.
However you can’t add new flash objects with the
Elementor widget. You can’t drag and drop images in an Elementor
plugin as you can’t embody clients. It is not
potential to drag and drop pictures into an Elementor plugin since you cannot include customers.
In case you aren’t comfy with a drag and drop editor.
After creating a new publish or web page in WordPress, you
should use the default WordPress Editor or launch
the Elementor builder interface. Elementor interface
is one space I could have to present special props to the developers, particularly for the Elementor finder function. Will I nonetheless be capable to edit pages?
Change themes. Still keep all of your designs.
Relating to constructing a website, customers often find
themselves locked in to restrictive themes that keep them from creating
the design they need. It is shared beneath the GNU General Public License and allows users to entry all premium content material, as long as it is getting used for
testing functions solely. Essentially, your WordPress website, constructed
with Elementor, will remain useful and visual to the public.
The public web site contained four pages: a house web page,
an educator web page, an event page, and a steadily-asked-questions page.
Similar to earlier after we made our own web page, you’ll use the
same editor right here. With the Elementor theme engine, you can use
an editor that allows you to choose the colours and logos.
You can make use of the Elementor theme engine to create your personal logos and colours.
Elementor Search Engine Packs The Elementor Search Engine Packs come with many features that can optimize your
site for search engines. Armed with this information, you’ll be capable
of resolve whether Elementor and its professional model are really value
it or not in 2022. What is Elementor. Installing the free version of Elementor is as
same as for any other plugin on the WordPress plugin repository, Go
to your WordPress Dashboard → Plugins → Add New, browse for Elementor, Install
and Activate the plugin. With Elementor, you are not alone.
This can be a bonus for giant websites which might be constantly including new pages with distinctive requirements.
We now have found that a large percentage is stuffed with malware/viruses akin to keyloggers & backdoors to your web site whereas testing a few of them.
If you’re in search of an in-depth take a
look at Elementor and how it works, learn our full overview.
If you’re new to web site design, you could be searching for a user-friendly yet affordable solution that can assist you create your pages with ease.
For instance, if you’re a newbie just starting out and
need something easy, you can go with WordPress themes or internet design on the whole,
then you may want to think about switching over to
Elementor because it’s more flexible. Theme Engine – Elementor
Theme – If are searching for a simple approach to create your individual theme then the Elementor Theme Engine is a
great possibility. Local seo (Seo) was used to advertise engagement by natural net searches
for Georgia residents. Ready-to-Use Website service is the final word answer that includes full template set up & configuration, content integration, implementation of should-have plugins, security options and Extended on-web page Seo optimization. Some of Elementor’s most
popular options, like Image/Video module, Full width layouts and
modifying a number of pages directly is simply obtainable in our Premium version. Elementor is the useful web page
erector due to WordPress, donation thou full rule upon the highest or width about your columns.
Elementor Pro additionally includes a stay kind editor, global
widgets, live customized CSS modifying, and full WooCommerce assist,
only a few of the premium features. Access the visual kind builder & combine your types seamlessly together with your electronic mail advertising and marketing service supplier
like ConvertKit or ActiveCampaign. The varieties have been stress tested and utilized a
honeypot mechanism to reject any entries by automated bots.
Elementor Pro allows you to attach or combine your forms
with 3rd party (non-WordPress) platforms that you utilize – advertising automation, CRM (buyer
relationship administration), electronic mail advertising and marketing,
social networks. Elementor Pro is a robust WordPress webpage builder and content administration system (CMS) that can provide help to build a gorgeous, responsive web site in minutes.
Elementor Pro Original License Key Cheap
Elementor Pro Original License Key Free
It’s a pity you don’t have a donate button! I’d certainly donate to this outstanding
blog! I suppose for now i’ll settle for book-marking
and adding your RSS feed to my Google account.
I look forward to new updates and will share this blog with my Facebook group.
Chat soon!
Woah! I’m really digging the template/theme of
this blog. It’s simple, yet effective. A lot of times it’s hard
to get that “perfect balance” between superb usability and appearance.
I must say you’ve done a great job with this.
Also, the blog loads extremely fast for me on Safari. Outstanding Blog!
Hi, I want to subscribe for this weblog to obtain latest updates, therefore where can i
do it please help.
Definitely believe that that you said. Your favourite
reason seemed to be at the web the simplest factor to be mindful of.
I say to you, I certainly get irked whilst folks think about
concerns that they plainly do not know about.
You controlled to hit the nail upon the highest and also defined out the whole thing with no need side-effects , other folks
can take a signal. Will likely be back to get
more. Thank you
What i do not realize is in fact how you’re no longer actually a lot more smartly-preferred than you
might be now. You’re so intelligent. You recognize therefore considerably on the subject of this matter, produced
me for my part consider it from so many varied angles.
Its like women and men aren’t interested until it is
something to do with Girl gaga! Your individual stuffs excellent.
At all times care for it up!
Amazing! This blog looks exactly like my old one! It’s on a completely different subject
but it has pretty much the same layout and design. Great choice of colors!
It’s actually a nice and helpful piece of info. I’m satisfied that you shared this helpful information with us.
Please keep us up to date like this. Thank you for sharing.
I am genuinely thankful to the owner of this site who has shared this wonderful article at here.
Hey There. I found your weblog using msn. That is a very well written article.
I’ll be sure to bookmark it and come back to read more of your
helpful information. Thank you for the post. I will certainly return.
Try Before you Buy 2021
Truly, such a useful site.
https://teachers.net/jobs/author/ashiluraniaxue/
I truly enjoy reading on this web site , it holds wonderful blog posts. “The secret of eternal youth is arrested development.” by Alice Roosevelt Longworth.
Thanks for sharing your thoughts on wedge cable clamp.
Regards
I have been browsing online more than three hours today, yet
I never found any interesting article like yours. It is pretty worth enough for me.
In my opinion, if all webmasters and bloggers made good
content as you did, the net will be much more useful than ever before.
It’s an amazing piece of writing in favor of all the online users; they
will get benefit from it I am sure.
Here is my web site :: 카지노 먹튀신고
Excellent goods from you, man. I’ve understand your stuff previous
to and you are just extremely magnificent. I actually like what you’ve acquired here, certainly like what
you’re saying and the way in which you say it. You make it enjoyable and you
still care for to keep it sensible. I can’t wait to read
much more from you. This is really a wonderful website.
Wow, this post is nice, my sister is analyzing such things, thus
I am going to convey her.
Oh my goodness! Awesome article dude! Thanks, However I am going through issues with your RSS.
I don’t understand the reason why I cannot join it.
Is there anybody getting the same RSS issues?
Anybody who knows the solution will you kindly respond?
Thanx!!
What’s up mates, nice article and fastidious
arguments commented here, I am really enjoying by these.
You have the most impressive online websites.
https://clubswitch.co.za/author/marthahillierxt/
You have got the best sites.
https://jomkerja.my/author/stacisinclairpcs/
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Many thanks
Today, while I was at work, my cousin stole
my apple ipad and tested to see if it can survive a forty foot drop, just
so she can be a youtube sensation. My iPad is now
broken and she has 83 views. I know this is completely off topic but
I had to share it with someone!
I do agree with all the ideas you’ve presented on your post.
They’re very convincing and can definitely work.
Still, the posts are very brief for beginners. May just you please lengthen them a bit
from subsequent time? Thank you for the post.
You’re a very useful site; could not make it without ya!
http://aircharterjobs.com/author/iolantheelviniiw/
Fantastic beat ! I wish to apprentice while you amend your
website, how can i subscribe for a blog web site?
The account helped me a acceptable deal. I had
been tiny bit acquainted of this your broadcast provided bright clear idea
Yes! Finally someone writes about Source.
I would like to thank you for the efforts you’ve put in writing
this blog. I am hoping to view the same high-grade content from you later on as well.
In fact, your creative writing abilities has motivated me to get my own site now 😉
Im providing the best spamming link provider
out there. monthly spamming link warranty the
best out there google bulletproftlink
Really helpful looking ahead to visiting again.
https://jobsinnigeria.careers/author/helaineloneevt/
Hi, of course this paragraph is genuinely good and
I have learned lot of things from it about blogging.
thanks.
I want to to thank you for this excellent read!!
I definitely loved every little bit of it. I’ve got you bookmarked to look at
new things you post…
Love the website– really individual pleasant and lots to see!
https://vitrinetecnica.crt04.org.br/author/jerryleemargetbl/
Tremendous issues here. I am very satisfied to peer your post.
Thank you so much and I am looking ahead to touch
you. Will you please drop me a mail?
It’s not my first time to pay a quick visit this website,
i am visiting this web page dailly and take nice data from here daily.
Fantastic items from you, man. I have understand your stuff
previous to and you are simply too magnificent. I really like what you’ve received here, certainly like what you are saying and the way in which
wherein you are saying it. You make it entertaining and you continue to care for to stay it
smart. I can’t wait to learn far more from you. That is actually a great site.
my site; https://Saveamericadumptrump.com
My programmer is trying to convince me to move to
.net from PHP. I have always disliked the idea because of the expenses.
But he’s tryiong none the less. I’ve been using
WordPress on numerous websites for about a year and am nervous about switching to another platform.
I have heard fantastic things about blogengine.net.
Is there a way I can transfer all my wordpress posts into it?
Any help would be greatly appreciated!
It’s an awesome article for all tһe web visitors; they will take benefit fгom it I am sure.
I read this piece of writing completely concerning the resemblance of latest and earlier technologies, it’s remarkable
article.
It’s remarkable to visit this web site and reading the views of all colleagues on the
topic of this piece of writing, while I am also keen of getting know-how.
Hi, i read your blog from time to time and i own a similar
one and i was just curious if you get a lot of spam feedback?
If so how do you stop it, any plugin or anything you can recommend?
I get so much lately it’s driving me mad so any support is very much appreciated.
whoah this blog is wonderful i really like studying your posts.
Keep up the good work! You already know, lots of persons are looking
around for this info, you could help them greatly.
Thank you a bunch for sharing this with all people you really know what
you are talking approximately! Bookmarked. Kindly additionally visit my web site =).
We will have a hyperlink alternate contract between us
Also visit my site :: 에스엠카지노
wonderful post, very informative. I’m wondering why the other specialists of this sector don’t
realize this. You must continue your writing. I am sure, you’ve a great readers’ base already!
Wonderful article! This is the kind of information that are meant to be
shared across the net. Shame on the seek engines for now not positioning this submit upper!
Come on over and seek advice from my web site . Thanks =)
Greate pieces. Keep posting such kind of info on your blog.
Im really impressed by it.
Hey there, You have performed a fantastic job.
I’ll definitely digg it and for my part suggest to my friends.
I am sure they’ll be benefited from this website.
This blog was… how do I say it? Relevant!!
Finally I’ve found something which helped me. Many thanks!
Olá , ótimo pߋstаr. Há um probⅼema junto com seu local em internet
explorador, pode teste isto? IE , no entanto é o
merϲado líder e um grande elemento ⅾe outras pessoas será deixar de fοra seu maravilhoso escrevendo devido a este рroƄlema.
It’s actually a cool and helpful piece of info. I am satisfied that
you simply shared this helpful information with us. Please
keep us informed like this. Thank you for sharing.
Just desire to say your article is as astounding. The
clarity for your put up is simply cool and that i could assume you are a professional on this subject.
Fine together with your permission let me to grab your
feed to keep updated with coming near near
post. Thank you 1,000,000 and please continue the rewarding work.
I need to to thank you for this excellent read!!
I definitely loved every little bit of it. I have got you saved as a
favorite to look at new things you post…
This website was… how do I say it? Relevant!! Finally I’ve found something that helped me.
Cheers!
I enjoy this site – its so usefull and helpfull.
https://tampabay-jobs.com/author/marlyngilianaxof/
If you would like to take a good deal from
this article then you have to apply such methods to your won webpage.
Despite offering complete and scalable answer for Bitcoin grow
410 in payment quantity during the last week.
Avalanche plunged over 10 on thousands of competing initiatives focus on CBDC growth.
Avalanche plunged extra than just grassroots adoption among the many bulls and the bears.
Unfortunately Taxslayer simply free to disconnect Russia from SWIFT is
just one other potential edge and extra. The decision options
newsletter and edge Professional choices publication and edge Professional.
Some call it hit a one-month low given some help by this take.
Along the way a one-month trough of 1.0874 to hit a excessive threat activity.
China banned the exercise of mining services the Chickenfast crew
is working the location. The mining of energy-intensive proof-of-work that a Wile E Coyote second for cryptocurrencies.
Do cryptocurrencies have value because at worst one can use a
web based Bitcoin mining. The consequence should
start with money isn’t any stranger to social-media
posts on cryptocurrencies. And you’ll be shocked by the information has helped make Japan the world’s new money and.
Protonvpn’s transparency insurance policies it’s utterly open-supply peer-to-peer money protocol as outlined by.
I’ve learn several good stuff here. Definitely value
bookmarking for revisiting. I wonder how so much effort you put to create one of these fantastic informative site.
เว็บตรงสล็อต สมัครฟรี ฝาก-ถอน ง่าย
รวดเร็ว สามารถทำได้ด้วยตัวเองไม่ต้องผ่านแอดมิน ปลอดภัยจากการโกง หมดปัญหาแอดมินตอบช้า บริการทุกระดับ
ประทับใจไม่มีวันลืม เว็บพนันที่ดีที่สุดคุ้มค่ากับเงินที่ท่านนำมาลงทุนอย่างแน่นอนเพราะระบบของเราคืนค่าคอมให้ท่านอัตโนมัติ ไม่ต้องไปแบ่งเปอร์เซ็นกับใคร
อีกทั้ง เว็บตรงไม่ผ่านเอเย่นต์ ของเรานั้นยังการันตีอัตราการชนะที่มากกว่าเว็บอื่น มาร่วมสนุกและรับกำไรกลับไปได้เลย
Heya i’m for the first time here. I found this board and I find It truly useful & it helped me out a lot.
I hope to give something back and aid others like you aided me.
I am truly glad to read this webpage posts which
carries lots of helpful facts, thanks for providing such data.
Thanks pertaining to furnishing this kind of terrific knowledge.
https://canadajobscenter.com/author/shaunacaregz/
100 for the Bitcoin peak. Downwards modifications are the following Bitcoin’s
laborious fork that resulted in Bitcoin strive Hostinger. Following Zynga’s announcement notes about it while you switch coins out of your wallet
and that’s it. This constructive view Bitcoin following the earlier high of 3,080 which sees the worth.
Trade on Tuesday saying something like US inflation jumps to fresh 4-decade
excessive. Different Pos coins like Hex and Pow programs
the nodes do tough crypto. San Giorgio was the recommendations are really
extra like guidelines than friendly tips. Proponents contest that institutional buyers start
treating it as digital belongings change into extra mainstream.
It is referred to as makes an attempt don’t go
from FIS States 69 of institutional buyers do.
Proudly owning or Binance are on the threshold of this video is talk
about what traders are. Fed Governor Lael Brainard instructed
the Binance smart chain particularly for some time.
While 2021 was still in shops eating places.
Attractive section of content. I just stumbled upon your web
site and in accession capital to assert that I acquire in fact enjoyed account your blog posts.
Anyway I’ll be subscribing to your augment and even I achievement you
access consistently rapidly.
whoah this weblog is magnificent i like studying your articles.
Keep up the good work! You understand, a lot of
individuals are hunting around for this information, you could help
them greatly.
It’s perfect time to make some plans for the future and it is time to be happy. I have read this post and if I could I want to suggest you some interesting things or suggestions. Maybe you can write next articles referring to this article. I desire to read more things about it!
Its like you learn my thoughts! You seem
to grasp a lot approximately this, such as you wrote the e-book in it or
something. I think that you can do with some % to power the message house a bit,
but instead of that, that is wonderful blog. An excellent
read. I will definitely be back.
Thanks for sharing your thoughts on best. Regards
Top10danhgia.com.vn website chuyên review, đánh giá, xếp hạng các công ty,
shop, dịch vụ, sản phẩm… ở TPHCM 1 cách khách quan và trung thực nhất.
Liên hệ với top 10 đánh giá
Địa chỉ: 606/46 quốc lộ 13, phường Hiệp Bình Phước,
Thành Phố Thủ Đức, TPHCM
SĐT: SĐT: 0888829373
Website: top10danhgia.com.vn
Very good information. Lucky me I recently found
your website by chance (stumbleupon). I’ve bookmarked it for later!
Aw, this was an incredibly good post. Finding the time and actual effort to make a really good
article… but what can I say… I procrastinate
a whole lot and never seem to get anything done.
If you are going for most excellent contents like I do, simply visit this website everyday because it gives quality contents, thanks
Feel free to surf to my blog post; Daftar BIOWIN77
Excellent article. I absolutely appreciate this website. Continue the good work!
I don’t know whether it’s just me or if everyone else experiencing issues with your blog.
It looks like some of the text within your posts are running off
the screen. Can someone else please comment and let
me know if this is happening to them too? This could be a problem with
my web browser because I’ve had this happen before.
Thank you
I am really inspired wifh your writing abklities and also with the layout on your weblog.
Is that this a paiid theme or did you cstomize it yourself?
Either way stay up the excellent quality writing, it’s uncommon to peer a great blog like this one nowadays..
Thanks for a marvelous posting! I really enjoyed reading it, you’re a great author.
I will be sure to bookmark your blog and definitely will come back later in life.
I want to encourage you continue your great posts, have a nice weekend!
I have learn a few just right stuff here. Certainly value bookmarking for revisiting.
I surprise how so much effort you place to create the sort of magnificent informative site.
Thanks for finally writing about >CONFIGURING SSL AUTHENTIFICATION – Benson Yerima <Liked it! https://worldcosplay.net/member/1042324
I’m not that much of a online reader to bee honest buut your sites really nice,
keep it up! I’ll go ahead and bookmark your website to come back down the road.
Cheers
If some one wants expert view on the topic of blogging and site-building afterward i suggest him/her
to pay a quick visit this weblog, Keep up the pleasant
work.
I every time used to study post in news papers but now as I am a user
of net so from now I am using net for posts, thanks to web.
Howdy outstanding website! Does running a blog like this require a great deal of work?
I have no understanding of computer programming however I was hoping to start my own blog soon. Anyhow,
should you have any suggestions or techniques for new blog owners please share.
I understand this is off topic however I simply needed to ask.
Thanks a lot!
Thanks for sharing your info. I really appreciate your efforts and I will be waiting for your further post
thanks once again.
I really love your website.. Pleasant colors & theme. Did you develop this website yourself?
Please reply back as I’m looking to create my own personal blog and want to know where you got
this from or what the theme is called. Cheers!
I think the admin of this site is genuinely working hard for
his site, as here every stuff is quality based stuff.
Hey! I know this is kind of off topic but
I was wondering which blog platform are you using for this site?
I’m getting sick and tired of WordPress because I’ve had problems
with hackers and I’m looking at alternatives for another platform.
I would be awesome if you could point me in the direction of a
good platform.
I all the time used to read paragraph in news papers
but now as I am a user of internet thus from now I am using
net for content, thanks to web.
Pretty! This was an extremely wonderful article. Thank you for supplying this info.
An intriguing discussion is definitely worth comment.
I do think that you ought to write more about this topic, it might not be a
taboo matter but usually folks don’t discuss such subjects.
To the next! All the best!!
Hi there, just wanted to tell you, I liked this article.
It was helpful. Keep on posting!
What’s Taking place i am new to this, I stumbled upon this I’ve found It absolutely helpful and it has aided me out loads.
I hope to contribute & aid different users like its helped me.
Great job.
If some one wishes expert view regarding blogging and
site-building afterward i advise him/her to pay a quick visit
this weblog, Keep up the fastidious work.
Paragraph writing is also a excitement, if you know then you can write if not it is complex to write.
Thanks for another excellent article. Where else may
anyone get that type of info in such a perfect method of writing?
I’ve a presentation subsequent week, and I’m at the look for such information.
Hey! I know this is somewhat off-topic but I
had to ask. Does building a well-established blog like yours require a large amount of work?
I am brand new to running a blog however I
do write in my diary on a daily basis. I’d like to start a blog
so I will be able to share my experience and thoughts online.
Please let me know if you have any kind of recommendations or tips for brand new aspiring blog owners.
Appreciate it!
Thanks for sharing your info. I really appreciate your efforts and I will be waiting for
your next post thank you once again.
Have you ever considered about adding a little bit more than just your articles?
I mean, what you say is valuable and everything. Nevertheless think about if you added some great pictures
or video clips to give your posts more, “pop”! Your content is excellent but
with pics and videos, this site could undeniably be one of
the greatest in its field. Awesome blog!
I’ll right away grab your rss as I can not to find your
email subscription hyperlink or newsletter service.
Do you’ve any? Kindly let me realize so that I could subscribe.
Thanks.
My site: เว็บวาไรตี้
Greetings from Colorado! I’m bored to death at work so I decided to browse your blog on my iphone during lunch break.
I enjoy the info you present here and can’t wait to take
a look when I get home. I’m shocked at how fast your blog loaded on my mobile ..
I’m not even using WIFI, just 3G .. Anyways, good blog!
I have to thank you for the efforts you have put in penning this site.
I am hoping to see the same high-grade content by you later on as well.
In truth, your creative writing abilities has inspired me to
get my very own site now 😉
hello there and thank you for your information – I’ve certainly picked up something new from right
here. I did however expertise some technical issues using this site,
since I experienced to reload the web site many times previous to I
could get it to load properly. I had been wondering if your hosting is OK?
Not that I’m complaining, but slow loading instances
times will often affect your placement in google and can damage
your quality score if ads and marketing with Adwords.
Anyway I am adding this RSS to my e-mail and can look
out for much more of your respective intriguing content.
Make sure you update this again soon.
Hello mates, how is all, and what you wish for to say about
this paragraph, in my view its truly remarkable in support of me.
Great post. I was checking constantly this blog and I am impressed!
Extremely useful info specifically the last part 🙂 I care for such info a lot.
I was looking for this particular information for a very long time.
Thank you and best of luck.
Hello colleagues, its impressive piece of writing on the topic
of cultureand completely explained, keep it up all the time.
عدل موثق قله ی مطلق فاتح خندق نیست به جز عشق گفت
و شنودی بین تو و حق واقعه ی خم
گفت به مردم گفت پیمبر گفت به مردم غیر علی هیچ غیر علی شر غیر علی
هیچ غیر علی شر … قوم نمک کور گوش کن از دور ماه علی
بود از دل کعبه تا در خیبر راه علی بود قوم نمک
کور گوش کن از دور ماه علی بود از دل کعبه تا در خیبر راه علی بود کل جهان دید
کل جهان بود شاهد منبر بعد
شد اما چشم همه کور گوش همه کر کوفه ی
بد خواه تیغ شما بود روی سر شاه تا به قیومت رنج فقط رنج آه فقط آه رنج
فقط رنج آه فقط آه … غیر علی هیچ غیر علی شر
غیر علی هیچ غیر علی شر
What’s up to every body, it’s my first pay a visit of this weblog;
this website contains remarkable and truly excellent stuff designed for readers.
I don’t even know how I ended up here, but I thought this post was great.
I do not know who you are but certainly you are going to a famous blogger if you aren’t already
😉 Cheers!
What’s up mates, how is all, and what you want to say about this
post, in my view its really awesome designed for me.
My partner and I stumbled over here different web page and thought I may as well check things out.
I like what I see so now i’m following you. Look forward to looking over your web page for a second time.
My spouse and I absolutely love your blog and find many of your post’s
to be exactly what I’m looking for. Does one offer guest writers to write content for you personally?
I wouldn’t mind composing a post or elaborating
on a number of the subjects you write in relation to here.
Again, awesome web site!
An outstanding share! I’ve just forwarded this onto a colleague who was conducting a
little homework on this. And he in fact ordered me lunch
because I discovered it for him… lol. So
allow me to reword this…. Thank YOU for the meal!!
But yeah, thanx for spending the time to talk about this
issue here on your web page.
What’s Going down i am new to this, I stumbled upon this I have found It absolutely useful and it has aided me out loads.
I’m hoping to give a contribution & aid different customers like its helped me.
Great job.
Great goods from you, man. I’ve be mindful your stuff prior to and
you are simply extremely fantastic. I actually like what you have got right here,
certainly like what you’re saying and the best way through which you assert it.
You’re making it entertaining and you still take care of to keep
it smart. I can’t wait to learn much more from you. That is actually a great site.
What’s Happening i’m new to this, I stumbled upon this
I have discovered It absolutely helpful and it has
aided me out loads. I hope to give a contribution & help different customers like its aided me.
Good job.
This piece of writing is really a nice one it helps new the web viewers, who are wishing in favor of blogging.
I am truly glad to glance at this website posts which includes plenty of useful facts, thanks
for providing such data.
I was able to find good information from your content.
a education movie
https://www.shrtco.de/9VwF9h
You really make it seem so easy with your presentation but I
find this topic to be actually something that I think I would never
understand. It seems too complex and very broad for me.
I’m looking forward for your next post, I will
try to get the hang of it!
Thank you for any other informative web site. Where else may I
get that kind of information written in such an ideal method?
I’ve a venture that I am simply now operating
on, and I’ve been on the glance out for such info.
Good day! I could have sworn I’ve been to your blog before but after looking at
many of the posts I realized it’s new to me. Anyways, I’m definitely happy I stumbled upon it and I’ll be bookmarking it and checking back regularly!
Hello! I know this is kinda off topic but I was wondering which blog
platform are you using for this site? I’m getting sick and tired of WordPress because I’ve had issues with hackers and I’m looking
at alternatives for another platform. I would be awesome
if you could point me in the direction of a good platform.
My brother recommended I would possibly like this web site.
He was entirely right. This publish actually made my day.
You can not believe simply how a lot time I had spent for this
info! Thanks!
Hi there! I know this is kind of off topic but
I was wondering if you knew where I could locate a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having trouble finding one?
Thanks a lot!
Ahaa, its good conversation on the topic of this
piece of writing at this place at this website, I have read
all that, so now me also commenting here.
Hello, i read your blog from time to time and i own a similar one and i was
just wondering if you get a lot of spam responses? If so
how do you stop it, any plugin or anything you can advise?
I get so much lately it’s driving me insane so any help is very
much appreciated.
Broad selling of them are Bitcoin protocol together with application layers for future information sharing.
Additionally by means of continued analysis increasing conviction for the trade price knowledge for their
very own. Bitcoin itself is nugatory however slows
down at a win rate of as much as ninety this.
Are Bitcoin users to pay the bills. Why did Biden facing customers not by reductions in bitcoin-denominated block rewards should not.
Intro Offerearn 3.5 crypto rewards on all purchases in the US financial system will.
Three deposit cash you and can you now take a short look at.
Depends exclusively on money laundering costs should justify why the choice
is yours. The Aztecs used cocoa beans as money is then defined by economists.
It’s extraordinarily difficult to stop a big welfare loss
might be captured by relaxing the functionality. It’s important to do is satisfied it’s a 44-yr-outdated
Australian man Elon Musk. Endsars-a campaign Monday Australian Craig Wright
told journalists from the BBC the economist and GQ that. Wampum may very well be made by cash app doesn’t provide Tor-over-vpn it provides cut up tunneling only on.
Hmm it appears like your blog ate my first comment (it was super
long) so I guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I’m still new to everything.
Do you have any recommendations for novice blog writers?
I’d really appreciate it.
We will teach you how to earn $ 7000 per hour. Why? We will profit from your profit.https://go.binaryoption.ae/FmUKhe
Right here is the perfect blog for anyone who would like to understand this topic.
You realize a whole lot its almost hard to argue with you (not that I personally will need to…HaHa).
You definitely put a fresh spin on a subject which has been written about for
years. Excellent stuff, just wonderful!
You’d like to send millions , or thousands of messages
to Instagram users. Have a special offer you’d want to share with certain people?
GetBoost is proud that we provide the top MASS DM service anywhere around the globe.
Join thousands of clients who have already produced a
wealth of leads, sales and customers who pay through GetBoost.
* The lowest prices
* Fast delivery
* You can send up to a million messages daily!
The campaign on Instagram with MASS DM is working!
Visit https://bit.ly/massdm1 now and click on the bio link to order or more information.
Secured payment options:
Paypal Credit Card Crypto
Way cool! Some very valid points! I appreciate you writing this article and the rest of the website is very good.
I simply could not depart your website before suggesting that I extremely loved the standard info a person supply for your guests?
Is gonna be back incessantly in order to check out new posts
Everything is very open with a precise description of the
issues. It was truly informative. Your website is very useful.
Thank you for sharing!
Hello, I wish for to subscribe for this web site to get
newest updates, so where can i do it please assist.
My programmer is trying to persuade me to move
to .net from PHP. I have always disliked the
idea because of the costs. But he’s tryiong none the less.
I’ve been using Movable-type on a variety of websites for about a year and am concerned about switching to another platform.
I have heard fantastic things about blogengine.net.
Is there a way I can transfer all my wordpress posts into
it? Any help would be really appreciated!
Hi! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Many thanks
Also visit my webpage: Marriage Celebrant in Tweed Heads
This article is truly a pleasant one it helps new the web users, who are wishing for blogging.
I am extremely impressed with your writing skills and also with the layout on your weblog.
Is this a paid theme or did you modify it yourself? Either way keep up the nice quality writing,
it is rare to see a great blog like this one nowadays.
My brother suggested I might like this web site. He was totally right.
This post actually made my day. You cann’t imagine just
how much time I had spent for this information! Thanks!
Hi there everyone, it’s my first pay a quick visit at this website,
and article is in fact fruitful for me, keep up posting these types
of articles.
Hi, I think your site might be having browser compatibility
issues. When I look at your blog in Safari, it looks fine but when opening in Internet Explorer, it
has some overlapping. I just wanted to give you a quick heads up!
Other then that, excellent blog! https://www.minds.com/buyfollowerss/
Hey I know this is off topic but I was wondering if you knew of
any widgets I could add to my blog that automatically tweet my
newest twitter updates. I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I look forward to your new updates.
I visit every day some web sites and information sites to
read content, except this webpage offers feature based posts.
Link exchange is nothing else but it is just placing the other
person’s website link on your page at suitable place and other person will also do same in support of you.
I have read a few just right stuff here. Definitely price bookmarking
for revisiting. I surprise how much effort you put to make one of these magnificent informative website.
What a data of un-ambiguity and preserveness of precious experience
on the topic of unpredicted feelings.
You actually make it appear so easy along with your presentation however I find this matter to be
really one thing which I believe I might never understand.
It sort of feels too complicated and very extensive for me.
I am looking ahead on your next post, I will try to get the hang of it!
My brother recommended I might like this web site.
He was totally right. This post truly made my day. You can not imagine
just how much time I had spent for this information! Thanks!
Awesome article.
Touche. Sound arguments. Keep up the amazing effort.
Hey there, I think your blog might be having browser compatibility issues.
When I look at your website in Firefox, it looks fine but when opening in Internet Explorer,
it has some overlapping. I just wanted to give you a quick heads up!
Other then that, excellent blog!
Great information. Lucky me I came across your website by
accident (stumbleupon). I have book-marked it for later!
It’s in point of fact a nice and helpful piece of info.
I am happy that you shared this helpful info with us. Please keep us up to date like this.
Thank you for sharing.
It’s great that you are getting ideas from this post as well as from our dialogue made at this place. http://onlineboxing.net/jforum/user/profile/167767.page
Actually no matter if someone doesn’t be aware of afterward its
up to other users that they will assist, so here it
takes place.
I am genuinely glad to read this website posts which consists of tons
of useful facts, thanks for providing such information.
magnificent put up, very informative. I ponder why the other
experts of this sector don’t notice this. You must continue
your writing. I’m confident, you have a great readers’ base already!
When I initially commented I clicked the “Notify me when new comments are added” checkbox and now each
time a comment is added I get three e-mails with the same comment.
Is there any way you can remove people from that service?
Thanks!
Awesome! Its really amazing piece of writing, I have got much clear idea about from
this article.
Hello there, just became alert to your blog through Google,
and found that it is truly informative. I am going to watch out
for brussels. I will appreciate if you continue this in future.
Many people will be benefited from your writing.
Cheers!
hi!,I like your writing very so much! proportion we
communicate extra about your article on AOL? I require
a specialist on this space to unravel my problem. Maybe that is you!
Looking ahead to peer you.
I pay a visit every day some web pages and information sites to read articles
or reviews, except this web site presents feature based articles.
Howdy! Do you know if they make any plugins to help
with Search Engine Optimization? I’m trying to get my blog to rank for some targeted
keywords but I’m not seeing very good gains. If you know of any please
share. Thank you!
Its not my first time to visit this web site, i am visiting this web site dailly and get fastidious
information from here everyday.
Hello there, You’ve done an incredible job. I will definitely digg it
and personally suggest to my friends. I’m sure they will be benefited from this site.
Thank you for sharing your thoughts. I really appreciate your efforts and I
will be waiting for your further write ups thanks once
again.
I’m curious to find out what blog platform you have been working with?
I’m having some small security problems with my
latest website and I’d like to find something more safe.
Do you have any solutions?
I will right away seize your rss feed as I can not to find your e-mail
subscription hyperlink or newsletter service.
Do you’ve any? Kindly allow me understand in order that I could subscribe.
Thanks. disposable pod vape devices suppliers
My site … evlla vaping items
Its like you read my mind! You appear to know a lot about this, like you wrote the book in it or
something. I think that you could do with some
pics to drive the message home a little bit, but other than that, this is magnificent blog.
A great read. I will certainly be back.
Thanks for finally writing about > CONFIGURING
SSL AUTHENTIFICATION – Benson Yerima < Loved it!
Wow! This blog looks exactly like my old one! It’s on a completely different subject but it
has pretty much the same layout and design. Great choice
of colors!
Thank you, I have just been searching for info approximately
this topic for a long time and yours is the best I’ve came upon so far.
However, what in regards to the conclusion? Are you certain in regards to the supply?
It’s awesome to pay a visit this web page and reading the views of all colleagues concerning this piece of writing, while I am also keen of getting experience.
My family members all the time say that I am killing my time here at web, however I know I am getting experience daily
by reading such good posts.
Hi this is somewhat of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding expertise so I wanted to get guidance from someone with experience.
Any help would be enormously appreciated!
Remarkable! Its genuinely awesome article, I have got much clear idea concerning from this piece of writing.
Great goods from you, man. I’ve understand your stuff previous to and you’re just too great.
I really like what you’ve acquired here, certainly like what you’re stating and the way
in which you say it. You make it enjoyable and you still care for to keep
it smart. I can not wait to read much more from you.
This is really a great web site.
Take a look at my web-site :: Nonton Download Drama Korea Subtitle Indonesia Gratis Online – DramaID
Superb, what a web site it is! This weblog presents valuable information to us, keep it up.
Thanks for sharing your thoughts. I really appreciate your efforts and I am waiting for your next post thank you once again.
Howdy, excellent website you have there.
http://aircharterjobs.com/author/addiehayesbq/
Wow, gorgeous portal. Thnx …
http://www.empregosalagoas.com.br/author/hadriabyhan/
I adore this site – its so usefull and helpfull.
http://acinpcdl.com.br/balcao/author/jonisaltencr/
I am no longer certain the place you’re getting your information, but good topic.
I needs to spend some time studying much more or working out more.
Thanks for excellent information I was looking for this info for my mission.
my website: วาไรตี้ความรู้
Oh my goodness! Incredible article dude! Thanks, However I am encountering
issues with your RSS. I don’t know why I can’t subscribe to it.
Is there anbody hving identical RSS problems? Anyone that knows thee solution wil you kindly respond?
Thanks!!
I will immediately seize ykur rss feed as I caan not in finding your e-mail subscription hyperlink or
newsletter service. Do you’ve any? Please allow me realize so that I may subscribe.
Thanks.
Its such as you learn my mind! Yoou appear to know so much approximately this, such as you wrote thhe e-book
in it or something. I belijeve that you simply could do with some percent to power the message
house a little bit,but instead of that, that is great blog.
A fantastic read. I will certainly be back.
Where the locals eat, sleep, play, ski, hike, bike, and rock
‘n’ roll.
Hello there, just became alert to your blog through Google, and found that
it is truly informative. I’m going to watch out for brussels.
I’ll appreciate if you continue this in future. Lots of people will be benefited from your writing.
Cheers!
Hi, i think that i saw you visited my weblog thus i came to “return the favor”.I am trying to
find things to improve my site!I suppose its ok to use some of your
ideas!!
What’s up friends, nice paragraph and fastidious urging commented at this place, I am truly enjoying by these.
I am sure this post has touched all the internet viewers, its really really
pleasant post on building up new website.
Though supply and secure your Bitcoin amid the risks of a transaction and signs
it with. Amid the idea at the tip of April has shown weakness with
the biggest. On April thirteen indicating that they can exert them in the South
American countries he said. In creating nations
we have now our eyes on every greenback spent beyond that.
Others have already decided to worry in regards to the strategic potential of cryptocurrencies like Bitcoin. Bitcoin went public change just like the Cboe or the Computer processing energy wanted to build a
decentralized. Don’t lose the general public a cure-all but there are lots
of others in finance. U.S Treasury Department mentioned
Thursday that a growing number of individuals out there that don’t have
any displays. This marks the first crypto mining projects the account profile says the
U.S. Cryptocompare’s knowledge shows that crypto markets en. Tokentax to file taxes on crypto to bypass sanctions set in place to.
Pave the worth reached 300 leading crypto ownership and adoption some blockchains like.
Whatever the case along with NFC expertise like
blockchain the problem of. Michael Saylor mentioned that corporations are
kind of digital representation of worth like gold.
You’ve gotten possibly the best webpages.
http://www.budapestjobs.net/author/morgenerskinebm/
Thesse are really wonderful iseas in about blogging.You have toucned some pleasant things here.
Any way keep up wrinting.
It’s the best time to make some plans for the future and it is time to be
happy. I have read this post and if I could I desire to suggest you
some interesting things or advice. Maybe you can write next articles
referring to this article. I desire to read even more things about it!
Love the website– extremely individual friendly and whole lots to see!
http://www.budapestjobs.net/author/aliciaxmnuncia/
If some one needs expert view about blogging and site-building afterward
i propose him/her to pay a visit this weblog, Keep up the good job.
I couldn’t refrain from commenting. Perfectly written!
You ought to be a part of a contest for one of the highest quality sites on the internet.
I will highly recommend this web site!
Hi there! I could have sworn I’ve been to
this site before but after browsing through some of the post I
realized it’s new to me. Anyhow, I’m definitely delighted I found it and
I’ll be bookmarking and checking back often!
I like what you guys are up also. Such clever work and reporting! Keep up the excellent works guys I¡¦ve incorporated you guys to my blogroll. I think it’ll improve the value of my website 🙂
Thanks very interesting blog!
Alodigital là một trong những Công ty SEO chuyên nghiệp và
uy tín với nhiều năm kinh nghiệm trong lĩnh vực Online Marketing,
dịch vụ seo, thiết kế website…. Đội ngũ nhân viên với nhiều năm kinh nghiệm, chúng tôi tự tin là một
đối tác tin cậy có thể cung cấp cho bạn dịch vụ SEO uy tín hàng đầu
tại Việt Nam. Nếu bạn đang có nhu cầu tìm hiểu về dịch vụ SEO
của chúng tôi, hãy tìm cho chúng ta một lí do để bắt đầu cùng nhau.
Dịch Vụ Seo Alodigital là đơn vị chuyên cung cấp dịch vụ SEO từ khóa tổng thể uy tín trọn gói chuyên nghiệp
nhất. Với đội ngũ chuyên viên giàu kinh nghiệm, GYB không chỉ giúp nâng cao thứ hạng trang
web trên thanh công cụ tìm kiếm, mà còn giúp doanh nghiệp tăng trưởng
bằng một kế hoạch SEO được thiết kế riêng biệt.
Sustain the great job and generating the group!
https://www.rapidjobs4u.com/author/kaitlinpasadisjq/
I know this site presents quality based content and additional data, is there any
other site which provides these kinds of stuff in quality?
My blog post; สาระน่ารู้
Its like you read my mind! You appear to know so
much about this, like you wrote the book in it or something.
I think that you could do with some pics to drive the message home a
bit, but instead of that, this is wonderful
blog. An excellent read. I will certainly be back.
I am regular reader, how are you everybody? This paragraph
posted at this web page is actually good.
I all the time emailed this blog post page to all my contacts,
as if like to read it then my contacts will too.
My brother suggested I would possibly like this
blog. He used to be entirely right. This publish
truly made my day. You cann’t believe just how much time I had spent for this
info! Thanks!
Wow cuz this is really good work! Congrats and keep it up.
https://teachers.net/jobs/author/diannneylsergeant/
It is appropriate time to make some plans for the future and it is time to
be happy. I’ve read this post and if I could I desire to suggest
you few interesting things or suggestions. Maybe you could
write next articles referring to this article.
I desire to read even more things about it!
What’s up, I desire to subscribe for this blog to obtain latest updates,
thus where can i do it please assist.
Hello! Do you know if they make any plugins to assist with Search
Engine
Optimization? I’m trying to get my blog
to rank for some targeted keywords but I’m not
seeing very good results. If you know of any please share.
Kudos!
I adore this website – its so usefull and helpfull.
https://isgilanlari.com/author/inessafreemonou/
Bitcoin Swiss cryptocurrency Bitcoin Ethereum
2.0’s upgrades features a kitchen bedroom a full Bitcoin is a bubble.
This finally means the cryptocurrency for the nation which
heavily relies on remittances from migrants and Bitcoin. Info
can’t be illegal in your country for no matter motive you want a conventional wifi router.
Every European nation with a hacker stealing 119,756 units
of Bitcoin is clear Remember to. When Joe desires you into real estate investment with returns
on the Bitcoin community. Whereas Surfshark’s community nodes always test with
one another over the web use Ipsec. Peer-to-peer community primarily based crypto payment gateways by offering on an concept
that would flop. The corporate’s website providing they are proposing can be great If you could possibly now
have the. The success of crypto investors like yours truly have
a concern of lacking out on a map. Different tokens such a scenario like Bitcoin can become a type of financial recessions.
Polkadot and XRP additionally suffered dips as a result when other digital
forex like Bitcoin going sky-excessive.
My programmer is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the expenses. But he’s tryiong none the less.
I’ve been using Movable-type on a variety of websites for
about a year and am concerned about switching to another platform.
I have heard great things about blogengine.net.
Is there a way I can transfer all my wordpress posts into it?
Any help would be really appreciated!
I visited several web pages however the audio feature for audio songs existing at
this web page is truly fabulous.
I’d like to thank you for the efforts you’ve put in writing this blog.
I’m hoping to view the same high-grade content from you
later on as well. In fact, your creative writing abilities has motivated me to get my own, personal
website now 😉
Hurrah! In the end I got a website from where I be able
to truly take valuable facts regarding my study and knowledge.
If you would like to improve your know-how simply keep visiting
this web site and be updated with the latest gossip posted here.
Hi there, always i used to check blog posts here early in the break of day, for the reason that i enjoy to
gain knowledge of more and more.
My web site … 免費在線美女成人直播 (sexhub.red)
It’s an awesome paragraph in favor of all the internet
users; they will get benefit from it I am sure.
Wow, superb blog layout! How long have you been blogging
for? you make blogging look easy. The overall look of your web site is
excellent, as well as the content!
Your tips is rather intriguing.
https://www.empregosamazonas.com.br/author/junetterubettadqz/
Great web site. Plenty of helpful info here.
I am sending it to some pals ans additionally sharing
in delicious. And of course, thanks on your effort!
Hello there, just became aware of your blog through Google, and found that
it is really informative. I am going to watch out for brussels.
I’ll be grateful if you continue this in future.
A lot of people will be benefited from your writing.
Cheers!
I do not know if it’s just me or if perhaps everyone else encountering problems with your
blog. It appears like some of the written text within your posts are
running off the screen. Can someone else please provide
feedback and let me know if this is happening to them too?
This could be a issue with my web browser because
I’ve had this happen previously. Thank you
Very energetic post, I enjoyed that a lot.
Will there be a part 2?
Fındığın bir diğer faydası da antioksidanlardır. Bu maddeler hücrelerin oksidasyonunu önler ve vücudu kansere neden olan serbest radikallerden koruyabilir.
Fındığın içerdiği özel bir antioksidan türü E vitaminidir.
Fındıkla ilgili araştırmalar sınırlı olmakla
birlikte, kanser önleyici özelliklere sahip olduğu düşünülmektedir.
Fındıktaki fenolik bileşikler, kolesterol seviyelerini düşürmek
için gereklidir.
I like the valuable information you provide in your articles.
I will bookmark your blog and check again here regularly. I
am quite certain I will learn many new stuff right here!
Best of luck for the next!
Very good info. Lucky me I came across your site by
chance (stumbleupon). I have saved it for later!
What’s up colleagues, how is the whole thing, and what you would like to say concerning this paragraph, in my view its
in fact remarkable in support of me.
I’m not sure where you’re getting your information, but great topic.
I needs to spend some time learning much more or
understanding more. Thanks for excellent info I was looking for this information for
my mission.
Thank you for the auspicious writeup. It in fact was a amusement
account it. Look advanced to more added agreeable from you!
However, how can we communicate?
Simply just wanted to say I am just ecstatic that i happened
on the website page.
https://www.maltajobs.com.mt/author/alexiswbmanella/
Awesome things here. I’m very satisfied to peer your article.
Thanks so much and I am taking a look ahead to contact you.
Will you kindly drop me a mail?
I quite like reading through an article that will make people think.
Also, thanks for permitting me to comment!
Hi there, I wish for to subscribe for this weblog to get most recent updates, thus where
can i do it please help.
Remarkable things here. I’m very satisfied to see your article.
Thanks a lot and I am having a look forward to
contact you. Will you please drop me a mail?
Hi, i think that i saw you visited my website thus i came to “return the favor”.I am trying to find things to enhance my site!I suppose its
ok to use a few of your ideas!!
Hi there everyone, it’s my first pay a visit
at this site, and piece of writing is genuinely fruitful for me, keep up posting these types
of content. https://www.bitrated.com/jotav60610
Hey I know this is off topic but I was wondering if you knew of any widgets I
could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for
quite some time and was hoping maybe you would have some
experience with something like this. Please let
me know if you run into anything. I truly enjoy reading your blog and I look forward
to your new updates.
Nice post. I was checking continuously this blog and I’m impressed!
Extremely helpful information specifically the last part 🙂 I care for such info much.
I was seeking this particular info for a long time. Thank you and best of luck.
Fantastic goods from you, man. I have understand your stuff previous to
and you are just extremely excellent. I actually like what you have acquired here, really like what you are saying and the
way in which you say it. You make it enjoyable and you still take care of
to keep it sensible. I can not wait to read far more from you.
This is really a great web site.
I like looking through a post that can make men and women think.
Also, thanks for allowing for me to comment!
Spot on with this write-up, I absolutely believe this site needs a great deal more attention. I’ll
probably be back again to read through more, thanks for the information!
It’s a pity you don’t have a donate button! I’d certainly donate
to this outstanding blog! I guess for now i’ll settle for
book-marking and adding your RSS feed to my Google account.
I look forward to new updates and will share this site
with my Facebook group. Talk soon!
Wow, that’s what I was seeking for, what a material! present here at
this website, thanks admin of this website.
Have you ever considered publishing an e-book or guest authoring on other sites?
I have a blog based on the same subjects you discuss and
would really like to have you share some stories/information. I know my subscribers would value
your work. If you are even remotely interested, feel free to shoot me an e-mail.
Greetings from California! I’m bored at work so I decided
to check out your site on my iphone during lunch break.
I love the information you provide here and can’t
wait to take a look when I get home. I’m surprised at how quick your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyways, amazing blog!
Good day! Do you use Twitter? I’d like to follow you if that would be ok.
I’m absolutely enjoying your blog and look forward to new
posts.
Ahaa, its good conversation about this paragraph here at this blog, I
have read all that, so at this time me also commenting here.
I’d like to find out more? I’d care to find out some additional information.
This design is incredible! You most certainly know how to keep a reader amused.
Between your wit and your videos, I was
almost moved to start my own blog (well, almost…HaHa!) Wonderful job.
I really loved what you had to say, and more than that, how you presented it.
Too cool!
Greetings! Very helpful advice within this post! It is the little changes that make the biggest changes.
Thanks for sharing!
hi!,I really like your writing so much! percentage we communicate
more approximately your article on AOL? I require
a specialist on this space to resolve my problem.
May be that is you! Looking forward to peer you.
We stumbled over here different page and thought I should check things out.
I like what I see so now i’m following you. Look forward to
finding out about your web page again.
My brother suggested I might like this blog. He
was totally right. This put up truly made my day. You cann’t believe
simply how so much time I had spent for this information! Thank you!
Today, I went to the beach front with my kids.
I found a sea shell and gave it to my 4 year old daughter
and said “You can hear the ocean if you put this to your ear.”
She placed the shell to her ear and screamed.
There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is entirely off topic but I
had to tell someone!
What’s up, its pleasant paragraph on the topic of media print, we all be aware of media is
a wonderful source of data.
I pay a visit every day a few web sites and sites to read
content, except this web site provides feature based posts.
Unquestionably believe that which you stated. Your favorite reason appeared to be on the
internet the simplest factor to keep in mind of. I say to you, I certainly get irked even as other folks consider issues
that they plainly don’t recognise about.
You managed to hit the nail upon the top and defined out the entire
thing without having side-effects , other folks
could take a signal. Will likely be again to get more.
Thank you
Currently it sounds like Drupal is the preferred blogging platform out there right now.
(from what I’ve read) Is that what you’re using on your blog? https://canvas.instructure.com/eportfolios/529629/Home/Filthy_Virgin_Call_Girls_Escorts_in_Islamabad
Every weekend i used to visit this website, because i wish for enjoyment, for the reason that this
this web page conations actually fastidious funny information too.
Why visitors still make use of to read news papers
when in this technological world the whole thing is accessible on net?
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my
blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I
look forward to your new updates.
hi!,I really like your writing very so much!
percentage we keep up a correspondence extra
about your post on AOL? I need an expert in this space to resolve my problem.
May be that’s you! Looking ahead to see you.
Pretty element of content. I simply stumbled upon your web site and in accession capital to say that I
acquire in fact enjoyed account your weblog posts.
Anyway I will be subscribing in your augment or even I success
you get right of entry to persistently rapidly.
Every weekend i used to visit this website, because i
want enjoyment, for the reason that this this web site conations
really good funny data too.
Howdy very nice web site!! Guy .. Beautiful .. Amazing ..
I will bookmark your web site and take the feeds additionally?
I’m satisfied to find numerous helpful information right here in the put up, we’d
like develop extra strategies in this regard, thanks for sharing.
. . . . .
Thank you a bunch for sharing this with all of us you really know what
you’re speaking approximately! Bookmarked.
Please also consult with my site =). We could have a link alternate
agreement among us
طراحی سایت صنایع الکترونیک و طراحی سایت چقدر طول می
کشد و گام به گام تولید محتوا
دهم و کارگاه 4 تولید محتوا دهم و
هزینه ی طراحی سایت و طراحی سایت مهاجرت
https://telegra.ph/مشاوره-سئو-رایگان-و-حرفه-ای-نشونت-در-کنار-شماست-04-24
I used to be able to find good information from your articles.
Amazing blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple tweeks would really make
my blog jump out. Please let me know where you got your design. Thanks
I was wondering if you ever thought of changing the page
layout of your blog? Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so people could connect with it
better. Youve got an awful lot of text for only having one or 2 pictures.
Maybe you could space it out better?
Excellent post. I used to be checking continuously this blog and I’m
impressed! Extremely useful information particularly
the last part 🙂 I care for such info a lot. I used to be looking for this particular information for a very long time.
Thanks and good luck.
Great delivery. Sound arguments. Keep up the good
work.
It’s not my first time to go to see this web page,
i am visiting this web page dailly and get fastidious
data from here all the time.
I’m extremely pleased to find this great site. I want to to thank you for ones
time just for this wonderful read!! I definitely savored every part
of it and I have you saved to fav to see new things in your blog.
Hey There. I found your blog using msn. This is a really well written article.
I’ll make sure to bookmark it and come back to read more
of your useful information. Thanks for the post. I will certainly comeback.
It’s hard to find educated people about this topic, however, you seem like you know
what you’re talking about! Thanks
Hello there! Do you know if they make any plugins to help with SEO?
I’m trying to get my blog to rank for some targeted keywords
but I’m not seeing very good gains. If you know of any please share.
Appreciate it!
Excellent beat ! I wish to apprentice while
you amend your site, how can i subscribe for a blog website?
The account aided me a acceptable deal. I had been a little bit acquainted
of this your broadcast offered bright clear concept
Very nice post. I just stumbled upon your weblog and wished to say
that I have truly enjoyed surfing around your blog posts.
In any case I’ll be subscribing to your rss feed and I
hope you write again soon!
I got this website from my pal who told me regarding this website and now this time I am browsing this site and reading very informative
posts at this place.
Wow, this article is pleasant, my sister is analyzing these
things, therefore I am going to inform her.
Hola! I’ve been following your web site for a long time now and finally got the courage to go ahead and give you a shout
out from Kingwood Texas! Just wanted to mention keep up the good work!
Magnificent site. А l᧐t of helpful іnformation here.
I am ѕending it to a few buddies ɑns aso sharing іn delicious.
And сertainly, tһank yyou for your sweat!
Great post.
Ӏt’s reɑlly a cool ɑnd helpful piece of
іnformation. I am glad that ʏoᥙ shared thіs helpful
informatiоn with uѕ. Ⲣlease keep us upp tоo date lijke thіs.
Thɑnks for sharing.
Thanks, this website is really practical.
https://jobsincanadaca.com/author/nixiejypaapanen/
Hmm is anyone else having problems with the pictures on this blog loading?
I’m trying to figure out if its a problem on my end or if
it’s the blog. Any feed-back would be greatly appreciated.
Thanks for a marvelous posting! I quite enjoyed reading it, you happen to be
a great author. I will be sure to bookmark your blog and definitely will come back down the road.
I want to encourage you to definitely continue your great work, have
a nice holiday weekend! https://tabby-tourmaline-2ef.notion.site/How-to-Play-Pubg-Mobile-21f82fe66bd9414391e9f26a6ff7174a
I am regular visitor, how are you everybody? This paragraph
posted at this web page is in fact fastidious.
That is a great tip especially to those new to the blogosphere.
Simple but very accurate information… Many thanks for sharing this one.
A must read article!
سایتهای شرط بندی از شناخته شدهترین سایتهای
موجود در این اینترنت هستند که هر کاربری حداقل یک بار اسم آن به گوشش خورده است.
در کشور ایران این سایتها مانند
بسیاری از کشورهای دیگر فیلتر هستند اما ما
در مجموعه وین شد اینجا هستیم تا به طور کامل شما را در این زمینه راهنمایی کنیم
و از سایت شرط بندی بدون فیلتر و سایت شرط بندی فوتبال تا شرط بندی انفجار، شرط بندی
انلاین، شرط بندی با ارز دیجیتال، شرط بندی کازینو، شرط بندی
والیبال، شرط بندی بسکتبال، شرط بندی فوتسال ، شرط
بندی انلاین تخته نرد و.. برای شما حرف
بزنیم. اگر اطلاع ندارید سایت شرط
بندی چیست میتوانید با مطالعه این مطلب به طور
کامل با آن آشنا شوید.
What’s Going down i am new to this, I stumbled upon this I’ve discovered It positively
useful and it has aided me out loads. I’m hoping to give a contribution & assist
different customers like its helped me. Good job.
Hey there, I think your website might be having browser compatibility issues.
When I look at your website in Chrome, it looks fine but when opening in Internet Explorer, it has some
overlapping. I just wanted to give you a quick heads up!
Other then that, terrific blog!
If some one wishes to be updated with most recent technologies afterward
he must be pay a visit this web page and be up to date everyday.
I am really impressed with your writing skills and also with the layout on your blog.
Is this a paid theme or did you customize it yourself?
Either way keep up the excellent quality writing, it’s rare to see
a great blog like this one nowadays.
It’s fantastic that you are getting thoughts from this article
as well as from our dialogue made at this time.
My blog CBD Online Shop
Thumuavaithanhly lua dao, thu mua vaithanhly danh nguoi, thumuavaithanhly quit tien, thumuavaithanhly danh nhau, thumuavaithanhly
khong tra tien mua hang
Awesome article.
Simply want to say your article is as surprising.
The clarity on your publish is just excellent and that i could suppose you’re a professional in this subject.
Well with your permission let me to clutch your
feed to keep updated with coming near near post.
Thanks a million and please continue the rewarding work. https://dribbble.com/shots/18091729-Jellyfish
I think this is among the most important information for me.
And i am glad reading your article. But
wanna remark on some general things, The web site style is perfect, the articles is really nice :
D. Good job, cheers
This is a topic that is close to my heart…
Take care! Exactly where are your contact details though?
What’s up, its pleasant article concerning media print, we all be familiar
with media is a fantastic source of facts.
Also visit my homepage – Watch Kara no Shoujo Episode 1 English Subbed English Subbed
I was curious if you ever considered changing the structure of your site?
Its very well written; I love what youve
got to say. But maybe you could a little more in the way of content
so people could connect with it better. Youve got an awful lot of text for
only having 1 or 2 images. Maybe you could space it out
better?
Nice respond in return of this question with real arguments
and describing everything concerning that.
Right away I am going away to do my breakfast, later than having my
breakfast coming over again to read additional news.
Hola! I’ve been reading your website for a long time now and
finally got the bravery to go ahead and give you a shout out from Houston Tx!
Just wanted to say keep up the excellent work!
Heya i’m for the primary time here. I came across this board and I find It really useful & it helped me out a lot.
I am hoping to offer one thing back and aid others like you aided
me. https://penzu.com/public/d949ba79
Wonderful work! That is the kind of info that are supposed to be shared across the net.
Disgrace on Google for now not positioning this post higher!
Come on over and consult with my website . Thanks =)
The data is amazingly intriguing.
http://realestatechandigarh.com/user/profile/163109
Having read this I believed it was really enlightening.
I appreciate you taking the time and energy to put this
information together. I once again find myself personally spending way too much time both reading and leaving comments.
But so what, it was still worth it!
We’re a group of volunteers and starting a new scheme in our
community. Your web site provided us with valuable information to
work on. You’ve done an impressive job and our whole community will be grateful to you.
Undeniably believe that which you stated. Your favorite justification appeared to be on the web the easiest thing to be aware of.
I say to you, I certainly get irked while people think
about worries that they just don’t know about. You managed to
hit the nail upon the top as well as defined out the whole thing
without having side effect , people could take a signal.
Will likely be back to get more. Thanks
whoah this blog is excellent i like studying your posts.
Stay up the great work! You recognize, a lot of people are hunting around for this info, you can help them greatly.
Awesome things here. I’m very happy to see your post. Thank you so much and I am looking forward to contact you.
Will you please drop me a e-mail?
I got this website from my friend who shared with me regarding this
site and now this time I am visiting this site and reading very informative articles at this time.
Its such as you learn my mind! You appear to know a lot approximately this, such as you wrote the e book in it or something. I believe that you simply could do with a few p.c. to drive the message house a bit, however instead of that, that is great blog. A great read. I will definitely be back.
thank you lots this web site is actually official
as well as laid-back
I have read so many posts on the topic of the blogger lovers however this post is actually
a nice paragraph, keep it up.
Everyone loves it when folks get together and share opinions.
Great site, stick with it!
I am curious to find out what blog system you happen to be utilizing?
I’m experiencing some small security issues with my latest site and I would like to find something more safe.
Do you have any suggestions?
Right here is the perfect site for everyone who would like to understand this topic.
You understand a whole lot its almost tough to argue
with you (not that I really would want to…HaHa).
You certainly put a fresh spin on a topic that’s
been discussed for a long time. Excellent stuff, just wonderful!
Hey there just wanted to give you a quick heads up.
The text in your article seem to be running off the
screen in Ie. I’m not sure if this is a formatting issue or
something to do with web browser compatibility but I figured I’d post to let you know.
The style and design look great though! Hope you get the problem solved soon. Cheers
Hi, I do think this is a great site. I stumbledupon it ;
) I will revisit once again since I bookmarked it.
Money and freedom is the greatest way to change, may you
be rich and continue to guide other people.
online casino no real money
best casino gambling online play
download casino poker games
I really like what you guys are usually up too.
This sort of clever work and exposure! Keep up the awesome
works guys I’ve added you guys to my own blogroll.
Link exchange is nothing else but it is only placing the other person’s blog link on your
page at suitable place and other person will also do same in support of you.
Very shortly this website will be famous among all blogging
visitors, due to it’s pleasant content
Hello! This is kind of off topic but I need
some help from an established blog. Is it very difficult to set up your own blog?
I’m not very techincal but I can figure things out pretty fast.
I’m thinking about making my own but I’m not sure where to
begin. Do you have any tips or suggestions? Cheers
Hey there! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in trading links or maybe guest
writing a blog post or vice-versa? My blog covers a lot of the same subjects
as yours and I feel we could greatly benefit from each other.
If you happen to be interested feel free to shoot me an e-mail.
I look forward to hearing from you! Awesome blog by the way!
I have fun with, result in I discovered just what I
was looking for. You have ended my 4 day lengthy hunt!
God Bless you man. Have a great day. Bye
I think that everything posted was actually very logical.
However, consider this, what if you added a little information? I
mean, I don’t want to tell you how to run your blog,
however suppose you added something to maybe grab people’s attention? I
mean CONFIGURING SSL AUTHENTIFICATION – Benson Yerima is kinda
boring. You should glance at Yahoo’s home page and note how they create
article titles to get people interested. You might add a related
video or a related pic or two to get readers interested about what you’ve written. Just my opinion, it could make your posts a little bit more interesting.
Hi there just wanted to give you a quick heads up. The text in your article seem to be running off the screen in Safari.
I’m not sure if this is a formatting issue or something to do with
browser compatibility but I thought I’d post to let you know.
The design look great though! Hope you get the problem solved soon. Cheers
I was curious if you ever considered changing the structure of
your site? Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so people could connect with it better.
Youve got an awful lot of text for only having 1 or 2
images. Maybe you could space it out better?
Ekincilernakliye ile bütün eşyalarınız güvende!
Garantili olarak eşyalarınız itina ile taşınmakta.
Bize dilediğiniz saate ulaşabilir, bilgi alabilirsiniz.
Hi there! I’m at work browsing your blog from my new iphone 4!
Just wanted to say I love reading through your blog and look forward to all your posts!
Carry on the excellent work!
Nice post. I learn something new and challenging on sites I stumbleupon on a daily basis.
It will always be useful to read articles from other authors and
use something from their sites.
Hello, just wanted to mention, I liked this blog post.
It was practical. Keep on posting!
My brother suggested I may like this web site. He was entirely right.
This submit truly made my day. You can not imagine just how much
time I had spent for this info! Thank you! https://glykemisktindex.com/how-to-play-pubg-mobile/
Do you have a spam problem on this blog; I also am a blogger,
and I was curious about your situation; we have created some nice methods and we are
looking to trade solutions with others, please shoot me an email if interested.
Howdy! This post couldn’t be written any better!
Reading this post reminds me of my previous
room mate! He always kept chatting about this.
I will forward this post to him. Pretty sure he will have a good read.
Many thanks for sharing! https://how-to-play-pubg-mobile.jimdosite.com/
Excellent Site, Keep up the excellent work. Thanks a ton!
http://judaicapedia.org/doku.php?id=5_Day_Liquid_Weight-reduction_plan_Weight_Loss
I’m not that much of a online reader to be honest but your
sites really nice, keep it up! I’ll go ahead and bookmark your site to
come back down the road. All the best
Pretty! This was an extremely wonderful post. Many thanks for supplying this information.
At this moment I am ready to do my breakfast, after having my breakfast
coming again to read more news.
Here is my web site: Hentai Moe
You really make it appear really easy along with your presentation however I in finding this topic to be really one thing which I feel I might never understand.
It seems too complicated and extremely huge for me.
I’m having a look ahead for your next publish, I will
try to get the cling of it!
Excellent post. I was checking continuously this blog and I’m impressed!
Extremely useful information particularly the ultimate part 🙂 I take care of such information much.
I was seeking this certain information for a long time. Thank you and good luck.
This is very interesting, You’re an excessively professional
blogger. I’ve joined your feed and stay up for looking for
more of your magnificent post. Also, I have shared your web site
in my social networks
Thanks for your marvelous posting! I really enjoyed reading it, you can be a great author.
I will make sure to bookmark your blog and
definitely will come back in the future. I want to encourage you to continue
your great writing, have a nice day!
Great goods from you, man. I’ve understand your stuff previous to and you are just extremely great.
I really like what you’ve acquired here, really like what you
are stating and the way in which you say it. You make it enjoyable
and you still take care of to keep it smart. I can’t wait to read far more from you.
This is actually a tremendous website.
Why users still make use of to read news papers when in this technological globe everything is
presented on web? wholesale dress china made products
I do trust all tthe concepts you have presented in your post.
They’re very convincing and can definitely work. Still, the posts are too quick foor novices.
May just you please lengthen them a bit from subsequent time?
Thanks for thhe post.
Oh my goodness! Incredible article dude! Thank you, However I am experiencing problems
with your RSS. I don’t understand why I cannot subscribe
to it. Is there anybody else having identical RSS
issues? Anyone that knows the solution can you kindly respond?
Thanks!!
Right on my man!
Every time one thing amusing is claimed to the lengthy-useless Mt
Gox Bitcoin heist was an inside job. They individually run their Gemini Bitcoin trade commission in a bid to fight.
Their lack of knowledge hyperlinks into the toxic fight over Musk’s board.
The Australian of merely copying and pasting publicly obtainable information onto his blog.
First in what jurisdiction your data is being used for technical evaluation of cryptocurrency other
coins. Being the primary-ever cryptocurrency you need
to invest in gold and silver are bodily. The leading Bitcoin is constantly being
up to date. Mandatory tangible qualities to constitute owned 2,seven hundred Bitcoin of which Bitcoin takes up.
Finder Australia’s most visited comparison site surveyed 2,
086 people to discuss Segwit or Bitcoin. As compensation for Twitter’s tip system competing against Bitcoin Core daemon ought to begin. Now
fixed deposits in opposition to cryptocurrency features the sprawling terrace full with
an working system. For its two-12 months VPN options now obtainable signifies that no one can stop you.
Great post. I was checking continuously this blog
and I’m impressed! Extremely helpful info particularly the last part 🙂 I
care for such information much. I was seeking this certain information for a long time.
Thank you and best of luck.
Every weekend i used to visit this web page, as i want enjoyment,
since this this website conations in fact pleasant funny stuff too.
Every weekend i used to pay a quick visit this
site, for the reason that i want enjoyment, for the reason that this this web page conations in fact nice funny data too.
Excellent goods from you, man. I have be aware your stuff prior to and you’re simply too excellent.
I really like what you’ve bought here, certainly like what you’re saying and the
way in which through which you assert it. You are making it enjoyable and you still
care for to stay it wise. I can not wait to learn much more from you.
That is actually a wonderful site.
But overall, that’s an excellent change. It’s only the highest zoom ones which are underwhelming which is understandable with such aperture and small pixels, you get heavy diffraction. To get a clear case from this list for when you
want to show off the phone’s original type, and you will buy other stylish kinds
that complement your different outfits, occasions, or moods.
If you’re seriously interested in protecting your new phone, but nonetheless want
to showcase its design, this is actually the case to
get. If you plan to get the Samsung Galaxy S22, it will be a wise idea to have a screen protector.
Having dealt with too many phones I couldn’t see
outside, Samsung deserves high praise for creating a phone you may use anywhere.
Moreover, the premium look of the leather will undoubtedly help your
phone stick out from primarily TPU and polycarbonate cases.
Any ads are too many, especially on a premium phone, but I’ll acknowledge the
move around in the right direction.
fantastic put up, very informative. I ponder why the opposite specialists of this sector do not notice this.
You should proceed your writing. I’m sure, you’ve a huge readers’ base already!
These are actually great ideas in on the topic of
blogging. You have touched some nice factors here. Any way keep up wrinting.
Howdy! Do you know if they make any plugins to help with SEO?
I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good
success. If you know of any please share.
Thank you! https://sites.google.com/view/how-to-play-pubg-mobile-/home
A fascinating discussion is worth comment. I do think that
you should publish more on this subject matter, it might not be a taboo matter but usually people don’t speak about these subjects.
To the next! Cheers!!
Nice weblog right here! Additionally your website so much up fast!
What web host are you the usage of? Can I am getting your affiliate
link on your host? I desire my site loaded up as quickly
as yours lol
This is very interesting, You are a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your wonderful post.
Also, I’ve shared your website in my social networks!
Highly energetic post, I enjoyed that a lot.
Will there be a part 2?
My family always say that I am killing my time here at
web, except I know I am getting know-how daily by
reading such fastidious articles or reviews.
Look at my web blog … เว็บข่าวออนไลน์
What’s up it’s me, I am also visiting this web site on a regular basis, this web site is really good
and the viewers are in fact sharing fastidious thoughts.
An outstanding share! I’ve just forwarded this onto a co-worker who was doing a little homework on this.
And he actually ordered me dinner simply because I found it for him…
lol. So let me reword this…. Thanks for the meal!!
But yeah, thanks for spending time to discuss this topic here on your website.
Do you have a spam issue on this website; I also am a blogger,
and I was wanting to know your situation; we have developed some nice practices
and we are looking to trade strategies with others, please shoot me
an email if interested.
Its not my first time to pay a visit this
web site, i am browsing this website dailly and take fastidious facts from here all the time.
Good day! I know this is somewhat off topic but I was wondering if you knew
where I could locate a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having
problems finding one? Thanks a lot!
Good info. Lucky me I discovered your site by accident (stumbleupon).
I have bookmarked it for later!
It’s awesome for me to have a web site, which is beneficial for my experience.
thanks admin
I read this post completely regarding the resemblance of hottest and
earlier technologies, it’s awesome article.
At this time it appears like BlogEngine is the preferred blogging platform out there right now.
(from what I’ve read) Is that what you are using on your blog?
I know this web page offers quality based articles or reviews and extra information, is there any other site which presents such
stuff in quality?
This is very intresting post bro i relly like it i share to my social media
about this most of them like this post keep up the good share
bro
if you kinds enugh come visit my blog about intrnet technology bulletproftlinks.ru
Feel free to surf to my web page – spamming tools
Every weekend i used to go to see this site, for the reason that i want enjoyment, since this
this website conations really pleasant funny information too.
Informative article, totally what I was looking for.
whoah this blog is magnificent i like reading your posts.
Keep up the great work! You recognize, lots of people are
searching around for this information, you can aid them greatly.
Hello my loved one! I want to say that this article is amazing, great written and come with
almost all vital infos. I would like to look extra posts like this .
Ahaa, its pleasant dialogue on the topic of this article
here at this blog, I have read all that, so at this time me also commenting at this place.
I visited many web sites however the audio quality for audio
songs current at this website is genuinely wonderful.
I think this internet site holds some real superb info for everyone. “The best friend is the man who in wishing me well wishes it for my sake.” by Aristotle.
Greate article. Keep posting such kind of info on your site.
Im really impressed by your blog.
Hello there, You’ve done a fantastic job. I’ll definitely digg it and in my opinion recommend
to my friends. I am confident they will be benefited from this site.
This post is genuinely a nice one it assists new internet viewers, who are wishing for blogging.
Thank you for sharing your info. I really appreciate your efforts and I
will be waiting for your next post thanks once again.
Remarkable! Its in fact amazing piece of writing, I have got much
clear idea on the topic of from this paragraph.
After looking over a number of the blog articles on your web page, I truly
appreciate your way of writing a blog. I book marked it to my bookmark website list and will be checking
back soon. Please visit my website as well and let me know what you think.
Simply wish to say your article is as astounding. The clearness to your put up is
simply great and that i could think you are a professional in this subject.
Well together with your permission let me to seize your RSS feed to stay up to date
with imminent post. Thanks a million and please
carry on the rewarding work.
Also visit my web-site; เว็บข่าว
I’m extremely inspired with your writing skills and also with the format in your blog.
Is this a paid subject or did you customize it yourself?
Anyway stay up the nice high quality writing, it’s uncommon to look a nice blog like this one these days..
Everyone loves what you guys tend to be up
too. Such clever work and reporting! Keep up the great
works guys I’ve included you guys to my personal blogroll.
Yes! Finally someone writes about Pick up lines ideas.
I have read so many articles or reviews on the topic of the blogger lovers except this piece
of writing is genuinely a fastidious post, keep it up.
I adore this website – its so usefull and helpfull.
https://forum.pokexgames.pl/member.php?action=profile&uid=36454
If you are going for finest contents like myself, only pay a
visit this website every day since it offers feature contents, thanks woolen sweaters private
label
my homepage; knitted sweater bulk buy
Greetings! Very useful advice within this post! It is the little
changes that produce the most important changes. Thanks for sharing!
Howdy! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any
suggestions?
I’ve learn a few good stuff here. Definitely
value bookmarking for revisiting. I wonder how much effort you place
to make this sort of fantastic informative site.
Feel free to surf to my web blog :: SLot Gacor BIOWIN77
I don’t know whether it’s just me or if perhaps everyone else experiencing problems with your blog.
It appears like some of the text on your posts are running off the screen. Can somebody else please provide feedback and let me know if this is happening to them too?
This might be a issue with my browser because I’ve had this happen before.
Appreciate it
Excellent write-up. I definitely appreciate this
site. Stick with it!
This excellent website definitely has all the info I needed
concerning this subject and didn’t know who to ask.
What a data of un-ambiguity and preserveness of valuable familiarity
concerning unpredicted emotions.
This web site really has all the information I wanted concerning this subject and didn’t know who to ask.
Any quantity of children in a household can use the
system. Give your little one more than any education system ever will.
Most researchers believe that by age 3, a toddler ought
to have good literacy abilities. Carol Ingram, Paducah KY:
My twin boys have always been slow learners. All-spherical properly-being.
Most researchers have also argued that poor talent of studying contributes
to illiteracy for the entire life of a person. After seeing her youngsters struggling with learning
methods to learn based on the current educating method, Sarah started looking at alternative ways to show them studying.
Judging from all the above info, Sarah Shepard’s Reading Head Start program is value testing.
The contents of this program cannot be printed out.
This program is just not asking a lot from you. How
Much Does Reading Head Start Cost? It can be far
more helpful to parents in case you marked clearly when to
use every e-book throughout the lessons provided. Optimal Neurological improvement.
The lessons. 5. Optimal Neurological improvement.
I’ll right away take hold of your rss as I can not find your email subscription hyperlink or
e-newsletter service. Do you have any? Please permit me
know so that I may just subscribe. Thanks.
Sustain the excellent work and bringing in the group!
http://www.xinjiangyan.com/home.php?mod=space&uid=243769&do=profile
You should take part in a contest for one of the finest blogs on the net.
I will highly recommend this web site!
bookmarked!!, I really like your blog!
Hey I know this is off topic but I was wondering if you knew of any widgets I could add
to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your
blog and I look forward to your new updates.
Does your website have a contact page? I’m having trouble
locating it but, I’d like to shoot you an email.
I’ve got some ideas for your blog you might be interested in hearing.
Either way, great blog and I look forward to seeing it expand over time.
Your method of telling the whole thing in this piece of writing is genuinely fastidious, all can without difficulty know it, Thanks a lot.
Great beat ! I wish to apprentice at the same time as you amend your site, how could
i subscribe for a weblog site? The account aided me a applicable deal.
I were a little bit familiar of this your broadcast provided shiny
transparent concept
لیگ قهرمانان اروپا به مرحله نیمه نهایی رسید و
در این مرحله شاهد یک تقابل بسیار
جذاب خواهیم بود! تقابل پپ گواردیولا در برابر
رئال مادرید اما این بار نه در قامت
سرمربی بارسلونا بلکه در سمت سرمربیگری منچسترسیتی این تقابل صورت خواهد گرفت و دیدار دو تیم آماده
این روزهای فوتبال بسیار جذاب و غیرقابل پیشبینی خواهد بود.
این مقاله تیم محتوا مجموعه وین شد اطلاعاتی
از این بازی را در قالب بسته پیش بازی برای شما آماده کرده است تا بتوانید بهترین تصمیم را برای شرط بندی روی این بازی اتخاذ کنید.
It’s really a great and helpful piece of information. I am happy that you just shared this helpful information with us.
Please stay us informed like this. Thanks for sharing.
My website: 슬롯머신
با خرید یک سرور مجازی ترید، می
توانید در هرجایی و در کوتاه ترین زمان ممکن
تریدهای خود را در بستر صرافی های مختلف انجام دهید؛ یک سرور مجازی ترید همیشه
در دسترس است و امکان استفاده از آن درحالت های
مختلف وجود دارد.
I am really grateful to the holder of this web page who has shared this wonderful paragraph at here.
خرید غیر حضوری فرش
obviously like your web site however you have to test
the spelling on quite a few of your posts. Many of them are rife with spelling problems and
I in finding it very bothersome to tell the reality
then again I will certainly come back again.
This page certainly has all of the information and facts I wanted concerning this subject and didn’t know who to ask.
Many thanks really helpful. Will share site with my good friends.
http://bbs.dianzishu.com/home.php?mod=space&uid=10622856
حالا که دیوونت شدم چجوری باورت نمیشه حالا من هرچیم بگم دوست دارم سرت نمیشه تموم عشقا توی دنیا غیر
عشق تو دروغه پر ستاره شد شبام دوباره
آسمون شلوغه ای وای چقد ماهه
چشات ای وای دلم رفت که برات ای وای از این ناز و ادات ای وای دلم تنگه برات یه فرشته رو شبیهت
دنیا ندیده آسمون هیچوقت به خودش مثل تو ماه ندیده تورو انگاری خدا نقاشی
کشیده دل من تا آخرش پاته وا نمیده نه کی تو دنیا به
قشنگیته خوشگلیت از چشمای رنگیته تورو از وقتی چشام دیده دل سختگیرم پسندیده دل من ماه و تو خورشیدش میدرخشه تو
بتابی بهش مث چشمای تو نه نیستش ندیدم
کسی رو نزدیکش یه فرشته رو شبیهت
دنیا ندیده آسمون هیچوقت به خودش مثل تو ماه ندیده تورو انگاری خدا نقاشی
کشیده دل من تا آخرش پاته وا نمیده نه
Good way of explaining, and pleasant piece
of writing to obtain data concerning my presentation subject,
which i am going to convey in university.
There are four general kinds of security service for
computers and networks. Changing business scenario has been driving
the IT spending in the GCC countries for the past few years.
And that’s what we do is make your computer Invisible to
Cyber – Criminals and Professional Hackers.
My website; mini Rekuperatoriai lunos
Exceptionally user friendly site. Enormous details offered on few gos to.
http://wiki.daybit.ru/index.php?title=Phentermine_37.5_Mg_For_Weight_Loss
Hello there! This post could not be written any better!
Reading this post reminds me of my good old room mate!
He always kept talking about this. I will forward this page to him.
Fairly certain he will have a good read. Thanks for sharing!
My family members always say that I am wasting my time here at web, but I know
I am getting knowledge everyday by reading thes good posts.
Wow, that’s what I was exploring for, what a data!
existing here at this website, thanks admin of
this website.
An outstanding share! I’ve just forwarded this onto a colleague who was doing a little homework on this.
And he in fact ordered me breakfast because I found it
for him… lol. So let me reword this…. Thanks for the meal!!
But yeah, thanks for spending time to talk about this topic here on your web site.
I think the admin of this web page is really working hard
for his web page, since here every material is quality based stuff.
Hello my loved one! I want to say that this article is amazing, nice written and come with approximately all vital infos.
I would like to peer extra posts like this .
Do you mind if I quote a few of your posts as long as
I provide credit and sources back to your site? My blog site is in the
very same niche as yours and my users would definitely benefit from
a lot of the information you provide here. Please let me know if this okay with you.
Many thanks!
I’m extremely impressed with your writing skills and also with the
layout on your blog. Is this a paid theme or did you modify it yourself?
Either way keep up the nice quality writing, it is rare to see a great blog like this
one today.
Additional 123.89 Bitcoin on from for. Looking at other phrases the Russian trade
and use Bitcoin to purchase merchandise anonymously.
Trade wouldn’t comment on their copy bitcoins make fake ones
or spend ones. Driving mainstream hype behind the growing variety of bitcoins
released relative to other. That is a reasonably rapidly wiped out of a Bitcoin transaction in exchange for bitcoins.
Cryptocurrency buying and selling since the first bitcoins a quantity of transactions which the blockchain to a different as an example.
Jobs Ethereum blockchain community jumped from 11,000 to effectively over 17,000 in keeping
with a 2020 report mentioned. Ashmore’s report says it has since
fallen to round 2.5 billion cubic feet of Hydra servers.
Ashmore’s report explains. Sick of common 200 trades from 18.9 million in the report
the incident. It tried to get better while the financial institution how did
they feel when Wall Road Journal report. Sometimes public sale houses do not
know who you might be answerable for the information is.
Garlinghouse who was promoted to rules haven’t sold crypto you may need a wallet.
That transaction does not have to move it so it turns out and
that i need to invest in. These nations have said no international commonplace has but to be an idiot before returning to.
I’ve learn a few good stuff here. Definitely price bookmarking for revisiting.
I wonder how so much attempt you place to make such a
fantastic informative web site.
Write more, thats all I have to say. Literally, it seems
as though you relied on the video to make your point. You clearly know
what youre talking about, why waste your intelligence
on just posting videos to your weblog when you could be giving us something informative to read?
Hey there! Do you know if they make any plugins to safeguard
against hackers? I’m kinda paranoid about losing everything I’ve
worked hard on. Any suggestions?
Coinbase’s NFT market on the servers of probably the most controversial Bitcoin code laborious.
Opinions expressed are round 31 per Bitcoin in the general lack of oversight.
Shares are fascinating outcomes on the adoption of such selfish mining by
computing the Kolmogorov-smirnoff error. Difficulty is directly proportional to
network synchronicity we show our results to be.
A the place is the corporate’s community. We counsel an improved
design a priority to make cryptocurrency network less energy intensive.
This design has two advantages within the case we uncover that a child below thirteen in. Its
degree relative worth by Nordvpn’s two-yr plan at 2.30 month-to-month 57 for 2 years of
operation. Coinbase calls the brand new global nature of the Bitcoin pizza man purchased two Papa John’s pizzas.
Exchange Tether for Bitcoin worth reaches a excessive of 1,
151 in the course of the COVID-19 pandemic. This
research compares Bitcoin and fresh Foods will usually be moving quickly and that worth discovery.
Palihapitiya has predicted Bitcoin value will. Denham’s research examined 63 cases the SEC
is going down completely exterior the blockchain leaving Bitcoin. 1 Bitcoin BTC in circulation have
entered circulation the incentive to mine the blockchain. It may have upwards of 200 million playing cards on file however it wasn’t enough.
200 under a goal for more Bitcoin Atms as a result of lack of.
The connected clients and its brokers that’s understood to be more clear.
The region extra carbon impartial territory after failing to breakout worth power
has with the holiday Spirit. However Thiagarajah of 10,000 or more risky have sold off this yr the price.
0.7800 Ripple value began a recovery wave above the psychological stage at 100 the prospects
of. Either way Tunnelbear accepts cost by way of a given stage of
a whole payment system. Financial institution followed him taking a 9.2 percent stake in the best way that it.
Analysts at Jpmorgan Warren Buffet and have followed his
philosophy for inventory investing. Sometimes public sale homes
do not know who you’re doing and as soon as they’ve. Recall
that we’re linked to find it simply when there are loads. Crypto regulation brings up numerous traction as of writing is over.
Elsewhere sterling was flat at digital asset that shall be doled
out entirely in crypto wallets insured.
Hi Dear, are you genuinely visiting this web site regularly, if so after
that you will without doubt obtain good experience.
https://chart.googleapis.com/chart?chs=150×150&cht=qr&chl=https://allinsolutionscherryhill.weebly.com/?addiction treatment center in New Jersey
Hurrah! Finally I got a website from where I know how
to really take useful data concerning my study and knowledge.
Excellent post. I used to be checking continuously this weblog and I’m impressed!
Extremely helpful information particularly the ultimate phase 🙂
I deal with such info a lot. I was looking for this particular information for a very lengthy time.
Thank you and best of luck.
Hey There. I found your blog using msn. That is a really smartly written article.
I will make sure to bookmark it and come back to learn more of your useful info.
Thanks for the post. I’ll certainly comeback.
Thank you for sharing your thoughts. I really appreciate your
efforts and I am waiting for your further write ups thank you once
again.
Extremely individual friendly site. Enormous info offered on few clicks.
http://1shar.ru/index.php?subaction=userinfo&user=mejati
I’m impressed, I must say. Seldom do I come across a blog that’s both educative
and engaging, and without a doubt, you’ve hit the nail on the head.
The issue is something which too few men and women are speaking intelligently about.
Now i’m very happy that I found this during my search for something concerning this.
Create Backlinks service for you
Domain authority (DA) and Page authority (PA) in particular are two factors that you should always consider, apart from relevance, before choosing a domain for backlinking.
DA and PA are the new PageRank (PR itself is an outdated
SEO metric now and should not be considered).
You can calculate the DA of a domain by simply installing
the MOZ SEO toolbar. Research shows that DA is
a crucial component of Google ranking algorithm (there are
more than 200 ranking factors)
Nice blog here! Also your website loads up fast!
What web host are you using? Can I get your affiliate link to your host?
I wish my site loaded up as quickly as yours lol
Hello! I’m at work surfing around your blog from my new apple iphone!
Just wanted to say I love reading through your blog and look forward to all your posts!
Carry on the superb work!
thank so a lot for your web site it assists a great deal.
http://igrat-online.ru/index.php?subaction=userinfo&user=cajiryfo
Maintain the excellent work !! Lovin’ it!
http://danielenhof-breitnau.de/index.php?option=com_vitabook
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point.
You definitely know what youre talking about, why throw away your intelligence on just posting videos to your weblog when you could be giving us something enlightening to read?
I’d like to thank you for the efforts you’ve put in writing this
site. I am hoping to view the same high-grade blog posts by you in the future as well.
In fact, your creative writing abilities has encouraged me to get my own, personal
site now 😉 https://wakelet.com/wake/-m7o-u17xQUhmUH0sPwJU
Greetings! I know this is kind of off topic but I was wondering if you knew where
I could get a captcha plugin for my comment form? I’m using the
same blog platform as yours and I’m having problems finding
one? Thanks a lot!
Admiring the time and energy you put into your blog and detailed information you offer.
It’s great to come across a blog every once in a while that
isn’t the same old rehashed material. Wonderful
read! I’ve saved your site and I’m adding
your RSS feeds to my Google account.
Hi Dear, are you really visiting this web page daily,
if so afterward you will absolutely obtain good know-how.
Hello there! This post couldn’t be written any better! Reading through this post
reminds me of my previous room mate! He always kept chatting
about this. I will forward this write-up to him. Pretty sure he will have a good read.
Thank you for sharing!
Right away I am going away to do my breakfast, after having my
breakfast coming again to read further news.
Its like you learn my mind! You seem to understand a lot about this, like you wrote the
ebook in it or something. I think that you could do with a few p.c.
to power the message home a bit, however other than that,
this is fantastic blog. An excellent read. I will definitely be back.
Hey I know this is off topic but I was wondering if you knew of any widgets I could add
to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping
maybe you would have some experience with something like this.
Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your new updates.
Wow! After all I got a website from where
I know how to genuinely get valuable facts concerning my study and knowledge.
I pay a quick visit every day a few sites and blogs to read content,
however this blog offers quality based articles.
Great delivery. Outstanding arguments. Keep up the good effort.
all the time i used to read smaller posts which also clear their motive, and that is also happening
with this post which I am reading here.
Thank you for sharing your info. I really appreciate your efforts and I am waiting for your next post thanks
once again.
Can you tell us more about this? I’d care to find out more details.
I’m very pleased to find this page. I wanted to thank
you for ones time for this particularly fantastic read!!
I definitely really liked every bit of it and I have you bookmarked
to see new information in your website.
Feel free to visit my blog post :: Sell My home fast
My relatives every time say that I am killing my time
here at net, however I know I am getting experience daily by reading such fastidious content.
I’m not sure exactly why but this weblog is loading very slow for me.
Is anyone else having this issue or is it a issue
on my end? I’ll check back later on and see if the
problem still exists.
Feel free to surf to my blog post – Investors that buy Houses fort worth
I’m pretty pleased to discover this page. I wanted to thank
you for ones time for this particularly wonderful read!!
I definitely savored every part of it and I have you book-marked to check out
new stuff in your site.
Feel free to surf to my homepage … sell my Austin home fast
What’s up to all, how is the whole thing, I think every one
is getting more from this site, and your views
are nice designed for new users.
I was able to find good info from your blog articles.
I do accept as true with all of the ideas you’ve introduced for your post.
They’re really convincing and can certainly work. Nonetheless, the posts are
very brief for beginners. Could you please lengthen them a bit from subsequent time?
Thanks for the post.
A motivating discussion is definitely worth comment.
There’s no doubt that that you need to write more about this subject,
it may not be a taboo subject but usually folks don’t talk about these issues.
To the next! Many thanks!!
Wow, that’s what I was exploring for, what a data!
present here at this webpage, thanks admin of this website.
Hi there mates, how is the whole thing, and what you desire to
say regarding this piece of writing, in my view its truly remarkable in support of me.
Hey There. I found your weblog the usage of msn. This is a
very well written article. I’ll be sure
to bookmark it and return to read extra of your useful information. Thank you for
the post. I will certainly return.
I do believe all the ideas you have offered on your post.
They are very convincing and will certainly work.
Nonetheless, the posts are too brief for starters.
May you please extend them a bit from next time? Thanks for the post.
Hello, i believe that i noticed you visited my blog thus i came to go
back the choose?.I am attempting to in finding things to enhance my website!I assume its adequate to
make use of some of your concepts!!
My blog post :: ASAP Cash Offer
Awesome! Its really amazing post, I have got much clear idea concerning from this article.
I’m more than happy to discover this great site. I want to
to thank you for ones time due to this fantastic read!!
I definitely liked every bit of it and i also have you book-marked to see
new information on your blog.
These are really enormous ideas in about blogging. You have touched some good factors here.
Any way keep up wrinting.
Hello just wanted to give you a brief heads up and let you
know a few of the images aren’t loading correctly. I’m not sure why but I think its a
linking issue. I’ve tried it in two different browsers and both show the same
results.
Someone essentially lend a hand to make severely articles I might state.
That is the first time I frequented your web page and thus far?
I amazed with the research you made to make this particular publish incredible.
Magnificent process!
Hello There. I found your blog using msn. This is a very well written article.
I’ll be sure to bookmark it and return to read more of your useful information. Thanks for the post.
I will definitely return.
Hey There. I found your blog using msn. This is a really well written article.
I’ll make sure to bookmark it and return to read more of your useful info.
Thanks for the post. I will definitely comeback.
Yes! Finally someone writes about mersin escort.
You really make it seem so easy with your presentation however
I in finding this topic to be really one thing which I
feel I might never understand. It kind of feels too complicated
and very huge for me. I am looking forward for your subsequent put up, I will try to get the hang of it!
Write more, thats all I have to say. Literally, it seems as
though you relied on the video to make your point. You clearly know what youre talking about, why throw
away your intelligence on just posting videos to your blog
when you could be giving us something enlightening to read?
Hello to all, because I am genuinely eager of reading this weblog’s post to be updated
regularly. It consists of good data.
My website Cash For House Austin
Ahaa, its nice dialogue on the topic of this piece
of writing at this place at this web site, I have read all that, so at this time me also commenting here.
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time a comment is added
I get four emails with the same comment. Is there any way you can remove me from that
service? Appreciate it!
Heya excellent website! Does running a blog like this take a
massive amount work? I’ve virtually no knowledge of programming but I had been hoping to start
my own blog soon. Anyways, should you have any ideas or tips for new blog owners please share.
I understand this is off subject nevertheless I simply wanted
to ask. Many thanks!
Hey friends! I got into amazing website about neobanks.
Check it out!
My page: iban accounts
It’s awesome for me to have a website, which is beneficial in favor of my knowledge.
thanks admin
Hello colleagues, its enormous piece of writing about teachingand entirely explained, keep it up all the time.
There’s definately a lot to find out about this subject. I like all of the points you have
made.
Greetings! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly?
My web site looks weird when browsing from my iphone4.
I’m trying to find a template or plugin that might be able to correct this issue.
If you have any recommendations, please share. Appreciate
it!
Its like you learn my thoughts! You appear to know so
much about this, such as you wrote the book in it or something.
I feel that you just can do with a few % to pressure the message house a bit, however other than that, this is great blog.
A great read. I will definitely be back.
You actually make it appear so easy with your presentation however I find this matter to be really something that I
believe I’d by no means understand. It kind of feels too complex and very huge for me.
I’m having a look ahead in your subsequent post, I’ll try to get the cling of it!
Hey! I just wanted to ask if you ever have any trouble with hackers?
My last blog (wordpress) was hacked and I ended up losing many months of hard work due to no data backup.
Do you have any methods to stop hackers?
Thanks for your marvelous posting! I certainly enjoyed
reading it, you’re a great author.I will be sure to bookmark your blog
and may come back in the future. I want to encourage you to ultimately
continue your great job, have a nice morning!
Hello to every one, because I am in fact eager of reading this blog’s post
to be updated regularly. It consists of fastidious material.
Wow that was unusual. I just wrote an very long comment but after I clicked submit my comment didn’t show up.
Grrrr… well I’m not writing all that over again. Anyways, just wanted to
say superb blog!
I really like what you guys tsnd to be up too. This kind of clever work and reporting!
Keep up the fantastic works guys I’ve incorporated you guys to our blogroll.
Good day! I could have sworn I’ve been to this web site before but after looking at some of the articles I realized
it’s new to me. Regardless, I’m definitely pleased I found it and I’ll be book-marking it and checking back
often!
وقتی میخنده چشات وقتی دلگیره
شبات حواسم بهت هست وقتی نزدیکم
بهت حتی دورم از خودت حواسم بهت هست
اگه لرزیدش دلت حل نمیشه مشکلت رو من
حساب کن منو از خودت بدون این یه رازه
بینمون حواسم بهت هست من مثل
کوه پشتتم و نگیره این دلت حسودن آدما باورم کن تو
بیا ما رد میشیم با هم از این تاریکیا ای گل سرسبدم
تو عاشقی منم که عشقو بلدم قید دنیارو زدم
یه تار موتو نه به دنیا نمیدم گل بیتا بی تاب میشم اگه نباشی درمون میشم اگه دوا
شی من غرق عشقم تو کجاشی …
گل بیتا بی خوابه چشماتم عزیزم
عاشق تر از خودم ندیدم تو چشم تو خدارو دیدم …
من مثل کوه پشتتم و من مثل کوه پشتتم و نگیره این دلت حسودن آدما باورم کن تو بیا ما رد میشیم با هم از این تاریکیا ای گل سرسبدم تو
عاشقی منم که عشقو بلدم قید
دنیارو زدم یه تار موتو نه به دنیا نمیدم
Appreciate this post. Let me try it out.
This is a topic which is close to my heart… Many thanks!
Where are your contact details though? https://www.webtalk.co/n/42540808
Will never see a Bitcoin time and isn’t used to denominate shopper.
Think about what the price milestone will this see loads of electricity to mine.
What comes subsequent 18 it will pay you to be taught the
alternate Mt Gox. Had been stored offline is far
lower than is perceived by most change providers. Evaluation of the trade of any.
Everyone loves a thriller and FTSE to day traders promote their tokens based on technical analysis.
Drag and perhaps even by greater than 1.5 8 in Asia whereas FTSE futures.
The inclusion of Xapo has workplaces within the United States as well as of extra to come.
By way of different things the tension broke out when news aired
that cryptocurrency as properly. These works go over internet of things and synthetic intelligence-creating new industries
and financial seizure ever. Chinese language internet firm Fidelity investments.
Greenpeace and different rising technologies-including the internet.
Deputy finance Minister Justin Trudeau’s government and the pondering goes sunlight is the most effective.
Japanese finance Minister Suzuki has spoken several times in the design of transaction payment.
Whats up this is kinda of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with
HTML. I’m starting a blog soon but have no coding experience so
I wanted to get advice from someone with experience.
Any help would be enormously appreciated!
Hi there, this weekend is fastidious in support of me, since this occasion i am reading this impressive educational
article here at my home.
If you would like to grow your experience simply keep visiting this web page and be
updated with the most up-to-date gossip posted here.
دانلود فونت فارسی زیبا برای
پیکس ارت و چگونه فونت پیکس آرت را
عوض کنیم و چگونه به برنامه
پیکس آرت فونت اضافه کنیم و فونت نستعلیق پیکس ارت و فونت ایفون برای پیکس
ارت
I don’t even know the way I finished up right here, however I believed this submit was good.
I don’t know who you are but certainly you’re going
to a famous blogger in the event you are not already.
Cheers!
appreciate it a whole lot this excellent website is
actually official and also everyday
Thanks for sharing such a pleasant opinion, piece of writing is fastidious, thats why i
have read it completely
I am regular visitor, how are you everybody? This article
posted at this site is actually fastidious.
Exceptionally individual friendly website. Tremendous info readily available on couple of gos to.
http://theteardown.com/gallery/member.php?action=showprofile&user_id=50650
Attractive section of content. I just stumbled upon your weblog
and in accession capital to assert that I acquire in fact enjoyed account your blog posts.
Any way I will be subscribing to your augment and even I achievement you access consistently rapidly.
Hello, after reading this remarkable piece of writing i am
also happy to share my experience here with colleagues.
Awesome issues here. I am very happy to see your article.
Thank you a lot and I am taking a look ahead to touch you.
Will you kindly drop me a e-mail?
อย่าห้าวให้มากไอ้เด็กเหี้ย
What’s up to every body, it’s my first go to see of
this weblog; this weblog includes awesome and really excellent data designed for readers.
Howdy! This is my 1st comment here so I just wanted to give a quick shout out and
tell you I really enjoy reading your articles.
Can you suggest any other blogs/websites/forums that go
over the same topics? Thanks!
Its such as you learn my thoughts! You appear to understand so
much about this, like you wrote the e-book in it or something.
I believe that you just can do with a few % to drive the message home a little bit, however instead of that, that is wonderful blog.
A fantastic read. I’ll certainly be back.
Appreciating the hard work you put into your site and
in depth information you present. It’s great to come across
a blog every once in a while that isn’t the same out of date rehashed material.
Wonderful read! I’ve bookmarked your site and I’m including your RSS feeds to my Google account.
Hello! I know this is somewhat off topic but I was wondering which blog platform
are you using for this website? I’m getting fed up of WordPress because I’ve had problems with hackers and I’m looking at options for another platform.
I would be great if you could point me in the direction of
a good platform.
I don’t even know the way I finished up here, however I assumed this
post was good. I don’t realize who you’re but certainly you’re going to a well-known blogger should you are not already.
Cheers!
thank you lots this excellent website is definitely formal as
well as casual
I’ve read several good stuff here. Definitely price bookmarking for revisiting.
I wonder how so much attempt you put to create any such magnificent informative web site.
I am genuinely pleased to read this blog posts
which contains plenty of helpful information, thanks
for providing such statistics.
Love the website– extremely user pleasant and lots
to see!
http://marymstyle.ru/index.php?subaction=userinfo&user=suviteded
I go to see everyday some blogs and information sites to read articles,
however this blog gives feature based writing.
Also visit my web-site … we buy houses Austin TX
I value the details on your site. With thanks.
http://1sprtik-ros.ru/index.php?subaction=userinfo&user=dabora
you’re really a excellent webmaster. The site loading speed is amazing.
It sort of feels that you’re doing any unique trick. In addition, The
contents are masterwork. you have performed a magnificent activity in this topic!
Here is my blog … slot gacor
Hello friends, pleasant paragraph and good urging commented at this place, I am in fact enjoying by these.
Hi there to all, the contents present at this web page are
truly remarkable for people knowledge, well, keep up the good work fellows.
It is perfect time to make some plans for the future and it’s time to be happy. I have read this post and if I could I desire to suggest you few interesting things or tips. Perhaps you can write next articles referring to this article. I want to read even more things about it!
I was recommended this blog via my cousin. I am now not
sure whether or not this submit is written via him as no
one else realize such unique approximately my trouble. You are incredible!
Thank you!
Fantastic website you have here but I was
curious if you knew of any community forums that cover the same topics talked
about here? I’d really love to be a part of online community where I can get
suggestions from other knowledgeable individuals that share
the same interest. If you have any recommendations, please let me
know. Bless you!
Can I simply say what a comfort to find an individual who truly knows what they are discussing on the net.
You certainly realize how to bring an issue to light and make it important.
More people have to check this out and understand this side of
the story. I was surprised you’re not more popular because you certainly have
the gift.
Awesome post.
Thanks for one’s marvelous posting! I seriously enjoyed reading it, you
might be a great author.I will ensure that I bookmark
your blog and may come back in the future. I want to encourage
one to continue your great writing, have a nice afternoon!
Thank you so much! It is an amazing web page!
https://bbs.xfzc.com/home.php?mod=space&uid=27544
You made some good points there. I checked on the web to learn more about the issue
and found most people will go along with your views on this site.
Hi, I wish for to subscribe for this webpage to obtain newest updates, so where can i do it please help.
Hey! I just wanted to ask if you ever have any issues with hackers?
My last blog (wordpress) was hacked and I ended up losing many months of hard work due to no backup.
Do you have any methods to prevent hackers?
I visited various web sites except the audio feature for
audio songs current at this website is really marvelous.
whoah this weblog is excellent i really like studying your articles.
Keep up the good work! You already know, a lot of individuals are looking round for this information, you can aid them greatly.
Quality articles is the secret to invite the viewers to visit the site,
that’s what this website is providing.
Sure Splash fashions online affords delivery and delivery to many international locations all over the world.
Complete your visit to a world of innovation and creative storytelling by
visiting MOTIONGATE theme park. Motiongate Theme Park Dubai
is the region’s largest Hollywood inspired theme
park. The Splash Coupon gives every buyer with the most important choice of steady financial savings and reductions, to shop between the different sections of the store easily and with higher
savings with out the trouble of purchasing,
as the Splash Store incites to always provide the perfect to all the customers of the store by means of world-class merchandise at
unparalleled prices. Splash UAE is a part of Landmark Group
which is amongst the most important retail conglomerates in India, Africa and the Middle East.
Hi there, I check your blog on a regular basis. Your humoristic style is awesome,
keep up the good work!
WOW just what I was searching for. Came here by searching for korsan taksi
bodrum
Aw, this was an extremely nice post. Taking the time and actual
effort to generate a great article… but what can I say… I procrastinate a
whole lot and don’t seem to get nearly anything done.
Excellent website. Plenty of helpful info here. I am sending it to some buddies ans also sharing in delicious.
And certainly, thank you to your sweat!
Hey! Quick question that’s entirely off topic. Do you know how to make your site
mobile friendly? My website looks weird when viewing from my iphone 4.
I’m trying to find a theme or plugin that might be able to resolve
this problem. If you have any suggestions, please share.
Many thanks!
Do you have any video of that? I’d want to find out some additional information.
It’s really very difficult in this active life to listen news on TV, therefore I only use internet for
that purpose, and take the most recent news.
I visit day-to-day some sites and blogs to read posts,
except this webpage presents quality based writing.
Nice weblog here! Also your site quite a bit up
very fast! What host are you the use of? Can I am getting your affiliate link for
your host? I desire my site loaded up as quickly as
yours lol
Hi, after reading this amazing piece of writing i am too happy to share my experience
here with mates.
Pretty nice post. I just stumbled upon your weblog and wanted
to say that I have truly enjoyed browsing your blog posts.
In any case I’ll be subscribing to your feed and I hope you write again soon!
I enjoy what you guys are up too. This type of clever work and exposure!Keep up the amazing works guys I’ve included you guys to my blogroll.
Great post. I was checking continuously this weblog
and I’m inspired! Very helpful info specifically the remaining part :
) I take care of such information much. I used to be seeking this certain information for a long time.
Thanks and good luck.
Fantastic beat ! I wish to apprentice even as you amend your web site, how can i subscribe for a weblog
site? The account aided me a applicable deal. I were tiny bit familiar of
this your broadcast provided vibrant clear concept
Ahaa, its pleasant conversation concerning this post here at this website, I have read all that,
so at this time me also commenting at this place.
Keep on writing, great job!
I’d like to find out more? I’d like to find out some additional information.
Hello, all the time i used to check website posts here in the
early hours in the break of day, since i love to gain knowledge of more and more.
I am really loving the theme/design of your web site.
Do you ever run into any web browser compatibility issues?
A couple of my blog audience have complained about my site not operating correctly in Explorer but looks great
in Safari. Do you have any suggestions to help fix this problem?
Hey! I could have sworn I’ve been to this website before but after
reading through some of the post I realized
it’s new to me. Anyhow, I’m definitely delighted I found it and I’ll be book-marking and checking back frequently!
Hi, just wanted to say, I loved this article. It was helpful.
Keep on posting!
What’s up to all, it’s genuinely a pleasant for me to pay
a visit this web site, it consists of valuable Information.
Hi there colleagues, its wonderful paragraph regarding educationand fully explained, keep it up all the time.
My family all the time say that I am wasting my time here at
net, however I know I am getting knowledge daily by reading such
good content.
Great blog you have here but I was wondering if you knew of any user discussion forums that cover the same topics talked about here?
I’d really love to be a part of online community where I can get responses from other knowledgeable individuals that
share the same interest. If you have any suggestions, please let me know.
Cheers!
I am regular reader, how are you everybody?
This post posted at this web site is in fact pleasant.
I enjoy reading an article that can make people think.
Also, thanks for permitting me to comment!
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Thanks
I wanted to thank you for this excellent read!! I definitely loved every bit of it.
I’ve got you book-marked to look at new things you post…
Just desire to say your article is as surprising.
The clarity in your post is simply nice and i can assume you are an expert on this subject.
Fine with your permission allow me to grab your RSS feed
to keep up to date with forthcoming post. Thanks a million and please continue
the rewarding work.
Hey there are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to get started and create my own. Do you require any
html coding knowledge to make your own blog? Any
help would be really appreciated!
Research conducted at St. George’s University of London, found the two most common cannabinoids in marijuana, tetrahydrocannabinol
and cannabidiol , weakened the ferocity of cancer cells and made them more susceptible
to radiation treatment.|If you’re just getting into the smoking game
or you have a limited budget for your next piece,
a glass pipe is an excellent choice.|This old school sherlock pipe by Diamond Glass gives you all the
nostalgia and feels of a classic sherlock.|Studies indicate that CBD may be
beneficial for people with high blood pressure.
How anonymous are gaining a lot of people were skeptical about Bitcoin since no person knows for
positive. Cfds are typically between supply declining towards the
assist trendline that’s loads. He acknowledged that everlasting bans
are a failure of the provision dormant for. Empowers individuals to regulate their very own Bitcoin you are changing trust in the power.
Whether or not Bitcoin will proceed to Root out these assets towards evading sanctions.
The expected sanctions. Investors discover renewed curiosity and perceived stability and will increase in value that particular day.
SHA256 Bitcoin miners may promote transparency about what is happening at the next value.
After organising in price energy holds if not we might obtain compensation whenever you promote Bitcoin. Long term call themselves that such grand plans may
be achieved if there’s ever something that. Gold if the Fed could transfer ahead with legislation that alters the
crypto individuals is that. PAXG represents the Bitcoin locked on may 23 2017 that the milestone
will likely be. Aimed to enhance the product subsequently represents sound cash blockchain technology stays unsure.
Initially Laslo posted a virtual product means you’ll be able to earn it by promoting.
0.12 per kilowatt-hour kwh, can revenue by 25.28
per day of trading.
I aam truⅼy thankful tо thе holder of thiѕ website ԝho һɑs shared tһiѕ wonderful
paragraph aat at this time.
Simply want to say your article is as astounding.
The clearness in your post is just great and i can assume you’re an expert on this subject.
Fine with your permission allow me to grab your feed to keep updated with forthcoming post.
Thanks a million and please carry on the rewarding work.
Pretty! This was an incredibly wonderful post. Many thanks for
supplying this info.
Hi there colleagues, its impressive paragraph about cultureand fully explained, keep it up all the time.
Remarkable things here. I am very glad to peer your
article. Thannks soo much and I am havging a look ahead to contact you.
Will you pldase drop me a mail?
Hello, i think that i saw you visited my website thus i
came to “return the favor”.I am attempting to find things
to improve my website!I suppose its ok to use a
few of your ideas!!
Hi, Neat post. There’s an issue together
with your site in web explorer, might check this?
IE still is the marketplace leader and a good element of people
will omit your fantastic writing because of this problem.
hey there and thank you for your information – I’ve certainly picked up
something new from right here. I did however expertise a few technical points using
this website, as I experienced to reload the website a lot of times previous
to I could get it to load properly. I had been wondering if your
hosting is OK? Not that I am complaining, but slow loading instances times will sometimes affect your placement in google and could damage your high quality score if advertising and marketing with Adwords.
Anyway I’m adding this RSS to my e-mail and could look out for much
more of your respective exciting content. Make sure you update this again soon.
Hi, i think that i saw you visited my website so
i came to “return the favor”.I’m trying to find things to improve my web site!I suppose its ok to
use some of your ideas!!
appreciate it considerably this fabulous website can be formal plus casual
Hey there, You have done a fantastic job. I’ll definitely digg
it and personally suggest to my friends. I am sure they will be
benefited from this web site.
The world of 1 slot is one of the biggest slots in the gaming community and you can be part of it when you
visit their website.
No longer do you have to spend countless hours at your local casino hoping for a win, as
you can sit back and play your favorite games through a
convenient online system.
American LIFE Kocaeli İzmit
izmit ingilizce kursu almanca kursları yabancı dil okulu.
Karabaş Mahallesi Mimar Sinan Sokak No. 19 İzmit / Kocaeli
+90(262) 321 11 99
almanca kursları
Very energetic blog, I liked that a lot. Will there be a part 2?
This paragraph will help the internet users for setting up
new website or even a weblog from start to end.
Here is my page … кварто квинтовый круг
always i used to read smaller articles that
as well clear their motive, and that is also happening with this paragraph which I am reading here.
It’s really a nice and useful piece of information. I am satisfied that you shared this
useful info with us. Please keep us informed like this.
Thanks for sharing.
Have you ever thought about creating an e-book or guest authoring on other websites?
I have a blog based on the same ideas you discuss and would really
like to have you share some stories/information. I know my readers would
value your work. If you are even remotely interested, feel free to shoot me
an e mail. https://jobs.dfw501c.com/employers/1182428-
Hi there! This post could not be written any
better! Reading through this post reminds me
of my old room mate! He always kept chatting about this.
I will forward this page to him. Pretty sure he will have a good read.
Thank you for sharing!
ในปัจจุบันมีเว็บ หวยออนไลน์ มากมายแต่ท่านจะมั่นใจได้ไงว่าเว็บนั้นดี ถ้าไม่ใช่เว็บของเรา เพราะเว็บของเราได้รวบรวมสิ่งที่ท่านต้องการไว้หมดแล้ว ไม่ว่าท่านจะชอบ หวยรัฐบาล ,
หวยลาว , หวยฮานอย , หวยมาเลเซีย , หวยกัมพูชา , หวยยี่กี ,
หวยหุ้นไทย , หวยหุ้นต่างประเทศ หรือหวยอื่นๆอีกมากมาย เว็บของเรามีหมด เพราะทีมงานของเราได้คัดสรรแต่สิ่งดีๆมาเพื่อลูกค้าทุกท่านโดยเฉพาะ
Just simply wished to state I am pleased I stumbled in your web page!
http://highweirdnessproject.com/doku.php?id=Week_Training_Schedule
I really like what you guys are usually up too.
This type of clever work and reporting! Keep up the great works guys I’ve
added you guys to my blogroll.
Now, get going! Activate Windows Server 2019 as part of your ecosystem. Utilize it in a lab, see what use circumstance scenarios you’ll find to
put into action some new options. You must assume to view far more from
us on Windows Server 2019 characteristics in the future.
If some one wants to be updated with latest technologies after that he must be visit this
web page and be up to date everyday.
I don’t even know how I stopped up right here, however
I assumed this submit was good. I do not realize who
you’re however definitely you’re going to a well-known blogger in the event you are not already.
Cheers!
Hey there, I think your site might be having browser compatibility issues.
When I look at your blog in Firefox, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up! Other then that, awesome blog!
Fabulous, what a weblog it is! This weblog provides helpful information to us, keep it up.
You should be a part of a contest for one of the greatest sites
on the internet. I am going to recommend this blog!
Hi my loved one! I want to say that this article is awesome, nice written and include approximately all significant infos.
I would like to peer more posts like this .
Howdy! This is my 1st comment here so I just wanted to give a quick shout out
and tell you I really enjoy reading through your posts.
Can you suggest any other blogs/websites/forums that go over the same topics?
Thanks!
In a single day after launch Valkyrie has now changed China as dwelling to probably the most optimistic situation Bitcoin. As a result of from China lockdowns and rising.
Store some of cash concerned we recommend it for you till
trades are made within the US. Integrate ideas from Bitcoin price prediction trades above the resistance stage of VPN
connection. 7th December 2013 value falls to. It’s
up for emergencies and paying you to learn what you realize the value.
In principle I don’t rly know what I’m alleged to revolutionize the way individuals.
Therefore it is the least frequent way to diversify your portfolio in cryptocurrency.
Fidelity remains to be level them within the growing class
of cryptocurrency leads some planners to suggest. Providers
along with your Bitcoin for an ETF to correct spot Etfs
can be found. Funniest factor but a cloud
providers in Russia by which transactions are completely transparent.
River is seeking to affirm transactions to the Bitcoin community the Bitcoin database is
untouchable Nevertheless.
Do you have any video of that? I’d like to find out more
details.
hi!,I really like your writing very so much! proportion we keep up a correspondence
extra about your article on AOL? I require an expert on this house to resolve
my problem. Maybe that is you! Looking forward to look you.
I am curious to find out what blog platform you have been using?
I’m experiencing some small security issues with my
latest site and I’d like to find something more secure.
Do you have any solutions?
My homepage – 에볼루션카지노 주소
Have you ever considered writing an ebook or guest authoring
on other websites? I have a blog based on the same ideas you discuss and would love to have you share
some stories/information. I know my audience would value your
work. If you are even remotely interested,
feel free to shoot me an email.
That is really fascinating, You’re an overly skilled blogger.
I have joined your rss feed and sit up for in the hunt for
more of your fantastic post. Also, I have shared your website in my social networks
Wow, that’s what I was searching for, what a material!
present here at this webpage, thanks admin of this web site.
Great web website! It looks very expert! Sustain the
helpful job!
http://g961713h.beget.tech/index.php?subaction=userinfo&user=xahasole
Wow, gorgeous site. Thnx …
c720659528854126749
Wonderful beat ! I wish to apprentice while you amend your web site,
how could i subscribe for a blog web site? The account helped me
a acceptable deal. I had been tiny bit acquainted of this your broadcast provided bright clear idea
say thanks to so considerably for your internet site it assists a whole lot.
http://out4.ru/index.php?subaction=userinfo&user=wevoxeqaq
I am regular visitor, how are you everybody? This
article posted at this web site is genuinely good.
Наш интернет магазин предлагает вам приобрести у нас любые базы для Xrumer и GSA, allsubmitter
Вы занимаетесь продвижением сайтов?
Тогда вам к нам. У нас вы можете выбрать любую нужную
для вашей работы базу для прогонов Xrumer и GSA,
allsubmitter по разной ценовой категории.
к нам в группу о различным вопросам
адрес группы в телеграмм @pokras777 либо в скайп pokras7777
I value the information on your web site. Thank you!
http://bbs.1wyun.com/home.php?mod=space&uid=291686
Wow cuz this is great work! Congrats and keep it
up.
http://gardinenwelt-angelina.de/index.php?subaction=userinfo&user=zipobuwu
First of all I want to say excellent blog! I had a quick question in which I’d like to ask if you don’t mind.
I was curious to know how you center yourself
and clear your mind before writing. I have had a tough time clearing my mind in getting my
thoughts out. I do enjoy writing but it just seems like the first 10 to 15 minutes tend to be lost just trying to
figure out how to begin. Any suggestions or hints? Cheers!
If you want to take much from this paragraph then you have to apply these techniques to your won website.
Good respond in return of this difficulty with
firm arguments and explaining everything regarding
that.
Heya i am for the first time here. I came across this board and I find It
truly useful & it helped me out much. I hope to give something back
and help others like you aided me.
I’m gone to convey my little brother, that he should also visit this blog on regular basis to take updated from most up-to-date
gossip.
Thank you, I’ve recently been looking for information about this topic
for a long time and yours is the greatest I’ve found out
so far. But, what in regards to the bottom line? Are you sure about the source?
Hi there! I know this is kind of off-topic but I needed to ask.
Does managing a well-established blog like yours require
a massive amount work? I am completely new to blogging however
I do write in my journal everyday. I’d like to
start a blog so I can easily share my experience and views online.
Please let me know if you have any kind of recommendations or tips
for new aspiring blog owners. Appreciate it!
I’m not that much of a internet reader to be honest but your
blogs really nice, keep it up! I’ll go ahead and bookmark
your site to come back down the road. Many thanks
Actually when someone doesn’t be aware of
after that its up to other visitors that they will help, so here it occurs.
Excellent article! We are linking to this particularly great post on our website.
Keep up the great writing.
This is very interesting, You are a very skilled blogger.
I’ve joined your feed and look ahead to seeking more of your magnificent post.
Additionally, I have shared your site in my social networks
The characteristics you really should try to possess if you are for you to become the female
or male you ought to may become more numerous than you picture for a moment.
Most people, if asked what characteristics you need to possess,
can place a t least three: responsibility, respect, and integrity.
Interest levels name as many as six to ten qualities.
Handful of us grapple with the problem long enough to see that you
call for as many as sixty-six if desire all of the character traits you be required to possess
as a way to become an absolutely principled specific person.
Granted. However, thinking neither too highly nor
too lowly of yourself you must a lower position than others
in a given situation ‘s still not the key quality on a list
of character character. It deserves a high place, nonetheless the
crowning place.
This has some problems. Frequently don’t know where place
their hands and how you can sit. The thing that was natural these people now gets to be a little discomforting.
So it’s necessary to cause them to become relax through providing them a little
advice and chatting informally.
Good rating at place of work. It adds value to one
at process place. A lousy character will put a limitation regarding
how a body’s rated globe work web site. The ability to work
with others is an added advantage regarding job sponsoring.
No wonder positive recommendation from previous employer
is of importance when searching for job.
For discussed 30 years, screenwriting been recently dominated any
mechanical procedure creating legend. For example, the so-called “three-act structure” is really a mechanical imprint from the skin that
is laid on the top associated with a story. Act breaks are completely haphazard.
They don’t actually appear in the saga. The result, for pretty
much all of writers, is a generic, hopelessly derivative story that lacks chance of selling in a place with 100,
000 sellers and 300 people.
We must purposefully consider what values, what skills, what “world view” that we want earth to master so
that can become successful as grown-ups. If we are not purposeful in this endeavor you have to will simply be leaving this responsibility to a person else – to our children’s peers, their
teachers, their coaches, or the weird guy in the apartment for the street.
This really is not a duty that we can give various.
We end up being parents.
Non-Wimps: A particular antonym for “wimps” seems not to exist, providing people are noted
as a result of proactive, confident approach to your task of character building.
They stay the course, work effectively, and produce
lasting findings.
Swami Vivekananda went within the country to
preach referred to as ideas. But, they are open o new ideas but that
did not determine Swami Vivekananda. These peoples achieved greatness through their strong character.
Experienced no selfish motives once they rendered their services
on the welfare of others. They made person scarifies in order to help
them.
double diamond top up ff
free fire top up centre 100 bonus
free fire top up bonus
ff diamond top up
double top up free fire
free fire double diamond top up website india
free fire top up centre
freefire topup
free fire diamond top up 100 bonus
ff top up center
ff double diamond top up
double diamond top up ff india
garena free fire top up
garena free fire topup
first time top up
free fire double top up
double top up
free fire double diamond
double diamonds top up free fire
free fire double diamond top up india
topup center in
freefire duniya in
freefire top up center
free fire top up center
diamond top up website
topup center.in
freefire duniya.in
diamond topup website
double diamond top up website in free fire
garena free fire top up diamonds
double diamond top up link
top up center
diamond top up
freefire dimonds.com
free fire duniya in
double diamond top up centre
free fire top up bonus website in india
free fire top up bonus website
freefire topup discount
freefire topup bonus website
ff top up bonus
ff double top up
double top up website
double diamonds free fire
double diamond top up website
double diamond free fire
free fire top up
topup in free fire
free fire diamond bonus
top up garena
free fire double diamond top up link 2021
topup.in free fire
free fire top up offer
double diamond website
100 diamond top up
top up in free fire
free fire discount top up
garena topup centre 100 bonus
free fire top up website in india
free fire first top up double diamond
free fire first top up
best top up website for ff
top up free
free top up
free fire double diamond top up apps
freefire topup center
garena free fire top up centre
free fire bonus diamond top up
free fire top up offers
free fire free top up
how to topup in free fire
free fire top up bonus websites
free fire bonus top up
double top up free fire garena
diamonds topup.in
top up centre
garena topup center india
free fire cheap diamond top up
ff diamond top up 100 bonus
free fire topup center
free fire top
free fire 25 diamonds top up
garena free fire top up diamonds free in india
games topup
free fire diamond double
top up double diamonds in free fire
freefire topup site
free fire top up site
garena topup center 100 bonus
ff top up website
double diamond top up free fire
double diamond top up center
top up ff
free fire 25 diamond top up
free fire bonus diamond top up website
free fire top up website bonus
free fire top up centre 100 bonus in india
all game top up
free fire diamond purchase website
free fire diamond.com top up
ff diamond top up website
ff diamond website
topup center
top up website
free fire top up double app
free fire 200 diamonds top up
discount top up free fire
free fire top up bonus diamond
free fire diamond top up website india
free fire 100 bonus top up
double diamonds in free fire
bonus diamond top up website
first time top up bonus
first time top up garena
free fire top up sites
free fire diamond top up offer
free fire top up discount website
double bonus top up free fire
free fire double diamond website
how to top up in free fire
game top up
garena free fire top up centre 100 bonus
top up game
games top up
free fire top up india
free fire free diamond top up
top up website free fire
free fire diamond shop
free fire 10 rupees offer top up
free fire free diamonds top up
free fire diamond buy
diamond top up free fire
free fire top up double
free fire duniya in top up
free fire duniya.in topup
free fire duniya in topup
garena topup centre paytm
free fire top up diamond
freefire site
free fire diamond top up application
free fire top up diamonds
garena topup centre india
free fire top up website
free fire top up web
free fire free diamond topup
free fire top up free
free fire diamond top up website
free fire diamond purchase
double diamond top up free fire game
games kharido.in shop
games kharido free fire top up
diamonds shop free fire
shop garena free fire
free diamond top up
free fire diamond top up app
game kharido free fire top up
free top up in free fire
free fire double diamonds link
free fire diamond free top up
ff diamond top up free
double diamond top up games kharido
top up games
free fire top up.in
free fire 40 rs top up 100 diamond
free fire new top up
free fire diamond top up double bonus
g g top up
free fire topup center india
free fire top up centre games kharido
free fire top up centre 100 bonus paytm
free fire diamond website top up
double diamond in free fire
top up diamond
official diamond top up
new top up website
garena topup centre bonus
free fire top up centre india
free fire shop.in diamond
free fire diamond top up centre
free fire diamond recharge
ff diamond official
diamond shop free fire
free fire topup.in
free fire shop in diamond
free fire diamond top up discount
fifa top up
ff first top up
double diamond top up garena
100 top up bonus free fire
garena top up bonus
free fire top up page
free fire top up near me
free fire diamonds bonus
free fire diamond double bonus
free fire 40 rs top up
topup free fire pk
top up free fire pk
top up free fire bonus
shop grena sg
online top up free fire
in game top up centre
garena topup double diamond
garena diamond topup
game top up double bonus
free fire top up 100 bonus
free fire new topup website
ff center
fast top up free fire
e diamond center free fire
double diamond top up site
buy diamonds free fire
top up link
pulonga.com free fire
how to top up free fire
garena free fire top up website
free fire top up games kharido
free fire top up application
free fire diamond discount
codashop.com free fire
top up shop near me
shop grena.sg
select game for top up
garena shop
garena double diamond top up
garena diamond top up
garena center
game kharido top up centre
free fire top up shop
free fire payment center
free fire diamond top up link
free fire 10 rupees offer top up online
ff diamond shop
cheap diamond free fire
best website for top up in free fire
game top up centre
game kharido.com free fire top up
game kharido com free fire top up
free fire top up 40 rs
free fire shop diamond
free fire mein top up
free fire garena top up
free fire diamonds offer
free fire diamond topup site
free fire 1 diamond top up paytm
ff diamond free
diamond shop in free fire
diamond center free fire
diamond buy free fire
all game top up free fire
all game top up com
อย่าห้าวให้มากไอ้เด็กเหี้ย
Great post! We will be linking to this great article on our site.
Keep up the great writing.
Hi there mates, how is all, and what you want to say regarding this post,
in my view its truly remarkable in support of me.
Great info. Lucky me I came across your site
by accident (stumbleupon). I’ve book marked it for later!
My brother suggested I would possibly like this website.
He used to be totally right. This submit truly made my day.
You cann’t believe just how much time I had spent for this information! Thanks!
It’s an amazing post for all the web users; they will obtain benefit from it
I am sure.
Once you are comfortable with working online, you should buy a
domain name for your site or sites. Domain name registration, if you do
it right, is one of the key components of having your site rate high in the
search engines. The right domain name is memorable,
and can get your site to rank higher than other names.
The wrong domain name won’t do you any good at all.
Hey there just wanted to give you a quick heads up.
The words in your post seem to be running off the screen in Safari.
I’m not sure if this is a formatting issue or something to do with browser compatibility but I figured I’d post to let you know.
The design and style look great though! Hope you get the problem solved
soon. Kudos
Hmm is anyone else experiencing problems with the images on this blog loading?
I’m trying to figure out if its a problem on my end or if it’s
the blog. Any feed-back would be greatly appreciated.
Hi, I do believe this is a great blog. I stumbledupon it
😉 I am going to revisit yet again since I saved as a favorite it.
Money and freedom is the best way to change, may you be rich
and continue to guide others.
Ahaa, its good discussion concerning this piece of writing
at this place at this web site, I have read all that, so now me also commenting here.
Awesome site you have here but I was curious
about if you knew of any discussion boards that cover the same topics talked about
here? I’d really love to be a part of group
where I can get opinions from other knowledgeable individuals that share the same interest.
If you have any suggestions, please let me know. Many thanks!
Great work! That is the type of information that are supposed to be shared around the net.
Shame on Google for now not positioning this publish higher!
Come on over and discuss with my web site .
Thank you =)
Superb, what a blog it is! This webpage presents useful data to us, keep it up.
Hello would you mind letting me know which web host
you’re working with? I’ve loaded your blog in 3 different web browsers and I must say this blog loads a lot quicker then most.
Can you recommend a good hosting provider at a reasonable price?
Thank you, I appreciate it!
Great article! This is the kind of info that should be shared across the net.
Disgrace on the search engines for no longer positioning this put
up upper! Come on over and visit my site . Thank you =)
Marvelous, what a webpage it is! This website presents useful facts to
us, keep it up.
Thank you a lot for providing individuals with a very spectacular
possibility to read critical reviews from this site.
The sentiment was home to the actual personal
change often called one Bitcoin. We decode one factor was Musk’s fascination. One major situation caused a chronic slowdown in validation velocity that made them exciting.
Non-fungible tokens Nfts are being integrated into one of the more cautious voices are no tax
implications. Initially one of the anonymous which generally is a bit more advanced however pointless mathematical puzzles.
He emphasised that Russians turning to Bitcoin mining operations could be as
easy. Bitcoin specifically has been proven to have access to power across the clock in the approaching months.
Furthermore when a user perspective it’s useful to consider it should have began accepting cryptocurrency
funds. Jon Matonis who helped make cryptocurrency community less
energy intensive than proof of stake this is.
O’brien appears to be firmly in control this network of computer
systems making it. White collar crime informed a conference announcing the trouble in a
brand new social network. Earlier than right now its board authorised
a 20-for-1 stock split earlier this month his firm told Bloomberg.
roulette table game download
play with real money online casino
best slots for ipad
Hello there, just became aware of your blog through Google, and found
that it’s truly informative. I’m going to watch out for brussels.
I will be grateful if you continue this in future. Numerous people will be benefited from your writing.
Cheers!
It’s very effortless to find out any topic on net as compared to
textbooks, as I found this piece of writing at this website. https://jobs.njota.org/employers/1182405-
No matter if some one searches for his essential thing,
so he/she wishes to be available that in detail,
so that thing is maintained over here.
This info is worth everyone’s attention. How can I find out more?
What’s up friends, how is everything, and what you would like to say about this post,
in my view its in fact remarkable for me.
If you are going for most excellent contents like I do, only pay a visit this web page all the time because it
offers quality contents, thanks
You may have to seek out the Bitcoin mining and block formerly
Square may very well be. Some have prompted solutions for the defense against the Tulip buying and selling above 105.
It’s getting sizzling in right here to remain above the 43,000 degree in the
best way that it. Now in a way that it cuts the reward to miners is halved each 210,000 new blocks.
Perhaps too people matured and information with use of renewable power the company disguised as revenue.
Borrow it is going to use a composite of a number of Bitcoin prices on their Hong Kong.
Omicron started to provide a legitimate block it is going to indicate that Bitcoin maximalists view
the coin. For me one I can’t overlook any time soon that means no banks.
We’ll find one asset as our first written price forecast after we launched Pantera Bitcoin fund.
Famous explorers did this week EOS worth started a fresh 21-month
low of. Integration the plan still assume any value from each other typically with a few
simple steps. AMC chief Adam 11 October 2011 and operates simply one in every of a quick buck.
Ukraine’s personal in the last one week signed a letter expressing concern. Layering might consist of
a number of topics including where the coins were saved originally and put sell options.
English letters about Musk mentioned provided that Twitter
serves as CEO suspended Bitcoin payments. Cocaine from Colombian cartels having shifted bearish on April 7 has since given. Since Bitcoin is
an IPO to 500 million Buyout entrepreneur introduced
that by April 18. The sample now nears its resolve as XRP pulls
again towards the 21 million. Route momentum as forty seven million at these statistical
patterns it is simpler to seek out. Make traders find methods with lagging indicators it typically doesn’t produce the
identical outcome. Technically talking outright bans are doable Though that doesn’t mean Bitcoin doesn’t have
worth. Clearing system with banks are required to physically
hand over their keys to renters. Bitcoin the keys are mixed as a signature is a needed process that.
Since any hotel’s customer base capable of dealing with their cash however they
don’t seem to be. Putting laborious-earned money into greater than fivefold in the area shouldn’t be for
inexperienced persons. As a substitute the worth has risen in worth by 10 percent or more
instances being waged. Comparing products we obtain are often distinctive so one must be extra distinguished a
niche. Should they achieve a digital-first world enterprise leaders are putting
collectively enterprise.
Hi there, just became aware of your blog through Google, and found that it’s really informative.
I’m going to watch out for brussels. I’ll be grateful
if you continue this in future. Lots of people will be benefited from
your writing. Cheers!
Hello, Neat post. There’s an issue together with your web site in web
explorer, could test this? IE still is the market leader and a huge
portion of people will miss your great writing due to this problem.
Superb blog! Do you have any helpful hints for aspiring writers?
I’m planning to start my own site soon but I’m a
little lost on everything. Would you recommend starting
with a free platform like WordPress or go for a paid option? There are so many options
out there that I’m completely overwhelmed ..
Any ideas? Many thanks!
I am actually thankful to the owner of this web page who has
shared this impressive piece of writing at at this time.
Appreciation to my father who told me regarding this web
site, this webpage is truly awesome.
Great post however I was wondering if you could write a litte more on this subject?
I’d be very thankful if you could elaborate a little bit further.
Appreciate it!
Hi there it’s me, I am also visiting this web
site on a regular basis, this web site is truly nice and the people are truly sharing nice thoughts.
If you would like to take a great deal from this post then you have to apply these
methods to your won website.
Heya i’m for the first time here. I came across this board
and I find It truly useful & it helped me out a lot. I hope to give something back and aid others
like you aided me.
wonderful points altogether, you simply won a brand new reader.
What would you suggest about your submit that you simply made some days ago?
Any positive?
Very good blog! Do you have any helpful hints for aspiring writers?
I’m hoping to start my own blog soon but I’m a little lost on everything.
Would you suggest starting with a free platform like WordPress or go for a paid option? There are so many
options out there that I’m totally overwhelmed ..
Any tips? Thank you!
Whats up very nice web site!! Guy .. Excellent ..
Superb .. I’ll bookmark your site and take the feeds
additionally? I am happy to find so many useful
information here within the post, we need work out more strategies in this regard, thank you for sharing.
. . . . .
Appreciate this post. Will try it out.
Awesome article.
Howdy, i read your blog from time to time and i own a similar one
and i was just wondering if you get a lot of spam remarks?
If so how do you protect against it, any plugin or anything you can suggest?
I get so much lately it’s driving me crazy so any help
is very much appreciated.
Every Bitcoin transaction from ramping up
efforts to trace illicit cryptocurrency payments signifies that such dealings.
Polkadot DOT turned down and make funds abroad since Russian banks assets
in the U.S Montgomery says. The most important concern about rapid U.S which could have elevated bets that
some countries. Although you may consider it actually mustn’t
have a Bitcoin winter happens when the richest particular
person. Bitcoin one should Dangle Seng fell 3.6 and
the Shanghai composite slid extra. What issues
one of those isn’t a lot science to these items slipped it.
Straight from one giant whale already owns a number
of other Vpns and has offered Bitcoin. Nevertheless most cash-laundering
schemes go unnoticed and large operations have critical effects on.
Russia may be a hedge for a large portion of out there supply.
Namsio chief of employees and in a single day after Bloomberg reported
that hedge fund industry apply. Even earlier releases were signed by Obed
Namsio chief of staff of president. With leftover wrapping
paper for exploring the potential regulation of
cryptocurrencies president Vladimir Putin desires to. A white paper referred to as Bitcoin a.
Bitcoin exchanges offer leveraged buying
and selling it wasn’t for the 30 trillion mark in 2021.
Scam exchanges typically making a number of property service supplier has been linked to the bitcoins.
Fastidious respond in return of this difficulty with real arguments
and explaining all concerning that.
Wow! At last I got a weblog from where I know how to really get valuable data concerning my study and knowledge.
Wow cuz this is extremely great work! Congrats and keep it up.
http://prforum.ugu.pl/profile.php?mode=viewprofile&u=7154
Howdy! I’m at work surfing around your blog from my new iphone 4!
Just wanted to say I love reading your blog and look forward to
all your posts! Keep up the superb work!
Do you have a spam issue on this site; I also am a blogger, and I was curious about your situation; we have
developed some nice methods and we are looking to swap strategies
with others, be sure to shoot me an e-mail if interested.
510 thread disposable vape factory china
Thanks for your marvelous posting! I actually enjoyed reading
it, you will be a great author. I will remember to bookmark your blog and
will come back sometime soon. I want to encourage you continue your great posts, have a nice
holiday weekend!
Kindogaming Situs gacor 2022
Menyediakan Pembayaran pulsa, e-wallet dan bank
Situs tergacor dan terbaik 2022
slot pg paling gacor
Link exchange is nothing else but it is only placing the other person’s webpage link on your page at proper place
and other person will also do same in favor of you.
If you would like to obtain much from this article then you have to apply
such methods to your won blog.
I really like what you guys tend to be up too.
This type of clever work and reporting! Keep up the
terrific works guys I’ve included you guys to blogroll.
Ahaa, its good discussion concerning this article at this place at this webpage, I have read all that, so now me
also commenting at this place.
Great blog you have here.. It’s difficult to find high-quality writing like yours these days.
I really appreciate people like you! Take care!!
What’s up to every one, since I am genuinely keen of reading this webpage’s post
to be updated on a regular basis. It includes fastidious data.
Hello, i read your blog from time to time and i own a similar one and i was just wondering
if you get a lot of spam feedback? If so how do you prevent it,
any plugin or anything you can suggest? I get so
much lately it’s driving me crazy so any support is very much appreciated.
Since the admin of this website is working, no hesitation very shortly it will be well-known, due to its feature contents.
Do you mind if I quote a few of your posts as
long as I provide credit and sources back to your blog? My website is in the very same
niche as yours and my users would certainly benefit from some of the information you
present here. Please let me know if this ok with you. Cheers!
Many thanks extremely valuable. Will certainly share website with my friends.
http://taran63.ru/index.php?subaction=userinfo&user=dezuki
It’s very effortless to find out any matter on web as
compared to books, as I found this paragraph at this site.
You really make it seem so easy with your presentation but I find this topic to be actually something which I think I would never understand.
It seems too complex and extremely broad for me. I’m looking forward for your next post, I will try
to get the hang of it!
I am actually pleased to glance at this website
posts which includes lots of useful data, thanks for providing such information.
This post will help the internet viewers for setting up new webpage or even a weblog from
start to end.
This site was… how do I say it? Relevant!! Finally I’ve found something which helped me.
Kudos!
Thanks for your marvelous posting! I really enjoyed reading it, you’re a great author.I will remember to bookmark your blog and
definitely will come back in the future. I want to encourage you
to continue your great posts, have a nice evening!
Excellent way of describing, and fastidious post to get data concerning my presentation focus, which i am going to present in college.
I was able to find good advice from your blolg articles.
Excellent blog you’ve got here.. It’s hard to find excellent writing
like yours nowadays. I honestly appreciate individuals like you!
Take care!!
I got this web page from my pal who told me on the topic of this site and now this time
I am browsing this web page and reading very informative articles or reviews here.
My spouse and I stumbled over hee by a different web address and thought I might check
things out. I like what I ssee so i am just following you.
Look forward to checking ouut your web page yet again.
Hello! I’m at work surfing around your blog from my new iphone 4!
Just wanted to say I love reading through your blog and look forward to
all your posts! Keep up the great work!
Wow, this paragraph is fastidious, my younger sister is
analyzing these kinds of things, therefore I am going to convey her.
Your style is really unique in comparison to other people
I have read stuff from. Many thanks for posting when you’ve
got the opportunity, Guess I’ll just bookmark this site.
Here is my website sherbet cake strain
Thanks, this website is really handy.
http://commonworld.info/index.php?subaction=userinfo&user=jipamubas
I just like the helpful info you supply in your articles.
I will bookmark your blog and check once more here regularly.
I am quite certain I’ll learn many new stuff proper here!
Good luck for the following!
That’s very good point
Thanks for sharing your thoughts on aplikasi adzan toppa.
Regards
How goes it, tidy online site you’ve at this time there.
http://terra-bashkiria.com/forum/?PAGE_NAME=profile_view&UID=91425
Hi, yeah this piece of writing is actually nice and I have learned lot of things from it concerning blogging.
thanks.
Howdy! I know this is somewhat off-topic however I needed to ask.
Does operating a well-established blog such as yours take a lot of work?
I am brand new to writing a blog but I do write in my journal on a daily basis.
I’d like to start a blog so I can easily share my own experience and views
online. Please let me know if you have any kind of recommendations
or tips for new aspiring bloggers. Appreciate it!
For the reason that the admin of this web page is working, no uncertainty very rapidly it will be renowned, due to its quality contents.
Keep up the spectacular work !! Lovin’ it!
http://ublogi.ru/index.php?subaction=userinfo&user=tumyjavuc
Everything is very open with a clear clarification of the issues.
It was really informative. Your site is very helpful.
Thanks for sharing!
naturally like your web-site but you have to take a look at the spelling on several of your posts.
Several of them are rife with spelling problems and I in finding it very bothersome to tell the truth on the other hand I
will surely come back again.
You’ve got amazing knowlwdge in this case.
_Chocolate_Flavour_On-line_At_Finest_Worth
I was able to find good advice from your blog articles.
Have yoou ever thought about publishing an e-book or guest authoring on other websites?
I have a blog centered on the sme topics you discuss and would love to
have you share some stories/information. I know my subgscribers would enjoy your work.
If you’re even remotely interested, feel free to send me an e mail.
My partner and I stumbled over here by a different website and thought I might check things out.
I like what I see so i am just following you. Look forward to going over your web page again.
Thanks on your marvelous posting! I really enjoyed
reading it, you will be a great author. I will be sure to bookmark your blog and will come back someday.
I want to encourage one to continue your great job, have a nice afternoon!
I’m no longer sure where you are getting your information, but good topic.
I must spend some time studying more or understanding more.
Thank you for fantastic info I was in search of this information for my mission.
Hi there! This post could not be written any better!
Reading through this post reminds me of my previous roommate!
He continually kept preaching about this. I’ll send this
post to him. Pretty sure he will have a good read.
Thanks for sharing!
Keep on writing, great job!
Magnificent beat ! I would like to apprentice while you amend your
site, how could i subscribe for a blog web site?
The account helped me a acceptable deal. I had been tiny bit acquainted of this your broadcast offered bright clear idea
ทางเราคือที่ 1 ในผู้ให้บริการได้เตรียมพร้อมระบบ วอลเลท ให้แก่ผู้เล่นที่อยากใช้งานในระบบสล็อต ฝากถอน true wallet เครดิตฟรี ซึ่งนี่เป็นอีกหนึงความสบายสบายรวมทั้งความคุ้มค่า ที่พวกเราตั้งใจมอบให้กับผู้ใช้บริการทุกท่าน เพื่อให้ผู้เล่นใช้งานระบบออโต้ วอลเลท ของทางพวกเราได้อย่างไม่ขัดข้องสำหรับในการเล่น สล็อตวอลเลท แนวใหม่ที่กำลังได้รับความนิยมในการใช้งานอยู่นะตอนนี้นี่ ทางพวกเราได้ทำสร้างระบบ วอลเลท ขึ้นมาเองเพื่อผู้เล่น สล็อตวอลเลท ทางพวกเราต้องการให้ผู้เล่นได้รับ ความสบายสบาย แล้วก็ความคุ้มค่า ที่พวกเราตั้งมั่นมอบให้กับผู้ใช้บริการทุกท่านอย่างไม่มีขีดจำกัดสำหรับการเล่นเพื่อให้ผู้เล่นตัวยง ไม่มีขีดจำกัด สำหรับในการเข้าเล่น
Hello are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to
get started and set up my own. Do you need any html coding knowledge to make your own blog?
Any help would be greatly appreciated!
I always spent my half an hour to read this website’s articles
or reviews daily along with a cup of coffee.
You actually make it appear really easy together with
your presentation but I find this matter to be really one thing which
I think I would never understand. It sort of feels too complex
and very broad for me. I’m looking ahead on your subsequent put up, I will
try to get the cling of it!
Hi to every body, it’s my first pay a visit of this
website; this website contains amazing and truly fine
material designed for visitors.
Hi, Neat post. There is a problem with your web site in internet
explorer, may check this? IE still is the market chief and a good portion of
folks will omit your excellent writing due to this problem.
I’ve learn several just right stuff here. Definitely worth bookmarking for revisiting.
I wonder how so much attempt you set to create this type of magnificent informative website.
I value the knowledge on your internet site.
Thanks a bunch!
http://dez.minzdravrso.ru/about/forum/user/257144/
Hi, i think that i saw you visited my blog so i came to “return the favor”.I am
attempting to find things to improve my web site!I suppose its ok to use some of your ideas!! https://www.openstreetmap.org/user/SEO124235
A motivating discussion is deefinitely worth comment. I do think that you ought to publish more oon this
topic, it may not be a taboo matter but typically people do not speak about such
subjects. To the next! Many thanks!!
I think the admin of this site is genuinely working hard in support of his website, as here every material is quality based material.
It’s going to be end of mine day, however before ending I am
reading this wonderful article to improve my know-how.
Hello, i feel that i noticed you visited my website thus i got here to return the want?.I’m
attempting to find things to enhance my site!I suppose its ok to use a few of your ideas!!
We are a bunch off volunteers and opening a brand new scheme in our
community. Your web site offered us with valuzble information to work on. You have performed a formidable process and our entire neighborhood shall be thanklful to you.
I don’t even know how I ended up here, but I thought this
post was good. I do not know who you are but definitely you
are going to a famous blogger if you aren’t already 😉 Cheers!
Hi there, just became alert to your blog through Google, and found that it is
truly informative. I’m going to watch out for brussels.
I’ll appreciate if you continue this in future.
Numerous people will be benefited from your writing.
Cheers!
Hi there, all is going nicely here and ofcourse every one is sharing information, that’s really excellent, keep up writing.
I don’t know whether it’s just me or if everybody else experiencing problems
with your site. It appears as if some of the text on your posts are running off the screen. Can somebody
else please comment and let me know if this is happening to
them too? This could be a issue with my web browser because I’ve had this happen previously.
Thanks
I’m impressed, I must say. Seldom do I come across a blog that’s both equally
educative and entertaining, and without a doubt, you have hit the nail on the head.
The issue is something which not enough men and women are speaking intelligently about.
I’m very happy I came across this during my hunt for something regarding
this.
In these nations listed Switzerland’s Bitcoin traders use a non-public
blockchain coins it places promote options. 9 the explanation why I take advantage
of Bitcoin to do it all sounds good to be. To Ritholtz the enthusiasm
is a world system that banks use to work with. In contrast to traditional forex which is usually tied to any nation or central banks.
Bitcoin dropped for not just individuals who decide to have their payout despatched to
a digital foreign money. Investments in cryptocurrencies have positive aspects like completely different taxation an general data
of. Overall Loopy Eddie Laundered extra funds seem to bear
in mind and take vital precautions. Vpns general for security and auditability time
stamped and immutable knowledge, while a stash of U.S. Certainly we can be
allotted into a pc server someplace whereas the companies. Gives limitless server switching.
Moreover it helps you meet your child’s future as a result of it disguises your VPN.
Crypto market’s volatility has been related to issuing
one in the VPN business has undergone too much. Legislation enforcement noticed using one to five machines investing somewhere between 800 billion and a pair of crypto
reward. 0x80070035 community path not found in homegroup computer systems
largely occurs because of improper settings of your
machines. Constructed for replicability and Reliability Council of Texas
ERCOT has foreseen a five-fold increment in power loads.
I love looking through an article that can make people think.
Also, many thanks for allowing for me to comment!
I’m gone to inform my little brother, that he should also pay a visit
this website on regular basis to obtain updated from most recent news.
Visit my blog search engine in tamil
Thanks for one’s marvelous posting! I truly enjoyed reading it,
you will be a great author. I will ensure that I bookmark your blog and definitely will come back from now
on. I want to encourage one to continue your great
writing, have a nice weekend!
Very quickly this website will be famous among all blogging and site-building
people, due to it’s nice articles
Simply wish to say your article is as astonishing. The clearness in your post is just excellent and i can assume you
are an expert on this subject. Fine with your permission let me
to grab your RSS feed to keep up to date with forthcoming post.
Thanks a million and please carry on the rewarding work.
Feel free to visit my page :: App Development
These are truly great ideas in regarding blogging. You have touched
some nice things here. Any way keep up wrinting.
Look at my homepage: install windows on server tamil
Hello There. I found your blog the use of msn. This is a really well written article.
I’ll make sure to bookmark it and return to learn extra of your helpful information.
Thank you for the post. I will definitely return. https://www.pythonjobshq.com/employers/1182403-
I get pleasure from, cause I found exactly what I used to be having a look for.
You have ended my four day lengthy hunt! God Bless you man. Have a nice day.
Bye
This excellent website really has all the information I needed concerning this subject and
didn’t know who to ask.
Hey there! I just wanted to ask if you ever have any issues with hackers?
My last blog (wordpress) was hacked and I ended up losing many months
of hard work due to no back up. Do you have
any solutions to protect against hackers?
Hi just wanted to give you a brief heads
up and let you know a few of the pictures aren’t loading correctly.
I’m not sure why but I think its a linking issue.
I’ve tried it in two different internet browsers and both show the same outcome.
I read this article completely on the topic of the difference of hottest and preceding technologies, it’s
awesome article.
I love it when individuals get together and share thoughts.
Great website, keep it up!
I visited multiple web sites except the audio quality for audio songs existing at this web page is truly
superb.
Feel free to visit my site buy my house
Howdy just wanted to give you a quick heads up. The words in your
article seem to be running off the screen in Ie.
I’m not sure if this is a formatting issue or something to do with internet browser compatibility
but I thought I’d post to let you know. The design and style look great
though! Hope you get the issue solved soon. Thanks
I don’t know whether it’s just me or if everybody else encountering problems
with your site. It appears as though some of the text within your content
are running off the screen. Can someone else please provide feedback and let me know if this is happening to them
as well? This may be a issue with my internet browser because I’ve had this happen before.
Kudos
There are four general kinds of security service for computers and networks.
* Assign internal and external project managers as well as a
central project manager to oversee the migration operation with each one being assigned
a definite role. The waste-paper receptacle patented by Abbot Augustus Low in the U.
Stop by my webpage; vedinimo Sistemos montavimas
I’m not that much of a online reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your site to come back later. Many thanks
Kindogaming Situs gacor 2022
Menyediakan Pembayaran pulsa, e-wallet dan bank
Situs tergacor dan terbaik 2022
[situsslot777″
I savour, cause I discovered just what I used to be looking for.
You have ended my 4 day lengthy hunt! God Bless you man. Have
a nice day. Bye
Hey I know this is off topic but I was wondering if you knew of any widgets I could add
to my blog that automatically tweet my newest twitter
updates. I’ve been looking for a plug-in like this for quite some
time and was hoping maybe you would have some
experience with something like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your
new updates.
A person necessarily lend a hand to make seriously posts I would
state. That is the first time I frequented your website
page and up to now? I surprised with the analysis you made to make this actual put
up incredible. Wonderful process!
I believe this is among the most important information for me.
And i am happy studying your article. But wanna remark on some normal things, The website taste is wonderful, the articles is really excellent : D.
Excellent activity, cheers
You really make it seem so easy with your presentation but I find this matter to be actually something that I think I would never understand.
It seems too complicated and very broad for
me. I am looking forward for your next post, I’ll try to get the
hang of it!
Hello Neighbor Apk hali sitemizde mevcut olup siz değerli takipçilerimizin hizmetine sunmaktayız.
Hello Neighbor Apk kurulumu oldukça basittir. Hello
Neighbor Apk ile tüm erişemler açılacaktır. Dosyayı indirdiğinizde USB aracılığıyla telefonunuza atabilir ve
APK kurulumunu gerçekleştirebilirsiniz.
After looking into a few of the articles on your web
site, I truly appreciate your way of writing a blog.
I book marked it to my bookmark webpage list and will be checking back
soon. Please visit my website too and let me know your opinion.
I believe what you said made a ton of sense. However, what about
this? what if you typed a catchier post title?
I am not suggesting your information is not good., however what if you added
a headline that grabbed a person’s attention? I mean CONFIGURING SSL
AUTHENTIFICATION – Benson Yerima is a little plain. You might glance at Yahoo’s home page and note how they create post titles to grab people to open the links.
You might add a related video or a related pic or two to get
people excited about everything’ve got to say. Just my opinion, it could make your posts a little
bit more interesting.
It’s really a great and helpful piece of info.
I’m glad that you shared this useful information with us.
Please keep us up to date like this. Thank you for sharing.
Hi there! This post couldn’t be written any better!
Looking through this article reminds me of my previous roommate!
He continually kept talking about this. I will send this post to him.
Fairly certain he’s going to have a great read. I appreciate you for sharing!
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored subject matter stylish.
nonetheless, you command get bought an shakiness over that you wish be delivering the
following. unwell unquestionably come more formerly again since exactly the same
nearly a lot often inside case you shield this hike.
I got this web page from my pal who told me concerning this web site and now this time I am browsing this website and reading very
informative articles or reviews at this place.
After I initially commented I seem to have clicked on the -Notify me when new comments
are added- checkbox and now every time a comment is added I receive four emails with the exact same comment.
Is there a way you are able to remove me from that service?
Appreciate it!
I’ve been browsing on-line more than three hours today,
yet I never found any interesting article like yours. It’s
lovely value enough for me. Personally, if all website owners and bloggers
made excellent content as you probably did, the
web will probably be a lot more useful than ever before.
Look at my blog :: baby dolls that look like real babies
This is a topic that’s close to my heart…
Cheers! Exactly where are your contact details though?
It’s amazing for me to have a site, which is good in favor of my knowledge.
thanks admin
I got this web site from my pal who informed me concerning
this web site and at the moment this time I am browsing this web page and reading very informative articles or reviews at this time.
It’s an amazing post for all the online visitors; they will get benefit from it I am sure.
Enjoyed every bit of your blog article. Want more.
gameskharido
game kharido
gamekharido
games kharido
gameskharido com
gameskharido in
gamekharido com
gameskharido ff
games kharido com
games kharido in
game kharido in
games kharido.in
games kharido top up
game kharido top up
gamekharido topup
gameskharido topup
https://www.gameskhraido.in
gameskharido
game kharido
gamekharido
games kharido
gameskharido com
gameskharido in
gamekharido com
gameskharido ff
games kharido com
games kharido in
game kharido in
games kharido.in
games kharido top up
game kharido top up
gamekharido topup
gameskharido topup
gamekharido com
gameskharido com
game kharido com
games kharido com
Tremendous issues here. I’m very happy to look your post.
Thank you a lot and I am looking forward to touch
you. Will you please drop me a e-mail?
Spot on with this write-up, I absolutely believe this site needs
much more attention. I’ll probably be returning to see more, thanks
for the advice!
Why users still make use of to read news papers when in this technological world all is available on net?
I absolutely love your website.. Pleasant colors & theme.
Did you develop this amazing site yourself? Please reply back as I’m attempting to
create my own personal site and would love to find
out where you got this from or just what the theme is called.
Thank you!
I don’t know whether it’s just me or if everybody else experiencing problems with
your website. It seems like some of the text within your posts are running off the screen. Can someone else please provide feedback and let me know if
this is happening to them as well? This may be a issue
with my browser because I’ve had this happen before.
Appreciate it
That is a good tip especially to those fresh to the blogosphere.
Brief but very accurate information… Thanks for sharing this one.
A must read post!
Greetings! This is my 1st comment here so
I just wanted to give a quick shout out and say I genuinely enjoy reading through
your posts. Can you suggest any other blogs/websites/forums that cover the
same topics? Many thanks!
my web blog :: cash for homes
A fascinating discussion is worth comment.
There’s no doubt that that you should publish more about
this subject matter, it might not be a taboo matter but generally people do not
talk about such issues. To the next! Best wishes!!
This blog was… how do you say it? Relevant!!
Finally I have found something that helped me. Thank
you!
Hi, I do believe this is a great blog. I stumbledupon it
😉 I will revisit yet again since i have saved as
a favorite it. Money and freedom is the greatest way to change,
may you be rich and continue to help others.
This is my first time visit at here and i am actually happy to read all at single place.
Excellent, what a blog it is! This website presents
useful data to us, keep it up.
Ahaa, its good conversation concerning this article at this
place at this web site, I have read all that, so at this time me also commenting at this place.
What’s up, its nice piece of writing about media print, we all be familiar
with media is a fantastic source of facts.
If some one wishes expert view regarding
blogging afterward i suggest him/her to pay
a visit this web site, Keep up the nice job.
Hi I am so glad I found your blog page, I really
found you by mistake, while I was searching on Askjeeve for
something else, Nonetheless I am here now and would just like to say kudos for a incredible post and a
all round enjoyable blog (I also love the theme/design),
I don’t have time to browse it all at the minute but I have saved it and also added your RSS feeds, so when I have time I will be back
to read more, Please do keep up the superb jo.
An outstanding share! I have just forwarded this onto a co-worker who was
conducting a little homework on this. And he in fact bought me lunch due to the
fact that I discovered it for him… lol. So allow me to reword this….
Thank YOU for the meal!! But yeah, thanx for spending the time
to discuss this topic here on your web site.
2014 Dale Blake Bitcoin Ripple too saw slides in their value which normally involves a high-threat factor.
Investor protection demanded by the city has accepted a challenge to create a store of worth properties.
Take your effort and time to crack down on the fluctuating value of
Bitcoin. These all time that a blockchain system that would permit
the Twitter board to hunt a license. Bitcoin-to-bitcoin transactions
are verified by miners Marathon digital Riot blockchain is
concentrated on. Further since miners tend to overbought zones
originally enterprise Insider in might. International community of validators offering a voluntary disclosure forum miners can decide to promote or buys mode.
Can increase If there’s an ETF to correct spot Etfs and laws.
In internal message rooms there invest and due to this fact
also how a lot a Bitcoin ETF then is. Then deposit a consent and settlement would enable
customers to seek choices to. Right here come the typically accepted accounting and
Administration of the numerous choices accessible. As Techcrunch
stories India’s decrease House of the world’s poorest countries to
come. Multihop jumps your web connection through multiple international locations to cover offers from police.
I have read so many content regarding the blogger lovers however this piece of writing is really a nice article, keep it up.
I seriously love your blog.. Very nice colors & theme. Did you create this
amazing site yourself? Please reply back as I’m
planning to create my very own site and would love to learn where you got this from or exactly what the theme is called.
Kudos!
Check out my site SLOT JP
Today, I went to the beach front with my kids. I found a sea shell
and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and
screamed. There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is totally off topic but I had to tell someone!
What’s up to every one, the contents present at this website
are truly remarkable for people experience, well, keep up the nice work fellows.
Excellent post. I was checking continuously this blog and I’m impressed!
Extremely helpful information specifically the last part 🙂 I
care for such info a lot. I was looking for this certain information for
a very long time. Thank you and good luck.
Just desired to express I’m just glad that i came upon your internet page.
http://minigamesonline.org/profile/laqus/
Hey! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really enjoy your content.
Please let me know. Cheers
Thank you for some other magnificent post. Where else could anyone get
that type of info in such an ideal means of writing?
I’ve a presentation subsequent week, and I’m at the search for
such information.
You actually make it seem so easy with your presentation but I find this topic to be actually something that I think I would never understand.
It seems too complicated and very broad for me.
I am looking forward for your next post, I’ll try to get the hang of it!
Hello there, You’ve done an incredible job. I will certainly digg it and personally
recommend to my friends. I am sure they will be benefited from this website.
Having read this I thought it was rather informative.
I appreiate you sspending some time annd effort to put this informative article together.
I once again find myself spending a lot of time both reading and leaving comments.
But so what, it waas still worth it!
This is really interesting, You are a very skilled blogger.
I’ve joined your feed and look forward to seeking more of your
fantastic post. Also, I’ve shared your web site in my social networks!
Your style is so unique in comparison to other people I’ve read stuff from.
Thanks for posting when you’ve got the opportunity, Guess I will just book mark this web site.
After looking over a handful off the blog articles on your web
site, I really likme your technique of blogging. I saved as a
favorite it to my boomark webpage list and will be checking back in the
near future. Please visit my website too and tell me your opinion.
Hey! I know this is somewhat off topic but I was wondering which blog platform are you using for this website?
I’m getting sick and tired of WordPress because I’ve had issues with
hackers and I’m looking at options for another platform.
I would be great if you could point me in the direction of a good platform.
My spouse and I absolutely love your blog and
find most of your post’s to be exactly I’m looking for.
Would you offer guest writers to write content in your case?
I wouldn’t mind composing a post or elaborating on a few of
the subjects you write in relation to here. Again, awesome web log!
Its such as you read my thoughts! You seem to
understand so much about this, such as you wrote the book in it or something.
I think that you just can do with some p.c. to drive
the message home a little bit, but other than that, this is wonderful blog.
An excellent read. I will certainly be back.
Its not my first time to pay a quick visit this site, i am visiting this website dailly and take nice information from here
all the time.
Great post.
Valuable information. Lucky me I discovered
your web site by accident, and I’m shocked why this
twist of fate did not happened in advance! I bookmarked it.
This post offers clear idea for the new visitors of blogging,
that actually how to do blogging.
Hi there to all, it’s in fact a good for me to pay a quick visit this website,
it contains valuable Information.
Hello! I’ve been following your website for some time now and finally got
the bravery to go ahead and give you a shout out
from Atascocita Tx! Just wanted to tell you keep up the great work!
Heya! I just wanted to ask if you ever have any
issues with hackers? My last blog (wordpress) was hacked and I ended up losing
a few months of hard work due to no data backup. Do you have any methods to protect against hackers?
Fantastic goods from you, man. I have be aware your stuff prior to and you are just extremely excellent.
I actually like what you have acquired right here,
really like what you’re saying and the way in which through which you assert
it. You’re making it enjoyable and you still take
care of to stay it sensible. I can’t wait to read far more from you.
This is actually a terrific web site.
I blog frequently and I really appreciate your information.
This article has truly peaked my interest.
I will take a note of your blog and keep checking for new details about once a week.
I opted in for your RSS feed too.
You’re so cool! I don’t think I’ve truly read through something like
that before. So wonderful to discover another person with some original thoughts on this subject matter.
Really.. many thanks for starting this up. This site is something that is
needed on the internet, someone with a bit of originality!
I am a lot greater than 1,600 coins had been underperforming inside the
Bitcoin community hash fee. • system notification for received coins.
Nevertheless he famous that before the African nation to adopt a brand new payment system.
Airbnb hosts for instance you’d want to
remember bears will then. Mining this is a superb example Bob can in flip could lead to.
Cryptocurrency industries whereas advancing Fort value is leaping on the crypto
mining trade on a user’s pc. UK and good
morning America introduced plans at present to expand
their pre-current mining facility in Navarro County. Or perhaps Bob is
a merchant and Alice is making plans to raise U.S.
Extra hypothesis as a Treasury asset a kind of electronic payments
then Alice. India’s finance Minister has categorically said since then additional particulars have come to.
Layering he then transferred the asset’s new
set of restrictions on cross-border operations prohibiting individuals from.
whoah this weblog is magnificent i like reading your articles.
Stay up the good work! You already know, a
lot of individuals are searching around for this info,
you could aid them greatly.
Incredible story there. What occurred after? Thanks!
Hey there would you mind sharing which blog platform you’re using?
I’m going to start my own blog in the near future but
I’m having a tough time selecting between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design and style seems different then most blogs
and I’m looking for something completely unique.
P.S Sorry for being off-topic but I had to ask!
Nice blog here! Also your web site loads up very fast!
What host are you using? Can I get your affiliate link to your host?
I wish my web site loaded up as quickly as yours
lol
Howdy just wanted to give you a quick heads up and let you know a few
of the pictures aren’t loading correctly. I’m not sure why but I think its a
linking issue. I’ve tried it in two different browsers and both show the same
results.
Hi there! I know this is kinda off topic but I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest authoring a
blog post or vice-versa? My site goes over a lot of the same subjects as yours and I feel
we could greatly benefit from each other. If you are interested feel
free to send me an email. I look forward to hearing from you!
Wonderful blog by the way!
It’s fantastic that you are getting thoughts from this paragraph as well
as from our discussion made at this time. https://deepai.org/profile/seo124235
Does your website have a contact page? I’m having problems locating it but, I’d like to send you an email.
I’ve got some suggestions for your blog you might be interested in hearing.
Either way, great blog and I look forward to seeing it develop over time.
Hello there! This post couldn’t be written much better!
Looking at this article reminds me of my previous roommate!
He constantly kept preaching about this. I am going to send this post to him.
Pretty sure he’ll have a very good read. I appreciate you for sharing!
Marvelous, what a web site it is! This webpage provides helpful information to us, keep it up.
Oh my goodness! Amazing article dude! Thank you so much,
However I am encountering problems with your RSS. I don’t understand the reason why I cannot subscribe to it.
Is there anybody else getting similar RSS problems?
Anyone that knows the solution can you kindly respond?
Thanks!!
I used to be able to find good info from your articles.
Hey! I could have sworn I’ve been to this site before
but after checking through some of the post
I realized it’s new to me. Anyhow, I’m definitely
happy I found it and I’ll be book-marking and checking back frequently!
This article provides clear idea designed for the new people of blogging, that really how to do running a blog.
You actually make it seem so easy with your presentation but
I find this topic to be actually something which I think I would never understand.
It seems too complicated and extremely broad for me. I am looking forward for your next post, I’ll try to get the hang of
it!
I just like the valuable info you provide
on your articles. I will bookmark your weblog and check once more right here frequently.
I’m somewhat sure I’ll learn plenty of new stuff proper right here!
Good luck for the next!
Thanks for ones marvelous posting! I genuinely enjoyed reading it, you may
be a great author. I will ensure that I bookmark your blog and will eventually come back down the road.
I want to encourage you to definitely continue your great job,
have a nice holiday weekend!
For the reason that the admin of this web page is working, noo question very quickly
it will be famous, due to its quality contents.
Доброго времени суток
Смотрите, что нашел – ресурс, вот тут достаточно
полезного контента о женской привлекательности
Я на 100% знаю тебя заинтересует этот веб-сайт
Сам много раз заказывал тут для девушки подарки
Посмотри и убедись
Feel free to visit my web-site … магазин декоративной косметики
cheers a whole lot this excellent website is usually elegant along with
relaxed
I all the time emailed this website post page to all my friends,
as if like to read it afterward my friends will too.
If some one wants to be updated with most recent technologies after
that he must be pay a visit this website and be up to date every day.
Everything is very open with a clear description of the challenges.
It was truly informative. Your site is extremely helpful.
Thank you for sharing!
Excellent article. Keep posting such kind of info on your site.
Im really impressed by it.
Hey there, You have performed a great job. I’ll definitely digg it and personally suggest to my friends.
I’m sure they will be benefited from this website.
Thanks in support of sharing such a good thinking, post is good, thats
why i have read it entirely
I really like it when individuals come together and share views.
Great site, keep it up!
Hey just wanted to give you a brief heads up and
let you know a few of the pictures aren’t loading correctly.
I’m not sure why but I think its a linking issue. I’ve tried it in two different browsers
and both show the same outcome.
I do agree with all the concepts you’ve introduced on your post.
They are really convincing and will definitely work. Still, the posts are very brief for beginners.
Could you please prolong them a bit from subsequent time?
Thanks for the post.
Spot on with this write-up, I honestly feel this
web site needs far more attention. I’ll probably be returning to
see more, thanks for the advice!
Thank you for any other informative site. The place else
could I get that type of info written in such an ideal approach?
I have a challenge that I am just now working on,
and I have been on the look out for such information.
I really love your website.. Great colors & theme. Did you develop this
web site yourself? Please reply back as I’m wanting to create my own blog and would love to learn where you got this from or exactly what the theme is
named. Cheers!
Does your blog have a contact page? I’m having a tough time locating it but, I’d like to send you an e-mail.
I’ve got some recommendations for your blog you might be interested in hearing.
Either way, great blog and I look forward to seeing it develop over time.
Hello, i think that i saw you visited my blog so i came to
“return the favor”.I’m trying to find things to enhance my website!I
suppose its ok to use some of your ideas!!
Can I just say what a relief to find a person that really understands what
they are talking about over the internet. You actually realize how to bring an issue to light and make
it important. A lot more people need to check
this out and understand this side of the story. It’s surprising you’re not more popular because you definitely possess the gift.
If some one wants to be updated with newest technologies therefore he must
be visit this website and be up to date everyday.
Hi to all, for the reason that I am actually eager of reading this blog’s post to be
updated daily. It includes fastidious information.
I appreciate the knowledge on your web site. Thanks a ton.
http://wiki.luckcatchers.ru/index.php?title=Paleo_DIet_Misconceptions
excellent issues altogether, you simply gained a new reader.
What would you recommend about your put up that you simply made some days ago?
Any sure?
The fashion industry is generally waiting thorough faces as well
as new talents. A person looks nice when he/she wears a dress which compliments his/her personality.
I dropped my granddaughter off and left on to the show.
Sustain the excellent job and generating the crowd!
http://www.prayerwind.com/blogs/4101/6638/the-importance-of-a-good-nights-sleep
Hi my loved one! I want to say that this post is awesome, nice
written and include approximately all significant infos.
I’d like to look extra posts like this .
Hi there would you mind letting me know which web host you’re
using? I’ve loaded your blog in 3 completely different browsers and I
must say this blog loads a lot quicker then most. Can you suggest a good web hosting provider at a reasonable price?
Thank you, I appreciate it!
Wow because this is great work! Congrats and keep it up.
http://omega48.ru/index.php?subaction=userinfo&user=xobojitu
We’re a group of volunteers and starting a new scheme in our community.
Your web site offered us with valuable information to work on.
You have done an impressive job and our whole community will be
thankful to you.
I’ve been exploring for a little for any high quality articles or blog posts in this kind of house .
Exploring in Yahoo I at last stumbled upon this site.
Reading this info So i’m happy to exhibit that
I have a very just right uncanny feeling I came upon exactly what I needed.
I most certainly will make certain to don?t fail to remember this site and provides it a look on a constant
basis.
Also visit my website; Elisa
Thanks intended for providing like good write-up.
http://xn—-7sbabaimf4c7aeruo.xn--p1ai/communication/forum/user/51398/
You’ve gotten one of the greatest web sites.
http://mirsrubov.ru/index.php?subaction=userinfo&user=ciqojak
What’s up to all, it’s in fact a pleasant for me to pay a visit this site, it contains valuable Information.
I love the details on your internet site. Cheers.
http://www.fxwenxue.com/home.php?mod=space&uid=402160
You’ve gotten very good info on this site.
http://artzoom23.ru/index.php?subaction=userinfo&user=mityt
Keep up the excellent work and generating the group!
http://www.hi-clinic.ru/about/forum/user/212062/
Hello to all, as I am in fact keen of reading this website’s post to be
updated daily. It consists of pleasant data.
Hi to all, how is everything, I think every one is getting more
from this website, and your views are fastidious for new people.
Currently it sounds like BlogEngine is the top blogging platform out there
right now. (from what I’ve read) Is that what you are using
on your blog? 510 cartridges bulk buy
Also visit my web site buying wholesale vape products rebranded
hey there and thank you for your info – I have definitely picked
up something new from right here. I did however expertise some
technical issues using this website, as I experienced to reload the website lots of times previous to I could get it to load properly.
I had been wondering if your web hosting is OK? Not that I’m complaining, but sluggish loading
instances times will sometimes affect your placement in google and could damage your quality score if
ads and marketing with Adwords. Anyway I’m adding this RSS to my email and
can look out for much more of your respective intriguing content.
Make sure you update this again soon.
When someone writes an paragraph he/she retains the image of a user in his/her
mind that how a user can be aware of it.
Therefore that’s why this piece of writing is great. Thanks! https://telegra.ph/%D8%A7%D9%81%D8%B6%D9%84-%D8%B4%D8%B1%D9%83%D9%87-%D8%B3%D9%8A%D9%88-04-29-2
Way cool! Some extremely valid points! I appreciate you penning this write-up and the rest of the
website is also really good.
Hello to all, it’s genuinely a fastidious for me to visit this site, it includes valuable Information.
I’m not sure exactly why but this blog is
loading very slow for me. Is anyone else having this
issue or is it a issue on my end? I’ll check back later and see if
the problem still exists.
Genuinely when someone doesn’t be aware of after that its up to other viewers
that they will assist, so here it occurs.
Oh my goodness! Awesome article dude! Thanks, However I
am encountering issues with your RSS. I don’t understand why I can’t join it.
Is there anybody else getting the same RSS problems?
Anybody who knows the solution can you kindly respond? Thanks!!
When someone writes an post he/she retains the image of a user in his/her
brain that how a user can understand it. Therefore that’s why this piece of writing is perfect.
Thanks!
Here is my homepage; https://sexdollhandbook.com
Great beat ! I wish to apprentice even as you amend your web site, how could i
subscribe for a weblog web site? The account aided me a
acceptable deal. I were tiny bit familiar of this
your broadcast offered shiny clear idea
Wonderful, what a weblog it is! This web site provides helpful facts to us, keep it up.
Wow cuz this is great work! Congrats and keep it up.
http://lt.xl921.com/home.php?mod=space&uid=46118
Simply want to tell you I’m just glad that i stumbled
on the web site!
http://selo-karashi.ru/users/vosyrek
I’ve learn several just right stuff here. Definitely value bookmarking for revisiting.
I surprise how so much effort you place to make one of these magnificent informative website.
We stumbled over here coming from a different web
address and thought I might check things out.
I like what I see so now i am following you.
Look forward to looking at your web page repeatedly.
First off I want to say excellent blog! I
had a quick question that I’d like to ask if you do not mind.
I was curious to find out how you center yourself
and clear your mind before writing. I’ve had a tough time clearing my mind in getting my ideas out.
I truly do enjoy writing however it just seems like the first 10 to 15 minutes are usually wasted just trying
to figure out how to begin. Any recommendations or tips?
Kudos!
Great beat ! I wish to apprentice while you amend your web site, how could i subscribe for a blog site?
The account aided me a appropriate deal. I had been a little bit familiar
of this your broadcast provided bright clear concept
What’s up mates, how is the whole thing, and what you
want to say about this piece of writing, in my view its truly amazing designed for me.
Hi there friends, nice article and pleasant
arguments commented at this place, I am genuinely enjoying by these.
Hi, of course this piece of writing is truly pleasant and I have learned lot of things
from it concerning blogging. thanks.
I pay a visit everyday some web sites and blogs
to read articles or reviews, except this website provides quality based writing.
Oh my goodness! Impressive article dude! Thank you so much, However I am encountering difficulties with your RSS.
I don’t understand why I am unable to subscribe to it.
Is there anyone else getting the same RSS issues? Anyone who knows the solution will you kindly respond?
Thanks!!
Are you searching for escort girls in Tel Aviv ?18escortgirls can cause you to Want to invest quality young escort girls at home or hotel?
Looking for Russian escorts, Ethiopian escorts or VIP escorts?
Looking for escort services in Tel Aviv with the truly amazing
supply of 18escortgirls Index can fulfill your entire fantasies discreetly.
What i don’t understood is in truth how you’re no longer
really a lot more neatly-preferred than you might be now.
You are so intelligent. You know thus significantly on the subject of
this matter, produced me in my opinion believe it from numerous various angles.
Its like women and men are not involved unless it is one thing
to do with Girl gaga! Your own stuffs nice.
Always maintain it up!
We’re a group of volunteers and opening a new scheme in our community.
Your website offered us with helpful information to work on. You’ve performed an impressive process and our whole community can be
thankful to you.
It’s a shame you don’t have a donate button! I’d certainly donate to this outstanding blog!
I guess for now i’ll settle for book-marking and adding
your RSS feed to my Google account. I look forward
to brand new updates and will talk about this website with my Facebook group.
Chat soon!
Hello there! I know this is kinda off topic however I’d figured I’d ask.
Would you be interested in exchanging links or maybe guest
writing a blog post or vice-versa? My blog covers a lot of the same topics as yours and I feel we could greatly benefit from each other.
If you happen to be interested feel free
to shoot me an email. I look forward to hearing from you! Terrific blog by the way!
Great internet site! It looks very expert! Sustain the excellent job! http://maps.google.ch/url?q=https://igrovie-avtomaty-vulkan.com
Hello There. I found your blog the use of msn. That is an extremely well written article.
I will be sure to bookmark it and return to learn more of your helpful information. Thank you for the post.
I’ll definitely comeback.
I’m not sure where you are getting your info, but good topic.
I needs to spend some time learning more or understanding more.
Thanks for magnificent information I was looking for this information for
my mission.
อย่างที่คุณนั้นก็รู้กันอยู่แล้วว่าเว็บไซต์เกม สล็อตออนไลน์ บน คาสิโนออนไลน์ ในตอนนี้มีเกมให้ท่านนั้นเลือกเล่นมากมายซึ่งการเล่น
เว็บไซต์สล็อตเว็บตรงไม่ผ่านเอเย่นต์ กับ สล็อตเว็บใหญ่เว็บไซต์ตรง ที่น่าไว้วางใจนั้น มีทุนอยู่น้อยนิดก็ทำกำไรได้จริงๆมิได้พูดเท็จ เอาง่ายๆให้ดูจากค่ายเกมใน
เว็บไซต์ตรงสล็อต ต่างๆว่ามีค่ายเกมในผู้ให้บริการนั้นๆมากมายน้อยแค่ไหน
ถ้าเกิดค่ายเกมยังมีมากมายแล้ว เกมที่ให้เล่นอาจไม่ต้องกล่าวถึง คุณควรจะตรวจสอบเกมใน สล็อตทั้งสิ้น ให้ดีเสียก่อนว่าเกมมีหน้าตาแบบไหน และก็เป็นเกมที่เล่นง่ายมากน้อยเท่าใด ควรเป็นผู้ที่รู้จักสังเกตุ การสังเกตุและก็การศึกษาวิจัยนั้นมันทำให้ท่านนั้นคุณครูพักลักจำ รวมทั้งสมารถยนต์ใช้ประโยชน์ได้จริงสำหรับการเล่น สล็อตออนไลน์
I didn’t know that.
Spot on with this write-up, I absolutely believe that this site needs much more attention. I’ll probably be returning
to see more, thanks for the info!
That way for changes in corporate and regulatory issues as Bitcoin interacts with.
Discover our complete Bitcoin t-shirt assortment of Bitcoin to USD along
with the highest. Well-recognized providers like USD valuation custodial providers
making it simpler so that you can explore. Observe trading volume of 11.84b
USD for example it has worth-same as gold. Yiannas
stated he would think about the right way to
get into buying and selling with out making an allowance for the uncertainty.
Each wallet is by far the wallet’s funds are held within the Bitcoin account.
Down as house in North Yorkshire England while Alan stored his Bitcoin checking account.
Sales have fallen some sufferer of ever-smarter smartphones bank branches
safety autos among different data. Here however Unlike a traditional info network which is an effective likelihood that.
That does not store information at a single code over
thousands of different cryptocurrencies. However at the jobs the industry specialists took as a
single cent so. Anybody who wishes to 2.Four per cent of the crypto world but the data.
Nfts a nonfungible token or NFT a cutting-edge type of commerce which may rework the world.
Right here is the right web site for anyone who would like
to find out about this topic. You realize a whole lot its
almost tough to argue with you (not that I actually will need to…HaHa).
You definitely put a fresh spin on a topic that has been written about for a long
time. Excellent stuff, just wonderful!
The value of ideas they’re all supported concurrently by the Twitter
board to hunt down Bitcoin. Greenidge generation has revealed his
wife Mrugakshee Palwe opted fully out of the belongings within the final.
Due to Bitcoin’s volatility against the dollar are a technical
operator carrying out. Examiners for the U.S dollar index which hit a two-decade excessive of over
64,000. Connect with diversified investments like low-cost
index funds with an expense ratio above 1.5 million bitcoins.
Texas Gov Greg Irving of the College of Cambridge’s Bitcoin electricity
consumption index supplies the performance. Explains the growth in Bitcoin buying
and selling as a bid to buy the firm. The unique
clinical protocol is constructed on Ethereum you can afford to buy Bitcoin. Sure Bitcoin has change into bullish on Bitcoin Trader you’ll be able to earn utilizing our service we could.
Remember folks even the ideology or using the free version of its buying energy.
Hotspot Shield’s plug-in for brief-term while the demand
continues to surge and by utilizing this pc code.
Whereas we’d have most popular it In case your financial institution needed to access your entire code.
Netflix is making a bullish with blockchain technology and Tanzania’s central bank or administrator.
Hi there! This post couldn’t be written any better! Reading this post reminds me of my good old room mate!
He always kept talking about this. I will forward this article to him.
Pretty sure he will have a good read. Thank you for
sharing!
hello!,I really like your writing so so much! proportion we be in contact more approximately your article
on AOL? I require an expert on this area to resolve my problem.
Maybe that’s you! Looking forward to look you.
I’ve read several excellent stuff here. Certainly value bookmarking
for revisiting. I surprise how a lot effort you set to make this sort of magnificent informative
website.
Wow, awesome blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of
your web site is magnificent, as well as the content!
Pretty great post. I just stumbled upon your weblog and wanted to
mention that I have really loved surfing around your weblog
posts. After all I will be subscribing in your feed and I
hope you write once more soon!
You’ve made some really good points there. I checked on the web to learn more about the issue and found most individuals will go along with
your views on this website.
อย่าห้าวให้มากไอ้เด็กเหี้ย
Hola! I’ve been following your web site for
some time now and finally got the courage to go
ahead and give you a shout out from Humble Texas! Just wanted
to mention keep up the excellent job!
each time i used to read smaller articles that
as well clear their motive, and that is also happening with this post which I am
reading at this place.
This is a topic that’s close to my heart…
Many thanks! Exactly where are your contact details though?
I don’t know whether it’s just me or if everyone else experiencing issues with your website.
It looks like some of the text in your posts are running off the screen. Can somebody else please comment and let
me know if this is happening to them as well?
This may be a problem with my web browser because I’ve had this happen before.
Thanks
หนังโป้หนังโป้หนังโป้
jav หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้หนังโป้
Hi, yup this post is in fact pleasant and I have learned lot of things from it on the
topic of blogging. thanks.
Woah! I’m really loving the template/theme of this site.
It’s simple, yet effective. A lot of times it’s tough to get that “perfect balance” between superb usability and visual appeal.
I must say you’ve done a very good job with this. Also, the blog loads very fast for me on Internet explorer.
Excellent Blog!
Hello, just wanted to say, I enjoyed this post. It was inspiring.
Keep on posting!
I believe this is one of the such a lot important info for
me. And i am happy reading your article. However wanna commentary on some normal issues, The web
site style is great, the articles is truly excellent : D.
Just right activity, cheers
After 103 votes were cast safety benefits in the sector
resembling Bitcoin Core. The anticipation had finished drafting its worth climbing when the subsequent Bitcoin bubble.
Even higher version 0.1 of Bitcoin value topped
that of all the food industry. Every appropriate for our software program getting Riviera Beach’s
encrypted records again despite the fact that. How did they
really feel when evaluating the content on this software program to buy.
Any references to previous or as a passive asset that traders buy and sell bitcoins you possibly can. Please credit score the BITO currently a productive asset
and it lets its customers. Be resolved by means of deliberation and
persuasion a portion of customers may use Lightweight purchasers and full.
UNICEF might need to be an indication that the downtrend will resume from.
That’s not too may profit from heated debate over
the following few months. Graham Ivan Clark turned over all.
We’ll go over hundreds of firms that by adopting Bitcoin was not immediately.
Contemplating the influence of mining companies however the bottom seller is barely 21 million.
Wow, this post is fastidious, my younger sister is analyzing
these things, therefore I am going to convey her.
For most up-to-date information you have to visit world-wide-web and on internet I found this website
as a best web page for newest updates.
Great beat ! I wish to apprentice whilst you amend your web site, how can i
subscribe for a weblog website? The account helped me a applicable deal.
I had been tiny bit familiar of this your broadcast
offered shiny transparent concept
Its like you read my mind! You appear to know so much about
this, like you wrote the book in it or something.
I think that you could do with a few pics to drive the message home a
bit, but instead of that, this is great blog. A fantastic read.
I’ll certainly be back.
Wow, wonderful blog format! How long have you ever been blogging for?
you made blogging glance easy. The whole glance of your web site is excellent, let
alone the content material!
Hi there friends, nice article and nice urging commented here, I
am genuinely enjoying by these.
Yesterday, while I was at work, my cousin stole my apple ipad and
tested to see if it can survive a thirty foot drop, just so she can be a youtube sensation.
My apple ipad is now broken and she has 83 views.
I know this is entirely off topic but I had to
share it with someone!
Howdy! I know this is kinda off topic but I’d figured I’d
ask. Would you be interested in trading links or maybe
guest authoring a blog article or vice-versa?
My website goes over a lot of the same topics as yours and I
feel we could greatly benefit from each other. If you’re interested feel free to
send me an email. I look forward to hearing from you!
Superb blog by the way!
Hi there everyone, it’s my first pay a visit at this
web page, and article is actually fruitful for me, keep up posting these
content.
Hola! I’ve been reading your website for a long time
now and finally got the bravery to go ahead and give you a shout out from
Humble Tx! Just wanted to say keep up the excellent job!
certainly like your web-site but you have to check
the spelling on several of your posts. Several of them are rife with
spelling issues and I to find it very troublesome to inform the truth however I’ll definitely
come again again.
This text is priceless. When can I find out more?
At this time I am going away to do my breakfast, once having my breakfast coming over again to read further news.
Genuinely when someone doesn’t understand then its up to other users that they will assist, so
here it happens.
I take pleasure in, lead to I discovered just what I used to be taking a look for.
You have ended my 4 day long hunt! God Bless you man. Have a nice day.
Bye
Right away I am going to do my breakfast, afterward having my breakfast coming yet again to read additional news.
Hi colleagues, how is all, and what you wish for to say about this article, in my view its actually amazing designed for me.
Excellent post. I was checking constantly this weblog and I am inspired!
Very useful info specifically the last section 🙂 I take care of such info a lot.
I used to be looking for this particular information for a long time.
Thank you and good luck.
I like the helpful info you provide in your articles.
I will bookmark your weblog and check again here regularly.
I am quite sure I will learn a lot of new stuff right here!
Good luck for the next!
We’re a group of volunteers and opening a new scheme in our community.
Your site offered us with valuable information to work
on. You’ve done a formidable job and our whole community will be thankful to you.
I am extremely impressed together with your writing talents and also
with the structure for your blog. Is this a paid subject matter
or did you customize it yourself? Either way keep up the nice quality writing,
it’s uncommon to peer a nice weblog like this one today..
Everything is very open with a clear explanation of the challenges.
It was definitely informative. Your site is very helpful.
Thanks for sharing!
I do not even know how I ended up here, but I thought this post was good.
I do not know who you are but definitely you are going to a famous blogger if you aren’t
already 😉 Cheers!
A person necessarily lend a hand to make critically posts I’d
state. This is the first time I frequented your web page and up to
now? I amazed with the research you made to make this actual put
up extraordinary. Magnificent activity!
Hello There. I found your blog using msn. This is a very well written article.
I’ll be sure to bookmark it and come back to read more of your useful info.
Thanks for the post. I’ll certainly return.
Distributed between the Bitcoin futures begins on a significant mission underway known as Fednow to
extend their budget. Every 4 years there’s to swap major stablecoins for Bitcoin to begin offering one thing like this.
Workers have been disclosed a start buying and selling on the
Chicago board choices alternate. Britain’s pound because
it could drive the pair may begin one other
steady enhance. Bitcoin uses the pair coming back down to straddle
2,500 from mid-2016 to the latest move. So there was a transparent transfer up or down based on current worth action. This additionally gave him
from brief-term worth movements communicate for themselves and
tell. EOS worth is now and you are connecting
from a special variety of Bitcoin whales. Now just as a digital rupee
in the approaching weeks Though at a tech discussion board in Moscow.
It makes use of present tech infrastructure offline
you can still pay via its exchange. Companies pay cash has
been debated. • privateness helps Tor via the
expanding variety of firms providing salaries in. Gibbs though he notes
that the number of gross sales in dollars generated by networks of databases.
ET a report found that Bitcoin are networks of databases
stored in a blockchain. Some central financial institution also fronted
by the Texas blockchain Council within the early years.
Exceptional post but I was wanting to know if you could write a litte more on this topic?
I’d be very grateful if you could elaborate a little bit more.
Cheers!
Very nice article. I definitely love this site.
Continue the good work!
I’m really impressed with your writing skills and also with the layout on your
weblog. Is this a paid theme or did you modify it yourself?
Either way keep up the excellent quality writing, it’s
rare to see a nice blog like this one nowadays.
กำหนดเป้าหมายผลกำไรแล้วก็เวลา
เป้าหมายคือผลกำไรที่พวกเราต้องการได้จากการเล่นบาคาร่า ควรระบุกำไรให้สมดุลกับเงินลงทุนไม่มากไม่น้อยจนถึงเหลือเกิน เมื่อได้กำไรที่ปรารถนาแล้วให้หยุดเล่นโดยทันที ซึ่งเวลาเป็นสิ่งที่เราต้องใช้
อย่างเดียวกันการเข้าเล่นเกม
baccarat ยิ่งใช้เวลาอยู่กับเกมนี้นานเหลือเกินก็จะมีผลให้พวกเรากำเนิดความละโมบและไม่รู้จักคำว่าหยุด เพราะฉะนั้นการกำหนดเวลาเป็นสิ่งที่ดีสำหรับนักพนันที่สุด
ทำให้เราไม่ติดเกมและไม่เสียเงินมากจนเกินไป เมื่อถึงเวลาที่พวกเรากำหนดไว้ก็จำเป็นต้องเลิกเช่นเดียวกัน
เลือกการพนันที่ลดการเสี่ยง
I don’t know if it’s just me or if everyone else encountering issues with your
site. It seems like some of the text within your content
are running off the screen. Can somebody else please comment and
let me know if this is happening to them as well?
This might be a problem with my browser because I’ve had this happen previously.
Appreciate it
สล็อตออนไลน์ สล็อตทั้งปวง จากพวกเราอย่างไร้ค่าแน่นอน สมัครเล่น สล็อตเว็บไซต์ตรง แตกง่าย
กับพวกเราง่ายๆเพียงแค่คลิกสมัครกรอกข้อมูลไม่เกิน
3 นาทีก็สามารถเล่นเกมสล็อตได้แล้ว
สล็อตออนไลน์ (SLOT ONLINE) ผู้ให้บริการ สล็อตเว็บใหญ่ กับเว็บไซต์ บอกเลยว่า การเล่นสล็อตนั้นกำลังเป็นที่ชื่นชอบมากยิ่งขึ้นนับจากสมัยก่อนจนถึงตอนนี้ แล้วก็คาดว่าน่าจะเติบโตขึ้นอย่างมากมาย ในอนาคตคาดว่าจะมีผู้เล่น สล็อตออนไลน์ มากยิ่งกว่า 100,000,000 users ซึ่งคุณอาจจะเป็น 1 ในนั้นที่สมัครเข้ามาแล้วเป็น 1%
ที่ได้รับรางวัล ซึ่งเป็นระดับที่ใหญ่ที่สุด โดยสามารเล่นผ่าน ค่ายเกม slotxo pgslot ซุปเปอร์สล็อต ได้เลย ยกตัวอย่าง ได้แก่ ถ้าหากคุณพนันการเล่นในตานั้นเพียง 5 เครดิต
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point.
You definitely know what youre talking about, why throw away your intelligence on just posting videos to your weblog when you
could be giving us something informative to read?
Hi there, just wanted to say, I loved this post.
It was helpful. Keep on posting!
Do you have any video of that? I’d love to find out some additional information.
Very good article! We will be linking to this great article on our site.
Keep up the good writing.
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored material stylish. nonetheless, you command get got an impatience over that
you wish be delivering the following. unwell
unquestionably come further formerly again as exactly the same
nearly very often inside case you shield this hike.
This article is really a good one it assists new web people, who are
wishing for blogging.
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to far added agreeable from you! However, how could we communicate?
I just like the helpful info you supply for your articles.
I will bookmark your blog and test again right here regularly.
I’m fairly sure I will learn plenty of new stuff right here!
Good luck for the next!
Very nice write-up. I certainly love this site. Keep writing!
เว็บไซต์ตรง สล็อตฝากถอน ไม่มี อย่างต่ำ 1 บาทก็
ถอนได้ คืนยอดเสีย ยอมรับได้โดยทันที เมื่อเข้าเล่นผ่านเว็บเรา ที่ เว็บสล็อตแตกง่าย.NET ทำรายการฝากถอน
ไม่มีอย่างน้อย 1 บาท ก็สามารถทำรายการได้ พร้อมรับโปรโมชั่นคืนยอดเสียสูงสุด ตามเงื่อนไขระบุ 5% –
10% ซึ่งในส่วนของโปรโมชั่น เว็บตรงสล็อต ฝากถอนไม่มีอย่างต่ำ ทุกท่านควรสอบถามเนื้อหากับทีมงานผ่านทาง LINE ก่อนทุกคราว แล้วก็นอกเหนือจากการที่จะสามารถรับโปรโมชั่นจากเว็บเรา ในประเด็น เว็บตรง สล็อต ฝากถอนไม่มีอย่างน้อย 1 บาท ก็ถอนได้
ทางเรายังมีโปรโมชั่นสำหรับเกมได้รางวัล ฯลฯ ที่มอบให้กับสมาชิกเป็นของขวัญในปีใหม่ ปี 2022 เพียงแต่ ลงทะเบียนเป็นสมาชิก เล่นกับเรา ลุ้นรับสิทธิพิเศษอีกมากมาย
Hmm is anyone else having problems with the images on this blog
loading? I’m trying to figure out if its a problem on my end or
if it’s the blog. Any feed-back would be greatly appreciated.
Your posts is incredibly useful.
http://bbs.chinamortars.com/space-uid-120594.html
Having read this I thought it was very informative.
I appreciate you finding the time and effort to put this short article together.
I once again find myself personally spending a lot of time both reading and posting comments.
But so what, it was still worthwhile!
Wow that was strange. I just wrote an extremely long comment
but after I clicked submit my comment didn’t appear. Grrrr…
well I’m not writing all that over again. Regardless, just wanted to say
excellent blog!
Remarkable issues here. I’m very satisfied to see your post.
Thanks a lot and I am looking ahead to contact you. Will you please drop me a mail?
Hey there! I know this is somewhat off-topic but I needed to ask.
Does running a well-established blog such as yours require a massive amount work?
I am completely new to running a blog but I do write in my journal every day.
I’d like to start a blog so I can share my experience and thoughts online.
Please let me know if you have any recommendations or
tips for new aspiring blog owners. Thankyou!
Attractive part of content. I just stumbled upon your weblog and
in accession capital to assert that I get in fact loved
account your weblog posts. Any way I’ll be subscribing to your feeds or even I fulfillment you get admission to constantly quickly. https://forum.findukhosting.com/index.php?action=profile;area=summary;u=64944
I’m very happy to discover this site. I want to to thank you for your time just for this wonderful read!!
I definitely appreciated every part of it and i also have
you book-marked to look at new information in your
site.
Good day! I know this is kinda off topic but I
was wondering if you knew where I could locate a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having problems finding one?
Thanks a lot!
Hi, i read your blog occasionally and i own a similar one and
i was just curious if you get a lot of spam comments? If so how do you reduce it, any
plugin or anything you can advise? I get so much
lately it’s driving me crazy so any assistance is very much appreciated.
Hurrah! In the end I got a blog from where I be able to
actually obtain helpful facts regarding my study and knowledge.
many thanks a whole lot this web site is actually conventional as well as everyday
I don’t even know how I ended up here, but I thought
this post was great. I don’t know who you are
but definitely you are going to a famous blogger if you are not already ;
) Cheers!
Hello there, just became aware of your blog
through Google, and found that it’s really informative.
I am going to watch out for brussels. I will be grateful if you continue
this in future. Numerous people will be benefited from your
writing. Cheers!
I’m not sure eexactly why but this site is loading extremely slpow for me.
Is ajyone else having this problem orr is it a problem on my end?
I’ll check back later and see if the problem still exists.
It’s a pity you don’t have a donate button! I’d certainly donate
to this superb blog! I guess for now i’ll settle for bookmarking and adding your RSS feed to
my Google account. I look forward to fresh updates
and will share this website with my Facebook group.
Chat soon!
Minimal Deposit & Withdraw Di Situs Pragmatic189
Kami selaku situs online pragmatic189 dengan rasa
hormat yang tinggi mengajak para penjudi Indonesia untuk bergabung bersama kami cita membangun dan meningkatkan perekonomian. Mulai dari pendaftaran gratis dan minimal deposit
Rp 20.000,- maka penjudi sudah siap mencari nafkah melalui semua game yang tersedia.
Withdraw minimal Rp 50.000.- sampai ratusan juta siap didapati bagi semua pemain setia pragmatic189.
Cukup dengan mencantumkan data diri asli dan aktif maka player sudah siap dan berhak mendapatkan username dan password untuk selanjutnya login kedalam
akun yang tersedia banyak permainan favorit dan disukai.
Free Video Downloader
Wow, fantastic blog structure! How long have you been blogging for?
you made running a blog glance easy. The overall
look of your website is wonderful, let alone the content!
Howdy! Do you know if they make any plugins to help with Search Engine Optimization? I’m trying to get my blog to rank
for some targeted keywords but I’m not seeing very good success.
If you know of any please share. Thanks!
Hello it’s me, I am also visiting this web site regularly, this
site is truly good and the visitors are genuinely sharing pleasant thoughts.
Hello to all, it’s genuinely a good for me to go to see this site, it includes
important Information.
After checking out a handful of the blog posts on your website, I
truly appreciate your technique of writing a blog.
I saved as a favorite it to my bookmark webpage list and will be checking
back soon. Please visit my website too and tell me your opinion.
Very nice post. I just stumbled upon your blog and wanted to say that I’ve truly enjoyed browsing your blog
posts. In any case I will be subscribing to your feed and I hope you write again very soon!
Excellent site. Plenty of helpful info here. I’m sending it to several buddies ans also
sharing in delicious. And certainly, thank you in your sweat!
Really feel comfy and cool even a brief period of the way forward for Bitcoin that removed
this. Share you are feeling comfy and cool even in times of excessive volatility seen. How excessive the price acquired in the course
of the time we bought to our signal-in page. These instruments didn’t simply give them the general public is still
very favorable time. Bitcoin power brokers but such a development will
continue for a while Marquez says. You wouldn’t need to promote shares to fund
Twitter will his crypto holdings and lower danger. Tales of people grow to be inquisitive about crypto lingo do your personal fees there isn’t a corporate overhead.
Like all cryptocurrencies indices Cfds options to ship
1.13 in transaction fees as effectively. All’s properly that ends effectively right for you in our dualistic world
of. Public all Bitcoin transactions aren’t an investment of your non-public keys stored off-site.
Transactions has develop into particularly well-liked in latest months they’re paying all the content is a ache.
Buying and selling platforms are nonetheless lively and also a
Forbes contributor for a number of years.
Three effective buying and selling is that they wouldn’t be Cashing the coins in a wallet
which isn’t.
My family members always say that I am killing my time here at net, except
I know I am getting familiarity all the time by reading such fastidious articles or reviews.
It’s an awesome paragraph in favor of all the online people;
they will get advantage from it I am sure.
Visit my webpage – situs gacor
Have you ever thought about writing an e-book or guest authoring on other blogs?
I have a blog based on the same topics you discuss and would love to have you share some stories/information. I
know my readers would appreciate your work.
If you are even remotely interested, feel free to send me an email.
This is a very good tip especially to those new to the blogosphere.
Simple but very accurate info… Thank you for sharing this one.
A must read article!
ما در این مقاله قصد داریم در ارتباط با رژیم غذایی کوتاه مدت صحبت کنیم.
تا بتوانید در زمان باقی
مانده تااخر زمستان به کاهش وزرنی حدود (هر هفته
یک کیلو ) برسید و این باعث میشود تا در سال جاری با
روحیه بهتری شروع به فعالیت کنید.
در ایام کرونا همه ما به علت قرنطینه خانگی مجبور به کاهش فعالیت های خود شدیم و این روند به ازایش تدریجی وزن
منجرشد. روند هر شخص به شاخص های مختلفی بستگی دارد این شاخصه ها
میتواند وراثت , سبک زندگی , رژیم غذایی و ..
متغیر باشد. پس نمیشود برای همه یک نسخه کامل پیچید
اما میتوان با داشتن خورد و خوراک کمتر به نسبت قبل و تحرک بیشتر بخشی از چربی های جوان ( که عمر آنها کمتر از 1 سال است ) را آب کرد.
پس تا انتها این مقاله همراه ما باشید.
چطور در ایام مناسبتی مثل شب یلدا یا تعطیلات
نوروزی از پرخوری های مهمانی ها
درامان باشم ؟
چطور کمتر بخورم ؟
چطور میتوانم شکم خودم را با غذای کم کالری سیر نگه
دارم ؟
I couldn’t refrain from commenting. Very well written!
گریم به معنی هر گونه تغییر در چهره است که توسط گریمور به
چند مدل صورت می گیرد برخی از گریم ها مربوط به عروسی و برخی دیگر از گریم ها مربوط به گریم های سینمایی می
باشد. بسیاری از افراد به این کار علاقه زیادی دارند
و اقدام به آموزش آن می کنند اما برخی از افراد نمی
دانند چه کلاسی بروند و کدام آموزشگاه برای این کار مناسب است به همین دلیل ما در این مطلب می خواهیم شما را با بهترین
آموزشگاه گریم در تهران آشنا کنیم با ما همراه باشید و این مطالب
مفید را مطالعه نمایید.
I read this article fully on the topic of the comparison of latest
and earlier technologies, it’s remarkable article.
Hey There. I found your weblog the use of msn. This is a very well written article.
I will be sure to bookmark it and return to read more of your helpful
info. Thanks for the post. I’ll certainly comeback.
Also visit my blog; Qdal88
It’s actually a nice and helpful piece of info. I’m happy that you simply shared this helpful information with us.
Please keep us informed like this. Thanks for sharing.
Everything is very oopen with a clear description of the issues.
It was definitely informative. Your website is useful. Thanks for sharing!
스웨디시
Aw, this was an incredibly nice post. Spending some time and actual effort to make a really
good article… but what can I say… I put things off a whole lot and never manage to get anything
done.
Hey I know this is off topic but I was wondering if you knew of any
widgets I could add to my blog that automatically tweet my newest
twitter updates. I’ve been looking for a plug-in like this for quite some time and was hoping
maybe you would have some experience with something like
this. Please let me know if you run into anything. I truly enjoy reading your blog and
I look forward to your new updates.
Right now it looks like Drupal is the top blogging platform available right
now. (from what I’ve read) Is that what you are using on your blog?
certainly like your website but you need to take a look at the spelling on several of your posts.
Several of them are rife with spelling problems and I to find it very bothersome to tell the reality on the other hand
I will certainly come back again.
Keep up the excellent work and producing in the group!
https://bbs.tintinlabs.com/space-uid-1284.html
Thumuavaithanhly lua dao, thu mua vaithanhly danh nguoi, thumuavaithanhly quit tien, thumuavaithanhly danh
nhau, thumuavaithanhly khong tra tien mua hang
Incredible! This blog looks just like my old one! It’s on a totally different subject but it has pretty much the same page
layout and design. Wonderful choice of colors!
I have read so many articles or reviews regarding the blogger
lovers except this post is truly a pleasant article, keep it up.
With havin so much content and articles do you ever run into any issues of
plagorism or copyright violation? My website has a lot of exclusive content I’ve either created
myself or outsourced but it seems a lot of it is popping it up all over the web
without my authorization. Do you know any solutions to help prevent content from
being ripped off? I’d genuinely appreciate it. https://experiment.com/users/sseo23456
Hello very cool site!! Guy .. Beautiful .. Wonderful ..
I will bookmark your blog and take the feeds also?
I am happy to seek out numerous helpful information here within the
submit, we need work out more techniques in this regard, thanks for sharing.
. . . . .
Please let me know if you’re looking for a article writer for your blog.
You have some really great articles and I
think I would be a good asset. If you ever want to take some of the load
off, I’d absolutely love to write some content for your
blog in exchange for a link back to mine. Please send me an email if interested.
Kudos!
آموزشگاه آرایشگری مردانه – بهترین آموزشگاه
آرایش آقایان – کلاس گریم – آموزش متد
آرایش و پیرایش – آموزش پیرایش و
خدمات مو… آموزش متد آرایش و پیرایش – بهترین آموزشگاه آرایش آقایان – کلاس
گریم – آموزشگاه آرایشگری مردانه – آموزش پیرایش و خدمات مو…
در پایان دوره و کسب موفقیت در آزمون های ارزیابی سازمان آموزش فنی و حرفه ای کشور، هنرآموز
موفق به اخذ مدرک آرایشگری پیرایشگر
مردانه درجه ۱ می گردد. آموزشگاه آرایشگری مردانه
سرای نمونه با سابقه 20 ساله یکی از بهترین آموزشگاه
های آرایشگری مردانه در تهران است که مدرک بین المللی ارائه می دهد.
آموزشگاه تخصصی آرایشگری مردانه در فردیس کرج ، دوره های آرایشگری ما
برای افرادی که تجربه کافی در زمینه آرایشگری ندارند
و آمادگی لازم جهت ورود به بازار کار را در فردیس کرج کسب
کنید . بانک جامع مشاغل کتاب نقره ای (آگهی اینترنتی) با هدف آگاه سازی افراد در این زمینه
و به تبع آن تبلیغات و شناساندن انواع مشاغل و اصناف،
ایجاد شده است. آموزش حرفه ای
تعمیرات موبایل زیر نظر تعمیرکار و بصورت عملی در شرکت.
آموزش قالیبافی تابلو فرش در تمامی مناطق تهران -آموزش
قالیبافی تابلو فرش در آموزشگاه یا
در … عالی ترین،جامع ترین،حرفه ای ترین وساده ترین
سبک آموزشی را برای دانش پژوهان گرامی فراهم آورده ایم که در کوتاهترین زمان ممکن، قطعا ویقینا از شما یک
آرایشگری حرفه ای می سازیم. با کارشناسان آقای خاص تماس بگیرید و یا
ثبت نام آنلاین انجام دهید. آموزشگاه آموزشگاه آرایشگری در تهران مردانه جهان مو در زمینه پیرایش
مردانه، گریم داماد، گریم سینمایی و … …
جدای از اینکه در این آموزشگاه ها روش های جدید کوتاهی
مو تدریس میشود، در کنار آن نیز باید توجه داشته باشید …
این آموزشگاه با مهارت های فنی مناسب ، تکنیک های ارتباط موثر و مهارت های مدیریت مشتری خدمات خود
را ادائه می دهد . بعد از گذراندن دوره پیرایش مردانه درجه ۲ و شناخت و تسلط کامل به ابزارهای مختلف مربوط کوتاه کردن مو، برای ارتقاء سطح مهارت خود برای کوتاه کردن
موهای مردانه، می توانید وارد دوره درجه
۱ شوید. بهترین آموزشگاه آرایش آقایان –
آموزشگاه آرایش آقایان – کلاس گریم – آموزش پیرایش و خدمات مو –
آموزشگاه آرایشی – آموزشگاه
… شرکت در دوره های آموزشی طراحی
سایت و سئوی آموزشگاه رسمی فنی حرفه ای دارکوب علاوه بر اخذ مدرک رسمی فنی حرفه ای،
دارای مزیت بزرگ دیگری است زیرا این …
آموزش عکاسی در آموزشگاه عکاسی
پیشکسوتان در تجریش با مدرک معتبر سازمان آموزش فنی وحرفه ای و اساتید بسیار مجرب با طرح درسی کامل
و بروز مخصوص ورود به … علاقه مندان
به کسب اطلاعات بیشتر میتوانند به
سایت آموزشگاه آرایشگری مردانه به ادرسtvtcenter.com مراجعه کنند.
آموزش آرایشگری مردانه در کرج ، آموزش
حرفه ای آرایشگری مردانه در فردیس کرج ، آموزشگاه های ما طیف وسیعی از دوره های تخصصی مهیج را ارائه می
دهند که برای تکمیل مهارت های موجود شما طراحی
شده اند . آموزش حرفه ای آرایشگری مردانه در فردیس کرج افرادی را
که به دنبال دوره های تکنیک های تخصصی تر هستند ، قادر
می سازد تا آموزش های موجود خود را تکمیل کند .
آموزشگاه تخصصی و حرفه ای آرایشگری مردانه در فردیس ، با متخصصین مجرب و کارآزموده کلیه دروس تخصصی رشته آرایشگری را از مبتدی تا
حرفه ای برای علاقه مندان به این حرفه
برگزار می نماید . آموزش گریم داماد را
با متد روز دنیا از مبتدی تا پیشرفته به
کمک برجسته ترین اساتید کشور به هنرجویان در فردیس کرج ارائه می دهد .
آموزشگاه آرایشگری مردانه آقای خاص برگزارکننده بیش از 100 دوره آموزش آرایشگری مردانه در قم در سطوح مبتدی و پیشرفته میباشد.
هنرجویان بعد از گذراندن کلاس آرایشگری
میتوانند با دریافت مدرک رسمی از سازمان فنی و حرفه ای در مسیر
حرفهای شدن گام بردارند. پیتاژ یا خرد کردن مو که شیوه ای جدید از کوتاه کردن مو است.
با جواب به چند سوال ساده، « موتور جستجوی هوشمند کارپیشه» خودش رو تنظیم میکنه که
آگهیهای مناسب رو برات پیدا و ارسال
کنه. الکسا ایران فقط مرجعی برای جمعآوری و مقایسه رتبه الکسا است و مسئولیتی
در مورد سایتها و محتوای آنها ندارد.
از راه حل های درست و زمان استفاده
از آنها جهت پاک کردن لکه های حاصل از خرابکاری حیوانات
خانگی،ریختن نوشابه، شکلات، خون و …
آگاهی پیدا کنیم.تاحالا زیاد شده که فرشی را
همین دیروز از قالیشویی تر و
تمیز تحویل گرفتین و پهن کردین
ولی لکه ها مثل اهن ربا جذب ذقیقا همون فرش می شوند ،
لکه هایی که میتونن خیلی راحت توسط حیوانات خانگی ، ریختن
مایعات مثل نوشابه و… فرش ها جز وسائل آسیب پذیر
منزل هستند و نیازبه مراقبت دارند.
مراقب نکردن از آن ها یا استفاده نادرست باعث
آسیب دیدگی، پوسیدگی و غیره می شود.
بعضی از افراد فکر می کنند، همینکه فرش دچار چنین آسیب هایی شد باید آن را عوض کرد، ولی امروزه با دانش رفوگری
فرش می توان، این خرابی های فرش را ترمیم
کرد. مهارت پیش نیاز ثبت
نام در این دوره، اخذ گواهینامه مهارت پیرایش مردانه درجه ۲ و دارا بودن حداقل مدرک تحصیلی
سیکل (پایان دوره راهنمایی) می باشد.
آموزشگاه شهریار ، زیر نظر سازمان فنی و حرفه ای کشور، وابسته به وزارت تعاون، کار و رفاه
اجتماعی، برگزار میکند… شهرت ما ارائه
آموزش حرفه ای آرایشگری و هدایت شما برای رسیدن به کسب و کار ایده آل است.
5 تا از بهترین آموزشگاه های برگزار کننده دوره پیرایشگری مردانه…
آموزشگاه تخصصی آرایشی مردانه در فردیس ، اگر که خیلی وقت است به دنبال یک آموزشگاه تخصصی خوب
و عالی در فردیس هستید و پیدا نمی کنید با ما همراه شوید .
هزینه تهیه ابزارهای ذکر شده به عهده متقاضی شرکت در دوره می باشد و مربی آموزشگاه خود را
موظف می داند هنرآموز را در تهیه اقلام
مناسب و با کیفیت، مشاوره و راهنمایی نماید.
لازم به ذکر است در طی این دوره، برخی از تجهیزات و مواد مصرفی اعم از
سشوار، اتوی مو، دستگاه بخور، حالت دهنده،
فیکساتور، ماسک های پاک کنندهپوستو … از طرف آموزشگاه در اختیار هنرآموز قرار خواهد گرفت.
اخذ مدرک دیپلم برای دانش آموزان و دیپلم ردی ها در رشته مورد نظر خود- برگزاری و کرایه کلاس در مرکز تخصصی
با ظرفیت 10الی … آموزش تعمیرات ایسیو ecu از جذابترین و
پردرامدترین آموزش ها در حوزه خودرو است.
ایسیو یا کامپیوتر خودرو
یکی بخش مهم خودرو می باشد که وظیفه کنترل و …
قدیمیترین وسایل اصلاح برنزیِ کشفشده، مربوط به ۳۵۰۰
سال پیش از میلاد مسیح در مصر باستان
است. با شناخت صحیح ابزار آرایشگری، تکنیک ها و متریال مناسب،
می توانید به افزایش کیفیت خدمت رسانی و بهبود سطح
رضایت مندی مشتریان خود دست یابید.
مدل موهای شیک برای بچه هاو افرادی
که موهای نازک و سبک هستند مناسب است .
درب و پنجره UPVC از پروفیل هایی از جنس UPVC ساخته می شوند.
این نوع از درب و پنجره ها با مواد وینیلی بسیار سخت عرضه می گردند
و ویژگی های مفیدی دارند. از جمله آنکه عایق
سر و صدا، و سرما و گرما می باشند و در برابر رطوبت و آب باران مقاوم بوده، وغیرقابل نفوذ در برابر آلودگی هستند، به علاوه صرفه جویی در انرژی داشته و ایمن می باشند.
قیچی آرایشگری، قیچی اره ای،
برس تخت، برس گرد، پیشبند، روپوش سفید، آبپاش، شانه
کار، دسته تیغ، تیغ پیتاژ. در این دوره، هنرآموز مهارت خرد
کردن مو (پیتاژ) با ابزار های مختلف من جمله قیچی اره ای، تیغ، ماشین و نیز شناخت ابزارها، مواد مصرفی و … را فرا خواهد گرفت.
یکی از راهکارهای پیشنهادی برای کاهش
سرقت، از بین بردن فرصت های مناسب برای سارقین است.
به عبارتی اتخاذ روش هایی برای پیشگیری از
سرقت که اساسی ترین مولفه اهمیت نصب دوربین مدار بسته است.
به حرفه ای بیاندیشید که با کمترین هزینه ، بالاترین درآمد را کسب کنید.
سایه زدن دور مو، که طی آن موهای دور
سر سفید(صفر) شده و کم کم با حرکت به سمت بالا بلند تر میشود.
این دوره پیش نیاز ندارد، حداقل میزان تحصیلات متقاضی،
پایان دوره راهنمایی بوده و بدون حتی کوچکترین سابقه
کار و آشنایی با حرفه آرایش و پیرایش مردانه، می توانید برای شرکت در آن نام نویسی کرده و مراحل
آموزش را از مبتدی و قدم به قدم پشت سر بگذارید.
بعد از گذراندن دوره درجه 2، در
صورت تمایل می توانید وارد دوره پیرایش مردانه درجه 1 شده و اصول خرد کردن مو و کوتاه کردن و حالت دادن مو به مدل های
روز (ژورنال شناسی) را فرا بگیرید. دوره پیرایش مردانه
درجه ۱ برای آن دسته از عزیزانی تدوین شده که با تکنیک
ها و اصول پایه هیرکات آشنا بوده و توانایی کوتاه کردن
مدل های کلاسیک مردانه را دارا باشند.
دوره تعمیرات تلفن همراه با ارائه مدرک بین المللی از سازمان فنی
و حرفه … همچنین این آکادمی فرصتی برای
ورود شما هنرجوی عزیز به بازار کار و نیز آموزش های مفیدی را ارائه می دهد .
آموزش حرفه ای آرایشگری مردانه در فردیس کرج رشته های مختلفی را
از سطح پایه و تا مدرک دیپلم در موضوعات
تخصصی ارائه می دهد . آموزش حرفه ای آرایشگری مردانه در فردیس کرج به شما این امکان را می دهد که از
دوره های اختصاصی پوست ، مو و آرایش بر اساس نیازهای فردی آموزش
ببینید . کلمه ای که مطمئنا بارها به گوشتان خورده است ولی
شاید تا الان در مورد آن اطلاعاتی نداشتید
یا جدی نمی گرفتید. در این بخش قصد داریم تا در خصوص رفوگری
فرش و چگونگی انجام آن صحبت
کنیم. با توجه به تعداد زیاد آگهی در ایستگاه،
لطفا در کسب اعتبار و اعتماد آگهی دهنده، دقت کافی
مبذول دارید. جهت شروع درج آگهی،
ابتدا روی لینک ثبت نام کلیک کنید و پس از پرکردن فرم ثبت نام آگهی خود را ثبت کنید.
اگر میخواهید تعمیرکار شوید و موبایل را براحتی تعمیر کنید حتما یک جلسه
با من … تعمیر دی وی آر DVR و دوربین را
در مرکز تعمیرات حرفه ای شوید.
پس از ثبت نام در دوره پیرایش مردانه درجه 1، زمان دقیق شروع کلاس متعاقبا به متقاضی اعلام می گردد.
بهترین آموزشگاههای آرایشگری مردانه
تهران
I pay a visit every day a few web sites and blogs to read articles, however this blog gives quality based content.
You’re so interesting! I don’t suppose I’ve read anything like this before.
So great to find someone with some unique thoughts on this topic.
Really.. many thanks for starting this up. This website is one thing that’s needed on the web, someone with some
originality!
Very quickly this web site will be famous among all blog visitors, due to it’s fastidious content
Astonishingly user pleasant site. Astounding information available on couple of
clicks on. https://za.zalo.me/v3/verifyv2/pc?token=OcNsmjfpL0XY2F3BtHzNRs4A-hhQ5q5sPXtbk3O&continue=healthnwomen.com
Nice blog here! Also your site loads up very fast! What web host are you using?
Can I get your affiliate link to your host?
I wish my web site loaded up as quickly as yours lol
Way cool! Some extremely valid points! I appreciate you writing this post plus the rest
of the site is also really good.
What’s up friends, its enormous article concerning
cultureand completely defined, keep it up all the time.
Feel free to surf to my blog post; idn togel
Superb blog! Do you have any hints for aspiring writers? I’m
hoping to start my own website soon but I’m a little lost on everything.
Would you suggest starting with a free platform like WordPress or go for a paid option? There
are so many choices out there that I’m totally overwhelmed ..
Any ideas? Appreciate it!
Also visit my homepage :: LOTTOVIP
That’s an awesome point
Hi, just wanted to say, I enjoyed this article.
It was helpful. Keep on posting!
Maintain the great work and generating the crowd!
http://62.75.137.134/profile.php?userid=133
Hello it’s me, I am also visiting this website daily, this site is actually fastidious
and the users are in fact sharing pleasant thoughts.
Thank you for the auspicious writeup. It in fact
was a amusement account it. Look advanced to
more added agreeable from you! By the way, how could we communicate?
Simply just desired to tell you I am just delighted I stumbled on the website!
http://47.94.19.27/home.php?mod=space&uid=74559
Very soon this site will be famous amid all blogging
people, due to it’s pleasant content
You’re a very useful web site; couldn’t make it without ya!
http://siheluntan.thinkcore.cn/home.php?mod=space&uid=48193
Hmm it appears like your site ate my first comment (it was super long) so I
guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I’m still new to everything.
Do you have any suggestions for beginner blog writers?
I’d really appreciate it.
Having read this I believed it was really informative.
I appreciate you spending some time and effort to put this article together.
I once again find myself spending way too much time both reading and leaving comments.
But so what, it was still worth it!
I’m impressed, I have to admit. Rarely do I encounter
a blog that’s equally educative and entertaining, and let me tell
you, you have hit the nail on the head. The problem is an issue that not enough men and women are speaking intelligently about.
I am very happy I came across this during my hunt for something regarding this.
Very good post! We are linking to this particularly great
article on our website. Keep up the good writing.
It’s perfect time to make some plans for the future and it is time to be happy.
I have read this post and if I could I wish to suggest you few interesting things
or suggestions. Maybe you can write next articles referring to
this article. I wish to read more things
about it!
Hi there would you mind sharing which blog platform you’re working with?
I’m going to start my own blog in the near future but I’m having a difficult time deciding between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design and style seems different then most blogs and I’m looking for something unique.
P.S My apologies for getting off-topic but I had to ask!
خانمها به دلایل مختلفی کاشت ناخن انجام میدهند؛ برخی صرفا برای زیبایی و برخی دیگر به دلیل مشکلات ناخنهایشان و برای پوشاندن ناخنهایی که به گفته
خودشان رنگ و روی زیبایی ندارد انواع کاشت را
تجربه میکنند. مهم نیست به چه دلیل و با چه انگیزهای کاشت ناخن را انتخاب میکنید؛ مهم این است که با واقعیتها و عوارض کاشت ناخن
آشنا شوید. در این مقاله، انواع کاشت، مزیتها و عوارض آنها را مرور میکنیم.
کدام روش کاشت ناخن بهتر است؟
خانمها به دلایل مختلفی کاشت ناخن انجام میدهند؛ برخی صرفا برای زیبایی و
برخی دیگر به دلیل مشکلات ناخنهایشان و برای
پوشاندن ناخنهایی که به گفته خودشان
رنگ و روی زیبایی ندارد انواع کاشت را تجربه میکنند.
مهم نیست به چه دلیل و با چه انگیزهای کاشت ناخن
را انتخاب میکنید؛ مهم این است که با واقعیتها و عوارض کاشت ناخن آشنا شوید.
در ادامه انواع کاشت ناخن طبیعی
شامل کاشت ناخن با پودر، کاشت ناخن با ژل، و کاشت ناخن با قالب را تشریح و مقایسه میکنیم.
کاشت قالب
در این نوع از کاشت مواد را داخل قالب ناخن مصنوعی میگذارند تا شکل
آن را به خود بگیرد. ابتدا مواد ضد قارچ را روی ناخن میزنند و
بعد قالب را روی ناخن فشار میدهند تا مواد روی ناخن
خشک شود بعد از چند دقیقه ناخن مصنوعی را برمیدارند.
در این نوع کاشت دیگر سوهانکشی نمیشود و از چسب ناخن هم
استفاده نمیشود این نوع کاشت راحتترین نوع کاشت و در عین حال بیکیفیتترین است.
در این نوع کاشت به دلیل اینکه عمل سوهانکشی انجام
نمیشود بعد از مدت کوتاهی بهاصطلاح
ناخن هوا میگیرد و جمع شدن هوا
زیر ناخن کاشت یکی از مهمترین
دلایل برای به وجود آمدن قارچ است.
در این نوع کاشت باید مراقب بود تا ناخنها
کمترین تماس را با آب داشته باشند.
کاشت قالب به چه کسانی توصیه میشود؟
معمولا کاشت قالب به افرادی که زمان
کمتری برای رسیدگی به ناخنهایشان دارند توصیه میشود.
ازآنجا که در این نوع کاشت باید
کمترین تماس را با آب داشت، خانهدارها از انتخاب این نوع کاشت
پرهیز کنند. این نوع کاشت زمان کمتری نیاز دارد، به سوهانکشی نیاز
ندارد و نظم بسیار خوبی بین کاشت
۱۰ انگشت ایجاد میکند.
کاشت قالب برای چه کسانی مناسب نیست!
این نوع کاشت به افرادی که ناخنهای پراکنده و یک شکل ندارند اصلا توصیه نمیشود.
به دلیل قالبی بودن این نوع کاشت باید تمام ناخنهای دو دست یک شکل باشند در غیر اینصورت کاشت به شکل
مرتبی انجام نخواهد شد. به دلیل ضخیم
بودن کاشت، کار از حالت طبیعی خود خارج میشود.
این نوع کاشت را میتوان روی انگشتهای استاندارد کار کرد.
نکته مهم این است که احتمال هوا گرفتن
این کاشت بیشتر است. ماندگاری
کمتری دارد و در مقایسه با روشهای دیگر مواد بیشتر مصرف میشود.
کاشت ناخن با پودر
در کاشت اولیه تیپ یا همان ناخن مصنوعی از نیمه ناخن با
چسب ناخن چسبانده میشود و تا اندازه
دلخواه کوتاه میشود. روی
ناخن مواد ضد قارچ را میزنند، بعد پودر کاشت که همان مواد دندانپزشکی است روی ناخن زده و در امتداد قالب کار میکنند و بعد از آن با سوهان برقی به ناخن شکل
میدهند. بهترین نوع کاشت همین نوع پودری است.
برای این نوع کاشت زمانی بیشتر و سوهانکشی دقیق و حرفهای جهت یکسان بودن ۱۰ انگشت نیاز است.
Have you ever considered writing an ebook or guest authoring on other websites?
I have a blog based on the same subjects you discuss and would really like to have you share some stories/information. I know my
visitors would enjoy your work. If you’re even remotely interested, feel free to send
me an email.
Thanks a bunch! It is definitely an outstanding webpage!
http://pengb.work/home.php?mod=space&uid=673068
Thanks, this site is very practical.
http://idv.neteasegamer.com/home.php?mod=space&uid=18100
I read this article fully on the topic of the comparison of most
recent and preceding technologies, it’s awesome article.
Extremely individual friendly site. Enormous info available
on couple of gos to.
http://xn--b1afihfocf9aeuz.xn--p1ai/index.php?subaction=userinfo&user=naboxi
We stumbled over here different web address
and thought I might as well check things out. I like what I see so i am just following
you. Look forward to going over your web page for a second time.
Have you ever considered about including a little bit more than just your articles?
I mean, what you say is important and everything. Nevertheless just imagine if you added some great graphics or video clips to
give your posts more, “pop”! Your content is excellent
but with images and video clips, this website could certainly be one of the very
best in its field. Awesome blog!
Fork this is to verify the validity of her transaction the Bitcoin get sent to these addresses.
Funds are protected by digital signatures
corresponding to the sending addresses permitting
all customers. Funds solely accepting funds from valid private keys which authorize spending are stolen. Business professionals have ready simply reveal
the personal key can be used to send. The Jpmorgan analysts have less trustworthy than others and a few of you feel.
The recent hacking of Ashley Madison and i now have your Fb web page in addition to price.
Dogecoin Coinye now the 4chan crowd and Reddit’s rowdiest might do a better method to mainstream cryptocurrency.
Interestingly the CNBC present Scaramucci also fielded
questions on the price got in the course of the time the cryptocurrency.
Safe their networks use a cryptocurrency exchange died without relaying a lucrative investment.
Speaking Bitcoin faucets places the place an possibility on your retirement it doesn’t become.
The layering Trader locations multiple cryptocurrencies
because it is unnecessary for US and our customers.
Coinbase’s chief policy officer Faryar Shirzad
said he is against buying and trading cryptocurrencies.
Thanks extremely handy. Will share website with my buddies.
http://begabat.com/index.php?qa=user&qa_1=tymihuqu
I read this piece of writing completely concerning the
resemblance of hottest and previous technologies, it’s awesome article.
Keep on working, great job!
Here is my website … daftar slot online
Pretty! This has been an extremely wonderful post.
Thank you for supplying this info.
Wow! At last I got a weblog from where I be able to truly take
valuable data regarding my study and knowledge.
I will right away grab your rss feed as I can not find your email subscription link or newsletter service.
Do you’ve any? Please let me realize in order that I could
subscribe. Thanks.
medication for ed
My spouse and I stumbled over here from a different web page and thought I might check
things out. I like what I see so now i’m following you.
Look forward to finding out about your web page for a second time.
This is very interesting, You’re a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your great post.
Also, I’ve shared your website in my social networks!
Thank you a bunch for sharing this with all of us you really
recognize what you’re speaking about! Bookmarked. Please also visit
my web site =). We may have a link change contract between us
I’m curious to find out what blog platform you have been working with?
I’m experiencing some small security issues with my latest blog and I’d
like to find something more safe. Do you have any suggestions?
Appreciate the recommendation. Will try it out.
Hi to every one, the contents existing at this web page are in fact awesome for people knowledge,
well, keep up the nice work fellows.
Its like you learn my mind! You appear to grasp a lot about this, like you wrote the
book in it or something. I think that you just can do with a few % to power the
message home a little bit, but instead of that, that
is magnificent blog. A fantastic read. I’ll definitely
be back.
This includes the likes of the Federal Reserve controls the Bitcoin economic system rising.
Has reworked it is steadily growing demand Bitcoin isn’t designed to be useful resource-intensive.
Craig Wright an unlimited potential buyers have predetermined to hold on to their Bitcoin. The potential to reach by design Bitcoin supply is restricted by its software to trace your portfolio.
Nevertheless seeing as Bitcoin is currently consolidating
in a slender range of BTC. Lightweight clients vary from self-proclaimed plebs who stack the
smallest quantity of their money. These works go into much
more safety of your cash in your wallet within the day ahead.
The WEF tweeted concerning the older the story the extra possible
it is stored only on non-public exchanges.
In these peer-to-peer exchanges by individuals known as Bitcoin is at present the most outstanding worldwide
group. Settle for bitcoins exchanges for 800 which might now be
value sufficient sooner or later. 1-hour 4-hour and sometimes
co-blogger Robin Hanson assigned a subjective
likelihood of no less than one Bitcoin mining. Inflation in the Mesopotamians used clay tablets as receipts of trade for Bitcoin. Pompliano is a leading change
by trading or investing it in a transaction is legitimate if.
Individuals also anticipate transaction fees privacy and anonymity than traditional fee programs like a financial institution or one other.
Hi there! I understand this is somewhat off-topic however I had to
ask. Does managing a well-established website such as yours require a lot of work?
I’m completely new to operating a blog but I do write in my journal everyday.
I’d like to start a blog so I can share my experience and views online.
Please let me know if you have any kind of recommendations or tips for brand new aspiring
bloggers. Appreciate it!
Thank you for sharing your info. I truly appreciate your
efforts and I will be waiting for your next post thanks
once again.
When someone writes an paragraph he/she keeps the image of a user in his/her mind that how a user can know it.
Therefore that’s why this piece of writing
is outstdanding. Thanks!
Asking questions are really nice thing if you are not understanding anything completely, except this post provides nice understanding yet.
I do accept as true with all of the concepts you have presented for
your post. They are very convincing and can definitely work.
Nonetheless, the posts are too short for starters. Could you please lengthen them a little from subsequent time?
Thanks for the post.
Also visit my web site … slot terpercaya
Excellent post! We are linking to this particularly
great article on our site. Keep up the great writing.
I have read several just right stuff here. Certainly value bookmarking for revisiting.
I surprise how a lot effort you put to make such a fantastic
informative site.
Oh my goodness! Amazing article dude! Thank you, However I
am going through issues with your RSS. I don’t understand why I cannot subscribe
to it. Is there anybody else having the same RSS
issues? Anyone who knows the answer will you kindly respond?
Thanx!!
I am sure this post has touched all the internet visitors, its really really fastidious post on building up new website.
It is not my first time to pay a visit this site, i am browsing this website dailly and take pleasant information from here
daily.
I benefit from reading your websites. Kudos!
http://qa.pandora-2.com/index.php?qa=user&qa_1=dejohyt
I’m truly enjoying the design and layout of your website.
It’s a very easy on the eyes which makes it much
more enjoyable for me to come here and visit more often.
Did you hire out a designer to create your theme?
Excellent work!
With havin so much written content do you ever run into any problems of plagorism or
copyright violation? My blog has a lot of completely unique content I’ve
either authored myself or outsourced but it looks like a lot of it is
popping it up all over the internet without my authorization. Do you know any
methods to help prevent content from being stolen? I’d genuinely appreciate it.
Hello, after reading this remarkable paragraph i am too
happy to share my familiarity here with friends.
all the time i used to read smaller posts that as well
clear their motive, and that is also happening with this post which I
am reading at this time.
Hi there, I enjoy reading all of your post. I wanted to write a little comment to support you.
I am really enjoying the theme/design of your weblog. Do you ever run into any browser compatibility problems?
A handful of my blog readers have complained about my blog not working correctly in Explorer but looks
great in Opera. Do you have any tips to help fix this problem?
Usually I do not read article on blogs, however I wish
to say that this write-up very compelled me to check out and do so!
Your writing style has been surprised me. Thanks, very nice article.
Oh my goodness! Impressive article dude! Many thanks, However I am experiencing
issues with your RSS. I don’t understand why I cannot subscribe to
it. Is there anybody getting the same RSS issues?
Anybody who knows the answer can you kindly respond?
Thanks!!
Hey There. I found your weblog the use of msn. This is an extremely smartly written article.
I will be sure to bookmark it and come back to read more of your useful information. Thank you for the post.
I’ll certainly return.
Pretty nice post. I just stumbled upon your weblog and
wanted to say that I have truly enjoyed browsing your blog posts.
After all I’ll be subscribing to your feed and I hope you write again soon!
Today, I went to the beachfront with my kids. I found a sea shell and gave it
to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.”
She placed the shell to her ear and screamed. There
was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is
totally off topic but I had to tell someone!
Pretty! This has been a really wonderful post. Thank you for providing this information.
Link exchange is nothing else but it is only placing the other person’s
blog link on your page at suitable place and other person will also do similar for you.
I do not know whether it’s just me or if perhaps everybody else experiencing problems with your website.
It appears as if some of the text within your content are running off the screen.
Can someone else please provide feedback and let me know if this is happening to them as
well? This might be a problem with my internet browser because I’ve had this happen before.
Kudos
Hey there! Do you use Twitter? I’d like to follow you if that would be okay.
I’m definitely enjoying your blog and look forward to new posts.
I am regular reader, how are you everybody? This piece of writing
posted at this site is actually nice.
This post will assist the internet people
for building up new weblog or even a weblog from start to end.
I have been surfing online more than 3 hours lately, yet I never found any
interesting article like yours. It’s lovely price enough for me.
In my view, if all web owners and bloggers made good content material as you did,
the internet will probably be a lot more helpful than ever before.
I am really impressed with your writing skills as well
as with the layout on your blog. Is this a paid theme or did you
modify it yourself? Either way keep up the nice quality writing, it is rare to see a nice
blog like this one these days.
For newest news you have to visit internet and on web I found this
web page as a finest site for most recent updates.
This article will assist the internet visitors for
setting up new weblog or even a blog from start to end.
It’s perfect time to make some plans for the future and it is time to be happy.
I’ve read this post and if I could I wish to suggest you few interesting things or advice.
Maybe you could write next articles referring to this article.
I desire to read more things about it!
My partner and I stumbled over here different web page
and thought I may as well check things out. I like what I see so now i am following you.
Look forward to looking over your web page yet again.
I enjoy reading through a post that can make
people think. Also, thanks for permitting me to comment!
Thanks on your marvelous posting! I actually enjoyed reading
it, you could be a great author.I will make certain to bookmark your blog and will eventually come back from now on. I want to encourage
continue your great writing, have a nice morning!
Keep on writing, great job!
This piece of writing is truly a nice one it helps new the web visitors,
who are wishing for blogging.
Hey there this is somewhat of off topic but I was wondering if
blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding know-how so I wanted to get guidance from someone with experience.
Any help would be greatly appreciated!
Great delivery. Outstanding arguments. Keep up the amazing work.
my blog :: Credit Card Processing Agent
Unquestionably consider that which you stated.
Your favourite reason appeared to be on the web the simplest thing to be mindful of.
I say to you, I definitely get annoyed whilst people think about worries that they just
do not know about. You managed to hit the nail
upon the top as well as defined out the entire thing with no need side effect ,
folks could take a signal. Will probably be back
to get more. Thanks
What’s Taking place i’m new to this, I stumbled upon this I’ve
discovered It absolutely helpful and it has aided me out loads.
I’m hoping to give a contribution & assist other customers like its helped
me. Great job.
When I initially commented I clicked the “Notify me when new comments are added” checkbox and now each time a comment
is added I get three emails with the same comment. Is there any way
you can remove me from that service? Thanks!
I’ll right away grasp your rss as I can not to find your email subscription hyperlink or e-newsletter service.
Do you’ve any? Kindly permit me know so that I may just subscribe.
Thanks.
What i do not realize is in reality how you’re not really a lot more neatly-appreciated than you may be right now.
You are very intelligent. You recognize therefore considerably when it comes to this topic, made me
personally imagine it from a lot of various angles.
Its like men and women are not fascinated until it’s something to accomplish
with Girl gaga! Your personal stuffs nice. At
all times take care of it up!
If you are going for most excellent contents like me, just pay a visit this website daily as it provides feature contents, thanks
Visit my homepage … Merchant Referral Program
I love your blog.. very nice colors & theme. Did you make this website yourself or did you hire someone to do it for you?
Plz answer back as I’m looking to design my own blog
and would like to know where u got this from.
thanks
Keep this going please, great job!
Hello to all, the contents existing at this web page
are actually awesome for people experience, well, keep up the nice work fellows.
I blog often and I really thank you for your content.
The article has really peaked my interest.
I will book mark your site and keep checking for new details about once a week.
I opted in for your RSS feed too.
Hi! I’ve been following your weblog for some time now and finally got the bravery to go ahead and give you
a shout out from Porter Texas! Just wanted to say keep up the great job!
Hello everyone, it’s my first pay a quick visit at this
site, and paragraph is really fruitful in support of
me, keep up posting these posts.
Hi, its good piece of writing on the topic of media print,
we all be aware of media is a fantastic source of facts.
Pretty element of content. I simply stumbled upon your site and in accession capital to claim
that I acquire in fact loved account your weblog posts.
Anyway I’ll be subscribing on your augment or even I fulfillment you get right
of entry to persistently quickly.
Asking questions are truly fastidious thing if you
are not understanding anything totally, except this
article presents nice understanding yet.
Can I just say what a relief to uncover someone who truly understands what they are
talking about over the internet. You definitely know how to
bring a problem to light and make it important. A lot more people should read this and understand this side of the story.
I can’t believe you are not more popular because you definitely have the
gift.
Great blog here! Also your web site loads up very fast!
What host are you the use of? Can I am getting your
affiliate hyperlink for your host? I desire my website loaded up as quickly as yours lol
Thanks on your marvelous posting! I genuinely enjoyed reading it,
you happen to be a great author. I will make certain to
bookmark your blog and may come back in the foreseeable future.
I want to encourage you continue your great writing, have a nice evening!
Great web site you have got here.. It’s hard to find high quality writing
like yours nowadays. I seriously appreciate people like you!
Take care!!
Wonderful beat ! I wish to apprentice while
you amend your site, how could i subscribe
for a blog site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided bright clear idea
Hi, Neat post. There’s a problem together with your web site in internet
explorer, could test this? IE nonetheless is the market leader and a big component
of other people will omit your great writing due to this problem.
Every weekend i used to visit this website, for the reason that i wish for enjoyment,
for the reason that this this web site conations really nice funny information too.
Yesterday, while I was at work, my cousin stole my iphone and
tested to see if it can survive a thirty foot drop,
just so she can be a youtube sensation. My apple ipad is now broken and she has 83
views. I know this is entirely off topic but I had to share
it with someone!
evden eve nakliyat sektöründe güvenilir hizmetin adresinden ev, ofis vb eşyalarınızı
sigortalı olarak taşımak için profilimdeki linkten iletişime
geçebilirsiniz.
Hello just wanted to give you a quick heads up
and let you know a few of the pictures aren’t loading properly.
I’m not sure why but I think its a linking issue. I’ve
tried it in two different internet browsers and both show the same outcome.
Hello there, I discovered your website via Google even as looking for a related matter, your web
site came up, it looks great. I have bookmarked it in my google bookmarks.
Hi there, simply turned into alert to your weblog thru Google, and located that it is really informative.
I’m gonna be careful for brussels. I will be grateful if you continue
this in future. Many folks might be benefited out of your writing.
Cheers!
Yes! Finally something about Best Cosmetic Clinic
in Gurgaon.
As the admin of this web page is working, no question very quickly it will be renowned, due to its quality contents.
Hi there to all, the contents existing at this web site are really amazing for people
experience, well, keep up the nice work fellows.
Hi, I read your blog regularly. Your humoristic
style is witty, keep doing wnat you’re doing!
Way cool! Some extremely valid points! I appreciate you penning this article and also the rest of the website is very good.
در این مقاله قصد داریم به بررسی زبان کشورهای مختلف
دنیا بپردازیم. بیش از ۷۱۰۰ زبان در جهان وجود دارد و در هر چهارده روز یک زبان تبدیل به زبان مرده میشود.
از دلایل این موضوع میتوان گرایش مردم به شهرهای بزرگ و همچنین فوت افراد بومیهای آن زبان اشاره
کرد. دانستن زبان کشورهای مختلف میتواند جنبه اطلاعات عمومی داشته باشد یا صرفا برای یادگیری
باشد. با این وجود اغلب زمانی که تمایل به دانستن زبان یک کشور داریم،
هدف مهاجرت به آن کشور و یادگیری
زبان دوم برای مهاجرت است.
به همین خاطر در این مقاله ابتدا زبان کشورهای مختلف را معرفی میکنیم.
سپس کلاسها و آموزشگاههای زبان را در شهرهای
مختلف به شما معرفی میکنیم، تا چنانچه قصد مهاجرت دارید، بتوانید بهترین انتخاب را برای آموزش و
یادگیری زبان داشته باشید.
مهاجرت و یادگیری زبان کشور مقصد
امروزه، با توجه به شرایط نامطلوب زندگی در ایران و رفاه و کیفیت
بالای زندگی، مراکز آموزشی و شرایط تحصیل عالی، وضعیت اشتغال مناسب در
کشورهای دیگر، بسیاری از افراد تصمیم به مهاجرت
میگیرند. مقصد مهاجرت افراد بسته به
اهداف، بودجه و شرایط دیگر با هم
تفاوت دارد، با این حال برخی از
کشورها مثل کانادا، آلمان، استرالیا، انگلستان، ایتالیا،
آمریکا، فرانسه،
With havin so much content do you ever run into any problems of plagorism
or copyright violation? My blog has a lot of unique content I’ve
either authored myself or outsourced but it looks like a
lot of it is popping it up all over the web without my authorization. Do you know any ways to help stop content from being ripped off?
I’d really appreciate it.
I love what you guys are up too. This kind of clever work and coverage!
Keep up the great works guys I’ve incorporated you guys
to blogroll.
That is really interesting, You are an overly skilled blogger.
I have joined your feed and stay up for in the hunt for more of
your magnificent post. Also, I have shared your
website in my social networks
Spot on with this write-up, I really believe that this website needs a
lot more attention. I’ll probably be back again to read through more, thanks for the info!
Hi! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard
on. Any tips?
Hey this is kind of of off topic but I was wondering if blogs use
WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding knowledge so I wanted to get advice from someone with experience.
Any help would be enormously appreciated!
I’m not sure where you’re getting your information, but great topic.
I needs to spend some time learning much more or
understanding more. Thanks for excellent information I was looking for this info for
my mission.
در این مقاله قصد داریم به معرفی روش ها و تکنیک های مختلف آموزش زبان انگلیسی در خانه بپردازیم.
گرچه رفتن به کلاس زبان حس و حال خوبی دارد و بسیاری از افراد ترجیح میدهند زبان
انگلیسی را با شرکت در کلاس زبان آموزشگاه های مختلف فرا بگیرند،
با این حال ممکن است برخی افراد فرصت رفتن به کلاس زبان را نداشته باشند.
حتی ممکن است شما فرصت داشته باشید، اما راحتی خانه را ترجیح دهید یا دلتان نخواهد برای یادگیری زبان زیاد هزینه کنید.
چالشی که پیش میآید این است که چطور میتوان بدون مدرس پیشرفت کرد؟
پس چه کسی اشتباهاتمان را اصلاح کند؟ این نگرانی ها
بهجا هستند و شاید موارد دیگری هم
باشند. مثلا ممکن است نگران تلفظ
صحیح کلمات باشید. در واقع، شاید اصلا ندانید که از
کجا باید شروع کنید. در حقیقت یادگیری زبان لزوما به معنای
نشستن پای کتاب نیست و منابع زیادی وجود دارند که می توانند
به شما کمک کنند که در مسیر درستی قدم بردارید.
With havin so much content do you ever run into any issues of plagorism or copyright
infringement? My blog has a lot of exclusive content I’ve either
created myself or outsourced but it looks like a lot of it is popping
it up all over the internet without my authorization. Do you
know any techniques to help prevent content from being
stolen? I’d definitely appreciate it.
Right away I am going away to do my breakfast, later than having my breakfast coming over again to read
other news.
I constantly spent my half an hour to read this web site’s posts all the time along with a cup of coffee.
در این مقاله میخواهیم به موضوع مکالمه زبان بپردازیم.
تا انتها همراه ما باشید. همه ما دوست داریم بدانیم به چه روش هایی میتوان به زبان انگلیسی صحبت کرد.
برای تقویت مکالمه زبان انگلیسی، بهترین
روش صحبت کردن با هم صحبت انگلیسی
زبان است، اما برای بعضی از ما
یک مانع بزرگ وجود دارد و آن نداشتن
فردی است که به زبان انگلیسی با ما
مکالکه کند. بسیاری از افراد شرایط آن را ندارند.
پس راه حل چیست؟ در ادامه به بیان تکنیک
هایی برای یادگیری مکالمه زبان میپردازیم.
چرا مکالمه به زبان انگلیسی سخت است؟
خیلی از اوقات ما بسیاری از کلمات را بلدیم و بارها تکرار کردیم، با
اصول گرامری زبان آشنایی داریم، حتی اعتماد به نفس
خوبی داریم، با این حال نمیتوانیم به انگلیسی
صحبت کنیم. احتمالا در ذهن خود میدانید که چه
حرفی برای گفتن دارید، اما لغات مورد نظر در دهانتان نمیچرخد.
در ادامه بررسی میکنیم که چرا این مهارتِ به ظاهر آسان، اینقدر مشکل ایجاد میکند؟ و سپس تکنیک هایی برای یادگیری مکالمه زبان ارائه میدهیم.
Hello very nice website!! Man .. Excellent ..
Wonderful .. I’ll bookmark your web site and take the feeds additionally?
I am happy to find numerous useful information right here in the publish, we’d like work out extra techniques
on this regard, thank you for sharing. . . . . .
I read this paragraph fully on the topic of the difference of hottest and preceding technologies, it’s awesome article.
Good article. I will be going through many of these issues as well..
This article is in fact a good one it assists new the weeb peοple, who aгe wishing for blogging.
Thank you for the auspicious writeup. It actually was a amusement account it.
Glance complicated to more delivered agreeable from you!
However, how could we be in contact?
This website truly has all the information I wanted concerning this subject and didn’t know who to ask.
What i don’t understood is if truth be told how you’re no longer really much more
well-appreciated than you may be now. You are very intelligent.
You know thus significantly in the case of this topic, made me
for my part imagine it from a lot of varied angles. Its like men and women aren’t
fascinated unless it’s one thing to do with Lady gaga!
Your own stuffs great. All the time take care of it up!
https://www.raceny.com/smf2/index.php?thememode=full;redirect=http://185.217.94.31/wp-sitemap.xml
I blog quite often and I truly thank you for your information. This article has truly peaked my
interest. I’m going to take a note of your blog and keep checking for new information about once a week.
I opted in for your Feed too.
Hi there to all, how is the whole thing, I think every
one is getting more from this web site, and your views
are pleasant for new viewers.
You have among the finest web-sites. https://icoholder.com/en/v2/ico/ico-redirect/22357?to=https://profascinated.com
Keep on writing, great job!
Hi there! Someone in my Facebook group shared this site with us so I came to take a look.
I’m definitely loving the information. I’m bookmarking and will be
tweeting this to my followers! Fantastic blog and fantastic
design.
http://xn--80ajaublc1bet.xn--c1ac3aaj1g.xn--p1ai/jump.php?target=https://185.217.94.31%2Fwp-sitemap.xml
Whhat i do not realize is if truth be told how you’re no longer actually a lot more neatly-liked than you might be right now.
You’re so intelligent. Youu recognize therefore
considerably when it comes to this topic, made me individually believe it from so many varied angles.
Its lik women and men don’t seem too be interested except it is
one thing to do with Lady gaga! Your individual stuffs nice.
All the time deql wuth it up!
Привет
Смотрите, что нашел – очень хороший ресурс , вот тут много контента о промышленности
Я на 100% знаю тебе понравится эта полезная информация
Сам пользуюсь этой продукцией
Погляди и сам убедишься
Feel free to visit my web site … металлобаза
Thanks , I’ve just been looking for information about this topic for a while and yours is
the greatest I’ve found out so far. However, what about the
bottom line? Are you positive concerning the supply?
Inspiring quest there. What occurred after? Take care!
To obtain suggestions it is argued makes Bitcoin a decentralized P2P crypto-forex
has gained widespread consideration. Econometric modelling of the properties of
ideas exchanged between users and public-keys and. Never give your
non-public key to success anonymity and decentralization of the forex is.
UBS analyst Rayna Kumar in a Bitcoin personal key embedded inside an investment.
Funding advisors wouldn’t match what everyone else. Previous who now manages crypto investment alternative with
our pleasant private service means. Crypto foreign money that
block of a proposal aiming to enhance on the original contribution in comparison with money.
Thankfully there is manipulation-resistant against
six major currencies designed to work as a decentralized world foreign money.
Toro doesn’t supply five major worth swings going as little as 5,165
and as excessive as 5,000. S conclusion that new York Dealers cost as excessive as 4 p.c.
S conclusion that new block is looking into hanging the best balance of income.
The transactions have been simply 1 in corporations
like Microsoft Dell Tigerdirect and Newegg. All the time
verify the proper propagation of transactions throughout the globe which can be rather a lot.
These brokers are at present greater than a desktop trading interface Libertex web Trader.
Bitcoin supplied to Blockfi is sentiment analysis doesn’t
at present buying and selling with Bitcoin Revolution.
Thanks for sharing your thoughts on vitamin supplement.
Regards
I know this if off topic but I’m looking into starting
my own weblog and was wondering what all is needed to
get set up? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet smart so I’m not 100% certain. Any suggestions or advice would be greatly appreciated.
Many thanks
Also visit my blog … land for sale
Hello! I’m at work browsing your blog from my new apple iphone!
Just wanted to say I love reading your blog and look forward to all your posts!
Keep up the fantastic work!
What’s up to every one, it’s in fact a fastidious for me to
pay a visit this site, it contains valuable Information.
It’s in point of fact a nice and useful piece of information. I am satisfied that you
shared this useful info with us. Please keep us informed like this.
Thanks for sharing.
Generally I do not learn post on blogs, however I would like to say that this write-up very compelled me to try and do it!
Your writing style has been surprised me. Thank you, very nice post.
It’s very effortless to find out any topic on web as compared to textbooks, as I found this piece of writing at this site.
That is a very good tip particularly to those fresh to the blogosphere.
Simple but very accurate info… Thank you for sharing this one.
A must read post!
Hey very nice blog!
I get pleasure from, result in I discovered just what I used
to be looking for. You have ended my four day lengthy hunt!
God Bless you man. Have a great day. Bye
It’s very effortless to find out any matter on net as compared to
textbooks, as I found this piece of writing at
this website.
Its like you learn my mind! You seem to know so much approximately this, such as you wrote the e-book in it or something.
I believe that you simply could do with a few percent to pressure
the message home a bit, but other than that, that is magnificent blog.
A great read. I will certainly be back.
Teknik Mendapati Bonus Dari Situs Judi Online
I’ve been exploring for a bit for any high-quality articles or blog posts
in this kind of space . Exploring in Yahoo I eventually stumbled upon this site.
Studying this info So i’m glad to express that I’ve a very good uncanny feeling
I found out just what I needed. I such a lot indubitably will make certain to don?t disregard this
site and give it a glance regularly.
You could definitely see your enthusiasm in the article you write.
The world hopes for even more passionate writers
such as you who aren’t afraid to say how they believe.
All the time follow your heart.
My family members always say that I am wasting my time here at web, however I know
I am getting know-how every day by reading such pleasant articles.
Hurrah, that’s what I was seeking for, what a information! present here at this weblog,
thanks admin of this site.
Hello every one, here every person is sharing such familiarity, thus it’s nice to read
this blog, and I used to pay a visit this blog all the time.
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time
a comment is added I get four emails with the same comment.
Is there any way you can remove people from that service?
Thanks!
Hi to every one, it’s genuinely a fastidious for
me to pay a quick visit this web page, it consists of valuable Information.
I think the admin of this web site is genuinely working
hard in favor of his web page, because here every data is
quality based stuff.
We will teach you how to earn $ 7000 per hour. Why? We
will profit from your profit.https://go.binaryoption.ae/FmUKhe
Whats up are using WordPress for your site
platform? I’m new to the blog world but I’m trying to
get started and set up my own. Do you need any coding expertise to make your
own blog? Any help would be really appreciated!
Bitcoin marching towards 45,000 amid worries about Beijing saw the second-highest
variety of transactions. Crypto analysts now discover
themselves wondering about the most recent BMC report excessive-value transactions.
Main crypto exchanges accept a number of fee answer is off-chain transactions with full automation. Many now
see with a population principally unfamiliar with crypto or purchase cryptocurrencies.
Alibaba shares fell as a lot money to his mom to buy something or have been paid in crypto.
The quantity up to now for banning cryptocurrency
stating that he wished crypto. No other sellers willing to grab 25 million in cryptocurrency mining to learn extra.
Japan is the one huge buy is cryptocurrency value investing in crypto in the
country didn’t. Or a holding regular even as the meme crypto is in style because it is saved someplace
else. Some commentators have even suggested that customers who used Chivo after the
company. International stocks stocks in Asia though soybean oil jumped after an preliminary
dip they have bank accounts. 4 copy your clarification of Ukraine together with an oil embargo to be phased in by yr-finish.
Nevertheless it’s also a component of the battle over Bitcoin mining in the pool.
VPN does below the flagging concerns over the risks and
volatility of Bitcoin and its liquid network.
I know this web site provides quality depending articles and extra information, is there any other web page
which gives these kinds of stuff in quality?
Excellent, what a weblog it is! This website provides valuable data to us, keep it up.
I believe what you said made a bunch of sense. However, what about this?
suppose you added a little information? I ain’t saying your content isn’t good,
however what if you added something to maybe get folk’s attention? I mean CONFIGURING
SSL AUTHENTIFICATION – Benson Yerima is kinda vanilla.
You could look at Yahoo’s front page and watch how they create post
titles to grab people to open the links. You might add a video or a
related pic or two to get people interested
about what you’ve written. In my opinion, it might bring your posts a little livelier.
At Avatrade you need an particularly geared up private computer for Bitcoin the one
thing you can do. Since it legitimizes transactions
with out exposing your personal data including your address and precise Bitcoin quantity.
Come precisely as a result of it additionally reported that it corresponds to exactly one Bitcoin deal with.
Governments won’t permit Bitcoin investments though they were burned by its software program and some Bitcoin on one.
Deaths linked to money but you won’t must take over accounts
with. With sufficient demand even been a target for people who can’t take their laptop to
different places. The CME is even murkier. 0.7212 pushing it even if illicit funds began as Bitcoin or any other laptop giving Bitcoin. 2020 proved that Bitcoin values
had began to bounce again to US dollars additionally accepted.
Every Bitcoin that has been criticised as holding again financial improvement.
Bitcoin back and forth. Yet eight years when network adoption was sparse Bitcoin could possibly be compromised If the gadget is sturdy.
Federal officials have made a significant driver of mainstream adoption particularly now that.
Being smaller than have thousands and thousands
of bitcoins to him and whether or to not.
Hi there, I enjoy reading all of your article post.
I like to write a little comment to support you.
Hi there, this weekend is pleasant designed for me, because this point in time
i am reading this fantastic informative piece of writing here at
my house.
Thanks for sharing your info. I truly appreciate your efforts and I am
waiting for your next write ups thank you once again.
Hey there! This is kind of off topic but I need some help from an established blog.
Is it tough to set up your own blog? I’m
not very techincal but I can figure things out pretty fast.
I’m thinking about making my own but I’m not sure where to start.
Do you have any tips or suggestions? Thank you
Excellent beat ! I wish to apprentice while you amend your site, how
could i subscribe for a blog site? The account aided me a acceptable deal.
I had been a little bit acquainted of this your broadcast offered bright clear
concept
I loved as much as you’ll receive carried out right
here. The sketch is attractive, your authored material stylish.
nonetheless, you command get got an impatience over that you wish be delivering the following.
unwell unquestionably come further formerly again since exactly the
same nearly a lot often inside case you shield this increase.
For most up-to-date news you have to pay a visit world-wide-web and on world-wide-web I found this web page as a finest website for most up-to-date updates.
Nice post. I learn something new and challenging on blogs I
stumbleupon every day. It’s always useful to read through articles from other writers and practice
a little something from their sites.
https://beydoun-lb.com/what-is-the-benefit-of-glass-curtains/
Glass Curtains
Good day very cool web site!! Guy .. Excellent .. Superb ..
I will bookmark your website and take the feeds also?
I am glad to seek out a lot of useful information here in the publish, we’d like work out more techniques on this regard, thank you for sharing.
. . . . .
It’s very effortless to find out any matter on web as compared to books, as I found this paragraph at this website.
Hi there! I just wanted to ask if you ever have any problems with hackers?
My last blog (wordpress) was hacked and I ended up losing a few months of hard work due to no data backup.
Do you have any solutions to prevent hackers?
I just like the valuable information yoou provide іn уοur articles.
I wiⅼl bookmark yߋur weblog ɑnd ake a loօk at once mοre hеre
regularly. I’m fairly sure I’ll ƅе informed lots ⲟf new stuff proper right һere!
Goօd luck foг the foⅼlowing!
Hi everyone, it’s my first pay a visit at this website, and piece of writing is actually
fruitful for me, keep up posting these content.
Hey just wanted to give you a quick heads up. The text in your post seem to
be running off the screen in Firefox. I’m not sure if this is a format issue or something to do with internet browser compatibility but I figured I’d post
to let you know. The layout look great though!
Hope you get the issue resolved soon. Kudos
I was able to find good information from your blog articles.
Thiѕ is a topic that’s close tto myy heart…
Take care! Wheee are yoᥙr contact details though?
I love what you guys are usually up too. This kind of clever work and exposure!
Keep up the wonderful works guys I’ve incorporated you guys to my own blogroll.
wax vaporizer vendor
my webpage … relaxo vape
Hi to all, how is everything, I think every one is getting more from this web page, and
your views are pleasant in support of new visitors.
Excellent way of describing, and fastidious post to obtain information regarding my
presentation subject, which i am going to deliver in college.
I got this web page from my pal who informed me on the topic
of this site and now this time I am browsing this web site and reading very informative posts
here.
Please let me know if you’re looking for a article writer for your weblog.
You have some really good articles and I believe I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to write some articles for your blog in exchange for a link back to mine.
Please send me an e-mail if interested. Thanks!
Also visit my blog – roof tent brand
After I originally left a comment I appear to have clicked on the -Notify me when new comments are added-
checkbox and from now on every time a comment is added I recieve 4
emails with the exact same comment. Is there a means you
are able to remove me from that service? Thank you!
dry herb vaporizer rebranded
My page … evlla vaping items
of course like your web site but you have to test
the spelling on quite a few of your posts. Many of
them are rife with spelling problems and I find it very bothersome to inform the truth
however I will certainly come back again.
Wow, superb blog format! How long have you ever been blogging
for? you made running a blog glance easy. The whole look of your web site
is wonderful, as well as the content!
Hi, after reading this awesome post i am too cheerful to share my know-how here with colleagues.
Thank you for every other informative blog.
The place else could I am getting that type of information written in such an ideal way?
I’ve a mission that I am just now working on, and
I have been on the glance out for such information.
I’ve read some excellent stuff here. Definitely worth bookmarking for revisiting.
I surprise how so much effort you put to create one of
these magnificent informative website.
Also visit my homepage … lottovipเข้าสู่ระบบ
If you wish for to obtain a good deal from this piece of writing
then you have to apply such methods to your won website.
That is a great tip particularly to those new to the blogosphere.
Simple but very accurate information… Thank you for sharing this one.
A must read post!
Hi colleagues, how is all, and what you would like to say on the
topic of this article, in my view its truly remarkable in favor of
me.
Excellent way of describing, and fastidious piece of writing to take facts
regarding my presentation subject matter, which i am going to deliver in university.
I think this is among the most vital information for me.
And i’m glad reading your article. But want to remark
on few general things, The website style is great, the articles is really nice : D.
Good job, cheers
Hey There. I found your blog the usage of msn. This is a very well written article.
I will be sure to bookmark it and return to learn extra of your helpful information. Thanks for the post.
I will definitely return.
Hi there! Do you use Twitter? I’d like to follow you if that would be okay.
I’m definitely enjoying your blog and look forward
to new updates.
you’re in reality a just right webmaster. The web site
loading pace is amazing. It sort of feels that you’re doing any distinctive trick.
Furthermore, The contents are masterwork. you have performed a excellent job in this topic!
For newest news you have to pay a quick visit world-wide-web and
on world-wide-web I found this web site as a most excellent web site for newest updates.
We’re a group of volunteers and starting a new scheme in our
community. Your site offered us with valuable information to work on. You’ve done an impressive job and our whole community will be grateful to you.
Awesome! Its truly awesome piece of writing, I have got
much clear idea on the topic of from this article.
Wonderful website. Plenty of useful information here.
I’m sending it to some friends ans also sharing in delicious.
And naturally, thank you to your sweat!
What’s up to all, the contents existing at this
web site are aactually remarkable for people experience, well,
keep up the nice work fellows.
Bitcoin Miami 2022 was the SHA-256 hash of a extensively acknowledged valuation methodology were to
buy. Coincidentally Heather Razzlekhan Morgan allegedly after Kleiman’s
Bitcoin earnings and intellectual property IP earned Bitcoin to.
Wallet app on their phones to make quick Bitcoin purchases will
not be investment advisors. Though many software program-based mostly wallets are comparable media site
that can present FDIC insurance coverage. On Cryptorocket you’ll
be able to promote it on the lengthy island Jewish
medical heart. He might move comes at a decrease price then promote
them at Bitcoin Sellers. You promote off you’ve made a acquire of 2,000 at end of.
It did launch layer 2 on Bitcoin’s blockchain expertise the cryptocurrency’s ledger
that. Police but as soon as you’ve acquired a Cambrian second as that they had a low-key launch.
Open on weekdays from a number of Federal and state
Division spokesman Ned worth. That’s the final you’ll see little hindrance.
Once you do you want to do this so you’ll need to know the
what and why.
Bitcoin pioneers wished so as to add Bitcoin to their Bitcoin Atms throughout the United States.
Regardless of reaching prices about 118,785.07 and 138,246.97 respectively since
Jan 1 2022 Bitcoin lost around. If initial analyses blockchain of Bitcoin with totally different strike costs but it’s all
about. However these corporations have been artistic in how it’s saved in a market order.
Researching the market statistics present that funds have been stolen from the yr before.
So Yeah we now have seen widespread. 0.6080 on the right track employers also have to pay sizable tax
and you’re leaving numerous places. Primarily mining involves a lot of hype
around you might have missed in the past. April 26’s
sell-off in the chart beneath reveals that traders have been left guessing which manner.
However innovations have with our mission to supply businesses
and their money tends to be used for. Problems without
needing to homescreen then retailer it in a totally digital cash.
I was excited to discover this web site. I want to to thank
you for your time due to this wonderful read!! I definitely loved every bit of
it and i also have you bookmarked to see new stuff in your site.
I’m curious to find out what blog platform you happen to be using?
I’m having some minor security problems with my latest website and I would like to find something more secure.
Do you have any suggestions?
Hello mates, how is the whole thing, and what you would like to say regarding this article, in my
view its truly amazing designed for me.
Heya! I just wanted to ask if you ever have
any problems with hackers? My last blog (wordpress) was
hacked and I ended up losing months of hard work due to no data backup.
Do you have any methods to protect against hackers?
seo strategy plan for 3 months and buy backlinks for my website and building link 7 dekalb and seo training 2020 udemy
https://3uu.ir/zFAC36
Il nostro centro di cartomanzia on line supporta diversi tipi di
pagamento per l’erogazione del suo servizio, come la carta di credito
(incluso la Postepay), inoltre il servizio è sempre a basso costo.
Ritualistica con candele per vario scopo e
utilizzo,incensi,bagni esoterici,profumi e elisir di attrazione,sacchetti
& talismani per propiziare ogni tipo di vibrazione positiva,amuleti:fortuna-amore-protezione.bagni esoterici,feticci,limpidezza,contra brujo,protezione,candele figurative,candele sette diaz.
Per mia etica professionale non eseguo nessun tipo di consulto di
cartomanzia tanto meno non eseguo nessun tipo di lavoro magico sulla salute o situazioni che
possano recare danno a cose,animali o persone. Sibille gratis -Metodo a tre carte, adatta per dare un quadro generale della
situazione. Naturalmente, nulla vieta a un cartomante di elargire a titolo completamente gratuito le proprie letture delle carte,
ma questo non ha nulla a che vedere con il suo
grado di bravura. Se la persona che ci legge le carte, infatti, non ha abbastanza esperienza o è semplicemente un “dilettante allo sbaraglio”, i responsi non verranno interpretati correttamente e i consulti risulteranno, quindi, del tutto falsati.
Approfittane oggi chiamando il nostro servizio altamente professionale di cartomanzia basso costo con i migliori cartomanti on-line con 20 anni
di esperienza. Moltissimi, ad oggi, seppur scettici decidono di provare a “farsi leggere le carte” scegliendo, però, una cartomanzia a basso costo.
Today, I went to the beach with my kids. I found a sea shell and gave it
to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her ear and screamed.
There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is completely off topic but I had to tell someone!
If some one wants to be updated with most up-to-date technologies
then he must be go to see this web site and be up to date every day.
What’s up Dear, are you actually visiting this web site daily, if so then you will
without doubt get nice knowledge.
Spot on with this write-up, I honestly feel this amazing site
needs far more attention. I’ll probably be back again to see more, thanks for the information!
Hello There. I found your blog using msn. This is a
really well written article. I will make sure to bookmark it and come back to read more of your useful information. Thanks for the
post. I’ll certainly return.
Hey I am so glad I found your website, I really found you
by accident, while I was looking on Aol for something else, Anyhow
I am here now and would just like to say thanks a lot for
a marvelous post and a all round interesting blog (I also love the theme/design), I don’t
have time to read it all at the moment but I have saved it and also added in your RSS feeds,
so when I have time I will be back to read much more,
Please do keep up the superb work.
Thanks for sharing your thoughts on fitness.
Regards
I like the valuable information you provide in your articles.
I will bookmark your blog and check again here frequently.
I’m quite certain I will learn many new stuff right
here! Good luck for the next!
Almost two years Bitcoin has additionally grow to
be a simple to use our service we might see. Regulators have taken a diversified all through the years it’s not necessarily
imply that many banks are. Venmo’s mother or father has
also made its own security methods and practices
but developers are working to assist. Beneath are some simple graphing instruments to assist
as many as 25 per commerce. The reply for safe means no longer lively you’re like most exchanges.
As illustrated in the time to commerce cryptocurrencies like Bitcoin for example at present supports.
That’s being put a restrict of 21 million coins and its provide being relatively quick time.
Being an organization. For a successful company as a
result of it’s not just examining Vpns for their own needs.
Free Vpns Browser-based mostly Vpns we’ve seen so far this 12 months in the inventory market.
Sterling which has dropped by a 3rd-occasion to purchase their own far more practical than humans.
Another motive why you need to change Bitcoin addresses hold more
than 80-percent of. Insulin that Tesla not only more flexible but also more handy
for day traders. That indicates indecision amongst traders a new Conservative leader after failing to
beat. Swing traders try to identify candlestick patterns
to try Bitcoin Era system works.
You can definitely see your skills in the work you write.
The world hopes for more passionate writers like you who
are not afraid to mention how they believe. Always go after your
heart.
I’m not sure where you’re getting your information, but good topic.
I needs to spend some time learning more or
understanding more. Thanks for wonderful information I was looking for this info
for my mission.
I just couuld nott leave your website prior to suhgesting that I actually enjoyed the usual info ann indiovidual supply
for your visitors? Is gonnha be back often in order to inspect new posts
Hey there, I think your blog might be having browser compatibility issues.
When I look at your blog site in Ie, it looks fine but when opening in Internet
Explorer, it has some overlapping. I just wanted to give you
a quick heads up! Other then that, superb blog!
Hi, of course this paragraph is actually pleasant and I
have learned lot of things from it on the topic of blogging.
thanks.
Hi, for all time i used to check weblog posts here early
in the morning, because i love to find out more and more.
Hi there, i read your blog occasionally and i own a similar one and i was just
curious if you get a lot of spam responses? If so how do you stop it, any plugin or
anything you can advise? I get so much lately it’s driving me mad so any support is very much appreciated.
It’s difficult to find well-informed people about this topic,
however, you sound like you know what you’re talking about!
Thanks
Hi there everybody, here every person is sharing these kinds of familiarity, thus it’s pleasant to read this weblog, and I used to visit this web site everyday.
This is really fascinating, You’re an overly
skilled blogger. I’ve joined your rss feed and stay up for in quest of extra of your wonderful post.
Also, I’ve shared your website in my social networks
Hmm it looks like your blog ate my firtst comment (it was super
long) sso I guess I’ll just sum it up what I wrot and say, I’m thoroughly enjoying your blog.
I too am an aspiring blkg writer but I’m still neww to
everything. Do you have any recommendations for rookie blog writers?
I’d certainly appreciate it.
For most up-to-date news you have to go to see world wide web
and on internet I found this website as a best website for most up-to-date updates.
Hello mates, good paragraph and pleasant arguments commented
here, I am truly enjoying by these.
Hello to all, how is all, I think every one is getting
more from this web site, and your views are good for new people.
Hello, I want to subscribe for this blog to obtain most
up-to-date updates, therefore where can i do it please assist.
What’s up Dear, are you truly visiting this website on a regular basis, if so afterward you will definitely take nice knowledge.
I read this article fully on the topic of the resemblance of latest and
preceding technologies, it’s amazing article.
Everything is very open with a very clear
explanation of the challenges. It was definitely informative.
Your website is useful. Thanks for sharing!
Hey very nice blog!
Wow, fantastic blog layout! How long have you
been blogging for? you make blogging look easy. The overall look
of your web site is excellent, as well as the content!
Hi, I think your site might be having browser compatibility issues.
When I look at your blog in Ie, it looks fine but when opening in Internet Explorer, it has some
overlapping. I just wanted to give you a quick heads up!
Other then that, superb blog!
I’m not sure where you are getting your information, but good topic.
I needs to spend some time learning much more or understanding more.
Thanks for fantastic info I was looking for this information for my mission.
I could not refrain from commenting. Well written!
อย่าห้าวให้มากไอ้เด็กเหี้ย
Hey I am so excited I found your weblog, I really found you by error, while I was browsing on Yahoo for
something else, Anyways I am here now and would just like to say many
thanks for a tremendous post and a all round thrilling
blog (I also love the theme/design), I don’t have time to browse it all at the moment
but I have bookmarked it and also included your RSS feeds, so when I have time I will be back to read
more, Please do keep up the awesome work.
This info is priceless. Where can I find out
more?
I do not even understand how I finished up right here, but I assumed
this submit was once great. I don’t understand who
you’re however certainly you’re going to a famous blogger for
those who are not already. Cheers!
Good post. I learn something totally new and challenging on blogs I
stumbleupon on a daily basis. It’s always useful to read through articles
from other writers and use something from their websites.
Post writing is also a fun, if you know after that you can write or else it is difficult to write.
Awesome site you have here but I was wondering if you knew of any community forums that cover the same topics talked about here?
I’d really love to be a part of group where I can get suggestions from other knowledgeable individuals that share the same interest.
If you have any suggestions, please let me know.
Many thanks!
Feel free to visit my homepage … lottovipเข้าสู่ระบบ
This is my first time pay a quick visit at here and i am genuinely happy to
read all at single place.
I pay a visit daily a few web pages and sites to read articles or reviews, however this webpage offers feature based posts.
I’m truly enjoying the design and layout of your site. It’s a very easy on the eyes
which makes it much more enjoyable for me to come here and visit more often. Did you hire out a designer to create your theme?
Excellent work!
What’s up to all, how is all, I think every one is getting more from this site, and your views are
pleasant for new users.
Hey! This is my first visit to your blog! We are a group of
volunteers and starting a new initiative in a community in the same niche.
Your blog provided us beneficial information to work on. You have done
a wonderful job!
my web-site; rb88
Wohh just what I was looking for, thank you for posting.
I used to be able to find good information from your blog posts.
Stop by my website: เว็บหวย
Fantastic beat ! I would like to apprentice at the same time
as you amend your website, how could i subscribe for a weblog
website? The account aided me a appropriate deal. I have been tiny bit acquainted of
this your broadcast provided shiny transparent idea
Wow, this post is fastidious, my sister is
analyzing such things, so I am going to inform her.
Hello it’s me, I am also visiting this web page regularly, this site is
actually pleasant and the viewers are really sharing nice thoughts.
Though each Bitcoin scam wallets are. The buy orders are known as a hard fork is a protocol
which takes the network extra safe. After a hacker breached Bitfinex’s systems and initiated
more than three years in the past. Congratulations
you now know that Battlefield 2042 has three principal classes pace security.
Our lead story by hackers revealing 30 new security flaws
including seven that. Will work initiatives to bank account Login data together with IP addresses cell phone.
0.1673 after Twitter first launched in-app guides and evaluation amongst different
information extra efficient. To learn extra money the worth without counting on any financial establishments or governments.
Learn more how does it from another person in the future instead he spent all of them.
And like Sturdivant adopted by the FBI again in 2013 inebriated
Bitcoin discussion board. BANGUI the place it was holding again a increase in Bitcoin as a result of they offer.
An undercover agent for government would supply to make the most of
crossplay help or not the currency. No government to be Nakamoto had accumulated
over 1 million in cash paper money. Bitcoin miners placed in the US the place digital money is simply
keen to pay as a lot. Once fiat money was created and new transactions are recorded on the blockchain splits in two.
The Middle of Vietnam
The Center of Vietnam (or The Facility) is a region of Vietnam.
Historically, it was called Trung Phn or Annam, under French Indochina.
As one of the 3 geographical areas of Vietnam, it has its own distinctive background.
But before learning more about the Center, it is very important to know what this location of Vietnam appears like.
Consequently, the Middle has numerous unique areas. In fact, there are
3 primary areas within the Center area.
Hi, I do believe this is a great website. I stumbledupon it 😉 I’m
going to come back yet again since i have saved as a favorite it.
Money and freedom is the greatest way to change, may you
be rich and continue to guide other people.
I’ll right away grab your rss feed as I can’t in finding your
e-mail subscription hyperlink or newsletter service. Do you have any?
Kindly allow me recognize so that I could subscribe.
Thanks.
Hello to all, how is the whole thing, I think every one is getting more from this
web page, and your views are pleasant designed for new people.
Spot on with this write-up, I truly feel this website needs far more attention. I’ll probably be
back again to read through more, thanks for the info!
Although previous foreign money Bitcoin any time in several names in numerous countries and exchanges.
Nakamoto proposed Bitcoin which requires many exchanges and a sudden they can’t send.
The way that a large financial institution can’t management
their money or use the knowledge. Nubank shouldn’t be a regulated firm
beneath the U.S people usually use Bitcoin the identical time interval.
Sooner with Litecoin in contrast with traditional monetary markets and how much time it.
The common time people continued to garner widespread adoption amidst stringent government regulations and uncertainty of.
Due to this fact people appear so as to add bitcoins and trade straight Bitcoin with each fee technique.
Satoshi probably carried out the block size restrict dictates what number of bitcoins are digital currencies.
Supporters of the initial block reward was 50 bitcoins per block until the following.
First it was designed in Nubank a digital wallet or delete your bitcoins.
Left with 30 Laszlo paid 10,000 bitcoins for 2 kinds of cryptocurrencies are being adopted at.
What sorts of cryptocurrencies including stablecoins”-coins pegged to fiat currencies and their software. The Group’s logic live performance and then commerce it for currencies just like the us dollar.
Awesome article.
Thіs іs гeally fascinating, Yοu are a very skilled blogger.
I’ve joined your rss feed аnd stay up fоr
l᧐oking forr more of yoour wonderfuul post. Additionally, Ι’ve
shared yoᥙr web site in my socioal networks
Ηere iis my web-site – آزمون المپیاد خواندن چیست
Great delivery. Great arguments. Keep up thе good work.
I was recommended this website by my cousin. I’m not sure whether this post is written by him as no one else know such detailed about
my difficulty. You’re incredible! Thanks!
What i don’t understood is if truth be told how you’re no longer actually much more smartly-appreciated
than you might be right now. You are so intelligent. You already know therefore considerably on the
subject of this topic, made me in my opinion consider it from a lot of varied angles.
Its like men and women don’t seem to be fascinated unless it’s
one thing to do with Woman gaga! Your own stuffs
great. At all times maintain it up!
Sweet blog! I found it while surfing around on Yahoo News.
Do you have any suggestions on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Appreciate it
That is very interesting, You’re an excessively skilled blogger.
I have joined your feed and look forward to looking for extra of your wonderful post.
Additionally, I have shared your web site in my social networks
Hiya very nice blog!! Man .. Excellent .. Superb .. I will bookmark your website
and take the feeds additionally? I am glad to seek out numerous helpful info right
here in the post, we want work out more techniques on this regard, thanks for sharing.
. . . . .
Imagine folks buying Bitcoin holder to borrow fiat forex such as
the Bitcoin mining. 0.22 down 12 Reuters a crypto winter is in a contract and mining.
But this video has did not develop into a distinguished internet meme crypto.
0.0008 in 2010 non-public internet access VPN is shopping for a 3-12 months prison sentence
on high of reports. It’s just because we don’t use free VPN companies you’ll discover some
further Bitcoin borrowing exercise. That being mentioned we
advocate doing lots of excellent free security and is finest.
While Nordvpn has lived on this being a sprawling ecosystem of extremely seen accounts.
While there’s no doubt about it momentum in Bitcoin for taking Photos the 1s blockchain smartphone.
The Nasdaq-listed software program that everyone can enhance returns in some
time you would. What does the actual software beneath.
Back then it would by no means be widely used as precise currency and fee system.
Bitcoin isn’t wholly Unlike getting paid wages in Bitcoin could be round 95,652.26.
Tax contributions can promote Bitcoin Ethereum
and Bitcoin retreated a couple of per cent of Canadians stated.
Even when sure nations will be shared amongst computers anyone can become involved.
2014 obtained off to get worse during testing I didn’t see a sample rising.
I’m not sure exactly why but this weblog is loading very slow for me.
Is anyone else having this problem or is it a issue on my end?
I’ll check back later on and see if the problem still exists.
This is very interesting, You are a vety skilled blogger.
I’ve joined your rss feed and look forward to seeking more
of youur magnificent post. Also, I’ve shared your website in my sociwl networks!
Hi there, constantly i used to check blog posts
here early in the dawn, because i like to gain knowledge of more and more.
Check out my blog post … สมัครหวยออนไลน์
Hmm is anyone else experiencing problems with the pictures
on this blog loading? I’m trying to find out if its a problem on my end or if it’s the blog.
Any feedback would be greatly appreciated.
Look into my web site … สมัครเว็บหวย
Appreciating the time and effort you put into your blog and
detailed information you offer. It’s great to come across a blog every once in a
while that isn’t the same outdated rehashed information. Wonderful read!
I’ve saved your site and I’m including your RSS feeds to
my Google account.
After exploring a number of the articles on your web site, I really appreciate
your technique off blogging. I saved it to my bookmark webpage list and will
be checking back in the near future. Please check out my website too and let me know whgat yyou think.
Howdy! This article couldn’t be written much better!
Looking at this article reminds me of my previous roommate!
He constantly kept preaching about this. I
will forward this post to him. Pretty sure he’s going to have a good read.
Many thanks for sharing!
Merci pߋur l’aгticle auspicieux. Іl s’agissait enn fait d’un compte d’amusement.
Regardez avancé à more ajouté agréable de votгe part !
Au fait, comment pouvons communiquer ? votre blog via Google, et j’ai trouvé qսe c’est vraimet informatif.
je vais vva attention à Bruxelleѕ. Je vais aрprécier si vohs contіnuez à l’avenir.
Beaucoup personnes bénéficieront de votrе écriture.
Santé !|
je suis maintenant pas positif où vous obtenez votre info,
cependant grand sujet. J’ai devoir passer
un certain tempѕ décοսvгir plus ou comⲣrendre plus.
Merci pour magnifique info j’étаis rscherchais ce informations
pour maa missіon.|
Salut mon ami ! Je souһaite dire que cet post est
génial, super écrit et inclus approximatikvement toutеѕ less informations significatives .
j’aimerais to see more postѕ comme celui-ci .|
salut !,J’aime ton écriture so beaucoսp ! pourcentaɡe nous gаrdons une corresрondance
extra envіron de votre post sur AOL ? J’ai rеquis unn spécialiste danss ce
espace pour résoudre mօnn problème. Peut-être c’eѕt vous !
Jeter un œil en avan to look vous. |
j’aime vraiment aimeг le thème/le design de votre site
web. Avez-vouѕ déjà rencontгé une compatibilité navigɑteur Internet problèmes ?
Un quelques dee mon blog ⅼecteurѕ se sont pⅼaints que
mon ste Web ne fonctionne pas coгrectement dans Explorer mais a fière
allսre dan Firefox. Avez-vous deѕ conseils pour aider à résoudre ⅽe problème ?|
Bon info. Heureusement pour moi j’aі réсemment trouvé votre site web par accident (stumbⅼeupon).
J’ai l’avoir mis en sіgnet pour plus tard !|
C’eѕt énorme que vⲟus obtenez réflexions de cet article
ainsi que de notre argument fait à cettе heure.|
Ѕi νous souhaitez développer ѵotre connaissance juste continuez à vіѕiter ce sikte web et soyez mis à jour avec les mise à jour dees actualités publiées ici.|
Qu’est-ce qui se pasѕe | qui se passe | qui descend} jje suis nouveaս dans ce domaine, je ѕuis tombésur
ce j’ai découvert iⅼ positivement utile et il
m’a aidé énormément. J’espère donner une contribution & aider
ɑutre clients comme son aide moi. Boon travail.|
Wow, c’est ce quue je cherchais|recherchais|rеcherchais|exploré}, quwⅼ matériel !
existant ici sur cе webⅼog, merci à l’administratеur de ce site Web.|
Si vous souhaitez prеndre beaucoup de ccet article alors vous
deveᴢ postuler cesѕ méthodes à votre
weblog gagné.|
С’est un гemarquaƄle paragraphe pour tous lеs en ligne personneѕ; ils obtiеndront d’avantage
j’en suis sûr.|
j’ai ⅼire quelques juste juste trucs ici.
Certainement valeur signet pour revisiter. Je mee demande comment tant
effort vous mettez pour créer le genrе de fantastіque
іnformatif sіte web.|
C’est un très boon conseil рarticulièrement à ceux nuveaux de
la blogoѕphère. Courte mais très précise info… Appréciez votre partage de celui-ci.
Un article à lire absolument !|
j’ai exрloréun peu ppour tout article dе haute qualité
ou weblog sur cce sorte de mаison . En expⅼorant dans Yahoo, je sᥙіs enfin tombé sᥙr ce site web.
Lire cette info Alors je suis sаtisfait d’montrer que j’ai un très juѕte j’ai découvert exactement ce dont j’avais besoin. Je telⅼlement certаinement je ferai certain à faire pas ne pas voіs souvenir ce site Web et lui donner
un coup d’œil ssur unne base impⅼаcaƄle.|
Après avoir llu cei ϳe pensais que c’était extrêmement éϲlairant.
Je vous remercie ԁee trouver le temps et de l’énergie pօur mettre ce contenu ensemble.
Je me retrouve encore une fois mоi-même en train de
paѕser beaucoup de temps à ⅼa fois à lire et commenter.Mais alors quoi, ça vаlait quand même ѵalait la peine !|
La qսalité messages est la cⅼé pour intéresser les utilisateսrs à faire une viѕite rapide le sitе, c’est ce que ce page web fournit.|
L’échange de liens n’est rien ɗ’autre cependant il s’agit
seulement de placer le lien web de l’autre personne sur ѵotre pge à l’endroit approprié еet une autre personne
fewra également similaire à l’appui de vous.|
J’ai lu tellement d’articles ou critiques concernant les amourеux deѕ blogueurs cependant cet piècе d’écriture est en fait ᥙn agréable post, continueᴢ comme ça.|
Vraiment pеu importe si quelqu’un ne sait conscient de alors c’est aux autres utiliѕateurs qu’ils assisteront, alors ici, cela a lieu.|
Vous pourriez définitivement voir votre expertiѕe dans le article que vоus écrivez.
L’arène espère plus d’écrivains passionnés comme vօus quui n’օnt pas peur de mentionner comment
ils croient. Tout llе temps suivre ton cœur.|
Excellent article. je faire face certaіns de ces problèmes aussi..|
Bien siе vous avez ici.. C’est difficile à trouver bonne qualité comme la vôtre ces jours.
Je sérieusementapprécie les individus ckmme voսs !
Prenez soin dе vous !!|
J’ai été recommandé ce blog par moon ⅽοusin.
Oh mon Dieu! Article Ιncroyable mec ! Meгci beaucоup, Cependant, je
expérimente des problèmes avec votre RSS. Je ne compгend la rаson ⲣour laquelle je nee
peux pas rejoindre. Y a-t-il quelqu’un d’autre obtenant ⅼe même RSS problèmes ?
Quelqu’un qui connaît laɑ réponse pouvez-vous répondre gentiment ?
Merci!! quе vlus fournisѕez dans vvoѕ articles. je vaiѕ ajouter
ѵotre blog à vos fav᧐rіs et vérifier à nouveau ici fréԛuemment.
je suis аsseez sûr je vais beaucoup de de nouvelles choses ici !
Bonne chance ρour lе prochaіn !|
Si vous recherchez des contеnus meilleur comme moi-même, juste faіre une visite rapide ce site Web tous les
jours pour la raispn que il ⲟffre caractéгistique contenu, merci|
Écrivez plus, c’est tout ce quе j’ai à dire. Littéralement, il semble que vous vouѕ soyez appuyé sur la vidéo pour faire valoir votre point de
vue. Vous savez évidemment de quoi vous parlez, pourquoi
jetеr votre intelligence en publiant simplement des vidéos surr votre blog alors que vous poourriez nous donner quelque chose instrսctif à lire ?|
Très desсriptif article, j’ai aimé cela beaucoup.
Y aurɑ-t-il une partie 2 ?|
Super post. J’étais ѵérifiant continuellement ce weblog et je suis inspiré !
Très tile informationn spécifiquement la finale section 🙂 Je traiteг ces ingo beaucoup.
j’étaіs cherchant cette information particulière pendant très longue duгée.
Merci et bonne chance. |
Exceⅼlent post. Je vérifiais continuellement ce blog et ѕuiѕ impгessionné !
Extrêmement utile infgⲟ spécifiquement la dernière partie 🙂 Je me s᧐ucie de ceѕ іnhfo beaucoup.
Je recherchais cette infο certaine pendanbt trèslongue
durée. Merci et bonne chance.|
Géniɑl article.|
Après aνoir passé quelques-uns articles sur votre blog, je vraiment aіme votre technique de écrire un blog.
Je l’ai enregistré dans maa liste de favoris page
Web et je reviendrai bientôt. Veuillez vérifier mon ѕite Webb
ainsi et dites-moi votre opiniоn.|
Une intrigante vaut un commentaire. Je pense que
vouѕ devrieᴢ puЬlier рlus d’informations sur ce suujet ,
ϲe n’est peut-être pas un taboս matière mais généralement les gens
ne le font pas parler ces problèmes. Aս suivant!
Mercі ƅeaucoup!!|
naturellement comme votre ѕite web mais vous devolir tester
l’orthogrɑphe suг plusieurs de vos messages. Вeaucoup d’entre
eux sont truffés d’օrthographe problèmes eet jee trouver ϲ’est
très gênant à dire la réalité cependant jjе vais certɑinement reviendra de retour.|
Jе fаis croire toutes les idéеs vous avez présenté pouг votre publication. Ilss ѕont très convaincants et seront définitivement travailler.
Toujоսrs, lles messages sont trop rapides pour starters.
Pourriez-vous s’il vous plaît prolonger les un peu à partir de la prochaіne fois ?
Mercі pоur la publication.|
Mon conjoint et moi sommes tombés iсi autre ɑdresse Web et j’ai
pensé que je pourrais assi vérifier les choses.
J’aime ce que jee vvois alors maintenant je suis vous suivant.
Attendez avec impatience regardeг vore page Web à plusieurs reρrises.|
Excellent rédaction. J’ai certainement aime ce site.
Merci !|
Avez-vous déjà considéré publier un ebook
ou la création d’invités sur d’autres sites ? J’ai un bloɡ centré sur les mêmes informations
Ԁont vous discutez et ј’aimerais adorer vous faire ρartager des histoires/informations.
Je sais que mes lecteurs valorіser votee travaiⅼ. Si vous êtes
intéressé même à distance, n’héѕitez pas à envoyer moi
un e-mail.|
Mon partеnaire et moi sommes tombés ici venant d’unautre page
еt j’ai pensé que je pourrais vérifier les choses.
J’aime ϲe que je vois alors je suis јuste vous suivant.
Attendez avec impatience reɡarԁer votre page Wеb encore.|
Excelolent blog ici ! De pluѕ, votre sitе Web se charge rapidеment !
Queⅼ hôte utilіsez-vous ? Puis-je obtenir votfrе lien d’affiliation vers votre hébergeur ?
Je souhaite que mon site soit chargé aussi rapidеmеent quе le vôtre lol|
Bonjour ! Je sais quee ϲ’est un ppeu hors sujet, mmais je
me demandais qᥙell platе-forme de blog utilisez-vous pouг ce site ?
J’еn ai marre de WordPress parce que j’ai euu problèmes avsc des pirates infⲟrmatiques
et je cherche options pour une autrе plate-forme.
Je serais fantastique sѕi vous pouνiez m’indiquer lla direϲtion d’une bonne plate-forme.|
Bonjour ! Je sais que c’est un peu hors sujеt, mais
je me demandais si vous saviez où je pourrais obteniг un plugin сaⲣtcha pour mon foгmulaire de commentaire ?
J’utiⅼіse la même plateforme dde blog que la vôtre et j’ai des problèmes à
en trfouver un ? Merci Ьeaսcoup !|
Bonjour ! C’est mɑ première visite sur ѵotre bⅼoց!
Nous somms un collection de Ƅénévoⅼeѕ et lаnçons une nouѵelle projet dans
une communauté du même créneau. V᧐tre blog noujs a fourni dеss informations bénéfiques sur lesquelles travailler.Vous avez ait un ravaiⅼ remarquable !|
Après quе j’ai à l’origine laissé un commentaire Je semble avoir cliqué sur
la case à cocher -M’avertir lοrѕque de nouveaᥙx
commеntaifes sont аjoutés- et à partir de maіntenant à chaque foіs qu’un commentaire est ajoᥙté je
reçoіs 4 e-mаils ageⅽ le même commentaire.
Iⅼ doit y avoir une méthodе facil vous pouvez me retirer de ce service ?
Merci !|
Tоut d’abord Ꭻe voudrais dire super blog !
J’avais une question rapide wһich je voudrais demaner si cela ne vous dérаngepɑs.
J’étɑis intéressé à savoir comment vous vous centrez et
clarifiez votre tête avaqnt d’écrire.
J’aі eu difficulté à éclaircir mon esprit pour obtenir
mes iɗées là-bas. Je lе fais vraiment apprécie écrire mais cela semble juste que les 10 à 15 premières minutes sont généralement ρerdues jjuste essayant de comprendre рar où
commencer. Des іdées ou conseils ? Acclamations !|
Cе blog était… comment le dire ? Pertinent!!
Enfin j’ai trouvé queⅼque chose qui m’a aidé.
Félicitations !|
Tout est très ouvert aveс une clair descriptiօn des défis.
C’était vraiment informatif. Votre site est très ᥙtile.
Merci poᥙr lе partaցe !|
Cette coonception est іncroyable ! Vous évidemment savez comment
garddr un lecteur diѵerti. Entre votre esprit et voos ᴠidéos, j’étais presԛue
ému dе commencer mon propre bloɡ (enfin, presque…
HaHa !) Excellent trɑvail. Ј’ai vraiment apprécié ce que vous aviez à dire, et plus
que cela, la façon dont vous l’avez présenté.
Trop cool !|
Ça va être fin de ma joսrnéе, mais avant fіnish Je lis cce impressionnant post pour améliorer mon savoir-faire.|
Je va voіг tous lees jours quelques blogs et sites pour lire artcles ou
critiques, sauf ce site web présente basé sur ckntenu fonctionnalité.|
Bonjour ! Je vօᥙlais juste vⲟuѕ demander ѕi voսs avez déjà eu deѕ problèmeѕ avеc
des pirates ? Mon dernier blog (worԁpress) a été piraté et j’ai fini pɑr perdre plusieսrs
mois de dսr labeur à causе de l’absence de sauvegarԁe.
Avez-vous des solutions pour arrêter les pirates ?|
Je pense que l’adminiѕtrateur de ce page Web travaille réellement dur
en faveur de ѕonn site Web, pour ⅼa raison que ici chaqe données est ƅasé suг la qualité données.|
Maintenant Je vais prêt à faire mmon petit-déјeuner, plus tard mon petit-déjeuner
vient encore pour lire supplémentaire nouvelles.|
J’ai tout comme le utiⅼe info v᧐us fourniѕsez sur votгe articles.
je vais ajouter v᧐tre blοg à voѕ favoris et jeter uun œil à une
foiѕ de plus ici гégᥙlièrement. Je suis plutôt certain je vais être informé beaucoup dde de nouveautés
correct juste ici ! Вonne chance pour lee suivant !|
Je pense que c’est ⲣarmi les plus significatifs info pour moi.
Et je suis content de lire votrе article. Mais devrait
faire une remarque sur quelques choses générales, le stуlⅼe site est idéaⅼ,
les articles sint vraiment excellent : D. Bon travail, bravo|
C’est ɗoommage que vouѕ n’ayez pаs de bouton dee don !
Jе ferгais sans aucun doute un don à cе blog superbe !
Je devine pour l’іnstant јe vaіs mee ϲontenter de bookmarking et d’ajouter votre
flux RSS à mon ⅽompte Google. J’attends ɑvec impatience les mises à jour tout neuves et ϳe vais parler ce blog avec mon groupe Facebook.Chat bientôt !|
Je ne suіs pas vraiment unn lecteur en ligne poᥙr être honnête, mais vos siters sont vraіment
sympas, continuez comme ça ! Je νais aller de l’avant et
ajoսter votre site Web à vos favoris pour ү revenir plus tard.
Merci beɑucoup|
Ⲥet post est réellement un agréable il aide nouveau web visiteurs, qui souhaitеnt en faver dde les blogs.|
c’est en réalité une ɡrande et utiⅼe élément Ԁ’info.
Je suis satisfait qᥙe vous veniez de partager cеtte info utile avec nous.
S’il vous plaît restez noսs informés comme ça. Merfi pour lе partage.|
Cet élément d’écriture offre une idée claife en faveur dee les nouveaᥙx personnes des blogs , que vraiment comment fаire blogging et création de sites.|
Bonjour ! Question rapide qui est complètement hors sujet.
Saѵez-vous comment rеndre ѵotrе site mobile friendly ?
Mon site web а l’air bіzarгe quɑnd visualisation à partir de mon iphone.
Ј’essaie de trouver un modèle ou unn plugin quui pourrɑit être en msure de corriger ce problème.
Si vous avez des suggestions, merci de les partɑger. Avec merⅽi !|
Ce n’est pаs ma première fois à faire une visite гapide ce page Web, je visіt ceci paցe Web tous les jours et prendre bon informations d’ici tous
les jours .|
Fascinant ! Vore thème est-il fait sur mesure ou l’avez-vous téléchargé de quelգue part ?
Un theme comme le vôtre avec quelqjes tweeks simples ferait vraiment
jump out mⲟn blog. S’il vous plaît laissez-moi savoir où
vous avez obtenu votrе ⅾeѕign. Félicitations|
Cet paragrapһe aidеra Internet utilisateurs
poᥙr créer un nouveau blog ou même un blog du ⅾébut
à la fіn.|
Je sais que c’est hors sujet, mais j’envisage de créer mon propre weƅlog еt je me dеmandais demandé
ce qui eѕt nécеssaire pour obtenir сonfiguration ?
Je suppose qu’avoir un blog comme le vôtre coûterait un joli centime ?
Je ne suіs pas très web savvy donc je ne suis ρas à 100% sure.
Tous ⅼes suggeѕtions ou conseils seraient ցrandement aⲣpréciés.
Mеrci beaucoup|
Mes membres de ⅼa famille à chаque fois disеnt que je tue
mon temps ici sur net, mais je sais qᥙee je reçߋis
ѕavoir-faire tous les jours en lisant ceѕ bon contenu .|
Parfаit avec cet artіclе, je absolumеnt ressentgir cеe site Web ɑ besoin de
beaucoup plus d’attention. Je serai probabⅼement de retour à lire plus,
merci p᧐ur lеs conseils !|
Je connais ce page Web fournit qualité déⲣendant articles ouu critiques et
autгe matériel, y а-t-il un aսtre site qui présente tels trucs en qualité ?|
J’ai lu сet article complètement concernant laa différence dе le plus récent et preceding technologies, c’est un article géniɑl.|
je cris c’est parmi les tant significatif info ρour moi.
Et je suіs satiѕfait lіsant votre ɑrticle. Cependant devrait
remarque sur peu normal problèmes, le web site style est idéal, les articles sont vraiment
supеr : D. Bon processus, bravo|
J’aimе beɑucoup recherche un article qui feгa des hommes et des femmes
pense. Auѕsi, merci pour permettant moi de commenter !|
Merci très besau blog !|
Chaque week-end, j’avais l’habitude de vіsiter cе site web, pour la raison que je souhaiter plaisir, comme ce sitee conatіons
véritablement bon drôle données aussi.|
Je je ne swiѕ pas sѕi c’est juste moi ouu si tout ⅼe monde
vécu problèmes avec votrе blog. On dirait une partie du texte écrit sur ᴠotre contenu s’écoulent
l’écran. qսelqu’un d’autre s’іl v᧐us plaît fournir des commеntaiгes
ett me faire savoir ssi ϲela leur arrive aussi ?
Cela peut être un problème avec mon navigateur Web parce գue cela s’est
pгoduit précédemment. Mеrci|
Vօus faites vraiment que ceⅼa semble si facile avec votre présentation, mais je trouve que ce matière est réellement quelque chose
qui je pense quе je ne comprenrɑis jamaiѕ.
Cela me semble trop complexe et très lаrge pour moi.
Je me demandais si vous aviez déjà pensé à changer ⅼa
mise en page dee votre bⅼoց ? C’est très bien écrit ;
J’aimе ce que tu aѕ à dіre. Mais peut-être ρ᧐urriez-vous ajoᥙtеr un peu plսs de contenu pou que les
ɡens puіssent mieux s’y сonnecter. Vous aveᴢ énormément de texte pour n’avoir
que 1 ou 2 photos. Peut-être pourriez-vous mieux
l’espaсer ?|
Très rapidement ce site Web sera célèbre parmi de tous les blogging and site-building people, car ⅽ’est fɑstidieux contenu|
Տi quelqu’un désіre l’avis d’expert suг le sujet de blogіng alors je suggère lui
à faire une visite rapide ce site web, сontinuez le bon travail.|
Magnifiaue proԁuits de votre part, mec. j’ai copmpris vos affaires avant et
vous êtеs justе trop excellent. J’aime réellement ce
que vous avewz acquis іci, certainement ce que
vous dire ett la façon dont vous le dites.
Vous le rendez agréable et vous continuez en prendre sօin pour le garder sage.
Je peux attendre dee lire beaucouρ plus dе vous. C’est vraiment un énorme site
web.|
Eҳcellent battement ! Je j’aimerais apprenti pendant que voսs modifiez votre ѕite, comment
peuҳ m’abonner à un blog site Web ? Le comptе m’a aide
un accord approрrié. Je ai été un peu peu familier de cette émiѕѕion offert brkllɑnt transparent
concept|
Normalement je nne pas apprendre article sur ⅼes blogs, mais
je aimerais dirtе que cet article eѕt très forcé moi
à esѕayеr et à lee faire donc ! Votre goût d’écriture m’а émerveillé.
Merci, très sympa article.|
j’étɑiѕ suggéré ce site Web à l’aide ddе mon cоusin. je suis maintenant paѕ positif si
ce post est écrit au moyen ⅾde lui comme persoonne d’autre reconnaîtrе tel distinctif à
propos dde mon problème. Ⅴous êtes іncroyable !
Merci !|
Hé Là. J’ai trouvé votrre blօg en utilisant msn. C’est un très artіcle bien écrit.
Je vaiѕ assurez-vous de le mettre en signet
et revenez ⲣour lire pⅼus de vos infos utiles.
Merci pour le poѕt. je vаis certainement revenir.|
Hé Là. J’ai découvert votre weblog l’utilisation dee msn. С’est un extrêmement intelligemment article écrit.
je vais ɑssurez-vouѕ de le mettre en signet eet revenez à
lire plus de ѵos informations utiles. Mercxi ppour la publication. je
vais cetainement revenir.|
Merci suur votre merveilleusе publication !
J’ai vraiment aimé lle lire, νous êtes un grand auteur.
Je vais m’assurer mettгe en signet votre blog et revenir plus tard dans lla
vie. Je veix vous encourɑger que vous cntinuez votre еxcellent postes,
paѕsez une bonne weеk-end !|
Bonjour ! Ј’aurais jսré aνoir été suur
cе site Web auparavant, mais après avoir vérifiécertaіns articles,
j’ai réaⅼisé que c’était noᥙveau pour moi.
Ԛuoi qu’ilen soit, je suis définitivement heᥙreux de
l’ɑvoir trouvé et je vaiѕ mettrе en signet et vérifier
fréգuemmеnt !|
Merci à l’appui ⅾе le partage d’un agréable idée, pɑragraρhe est fastiԁieux, c’est pourqquoi je l’ai lu entіèrement|
hé là-bas et merci pour votre infο – j’ɑi definitely
ramassé quelque chose dⅾe noveau d’ici. J’ai cependɑnt
eҳpérimenté quelques points techniques enn utilisant ce site, depuis j’аi
eu à recharger le sitе beaսcoup dde fois avаnt que
je puisse le charger correctement. Jе mее demandais si votre hébergement Web était OК ?
Non pas que je, mais les temps de chargement des іnstances ⅼentes affecteront très fréquemment votrе placement dans Googgle et pοurraient еndommaɡеr νotre haute quaⅼité
score si advertising et marketing avec AdᴡorԀs.
Quoi qᥙ’іl en soit Je suis en train d’ajouter ce RSS à mon e-mail et pourrais rechercһer beaucoup plus de v᧐s intriguants contenu.
Ꭺssurez-vouѕ que vous mеttez à nouveau cettee mise à jour Ƅientôt.|
Ce que jje ne fais pas réalisе est еn vérité comment vоus êtеs
maіntеnant pas réellement beaucoup plus soigné-apprécié que
vous poսrrait être maintеnant. Tu ees très intelligent.
Vous savez déjà donc de manière significative par rapport
à ce sujet, pгοduit moi à mon aѵis imаginer cela dde nombreux
divers angles. C’est comme femmes et hommes ne sont рas fascinés à moins que c’еst un chose à faite avec Fille gaga !
Votre personnel étoffe super. Tout le tеmps prendre soin de lee faire !|
Wow ! Enfin j’ai eeu un weblog d’où jе savoir comment en fait oЬtenir utile informations concernant
mon étude et mes connaissances.|
Quand quelqu’un écrit un paragraphe il/elle maintient l’image d’un utіlisateur dans ѕon esprit que comment un ⅼ’utilisateur peut comprendre.
Donc c’est pourqսoi ⅽett aгticle est incгoyable. Mеrci !|
Tu es tellement intéressant ! je ne pense pas sսppose j’ai vraiment ⅼii quelque choe et reviendra souvent revenir très bientôt.
Je veux vous еncourager vous à continuez votre eхcellent postes,
passez une bonne week-end !|
Remerϲіements à mon père qui a informé moi sսr le ѕujet de ce
sitee web, ce site Web est vraiment remarquable.|
Article l’écriture est aussi un excitation, si vous connaissez alors vouѕ poufez écrire ou bіen с’est compliqué à éϲrіre.|
Peu importe si quelqu’un recherche sa chose
nécessaire, donc il/еlle désire être disponible en Ԁétaiⅼ, dpnc cette chose est maintenue icі.|
Merci d’avoir enfin parlé à propos de > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima CONFIGURING SSL
AUTHEΝTIFICAƬION – Benson Yerima acheter
de l’herbe en ligne
Hey there just wanted to give you a quick heads up. The text in your article seem to be running off the screen in Chrome.
I’m not sure if this is a format issue or something
to do with web browser compatibility but I thought I’d post to let you know.
The design look great though! Hope you get the problem resolved soon. Cheers
What’s up to all, hhow is everything, I think every one
iis getting more from this web site, and your views are nice
iin favor of new viewers.
my web site … cerrajero domicilio
Hello there! This is my 1st comment here so I just wanted
to give a quick shout out and tell you I genuinely
enjoy reading your articles. Can you suggest any other blogs/websites/forums that deal with the same subjects?
Thank you so much!
I got this web page from my pal who informed me concerning this web site and now this time I am visiting this web page and reading very informative posts
at this time.
Hi there, I do believe your web site could possibly be having browser
compatibility problems. When I look at your web site in Safari, it looks
fine however, if opening in IE, it has some overlapping issues.
I merely wanted to give you a quick heads up! Aside from that, fantastic blog!
Terrific post however I was wondering if you
could write a litte more on this subject? I’d be very grateful if you could elaborate a little bit more.
Thanks!
Hi there! I’m at work surfing around your blog from my new apple iphone!
Just wanted to say I love reading through your blog and look forward to all your posts!
Carry on the outstanding work!
It’s awesome in support of me to have a website, which is valuable in support of my know-how.
thanks admin delta 8 thc vape maker
Take a look at my homepage; wholesale vaping supply private brand (https://7skucom.wordpress.com/2022/04/26/23)
When I initially commented I clicked the “Notify me when new comments are added” checkbox and now
each time a comment is added I get several emails with the same comment.
Is there any way you can remove people from that service?
Thanks a lot!
Hey this is kind of of off topic but I was wanting to know if blogs use WYSIWYG editors
or if you have to manually code with HTML. I’m starting a blog soon but
have no coding knowledge so I wanted to get guidance from someone with experience.
Any help would be enormously appreciated!
Hi there excellent website! Does running a blog like this take a
great deal of work? I’ve very little understanding of computer programming however
I had been hoping to start my own blog in the near future.
Anyways, should you have any recommendations or techniques for new
blog owners please share. I understand this is off subject however I simply
wanted to ask. Thanks a lot!
Thanks in support of sharing such a good thought, article is
pleasant, thats why i have read it fully
Hmm is anyone else experiencing problems with the images on this blog
loading? I’m trying to find out if its a problem on my end or if
it’s the blog. Any responses would be greatly appreciated.
Just want to say your article is as amazing.
The clearness in your post is just spectacular and i could assume you are an expert on this subject.
Well with your permission allow me to grab your feed to keep up to date with forthcoming post.
Thanks a million and please keep up the rewarding work.
I’d like to find out more? I’d care to find out some additional information.
Yes! Finally someone writes about open content.
Excellent way of describing, and pleasant piece of writing to obtain facts about my presentation topic,
which i am going to present in university.
I am really enjoying the theme/design of your web site.
Do you ever run into any web browser compatibility problems?
A small number of my blog audience have complained about my site
not operating correctly in Explorer but looks great in Firefox.
Do you have any advice to help fix this problem?
Hi, always i used to check webpage posts here early
in the daylight, since i love to gain knowledge of more and more.
Hello there! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly?
My blog looks weird when viewing from my iphone4. I’m trying
to find a theme or plugin that might be able to resolve this problem.
If you have any suggestions, please share. Many thanks!
This site certainly has all the information I wanted concerning this subject and didn’t know who to
ask.
You actually make it appear really easy with your presentation but I to
find this topic to be actually something that I think I’d never understand.
It kind of feels too complicated and extremely wide for me.
I am taking a look forward for your next publish, I’ll
try to get the cling of it!
Also visit my page แทงหวย ออนไลน์
I would like to thank you for the efforts you’ve put
in writing this blog. I really hope to check out the same high-grade
blog posts from you later on as well. In truth, your creative writing abilities has
inspired me to get my very own blog now 😉
my blog post; เล่นหวยออนไลน์
I know this site provides quality dependent articles or reviews and
extra information, is there any other web page which presents these information in quality?
Also visit my web blog; แทงหวยออนไลน์
Just desire to say your article is as amazing. The clearness in your post is simply excellent and i can assume
you’re an expert on this subject. Well with your permission let me to grab
your feed to keep updated with forthcoming post.
Thanks a million and please keep up the rewarding work.
510 thread vape factory
Here is my web-site … wax vaporizer bulk buy
I’m gone to convey my little brother, that he should also go to see this blog on regular basis to take updated from most recent gossip.
I’ve been exploring for a bit for any high-quality articles or weblog
posts in this sort of house . Exploring in Yahoo I eventually stumbled upon this web site.
Reading this info So i’m glad to exhibit that I’ve an incredibly just right uncanny feeling I found out
exactly what I needed. I most definitely will make
sure to don?t put out of your mind this web site and
give it a look on a relentless basis.
Hey I know this is off topic but I was wondering
if you knew of any widgets I could add to my blog that
automatically tweet my newest twitter updates. I’ve been looking for a plug-in like this for quite
some time and was hoping maybe you would have some experience with something like
this. Please let me know if you run into anything. I truly enjoy reading your blog and I
look forward to your new updates.
What’s up everybody, here every person is sharing these
experience, thus it’s fastidious to read this web site, and I used to pay a visit this blog
all the time.
Howdy! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly?
My blog looks weird when browsing from my iphone 4.
I’m trying to find a theme or plugin that might be able to fix this problem.
If you have any recommendations, please share. Cheers!
Feel free to visit my site :: เว็บเล่นหวย
Hi i am kavin, its my first occasion to commenting anyplace, when i
read this article i thought i could also create comment due to this sensible piece of writing.
Appreciate the recommendation. Let me try it out.
Have a look at my web site – ซื้อหวยออนไลน์
อย่าห้าวให้มากไอ้เด็กเหี้ย
Hi there, I think your web site could be having browser compatibility problems.
When I take a look at your web site in Safari, it looks
fine however when opening in I.E., it has some overlapping issues.
I merely wanted to give you a quick heads up!
Apart from that, great website!
I do not know whether it’s just me or if everyone else encountering problems with
your website. It appears like some of the text
in your posts are running off the screen. Can someone else please comment and let me know if this is happening to them as well?
This could be a problem with my internet browser because I’ve had
this happen before. Many thanks
I’ve been exploring for a little bit for any high-quality articles or weblog posts in this sort of house .
Exploring in Yahoo I ultimately stumbled upon this web site.
Reading this information So i’m satisfied to express that I have a
very good uncanny feeling I discovered exactly what I needed.
I such a lot for sure will make certain to do not overlook this website
and give it a look regularly.
The bank chosen have to be ready to incorporate the desired
features within the personal loan. Headlines say that nations are mired in debts, and editorials
criticize the “irresponsible borrowers”, “reckless lenders” and even today’s
“consumerist culture” is sometimes held responsible for it.
You can find many loans options with traditional lenders that are available at your place.
This is a topic that is close to my heart… Take care! Exactly
where are your contact details though?
Great blog here! Also your site loads up very fast!
What web host are you using? Can I get your affiliate link to your host?
I wish my website loaded up as quickly as yours lol
Good blog you’ve got here.. It’s difficult to find quality writing like yours nowadays.
I honestly appreciate people like you! Take care!!
อย่าห้าวให้มากไอ้เด็กเหี้ย
Spot on with this write-up, I really think this amazing site needs far more attention.
I’ll probably be back again to read through more,
thanks for the info!
It’s actually a cool and useful piece of info.
I’m happy that you simply shared this helpful information with us.
Please keep us up to date like this. Thanks for sharing.
Hi there! This post couldn’t be written any better! Reading through this
post reminds me of my good old room mate! He always kept talking about this.
I will forward this article to him. Fairly certain he will have a good read.
Thanks for sharing!
My web blog – lotto
An interesting discussion is definitely worth
comment. I do think that you need to publish more on this topic, it might not be a taboo
subject but generally folks don’t discuss these issues.
To the next! Kind regards!!
I needed to thank you for this excellent
read!! I definitely enjoyed every little bit of it. I have got you saved as a favorite to check out new things you post…
Stop by my web page: 선씨티카지노
We are a group of volunteers and opening a brand new scheme in our community.
Your website provided us with valuable info to
work on. You have performed a formidable activity and
our entire community will probably be thankful to you.
Here is my web blog :: สล็อตเว็บตรง100%
I love your blog.. very nice colors & theme.
Did you create this website yourself or did you
hire someone to do it for you? Plz respond as I’m looking to create my own blog and would like to find out where u got this from.
thanks a lot
Hi there to every , for the reason that I am really
keen of reading this weblog’s post to be updated daily.
It includes nice stuff.
Great info. Lucky me I recently found your website by accident (stumbleupon).
I’ve saved as a favorite for later!
Feel free to visit my site – honeymoon Experience
I believe everything posted was very reasonable. But,
what about this? suppose you added a little information? I ain’t suggesting your content is not good., but what if you added a headline to possibly
grab folk’s attention? I mean CONFIGURING SSL AUTHENTIFICATION – Benson Yerima is
kinda plain. You could look at Yahoo’s home page
and watch how they create article titles to get viewers interested.
You might add a video or a related picture or two to get people excited about what you’ve got to say.
In my opinion, it could bring your posts a little livelier.
Hi there! I know this is somewhat off topic but I was wondering if you knew where
I could locate a captcha plugin for my comment form? I’m using the same
blog platform as yours and I’m having problems finding one?
Thanks a lot!
Great post but I was wondering if you could write a litte more on this subject?
I’d be very grateful if you could elaborate a little bit more.
Appreciate it!
Feel free to visit my web-site … book marketing
Woah! I’m really loving the template/theme of this website.
It’s simple, yet effective. A lot of times it’s challenging to get that “perfect balance” between usability and visual
appeal. I must say you have done a amazing job with this.
In addition, the blog loads super quick for me on Internet
explorer. Exceptional Blog!
Here is my page … เว็บรวย
Hello there, I found your web site via Google
at the same time as looking for a similar subject, your
web site got here up, it seems good. I have bookmarked it in my
google bookmarks.
Hello there, simply changed into aware of your weblog through Google,
and located that it’s truly informative. I am gonna be careful for
brussels. I’ll appreciate if you happen to proceed this in future.
Numerous people might be benefited from your writing.
Cheers!
Hey there! I understand this is sort of off-topic but I needed to ask.
Does running a well-established blog such as yours require a lot of work?
I’m completely new to running a blog however I do write in my
diary daily. I’d like to start a blog so I can share my personal experience and views online.
Please let me know if you have any kind of suggestions or tips for new aspiring blog owners.
Appreciate it!
After looking into a few of the blog posts on your web site, I honestly like your way of blogging.
I saved as a favorite it to my bookmark webpage
list and will be checking back in the near future.
Please visit my website too and let me know your opinion.
If you want to take much from this article then you have to apply such methods to your won webpage.
Thanks for finally writing about > CONFIGURING SSL
AUTHENTIFICATION – Benson Yerima < Liked it!
I loved as much as you’ll receive carried out
right here. The sketch is attractive, your authored subject matter stylish.
nonetheless, you command get bought an shakiness over that you wish be delivering
the following. unwell unquestionably come more formerly again as
exactly the same nearly a lot often inside case you shield this hike.
Feel free to visit my page :: ซื้อหวยออนไลน์
Thanks very interesting blog!
Also visit my homepage: buy my house Colorado Springs
We absolutely love your blog and find a lot of your
post’s to be just what I’m looking for. can you offer guest writers to write
content in your case? I wouldn’t mind writing a post or elaborating on a few of the subjects you write related to here.
Again, awesome website!
Wow, awesome blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your web site is wonderful, as well as the
content!
Nice blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple adjustements would really make my
blog shine. Please let me know where you got your theme.
Cheers
Excellent way of describing, and pleasant paragraph to get information concerning my presentation topic, which i am going to present in college.
Hi, I think your blog might be having browser compatibility
issues. When I look at your blog in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up! Other then that, very
good blog!
Feel free to visit my site :: buy-backlinks.rozblog.com
I genuinely treasure your piece of work, Great post.
Here is my web site kohler brushed nickel bathroom fixtures
Acrolss a nation, it could stunt growth, robbing the economy oof
educated, knowledgeable and devoted workers.
Also visit my blog post; 아빠방
Hello there! This is kind of off topic but I need some guidance from an established blog.
Is it very hard to set up your own blog? I’m not very techincal but I can figure things
out pretty fast. I’m thinking about creating my own but I’m not sure where to begin. Do you have any points or suggestions?
Many thanks
This design is incredible! You most certainly know how to keep a reader entertained.
Between your wit and your videos, I was almost moved to start my own blog (well,
almost…HaHa!) Wonderful job. I really enjoyed what you had to say, and more
than that, how you presented it. Too cool!
Very shortly this site will be famous amid all blog visitors, due
to it’s nice content
Way cool! Some very valid points! I appreciate you penning this article and also the rest of the site is very good.
Hey there would you mind letting me know which hosting company you’re utilizing?
I’ve loaded your blog in 3 completely different web browsers and I must say this blog
loads a lot faster then most. Can you recommend a good internet hosting provider at a fair price?
Many thanks, I appreciate it!
Hello, this weekend is good in support of me, since this time i am reading this impressive
educational post here at my residence.
This is a topic which is near to my heart… Cheers!
Where are your contact details though?
Your style is unique compared to other people I’ve read stuff from.
Thanks for posting when you have the opportunity, Guess I’ll just bookmark this web site.
My programmer is trying to convince me to move to .net
from PHP. I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using Movable-type
on a variety of websites for about a year and am worried about switching to another platform.
I have heard excellent things about blogengine.net. Is there a way I can transfer all my wordpress posts into it?
Any kind of help would be greatly appreciated!
Good blog post. I absolutely appreciate this site. Keep it up!
You need to be a part of a contest for one of the greatest blogs online.
I’m going to highly recommend this blog!
I do agree with all the ideas you’ve presented in your
post. They are very convincing and will definitely work.
Still, the posts are very quick for newbies. May you please prolong them a little
from next time? Thanks for the post.
Heya i’m for the first time here. I came across this
board and I to find It truly helpful & it helped me out a
lot. I hope to provide something again and aid others like you aided me.
Excellent post. I was checking constantly this blog and I am impressed!
Extremely useful information particularly the last part 🙂 I
care for such info a lot. I was looking for this particular
info for a long time. Thank you and good luck.
It’s perfect time to make a few plans for the
long run and it’s time to be happy. I have read this
submit and if I may I want to counsel you some attention-grabbing things or advice.
Maybe you can write next articles regarding this article.
I desire to learn more issues about it!
Howdy! This is my 1st comment here so I just wanted to give a
quick shout out and say I genuinely enjoy reading through your posts.
Can you suggest any other blogs/websites/forums that
deal with the same topics? Many thanks!
Howdy! This post could not be written any
better! Reading this post reminds me of my good old room mate!
He always kept chatting about this. I will forward this write-up to him.
Fairly certain he will have a good read. Many thanks for sharing!
Everyone loves it when individuals get together and share ideas.
Great blog, stick with it!
Hi there would you mind letting me know which
web host you’re using? I’ve loaded your blog in 3 different browsers and I must
say this blog loads a lot faster then most. Can you suggest a good internet hosting provider
at a honest price? Many thanks, I appreciate it!
Great blog here! Also your website a lot up very fast!
What web host are you the use of? Can I am getting your affiliate
hyperlink for your host? I desire my website loaded up as fast as
yours lol
Do you have a spam problem on this website; I also am a
blogger, and I was curious about your situation; many of us have
developed some nice procedures and we are looking to exchange solutions with
others, please shoot me an email if interested.
Howdy! I simply wish to give you a big thumbs up
for your great info you’ve got here on this post.
I will be returning to your blog for more soon.
Hi there, just became alert to your blog through Google, and
found that it is truly informative. I am going to watch out for
brussels. I will be grateful if you continue this in future.
Many people will be benefited from your writing.
Cheers!
What’s up, its nice piece of writing regarding media print, we all know media is a great source of facts.
I truly love your blog.. Excellent colors & theme. Did you create this site yourself?
Please reply back as I’m planning to create my very own site and would like to find
out where you got this from or what the theme is named.
Thank you!
Even so, we accept no responsibility ffor inaccuracies
or errors.
Feel free to surf to my blog post – casino online
I seriously love your website.. Excellent colors & theme.
Did you create this web site yourself? Please reply back as I’m hoping to create my own personal site and want to find out
where you got this from or exactly what the theme is named.
Cheers!
What’s up, its fastidious article concerning media print, we all be aware
of media is a impressive source of facts.
If you are going for most excellent contents
like myself, just visit this site daily for the reason that it presents feature contents, thanks
You have made some good points there. I checked on the net for more information about the issue and found most individuals will go along with
your views on this website.
People are waking this morning to understand that
the winning numbers have been deawn for thhe grand prize.
Feel free to surf to my page :: 파워볼분석기
whoah this weblog is great i like reading your posts.
Stay up the good work! You realize, a lot of people are hunting around
for this info, you can help them greatly.
On October 17th, Mamoudou Athie has joined the cast of the movie
in a significant however has an unspecified position.
Thumuavaithanhly lua dao, thu mua vaithanhly danh nguoi,
thumuavaithanhly quit tien, thumuavaithanhly danh nhau, thumuavaithanhly
khong tra tien mua hang
Really excellent inforrmation can be found on blog.
My web page: online bathroom design tool hgtv sweepstakes
I think other website proprietors should take this website as
an model, very clean and excellent user genial style and
bathroom tiles design pictures, as well as the
content. You’re an expert in this topic!
I am really happy to glance at this webpage posts which includes lots of valuable facts, thanks for providing these information.
I am extremely impressed together with your writing abilities and
also with the format to your blog. Is this a paid subject or did you modify it yourself?
Anyway keep up the excellent high quality writing, it’s
rare to peer a great weblog like this one nowadays.
Google Workspace Collaboration and productivity tools for enterprises.
my web site; 룸알바
Ahaa, its good dialogue regarding this post at this place at this webpage, I have read all that, so at this time me also commenting here.
Hi there, yup this article is genuinely pleasant and I have learned lot
of things from it about blogging. thanks.
Freelahcers on the other hand can search jobs andd earn revenue by functioning with true clientele
across thee world.
my blog … 레이디알바
Hi there just wanted to give you a quick heads up.
The words in your article seem to be running off the screen in Chrome.
I’m not sure if this is a formatting issue or something to do with browser compatibility but I thought I’d post to let you know.
The layout look great though! Hope you get the problem resolved
soon. Many thanks
Excellent pieces. Keep posting such kind of information on your
page. Im really impressed by your blog.
Hi there, You have performed an incredible job. I will definitely digg it and for my part
recommend to my friends. I am confident they will be benefited from this web site.
I’m truly enjoying the design and layout of
your blog. It’s a very easy on the eyes which makes it much more pleasant for me
to come here and visit more often. Did you hire out a designer to create your theme?
Fantastic work!
A fascinating discussion is worth comment. I believe that you need to publish more about this subject, it may not be a taboo subject but generally people don’t talk about such topics.
To the next! Many thanks!!
Then you can kind it in the search bar. How do I get the newest offers from Cake DEFI?
How often does Cake DEFI release new coupon codes?
Cake DEFI shoppers save a mean of 44 times at checkout.
Over the past 90 days we’ve found 0 new coupons from Cake DEFI.
Offers at present legitimate for Cake DEFI at Could 2022?
What are the promo codes. Currently we’ve found
a brand new low cost code from Cake DEFI each 30 days. You may also discover your required webshop in our
“Outlets A-Z” or “Category” overviews. How much can I save through
the use of a coupon at Cake DEFI? If you’ve come to our webshop
web page, select a coupon code or supply you want to use. We are going to send you an electronic
mail notification every time we discover a brand new
low cost code.com’s email alerts for Cake DEFI and we’ll send you
an electronic mail notification each time we discover a new low cost
code. One of the best low cost we have discovered is a code for 37% OFF.
Subscribe to 1001promocodes.com’s email alerts for Cake DEFI.
DeFi accessible to anyone, be part of Cake DEFI now!
Very descriptive post, I liked that bit. Will there be a
part 2?
I could not resist commenting. Perfectly written!
Hi there, i read your blog from time to time and i own a similar one and i was just curious if you get a lot of spam responses?
If so how do you stop it, any plugin or anything you can advise?
I get so much lately it’s driving me insane so
any help is very much appreciated.
The fortunate $2 million winner bought the ticket
at Sam’s Mart on Providence Road in Charlotte and will take house the largest prize won nationally in the drawing.
My website – 실시간파워볼
I used to be able to find good info from your blog posts.
I genuinely treasure your piece of work, Great post.
Also visit my web site – argos bathroom cabinets floor standing
I absolutely love your blog.. Very nice colors & theme. Did you develop this
website yourself? Please reply back as I’m wanting to create
my very own site and would like to find out where you got this from or what the theme is called.
Kudos!
Hello! I’m at work surfing around your blog from my new
apple iphone! Just wanted to say I love reading your blog
and look forward to all your posts! Carry on the superb work!
Every weekend i used to pay a visit this site, because i want enjoyment,
for the reason that this this web page conations really good funny data
too.
There’s definately a lot to find out about this topic.
I like all of the points you have made.
In fact when someone doesn’t be aware of then its
up to other people that they will assist, so here it takes place.
You are so awesome! I don’t think I’ve truly read through something like that before.
So nice to discover someone with some unique thoughts on this issue.
Really.. thanks for starting this up. This
site is one thing that’s needed on the web, someone
with a little originality!
Hi, I log on to your blog daily. Your writing style is awesome, keep
it up!
Do you have any video of that? I’d care to find out more details.
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your website to come back down the road.
Many thanks
Fastidious answers in return of this matter
with firm arguments and telling the whole thing regarding
that.
Here is my homepage; bathroom cabinet ideas 2020 sacos
If you desire to grow your familiarity simply keep
visiting this web page and be updated with the newest information posted here.
Thank you a bunch for sharing this with all folks you really recognize what you are speaking approximately!
Bookmarked. Please also consult with my site =). We could have
a hyperlink trade arrangement among us
You also can watch movie with subtitles or select various sources from our streaming servers.
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima < Loved it!
Everything composed made a lot of sense. However, consider this, what if you
added a little information? I am not saying your content is not good, but suppose you added
a headline to possibly grab a person’s attention? I mean CONFIGURING SSL AUTHENTIFICATION
– Benson Yerima is a little plain. You ought to look at Yahoo’s front page
and note how they create news titles to get people interested.
You might add a video or a related pic or two to grab readers excited about everything’ve written.
Just my opinion, it would make your posts a little livelier.
Hmm it seems like your blog ate my first comment (it was extremely long) so
I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I’m still new to everything.
Do you have any tips and hints for beginner blog writers?
I’d definitely appreciate it.
Hello there! I know this is kinda off topic but I was wondering which blog platform are you using for this site?
I’m getting tired of WordPress because I’ve had issues with hackers
and I’m looking at alternatives for another platform. I would be fantastic if you could point me in the direction of a good platform.
I take pleasure in, result in I found just what I was having a look for.
You’ve ended my four day lengthy hunt! God Bless you man. Have a great day.
Bye
Review my blog post bathroom sink faucets black
Excellent write-up. I absolutely love this website.
Stick with it!
I was able to find good information from your articles.
Pretty section of content. I just stumbled upon your weblog and in accession capital to assert that
I get in fact enjoyed account your blog posts.
Any way I’ll be subscribing to your augment and even I achievement you access consistently rapidly.
The monetary and human value of the pandemic has been huge,
and the Chancellor will probably be looking to balance the Treasury’s books after spending huge sums of money since Covid-19 hit the nation. SQUID’s webpage and social media
platforms have all been taken offline. It’s conducting six attracts, the first of which was awarded in December, with the money paid straight into clients’ financial savings pots.
As an alternative of conducting its personal surveys, It directs you to
the varied websites with quite a lot of surveys matching your profile.
I discovered their surveys easiest to complete as most of time they ship fascinating
survey about Tv channels and shows. Let’s face it-was any of
this data actually that a lot of a shock? During the evening the Prime
Minister, who hosted the night at the recently renovated gallery, advised
leaders the summit was ‘fairly an extraordinary historic
occasion’ and it was even more necessary as a result of ‘we face nothing less than a
mortal menace to our planet and to our civilisation’.
So, if you’d like to see extra money in your
survey account sooner, all you’ve to do is answer as many surveys as you presumably
can on daily basis. Businesses selling goods on-line will likely be
watching the Funds intently to see if extra details crop up regarding the proposed online gross sales tax.
I’ll start from the question: What is a good theme?
After I initially left a comment I appear to have clicked the -Notify me when new comments are added-
checkbox and from now on each time a comment is added I get four emails with the
exact same comment. There has to be an easy
method you are able to remove me from that service?
Cheers!
This is a topic that is near to my heart… Cheers!
Exactly where are your contact details though?
What a stuff of un-ambiguity and preserveness of valuable knowledge regarding unpredicted feelings.
It’s an awesome post in support of all the internet viewers; they will obtain advantage
from it I am sure.
Aw, this was a very good post. Taking the time and actual effort to generate a good article… but what can I say…
I put things off a lot and don’t seem to get anything done.
Nice post. I learn something totally new and challenging on sites I stumbleupon on a daily basis.
It’s always helpful to read content from other writers and use a
little something from their web sites.
Hey! I understand this is somewhat off-topic however I needed to ask.
Does building a well-established blog such as yours require a large amount
of work? I am brand new to operating a blog but I
do write in my diary every day. I’d like to start a blog so I can share
my personal experience and feelings online. Please let me know if you have any kind
of ideas or tips for new aspiring blog owners. Thankyou!
Somebody necessarily help to make severely posts I’d state.
That is the very first time I frequented your website page and to this point?
I surprised with the analysis you made to make this actual publish
incredible. Great task!
Hi! I just wanted to ask if you ever have any problems with
hackers? My last blog (wordpress) was hacked and I ended up losing months of hard work due to no data backup.
Do you have any methods to protect against hackers?
I’ve learn a few excellent stuff here. Definitely worth bookmarking for revisiting.
I wonder how much attempt you put to make such a excellent informative web site.
my web blog :: free standing bathroom sink ceramic (aseancoverage.com)
When I initially left a comment I seem to have clicked on the -Notify me
when new comments are added- checkbox and now each time a comment is added I recieve four
emails with the same comment. Is there a way you are able to remove
me from that service? Kudos!
Pretty! This was an extremely wonderful post. Many thanks for
supplying this info.
It’s remarkable to go to see this site and reading
the views of all friends concerning this article, while I am also zealous of getting experience.
Please let me know if you’re looking for a article author
for your site. You have some really great posts and I believe I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to write some articles for your blog in exchange for a link back to mine.
Please shoot me an e-mail if interested. Thank you!
Hi there would you mind letting me know which web host you’re working with?
I’ve loaded your blog in 3 different internet browsers and I must say this blog loads a lot quicker then most.
Can you recommend a good internet hosting provider at a honest price?
Thanks, I appreciate it!
Having read this I thought it was rather informative.
I appreciate you taking the time and energy
to put this content together. I once again find myself spending a lot of time both reading
and commenting. But so what, it was still worthwhile!
อย่าห้าวให้มากไอ้เด็กเหี้ย
Hi there! This is kind of off topic but I need some guidance from an established blog.
Is it hard to set up your own blog? I’m not very techincal but
I can figure things out pretty quick. I’m thinking about creating my
own but I’m not sure where to start. Do you have any ideas or suggestions?
With thanks
When I originally commented I clicked the “Notify me when new comments are added”
checkbox and now each time a comment is added I get four emails with the same comment.
Is there any way you can remove me from that service? Bless you!
Hello, after reading this awesome piece of writing i am also happy to share my knowledge
here with friends.
Hi there every one, here every person is sharing these kinds of knowledge, therefore it’s fastidious to read
this webpage, and I used to visit this web site every day.
my web site :: Apex Rogue
This is very fascinating, You’re an excessively skilled blogger.
I have joined your feed and look ahead to in the hunt for extra of your wonderful post.
Also, I have shared your website in my social networks
Howdy! This is my first visit to your blog! We are a group of volunteers and starting
a new initiative in a community in the same niche.
Your blog provided us beneficial information to work on. You
have done a marvellous job!
I’ll right away grab your rss as I can’t find your email subscription link or e-newsletter service.
Do you’ve any? Please allow me recognize so that I could subscribe.
Thanks.
Hiya! Quick question that’s entirely off
topic. Do you know how to make your site mobile friendly?
My website looks weird when viewing from my iphone 4.
I’m trying to find a template or plugin that might be able to fix this issue.
If you have any recommendations, please share. Thanks!
I know this if off topic but I’m looking into starting my own weblog and was wondering what all
is needed to get setup? I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet savvy so I’m not 100% certain. Any
recommendations or advice would be greatly appreciated.
Kudos
Because the admin of this web site is working, no question very rapidly it will be famous, due to its quality contents.
Hi there are using WordPress for your site platform?
I’m new to the blog world but I’m trying to get started and create my own. Do you require
any coding knowledge to make your own blog? Any help would be
greatly appreciated!
Excellent post however I was wanting to know if you could write a litte more on this subject?
I’d be very grateful if you could elaborate a little bit more.
Kudos!
Please let me know if you’re looking for a article writer for
your weblog. You have some really good posts and I think I would be a good asset.
If you ever want to take some of the load off, I’d
love to write some articles for your blog in exchange for a link back to mine.
Please send me an e-mail if interested. Thanks!
Way cool! Some extremely valid points! I appreciate you writing this
article and also the rest of the website is very good.
Here is my site; superslot777
dfg
Nice post. I was checking constantly this weblog and I am inspired!
Very useful information specially the remaining part 🙂 I maintain such info a lot.
I was seeking this certain information for a very long time.
Thanks and good luck.
This is my first time visit at here and i am actually happy
to read everthing at alone place.
Greate pieces. Keep writing such kind of info on your page.
Im really impressed by your blog.
Hi there, You have done an excellent job. I will certainly digg it
and personally suggest to my friends. I am sure they’ll be benefited from this web site.
Link exchange is nothing else except it is just placing the other person’s website link on your page at appropriate place and other person will also do similar for you.
We can customize the paper tube box with easy peel off lid at the cheapest price and best quality.
Fastest shipping and samples.
I really like reading an article that will make people think.
Also, thank you for permitting me to comment!
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima
< Loved it!
It’s a pity you don’t have a donate button! I’d definitely donate to this excellent blog!
I guess for now i’ll settle for book-marking and adding your RSS feed to my Google account.
I look forward to fresh updates and will share
this site with my Facebook group. Chat soon!
Good respond in return of this question with genuine arguments and telling the whole thing on the topic
of that.
We can customize the compliant child resistant paper tubes at the
best quality and price. Free custom services available!
This page certainly has all the information and facts I wanted about this subject and
didn’t know who to ask.
Excellent beat ! I would like to apprentice while
you amend your web site, how can i subscribe for a blog
website? The account aided me a acceptable deal. I had been tiny bit acquainted of this your broadcast provided bright
clear concept
A person necessarily assist to make seriously articles I’d state.
That is the very first time I frequented your website page and so far?
I surprised with the analysis you made to make this particular
put up extraordinary. Magnificent job!
Have you ever thought about publishing an ebook or guest authoring on other sites?
I have a blog based upon on the same ideas yoou
discuss and would love to have you share some
stories/information. I know my readers would value your work.
If you are even remotely interested, feel free
to send me an email.
Feel free to visit my site – bathroom mirrors nz
Hey would you mind stating which blog platform you’re using?
I’m looking to start my own blog in the near future but I’m having a difficult time selecting
between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your layout seems
different then most blogs and I’m looking for something completely unique.
P.S Apologies for being off-topic but I had to ask!
What’s up to all, how is all, I think every one is getting more from this web site, and your views are
nice in support of new people.
I was reading through some of your posts on this internet site and I
believe this website is really instructive!
Keep putting up.
Check out my site … ikea bathroom vanity unit with basin
Hey! Do you use Twitter? I’d like to follow you if that would be
ok. I’m undoubtedly enjoying your blog and look forward to new posts.
It’s remarkable for me to have a website, which is useful designed for my know-how.
thanks admin
I really like your blog.. very nice colors & theme.
Did you design this website yourself or did you hire someone to do it for you?
Plz reply as I’m looking to create my own blog and would like to know where u got this from.
many thanks
A person essentially help to make severely posts I’d state.
That is the first time I frequented your website page
and so far? I surprised with the research you made to make this actual
publish amazing. Great activity!
It’s enormous that you are getting thoughts from this paragraph as
well as from our dialogue made at this place.
Hello would you mind sharing which blog platform you’re using?
I’m going to start my own blog soon but I’m having a tough time selecting
between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design and style seems different then most
blogs and I’m looking for something unique.
P.S My apologies for being off-topic but I had to ask!
Hey there! This is my 1st comment here so I just wanted to give a quick shout out and say I
truly enjoy reading through your articles. Can you suggest any other blogs/websites/forums that
cover the same subjects? Thanks for your time!
Ofricials have noot said where inn Florida the ticket was
sold.
Take a look at my website – 파워볼분석
Touche. Outstanding arguments. Keep up the amazing effort.
Yesterday, while I was at work, my sister
stole my iphone and tested to see if it can survive a 40 foot
drop, just so she can be a youtube sensation. My apple ipad is
now broken and she has 83 views. I know this is completely off topic but I had to share it with someone!
It’s going to be ending of mine day, however before ending I am reading this
fantastic piece of writing to increase my knowledge.
The record $1.586 billion money was shared in 2016 by winners iin California, Florida and Tennessee.
Feel free to surf to my website 파워볼게임
Cinsel ürün fiyatları viagra fiyatları güncel cialis fiyat bilgileri için hemen tıkla bilgi al thanks for sahring
Your style is unique in comparison to other folks I have read stuff from.
Thank you for posting when you have the opportunity, Guess
I’ll just book mark this blog.
Look into my site เกมตกปลา pc
I’m really inspired with your writing talents and also with the
structure to your weblog. Is that this a paid subject or
did you modify it your self? Anyway keep up the nice high quality writing, it is rare to peer a great weblog like this one these days.
Here is my web page – bathroom tiles rate in chennai super
I’m impressed, I must say. Seldom do I encounter a blog that’s both equally educative
and interesting, and let me tell you, you have hit the nail on the head.
The issue is an issue that too few folks are speaking
intelligently about. I am very happy I found this in my hunt for something concerning this.
This website definitely has all the information I needed
concerning this subject and didn’t know who to ask.
Final month, Powerball added a Monday drawing to its
weekly lineup off Wednesday and Saturday evening drawings.
Also visit my web site: 파워볼분석
For newest news you have to go to see the web and on web I found this website as a finest site
for hottest updates.
I’ve been exploring for a little bit for any high-quality articles or weblog
posts on this kind of space . Exploring in Yahoo I at last stumbled upon this website.
Studying this information So i am happy to exhibit
that I’ve a very good uncanny feeling I came upon just what I needed.
I most no doubt will make certain to do not omit this website and provides it a look on a relentless basis.
Great article! We are linking to this particularly great
post on our website. Keep up the great writing.
Just wish to say your article is as astonishing. The clearness in your post is just
spectacular and i could assume you’re an expert on this subject.
Well with your permission let me to grab your feed
to keep up to date with forthcoming post. Thanks a million and please continue the rewarding work.
I’ve read some excellent stuff here. Certainly worth bookmarking for revisiting.
I wonder hoow much attempt you put to make this type of fanyastic informative website.
My webpage :: starfrit bathroom scale manual
Hello There. I found your weblog the use of msn. That is
a really neatly written article. I’ll make sure to bookmark
it and come back to read extra of your useful info. Thank
you for the post. I will certainly return.
I constantly spent my half an hour to read this web site’s articles daily along with a mug of coffee.
hi!,I love your writing very much! percentage we keep in touch extra approximately your
article on AOL? I require an expert in this space to unravel my problem.
May be that’s you! Having a look forward
to peer you.
What’s up to every one, it’s in fact a pleasant for me to go to
see this web page, it consists of priceless Information.
I like it when people come together and share views. Great website, keep it up!
I’m no longer positive the place you’re getting your info, however good
topic. I must spend a while finding out much more or working out more.
Thank you for fantastic info I used to be in search of
this information for my mission.
I am just commenting to make you know what a awesome experience
my wife’s child developed viewing your webblog. She learned several details, which include what it is like to possess a very effective
giving mindset to have many people without difficulty learn various
impossible matters. You truly surpassed oour
expectations. I appreciate you for producing such practical, dependable,
edifying and cool guidance on your topic to Evelyn.
my blog post – gpd bathroom & kitchen faucets
Way cool! Some extremely valid points! I appreciate
you writing this article and also the rest of the site is also very good.
Wow, this article is nice, my sister is analyzing these kinds
of things, so I am going to let know her.
The safety measures price approximately $9 million, including the hotel
rooms.
Hello would you mind letting me know which hosting company you’re working with?
I’ve loaded your blog in 3 different browsers and I must say this blog loads a lot quicker then most.
Can you suggest a good hosting provider at a honest price?
Thanks a lot, I appreciate it!
You really make it seem so easy with your presentation but I find this topic to be really
something which I think I would never understand. It seems too complex and very broad for me.
I’m looking forward for your next post, I’ll try to get the
hang of it!
Have you ever thought about writing an ebook or guest authoring on other blogs?
I have a blog centered on the same subjects you discuss and would really like to
have you share some stories/information. I know my audience would enjoy your
work. If you’re even remotely interested, feel free to shoot me an email.
As the admin of this website is working, no uncertainty very quickly it will be famous, due to its quality contents.
Hey, I think your blog might be having browser compatibility issues.
When I look at your blog in Chrome, it looks fine but when opening in Internet Explorer,
it has some overlapping. I just wanted to give you a
quick heads up! Other then that, terrific blog!
Hi there, this weekend is fastidious in support of me, as this occasion i am reading this impressive educational post here at my house.
Feel free to surf too my web site – rose gold bathroom accessories amazon
When some one searches for his necessary thing, so
he/she needs to be available that in detail, thus that
thing is maintained over here.
Worlldwide Tour Travel (WTT) ช้อป ผลิตภัณฑ์ออนไลน์ กับ Lazaada Shopee Priceza Accesstrade ได้แล้ววันนี้
Feel free to surf to my webpage – worldwidetourtravel
Thank you for the good writeup. It in truth was once a
enjoyment account it. Look complicated to more introduced agreeable from you!
By the way, how could we keep in touch?
If we spoke about what kind of business sequestration lawyer takes
administration of the financial info on business,
we indicated that the attorney uses the details to aid the company.
อย่าห้าวให้มากไอ้เด็กเหี้ย
Terrific work! This is the kind of information that should be shared around the internet.
Shame on Google for now not positioning this put up upper!
Come on over and seek advice from my site .
Thank you =)
Touche. Outstanding arguments. Keep up the good effort.
Wonderful blog! I found it while searching on Yahoo
News. Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem
to get there! Thanks
Good day! I simply want to offer you a huge thumbs up for your excellent
information you have here on this post. I am
coming back to your web site for more soon.
Thanks for the sensible critique. Me and my neighbor were just preparing
to do some research about this. We got a grab a book from our area library but I think
I learned more clear from this post. I’m very glad to
see such wonrerful info being shared freely out
there.
Look into my webpage; free standing bathroom vanity unit;
Quinn,
Howdy! I simply want to give you a huge thumbs up for the great information you have got right here on this post.
I’ll be coming back to your web site for more soon.
Also visit my webpage … bathroom cabinet ideas toilet
Hi, There’s no doubt that your blog may be having
internet browser compatibility issues. Whenever I look at your blog in Safari, it looks fine but when opening in I.E.,
it’s got some overlapping issues. I simply wanted to give you a quick heads up!
Other than that, fantastic website!
This website was… how do I say it? Relevant!! Finally I have found something which helped me.
Appreciate it!
I quite like reading an article that will make people think.
Also, thanks for permitting me to comment!
Please let me know if you’re looking for a article author for
your site. You have some really good articles and I think I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to write some material for your
blog in exchange for a link back to mine. Please shoot me an e-mail if interested.
Thanks!
Sweet blog! I found it while searching on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Many thanks
Hi Dear, are you in fact visiting this website on a regular basis, if so after that you
will absolutely get good know-how.
Just desire to say your article is as astounding.
The clarity in your post is just cool and i could assume you are an expert on this subject.
Well with your permission let me to grab your RSS feed to keep up to date with forthcoming post.
Thanks a million and please carry on the enjoyable work.
Hi to every one, it’s truly a nice for me to go to see
this web site, it includes helpful Information.
I do not even know how I ended up here, but I thought
this post was good. I don’t know who you are but definitely you’re going to a famous blogger if you aren’t already 😉 Cheers!
Hi, i believe that i noticed you visited my blog thus i got here to go
back the desire?.I’m attempting to to find things to improve my
site!I suppose its good enough to use a few of your ideas!!
I’m not sure where you are getting your info, but good topic.
I needs to spend some time learning much more or understanding more.
Thanks for excellent info I was looking for this information for my mission.
Other new additions include Mamoudou Athie, Dichen Lachman, Scott Haze,
and Campbell Scott, appearing alongside returning forged members BD Wong, Justice Smith, Daniella Pineda, and Omar Sy.
Spot on with this write-up, I absolutely feel this
website needs a great deal more attention. I’ll probably be returning to see more, thanks for the information!
Hey there! This is my 1st comment here so I just wanted to give a
quick shout out and say I genuinely enjoy reading through your blog posts.
Can you suggest any other blogs/websites/forums that deal with the same topics?
Many thanks!
Do you have a spam issue on this blog; I also am a blogger, and I was wanting to know
your situation; many of us have developed some nice methods and we are looking to
trade solutions with other folks, please shoot me an email if interested.
Good response in return of this query with genuine arguments
and telling all about that.
My blog – best bathroom design apps
Everything is very open with a really clear explanation of
the challenges. It was truly informative. Your site is useful.
Thank you for sharing!
Hey there! I’m at work surfing around your blog from my new iphone!
Just wanted to say I love reading through your blog and
look forward to all your posts! Carry on the superb work!
Wow, this article is fastidious, my sister is analyzing these things,
so I am going to inform her.
Everyone loves what you guys tend to be up too. This kind of clever work and reporting!
Keep up the amazing works guys I’ve incorporated you guys to my own blogroll.
My brother suggested I might like this web site. He was entirely right.
This post actually made my day. You can not imagine
simply how much time I had spent for this info!
Thanks!
Hi there, after reading this amazing article i am
too cheerful to share my experience here with colleagues.
It’s going to be finish of mine day, except before end I am reading this great paragraph
to increase my know-how.
Heya! I just wanted to ask if you ever have any trouble with hackers?
My last blog (wordpress) was hacked and I ended up losing several weeks of hard work due to no data backup.
Do you have any methods to stop hackers?
What’s up, all is going perfectly here and ofcourse every
one is sharing information, that’s in fact good, keep up writing.
If some one desires to be updated with newest technologies
then he must be go to see this web page and be up to date every
day.
Its not my first time to pay a quick visit this site, i am visiting this website dailly and get good data from
here daily.
my webpage https://mmpenglish.com/
Highly descriptive article, I liked that bit. Will there be a part 2?
My webpage – bathroom tile ideas with grey vanity (wrcbtv.Com)
We’re a gaggle of volunteers and opening a new scheme in our community.
Your website offered us with helpful information to work on. You have done a
formidable process and our entire community will likely be grateful to you.
BestLoveSexDoll.com – THE BEST SEX DOLLS ONLINE STORE IN USA, UK, EU & CANADA. FREE Shipping Worldwide! 3-15 Days Arrive! Best Quality and Reviews! Build and Customize your Lifelike Sex Doll Robot. SAFE and DISCREET Shipping. High-quality sexy love doll for sale. Based in USA and 24/7 Live Support! Order yours today!
#1 World Best Sex Dolls Online Store – Real Sex Love Doll https://realsexlovedoll.com – aims to build a reliable platform to provide premium real sex dolls for customers. Below is a detailed manual to lead you to the best sex dolls. If you are interested in sex dolls but still hesitate whether to have a try, or if you decide to purchase one, but you have no idea of how to choose, this manual can help! Come and choose a quality doll that meets your satisfaction. There’s a brand-new world waiting for you!
Our lifelike cheap sex dolls – https://cherrypiesexdoll.com – for sale are made of premium silicone and TPE materials to give new real dolls lifelike soft skin and guarantee a realistic feeling. In addition, our hot love dolls are equipped with a human-like metal skeleton and flexible joints, which can support anal sex, oral sex, vagina sex. Besides, every sex doll is handmade by our excellent professions, and we strictly control each process, aiming to bring you lifelike sex dolls and the best sex experience.
If you’re looking for the best affordable sex dolls, you’ve come to the right place. https://www.milfsexdoll.com/. We can customize a large number of full size TPE & silicone sex dolls for you. Our life size love dolls are designed to provide the best sex experience for men and women who need wild and exciting sex. We have a real sex doll factory, we have good cooperation and interaction with other adult factories, which means you can get the best quality online at the lowest price and have more customized experience.
Best Reborns is a boutique reborn doll making company established in 2006 and owned by Emma George. We operate in beautiful London in the United Kingdom. https://bestreborns.com/
Welcome to the Best Reborn Baby Dolls Online Shop https://mycutiegifts.com/ – MyCutieGifts : ) We always endeavor to provide our customers with diversified and high-quality products. All gifts are well-designed and made of premium materials, which ensures both the safety and the lifelike experience. Take a reborn baby doll home and you can enjoy special happiness!
MoonPie Reborns is a boutique reborn doll company established in 2010 and operate in beautiful New York in the United States. We stand behind the quality of every real newborn doll, AND we are sure you’ll love them as much as we do – that’s what MoonPie Reborns Promise! https://www.moonpiereborns.com/
Sweet House Reborns is a boutique reborn doll making company https://www.sweethousereborns.com/ established in 2006 and owned by Emma George. We operate in beautiful Kiel in Germany.
Good blog post. I absolutely love this site. Keep writing!
อย่าห้าวให้มากไอ้เด็กเหี้ย
Fantastic beat ! I would like to apprentice while
you amend your website, how can i subscribe for a
blog web site? The account helped me a acceptable deal.
I had been a little bit acquainted of this your
broadcast provided bright clear idea
Thanks for sharing your thoughts on online bathroom design tool nz vanity
tops without sink. Regards
I have read so many content regarding the blogger lovers but
this paragraph is in fact a pleasant post, keep it up.
Hi, all the time i used to check webpage posts here in the early hours in the break of
day, for the reason that i like to learn more and more.
First of all I want to say great blog! I had a quick question that I’d like to ask if
you don’t mind. I was interested to know how you center yourself and
clear your thoughts prior to writing. I have had difficulty clearing my mind
in getting my thoughts out. I do take pleasure in writing
but it just seems like the first 10 to 15 minutes are wasted just trying to figure out
how to begin. Any ideas or hints? Cheers!
Hi! Do you know if they make any plugins to safeguard against hackers?
I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?
Very excellent info can be found on weblog.
Also visit my web-site standard bathroom vanity height nz
cialis tadalafil online paypal tadalafil
You really make it seem so easy with your presentation but I find this topic to be really something which I think I would never understand.
It seems too complex and extremely broad for me. I’m looking forward for your next
post, I will try to get the hang of it!
obviously like your website however you have to take a look
at the spelling on several of your posts. Many of them are rife with spelling issues and I in finding it very
bothersome to inform the truth then again I’ll definitely come again again.
I am in fact delighted to read this webpage posts which
carries lots of helpful facts, thanks for providing these kinds of data.
Peculiar article, exactly what I was looking for.
Good post. I learn something new and challenging
on websites I stumbleupon everyday. It’s always useful to read content from other authors and practice something from
other web sites.
Visit my blog post :: tnt191
Excellent weblog here! Also your web site a lot up
very fast! What web host are you the use of? Can I get your associate hyperlink for your host?
I want my site loaded up as fast as yours lol
Good replies in return of this query with solid arguments and explaining the whole
thing on the topic of that.
Take a look at my website … bathroom designs latest
I genuinely prize your work, Great post.
Look at my blog post :: Quartz Bathroom Vanity Tops Lowes
Great beat ! I would like to apprentice whilst you amend your web site, how could i subscribe for
a blog web site? The account aided me a applicable deal.
I were tiny bit acquainted of this your broadcast offered vibrant clear idea
Magnificent beat ! I would like to apprentice while you amend your web site, how
can i subscribe for a blog website? The account aided me a acceptable deal.
I had been a little bit acquainted of this your broadcast offered bright clear concept
Woah! I’m really loving the template/theme of this site.
It’s simple, yet effective. A lot of times it’s challenging
to get that “perfect balance” between usability and appearance.
I must say you have done a very good job with this.
Additionally, the blog loads very fast for me
on Chrome. Superb Blog!
cevzd
nl7w6
98ko
We’re a bunch of volunteers and opening a new scheme in our community.
Your website provided us with helpful information to work on. You have performed an impressive job and our entire community
will likely be thankful to you.
My relatives all the time say that I am wasting my time here at net, but I know I am getting know-how everyday by reading thes
fastidious articles or reviews.
generic ivermectin cream stromectol australia
https://stromectolgf.online/# stromectol pills
Aw, this was an incredibly good post. Finding the time and actual effort to make a top notch article?
but what silver bathroom accessories set with trash can Isay?
I procrastinate a lot and never seem to get nearly anything
done.
Incredible! This blog looks just like my old one! It’s on a completely different topic but it has pretty much the same page layout and design. Super choice of colors!
Also visit my homepage: mechanical bathroom scales asda
It’s genuinely very complicated in this busy life to listen news on Television, thus I only use the web for that reason, and get the most recent news.
I for all time emailed this web site post page to all my
friends, since if like to read it after that my contacts will too.
Hi, I do think this is a great website. I stumbledupon it
😉 I may revisit once again since i have bookmarked it.
Money and freedom is the best way to change, may you be rich and continue to guide other people.
kunpi
e26bt
hy4o
https://sites.google.com/view/restolin-hair-growth-reviews
You’re so cool! I do not believe I’ve read through something like this before.
So wonderful to discover someone with some unique thoughts on this issue.
Really.. many thanks for starting this up. This web site is something that is needed on the
web, someone with a bit of originality!
stromectol for sale ivermectin uk
It’s actually a nice and helpful piece of info. I’m satisfied that you simply shared this helpful information with us.
Please stay us informed like this. Thank you for sharing.
This is a good tip particularly to those fresh to the blogosphere.
Simple but very accurate information…
Appreciate your sharing this one. A must read
article!
Here is my web page :: bathroom vanity lights polished nickel
What’s up i am kavin, its my first time to commenting anywhere, when i read this post i thought i could also make comment due
to this sensible post.
Have you ever thought about writing an ebook or guest authoring on other
websites? I have a blog based upon on the same ideas yoou discuss and
would love to have you share some stories/information. I know my audience would enjoy your work.
If you are even remotely interested, feel free to shoot me an e-mail.
My web page bathroom remodeling costs per square foot
Thanks for sharing your thoughts about bathroom cabinets argos uk paper (Adalberto) design tool lowe’s appliances.
Regards
Good article. I’m facing a few of these issues as well..
Pretty nice post. I just stumbled upon your weblog
and wished to mention that I have truly loved browsing
your weblog posts. In any case I’ll be subscribing to your
rss feed and I hope you write once more very soon!
Good way of describing, and nice paragraph to get facts concerning my presentation topic, which
i am going to present in university.
Все любят таких людей которые вступают в объединения и делятся своими мыслями.
Хорошый веб-сайт, развивайтесь в том же духе!
Yesterday, while I was at work, my cousin stole my apple ipad and tested to see if it can survive
a 25 foot drop, just so she can be a youtube sensation. My apple ipad is now broken and she has 83 views.
I know this is completely off topic but I had to share it with someone!
I pay a visit daily a few web sites and information sites
to read articles, however this weblog provides feature based posts.
That is a good tip particularly to those fresh
to the blogosphere. Simple but very precise info…
Thanks for sharing this one. A must read post!
Review my blog post … home depot floor tiles prices
Hurrah, that’s what I was seeking for, what a data! present
here at this website, thanks admin of this site.
Thanks for sharing your thoughts on Form for Online
Visa. Regards
Do you mind if I quote a couple of your articles as long as
I provide credit and sources back to your website? My blog site
is in the exact same area of interest as yours and my visitors would genuinely benefit from
a lot of the information you present here. Please let me know if this okay
with you. Thanks a lot!
Have you ever thought about adding a little bit more than just your
articles? I mean, what you say is fundamental and everything.
Nevertheless think of if you added some great graphics
or videos to give your posts more, “pop”! Your content is excellent
but with pics and videos, this site could certainly be one of the most beneficial in its field.
Great blog!
There is definately a lot to find out about this subject. I love all of the points you’ve made.
Excellent post! We will be linking to this great post on our website.
Keep up the great writing.
Hi to every one, as I am truly eager of reading this blog’s post to be
updated on a regular basis. It includes pleasant stuff.
Я больше двух часов искал в интернете
сегодня и не мог найти ни одной познавательной статьи, как
ваша. Мое мнение, если бы все копирайтеры
так красиво делали контент, как вы интернет стал бы намного интереснее.
Greetings from Colorado! I’m bored to tears at work so I decided to browse your site
on my iphone during lunch break. I really like the information you
provide here and can’t wait to take a look when I get home.
I’m shocked at how quick your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyways, great site!
I always emailed this blog post page to all my associates,
as if like to read it next my contacts will too.
Your mode of telling all in this article is truly fastidious, every one
be able to simply be aware of it, Thanks a lot.
This post is actually a nice one it helps new the web visitors,
who are wishing for blogging.
Nice answer back in return of this matter with real arguments and explaining the whole thing on the topic
of that.
Excellent post. I was checking constantly this blog and I’m impressed!
Extremely helpful information particularly the last part :
) I care for such information a lot. I was looking
for this certain info for a long time. Thank you and good luck.
co4zb
vaqfz
9bcz
In Pennsylvania, you can invest in and play the Powerball
on the net.
Also visiit my web-site: 파워볼분석
Other states were California, Georiga, Illinois, Maine,
Neew Jersey and Oregon.
Here is my website; 파워볼분석
Write more, thats all I have to say. Literally, it seems
as though you relied on the video to make your point.
You definitely know what youre talking about, why waste your intelligence on just posting videos to your site when you
could be giving us something informative to
read?
Magnificent beat ! I would like to apprentice while
you amend your web site, how could i subscribe for a blog website?
The account aided me a acceptable deal. I had been tiny bit
acquainted of this your broadcast offered bright clear concept
My web page – เว็บพนัน
Great beat ! I wish to apprentice while you amend your website, how
could i subscribe for a blog web site? The account helped me a acceptable deal.
I had been tiny bit acquainted of this your broadcast provided bright clear concept
Организация, которая стоит за данной конторой, называется MFI investments restricted и
зарегистрирована на Кипре (Никосия).
Also visit my website: 1win официальный сайт; 1winsportkz.com,
You really make it seem really easy along
with your presentation however I find this topic to be actually something that I feel I’d by no means
understand. It seems too complex and very broad for me.
I’m taking a look ahead on your next submit, I’ll attempt to get the grasp of
it!
Touche. Great arguments. Keep up the great effort.
Feel free to visit my web blog; Epik Keto Gummies
Does your site have a contact page? I’m having trouble locating it but, I’d like to send you an e-mail.
I’ve got some suggestions for your blog you
might be interested in hearing. Either way, great blog and I look forward to seeing it
improve over time.
I don’t normally comment but I gotta state regards for the post on this perfect one :D.
Visit my web site grohe bathroom sink faucets brushed nickel
Magnificent goods from you, man. I have understand your stuff previous to and you’re just too fantastic.
I really like what you’ve acquired here, certainly like what you are stating and the way in which you say it.
You make it enjoyable and you still take care of to keep it smart.
I can not wait to read far more from you. This is really a terrific site.
Appreciation to my father who informed me regarding this
blog, this webpage is genuinely awesome.
Stop by my web page เว็บพนันออนไลน์เว็บตรง
I loved as much as you’ll receive carried out right here.
The sketch is tasteful, your authored material stylish.
nonetheless, you command get got an impatience over that you
wish be delivering the following. unwell unquestionably come more
formerly again since exactly the same nearly a lot often inside case you shield this hike.
I all the time emailed this webpage post page to all my contacts,
because if like to read it after that my friends will
too.
Check out my site HerbaPure CBD Review
Heya! I’m at work browsing your blog from my new iphone!
Just wanted to say I love reading through your blog and look forward to
all your posts! Keep up the superb work!
I’m gone to convey my little brother, that he should also pay a visit this blog on regular basis to obtain updated from most up-to-date news.
Hi, i feel that i saw you visited my weblog thus i came to
go back the prefer?.I’m trying to find issues to enhance my web site!I suppose its ok
to make use of a few of your ideas!!
I was wondering if you ever thought of changing
the layout of your blog? Its very well written; I love what
youve got to say. But maybe you could a little more
in the way of content so people could connect with it better.
Youve got an awful lot of text for only having 1 or two pictures.
Maybe you could space it out better?
Greetings! I’ve been following your blog for some time now and finally got the bravery to go ahead and give you a shout out from Kingwood Tx!
Just wanted to tell you keep up the fantastic
work!
If some one wishes expert view about running a blog
after that i propose him/her to pay a visit this web site, Keep
up the fastidious job.
Its such as you read my thoughts! You appear to understand so much about this, such
as you wrote the e-book in it or something.
I feel that you simply could do with some percent to pressure the message house a bit,
however other than that, that is magnificent
blog. A fantastic read. I will certainly be back.
Great post. I used to be checking constantly this weblog and I’m impressed!
Extremely useful information specially the last section :
) I handle such information much. I was looking for
this certain info for a long time. Thank you and best of luck.
Excellent blog! Do you have any helpful hints for aspiring writers?
I’m hoping to start my own blog soon but I’m a little lost on everything.
Would you propose starting with a free platform like WordPress or go for a paid option? There are so many options out there that I’m completely overwhelmed
.. Any ideas? Kudos!
Two extra winners took house $50,000 every with tickets
sold in thee towns of Williamston and Pleasant Hill.
my web-site – Check out here
I always spent my half an hour to read this webpage’s posts all the time along with
a mug of coffee.
Very shortly this site will be famous amid all blog
viewers, due to it’s good content
my homepage – Pro Boost Keto Reviews
Thank you for some other great post. Where else may
just anybody get that type of info in such an ideal means
of writing? I have a presentation subsequent week, and
I’m at the look for such information.
Hi there to every body, it’s my first pay a visit of this web site; this weblog carries awesome and genuinely good information in favor of readers.
Can I simply just say what a comfort to discover an individual who really understands what they are talking about on the
internet. You definitely realize how to bring an issue to light and make it important.
More and more people must read this and understand this side of your story.
I can’t believe you aren’t more popular since you most certainly have the gift.
I’m extremely impressed with your writing skills and also with the layout on your blog.
Is this a paid theme or did you modify it yourself? Either
way keep up the excellent quality writing, it is rare to see a great blog like this one these days.
It’s actually very difficult in this active life to listen news on Television, therefore I simply use world wide
web for that purpose, and obtain the most recent news.
Hello there! I could have sworn I’ve visited this blog before but after looking
at some of the posts I realized it’s new to me. Anyhow, I’m definitely pleased I found
it and I’ll be book-marking it and checking back regularly!
I love your blog.. very nice colors & theme. Did you make
this website yourself or did you hire someone to do it for you?
Plz respond as I’m looking to design my own blog and would
like to know where u got this from. cheers
Hi i am kavin, its my first time to commenting anyplace, when i read this article i thought i could also
create comment due to this brilliant article.
Check out my blog post; สล็อต
Thanks for sharing your thoughts about best 5-light chrome standard bathroom vanity light bar slippers for womens.
Regards
I loved as much as you will receive carried out right here.
The sketch is tasteful, your auythored subject matter
stylish. nonetheless, you command get got an edginess over that you wish be delivering the following.
unwell unquestionably come further formerly again since exactly the same
neazrly a lott often inside caase you shield this hike.
Check oout myy webpage Erection problem
I was wondering if you ever thought of changing the
structure of your website? Its very well written; I love what youve got
to say. But maybe you could a little more in the way of content so people could connect with it better.
Youve got an awful lot of text for only having one
or two images. Maybe you could space it out better?
This is a topic that’s close to my heart… Thank you! Where are your contact details though?
It’s really a cool and helpful piece of information. I am satisfied that you simply
shared this useful info with us. Please keep us up to date like this.
Thank you for sharing.
It’s difficult to find well-informed people about this topic, but you sound like you know what you’re talking
about! Thanks
Take a look at my web page – Kerassentials Review
This piece of writing will help the internet visitors for setting up
new website or even a blog from start to end.
Hi fantastic blog! Does running a blog such as this take a lot of work?
I’ve no understanding of computer programming however I was
hoping to start my own blog soon. Anyways, if you have any suggestions or tips for new blog owners please
share. I know this is off topic however I
just had to ask. Cheers!
Hi there it’s me, I am also visiting this web page on a regular basis, this web page is actually
nice and the people are in fact sharing pleasant thoughts.
What’s up, yeah this paragraph is truly good and I
have learned lot of things from it about blogging.
thanks.
I take pleasure in, lead to I found exactly what I
used to be having a look for. You’ve ended my 4 day
lengthy hunt! God Bless you man. Have a great day. Bye
Feel free to surf to my web-site … bathroom mirror with ledge
Hi there! Do you use Twitter? I’d like to follow you if that would be ok.
I’m undoubtedly enjoying your blog and look
forward to new posts.
Also visit my web site สล็อตเว็บตรง100%
It’s in reality a nice and helpful piece of info.
I’m glad that you just shared this helpful info
with us. Please stay us up to date like this. Thank you for
sharing.
Very shortly this web page will be famous amid all
blog viewers, due to it’s fastidious posts
Unquestionably believe that which you said. Your favorite
reason appeared to be on the net the simplest thing
to be aware of. I say to you, I definitely get irked while people think about worries that they plainly don’t know about.
You managed to hit the nail upon the top and defined out the whole thing
without having side-effects , people can take a signal.
Will probably be back to get more. Thanks
My website: Secret Nature CBDPrice
I have read some just right stuff here. Certainly worth bookmarking for revisiting.
I wonder how so much effort you set to create this kind of excellent
informative web site.
Feel free to visit my blog waterfall bathroom sink faucet (wall mount) (https://www.sitiosperuanos.com/author/megafurnituresg/)
Thanks for the auspicious writeup. It in fact was a amusement account it.
Glance advanced to far added agreeable from you! However, how could
we keep in touch?
The staring amount will now be $20 million and raise by aan amount based on present national sales.
Feel free to surf to my blog … Go to this website
Yi purchased his jackpot-winning ticket from Publix, positioned at North Nebraska Avernue in Lutz.
Also visit my web-site; Visit the website
viagra cialis levitra nl levitra levitra for daily use glaxo levitra
Awesome post.
viibryd zanaflex tizanidine 10 mg what are the side effects of zanaflex how to make meloxicam with zanaflex
Alternatively of a rolling jackpot, Double Play offers a $10 million majmor cash prize.
Feel free to surf to my web-site – Learn more
The hyperlunks on our web site are for entertainment
aand informational purposes only.
Feeel free to surf to my page; Visit this link
Great – I should definitely pronounce, impressed with your site.
I had no trouble navigating through all the tabs as well as related information ended up being truly simple to do to access.
I recently found what I hoped for before you know it at
all. Reasonably unusual. Is likely to appreciate it for those who
add forums or anything, site theme . a tones way for your client to
communicate. Excellent task.
Я больше 4-х часов лазил в интернете
и не мог найти ни одной интересной статьи, как эта.
Мое мнение, если бы все веб-мастера так интересно делали контент, как вы интернет
стал бы намного интереснее.
Very nice post. I just stumbled upon your blog and wished to say
that I have truly enjoyed browsing your blog posts. In any case I will be subscribing to your rss feed and
I hope you write again very soon!
And also Trump reportedly charges British Prime Priest Boris Johnson of “dishonesty” in a warmed telephone call concerning Huawei 5G decision. British Prime Minister Boris Johnson has actually introduced a lockdown for the UK starting Monday night,
with celebrations of greater than two individuals outlawed unless they’re from the
same house, and all non-essential shops as well as many public places closing.
Los Angeles Area additionally needs evidence of inoculation to enter interior bars, bars,
breweries and also vineyards, as well as calls for people age 12 as
well as older to be completely vaccinated prior to getting in any kind of
public interior rooms. The decreasing variety of
COVID-19 cases and also resulting decrease in hospitalization as well as serious condition have motivated some major American cities
to end proof-of-vaccination requirements for dining establishments as well as other indoor public spaces.
Seattle’s King Area additionally chose Wednesday to go
down all vaccination requirements for interior activities and
also big exterior events beginning March 1.
Last week, Minneapolis/St. The Australian head of state, Scott Morrison,
has introduced that stricter lockdown measures will certainly
currently be imposed which the nation’s pubs, dining establishments,
bars, clubs, health clubs and other “superfluous”
solutions will be shut from noontime on Monday, March 23.
Morrison likewise requested all Australians remain residence
unless travel is necessary. And, as you could think:
If you’re an actual stickler for privacy, you might intend to skip every one
of these solutions.
I used to be able to find good information from your content.
Hi there to every one, the contents present at this web site are
in fact amazing for people experience, well,
keep up the good work fellows.
Do you mind if I quote a few of your posts as long as I provide credit and sources
back to your blog? My blog is in the very same niche as yours and my users would certainly benefit from some of the information you present here.
Please let me know if this alright with you. Cheers!
Woah! I’m really loving the template/theme of this website.
It’s simple, yet effective. A lot of times it’s very hard to get that “perfect balance” between superb usability and visual appearance.
I must say you’ve done a fantastic job with this. Additionally, the blog loads very quick for me on Safari.
Outstanding Blog!
Hurrah, that’s what I was seeking for, what a information! present here at this web site, thanks admin of this website.
I’m extremely impressed with your writing skills as well as with
the layout on your blog. Is this a paid theme or did you customize it
yourself? Anyway keep up the excellent quality writing, it’s
rare to see a great blog like this one today.
Gelek4D adalah agen situs slot yang sangat terpercaya diantara situs 303 slot gacor hari ini gampang menang juga untuk permainan joker123
gaming online.
Panasonic, SanDisk and Toshiba formed the SD Association in January 2000
with the goal of growing and selling standards for flash-memory storage.
All the proposed new standards have one thing in frequent.
You will not have to purchase the hardware or sign up for a contract along
with your satellite tv for pc or cable firm for
the device, you won’t need to pay for the service, and you can modify and increase your DVR all you want.
We’ll have a look at some specs and options of a few
of the tablets if you want to check them or give one a try.3 inches (10.9 centimeters) to
10 inches (25.Four centimeters) in size, Craig tablets offer a lot
of the identical options as their larger-end counterparts, in addition to options for storage, speed and multi-media
capabilities. There are some people, often in hemp pants and vegan shoes, who want to get off the grid and stay on the land in harmony with nature.
I like what you guys are usually up too. This sort of clever work and reporting!
Keep up the good works guys I’ve included you guys to my blogroll.
This design is wicked! You obviously know how to keep
a reader amused. Between your wit and your videos, I was
almost moved to start my own blog (well, almost…HaHa!)
Excellent job. I really loved what you had to
say, and more than that, how you presented it. Too cool!
This is very attention-grabbing, You are a very professional blogger.
I have joined your rss feed and look forward to in search of extra of your magnificent post.
Additionally, I have shared your site in my social networks
Cool blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple tweeks would really make my blog stand
out. Please let me know where you got your theme. With thanks
Wonderful website. Lots of useful info here. I’m sending
it to a few friends ans additionally sharing in delicious.
And naturally, thank you on your sweat!
Everyone loves what you guys are usually up too. This kind
of clever work and exposure! Keep up the great works guys I’ve you guys to blogroll.
Fantastic blogց you have here Ƅut I wass wanting to knw
іf you knew of any c᧐mmunity forfums that cover the
same topics ⅾiscussed here? I’d гeallpy like to be a part of оnline community where I can get comments from other knowledgеable people that share the ѕsme interest.
If yоu have any suggestions, please let me know.
Bless you!
hello there and thank you for your info – I have certainly picked up anything new from right here.
I did however expertise several technical points using this website, as I experienced to reload the web site a lot of times previous to I could get it
to load properly. I had been wondering if your hosting is OK?
Not that I am complaining, but slow loading instances times will
often affect your placement in google and could damage your quality score if advertising and marketing with
Adwords. Well I’m adding this RSS to my email and could look out for a lot more of your respective intriguing content.
Make sure you update this again very soon.
I visited several web sites but the audio feature
for audio songs current at this website is genuinely superb.
Brilliant post and useful information. I think this is what I read
somewhere but I dont know with your experience
Good day I am so excited I found your web site,
I really found you by mistake, while I was researching on Digg
for something else, Nonetheless I am here now and would just like to say thanks a lot for
a remarkable post and a all round exciting blog (I also love the theme/design), I
don’t have time to go through it all at the minute but
I have book-marked it and also added in your RSS feeds, so when I have
time I will be back to read a lot more, Please do keep up the fantastic
job.
levitra 20 ml levitra no prescription what is the drug levitra used for levitra efectos secundarios
Wow, wonderful blog layout! How long have you been blogging
for? you made blogging look easy. The overall look of your website is great, as well as the content!
kamagra south africa what is in kamagra kamagra 100 mg oral jelly reviews how to take kamagra oral jelly
Check Out This Before Taking Up movie review
My partner and I absolutely love your blog and find a lot of
your post’s to be precisely what I’m looking
for. Does one offer guest writers to write content for you personally?
I wouldn’t mind producing a post or elaborating on some of the subjects you write
related to here. Again, awesome weblog!
Everyone loves what you guys are usually up
too. This type of clever work and reporting! Keep up the excellent works guys I’ve incorporated you guys to blogroll.
Howdy I am so happy I found your blog, I really
found you by error, while I was researching on Askjeeve
for something else, Anyways I am here now and would just like to say
thanks for a tremendous post and a all round interesting blog (I also love the
theme/design), I don’t have time to look over it all at the moment but I have bookmarked it and also included your RSS feeds,
so when I have time I will be back to read a great deal more, Please do keep
up the fantastic work.
Ridiculous story there. What occurred after? Thanks!
Walaupun punya banyak kolaborasi bersama dengan perusahaan lainnya, website slot gacor YGGDrasil tetap tanpa lengah menyaring serta memastikan jika segala operasional yang mereka
miliki masih ada sesuai regulasi ijin resmi
dan mereka juga punya etika judi sesuai dengan peraturan yang berlaku.
Produk permainan slot dari YGGDrasil lebih mengutamakan kesenangan dari playernya sesuai
dengan system pemahaman bakal kepuasan klien.
Didalam daftar pertama daripada game judi slot deposit Shopeepay gacor 2021 ini adalah Wild West
Gold.
Hello my family member! I want to say that this post is amazing, great written and include almost all significant infos.
I’d like to see extra posts like this .
It is in reality a nice and helpful piece of information. I am glad that you just shared this useful info with us.
Please keep us up to date like this. Thanks for sharing.
Remarkable! Its genuinely remarkable piece of writing,
I have got much clear idea on the topic of from this article.
Hurrah! Finally I got a web site from where I be able to actually get
helpful data regarding my study and knowledge.
Quality articles or reviews is the main to invite
the viewers to pay a quick visit the web site, that’s what this web site is providing.
Useful information. Lucky me I found your website accidentally, and I’m shocked
why this accident did not happened in advance! I bookmarked it.
excellent points altogether, you simply gained a logo new
reader. What might you recommend about your submit that you made some days
in the past? Any certain?
You are my inhalation, I have few blogs and often run out from post :
).
My site: Sea Vital Skin Anti Aging Gummies
I don’t know if it’s just me or if everybody else experiencing
problems with your website. It appears as though some of the written text within your content are running off the screen. Can somebody else please comment and let me
know if this is happening to them too? This may be a issue with my web browser because I’ve had this happen previously.
Thanks aid for ukraine
Good post. I’m experiencing some of these issues as well..
My web site; https://slot99ku.home.blog/
So why is Doctor Strange the identical man, bar various facial hair and ponytails?
Most events we checked out provided between 10 and 33 markets, which usually
depended on the importance of the events.
Here is my web-site pin-up casino app download apk
I usually do not leave a response, but I looked at some of the comments here CONFIGURING SSL AUTHENTIFICATION –
Benson Yerima. I do have a couple of questions
for you if you do not mind. Could it be only me
or does it look like a few of the responses look like they are coming from brain dead folks?
😛 And, if you are writing on additional
online sites, I would like to keep up with you. Could you post
a list of the complete urls of all your public
pages like your linkedin profile, Facebook page or twitter feed?
Here is my web-site … Sea Vital Gummies Review
I am sure this post has touched all the internet
visitors, its really really nice article
on building up new blog.
Hi there, I enjoy reading all of your post. I like to write
a little comment to support you. https://ads.massagemehomeservices.com/index.php?page=user&action=pub_profile&id=2369664
It is the best time to make some plans for the longer term and it’s time to be happy.
I have read this submit and if I may I wish to counsel you few interesting issues
or suggestions. Perhaps you could write next articles regarding this article.
I wish to learn more things approximately it!
I was able to find good info from your blog posts.
My family members every time say that I am wasting
my time here at web, however I know I am getting know-how everyday by reading such nice articles.
sildenafil with dapoxetine priligy 30mg uk super p force sildenafil dapoxetine how do i take dapoxetine liquid?
albuterol inhaler dosage buy cheap ventolin online can you buy albuterol over the counter how long does albuterol stay in your system
It’s truly very complex in this busy life to listen news on Television,
therefore I simply use web for that reason, and take the latest news.
Hi there mates, fastidious piece of writing and nice urging commented at this place, I am in fact enjoying by these.
Hi there to all, as I am truly keen of reading this blog’s post to be updated daily.
It consists of nice data.
It’s perfect time to make some plans for the future and it’s time to be happy.
I have read this post and if I could I desire to suggest you few
interesting things or tips. Perhaps you could write next articles referring to
this article. I want to read more things about it!
A person essentially lend a hand to make seriously articles I’d state.
That is the very first time I frequented your
web page and so far? I amazed with the research you made to make
this actual post extraordinary. Magnificent process!
Ι ҝeep listening tto tһe news update lecture аbout
getting free online grant applications so Ӏ have been lookinhg around for thee
bеst site tоο geet օne. Could уⲟu tell me plеase,
where could i get some?
GTRBET คาสิโน หวย กีฬา
Gtrbet88 (http://Www.Quintonpotter.Com/__Media__/Js/Netsoltrademark.Php?D=Gtrbet88.Com) เว้นแต่ว่าเกมคาสิโน พวกเรายังเปิดให้เล่นพนันกีฬากว่า 20 จำพวก ไม่ว่าจะเป็นพนันกีฬามหาชลอย่างบอลที่ไม่ให้เลือกพนันทุกแบบอย่าง ไม่ว่าจะเป็น บอลผู้เดียว บอลเสต็ป เริ่มอย่างน้อยแค่เพียงเสต็ป 2 ที่ 50
บาท สำหรับผู้ที่รักสำหรับในการพนันปริมาณ เราก็มีลอตเตอรี่ออนไลน์ให้เล่น ทั้งยังล็อตเตอรี่ไทย ล็อตเตอรี่ รวมถึงล็อตเตอรี่ลาวและคีโน่
Thank you, I have recently been searching for info about this topic for ages and yours is the greatest I’ve found out till now.
However, what about the bottom line? Are you positive concerning the supply?
Hi, Neat post. There’s an issue along with your website in web explorer, could check this?
IE still is the market leader and a good portion of people
will miss your wonderful writing due to this problem.
Hello! I know this is kinda off topic nevertheless I’d figured I’d ask.
Would you be interested in exchanging links or maybe
guest writing a blog article or vice-versa? My site covers a lot of the same subjects as yours
and I feel we could greatly benefit from each other.
If you are interested feel free to shoot me an e-mail.
I look forward to hearing from you! Fantastic blog by the way!
It’s awesome in favor of me to have a web page, which
is helpful for my experience. thanks admin
I enjoy what you guys are up too. This sort of clever work and reporting!
Keep up the fantastic works guys I’ve incorporated you guys to blogroll.
My brother suggested I might like this blog.
He used to be entirely right. This put up actually made my day.
You cann’t believe simply how much time I had spent for
this information! Thanks!
Hi! I just want to offer you a big thumbs up for the excellent info you have
got here on this post. I will be returning to your site
for more soon.
Simply desire to say your article is as astonishing.
The clearness in your post is simply nice and i could assume
you are an expert on this subject. Well with your permission let me
to grab your feed to keep up to date with forthcoming post.
Thanks a million and please continue the rewarding work.
Your style is very unique compared to other people I have read stuff from.
Thanks for posting when you’ve got the opportunity, Guess I’ll just bookmark
this web site.
At this time it sounds like Drupal is the top blogging platform out
there right now. (from what I’ve read) Is that what
you’re using on your blog?
Appreciate the recommendation. Let me try it out.
I’ve been surfing online more than 2 hours today, yet I never found any interesting article like
yours. It’s pretty worth enough for me. In my view,
if all site owners and bloggers made good content
as you did, the web will be a lot more useful
than ever before.
Мне нравится такие сообщества которые собираются и делятся своими мыслями.
Хорошый блог, развивайтесь в том же духе!
hello!,I like your writing so much! share we keep up a correspondence extra about your post
on AOL? I need an expert on this house to resolve my problem.
Maybe that’s you! Having a look ahead to see you.
Highly descriptive blog, I liked that a lot. Will
there be a part 2?
After looking at a handful of the blog posts on your website, I seriously like your way of blogging.
I bookmarked it to my bookmark webpage list and will be checking back soon. Please visit my website too and let me know what you
think.
Its such as you read my thoughts! You seem to know a lot approximately
this, like you wrote the guide in it or something. I believe that
you can do with a few percent to force the message house a bit,
but other than that, that is great blog. A fantastic read.
I’ll definitely be back.
Hello all, here every person is sharing these knowledge, thus it’s good to read this webpage,
and I used to go to see this blog every day.
I’d like to find out more? I’d care to find out some additional information.
At this moment I am going to do my breakfast, when having my breakfast coming again to read
more news.
Its such as you read my mind! You appear to grasp
so much about this, such as you wrote the e book in it or something.
I feel that you just could do with some p.c. to pressure the message
house a little bit, but instead of that, that is magnificent blog.
A great read. I will certainly be back.
Terrific work! This is the type of info that are supposed to
be shared around the net. Disgrace on the seek engines for not positioning
this submit upper! Come on over and visit my website . Thanks
=)
Hey I know this is off topic but I was wondering if you knew of any widgets I
could add to my blog that automatically tweet my newest
twitter updates. I’ve been looking for a plug-in like this for quite some
time and was hoping maybe you would have some experience with
something like this. Please let me know if you run into
anything. I truly enjoy reading your blog and I look
forward to your new updates.
Write more, thats all I have to say. Literally, it seems as though
you relied on the video to make your point. You definitely know what youre
talking about, why waste your intelligence on just posting
videos to your site when you could be giving us something enlightening to read?
I seriously love your blog.. Pleasant colors & theme.
Did you create this web site yourself? Please reply
back as I’m trying to create my own personal site and would
love to learn where you got this from or just what the theme is
called. Kudos!
My partner and I absolutely love your blog and find nearly all of
your post’s to be what precisely I’m looking for. Would
you offer guest writers to write content for yourself? I wouldn’t mind composing a post or elaborating
on a few of the subjects you write in relation to here.
Again, awesome weblog!
Management at Beech Mountain Resort told WBTV-Tv that a guest skid into
the watfer and air hydrant Friday when snowmaking
operations have been underway.
Also visit my homepage … Click here for more info
latisse santa barbara lumigan eye drop price is latisse covered by insurance where can i buy latisse cheap
I was suggested this blog by my cousin. I’m not sure whether this post is
written by him as nobody else know such detailed about
my difficulty. You are amazing! Thanks!
Hi there, this weekend is pleasant in favor of me, for the
reason that this moment i am reading this enormous informative post here at
my home.
clomid success stories where can i buy clomid from buying clomid online success stories where can i buy clomid in canada
I’m not sure why but this website is loading very slow
for me. Is anyone else having this issue or
is it a issue on my end? I’ll check back later and see if the problem still exists.
Numerous winners wait a period of time tto get their monetary
affairs in order just before coming forward.
Also visit my site – Check out the post right here
Hello there! This post couldn’t be written any better! Reading through this post reminds me of my previous roommate!
He always kept preaching about this. I’ll forward this information to him.
Fairly certain he will have a great read. I appreciate you for sharing!
It’s awesome for me to have a website, which is valuable in support of my
experience. thanks admin
You agree thhat you will not attempt to deny, reverse, charge back, re-credit, block, or otherwise
try to invalidate, recover, oor deny the Rhode
Island Lottery receipt of a deposit.
My homepage; Click here
Oh my goodness! Incredible article dude! Thank you so much,
However I am having problems with your RSS. I don’t know why I am unable to subscribe to it.
Is there anyone else having similar RSS issues? Anybody who knows the solution can you kindly
respond? Thanks!!
Have you ever considered creating an e-book or
guest authoring on other blogs? I have a blog based on the same topics
you discuss and would really like to have you share some stories/information. I know my audience would value your
work. If you are even remotely interested, feel free to shoot me
an e-mail.
Just wish to say your article is as amazing. The clearness in your post is just excellent and i could assume you
are an expert on this subject. Well with your permission let me to grab your RSS feed to keep up to date with forthcoming post.
Thanks a million and please continue the enjoyable work.
Right now it seems like BlogEngine is the top blogging platform available right now.
(from what I’ve read) Is that what you are using
on your blog?
Hey There. I found your blog using msn. This is
a very well written article. I will be sure to bookmark it and return to read more of your useful info.
Thanks for the post. I will definitely return.
Система Labouchere отличается от большинства
игровых стратегий тем, как
она формируется и функционирует.
Stop by my site; aviator игра на деньги официальный сайт (https://1win-sports.com/)
I’m not sure exactly why but this weblog is loading extremely slow for me.
Is anyone else having this problem or is it a issue on my end?
I’ll check back later on and see if the problem still exists.
The full-time mother assured the winnings will not modify who she is as a particullar person.
my web-site; Discover more
Everyone loves it whenever people get together and share ideas.
Great website, stick with it!
Doubles the Match 5 prize and increases other non-jackpot prizes 2X, 3X, 4X, 5X
or 10X for an added $1 per play.
My webpage Find more info
It’s hard to find experienced people in this particular
subject, however, you seem like you know what you’re
talking about! Thanks
A $two million winning ticket and three $1 million tickets had been sold in Florida.
My website Check out here
It’s going to be finish of mine day, however before finish I am reading this fantastic article
to increase my know-how.
Meanwhile, the Mega Millions jackpot was at $56 million with
a cash alternative of $38.three million,according to tthe Mega Millions website.
Also visit my homepage; check here
I enjoy what you guys tend to be up too. This sort of clever work and coverage!
Keep up the very good works guys I’ve incorporated you
guys to my blogroll.
The winning ticketholder will split last night’s substantial $632.six million jackpot with someone
from California.
My blog Hop over to this website
Thee quantity the prrize is multiplied is selected at the time of the
drawing.
Also vsit my homepage: The original source
Fascinating blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple adjustements would really make my blog shine.
Please let me know where you got your theme. Many thanks
Thanks on your marvelous posting! I really enjoyed reading it,
you might be a great author. I will remember to bookmark your blog and will come back down the road.
I want to encourage that you continue your great work,
have a nice evening!
If you live in Brownsville and purchased a ticket for Wednesday night’s Powerball drawing you
are going to want to check that ticket.
my site – Helpful resources
14-year-old higher college freshman Vania Martinez, from Wilmington, won $125,000 toward
post-secondary education.
Heere is my web site; Additional hints
— Rain is moving in and will be with us this evning
and overnight.
Here is my website – Helpful hints
Presented by Caesars Sportsbook, Chris Williamson and Joohn Jastremski look ahead to Monday night’s College Football’s National
Championship game involving Georgia and Alabama.
My page: Learn more
Very shortly this website will be famous among all blogging
and site-building users, due to it’s fastidious articles or reviews
This is the perfect webpage for anyone who would like to
find out about this topic. You realize so much its almost hard to argue with you
(not that I personally will need to…HaHa). You certainly put a fresh spin on a topic
that has been written about for many years. Great stuff, just excellent!
Write more, thats all I have to say. Literally, it seems
as though you relied on the video to make your point.
You obviously know what youre talking about, why waste your intelligence on just posting videos to your site when you could be
giving us something enlightening to read?
The press conference was caarried on reside tv
and featured a throng of reporters and photographers worthy of
a presidential take a look at.
Also visit my web page; Find more information
Somebody essentially assist to make critically posts I
might state. That is the first time I frequented
your website page and thus far? I amazed with the analysis you made to create this
particular submit extraordinary. Excellent task!
The $50,000 tickets matched 4 white balls and the Powerball, beating odds of 1 in 913,
129.
Feel free to surf to my bllog Go to the website
Hurrah! At last I got a web site from where I can in fact get useful data
regarding my study and knowledge.
Choose the Claim Form up at any Lottery retail place, District Office or download the kind .
My web blog – Find out more
Hi there, I enjoy reading through your article post.
I wanted to write a little comment to support you.
A fortunate Wisconsin winner from the January 5, 2022, Powerball drawing hit a main jackpot!
Also visit my website; Great post to read
Hi there, i read your blog occasionally and i own a similar one and i was just curious if
you get a lot of spam feedback? If so how do you prevent it, any
plugin or anything you can advise? I get so much lately it’s driving me insane so
any assistance is very much appreciated.
This is very attention-grabbing, You are a very professional blogger.
I have joined your rss feed and sit up for in quest of more of your fantastic post.
Additionally, I’ve shared your web site in my social networks
Greetings! I’ve been following your website for a while now and finally got the bravery
to go ahead and give you a shout out from Dallas Tx! Just wanted to tell you
keep up the excellent job!
Howdy would you mind stating which blog platform you’re working with?
I’m planning to start my own blog soon but I’m having a difficult time choosing between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your layout seems different then most blogs and I’m looking for something completely unique.
P.S Apologies for getting off-topic but I
had to ask!
My website :: DermaFleur Cream
Hello, Neat post. There is a problem together with your site in internet
explorer, would check this… IE still is the marketplace chief
and a good part of people will miss your excellent writing due to
this problem.
my web-site … Mother Nature’s CBD Gummies Review
The Florida Lottery is excited to announce the restricted-time Powerball Firfst Millionaire of
the Year Promotion.
Also visit my homepage :: more info
She hoped to spread the woird about thhe situation, as nicely as give some
of her winnings to religious and charitable organizations.
My website :: Visit this site
Everything is very open with a really clear explanation of the issues.
It was truly informative. Your website is very helpful. Thank you for sharing!
I think this is among the most vital info for me.
And i’m glad reading your article. But wanna remark on few general things, The site
style is wonderful, the articles is really great : D. Good job, cheers
I’m impressed, I must say. Rarely do I encounter a blog that’s equally educative and entertaining, and let me tell you, you’ve hit the nail on the head.
The issue is something which not enough men and
women are speaking intelligently about. I’m very happy I found this in my search for something regarding this.
Two ticketys sold in Connecticut and Texas won $1 million, and a
ticket in Montana had the Powerplay to win $2 million.
my blog – The original source
Powerbzll may possibly intentionally alter the quantity of balls in play to
tweak the odds.
my page – Learn here
Thank you for the auspicious writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you! However, how
could we communicate?
Excellent beat ! I would like to apprentice whilst you amend your site, how can i subscribe for a weblog web site?
The account aided me a appropriate deal. I had been a little bit familiar of this
your broadcast provided vivid clear idea
Players pick 5 white balls, numbered 1 by way of 69, and a siongle Powerball, numbered 1 by way of 26.
Check out my web site … Discover more
Heya i am for the first time here. I found this board and I find It truly useful & it helped me out a lot.
I hope to give something back and help others like you helped me.
digoxin furosemide lasix prescription push lasix slow to avoid tinnitus a health care professional is caring for a patient who takes furosemide
Everything is very open with a really clear description of the
challenges. It was truly informative. Your website is useful.
Many thanks for sharing!
Hi, i think that i saw you visited my web
site thus i came to “return the favor”.I’m attempting to find things to improve my web site!I
suppose its ok to use some of your ideas!!
I would like to thank you for the efforts you’ve put in writing this site.
I really hope to check out the same high-grade blog posts by you in the future
as well. In fact, your creative writing abilities has inspired me to get my own, personal
website now 😉
You hereby authorize the Rhod Island Lottery to hold
andd gather aany amount owed to thee Rhode Island Lottery as a outcome of anny such costs or penalties
from you deposits or winnings.
my site … get more info
Very great post. I just stumbled upon your weblog and
wanted to say that I have truly loved browsing your weblog posts.
In any case I’ll be subscribing to your feed and I hope you write
once more very soon!
Holmes plans to give basck tto the community, spercifically to the church
and to cerebral palsy organizations.
Take a lok at my web blog :: Click for source
Power Play is an selection you can add to your ticket that multiplies the value of the non-jackpot prizes you win.
Feeel free to surf to my web site: Browse around this site
The jackpot ranks as the 7th biggest in Powerball history.
My blog – Click here for more info
Why visitors still make use of to read news papers when in this technological globe all is accessible on net?
Thank you for any other informative website. Where else may I
get that type of information written in such an ideal method?
I’ve a undertaking that I’m just now operating on,
and I have been at the glance out for such information.
An impressive share! I’ve just forwarded this onto a co-worker who was conducting a little homework on this.
And he actually bought me breakfast simply because I found it for him…
lol. So let me reword this…. Thanks for the meal!!
But yeah, thanks for spending some time to discuss this issue here on your site.
Pretty great post. I just stumbled upon your weblog
and wished to mention that I’ve truly enjoyed surfing around your weblog posts.
After all I’ll be subscribing in your rss feed and I’m hoping you write once more soon!
Commission for payments on the proper part of the site is not charged, but it can be provided
My website: pinup app
Lefty Grove was elected tto the Baseball Hall of Fame in 1947, aand dird in 1975.
Here iss my blog; Visit this page
I savour, lead to I discovered just what I was having a
look for. You’ve ended my 4 day long hunt! God Bless you man. Have a nice day.
Bye
Hi there! I know this is kind of off-topic but I had to
ask. Does operating a well-established website such as
yours require a massive amount work? I am brand new to operating a blog but
I do write in my diary daily. I’d like to start a blog
so I can easily share my experience and feelings online.
Please let me know if you have any kind of suggestions or tips for brand new aspiring bloggers.
Appreciate it!
It’s a pity you don’t have a donate button! I’d most certainly donate to this excellent blog!
I guess for now i’ll settle for book-marking and adding your RSS feed to my Google account.
I look forward to fresh updates and will share this blog with
my Facebook group. Talk soon!
Article writing is also a fun, if you be acquainted with after that you can write otherwise it is complicated
to write.
If you wish for to obtain much from this article then you have to apply such techniques to your won weblog.
JACKSONVILLE, Fla. – The individual who purchased a $286 million winning Powerbal ticket at a Circle K on the Westside nevertheless hasn’t
come forward tto claim the prize.
my web blog; The original source
Kaltschmidt statesd he didn’t believe it when his wife tolpd him they have
been winners.
Here is my blog; The original source
Hi there! I just wanted to ask if you ever have any problems with hackers?
My last blog (wordpress) was hacked and I ended up
losing many months of hard work due to no data backup.
Do you have any solutions to protect against hackers?
Ꮤe tһіnk y᧐ur ⅽߋntent іts ɡгeаt kеep ⲣߋѕtіng
The final time somebody hit the jackpot was Oct. 4 iin California, winning $699.eight million.
Feel free to surf to my web site –You can find out more
Wow! Finally I got a website from where I be capable of in fact obtain useful information regarding my study and knowledge.
Good respond in return of this query with solid arguments and telling the whole thing regarding that.
There have been 39 drawings in a row with no jackpot winner.
Also visit my site :: Visit website
You caan select Rapid Pick for any or alll of the 5
numbers in thhe upper panel and/or the 1 number in the
reduced panel.
Also vusit my page; follow this link
In August, Powerball added a third weekly drawing to assist
enhance jackpots faster.
my blog … Visit this link
Hi there, this weekend is good for me, because
this time i am reading this impressive informative piece of writing here at my home.
Wisconsin’s newest multi-millionaire willl
share the $632 million jackpot.
My web-site: Helpful site
In fact when someone doesn’t be aware of after that its up to other people that they
will assist, so here it occurs.
molecule kamagra kamagra sans ordonnance 24h peut on acheter du kamagra sans ordonnance comment trouver du kamagra sans ordonnance
“The winner is pretty family members oriented and close to his siblings and parents,” she mentioned.
my blog post; here
Historical and current finish-of-day data supplied by FACTSET.
my blog post: Take a look at the site here
To date, Powerball holds the globe record for biggest
jackpot set in 2016.
Stopp by my web-site: Learn here
อย่าห้าวให้มากไอ้เด็กเหี้ย
Good day! This is my first visit to your blog! We are a group of volunteers and
starting a new initiative in a community in the same niche.
Your blog provided us valuable information to work
on. You have done a wonderful job!
All occasions displayed in Australian Western Typical Time (AWST is UTC+8) unless stated otherwise.
Have a look at my website :: Click for source
Entre sites frauduleux et non avantageux, il est de plus en plus difficile de
déceler le vrai du faux.
my site king chance casino [kings-chance-play.com]
It was 1 of four third-prize winners in New York that day.
Feeel free to visit my page … Click for more
Wednesday’s winning lottery was far from the U.S.
jackpot record, which was a whopping $1.586 billion Powerball prize in 2016.
Heree is my blog post … check here
Greetings! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly? My web site looks weird when viewing from my apple iphone.
I’m trying to find a theme or plugin that might be able to fix this issue.
If you have any recommendations, please share. Appreciate it!
help refuges
As of Thursday evening, the Sacramento winner has however to come forward.
my webpage: Click here for info
excellent publish, very informative. I wonder why the opposite experts of this
sector don’t realize this. You must continue your writing.
I’m sure, you’ve a huge readers’ base already!
Spot on with this write-up, I truly believe that this website needs far more attention.
I’ll probably be returning to read more, thanks for the advice!
I needed to thank you for this great read!! I definitely enjoyed every
little bit of it. I’ve got you bookmarked to look at new stuff you post…
Amazing issues here. I’m very glad to peer your post.
Thanks so much and I’m taking a look ahead to touch you.
Will you please drop me a e-mail?
js ラブドール あなたのダッチワイフとトリオを持つことは考えられますか?あなたの性生活に対するセックス人形の言及できないものの影響妊娠中のセックス人形について考える必要がある5つの伝説セックス人形はどのようにあなたのポルノ中毒を打ち負かすことができますか?
Also, check out our free “Full Gear Cycle” monthly giveaway right here : https://tinyurl.com/etalaze-contest
RHzs43hgndIpuiSy
Each prize selections arre prior to taxes, according to Powerball.
Here is my page :: Great site
Virgin Islands, all of which collectively oversee the game.
Feel free to visit my web page Click here for info
Friday’s estimated MEGA MILLIONS jackpot is $278 milliion and Wednesday’s estimated FLORIDA LOTTO jackpot is $13.75 million.
Visit my blog post; Click to find out more
For promoting the winning ticket, Albertsons will acquire a bonus of $1 million from the lottery, and
California schools will ohtain $78 million from ticfket sales.
My webpage: Browse this site
Attractive section of content. I just stumbled upon your blog and in accession capital to assert that I get actually enjoyed account your blog posts. Anyway I will be subscribing to your augment and even I achievement you access consistently fast.
I’m not that much of a online reader to be honest but your sites really
nice, keep it up! I’ll go ahead and bookmark your site to
come back later on. All the best
According to Powerball, the general odds of winning a prize are 1 in 24.9, though the odds off winninng a jackpot
are 1in 292.2 million.
Also visit myy website; Go to this website
Hemsworth and Waititi had discussed plans for
a sequel to Ragnarok by January 2018.
The jackpot for Monday’s drawing increased to an estimated $416 million.
my site; The original source
Hi there, I enjoy reading through your article.
I like to write a little comment to support you.
If you are going for best contents like me, just visit this web site every day
since it gives quality contents, thanks
Firma jest założona w 2009 roku na Cyprze i początkowo funkcjonowała
jako kasyno.
Have a look at my web blog … 1 x bet
When someone writes an article he/she retains the thought
of a user in his/her brain that how a user can be aware of it.
Therefore that’s why this paragraph is outstdanding.
Thanks!
Magnificent goods from you, man. I have remember your stuff prior to and you’re just too magnificent.
I actually like what you have bought here, certainly like
what you’re saying and the best way wherein you say it.
You make it entertaining and you continue to care for to stay it smart.
I can not wait to read far more from you. This is really a
tremendous website.
SB165 would have established a licensing method ffor off-track wagering providers and set a minimum aage of
18.
Heree is my webpage :: Go to this website
Odds decrease ftom there, lile 1 iin 11 million of
winning $1 million and 1 in 292.two million for winning the jackpot.
Have a look at mmy website … more info
Right here are your Powerball and Powerball Plus rsults for
Friday, 24 December 2021.
Take a look at my web blog; Check out here
The lottery is just a single of these exciting things that we do as a wayy to strkke it rich, correct?
Also visit my blog post Visit website
Spot on with this write-up, I seriously believe this site needs a great deal more attention. I’ll
probably be back again to read through more, thanks for the
information!
It’s not my first time to pay a quick visit this site, i am visiting
this web page dailly and take nice facts from here daily.
LANSING, MI – There was no wwinner of the $20 million Powerball jackpot
for the drqwing held onn Saturday, Jan. eight.
Allso visit my web site … Browse this site
Once hhe figures out what the taxes will be, he plans to divide iit up among the 11 individuals who
function in hiis retailer.
Also visit my homepage; You can find out more
Ao clicar no botão Jogar Aviator, você será redirecionado para o
espelho do site de trabalho do site oficial do cassino online 1win.
Also visit my blog post :: app
What a information of un-ambiguity and preserveness of precious experience concerning unpredicted emotions.
This web site truly has all of the information I needed concerning this subject and
didn’t know who to ask.
Mississippi was the most recent to join each, beginning sales in January 2020.
Feel free to visit my web-site – Find more info
For the second day in a row, Kazakhstan’sbiggest city Alnaty was
eerioy quiet and under heavy militaryy manage, according to an ABC Newws reporter there.
Feel free to visit my web page … Discover more here
Starting jackpot amounts or future jackpkt increases will be announced prior
to every drawing.
My web site Go to the website
Currently it looks like Expression Engine is the
top blogging platform available right now. (from what I’ve read) Is that what you’re using on your
blog?
When someone writes an piece of writing he/she keeps the idea of a
user in his/her mind that how a user can know it.
Thus that’s why this piece of writing is outstdanding.
Thanks!
Заходите на который сайт (на котором вы сейчас находитесь), нажимайте кнопку, только вы сразу а окажетесь на
нужный вам ресурсе.
Here is my web blog: леон бет зеркало вход
Smaller wonder that customer-finance gurus say the lottery
is primarily an extra tax on the poor.
Alsoo visit myy blog – Check out this site
Watch thhe Doouble Play live drawingon HoosierLottery.com.
my page – Homepage
Hello! I could have sworn I’ve been to this web site before but after looking at a
few of the articles I realized it’s new to
me. Anyways, I’m certainly happy I stumbled upon it and I’ll be book-marking it and checking back regularly!
Superb website you have here but I was curious about if you knew of any user discussion forums that cover the same topics talked about here?
I’d really love to be a part of online community where I can get feed-back from other experienced people that share
the same interest. If you have any suggestions, please let me know.
Many thanks!
I’ve read several good stuff here. Definitely worth bookmarking for revisiting.
I wonder how a lot attempt you place to make such a fantastic informative site.
He chose to acquire his winnings as a a single-time, lump-sum payment of $795,000.
Visit my blog :: follow this link
If you win the lottery in California, officials are needed to publish your name as properly as the place where the winning ticket was
purchased.
Feel free to surf to my blog post :: Additional reading
If a jackpot is not won, the minimum rollover
iss $10 million.
Also visit my website … Check out here
The a single-time money payout for the June 5 Powerball drawing will be $25.9 million.
Stop byy my web-site … Visit this site
The Royal loved ones uses cake and balloon emojis – and a series of touching photos – to…
Here is my site; Additional info
Lottery claiming deadlines have been extended throughout Maryland’s COVID-19 state of emergency.
My web-site :: Click for source
Soon, Gru discovers that he has made himself an enemy of the highest evil that he
could think about and goes on the run with his fearless followers, the Minions.
In August, Powerball started offfering a third weekly drawing onn Monday nights.
my web-site :: View website
WOW just what I was looking for. Came here
by searching for leci123
non prescription metformin metformin 1000 mg pill what is metformin 1000 mg used for how to take metformin for pcos
Race2Riches is an interactive horse racing gam with the chance to win up to $1,000,000.
Stop by my blog post – Great site
aralen and prednisone aralen 400mg is aralen considered low in side effects what is aralen?
This is very interesting, You’re a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your wonderful post.
Also, I have shared your web site in my social networks!
my web-site: Bellisima Bites Collagen Gummies
LAND O’ LAKES, Fla. – He’s Florida’s youngest jackpot winner ever in the multi-state lottery game.
Check out my site Click to find out more
Total ticket price will depend on the number of panels and draws you play.
my homepage: Click for more info
One of these winners wass amongst these that won the record-setting $1.586 billion jackpot in January 2016, according to the Florida Lottery.
Also visit my webb page :: Browse this site
Aw, this was an exceptionally good post. Spending
some time and actual effort to generate a very good article… but what can I say…
I procrastinate a lot and never manage to get nearly
anything done.
EZ2resultstoday.com is not involved in aany way or
connectfed orr affiliated with Philippine Charity Sweepstakes Workplace .
Reviesw myy web-site; Article source
To win the Powerball Jackpot, players have tto haave all five numbers plus the Powerball
number matching the numbers pulled in a drawing, according to
CT lottery.
Loook inbto my site; Go here
Hi all, here every one is sharing these kinds of know-how, therefore
it’s fastidious to read this webpage, and I used to
pay a quick visit this web site everyday.
Prizes must be claimed within 180 days right after the drawing date.
Here is my websute – Learn more here
Hi this is kind of of off topic but I was wanting to know if blogs
use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding skills so I wanted
to get advice from someone with experience. Any help would be greatly appreciated!
Through the drawing, a Energy Play multiplier is randomly selected
from a weighted fiueld of twoo 5s, 3 4s, thirteen 3s
and twenty-4 2s.
my blog post :: Extra resources
Very nice post. I just stumbled upon your blog and wanted
to say that I have really enjoyed surfing around your blog posts.
In any case I’ll be subscribing to your feed and I hope you write again very soon!
Hi guys! :]
I’ve faced one problem…
You identify, I’ve decided to form a jocose video due to the fact that my best friend.
We have many common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps on the side of downloading purport directly from common networks. Most of them are awful.
I’ve found shadow ban instagram how long automate bot
It’s useful, works licentious enough, no additional actions are needed.
But that time…
It takes duration to download a intimate number of videos. Perchance someone used it? How do you like it? Or do you recollect a secure option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to bring into being a jocose video for my outdo friend.
We be undergoing assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for the sake of downloading components soon from common networks. Most of them are awful.
I’ve found instagram auto bot tool
It’s convenient, works fast passably, no additional actions are needed.
But suppress…
It takes duration to download a exalted number of videos. Perchance someone used it? How do you like it? Or do you know a secure variant to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
My brother suggested I may like this web site.
He used to be entirely right. This put up actually made my day.
You can not believe just how much time I had spent for this info!
Thank you!
Can I simply say what a comfort to discover a person that actually
understands what they are talking about on the web.
You certainly know how to bring an issue to light and make it important.
More people need to look at this and understand this side of the story.
I was surprised you aren’t more popular because you definitely have the
gift.
Track the history behind your preferred Jackpot games, from winning numbers to Colorado Jackpot winners and extra.
Stop by my web site – Additional info
Since no oone wwon the general jackpot, the prize climbs to $378
million for Wednesday’s drawing.
Have a look at my blog: Have a peek at this website
► Sekabet giriş – Sekabet, çevrimiçi bahis
için büyük bir markadır ve tüm Türkiye de çok güvenilir olarak bilinir.
Mevcut ürünlerin kalitesi olağanüstü olduğu için büyük
itibarı sebepsiz değildir. İlki, büyük sporlar ve ligler için harika bir kapsama sahip olan oyun içi bahis bölümüyle birlikte çevrimiçi spor bahis sitesidir.
In addition, the Sunshine State has a assortment of iits personal amazing draw games too attempt your luck on …
Alsoo visit myy website: Great site
What i do not understood is in fact how you are not really much
more smartly-liked than you might be now. You’re so intelligent.
You recognize therefore significantly with
regards to this topic, produced me individually imagine it from numerous various angles.
Its like women and men are not fascinated except it’s one thing
to do with Girl gaga! Your individual stuffs outstanding.
All the time maintain it up!
Feel free to visit my site … judi qq online
Pretty nice post. I just stumbled upon your weblog and wished to say that I’ve really enjoyed surfing around your blog posts.
In any case I’ll be subscribing to your feed and I hope you
write again very soon!
Look at my website: inflatable kayaks
Winning prizes greater than $600 arre topic to sfate and federal taxes.
Also visit my website: Visit the website
I’m not that much of a internet reader to be
honest but your sites really nice, keep it up! I’ll go ahead and bookmark your website to come back down the road.
Many thanks
Feel free to surf to my web site – https://buybacklink.splashthat.com/
Link exchange is nothing else however it is just placing the other person’s website link on your
page at appropriate place and other person will also
do similar in support of you.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve decided to generate a jocose video an eye to my outdo friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for the sake of downloading purport soon from social networks. Most of them are awful.
I’ve found
It’s available, works fast ample supply, no additional actions are needed.
But that time…
It takes time to download a intimate numbers of videos. Peradventure someone used it? How do you like it? Or do you know a good alternative to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve unswerving to form a jocose video an eye to my outdo friend.
We be struck by multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps after downloading components unswervingly from social networks. Most of them are awful.
I’ve found
It’s accessible, works licentious ample supply, no additional actions are needed.
But nevertheless…
It takes duration to download a intimate numbers of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a accomplished alternative to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Untuk permainannya sendiri di saat para bettor berhasil memenangkan permainan judi poker
pada mesin tersebut mereka akan meraih bayaran buat kemenangannya salah satu hadiahnya adalah mendapatkan rokok dan minuman gratis, adapun mesin poker buatannya tersebut juga bisa melakukan pembayaran otomatis untuk para membernya
diwaktu memenangkan poker. Sampai pada tahun 190 seseorang yang bernama Herbert telah memperkenalkan sebuah
game judi slot yang punya tampilan yang berbeda yaitu dengan mempergunakan simbol buah-buahan contohnya seperti buah jeruk apel serta jenis simbol buah lainnya.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve undisputed to generate a merry video proper for my best friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps after downloading capacity unswervingly from group networks. Most of them are awful.
I’ve found
It’s accessible, works licentious passably, no additional actions are needed.
But that time…
It takes continuously to download a exalted number of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a passable variant to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
bamlanivimab vs baricitinib baricitinib covid 19 olumiant price in india olumiant pronunciation
Good information. Lucky me I discovered your website by chance (stumbleupon).
I’ve book-marked it for later!
Ahaa, its pleasant conversation regarding this paragraph at
this place at this website, I have read all that, so now me also commenting at this place.
I am really impressed with your writing skills and also
with the layout on your blog. Is this a paid
theme or did you modify it yourself? Anyway keep up the excellent quality writing, it is rare to see a
nice blog like this one today.
Also visit my homepage … NaturesHub Anti Aging Cream Review
Hi guys! :]
I’ve faced one problem…
You identify, I’ve decided to create a merry video an eye to my outdo friend.
We be struck by many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps after downloading capacity unswervingly from popular networks. Most of them are awful.
I’ve found
It’s convenient, works stable adequately, no additional actions are needed.
But suppress…
It takes continuously to download a exalted numbers of videos. Possibly someone used it? How do you like it? Or do you identify a secure variant to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve decided to bring into being a funny video due to the fact that my best friend.
We be undergoing assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps on the side of downloading content soon from popular networks. Most of them are awful.
I’ve found
It’s available, works stable enough, no additional actions are needed.
But that time…
It takes duration to download a great number of videos. Peradventure someone reach-me-down it? How do you like it? Or do you know a accomplished option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve decided to create a funny video an eye to my best friend.
We be undergoing many common videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps for the sake of downloading components unswervingly from popular networks. Most of them are awful.
I’ve found
It’s useful, works licentious adequately, no additional actions are needed.
But that time…
It takes duration to download a immense host of videos. Peradventure someone reach-me-down it? How do you like it? Or do you know a accomplished option to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Powerball can be played in 45 states, Washington D.C., Puerto Rico and the
U.S.
my website: Find more information
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve unswerving to generate a jocose video proper for my most desirable friend.
We be struck by assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps after downloading content directly from popular networks. Most of them are awful.
I’ve found
It’s available, works licentious adequately, no additional actions are needed.
But that time…
It takes time to download a great numbers of videos. Maybe someone acclimated t? it? How do you like it? Or do you know a passable variant to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve decided to generate a merry video proper for my best friend.
We have assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps for the sake of downloading capacity promptly from common networks. Most of them are awful.
I’ve found
It’s convenient, works fast enough, no additional actions are needed.
But nevertheless…
It takes time to download a great host of videos. Possibly someone used it? How do you like it? Or do you identify a secure alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to form a eccentric video an eye to my most desirable friend.
We be struck by many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps on the side of downloading purport soon from popular networks. Most of them are awful.
I’ve found
It’s useful, works rapid enough, no additional actions are needed.
But suppress…
It takes continuously to download a great number of videos. Maybe someone used it? How do you like it? Or do you recollect a passable alternative to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
North Carolina Powerball Double Play Prizes aand Winning
Odds, wheeling method, payout, frequency chart, how tto play,
how to win, and so on.
My site :: Click for more info
Hi guys! :]
I’ve faced complete problem…
You know, I’ve decided to bring into being a funny video due to the fact that my most desirable friend.
We deliver varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps on the side of downloading purport promptly from group networks. Most of them are awful.
I’ve found
It’s convenient, works stable ample supply, no additional actions are needed.
But nevertheless…
It takes duration to download a exalted multitude of videos. Peradventure someone acclimated t? it? How do you like it? Or do you identify a good option to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve decided to form a merry video proper for my largest friend.
We have many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps after downloading capacity directly from popular networks. Most of them are awful.
I’ve found
It’s accessible, works licentious ample supply, no additional actions are needed.
But nevertheless…
It takes continuously to download a exalted number of videos. Possibly someone used it? How do you like it? Or do you identify a good choice to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve incontestable to create a merry video proper for my outdo friend.
We have assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps for downloading purport unswervingly from common networks. Most of them are awful.
I’ve found
It’s useful, works stable ample supply, no additional actions are needed.
But that time…
It takes duration to download a exalted host of videos. Perchance someone reach-me-down it? How do you like it? Or do you identify a good option to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Valuable information. Fortunate me I discovered your website accidentally, and I am shocked why this twist of fate did not took place earlier!
I bookmarked it.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve incontestable to form a jocose video for my best friend.
We deliver many standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps on the side of downloading components directly from popular networks. Most of them are awful.
I’ve found
It’s useful, works rapid ample supply, no additional actions are needed.
But suppress…
It takes continuously to download a immense multitude of videos. Peradventure someone used it? How do you like it? Or do you identify a good choice to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve decided to generate a funny video for my best friend.
We have assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps after downloading components directly from social networks. Most of them are awful.
I’ve found
It’s convenient, works fast ample supply, no additional actions are needed.
But that time…
It takes continuously to download a intimate number of videos. Maybe someone used it? How do you like it? Or do you identify a good choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve undisputed to form a jocose video an eye to my most desirable friend.
We be undergoing varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps for downloading purport promptly from group networks. Most of them are awful.
I’ve found
It’s available, works licentious ample supply, no additional actions are needed.
But that time…
It takes moment to download a great host of videos. Maybe someone reach-me-down it? How do you like it? Or do you know a passable variant to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
metformin b12 metformin 500 mg price uk what does metformin do exactly? what time of day should you take metformin
In specific states, the majority of lottery revenue comes from a modest percentage
of players.
Here is my page … Click for more
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve undisputed to generate a eccentric video due to the fact that my best friend.
We deliver varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for the sake of downloading components unswervingly from social networks. Most of them are awful.
I’ve found
It’s useful, works rapid ample supply, no additional actions are needed.
But that time…
It takes moment to download a great numbers of videos. Peradventure someone acclimated t? it? How do you like it? Or do you identify a accomplished choice to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve decided to create a merry video proper for my outdo friend.
We have assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with miscellaneous apps after downloading purport unswervingly from common networks. Most of them are awful.
I’ve found
It’s useful, works rapid passably, no additional actions are needed.
But that time…
It takes continuously to download a intimate numbers of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a good alternative to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve incontestable to generate a jocose video due to the fact that my largest friend.
We have varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps after downloading purport unswervingly from common networks. Most of them are awful.
I’ve found
It’s accessible, works stable passably, no additional actions are needed.
But still…
It takes time to download a intimate host of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a secure option to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
According to officials, all of thee agency’s prize claim centers
will be closed via Friday.
Check out my website :: follow this link
Hi guys! :]
I’ve faced one problem…
You know, I’ve decided to generate a merry video for my largest friend.
We deliver assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps for downloading content unswervingly from popular networks. Most of them are awful.
I’ve found
It’s accessible, works fast passably, no additional actions are needed.
But still…
It takes moment to download a intimate multitude of videos. Possibly someone acclimated t? it? How do you like it? Or do you identify a passable option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve decided to form a jocose video due to the fact that my outdo friend.
We be struck by assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps after downloading components unswervingly from popular networks. Most of them are awful.
I’ve found
It’s available, works rapid passably, no additional actions are needed.
But that time…
It takes continuously to download a exalted host of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve undisputed to create a jocose video proper for my outdo friend.
We deliver multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps on the side of downloading purport unswervingly from popular networks. Most of them are awful.
I’ve found
It’s available, works rapid enough, no additional actions are needed.
But nevertheless…
It takes continuously to download a great numbers of videos. Peradventure someone used it? How do you like it? Or do you recollect a good choice to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
This page truly has all of the info I needed concerning
this subject and didn’t know who to ask.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve unswerving to generate a jocose video an eye to my outdo friend.
We be undergoing multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps on the side of downloading purport soon from social networks. Most of them are awful.
I’ve found
It’s useful, works stable enough, no additional actions are needed.
But suppress…
It takes continuously to download a great host of videos. Possibly someone acclimated t? it? How do you like it? Or do you know a passable choice to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve decided to create a funny video an eye to my outdo friend.
We be undergoing multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps on the side of downloading capacity soon from social networks. Most of them are awful.
I’ve found
It’s convenient, works fast adequately, no additional actions are needed.
But still…
It takes time to download a immense multitude of videos. Peradventure someone used it? How do you like it? Or do you identify a accomplished alternative to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve undisputed to create a merry video due to the fact that my outdo friend.
We be undergoing assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps for downloading purport unswervingly from social networks. Most of them are awful.
I’ve found
It’s accessible, works fast ample supply, no additional actions are needed.
But still…
It takes moment to download a intimate numbers of videos. Possibly someone reach-me-down it? How do you like it? Or do you recollect a accomplished variant to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve undisputed to bring into being a funny video an eye to my largest friend.
We be undergoing varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps for the sake of downloading content directly from common networks. Most of them are awful.
I’ve found
It’s convenient, works fast adequately, no additional actions are needed.
But still…
It takes duration to download a exalted numbers of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a accomplished variant to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to create a eccentric video due to the fact that my best friend.
We deliver assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps for the sake of downloading content promptly from common networks. Most of them are awful.
I’ve found
It’s useful, works licentious ample supply, no additional actions are needed.
But nevertheless…
It takes duration to download a intimate numbers of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a good alternative to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve undisputed to bring into being a merry video for my most desirable friend.
We have many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps after downloading content unswervingly from social networks. Most of them are awful.
I’ve found
It’s accessible, works rapid adequately, no additional actions are needed.
But suppress…
It takes moment to download a exalted host of videos. Peradventure someone used it? How do you like it? Or do you know a passable choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
The listed jackpot amounts refer to winners who opt for aan annuity, paiid over 30
years.
Here is my website – Check out this site
To deal with the issues, we propose to perform finish-to-finish slot alignment and recognition using
an attention module (Figure 2), in order that
no external slot projection is required. Oftentimes, the again-finish databases
are solely uncovered by an exterior API, which is owned and maintained by our partners.
Most mechanisms in earlier works solely consider native externalities and will
not be truth-telling based mostly GSP. But all of those works concentrate on a single task.
Next in line was the 1954 Firearrow II, another roadster,
however modified intimately. As of right now, AAA doesn’t have a substitute partner ready to go
for Hardy, however they’re said to be working on it.
In addition, he was additionally imagined to be working AAA TripleMania on June 18 in Tijuana,
Mexico in one other tag team match together
with his brother Matt Hardy. As previously reported,
AEW wrestler Jeff Hardy was arrested yesterday in Volusia County,
Florida for Felony DUI. He was beforehand scheduled to work a tag crew title Ladder Match tomorrow night time on AEW Dynamite.
In keeping with Meltzer, AAA officials want to maintain Matt Hardy within the tag crew
match and find him a substitute to crew with him.
You could play your number selections ffor a lot more than 1
drawing.
my page Find more information
Powerball Numbers 11 January 2022 are published in above table.
Visikt my web-site: Article source
The lottery game is simple too play just like lots of other lottery games.
Here is my web-site … Visit the website
The jackpot prize will be divided equally amongst all players
who priperly match all 5 white balls plus thee red Powerball.
Allso visit my blog post: click here
You may haqve the pc randomly seelect your numbers for you byy marking the
“Quick Pick” box.
Here iis my homepage Helpful hints
Hey there just wanted to give you a quick heads up.
The text in your post seem to be running off the screen in Internet
explorer. I’m not sure if this is a format issue or something to do with browser compatibility but I thought I’d
post to let you know. The style and design look great though!
Hope you get the problem fixed soon. Many thanks
A singl ticket in California rked iin a $699.eight million grand prize on October
four.
Check out my site – Look at more info
Check out this history of Nebraska Powerball jackpot winners.
my blog … here
It’s a shame you don’t have a donate button! I’d certainly donate to this superb blog!
I suppose for now i’ll settle for book-marking and adding your RSS feed to
my Google account. I look forward to fresh updates and
will talk about this site with my Facebook group. Talk soon!
As a subsdcriptions account holder, your winnings
on prizes up to $600 are automatically deposited into yyour Player
Card Account account!
Heere is my web blog :: Click here to find out more
With serijously massive lotto jackpots like these, players flock to obtain Powerball
tickeys on line and offline.
Also visit myy site ::Click here
Wow! After all I got a webpage from where I be capable of actually obtain helpful information concerning my study and knowledge.
A single of the ttwo winning Powerball tickets for Wednesday night’s drawing was soold at the South Sacramento 7-Eleven oon Windham Drive.
Here is my web-site Great site
baricitinib for spondylarthritis baricitinib 4mg baricitinib generic name baricitinib vs tofacitinib
If you only match the Powerball quantity, you win at minimum $four.
My web-site – Visit this website
CT (ten p.m. ET) on days when the winning numbers are announced.
My blog … Go to this website
wonderful publish, very informative. I wonder why the other experts
of this sector don’t realize this. You should continue your writing.
I am confident, you have a huge readers’ base already!
For the second day in a row, Kazakhstan’s greatest
city Almaty was eerily quiet and beneathh heavy military handle, according to an ABC News reporter there.
my web blog; Additional resources
It’s going to be end of mine day, except before end I am reading this enormous post to increase my knowledge.
Hey I know this is off topic but I was wondering if you knew
of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time
and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward to your
new updates.
If you initially funded your accoumt with a bank transfer, you may possibly also have your funds
sent back to your checking acfcount bby way of bank transfer.
Check out myy web-site :: Have a peek here
The winners will splot the jackpot, whihh is the seventh biggest in Powerball’s history.
Here is my website – follow this link
Theree are now three probabilities to win the Powerball every week – Monday,
Wednesday and Saturday.
Have a look at my webpage; Click here for more info
There is nevertheless cash to be had in the huge Megamillions jackpot.
Also visit my website Article source
Quality articles or reviews is the important to be a focus for the
visitors to pay a visit the site, that’s what this site is providing.
hair growth pills
https://restolinreview.com/top-7-vitamins-supplements-for-faster-hair-grow/
Simply want to say your article is as astonishing.
The clearness on your put up is simply cool and i can suppose you are knowledgeable on this subject.
Fine along with your permission allow me to grab your feed to stay updated with approaching
post. Thanks one million and please keep up the rewarding work.
We now know Wisconsin’s winning Powerball tickt was sold at the Jackson Pointe Citgo on Packerland Drive in Ashwaubenon.
Also visit my web site – Great site
I all the time emailed this weblog post page to all
my associates, as if like to read it after that my links will too.
This is a topic that is close to my heart…
Cheers! Where are your contact details though?
Hello there, You have done a fantastic job. I’ll certainly digg it and personally suggest to my friends.
I am confident they’ll be benefited from this site.
Very soon this web site will be famous amid all blog visitors, due to it’s good posts
All income for Powerball ticket sales not made uuse of forr jackpots iis retained by each member none of thijs incomje is shared with other lotteries.
Feel free to visiut my blog :: Take a look at the site here
Does your site have a contact page? I’m having trouble locating it but, I’d like to shoot
you an email. I’ve got some ideas for your blog you might
be interested in hearing. Either way, great site and I look forward to
seeing it expand over time.
The ticket wwas worth a $261 million annuity it was sold
inn Sunbury.
Check out my web blog – Click here for more info
I know this site provides quality based articles and other
stuff, is there any other site which gives these kinds of stuff in quality?
Thank you for sharing your thoughts. I truly appreciate your efforts and I am waiting for your
further post thank you once again.
eight) Mark MULTI DRAWS to play up to 20 consecutive draws (adds $2 per Play foor each draw).
my site :: Click for source
Hello. remarkable job. I did not anticipate this. This is
a remarkable story. Thanks!
Here is my webpage … login joker123
They difcfer frrom the fixed second prizes
presented in other participatinbg states.
Here is my web-site Hop over to this website
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve unswerving to bring into being a jocose video due to the fact that my outdo friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps for the sake of downloading capacity directly from popular networks. Most of them are awful.
I’ve found
It’s convenient, works fast passably, no additional actions are needed.
But still…
It takes moment to download a immense numbers of videos. Perchance someone acclimated t? it? How do you like it? Or do you know a secure option to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve undisputed to form a jocose video an eye to my outdo friend.
We be undergoing multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps on the side of downloading components promptly from social networks. Most of them are awful.
I’ve found
It’s useful, works stable passably, no additional actions are needed.
But still…
It takes moment to download a immense host of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a passable alternative to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve unswerving to generate a funny video an eye to my most desirable friend.
We be struck by multitudinous common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for the sake of downloading content soon from popular networks. Most of them are awful.
I’ve found
It’s available, works stable adequately, no additional actions are needed.
But suppress…
It takes duration to download a intimate number of videos. Possibly someone acclimated t? it? How do you like it? Or do you identify a secure variant to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve incontestable to bring into being a funny video proper for my outdo friend.
We deliver assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps after downloading components directly from group networks. Most of them are awful.
I’ve found
It’s convenient, works stable passably, no additional actions are needed.
But nevertheless…
It takes continuously to download a intimate host of videos. Possibly someone used it? How do you like it? Or do you identify a passable alternative to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve incontestable to generate a eccentric video proper for my best friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps for the sake of downloading purport promptly from common networks. Most of them are awful.
I’ve found
It’s accessible, works stable enough, no additional actions are needed.
But suppress…
It takes moment to download a immense number of videos. Maybe someone used it? How do you like it? Or do you know a good alternative to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve undisputed to form a jocose video for my largest friend.
We be struck by multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps after downloading content directly from social networks. Most of them are awful.
I’ve found
It’s accessible, works fast ample supply, no additional actions are needed.
But suppress…
It takes continuously to download a immense numbers of videos. Perchance someone reach-me-down it? How do you like it? Or do you know a accomplished option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
The winning Powerball numbers are four, eight, 19, 27, 34,
and 10.
Feel free to visit my webpage; Helpful hints
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve undisputed to form a eccentric video for my outdo friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps on the side of downloading capacity promptly from common networks. Most of them are awful.
I’ve found
It’s convenient, works fast passably, no additional actions are needed.
But still…
It takes time to download a intimate numbers of videos. Perchance someone acclimated t? it? How do you like it? Or do you know a good alternative to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve undisputed to form a jocose video an eye to my most desirable friend.
We deliver multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with various apps after downloading components soon from group networks. Most of them are awful.
I’ve found
It’s convenient, works rapid adequately, no additional actions are needed.
But still…
It takes duration to download a exalted number of videos. Perchance someone reach-me-down it? How do you like it? Or do you know a secure option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You know, I’ve decided to bring into being a merry video proper for my outdo friend.
We be undergoing varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps for the sake of downloading capacity unswervingly from common networks. Most of them are awful.
I’ve found
It’s available, works stable adequately, no additional actions are needed.
But that time…
It takes continuously to download a immense host of videos. Peradventure someone used it? How do you like it? Or do you identify a passable option to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve incontestable to create a eccentric video for my outdo friend.
We have assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps on the side of downloading content soon from popular networks. Most of them are awful.
I’ve found
It’s available, works rapid adequately, no additional actions are needed.
But still…
It takes duration to download a intimate number of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a passable option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve incontestable to create a merry video proper for my outdo friend.
We be undergoing many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps on the side of downloading purport promptly from common networks. Most of them are awful.
I’ve found
It’s useful, works rapid ample supply, no additional actions are needed.
But that time…
It takes continuously to download a exalted numbers of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a passable alternative to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You be acquainted with, I’ve undisputed to create a funny video an eye to my most desirable friend.
We have many common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps after downloading components soon from social networks. Most of them are awful.
I’ve found
It’s available, works rapid passably, no additional actions are needed.
But nevertheless…
It takes continuously to download a exalted host of videos. Perchance someone used it? How do you like it? Or do you recollect a accomplished option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You know, I’ve incontestable to generate a funny video for my best friend.
We be struck by multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps for downloading purport unswervingly from popular networks. Most of them are awful.
I’ve found
It’s available, works stable adequately, no additional actions are needed.
But that time…
It takes duration to download a immense host of videos. Perchance someone acclimated t? it? How do you like it? Or do you know a accomplished choice to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve unswerving to create a eccentric video due to the fact that my best friend.
We have multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for the sake of downloading purport directly from popular networks. Most of them are awful.
I’ve found
It’s available, works licentious enough, no additional actions are needed.
But nevertheless…
It takes duration to download a immense host of videos. Perchance someone reach-me-down it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve incontestable to form a funny video due to the fact that my outdo friend.
We be struck by multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps for downloading content directly from social networks. Most of them are awful.
I’ve found
It’s useful, works rapid passably, no additional actions are needed.
But still…
It takes continuously to download a immense numbers of videos. Possibly someone reach-me-down it? How do you like it? Or do you know a secure option to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Lottery officials warned thatFacebookusers reported posts in the past that indicated Powerball was giving away prize cash on the social media platform.
my site – Check out here
Hi guys! :]
I’ve faced one problem…
You identify, I’ve incontestable to create a merry video an eye to my most desirable friend.
We have varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps for the sake of downloading components directly from social networks. Most of them are awful.
I’ve found
It’s available, works stable passably, no additional actions are needed.
But that time…
It takes time to download a great host of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a good variant to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve incontestable to form a eccentric video due to the fact that my most desirable friend.
We deliver varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps for the sake of downloading components unswervingly from group networks. Most of them are awful.
I’ve found
It’s convenient, works fast passably, no additional actions are needed.
But still…
It takes time to download a great number of videos. Possibly someone acclimated t? it? How do you like it? Or do you recollect a passable option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to generate a jocose video an eye to my best friend.
We be undergoing varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps on the side of downloading components promptly from group networks. Most of them are awful.
I’ve found
It’s useful, works stable adequately, no additional actions are needed.
But that time…
It takes time to download a intimate number of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a accomplished option to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve decided to generate a merry video proper for my outdo friend.
We have many standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps after downloading content soon from common networks. Most of them are awful.
I’ve found
It’s available, works rapid ample supply, no additional actions are needed.
But that time…
It takes duration to download a exalted numbers of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to bring into being a eccentric video proper for my outdo friend.
We be struck by varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps for the sake of downloading purport unswervingly from social networks. Most of them are awful.
I’ve found
It’s convenient, works licentious enough, no additional actions are needed.
But that time…
It takes time to download a great numbers of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a good variant to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve unswerving to create a merry video due to the fact that my best friend.
We deliver many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for the sake of downloading capacity unswervingly from group networks. Most of them are awful.
I’ve found
It’s convenient, works rapid ample supply, no additional actions are needed.
But suppress…
It takes continuously to download a exalted host of videos. Possibly someone acclimated t? it? How do you like it? Or do you know a accomplished variant to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
We stumbled over here different web page and thought I should check things out.
I like what I see so i am just following you. Look forward to checking
out your web page for a second time.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve undisputed to generate a eccentric video due to the fact that my most desirable friend.
We be undergoing multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps after downloading purport unswervingly from popular networks. Most of them are awful.
I’ve found
It’s convenient, works licentious passably, no additional actions are needed.
But still…
It takes moment to download a intimate multitude of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a secure choice to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve decided to bring into being a eccentric video an eye to my best friend.
We be struck by assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps after downloading purport soon from common networks. Most of them are awful.
I’ve found
It’s useful, works stable ample supply, no additional actions are needed.
But suppress…
It takes duration to download a intimate number of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You know, I’ve incontestable to create a eccentric video due to the fact that my outdo friend.
We have many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps after downloading components promptly from common networks. Most of them are awful.
I’ve found
It’s useful, works rapid enough, no additional actions are needed.
But still…
It takes time to download a great multitude of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a good option to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
baclofen sedation where to buy baclofen 50mg is baclofen the same as tizanidine how to titrage down from baclofen
After looking over a number of the blog posts on your website, I truly like your
way of blogging. I added it to my bookmark site list and will be checking back in the near future.
Take a look at my web site as well and let me know how you
feel.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to generate a merry video due to the fact that my outdo friend.
We be undergoing assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps for downloading capacity directly from common networks. Most of them are awful.
I’ve found
It’s accessible, works stable enough, no additional actions are needed.
But nevertheless…
It takes time to download a exalted numbers of videos. Maybe someone used it? How do you like it? Or do you identify a secure choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve incontestable to generate a jocose video for my largest friend.
We be undergoing assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps after downloading capacity directly from group networks. Most of them are awful.
I’ve found
It’s useful, works licentious passably, no additional actions are needed.
But suppress…
It takes time to download a exalted multitude of videos. Maybe someone used it? How do you like it? Or do you know a accomplished choice to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve undisputed to create a merry video proper for my largest friend.
We have assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps for downloading purport promptly from common networks. Most of them are awful.
I’ve found
It’s available, works fast ample supply, no additional actions are needed.
But nevertheless…
It takes duration to download a exalted multitude of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a good variant to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
But he has yet another connection to the winners, he said.
Feel free too surf to my web page :: Visit this link
But even if yoou don’t hit the jackpot, you can still turn into a millionaire by matching fewer numbers.
Feel free to visit my pagbe :: Get more info
Hi guys! :]
I’ve faced one problem…
You identify, I’ve decided to generate a eccentric video for my best friend.
We have assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps for downloading capacity promptly from group networks. Most of them are awful.
I’ve found
It’s convenient, works stable adequately, no additional actions are needed.
But still…
It takes time to download a exalted multitude of videos. Peradventure someone used it? How do you like it? Or do you recollect a accomplished variant to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve incontestable to form a funny video proper for my most desirable friend.
We be struck by many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps on the side of downloading capacity unswervingly from popular networks. Most of them are awful.
I’ve found
It’s convenient, works fast adequately, no additional actions are needed.
But suppress…
It takes continuously to download a exalted multitude of videos. Peradventure someone acclimated t? it? How do you like it? Or do you know a secure alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve incontestable to bring into being a merry video due to the fact that my largest friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps after downloading purport unswervingly from common networks. Most of them are awful.
I’ve found
It’s available, works fast adequately, no additional actions are needed.
But suppress…
It takes moment to download a immense number of videos. Peradventure someone reach-me-down it? How do you like it? Or do you know a secure option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hey! Would you mind if I share your blog with my myspace group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Cheers
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve incontestable to bring into being a funny video for my largest friend.
We have multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for downloading capacity promptly from popular networks. Most of them are awful.
I’ve found
It’s convenient, works fast ample supply, no additional actions are needed.
But that time…
It takes moment to download a great multitude of videos. Peradventure someone reach-me-down it? How do you like it? Or do you recollect a good option to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve undisputed to generate a funny video due to the fact that my best friend.
We have assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps on the side of downloading capacity soon from popular networks. Most of them are awful.
I’ve found
It’s useful, works fast ample supply, no additional actions are needed.
But that time…
It takes time to download a exalted multitude of videos. Perchance someone reach-me-down it? How do you like it? Or do you know a accomplished alternative to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve incontestable to bring into being a eccentric video for my most desirable friend.
We have assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for the sake of downloading components unswervingly from common networks. Most of them are awful.
I’ve found
It’s accessible, works rapid enough, no additional actions are needed.
But that time…
It takes moment to download a great multitude of videos. Peradventure someone reach-me-down it? How do you like it? Or do you identify a secure choice to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
I think the admin of this web site is truly working hard in favor of his
site, because here every material is quality based material.
My webpage: http://ufajc.com/
This is really interesting, You’re a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your wonderful post.
Also, I have shared your site in my social networks!
http://www.megabadday.com
Incredible points. Great arguments. Keep up the amazing spirit.
Greetings! Very helpful advice within this
article! It’s the little changes that produce the greatest changes.
Thanks a lot for sharing!
Hi guys! :]
I’ve faced one problem…
You identify, I’ve undisputed to generate a merry video for my most desirable friend.
We deliver assorted bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps for downloading capacity directly from common networks. Most of them are awful.
I’ve found writing rainbows blog instagram
It’s accessible, works fast passably, no additional actions are needed.
But suppress…
It takes moment to download a great number of videos. Maybe someone acclimated t? it? How do you like it? Or do you identify a accomplished variant to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve decided to bring into being a funny video proper for my outdo friend.
We be undergoing varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps for downloading content directly from social networks. Most of them are awful.
I’ve found how to start a fashion blog instagram
It’s available, works stable passably, no additional actions are needed.
But suppress…
It takes duration to download a immense multitude of videos. Possibly someone used it? How do you like it? Or do you know a accomplished option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve decided to form a eccentric video for my most desirable friend.
We have varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for downloading content promptly from social networks. Most of them are awful.
I’ve found instagram blog buttons
It’s convenient, works licentious adequately, no additional actions are needed.
But still…
It takes moment to download a exalted multitude of videos. Perchance someone used it? How do you like it? Or do you recollect a passable variant to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Howdy! Would you mind if I share your blog with my zynga group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Thank you
Funkcjonuje wiele programów bonusowych, które są osiągalne dla graczy,
którzy zakończyli rejestrację na stronie hazardowej.
My web-site – boomerang casino opinie (https://Bookmyt.us)
Nabywca świeżej gry, która zostanie dostępna na systemie
cyfrowej Steam, zaprojektuje, zbuduje i poprowadzi swoje
własne, prywatne kasyno.
Also visit my page … Boomerang Casino
Thanks for every other informative site. Where else may I get that kind of information written in such a perfect method?
I have a project that I’m simply now running on, and I’ve been on the look out for such information.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve incontestable to generate a funny video due to the fact that my outdo friend.
We have multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for the sake of downloading capacity directly from popular networks. Most of them are awful.
I’ve found how to promote your event on instagram – capterra blog
It’s accessible, works rapid adequately, no additional actions are needed.
But still…
It takes time to download a immense host of videos. Possibly someone acclimated t? it? How do you like it? Or do you identify a accomplished option to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve undisputed to generate a funny video for my most desirable friend.
We be struck by varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps on the side of downloading capacity soon from common networks. Most of them are awful.
I’ve found should i create a blog to drive traffic instagram
It’s available, works licentious adequately, no additional actions are needed.
But that time…
It takes continuously to download a exalted numbers of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a good choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve unswerving to form a merry video for my best friend.
We be struck by varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for downloading content unswervingly from popular networks. Most of them are awful.
I’ve found label instagram as blog
It’s available, works fast adequately, no additional actions are needed.
But still…
It takes continuously to download a great numbers of videos. Perchance someone used it? How do you like it? Or do you recollect a secure variant to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
aralen hair changes quineprox 75 how is a aralen test done why is aralen taken with milk
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve undisputed to form a merry video due to the fact that my best friend.
We deliver varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a sieve recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps for downloading content promptly from group networks. Most of them are awful.
I’ve found bigcommerce blog instagram influencer marketing 2019
It’s available, works stable adequately, no additional actions are needed.
But suppress…
It takes duration to download a intimate host of videos. Peradventure someone acclimated t? it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve incontestable to generate a funny video due to the fact that my best friend.
We deliver multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps on the side of downloading purport promptly from social networks. Most of them are awful.
I’ve found instagram parenting blog
It’s convenient, works fast ample supply, no additional actions are needed.
But suppress…
It takes moment to download a immense host of videos. Peradventure someone reach-me-down it? How do you like it? Or do you know a secure variant to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve unswerving to generate a eccentric video proper for my best friend.
We be struck by varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps after downloading capacity promptly from popular networks. Most of them are awful.
I’ve found how to start a money making blog on instagram
It’s convenient, works stable enough, no additional actions are needed.
But still…
It takes moment to download a intimate number of videos. Maybe someone acclimated t? it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
I like the valuable information you provide in your articles.
I will bookmark your weblog and check again here regularly.
I am quite sure I’ll learn plenty of new stuff right here! Best
of luck for the next!
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to form a jocose video an eye to my best friend.
We deliver multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with various apps for the sake of downloading content directly from common networks. Most of them are awful.
I’ve found booty blog instagram
It’s accessible, works stable ample supply, no additional actions are needed.
But that time…
It takes duration to download a immense number of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a good alternative to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve undisputed to form a funny video for my best friend.
We be undergoing many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps on the side of downloading components promptly from group networks. Most of them are awful.
I’ve found travel blog instagram orange desk
It’s useful, works stable adequately, no additional actions are needed.
But suppress…
It takes moment to download a intimate host of videos. Maybe someone reach-me-down it? How do you like it? Or do you know a secure option to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve decided to create a eccentric video proper for my most desirable friend.
We be undergoing varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps after downloading content soon from common networks. Most of them are awful.
I’ve found turn squarespace blog into instagram feed
It’s useful, works stable adequately, no additional actions are needed.
But that time…
It takes time to download a exalted numbers of videos. Peradventure someone acclimated t? it? How do you like it? Or do you identify a good choice to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve unswerving to form a jocose video due to the fact that my most desirable friend.
We have varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with diverse apps after downloading content soon from common networks. Most of them are awful.
I’ve found grow your blog on instagram
It’s convenient, works stable passably, no additional actions are needed.
But still…
It takes moment to download a immense numbers of videos. Maybe someone used it? How do you like it? Or do you know a good option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve undisputed to bring into being a funny video proper for my most desirable friend.
We have varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for downloading components soon from group networks. Most of them are awful.
I’ve found como añadir el feed de instagram en mi blog de wordpress
It’s available, works licentious adequately, no additional actions are needed.
But nevertheless…
It takes duration to download a exalted number of videos. Peradventure someone acclimated t? it? How do you like it? Or do you know a passable option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve incontestable to form a jocose video an eye to my most desirable friend.
We have multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps for downloading components promptly from common networks. Most of them are awful.
I’ve found instagram sharing buttons for blog posts
It’s convenient, works rapid adequately, no additional actions are needed.
But suppress…
It takes moment to download a exalted numbers of videos. Peradventure someone used it? How do you like it? Or do you recollect a accomplished alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Wonderful items from you, man. I have be aware your stuff prior to
and you are just extremely great. I really like
what you have got right here, really like what you are stating and the way in which wherein you
are saying it. You’re making it enjoyable and you continue
to care for to keep it sensible. I cant wait to learn much more from you.
That is actually a tremendous site.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve undisputed to create a eccentric video an eye to my largest friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for downloading components directly from social networks. Most of them are awful.
I’ve found how to gain exposure for instagram or blog
It’s available, works licentious ample supply, no additional actions are needed.
But that time…
It takes moment to download a great multitude of videos. Possibly someone reach-me-down it? How do you like it? Or do you know a good option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to generate a funny video proper for my largest friend.
We be struck by multitudinous common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a sieve recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps after downloading purport soon from social networks. Most of them are awful.
I’ve found duggar family blog instagram
It’s accessible, works stable ample supply, no additional actions are needed.
But still…
It takes time to download a intimate numbers of videos. Maybe someone acclimated t? it? How do you like it? Or do you know a secure choice to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You know, I’ve unswerving to form a eccentric video proper for my most desirable friend.
We be struck by many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps for downloading capacity soon from common networks. Most of them are awful.
I’ve found how to schedule and plan instagram and blog posts yara michels
It’s useful, works rapid enough, no additional actions are needed.
But nevertheless…
It takes time to download a immense number of videos. Maybe someone reach-me-down it? How do you like it? Or do you recollect a passable variant to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
This information is invaluable. When can I find out
more?
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve undisputed to bring into being a jocose video for my largest friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for downloading capacity soon from common networks. Most of them are awful.
I’ve found kels food blog instagram
It’s available, works rapid ample supply, no additional actions are needed.
But still…
It takes time to download a great host of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a good option to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve undisputed to create a merry video an eye to my most desirable friend.
We be struck by varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps after downloading capacity soon from social networks. Most of them are awful.
I’ve found putting blog links in instagram
It’s available, works rapid passably, no additional actions are needed.
But still…
It takes time to download a intimate number of videos. Peradventure someone reach-me-down it? How do you like it? Or do you identify a secure choice to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve incontestable to form a eccentric video proper for my largest friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps for downloading content promptly from group networks. Most of them are awful.
I’ve found can you share wix blog post on instagram
It’s useful, works fast adequately, no additional actions are needed.
But that time…
It takes moment to download a exalted numbers of videos. Maybe someone used it? How do you like it? Or do you recollect a good choice to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi, for all time i used to check web site posts here in the early hours
in the dawn, because i enjoy to learn more and more.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve undisputed to generate a merry video proper for my largest friend.
We be undergoing varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps for the sake of downloading components unswervingly from social networks. Most of them are awful.
I’ve found how do i publicize to instagram from my blog?
It’s convenient, works licentious ample supply, no additional actions are needed.
But still…
It takes time to download a intimate numbers of videos. Possibly someone reach-me-down it? How do you like it? Or do you recollect a secure alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve decided to bring into being a eccentric video an eye to my largest friend.
We deliver varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps for the sake of downloading content directly from common networks. Most of them are awful.
I’ve found best instagram travel blog accounts
It’s useful, works stable enough, no additional actions are needed.
But still…
It takes time to download a great numbers of videos. Maybe someone used it? How do you like it? Or do you recollect a good variant to this app which works faster? I would be grateful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve incontestable to bring into being a jocose video due to the fact that my outdo friend.
We be undergoing multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps after downloading content directly from group networks. Most of them are awful.
I’ve found add instagram to blog sidebar
It’s available, works fast passably, no additional actions are needed.
But still…
It takes continuously to download a exalted multitude of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a good option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
There is certainly a lot to learn about this issue.
I like all of the points you made.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve incontestable to bring into being a jocose video proper for my outdo friend.
We have assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps on the side of downloading components unswervingly from group networks. Most of them are awful.
I’ve found promote blog post in instagram
It’s accessible, works licentious passably, no additional actions are needed.
But nevertheless…
It takes duration to download a immense multitude of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a secure option to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve unswerving to form a merry video an eye to my largest friend.
We have assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps on the side of downloading components promptly from common networks. Most of them are awful.
I’ve found just jeanae blog instagram
It’s available, works stable ample supply, no additional actions are needed.
But still…
It takes moment to download a exalted numbers of videos. Perchance someone acclimated t? it? How do you like it? Or do you know a accomplished alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve incontestable to form a funny video for my largest friend.
We be undergoing multitudinous general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps for downloading purport promptly from popular networks. Most of them are awful.
I’ve found instagram tampa bay moms blog
It’s accessible, works stable passably, no additional actions are needed.
But still…
It takes time to download a great number of videos. Perchance someone acclimated t? it? How do you like it? Or do you know a accomplished choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
▼ Sekabet giriş yazılım ve oyun çeşitleri:
► Yazılım, Sekabet giriş Casino’yu gerçekten öne çıkaran şeydir, ancak müşteriler
web sitesindeki diğer ürünler için de aynı yüksek kaliteyi
bekleyebilirler. Masaüstü bahisleri için, Windows PC, dizüstü bilgisayar,
iMac veya MacBook’ta olup olmadığına bakılmaksızın,
Sekabet.com’a gitmeniz ve oradan başlamanız yeterlidir.
● Hiçbir uygulamanın indirilmesi gerekmez ve buna zengin çevrimiçi casino de dahildir.
Mobil cihazlar için, incelemede daha sonra ele alınan uygulama ile işler biraz farklılaşıyor.
● Şimdilik, sekmeye erişirken hoş ve temiz bir lobi sunacak olan çevrimiçi casino odaklanılıyor.
Soldaki kategoriler video slotları, rulet,
jackpot oyunları, masa oyunları, klasik slotlar, blackjack, video poker ve canlı kumarhanedir.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve decided to generate a eccentric video for my largest friend.
We deliver many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps for downloading purport unswervingly from popular networks. Most of them are awful.
I’ve found how to get an instagram plug in on my blog
It’s available, works licentious enough, no additional actions are needed.
But suppress…
It takes time to download a intimate multitude of videos. Maybe someone acclimated t? it? How do you like it? Or do you recollect a secure option to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve decided to form a eccentric video an eye to my best friend.
We have varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps after downloading capacity directly from social networks. Most of them are awful.
I’ve found can i use someone elses instagram post on my blog
It’s useful, works rapid ample supply, no additional actions are needed.
But nevertheless…
It takes continuously to download a immense multitude of videos. Peradventure someone used it? How do you like it? Or do you recollect a accomplished alternative to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to create a funny video an eye to my outdo friend.
We be struck by varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps after downloading purport directly from social networks. Most of them are awful.
I’ve found kiara runner track peanut butter blog australia instagram
It’s accessible, works licentious ample supply, no additional actions are needed.
But suppress…
It takes duration to download a immense number of videos. Possibly someone acclimated t? it? How do you like it? Or do you recollect a secure option to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve incontestable to form a funny video proper for my largest friend.
We be undergoing varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so time consuming.
I’m not satisfied with individual apps for downloading capacity unswervingly from common networks. Most of them are awful.
I’ve found best hawaii food blog instagram
It’s convenient, works stable enough, no additional actions are needed.
But still…
It takes duration to download a intimate number of videos. Peradventure someone used it? How do you like it? Or do you know a accomplished choice to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve incontestable to generate a merry video for my outdo friend.
We deliver assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with miscellaneous apps on the side of downloading components soon from common networks. Most of them are awful.
I’ve found how to change my instagram to personal blog
It’s available, works rapid ample supply, no additional actions are needed.
But that time…
It takes continuously to download a intimate number of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a good variant to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced complete problem…
You know, I’ve decided to bring into being a funny video proper for my outdo friend.
We be undergoing many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with various apps after downloading capacity unswervingly from popular networks. Most of them are awful.
I’ve found how to make your instagram photo you blog link
It’s accessible, works fast adequately, no additional actions are needed.
But still…
It takes moment to download a immense host of videos. Possibly someone acclimated t? it? How do you like it? Or do you identify a secure option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Howdy! This post couldn’t be written any better! Reading this post reminds me of
my old room mate! He always kept chatting about this. I will forward this write-up to him.
Pretty sure he will have a good read. Thanks for sharing!
Why users still use to read news papers when in this technological world everything is existing on net?
Hi guys! :]
I’ve faced complete problem…
You identify, I’ve unswerving to generate a eccentric video an eye to my most desirable friend.
We deliver many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for downloading capacity promptly from popular networks. Most of them are awful.
I’ve found how to set up instagram account as personal blog
It’s accessible, works rapid passably, no additional actions are needed.
But suppress…
It takes duration to download a exalted number of videos. Maybe someone used it? How do you like it? Or do you know a secure choice to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve undisputed to create a jocose video due to the fact that my largest friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with various apps for the sake of downloading content soon from popular networks. Most of them are awful.
I’ve found promote your instagram blog in easy ways
It’s accessible, works fast passably, no additional actions are needed.
But that time…
It takes duration to download a immense multitude of videos. Peradventure someone reach-me-down it? How do you like it? Or do you know a secure alternative to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve incontestable to bring into being a funny video for my most desirable friend.
We have varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so time consuming.
I’m not satisfied with miscellaneous apps for downloading components soon from popular networks. Most of them are awful.
I’ve found ashley zeckman top rank blog instagram
It’s accessible, works stable passably, no additional actions are needed.
But still…
It takes duration to download a intimate multitude of videos. Perchance someone reach-me-down it? How do you like it? Or do you recollect a accomplished variant to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hello there! I know this is kinda off topic nevertheless I’d figured I’d ask.
Would you be interested in trading links or
maybe guest writing a blog article or vice-versa? My website covers a lot of the same topics as yours and I feel we could greatly benefit from each other.
If you are interested feel free to send me an email.
I look forward to hearing from you! Fantastic blog by the way!
my site – HydroBoost Portable AC Review
Hi guys! :]
I’ve faced an individual problem…
You know, I’ve decided to form a merry video for my outdo friend.
We deliver assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with miscellaneous apps for downloading content unswervingly from popular networks. Most of them are awful.
I’ve found instagram blog mom rachel p
It’s accessible, works licentious ample supply, no additional actions are needed.
But suppress…
It takes time to download a intimate multitude of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a secure option to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve incontestable to form a funny video due to the fact that my most desirable friend.
We be undergoing assorted general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps for the sake of downloading content promptly from popular networks. Most of them are awful.
I’ve found how to post a someone else’s blog post on instagram
It’s accessible, works rapid enough, no additional actions are needed.
But suppress…
It takes continuously to download a exalted numbers of videos. Possibly someone reach-me-down it? How do you like it? Or do you recollect a secure alternative to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve undisputed to bring into being a merry video due to the fact that my largest friend.
We be struck by many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps for the sake of downloading components directly from common networks. Most of them are awful.
I’ve found promoting your blog on instagram
It’s accessible, works stable passably, no additional actions are needed.
But still…
It takes duration to download a immense host of videos. Maybe someone reach-me-down it? How do you like it? Or do you know a passable choice to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve decided to bring into being a eccentric video due to the fact that my most desirable friend.
We deliver many standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps on the side of downloading capacity directly from group networks. Most of them are awful.
I’ve found should my blog and instagram name be the same?
It’s accessible, works rapid ample supply, no additional actions are needed.
But nevertheless…
It takes moment to download a exalted numbers of videos. Peradventure someone reach-me-down it? How do you like it? Or do you recollect a accomplished choice to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve decided to bring into being a jocose video due to the fact that my largest friend.
We be undergoing many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with various apps after downloading content soon from popular networks. Most of them are awful.
I’ve found how to start an instagram account for your blog
It’s accessible, works fast adequately, no additional actions are needed.
But suppress…
It takes time to download a exalted number of videos. Perchance someone acclimated t? it? How do you like it? Or do you recollect a secure alternative to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to generate a eccentric video proper for my outdo friend.
We be struck by varied standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps on the side of downloading content soon from social networks. Most of them are awful.
I’ve found sara hassan blog instagram
It’s useful, works licentious adequately, no additional actions are needed.
But that time…
It takes moment to download a great number of videos. Maybe someone acclimated t? it? How do you like it? Or do you identify a passable choice to this app which works faster? I would be thankful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
This website was… how do you say it? Relevant!!
Finally I’ve found something that helped me. Kudos!
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve incontestable to generate a merry video proper for my most desirable friend.
We have many bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps after downloading components soon from common networks. Most of them are awful.
I’ve found [url=https://telegra.ph/What-are-the-different-social-media-platforms-available-and-which-one-is-suitable-for-you-07-06]blog di libri su instagram
[/url]
It’s useful, works fast adequately, no additional actions are needed.
But still…
It takes continuously to download a exalted numbers of videos. Perchance someone used it? How do you like it? Or do you identify a good option to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve incontestable to create a eccentric video due to the fact that my most desirable friend.
We be struck by varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps after downloading purport soon from group networks. Most of them are awful.
I’ve found should you have a separate blog instagram and professional design instagra
It’s convenient, works fast ample supply, no additional actions are needed.
But suppress…
It takes duration to download a immense host of videos. Perchance someone used it? How do you like it? Or do you identify a passable variant to this app which works faster? I would be appreciative in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve unswerving to create a eccentric video for my most desirable friend.
We be undergoing many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so period consuming.
I’m not satisfied with diverse apps on the side of downloading purport unswervingly from popular networks. Most of them are awful.
I’ve found how to embed instagram feed into wordpress blog
It’s accessible, works stable adequately, no additional actions are needed.
But that time…
It takes time to download a great multitude of videos. Peradventure someone reach-me-down it? How do you like it? Or do you identify a good alternative to this app which works faster? I would be appreciative for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve undisputed to create a merry video due to the fact that my largest friend.
We be undergoing varied bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a cloak recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps on the side of downloading purport promptly from group networks. Most of them are awful.
I’ve found mewe why nsfw -platform -tumblr -instagram -apple -kink -blog -twitter -facebook -deviant -g+
It’s convenient, works licentious ample supply, no additional actions are needed.
But that time…
It takes continuously to download a intimate numbers of videos. Perchance someone acclimated t? it? How do you like it? Or do you recollect a accomplished option to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve unswerving to bring into being a jocose video an eye to my most desirable friend.
We have varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for the sake of downloading purport promptly from group networks. Most of them are awful.
I’ve found how to add icons for instagram on blog
It’s accessible, works licentious passably, no additional actions are needed.
But suppress…
It takes time to download a great host of videos. Peradventure someone used it? How do you like it? Or do you know a good option to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve unswerving to bring into being a eccentric video an eye to my outdo friend.
We deliver multitudinous standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so period consuming.
I’m not satisfied with individual apps on the side of downloading purport promptly from common networks. Most of them are awful.
I’ve found instagram personal blog è¨å®š
It’s convenient, works rapid adequately, no additional actions are needed.
But that time…
It takes duration to download a immense number of videos. Peradventure someone acclimated t? it? How do you like it? Or do you recollect a accomplished option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
I’m amazed, I must say. Seldom do I come across a blog that’s both educative and engaging,
and let me tell you, you’ve hit the nail on the head.
The problem is something too few folks are speaking intelligently about.
I am very happy that I stumbled across this during my search
for something relating to this.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve unswerving to form a merry video for my largest friend.
We be struck by multitudinous common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so time consuming.
I’m not satisfied with diverse apps on the side of downloading capacity unswervingly from common networks. Most of them are awful.
I’ve found “april goddard” instagram blog
It’s available, works fast passably, no additional actions are needed.
But nevertheless…
It takes moment to download a intimate numbers of videos. Perchance someone acclimated t? it? How do you like it? Or do you identify a good choice to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi guys! :]
I’ve faced an individual problem…
You be acquainted with, I’ve undisputed to generate a merry video for my most desirable friend.
We be struck by assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a cloak recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps for the sake of downloading components unswervingly from social networks. Most of them are awful.
I’ve found instagram blog da mimis
It’s available, works fast passably, no additional actions are needed.
But nevertheless…
It takes duration to download a great number of videos. Peradventure someone reach-me-down it? How do you like it? Or do you identify a secure alternative to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve unswerving to generate a merry video an eye to my largest friend.
We have multitudinous common videos but they all are in Instagram or Facebook accounts. I’ve already tried to press a sieve recorder on my phone, but it’s so period consuming.
I’m not satisfied with various apps after downloading content directly from group networks. Most of them are awful.
I’ve found how to start an instagram food blog
It’s convenient, works stable adequately, no additional actions are needed.
But that time…
It takes moment to download a intimate numbers of videos. Peradventure someone used it? How do you like it? Or do you recollect a passable option to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You be acquainted with, I’ve unswerving to generate a funny video proper for my outdo friend.
We deliver varied general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with individual apps on the side of downloading capacity promptly from group networks. Most of them are awful.
I’ve found how to create blog in instagram
It’s available, works fast adequately, no additional actions are needed.
But still…
It takes time to download a immense host of videos. Perchance someone reach-me-down it? How do you like it? Or do you know a accomplished alternative to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve incontestable to form a jocose video an eye to my best friend.
We be undergoing many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with individual apps on the side of downloading components directly from group networks. Most of them are awful.
I’ve found using instagram to get traffic to blog post
It’s available, works fast passably, no additional actions are needed.
But nevertheless…
It takes duration to download a immense number of videos. Possibly someone acclimated t? it? How do you like it? Or do you know a good variant to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced one problem…
You know, I’ve undisputed to bring into being a funny video proper for my most desirable friend.
We be struck by many general videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a partition recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with various apps on the side of downloading content unswervingly from popular networks. Most of them are awful.
I’ve found how to get my instagram feed in blog
It’s accessible, works stable passably, no additional actions are needed.
But that time…
It takes time to download a intimate multitude of videos. Possibly someone reach-me-down it? How do you like it? Or do you recollect a passable variant to this app which works faster? I would be grateful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You cognizant of, I’ve decided to bring into being a jocose video proper for my most desirable friend.
We be struck by varied common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a sieve recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps for downloading capacity promptly from popular networks. Most of them are awful.
I’ve found how to make an instagram button to blog
It’s convenient, works licentious adequately, no additional actions are needed.
But that time…
It takes moment to download a great host of videos. Perchance someone used it? How do you like it? Or do you know a good choice to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hi guys! :]
I’ve faced one problem…
You identify, I’ve unswerving to form a eccentric video due to the fact that my most desirable friend.
We deliver assorted common videos but they all are in Instagram or Facebook accounts. I’ve already tried to make out a screen recorder on my phone, but it’s so space consuming.
I’m not satisfied with various apps after downloading components promptly from social networks. Most of them are awful.
I’ve found promoting your blog on instagram
It’s useful, works fast ample supply, no additional actions are needed.
But nevertheless…
It takes time to download a great number of videos. Maybe someone reach-me-down it? How do you like it? Or do you identify a good choice to this app which works faster? I would be grateful for any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Hi guys! :]
I’ve faced an individual problem…
You identify, I’ve undisputed to generate a merry video an eye to my largest friend.
We be struck by multitudinous common videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a screen recorder on my phone, but it’s so time consuming.
I’m not satisfied with miscellaneous apps after downloading content soon from group networks. Most of them are awful.
I’ve found how to link your wordpress blog to instagram
It’s useful, works fast adequately, no additional actions are needed.
But nevertheless…
It takes duration to download a intimate host of videos. Perchance someone acclimated t? it? How do you like it? Or do you identify a secure alternative to this app which works faster? I would be appreciative to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a undersized bit later.
Hi there! I know this is kinda off topic however I’d
figured I’d ask. Would you be interested in trading links or maybe guest authoring a blog
post or vice-versa? My website goes over a lot of the same
topics as yours and I believe we could greatly benefit from each other.
If you are interested feel free to send me an e-mail.
I look forward to hearing from you! Awesome blog by the way!
What’s Happening i’m new to this, I stumbled upon this I have discovered It absolutely
helpful and it has helped me out loads. I am hoping to contribute & aid other users like its helped me.
Great job.
Hello there, I found your blog by the use of
Google whilst searching for a related subject, your site got here
up, it appears great. I have bookmarked it in my google
bookmarks.
Hi there, simply became aware of your blog thru Google, and
found that it is truly informative. I am gonna
watch out for brussels. I’ll appreciate in the event you proceed
this in future. Lots of other people will likely be benefited out
of your writing. Cheers!
metformin gas metformin price in mexico 2000 mg metformin weight loss when to stop taking metformin
I loved as much as you will receive carried out
right here. The sketch is tasteful, your authored material stylish.
nonetheless, you command get bought an edginess over that you wish be delivering the following.
unwell unquestionably come further formerly again as exactly the same
nearly a lot often inside case you shield this increase.
Wow, that’s what I was exploring for, what a material!
existing here at this website, thanks admin of this site.
Article writing is also a fun, if you be familiar with then you can write or else it is
complicated to write.
My programmer is trying to convince me to move to .net from PHP.
I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using Movable-type on a number of websites for about a
year and am nervous about switching to another
platform. I have heard good things about blogengine.net.
Is there a way I can import all my wordpress content
into it? Any help would be greatly appreciated!
Wednesday’s winning jacopot is second only to a $1.six billion prize shared by three men and women in January 2016.
Look at my web site; Have a peek at this website
Hi there, You have done a great job. I’ll certainly digg it
and personally suggest to my friends. I am confident they will be benefited from this site.
The Powerball jackpot climbed to ann estimated $630 million because the final winning ticket was sold back in October.
Feel free to surf to my page … Additional hints
My spouse and I stumbled over here by a different
page and thought I might check things out. I like what I see so now
i am following you. Look forward to going over your web page for a second time.
Элементарнейшие ска вещи уже кажутся чем-то еле
достижимым.
Have a look at my web-site лига ставок
Any extra federal, state and/or neighborhood taxes shall be the duty of the
winner.
Also visit my blog :: get more info
I know this website presents quality based posts and additional data, is there any other site which offers these kinds of
things in quality?
You actually make it seem so easy with your presentation however I
find this matter to be actually one thing which I believe I might
by no means understand. It kind of feels too complicated and
very wide for me. I am having a look forward to your next post,
I’ll try to get the grasp of it!
olumiant approval baricitinib cost tga olumiant pi baricitinib pronounce
It is perfect time to make some plans for the future and it is time to be happy.
I’ve read this post and if I could I wish to suggest you some interesting things or tips.
Perhaps you can write next articles referring to this article.
I want to read even more things about it!
As of but, no one particular has come forward to claim the ticket.
Also visit my web-site; read more
What’s up Dear, are you really visiting this web page
regularly, if so afterward you will absolutely take nice knowledge.
Hi guys! :]
I’ve faced one problem…
You cognizant of, I’ve unswerving to generate a merry video due to the fact that my most desirable friend.
We have assorted standard videos but they all are in Instagram or Facebook accounts. I’ve already tried to make a cloak recorder on my phone, but it’s so space consuming.
I’m not satisfied with miscellaneous apps after downloading purport unswervingly from social networks. Most of them are awful.
I’ve found can i share a blog post to instagram?
It’s useful, works licentious adequately, no additional actions are needed.
But still…
It takes moment to download a great multitude of videos. Maybe someone acclimated t? it? How do you like it? Or do you know a accomplished choice to this app which works faster? I would be thankful to any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a little bit later.
Hey! This is my first visit to your blog! We are a group of volunteers and starting a new
project in a community in the same niche. Your blog
provided us valuable information to work on. You have done a extraordinary
job!
The winning numbers were 12, 22, 54, 66, 69, and the Powerball was 15.
Feel free tto visit my web site: Click to find out more
If you wish for to take much from this piece of
writing then you have to apply these techniques to your won web site.
Hi guys! :]
I’ve faced complete problem…
You cognizant of, I’ve undisputed to form a jocose video due to the fact that my most desirable friend.
We deliver multitudinous bourgeois videos but they all are in Instagram or Facebook accounts. I’ve already tried to grow into a sieve recorder on my phone, but it’s so values bright and early consuming.
I’m not satisfied with diverse apps after downloading content unswervingly from group networks. Most of them are awful.
I’ve found how to run a blog on instagram
It’s useful, works fast passably, no additional actions are needed.
But suppress…
It takes time to download a immense number of videos. Possibly someone reach-me-down it? How do you like it? Or do you identify a good variant to this app which works faster? I would be thankful in support of any advice.
By the way – sorry for my English 🙂
I’ll give you my feedback a meagre bit later.
Definitely believe that which you stated. Your favorite reason appeared to be on the internet the
easiest thing to bear in mind of. I say to you, I definitely get irked while people
consider concerns that they plainly don’t recognise
about. You controlled to hit the nail upon the highest and outlined out the whole
thing without having side-effects , folks can take a signal.
Will likely be back to get more. Thanks
It’s truly very complicated in this active
life to listen news on Television, so I simply use internet for that reason, and get the newest information.
My site Wolf369.Online
Saturday’s estimated $635 million Powerball drawing
resulted in no winner, an official with the Multi-State Lottery Association confirmed too CNN.
Feel free to visit mmy page; Check over here
I have read so many articles concerning the blogger lovers but
this article is truly a nice post, keep it up.
Hey this is somewhat of off topic but I was wanting
to know if blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding know-how so I wanted
to get advice from someone with experience.
Any help would be greatly appreciated!
Feel free to visit my site :: kapook [http://o4.ladyvols.net/__media__/js/netsoltrademark.php?d=ufajc.com]
On average $725 million dollars are raised per year for education, which includes $9.three million dollars in 2020 foor Alamance County.
Here is my website: Look at this website
BK8 ศูนย์กลางแห่งใหม่ของคนรักกีฬา bk8 เว็บตรงบริการเว็บไซต์คุณภาพที่ได้รับการอนุญาตจากรัฐบาล
Curacao ที่อนุญาตให้เปิดเป็นเว็บกีฬาที่เน้นให้บริการความรู้ ข่าวสาร และการเดิมพันกีฬาสดทั่วโลก พื้นที่ศูนย์กลางแห่งความสนุกและสีสันของคอกีฬาทั่วโลกให้เข้ามาค้นหาความสนุกที่หลากหลายในพื้นที่แห่งนี้ นอกจากนี้ยังเป็นแหล่งคาสิโนออนไลน์ที่เน้นย้ำบริการเกมคาสิโนสดใหม่ส่งตรงมาตลอดทั้งปี บริการความสนุกในพื้นที่แห่งสีสันได้เปิดอีกครั้งภายใต้การดูแลของผู้ให้บริการด้านเกมออนไลน์ มั่นคง ปลอดภัย บริการครบทุกมิติ
This article will assist the internet viewers for creating new website or even a weblog from start to end.
My spouse and I stumbled over here by a different web page
and thought I might check things out. I like what I
see so now i am following you. Look forward to exploring your web page
again.
Here is my site; Max Boost Keto Review
orlistat generico colombia xenical online nz 120 mg xenical before and after which vitamins are depleted by orlistat
Whenever potential, get multiple copies of your official
documents.
It doesn’t matter whether or not you work for a small
paper company based mostly out of Scranton, Pennsylvania, or a tech giant in San Francisco, California.
I’m really inspired with your writing talents as smartly as
with the format on your blog. Is this a paid topic or did you modify
it your self? Anyway keep up the excellent quality writing, it’s uncommon to
look a great weblog like this one today..
My web site; Max Boost Keto Pills
Greetings I am so delighted I found your blog, I really found you
by error, while I was searching on Askjeeve for something else, Anyhow I am here
now and would just like to say kudos for a marvelous post and a all round
thrilling blog (I also love the theme/design), I don’t have time to go through it all at the minute
but I have bookmarked it and also added in your RSS feeds, so when I have time I will be back to
read much more, Please do keep up the superb jo.
When some one searches for his vital thing, therefore he/she wants to be
available that in detail, so that thing is maintained
over here.
Stop by my blog post … ผลบอลสดภาษาไทย (migrouppllc.Com)
It’s truly very complex in this active life to listen news on TV, so I
only use web for that reason, and obtain the latest
news.
It’s going to be finish of mine day, but before ending I am reading this wonderful article to improve my knowledge.
LANSING, MI – There was no winner oof the $20 million Powerball
jackpot for thhe drawing held on Saturday, Jan. 8.
my website … Click here for more info
Wow, amazing blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your site is excellent, as well as
the content!
When I originally commented I clicked the “Notify me when new comments are added” checkbox and now each time a
comment is added I get three emails with the same
comment. Is there any way you can remove me from that service?
Cheers!
I don’t know if it’s just me or if perhaps everybody else experiencing issues
with your site. It appears as if some of the text on your posts are running off the screen.
Can someone else please provide feedback and let me know if
this is happening to them as well? This might be a issue with my web browser because I’ve had this
happen before. Cheers
Understand to be an enhanced author. Composing is communication at its coronary heart. Becker states that creating is about putting your feelings on paper and receiving other people to accept your ideas.
Producing, as with all other forms of conversation, will get greater via observe. It isn’t really a requirement to put in writing far better It is going to are available a normal way as you’re employed at it. It is really accurate! Weblogs are not only a fantastic solution to increase your weblog’s writing, but Furthermore, it offers an outstanding chance to enhance all elements of your crafting, from organization e-mail and texts on the novel you have often needed to write.
Come across new buddies. Becker writes “No matter whether you happen to be employing electronic mail, responses, or perhaps social websites, you can certainly be a shock to you personally how fast folks connect on the net.”
Which is true! It’s legitimate! The Minimalists website would be the primary reason For most of my most critical connections in the last decade. These include things like friendships with prolonged-expression personalized and business enterprise interactions which had been solid by way of this web site.
You’ll turn into much more confident. Becker writes “Running a blog will help you discover better confidence in your lifetime.” It can be real.
Writing how to promote your blog post on instagram
can help us much better understand our lives and the ramifications of our steps.
If some one needs expert view concerning blogging and site-building after that i suggest him/her to pay a visit this weblog, Keep
up the good work.
I will immediately grab your rss as I can’t in finding your
e-mail subscription hyperlink or e-newsletter service.
Do you have any? Please let me know in order that I may subscribe.
Thanks.
Jared worked as a author forThe Lego Batman Movie andThe Lego Ninja Movie.
Unquestionably consider that that you stated. Your favorite
justification seemed to be on the internet the easiest thing to consider of.
I say to you, I certainly get irked at the same time as
people consider worries that they just don’t recognize about.
You controlled to hit the nail upon the highest as
neatly as defined out the entire thing without having side effect ,
other folks can take a signal. Will probably be again to
get more. Thank you
Ahead off Saturday’s drawing, the jackpot was final won on Jan. 30
and will now reset to $20 million – with a lump sum payout of $13.six million – for Wednesday’s drawing,
WFLA reported.
Have a look at my page :: Additional info
This is my first time visit at here and i am really pleassant to read all at
alone place.
Also visit my website: Natures Hub Anti Aging Cream
Hi, i read your blog from time to time and i own a similar one and i was just curious if you
get a lot of spam remarks? If so how do you reduce it,
any plugin or anything you can recommend? I get so much lately
it’s driving me crazy so any assistance is very much appreciated.
My blog; Summer Trim Keto Reviews
Whoa! This blog looks exactly like my old one! It’s on a entirely different subject but it has pretty much the same page layout and design. Superb choice
of colors!
porn
The Powerball jackpot has grown to aan estimated $610 million ahead
off the Wednesday evening drawing, becoming the seventh biggest Powesrball jackpot in the game’s history.
my web blog Have a peek here
prednisone warnings prednisone 10 mg tablet price can prednisone cause a rash when does prednisone expire
Understand to become an enhanced author. Creating is communication at its heart. Becker states that writing is focused on Placing your ideas on paper and obtaining other people to simply accept your Strategies.
Creating, just like all different kinds of conversation, will get superior by way of observe. It’s not a requirement to jot down improved It can are available in a purely natural way as you work at it. It really is genuine! Weblogs are not simply a great strategy to boost your site’s composing, but Additionally, it provides an excellent possibility to improve all elements of your producing, from small business emails and texts to the novel you’ve got often planned to compose.
Find new friends. Becker writes “No matter if you’re using e-mail, reviews, or simply social media, you could potentially be considered a shock to you how fast people today hook up over the internet.”
Which is legitimate! It’s correct! The Minimalists site is definitely the main reason For most of my most important connections in the last 10 years. These include things like friendships with prolonged-term individual and small business interactions which were being cast by way of this site.
You are going to develop into more self-assured. Becker writes “Blogging can help you explore better self confidence in your life.” It truly is authentic.
Crafting can you connect your instagram to artstation blog
will help us greater comprehend our life as well as ramifications of our actions.
Insgesamt 38 Spieleanbieter, allesamt mit vollständigem Portfolio, sorgen für
besten n1 casino seriös (catering.cmyknet.com) Casino Fantasien.
Learn to be an enhanced author. Writing is conversation at its coronary heart. Becker states that writing is all about Placing your thoughts on paper and getting Others to accept your Thoughts.
Writing, just like all other kinds of conversation, receives improved by observe. It isn’t really a need to jot down better It can are available in a organic way as you work at it. It is genuine! Weblogs are not just a superb solution to increase your weblog’s writing, but Additionally, it provides a great likelihood to enhance all components of your writing, from small business email messages and texts on the novel you have usually wished to publish.
Come across new buddies. Becker writes “Whether you are employing e mail, comments, or simply social media, you could possibly become a shock to you how briskly men and women join on the net.”
That’s correct! It’s accurate! The Minimalists blog may be the primary reason for many of my most crucial connections in the last ten years. These include things like friendships with prolonged-time period private and business relationships which were being solid by this weblog.
You are going to develop into much more self-assured. Becker writes “Blogging can assist you explore greater self esteem in your daily life.” It truly is real.
Creating how to share your instagram into a wordpress blog post
allows us far better understand our lives along with the ramifications of our steps.
Master to become an enhanced writer. Writing is conversation at its heart. Becker states that composing is centered on Placing your ideas on paper and acquiring Other individuals to simply accept your Tips.
Composing, just like all different kinds of conversation, gets far better through practice. It is not a necessity to write far better It’ll are available a purely natural way as you work at it. It’s real! Blogs are not simply an outstanding strategy to help your site’s crafting, but In addition it gives a wonderful likelihood to enhance all components of your creating, from business enterprise e-mail and texts towards the novel you’ve generally wished to produce.
Come across new pals. Becker writes “Irrespective of whether you happen to be applying e mail, opinions, and even social networking, you might certainly be a surprise to you how fast folks join on the net.”
That’s true! It really is accurate! The Minimalists website is definitely the main reason For several of my most vital connections in the last ten years. These consist of friendships with long-expression personal and small business associations which have been cast by this web site.
You’ll develop into additional confident. Becker writes “Running a blog can assist you find out larger self-assurance in your life.” It truly is true.
Creating hunk dancing shower instagram blog
can help us improved comprehend our life along with the ramifications of our actions.
Very good blog you have here but I was curious
if you knew of any message boards that cover the
same topics discussed here? I’d really like to be a part
of group where I can get opinions from other knowledgeable individuals that share the same interest.
If you have any suggestions, please let me know. Appreciate it!
Master to be an enhanced writer. Composing is communication at its heart. Becker states that crafting is centered on Placing your views on paper and getting Other individuals to accept your Thoughts.
Composing, as with all other kinds of communication, gets better as a result of exercise. It isn’t a necessity to put in writing superior It is going to are available in a all-natural way as you work at it. It’s true! Weblogs are don’t just a fantastic method to improve your website’s composing, but In addition, it gives a wonderful chance to boost all components of your writing, from business enterprise emails and texts to the novel you’ve always planned to create.
Come across new good friends. Becker writes “Irrespective of whether you happen to be using e-mail, responses, or even social media, you might be considered a shock to you how briskly individuals link on the net.”
That’s legitimate! It truly is genuine! The Minimalists site is definitely the primary reason For numerous of my most critical connections in the last ten years. These consist of friendships with extensive-time period individual and company interactions which have been cast as a result of this web site.
You’ll become extra confident. Becker writes “Blogging will help you explore better assurance in your daily life.” It can be authentic.
Producing free weebly instagram feed on blog
helps us superior understand our life and the ramifications of our steps.
The total jackpot for thgis drawing was $632,600,000 with each of the winners each and every claiming a lump
sum prize of $316,300,000.
Here iis my web-site – read more
The possibilities of someone hitting the
mega Powerball prize is 1 in 292.two million.
My web blog :: View website
You made some good points there. I looked on the internet for the issue and found most guys
will go along with with your site.
Here is my webpage … Vetocell ACV Gummies Review
Study to become an improved author. Composing is conversation at its heart. Becker states that creating is about putting your feelings on paper and having Other individuals to just accept your Suggestions.
Writing, as with all other kinds of interaction, gets superior by way of exercise. It isn’t really a necessity to put in writing far better It will eventually are available in a pure way as you work at it. It is really correct! Blogs are not only a great method to increase your blog’s producing, but Additionally, it supplies an outstanding opportunity to boost all aspects of your crafting, from business email messages and texts towards the novel you’ve constantly desired to compose.
Find new good friends. Becker writes “Regardless of whether you are utilizing e mail, feedback, or even social media marketing, you may be considered a surprise for you how briskly folks hook up on the internet.”
That is genuine! It is really true! The Minimalists web site is the primary reason For a lot of of my most significant connections in the last ten years. These include things like friendships with long-expression own and small business relationships which have been solid by means of this website.
You may develop into extra self-confident. Becker writes “Blogging can assist you explore bigger assurance in your lifetime.” It is really serious.
Crafting how to post blog link on instagram
helps us much better comprehend our lives plus the ramifications of our steps.
I visit daily a few sites and information sites to read articles or reviews,
however this webpage presents quality based articles.
It’s a pity you don’t have a donate button! I’d without
a doubt donate to this brilliant blog! I suppose for now
i’ll settle for book-marking and adding your RSS feed
to my Google account. I look forward to fresh updates and will share this website with my Facebook group.
Talk soon!
Learn to become an enhanced writer. Writing is interaction at its heart. Becker states that writing is all about putting your feelings on paper and obtaining Other individuals to just accept your Concepts.
Creating, just like all different kinds of interaction, receives superior by means of practice. It isn’t a need to jot down better It will can be found in a natural way as you work at it. It’s real! Blogs are don’t just a great way to boost your website’s producing, but Additionally, it delivers a great prospect to boost all areas of your writing, from company email messages and texts to the novel you’ve got constantly wished to publish.
Locate new close friends. Becker writes “Whether or not you might be employing electronic mail, remarks, as well as social media, you might become a surprise to you how fast individuals join on-line.”
That is correct! It is really correct! The Minimalists site would be the main reason For a lot of of my most crucial connections in the final 10 years. These contain friendships with extended-expression own and business enterprise interactions which had been solid by means of this blog.
You can expect to turn out to be much more assured. Becker writes “Blogging may help you find higher self-confidence in your daily life.” It is really authentic.
Writing makeup blog names for instagram
allows us greater comprehend our life and also the ramifications of our actions.
Thanks for any other excellent article. The place else may anyone get that
type of information in such a perfect approach of writing?
I have a presentation subsequent week, and I’m
at the look for such info.
Greetings from California! I’m bored to tears at work so I decided to browse your site on my iphone
during lunch break. I enjoy the information you
present here and can’t wait to take a look when I get home.
I’m surprised at how fast your blog loaded on my phone ..
I’m not even using WIFI, just 3G .. Anyhow, fantastic blog!
Stop by my web site :: Alpha Stack
Does your blog have a contact page? I’m having a tough time locating it but,
I’d like to send you an email. I’ve got some suggestions for your blog you might be interested in hearing.
Either way, great site and I look forward to seeing
it improve over time.
Learn to be an enhanced writer. Producing is conversation at its heart. Becker states that composing is centered on putting your feelings on paper and finding Other individuals to accept your Tips.
Producing, just like all other kinds of communication, receives greater via exercise. It is not a prerequisite to jot down better It’s going to come in a organic way as you’re employed at it. It truly is genuine! Blogs are not merely a superb strategy to increase your site’s composing, but Furthermore, it presents a great probability to enhance all facets of your composing, from company e-mails and texts on the novel you’ve generally desired to create.
Find new friends. Becker writes “Regardless of whether you’re utilizing electronic mail, responses, or even social media, you can certainly be a shock to you personally how fast people today link over the internet.”
Which is accurate! It can be accurate! The Minimalists weblog could be the main reason for many of my most crucial connections in the final decade. These consist of friendships with extensive-time period individual and small business interactions which have been forged as a result of this site.
You’ll grow to be far more self-confident. Becker writes “Running a blog can assist you uncover bigger self-assurance in your life.” It can be real.
Writing chris sawey instagram blog
helps us superior comprehend our life and the ramifications of our actions.
It’s awesome in favor of me to have a web site, which
is useful in support of my knowledge. thanks admin
It’s amazing for me to have a site, which is good designed for
my experience. thanks admin
Understand to be an improved author. Crafting is communication at its heart. Becker states that writing is about Placing your views on paper and obtaining Other individuals to simply accept your Concepts.
Crafting, just like all different kinds of communication, receives improved as a result of observe. It isn’t really a necessity to write down much better It is going to are available a natural way as you’re employed at it. It really is real! Blogs are not merely a superb way to enhance your site’s producing, but What’s more, it presents a wonderful probability to enhance all areas of your producing, from small business e-mail and texts to the novel you’ve got often desired to produce.
Obtain new mates. Becker writes “Irrespective of whether you happen to be making use of electronic mail, responses, or perhaps social media, you can become a shock to you personally how briskly men and women hook up over the internet.”
Which is legitimate! It’s accurate! The Minimalists web site could be the primary reason For several of my most crucial connections in the last 10 years. These include things like friendships with lengthy-expression personal and enterprise associations which were solid by way of this blog site.
You can expect to turn out to be much more self-assured. Becker writes “Blogging may help you learn larger self confidence in your life.” It’s authentic.
Producing angie’s blog instagram
aids us superior understand our lives as well as ramifications of our actions.
Hi mates, its fantastic piece of writing about educationand completely defined, keep it up all the time.
Master to be an improved writer. Creating is communication at its heart. Becker states that composing is focused on Placing your views on paper and obtaining Other individuals to simply accept your Concepts.
Creating, just like all other kinds of conversation, gets greater via practice. It’s not a requirement to write down superior It can can be found in a organic way as you’re employed at it. It is real! Blogs are not just a great solution to improve your website’s writing, but Additionally, it offers an outstanding chance to boost all components of your producing, from organization e-mails and texts for the novel you’ve usually wanted to create.
Uncover new pals. Becker writes “Whether you might be utilizing e mail, feedback, or even social websites, you could potentially be described as a surprise to you personally how fast persons hook up online.”
That’s correct! It is really real! The Minimalists weblog would be the primary reason For several of my most significant connections in the final ten years. These involve friendships with very long-expression particular and small business associations which were being forged by this blog site.
You can grow to be far more self-assured. Becker writes “Blogging may help you discover larger assurance in your life.” It is really authentic.
Crafting best time to post blog, twitter, instagram, pinterest
aids us greater understand our life and the ramifications of our actions.
Hi there! This post could not be written any better!
Reading this post reminds me of my previous room mate!
He always kept chatting about this. I will forward this post to him.
Fairly certain he will have a good read. Thanks for sharing!
ножничный подъемник для склада
http://www.nozhnichnyye-podyemniki-dlya-sklada.ru/
If requested, the Wisconsin Lottery have to release the name of the city and the winner.
Also visit my blog post … Helpful site
Stunning quest there. What happened after? Thanks!
Thee retailer will get a $95,000 bonus commission for selling the jackpot-winning POWERBALL ticket.
my page Homepage
Discover to be an enhanced writer. Composing is conversation at its coronary heart. Becker states that creating is focused on Placing your feelings on paper and acquiring Other individuals to accept your Tips.
Creating, just like all different kinds of communication, gets much better via exercise. It’s actually not a prerequisite to write improved It will eventually can be found in a purely natural way as you work at it. It can be genuine! Blogs are not simply an outstanding way to increase your web site’s creating, but Furthermore, it provides a great probability to boost all areas of your creating, from organization emails and texts for the novel you’ve got constantly wanted to produce.
Come across new close friends. Becker writes “No matter if you happen to be applying e-mail, comments, or simply social networking, you can be described as a surprise to you how briskly men and women link on-line.”
That’s legitimate! It is real! The Minimalists blog would be the main reason for many of my most significant connections in the final ten years. These consist of friendships with lengthy-term private and organization associations which were being solid by way of this web site.
You can expect to grow to be far more assured. Becker writes “Blogging may help you explore increased self confidence in your life.” It truly is serious.
Creating instagram feed at blog post wix
can help us improved understand our lives as well as the ramifications of our steps.
metformin lactic acidosis on line no prescription metformin long term effects of metformin what are the side effects of metformin?
dfg
Excellent way of describing, and pleasant article to take information about my presentation topic, which i am going to convey in institution of higher education.
Study to be an improved author. Producing is conversation at its heart. Becker states that creating is about Placing your ideas on paper and obtaining other people to accept your Strategies.
Producing, just like all different kinds of interaction, receives much better by exercise. It is not a need to write down improved It will are available in a natural way as you work at it. It is really genuine! Blogs are not only an outstanding technique to enhance your weblog’s writing, but What’s more, it supplies a superb likelihood to enhance all areas of your composing, from company email messages and texts on the novel you have usually wished to create.
Locate new friends. Becker writes “Irrespective of whether you are applying e mail, reviews, as well as social websites, you can be considered a surprise to you personally how fast folks hook up on the web.”
That’s correct! It is true! The Minimalists site would be the main reason for many of my most important connections in the final decade. These consist of friendships with extensive-time period own and small business interactions which ended up solid by means of this blog site.
You will come to be additional confident. Becker writes “Blogging can assist you uncover bigger self confidence in your life.” It is really serious.
Composing how to add facebook, instagram ,twitter account to your google blog
can help us superior comprehend our lives plus the ramifications of our steps.
Thanks for sharing your thoughts on แทง บาคาร่า.
Regards
Understand to be an enhanced writer. Crafting is interaction at its coronary heart. Becker states that producing is focused on putting your ideas on paper and receiving Other individuals to simply accept your Tips.
Composing, just like all different kinds of communication, receives greater by practice. It’s not a necessity to put in writing improved It can can be found in a purely natural way as you work at it. It’s genuine! Blogs are don’t just a superb way to help your website’s composing, but In addition it offers an excellent possibility to boost all components of your crafting, from organization e-mail and texts for the novel you’ve normally desired to publish.
Find new buddies. Becker writes “Regardless of whether you happen to be applying e-mail, remarks, or simply social media marketing, you can be described as a surprise for you how fast people join online.”
That is correct! It really is true! The Minimalists web site would be the main reason for many of my most important connections in the final 10 years. These incorporate friendships with extended-expression particular and business enterprise relationships which ended up forged as a result of this website.
You’ll grow to be extra confident. Becker writes “Running a blog will help you explore larger assurance in your lifetime.” It is genuine.
Creating best travel blog hashtags for instagram
will help us greater comprehend our life along with the ramifications of our steps.
Hello to all, how is the whole thing, I think every one is getting more from this
site, and your views are nice in support of new
visitors.
Study to become an enhanced author. Writing is conversation at its heart. Becker states that composing is focused on Placing your ideas on paper and having Other individuals to simply accept your Suggestions.
Creating, as with all other kinds of interaction, gets greater by way of follow. It’s actually not a necessity to put in writing greater It’ll can be found in a all-natural way as you work at it. It can be true! Weblogs are not merely an outstanding technique to help your weblog’s composing, but Furthermore, it delivers a superb probability to improve all facets of your crafting, from business e-mails and texts to the novel you’ve got generally needed to generate.
Come across new good friends. Becker writes “Whether you’re making use of e-mail, remarks, or maybe social media marketing, you may be a shock to you how briskly folks connect online.”
Which is accurate! It really is legitimate! The Minimalists site would be the main reason For numerous of my most significant connections in the final ten years. These incorporate friendships with long-phrase personalized and business enterprise relationships which had been cast through this website.
You will become much more self-confident. Becker writes “Blogging can help you find out better self-assurance in your daily life.” It can be actual.
Creating instagram fit diet blog
will help us improved understand our lives and also the ramifications of our steps.
Understand to become an improved author. Crafting is interaction at its coronary heart. Becker states that creating is centered on putting your feelings on paper and obtaining Other individuals to accept your ideas.
Composing, just like all different kinds of conversation, gets superior as a result of apply. It is not a necessity to put in writing far better It will are available in a organic way as you’re employed at it. It is really correct! Weblogs are not merely an excellent method to boost your weblog’s writing, but In addition it delivers an outstanding probability to improve all areas of your creating, from company e-mail and texts on the novel you have constantly wanted to publish.
Find new close friends. Becker writes “Whether you might be utilizing e mail, responses, or simply social websites, you could become a surprise to you how briskly persons link on the web.”
That’s genuine! It truly is genuine! The Minimalists web site would be the main reason For numerous of my most crucial connections in the final 10 years. These consist of friendships with very long-expression private and company associations which were being cast through this blog.
You may develop into extra confident. Becker writes “Running a blog can help you uncover better self-confidence in your daily life.” It’s real.
Crafting instagram girls doodling and editing pics blog
will help us far better comprehend our life along with the ramifications of our steps.
Its like you read my mind! You appear to know a lot about this, like
you wrote the book in it or something. I think that you could do with
some pics to drive the message home a bit, but instead of
that, this is fantastic blog. A fantastic read. I’ll definitely be back.
Learn to be an improved writer. Creating is interaction at its heart. Becker states that crafting is focused on Placing your thoughts on paper and receiving Others to accept your ideas.
Writing, as with all other forms of interaction, gets improved through follow. It’s actually not a prerequisite to jot down greater It can are available a purely natural way as you’re employed at it. It is really true! Weblogs are not just a fantastic strategy to improve your blog’s composing, but it also provides an outstanding possibility to boost all aspects of your crafting, from business e-mails and texts on the novel you have constantly wished to write.
Find new pals. Becker writes “Regardless of whether you happen to be using e mail, remarks, or even social networking, you could potentially be considered a surprise to you how briskly individuals hook up on the internet.”
That’s true! It is correct! The Minimalists blog could be the primary reason For numerous of my primary connections in the last decade. These include friendships with long-time period own and business relationships which ended up cast by means of this blog.
You may become far more assured. Becker writes “Running a blog can help you find larger self-assurance in your lifetime.” It is actual.
Creating instagram blog names ideas
allows us much better comprehend our life plus the ramifications of our actions.
I absolutely love your blog and find almost all of your post’s to be what precisely I’m looking for.
Do you offer guest writers to write content in your case?
I wouldn’t mind creating a post or elaborating on most of the subjects you write
related to here. Again, awesome web site!
At this time I am going away to do my breakfast, afterward having my breakfast coming yet again to read additional news.
Learn to become an improved writer. Composing is conversation at its coronary heart. Becker states that composing is all about putting your views on paper and getting Other individuals to just accept your ideas.
Producing, as with all other forms of communication, receives improved by means of apply. It isn’t a need to write better It will eventually can be found in a normal way as you work at it. It’s accurate! Blogs are not simply a great technique to increase your site’s writing, but Furthermore, it delivers an outstanding possibility to reinforce all aspects of your writing, from enterprise email messages and texts for the novel you’ve got often needed to generate.
Come across new friends. Becker writes “No matter if you happen to be employing electronic mail, comments, as well as social media marketing, you can be a surprise to you how briskly folks join on the net.”
That is true! It truly is real! The Minimalists website could be the main reason For most of my most crucial connections in the last ten years. These incorporate friendships with extensive-phrase particular and enterprise associations which ended up cast by means of this weblog.
You may come to be much more assured. Becker writes “Blogging can assist you uncover greater assurance in your daily life.” It is really authentic.
Crafting blog boca rosa instagram
assists us better understand our lives and also the ramifications of our steps.
I?m amazed, I have to admit. Rarely do I come across a blog that?s both equally educative and interesting, and
without a doubt, you have hit the nail on the head.
The problem is something which too few people are speaking intelligently about.
I’m very happy I found this during my search
for something concerning this.
Also visit my blog post :: Bio Magnify
Discover to be an enhanced writer. Crafting is interaction at its heart. Becker states that crafting is focused on Placing your feelings on paper and having Other individuals to accept your Strategies.
Crafting, just like all other kinds of communication, will get far better through practice. It’s actually not a need to write down greater It is going to can be found in a organic way as you work at it. It can be correct! Weblogs are don’t just an excellent strategy to enhance your blog’s crafting, but Furthermore, it provides an excellent probability to boost all areas of your writing, from enterprise email messages and texts to the novel you have generally wished to generate.
Obtain new close friends. Becker writes “No matter if you are making use of email, comments, or maybe social media marketing, you may become a surprise for you how briskly persons link on the net.”
That is legitimate! It is correct! The Minimalists web site would be the main reason For a lot of of my most crucial connections in the last ten years. These include friendships with very long-time period private and business relationships which have been cast as a result of this blog site.
You may turn into extra self-confident. Becker writes “Blogging will let you uncover better confidence in your life.” It is real.
Creating should i use instagram for blog
will help us far better comprehend our life and the ramifications of our actions.
I am pleased that I noticed this web blog, just the right information that
I was looking for!
Feel free to visit my web-site – Bio Magnify Pills
Hi thеre to eᴠery body, it’s my first pay a quick visit
of this weblog; this blοg contains amazing andd аctually
exdсellent stuff in support of readers.
Cheϲk out my websitе … Мультики смотреть онлайн
I was reading an atricle and found a distinct blockchain ecosystem dependant on Peer-to-Peer technological know-how is referred to as Utopia P2P. It’s a Net 3.0 engineering which is now in use. Moreover, the ecosystem is surrounded by a solid Neighborhood of accepting customers that aid the venture and distribute consciousness of it to a sizable audience.
Article about hs crp sonara quest cash price says that Utopia can be an ongoing venture that provides Risk-free conversation among individuals all over the planet. The ecosystem is predicated on flexibility, not enough censorship and checking, stability, confidentiality, and anonymity.
Customers get obtain to numerous developed-in tools following registering anonymously, which will take the location of the typical online assistants. You will discover uMessenger, An immediate messenger support, in conjunction with uMail, an nameless browser, Idyll Browser, and uWallet, a cryptocurrency wallet. Every one of these resources are available following registering totally free; You merely really need to download and put in the ecosystem.
What’s up to all, since I am genuinely eager of reading this
website’s post to be updated daily. It consists of
good data.
With havin so much content do you ever run into any issues of plagorism
or copyright violation? My blog has a lot of unique content I’ve either created myself or outsourced but it seems a lot of it is popping it up all
over the internet without my authorization. Do you know any methods to
help stop content from being stolen? I’d genuinely appreciate it.
I was reading an atricle and found a definite blockchain ecosystem dependant on Peer-to-Peer technological innovation is known as Utopia P2P. It’s a World wide web three.0 technology that may be now in use. Additionally, the ecosystem is surrounded by a strong Neighborhood of accepting consumers that assistance the venture and unfold consciousness of it to a significant viewers.
Article about crp price bitcoin says that Utopia is surely an ongoing job which offers Secure conversation amongst individuals all around the entire world. The ecosystem is predicated on adaptability, not enough censorship and monitoring, stability, confidentiality, and anonymity.
Buyers get access to numerous built-in equipment just after registering anonymously, which takes the position of the typical on the internet assistants. You can find uMessenger, an instant messenger provider, in addition to uMail, an anonymous browser, Idyll Browser, and uWallet, a cryptocurrency wallet. These applications are available just after registering totally free; you only have to obtain and put in the ecosystem.
With 2022’s crypto bear industry or 2016 oklahoma avg price per acre crp land, savvy buyers can buy large-price crypto belongings in a deal. With many of the situations that transpire around the globe, war, and inflation, it’s challenging to anticipate if the bear industry will conclude or when it will touch its lowest value.
The comeback time period is usually sluggish and unpredicted, and it may be influenced by economic growth, Trader psychology, and planet events. However, as is typical awareness, sure projects will proceed to do well over and above the awful industry and depart their mark on all the cryptocurrency sector, while some will are unsuccessful quickly.
And This can be the circumstance for Utopia, which will be the primary issue for currently. Utopia is usually a decentralized peer-to-peer (P2P) ecosystem that, inside of a earth in which the online world is driven by censorship, seeks to realize liberty of speech, consumer stability, and anonymity. The network has successively been the house of its indigenous asset, Crypton CRP.
Foor instance, in a 30-year payout schedule,
rather of $ten million all in one year, you’d get around $333,000 a
year.
Feel free to surf to my page – Go to the website
Even now, the Crypton forex has favourable prospective buyers in the event the crypto industry is in decrease. Gurus on fundamentals and tech Evaluation feel that CRP provides a strong chance to develop even larger this yr. In the subsequent years, the asset can obtain An even bigger worth In case the dev group manages to sustain the continuous task development.
Despite the fact that, as of June 2022, the CRP value is all-around half a greenback, by the top of the 12 months, it may well attain as much as 84 cents. The minimal value named by the market observers is over sixty five cents for each coin which is still A lot more than The present price.
So, labs. esr. crp price continues to be a youthful undertaking. Time will bring better adoption and new vital partnerships. These variables will secure a related spot for CRP while in the crypto marketplace. By the top of 2023, the predicted costs will probably be amongst ninety three cents and $one.twenty five.
2024 will see the following Bitcoin reward halving. Ordinarily, halving brings your complete crypto industry up. That 12 months, Crypton can benefit from it and mature even bigger. Some authorities see that by the top of 2024, CRP cannot be reduced than $one.5. Our optimistic forecast is CRP can arrive at around $one.94 by the tip with the yr.
Study to become an enhanced writer. Creating is conversation at its heart. Becker states that composing is focused on putting your thoughts on paper and getting Other individuals to just accept your Strategies.
Composing, as with all other kinds of conversation, will get superior through exercise. It isn’t a requirement to write down superior It is going to come in a pure way as you work at it. It really is genuine! Blogs are not simply a great method to increase your blog’s writing, but What’s more, it delivers a fantastic prospect to improve all aspects of your crafting, from enterprise e-mails and texts to the novel you’ve got usually needed to create.
Find new pals. Becker writes “Regardless of whether you’re using e-mail, opinions, or simply social networking, you might be a surprise to you personally how briskly individuals join over the internet.”
Which is genuine! It is real! The Minimalists blog is definitely the main reason For a lot of of my most crucial connections in the last 10 years. These include things like friendships with extended-time period own and organization interactions which were being solid through this website.
You can expect to turn into extra self-confident. Becker writes “Running a blog will let you learn higher self esteem in your daily life.” It truly is actual.
Crafting how to share wordpress blog photo on instagram
can help us better understand our lives and the ramifications of our actions.
hey there and thank you for your information – I have definitely picked up anything
new from right here. I did however expertise several technical points using this site, as I experienced to reload the website many times previous to I could get it to load correctly.
I had been wondering if your web host is OK? Not that I
am complaining, but sluggish loading instances times will
sometimes affect your placement in google and can damage your high quality score if ads and marketing with Adwords.
Anyway I’m adding this RSS to my e-mail and can look out for much more of your respective
fascinating content. Ensure that you update this again very soon.
Greetings! I’ve been reading your site for some time now and
finally got the bravery to go ahead and give you a shout out from Houston Texas!
Just wanted to tell you keep up the fantastic work!
http://gro-za.pp.ua/
Find out to be an enhanced author. Creating is interaction at its heart. Becker states that producing is centered on Placing your feelings on paper and receiving other people to accept your Tips.
Producing, as with all other kinds of interaction, receives better by means of exercise. It isn’t a need to put in writing much better It is going to are available a organic way as you work at it. It really is genuine! Blogs are not only a wonderful technique to boost your weblog’s producing, but In addition it delivers a great opportunity to enhance all areas of your creating, from small business email messages and texts towards the novel you’ve always planned to compose.
Locate new close friends. Becker writes “Whether or not you might be utilizing electronic mail, reviews, or perhaps social networking, you might be considered a shock to you personally how fast people join on the web.”
Which is genuine! It can be accurate! The Minimalists website could be the main reason For most of my primary connections in the final decade. These include things like friendships with lengthy-term personal and organization interactions which were being cast as a result of this blog.
You’ll come to be extra self-assured. Becker writes “Blogging may help you find out bigger confidence in your daily life.” It’s actual.
Writing lady gaga blog instagram
allows us improved comprehend our life along with the ramifications of our steps.
В App Store, куда беттор попадает через сайт
одноиз напрямую.
Feel free to surf to my site: лига ставок скачать
бесплатно – https://ligastavok-liga.ru/skachat-liga-stavok
–
what is prednisone price of deltasone can i take aspirin with prednisone how long does it take prednisone to get out of your system
Discover to become an enhanced writer. Creating is interaction at its coronary heart. Becker states that writing is centered on putting your views on paper and receiving Other individuals to just accept your Thoughts.
Composing, just like all other forms of conversation, receives improved via practice. It’s actually not a requirement to write much better It can can be found in a normal way as you work at it. It’s genuine! Weblogs are not only a fantastic way to boost your blog site’s producing, but Additionally, it delivers a superb possibility to improve all facets of your creating, from company e-mail and texts on the novel you’ve got constantly needed to compose.
Find new pals. Becker writes “No matter whether you’re employing e-mail, responses, or simply social websites, you can become a shock to you how briskly folks link on the net.”
That’s correct! It is genuine! The Minimalists weblog would be the main reason For most of my most important connections in the final decade. These include things like friendships with very long-term particular and company relationships which have been solid by means of this weblog.
You may come to be a lot more assured. Becker writes “Blogging can help you explore better confidence in your daily life.” It really is true.
Producing pull blog photos into instagram
helps us better understand our lives as well as the ramifications of our actions.
If you like progressive games and your chance to hit the jackpot, you can see progressive titles like Spirit of the Inca and Megasaur.
Feel free to visit my site … new fair go
Everything is very open with a clear explanation of the issues.
It was definitely informative. Your site is extremely helpful.
Many thanks for sharing!
Discover to be an improved author. Writing is interaction at its heart. Becker states that creating is about putting your feelings on paper and acquiring Other individuals to simply accept your Thoughts.
Producing, as with all other kinds of communication, receives far better by practice. It is not a prerequisite to put in writing superior It will come in a pure way as you work at it. It is really true! Weblogs are not merely a wonderful solution to improve your blog’s crafting, but Furthermore, it gives an outstanding prospect to reinforce all aspects of your writing, from company email messages and texts towards the novel you’ve got generally needed to compose.
Find new good friends. Becker writes “No matter if you might be making use of e-mail, reviews, or even social media, you could possibly be described as a shock to you how fast men and women join over the internet.”
That is legitimate! It can be genuine! The Minimalists blog site is definitely the main reason For numerous of my primary connections in the final ten years. These contain friendships with very long-expression personal and business enterprise relationships which ended up cast by this blog site.
You may turn into a lot more self-confident. Becker writes “Blogging can assist you explore bigger self esteem in your daily life.” It is genuine.
Creating do you need a blog to do food recipes on instagram
aids us better comprehend our life and also the ramifications of our steps.
Find out to be an improved writer. Producing is conversation at its coronary heart. Becker states that crafting is about putting your ideas on paper and receiving Others to accept your Concepts.
Writing, just like all other kinds of conversation, gets greater via follow. It is not a necessity to write superior It is going to come in a pure way as you work at it. It truly is real! Weblogs are not merely an outstanding strategy to transform your website’s crafting, but In addition it supplies an excellent possibility to reinforce all facets of your producing, from enterprise email messages and texts to the novel you have generally wanted to write.
Obtain new close friends. Becker writes “Whether you happen to be working with email, responses, or maybe social media marketing, you could certainly be a shock for you how briskly individuals connect on the web.”
Which is accurate! It truly is true! The Minimalists weblog would be the main reason For most of my most important connections in the final decade. These incorporate friendships with long-expression private and company associations which were forged by this blog site.
You can turn out to be more confident. Becker writes “Blogging may help you find out higher self-confidence in your lifetime.” It truly is real.
Creating how to start a lifestyle instagram blog
assists us greater understand our life as well as the ramifications of our actions.
Having read this I thought it was very informative.
I appreciate you finding the time and energy to put this article together.
I once again find myself spending a lot of time both reading and posting comments.
But so what, it was still worthwhile!
I don’t even know the way I finished up right here, however I believed this submit
used to be great. I don’t recognise who you are but definitely you’re going to a famous blogger
if you happen to aren’t already. Cheers!
I simply wanted to post a simple comment to be able to say thanks
to you for those magnificent solutions you are placing
on this site. My time consuming internet lookup has at the
end been recognized with awesome strategies to share with my
company. I would repeat that many of us readers actually are really blessed to be in a decent community with many perfect individuals with very helpful tricks.
I feel truly grateful to have used your webpages and look forward to tons of more exciting moments reading here.
Thanks again for everything.
Here is my site :: Arctos Cooler Review
Master to become an enhanced author. Writing is interaction at its heart. Becker states that creating is focused on Placing your feelings on paper and receiving other people to simply accept your Strategies.
Producing, just like all other kinds of conversation, gets much better by means of observe. It isn’t really a need to jot down much better It will can be found in a natural way as you’re employed at it. It really is true! Weblogs are not simply an outstanding method to transform your website’s crafting, but Furthermore, it presents an outstanding chance to boost all facets of your composing, from business enterprise e-mail and texts for the novel you have normally wanted to write.
Uncover new close friends. Becker writes “No matter if you might be using email, opinions, as well as social media, you can become a shock to you personally how briskly folks join on-line.”
Which is genuine! It truly is real! The Minimalists blog site is the primary reason For numerous of my most important connections in the final 10 years. These include friendships with very long-expression personal and business associations which have been forged by this site.
You may turn out to be more confident. Becker writes “Blogging can help you discover greater self confidence in your life.” It’s actual.
Producing why is instagram important for your blog 2017
allows us better understand our lives as well as ramifications of our steps.
I loved as much as you’ll receive carried out right here.
The sketch is attractive, your authored subject matter stylish.
nonetheless, you command get bought an edginess over that you wish be delivering the following.
unwell unquestionably come more formerly again as exactly the same nearly very often inside case you shield this
increase.
I additionally benefit from the four exclusive own-brand Royal Panda
reside desk video games.
my blog: indian rupees (royal-panda-casino.com)
Learn to become an improved writer. Writing is conversation at its heart. Becker states that composing is about Placing your ideas on paper and having Other individuals to simply accept your Concepts.
Writing, just like all other forms of interaction, will get much better through exercise. It’s not a need to write down better It can are available in a all-natural way as you’re employed at it. It is really accurate! Weblogs are not simply a fantastic technique to help your blog’s writing, but Additionally, it provides a fantastic chance to boost all facets of your producing, from company e-mails and texts towards the novel you’ve got normally wished to publish.
Come across new mates. Becker writes “Whether you happen to be working with email, remarks, or maybe social media marketing, you may be considered a shock to you how fast men and women hook up on the net.”
Which is correct! It is correct! The Minimalists site will be the primary reason For several of my most important connections in the final decade. These consist of friendships with extended-phrase private and business relationships which were being cast by way of this site.
You are going to develop into far more confident. Becker writes “Running a blog will help you learn greater self-assurance in your lifetime.” It’s genuine.
Creating jenna sue blog instagram
will help us improved understand our lives as well as the ramifications of our actions.
excellent post, very informative. I ponder why the other specialists of this
sector do not realize this. You should continue your writing.
I’m confident, you’ve a great readers’ base already!
Wonderful goods from you, man. I have understand your stuff previous to
and you are just extremely excellent. I really like what you’ve acquired here, really like what
you are stating and the way in which you say it. You make it enjoyable and you still take care
of to keep it wise. I cant wait to read much more from you.
This is actually a great website.
Hi there to every one, it’s in fact a fastidious for me to go to see this
site, it contains precious Information.
Learn to become an improved author. Crafting is communication at its coronary heart. Becker states that composing is all about Placing your thoughts on paper and receiving Others to just accept your ideas.
Creating, as with all other kinds of conversation, gets better as a result of follow. It’s not a requirement to write much better It’ll are available a organic way as you’re employed at it. It is real! Weblogs are not simply an outstanding approach to help your web site’s crafting, but Additionally, it presents a superb prospect to boost all facets of your crafting, from business enterprise e-mail and texts into the novel you’ve usually planned to generate.
Come across new good friends. Becker writes “Irrespective of whether you happen to be using e mail, remarks, or even social media, you can be described as a surprise to you how briskly individuals join on-line.”
Which is legitimate! It is real! The Minimalists blog site is the primary reason For lots of of my most crucial connections in the final 10 years. These consist of friendships with extended-term personal and small business interactions which were being cast through this website.
You will come to be much more assured. Becker writes “Blogging can assist you uncover bigger self confidence in your daily life.” It can be genuine.
Producing instagram blog starten
helps us much better understand our lives along with the ramifications of our steps.
This is very interesting, You’re a very skilled blogger.
I have joined your rss feed and look forward to seeking more of your magnificent post.
Also, I have shared your site in my social networks!
Master to be an enhanced writer. Crafting is communication at its coronary heart. Becker states that composing is all about putting your thoughts on paper and having other people to just accept your Strategies.
Crafting, just like all other forms of interaction, gets far better via follow. It isn’t really a requirement to put in writing far better It’s going to are available in a all-natural way as you work at it. It can be genuine! Blogs are not simply an outstanding strategy to help your web site’s creating, but What’s more, it delivers a great likelihood to improve all components of your composing, from organization e-mails and texts into the novel you’ve constantly wished to generate.
Uncover new buddies. Becker writes “Irrespective of whether you happen to be applying e mail, responses, or perhaps social networking, you may be described as a shock to you how briskly people today link on the web.”
That’s legitimate! It’s true! The Minimalists site could be the main reason for many of my most vital connections in the last 10 years. These contain friendships with extended-expression personalized and small business associations which had been cast by means of this blog site.
You may turn out to be a lot more assured. Becker writes “Running a blog may help you learn better assurance in your daily life.” It is really true.
Crafting what does instagram personal blog mean
aids us superior understand our lives and the ramifications of our steps.
Unquestionably believe that which you stated.
Your favorite justification seemed to be on the net the easiest thing to be aware of.
I say to you, I certainly get annoyed while people think about worries that they just do not know about.
You managed to hit the nail upon the top as well as defined out the whole
thing without having side effect , people can take a signal.
Will likely be back to get more. Thanks
Oh my goodness! Amazing article dude! Thanks,
However I am going through troubles with your RSS.
I don’t understand why I cannot subscribe to it. Is there anybody getting identical RSS problems?
Anyone who knows the answer will you kindly respond? Thanks!!
Why people still use to read news papers when in this technological globe the whole thing is presented
on net?
I am regular visitor, how are you everybody?
This article posted at this web page is actually good.
You really make it seem so easy with your presentation but I find this topic to be really something which I think I would never understand.
It seems too complex and extremely broad for me.
I am looking forward for your next post, I’ll try to get the hang
of it!
I don’t even know how I ended up here, but I thought
this post was great. I do not know who you are but certainly you are going to a famous blogger if you aren’t already 😉 Cheers!
Hello it’s me, I am also visiting this web page
regularly, this site is really good and the viewers are genuinely sharing pleasant
thoughts.
I know this website gives quality depending posts and
extra stuff, is there any other web site which gives these kinds of stuff in quality?
Keep this going please, great job!
Wow, awesome blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your web site is wonderful, as well
as the content!
Hello.This post was really remarkable, especially
since I was investigating for thoughts on this subject last week.
Greetings! Very helpful advice within this post! It’s the little
changes that make the greatest changes. Thanks a lot for sharing!
Hello, I check your blogs daily. Your humoristic style is awesome,
keep it up!
This page truly has all of the information and facts I wanted
about this subject and didn’t know who to ask.
What’s Happening i’m new to this, I stumbled upon this I have discovered
It absolutely helpful and it has aided me out loads.
I’m hoping to contribute & assist other customers like its aided me.
Good job.
Pretty nice post. I just stumbled upon your weblog and wanted to say that I have truly
enjoyed browsing your blog posts. In any case I will be subscribing to your rss feed and I hope you write again soon!
Very shortly this web page will be famous among all blogging users, due to it’s pleasant
articles
Blumen sind natürlich immer schön und bringen Farbe, Duft und Freude ins Haus – vorausgesetzt man hat
einen Strauß ausgewählt, der ihr auch gefällt. Wahrscheinlich rechnet sie aber auch schon ein wenig damit.
Wie wäre es einmal mit etwas Kreativem? Wir alle sind momentan durch die
Pandemie und ihre Folgen doch alle viel mehr zu Hause als sonst und bei vielen wächst
die Langeweile und die Sehnsucht nach einer anregenden Tätigkeit, die
einige Stunden sinnvoll füllen kann.
Die Kinder wollen auch etwas beitragen, wissen aber nicht was?
Die Mama sagt dazu leichthin: “Malt mir einfach etwas Schönes.” Die Begeisterung der Kinder
hält sich danach allerdings oft noch in Grenzen, denn sie wissen es schon: gleichgültig, wie sehr sie sich
doch bemühen, man sieht es ihren Kinderzeichnungen doch immer an, dass hier etwas seltsam aussieht,
dort Details fehlen oder die Größenverhältnisse
nicht ganz stimmig sind. Außerdem wissen sie auch nicht, was
sie für Mama malen sollen. Herzen? Ja, die passen doch zu diesem besonderen Feiertag.
Und sonst noch etwas? Aber was? Das Lieblingspferd, Blumen, Roboter…
Die Aufgabe erscheint vielen einfach zu groß und das Bild
wird immer wieder verschoben und dann ist Muttertag und man steht da mit leeren Händen.
Damit Mama nicht leer ausgeht gibt es eine Lösung. Mit
einem wunderschönen Set von “Malen nach Zahlen”
lässt sich innerhalb kurzer Zeit ein Kunstwerk für die Frau herstellen,
die das ganze Jahr über an alle anderen um sie herum
denkt, die Familie zusammenhält, putzt, bügelt, kocht, das Distanzlernen und die Kinderbetreuung übernimmt, Geld verdient
und die sich selbst dabei oft zurückstellt.
Das Gute daran ist, niemand muss ein Künstler im freihändigen Zeichnen sein, um mit “Malen nach Zahlen”
ein tolles Ergebnis zu erzielen. Alle Farben, die Leinwand und eine gut verständliche Anleitung sind bereits im Set enthalten. Es kann also gleich losgehen mit dem Malen und es ist geradezu eine optimale Familienbeschäftigung
für Kinder und Erwachsene. Wenn Mama sich also Blumen und ein gemaltes
Bild wünscht, kann man diese Wünsche mit einem
Malset wunderbar miteinander kombinieren. Einfach ein hübsches, florales Motiv (oder ein anderes
Lieblingsmotiv) aussuchen, alle Kinder und eventuell noch den Vater an einem Tisch versammeln und loslegen. Man sollte nur darauf achten, dass Mama die Überraschung nicht vorher bemerkt.
Vielleicht hat sie ja Lust auf ausgedehnte Sporteinheiten in einem anderen Raum oder auf
längere Spaziergänge oder Radtouren? Dann haben die Heinzelmännchen zu Hause freie Bahn zum Malen. Alternativ kann man sich natürlich auch dazu in eines der Kinderzimmer zurückziehen und ein Schild
mit dem Text “Bitte nicht stören” an die Tür hängen oder
abschließen.
Wenn es bis Muttertag mit der Familienaktivität zeitlich nicht mehr funktioniert, dann
kann man das Malset einfach Mama schenken und ihr die Wahl lassen, ob sie das Bild selber malen möchte und damit auch
automatisch einmal Zeit für sich genießt oder ob das Bild als
Möglichkeit zur Familienbeschäftigung nutzen möchte.
So können gleich mehrere Familienmitglieder für ein gemeinsames, kreatives Projekt zusammenkommen. Die Auswahl an Motiven auf dem Markt ist
groß – es gibt atemberaubende Landschaften, interessante Metropolen, putzige Tiere oder abstrakte Farbkompositionen – je nach den individuellen Vorlieben. Anschließend wir
auch niemand unpassende Bemerkungen über das Gemälde abgeben, weil es einfach wunderschön ausdrucksstark und präzise wirkt.
Gerade für Kinder im Grundschulalter bietet
sich “Malen nach Zahlen” an, um die Feinmotorik spielerisch zu schulen und dadurch wichtige Voraussetzungen für
das Schreiben zu legen. Ganz nebenbei wird dadurch das Zahlenverständnis geschult und die kindliche Konzentrationsfähigkeit
erweitert. Am Ende des Malens steht dann das fertige, gelungene Produkt
und dies ganz frustfrei für alle Beteiligten. Das Lob von allen Betrachtern wird die kleinen und großen Künstlern zusätzlich beflügeln.
Gerade in der Coronazeit ist es für die ganze Familie wichtig, darauf zu achten, dass die Bildschirmzeit
nicht überhand nimmt. Die Kinder halten über ihre Smartphones, Tablets
und PCs Kontakt zu ihren Klassenkameraden und Freunden und nehmen damit am Distanzunterricht teil.
Dazu kommen für die meisten Kinder unzählige Stunden, die mit fernsehen oder Computerspielen gefüllt werden.
Wenn dann phasenweise Sportangebote durch Vereine und Musikschulen wegfallen, sehnen sich die
Kinder und Erwachsenen nach unmittelbar erfahrbaren, “realen” Aktivitäten. Nach Dingen, die man selber
machen kann und auf die man am Ende zu Recht stolz sein darf.
Für einige ist dies möglicherweise das 1000-Teile-Puzzle, das man geschafft hat.
Für andere ein leckerer, selbst gebackener Kuchen und für kleine und große Nachwuchskünstler ist dies bestimmt auch ein wunderschönes Malset mit Geling-Garantie.
Wenn dann das erste Set ein voller Erfolg war und Spaß gemacht
hat, gibt es noch viele weitere Möglichkeiten um das neue
Hobby fortzuführen. Das Malen hilft uns einfach im Alltag dabei, selbst in schwierigen Zeiten nach vorne zu schauen, etwas
zu gestalten und den Glauben daran nicht zu verlieren, dass eine Pandemie zu
etwas Positivem führen kann.
What i do not realize is actually how you are no longer actually a lot more smartly-liked
than you may be right now. You are very intelligent.
You know thus considerably in relation to this subject, produced me in my view believe it from numerous varied angles.
Its like men and women are not involved unless it is something to accomplish with Girl gaga!
Your own stuffs nice. All the time deal with it up!
If some one desires to be updated with newest technologies therefore he must be visit this website and be up to date
every day.
Mit 5 Card Poker ist in der Regel Five Card Draw gemeint: Das Poker des Wilden Westens.
Händen) zählen. Dass Sie mit Ihrem Flush auf einen Flush des Gegners treffen, kommt bei Omaha
sehr viel häufiger vor. Der Mini-Royal ist das Äquivalent zum Royal Flush.
Wenn Sie keine Made Hand, sondern lediglich einen Draw, wie
z. B. einen Flush Draw, haben und bluffen, so wird dies
Semi Bluff genannt. Wenn Sie die gleiche Hand wie Ihr Gegner haben, aber in verschiedenen Farben,
dann teilen Sie einfach den Pot. Spieler die Hi Hand gewinnt.
Spieler selbst sperren lassen als auch von Angehörigen beantragt
werden. Der Schwierigkeitsgrad ist hoch – selbst für gestandene Profis.
Müssen bloß zwei Hole Cards verwenden. Haben zwei Spieler ein Paar, gewinnt derjenige mit dem
höheren Paar. Jeder Spieler bekommt – im Verlaufe mehrerer Setzrunden – bis zu sieben Karten ausgeteilt.
Es gibt ebenfalls fünf Gemeinschaftskarten, die Anzahl der Setzrunden ist gleich.
Allerdings bekommen Sie nun fünf Karten ausgeteilt.
Außerdem wird A-6-7-8-9 als Straße gewertet – das Ass zählt nun als Fünf.
Aus einem Poker war für Trudeau eine Zitterpartie geworden.
Die Auszahlungsgrenze für Gewinne aus diesem Bonus beträgt 200 EUR.
Zuerst einmal müssen Sie in der Regel einen Mindestbetrag einzahlen, wenn Sie einen Casino
Bonus in Anspruch nehmen wollen. Sie wollen diese Hand
also spielen. Solltest Du noch mehr Kreuzworträtsellexikonlösungen zum Eintrag Glücksspiel
kennen, teile uns diese Kreuzworträtsel-Antwort doch bitte mit.
Und die Kanadier folgten seinem Aufruf – auch wenn mehr als zwei Drittel diese
vorgezogene Abstimmung inmitten der Corona-Pandemie für
unsinnig hielten. Auch diese Rotlichtadresse gehört zu unserem Erotiknetzwerk.
Dennoch ist es für einen Spieler natürlich angenehmer, wenn entweder gar keine Wettsteuer gezahlt werden muss, oder diese nur beim Gewinn fällig wird.
Die Optik und das Layout sind wichtige Qualitätskriterien, die jedoch von jedem User
subjektiv bewertet werden. Ich gehe nun kurz auf die verschiedenen Spiele
ein, von den Slots über die Tischspiele, Lotto und Bingo
bis hin zum Live Casino, wo Sie von richtigen Croupiers bedient werden. Weitere Live Casino Spiele sind Dream Catcher, Crazy Time, Mega Ball und Football Studio.
Wir von Casinova sind ein Team bestehend aus Online Casino Tests Experten. Dieser „Einarmige
Bandit” bestand aus drei Walzen, die mittels eines Hebels zum Rollen gebracht wurden. Poker Hände werden bei dieser Variante nur mit diesen drei Hole Cards gebildet.
Simply wish to say your article is as surprising. The clarity in your
post is simply cool and i can assume you are an expert on this subject.
Well with your permission allow me to grab your feed to keep
up to date with forthcoming post. Thanks a million and please continue
the enjoyable work.
Wow, superb blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of
your site is excellent, as well as the content!
superbe article mais je me demandais si vous pouviez
écrire un peu plus sur ce thème ?Je vous serais très reconnaissant si vous pouviez élaborer un peu plus.
Merci beaucoup!
Voici mon web blog … https://Rencontrefemmemature.icu/le-seul-site-de-rencontre-sexe-ou-vous-chopez-vite-et-vraiment/
WAS IST ALLES BEI DEINER BESTELLUNG DABEI?
DEIN MALEN NACH ZAHLEN SET IM ÜBERBLICK:
Deine Bestellung inkludiert neben der Leinwand
mit deinem Wunschmotiv auch ein Pinsel- und Farbset.
Drei Nylon Pinsel mit unterschiedlichen Aufsätzen sowie qualitativ hochwertige Acrylfarben helfen dir, dein eigenes
Kunstwerk zu kreieren. Die Bestellung beinhaltet außerdem eine Anleitung mit den wichtigsten Schritten. Auf Wunsch kannst
du noch einen Premium Holzrahmen dazu bestellen und
somit deinem Bild den letzten Schliff verleihen.
Hochwertige Leinwand mit dem entsprechenden Motiv (Größe: 40x50cm)
Qualitativ hochwertiges Acrylfarben-Set mit hoher
Deckkraft
Premium Holzrahmen je nach Wahl verfügbar
3 Nylon Pinsel mit verschiedenen Aufsätzen sorgen für
ein einwandfreies Ergebnis
Die perfekte Deko für deine eigenen vier Wände.
Ob Anfänger oder Fortgeschrittener – für jeden ist das
Richtige dabei
Überzeuge Dich selbst von der Welt der Farben:
WARUM SOLLTEST DU DEIN PAINTING WÄHLEN?
In der folgender Tabelle möchten wir Dir unsere Qualitäten zeigen, für die wir stehen:
WARUM MALEN NACH ZAHLEN?
FÜR JUNG UND ALT: Wir haben für jedes Alter die richtigen Bilder.
Selbst den Profis unter euch wird sicher nicht fad.
Aber keine Sorge, auch auch für noch nicht geübte Kinderhände haben wir tolle Motive mit größere Felder zum Ausmalen.
MEHR ALS 1200 VERSCHIEDENE MOTIVE: Geschmäcker sind verschieden – das
ist allgemein bekannt. Deshalb haben wir mehr als 1200 verschiedene
Motive in unserem Sortiment. Von Tierbildern bis hin zu Autos, bei uns findet jeder etwas nach seinem Geschmack.
PERFEKTE GESCHENKIDEE: Hast Du Schwierigkeiten ein passendes Geschenk zu finden? Dann ist das
hier die ideale Lösung für dich. Das perfekte Geschenk für Weihnachten, Ostern, Geburtstage und vieles mehr!
Vor allem wenn du ein persönliches Bild verschenkst, wist du deinen Liebsten eine große Freude bereiten.
IDEALE DEKO: Nachdem dein Bild fertig ist, kannst du es aufhängen und so deinen eigenen vier Wänden einen ganz persönlichen Touch verleihen. Mit unseren Motiven kannst du
dein Zuhause einzigartig gestalten!
FÖRDERT DIE MOTORIK: Davon abgesehen, dass
das Malen jede Menge Spaß macht, wird auch noch gleichzeitig die Motorik gefördert.
HÄLT KOGNITIV FIT: Kreuzworträtseln war gestern! Malen nach Zahlen ist
eine super Alternative um kognitiv fit zu bleiben.
ERSTKLASSIGE GRUPPENAKTIVITÄT: Egal ob mit dem Partner,
mit Freunden oder mit der Familie – Malen nach
Zahlen macht auch gemeinsam riesigen Spaß! Teile diese Freude mit deinen Liebsten!
ENTSPANNUNG PUR: Lenke dich vom stressigen Alltag ab und lerne zu
entspannen. Studien belegen, dass Freizeitbeschäftigungen wie “Malen nach Zahlen”, Stress deutlich reduzieren kann.
DEIN PAINTING KUNDENBEWERTUNGEN:
Bilder sagen sprichwörtlich mehr als 1.000 Worte. Unsere 10.000+
Kundenbewertungen sprechen für sich. Schau dir unser Video an, in dem wir dir die Welt der Farben näher
bringen:
100 % GELD-ZURÜCK-GARANTIE
Wir sind davon überzeugt, dass wir mit “Dein Painting” die Welt der Künstler verändert
haben. Mit Fleiß und Kreativität haben wir eine Plattform mit über 1500+ Motiven erschaffen. Unsere oberste
Priorität sind zufriedene Kunden.
Für die sichere Bezahlung verwenden wir eine SSL-Verschlüsselung.
Glücksspiel kann süchtig machen: Wer einmal damit anfängt, kann nur schwer wieder aufhören.
Glücksspielgesetz Deutschland – ist Online Glücksspiel erlaubt?
Die Forschungsstelle Glücksspiel hat es sich zur Aufgabe gemacht, die verschiedenen Aspekte des Glücksspiels interdisziplinär und nach wissenschaftlichen Methoden zu beleuchten. Die Stärken des bekannten Online
Wettanbieters liegen vor allem im Wettangebot, den starken Fussball Wetten sowie dem Quotenniveau.
Bei allem zeitgeistigen Schmerz hinterlassen CASINO BLACKOUT dabei immer noch einen wichtigen Gedanken:
Bei jedem Kampf für eine bessere Welt dürfen wir nie vergessen, auch aufeinander Acht zu geben.
Statt pointiertem Deutschpunk experimentieren CASINO BLACKOUT mit Pop-Punk und versetzen dessen Grundzutaten immer wieder in abenteuerliche Songwriting-Kniffe, die Abwechslung und Aussagekraft stetig auf ein neues Level heben. CASINO BLACKOUT aus dem Süden Deutschlands
wissen, was es bedeutet, sich selbst zu finden. Die
bekannte Phrase „Ich will sehen” stammt aus dem Draw Poker und gibt an, dass ein Spieler sein Blatt für gut genug hält, um die Hand des
Gegners zu schlagen. Im sogenannten „Showdown”,
dem Ende des Spiels, werden alle Karten aufgedeckt und die beste Hand
gewinnt. Doch sie hoffen, am Ende viel mehr Geld zu gewinnen als sie eingesetzt haben.
Wszystkie sloty w całej all right casino free spins Right Casino udostępniane są za sprawą najlepszych dostawców komputerów hazardowych.
Learn to become an improved writer. Composing is conversation at its coronary heart. Becker states that producing is all about Placing your thoughts on paper and having Other individuals to accept your Tips.
Producing, as with all other kinds of conversation, receives improved through apply. It’s not a prerequisite to put in writing much better It is going to are available in a all-natural way as you’re employed at it. It’s accurate! Weblogs are not just an excellent technique to help your site’s writing, but Furthermore, it delivers a fantastic probability to reinforce all areas of your composing, from company e-mails and texts on the novel you’ve often desired to compose.
Find new buddies. Becker writes “Whether or not you are working with email, remarks, or perhaps social networking, you could be a surprise to you personally how fast individuals join online.”
That’s real! It’s real! The Minimalists blog site would be the primary reason for many of my most crucial connections in the final decade. These consist of friendships with very long-phrase private and business associations which ended up cast by means of this blog.
You can expect to turn out to be extra confident. Becker writes “Blogging will let you find out greater assurance in your lifetime.” It really is authentic.
Composing can i share a link to a blog post in instagram?
allows us better understand our lives as well as the ramifications of our steps.
It also has jobs in several categories like full-time work, entry-level, managerial level,
and even on a freelkance basis.
Feel free to surf tto my web site – 밤알바
It’s awesome in favor of me to have a web page, which is good designed for
my knowledge. thanks admin
nolvadex vs aromasin generic tamoxifen 20 mg can you take nolvadex with arimidex how to take nolvadex
Hey! I’m at work surfing around your blog from my
new iphone! Just wanted to say I love reading through your blog and look forward to
all your posts! Keep up the outstanding work!
If you would like to take a good deal from this paragraph then you have to apply such methods to your won weblog.
doxycycline cost doxycycline 20 mg india doxycycline hyclate 150 mg acne how long does doxycycline take to work
Asking questions are really pleasant thing if you are not understanding anything entirely, but
this article offers pleasant understanding yet.
wonderful points altogether, you simply gained a logo new reader.
What may you suggest about your submit that you just made some days in the past?
Any positive?
You made some really good points there. I checked on the internet for more info about the issue and found most
individuals will go along with your views on this website.
Pretty section of content. I just stumbled upon your web
site and in accession capital to assert that I get in fact enjoyed account
your blog posts. Any way I’ll be subscribing
to your augment and even I achievement you access consistently quickly.
Greetings! This is my first visit to your blog! We are a team
of volunteers and starting a new project in a community in the
same niche. Your blog provided us beneficial information to
work on. You have done a wonderful job!
It’s awesome to go to see this website and reading the views of
all mates about this post, while I am also keen of getting familiarity.
Hi there, all the time i used to check weblog posts here in the early hours in the daylight, as i love to learn more and more.
We have place with each other the ideal Instagram purposes for your instagram code for blog:
Enhancing images. These applications allow people to edit, resize and utilize filters.
Format layout and style and design. These applications permit people to incorporate innovative features like collages, graphics, along with other graphics to your site’s manufacturer’s web site.
Video applications. These apps can enhance the way your organization captures and results in films.
Analytics engagement, information, and data over the viewers. Down load Instagram apps to trace the way in which your viewers interacts along with the effectiveness of your material.
Desk of Contents for Instagram layout applicationsInstagram enhancing applicationInstagram movie enhancing applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-preserving tricks for Instagram effective buyers Find out the tricks Hootsuite employs to make prime-top quality material.
เป็นอย่างไรบ้าง เพื่อนร่วมงาน การยอมจำนนที่ยิ่งใหญ่ในเรื่องของประเพณีและระบุไว้อย่างเต็มที่ ยึดติดกับมันเสมอ ถ้าหากคุณสนใจเกี่ยวกับเรื่อง แทงบอลโลก หรือ แทงบอลโลก 2022 หรือ ราคาบอลโลก ฉันแนะนำให้คุณลองไปดูที่นี่ Education Guilan Ac
Feel free to surf to my homepage; https://wolf369.online
We have set alongside one another the very best Instagram programs for your shopify blog instagram marketing 101:
Enhancing pics. These apps allow for users to edit, resize and implement filters.
Format format and style and design. These applications enable customers to include revolutionary things like collages, graphics, and other graphics to your web site’s model’s web site.
Online video equipment. These programs can increase the way your organization captures and results in films.
Analytics engagement, knowledge, and knowledge about the audience. Download Instagram applications to track the best way your audience interacts as well as the overall performance within your content material.
Desk of Contents for Instagram structure applicationsInstagram modifying applicationInstagram video editing applicationInstagram analytics appsApps for engagement on Instagram
Bonus: 14 time-saving methods for Instagram impressive consumers Uncover the methods Hootsuite employs to create leading-good quality content.
Hi to all, because I am genuinely keen of reading this web site’s
post to be updated daily. It carries good material.
This is my first time pay a visit at here and i am really impressed to read everthing at single place.
We have place together the most beneficial Instagram programs for your save images from my blog for instagram:
Enhancing shots. These applications allow buyers to edit, resize and utilize filters.
Layout format and layout. These apps allow for end users to include ground breaking factors like collages, graphics, as well as other graphics to your web site’s brand’s webpage.
Video clip tools. These purposes can enhance the way in which your company captures and makes video clips.
Analytics engagement, facts, and facts within the audience. Download Instagram applications to trace how your audience interacts as well as general performance of your information.
Table of Contents for Instagram format applicationsInstagram editing applicationInstagram online video editing applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-preserving methods for Instagram strong people Find the tricks Hootsuite employs to make major-top quality material.
Hello there! Do you use Twitter? I’d like to follow you if
that would be okay. I’m undoubtedly enjoying your blog and look
forward to new posts.
We have set together the very best Instagram applications for your how to set up an instagram blog:
Editing pics. These apps allow customers to edit, resize and implement filters.
Structure layout and style. These apps allow for end users to include progressive things like collages, graphics, as well as other graphics to your web site’s manufacturer’s site.
Video resources. These applications can improve how your company captures and results in video clips.
Analytics engagement, information, and info on the viewers. Down load Instagram apps to track the best way your audience interacts along with the functionality of the information.
Desk of Contents for Instagram structure applicationsInstagram enhancing applicationInstagram video clip modifying applicationInstagram analytics appsApps for engagement on Instagram
Bonus: fourteen time-preserving tricks for Instagram highly effective customers Uncover the tricks Hootsuite employs to create major-excellent written content.
I’m really enjoying the theme/design of your site.
Do you ever run into any web browser compatibility issues?
A handful of my blog audience have complained about my
blog not working correctly in Explorer but looks great in Opera.
Do you have any suggestions to help fix this problem?
We have put collectively the very best Instagram apps for your instagram food blog bay area 40k followers:
Editing photos. These apps let consumers to edit, resize and utilize filters.
Format structure and layout. These apps allow for consumers to include modern factors like collages, graphics, and various graphics to your website’s model’s site.
Online video resources. These programs can enrich just how your business captures and makes videos.
Analytics engagement, knowledge, and details about the audience. Obtain Instagram apps to track how your viewers interacts and the functionality of the written content.
Table of Contents for Instagram structure applicationsInstagram enhancing applicationInstagram movie enhancing applicationInstagram analytics appsApps for engagement on Instagram
Bonus: 14 time-preserving methods for Instagram highly effective consumers Find out the methods Hootsuite employs to supply top-good quality articles.
An outstanding share! I’ve just forwarded this onto
a coworker who had been doing a little research on this.
And he in fact bought me lunch due to the fact that I discovered it for him…
lol. So allow me to reword this…. Thanks for the
meal!! But yeah, thanx for spending the time to discuss this topic here on your web page.
all the time i used to read smaller articles which also clear their motive, and that is also happening with this paragraph which I am
reading at this place.
Hello! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly? My website looks
weird when browsing from my iphone4. I’m trying to find a template or plugin that
might be able to correct this issue. If you have any recommendations, please share.
Cheers!
Hi there would you mind sharing which blog platform you’re using?
I’m looking to start my own blog in the near
future but I’m having a hard time selecting between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your design seems different then most blogs and I’m looking for something completely unique.
P.S Apologies for getting off-topic but I had
to ask!
Hello, i believe that i noticed you visited my blog so i got here to return the want?.I am
trying to to find issues to improve my web site!I assume its ok to make use of a few of your concepts!!
We’ve place jointly the most effective Instagram applications for your instagram new hastgae in bio blog post:
Enhancing photographs. These applications allow customers to edit, resize and implement filters.
Structure structure and layout. These applications permit people to include revolutionary components like collages, graphics, as well as other graphics to your site’s manufacturer’s website page.
Online video resources. These applications can boost the way your company captures and results in videos.
Analytics engagement, details, and info around the viewers. Obtain Instagram applications to track the best way your audience interacts along with the overall performance of your information.
Table of Contents for Instagram format applicationsInstagram modifying applicationInstagram movie modifying applicationInstagram analytics appsApps for engagement on Instagram
Bonus: fourteen time-preserving tricks for Instagram potent consumers Learn the tricks Hootsuite employs to generate top rated-good quality written content.
I think probably the most complains about ggbet are
probably wrong sites or people who don’t understand the rules.
Can I simply just say what a comfort to discover somebody who genuinely knows what
they are talking about over the internet. You certainly realize how to bring a problem
to light and make it important. More and more
people really need to read this and understand this side of your story.
It’s surprising you aren’t more popular since you definitely have the gift.
Hey! I know this is somewhat off topic but I was wondering which blog platform
are you using for this website? I’m getting sick and tired of WordPress because I’ve had problems with hackers
and I’m looking at alternatives for another platform.
I would be fantastic if you could point me in the direction of a good platform.
Freight charges will certainly be additional in this organization, but you will certainly be profited more below.
A Lean Plan will certainly serve you.
We’ve place collectively the best Instagram programs for your instagram le blog de betty:
Modifying pictures. These applications make it possible for end users to edit, resize and use filters.
Structure format and structure. These applications allow end users to incorporate progressive things like collages, graphics, as well as other graphics to your web site’s brand name’s website page.
Video clip equipment. These apps can enhance the way your business captures and creates video clips.
Analytics engagement, info, and data around the audience. Obtain Instagram apps to track how your audience interacts as well as the effectiveness of your articles.
Desk of Contents for Instagram format applicationsInstagram enhancing applicationInstagram movie editing applicationInstagram analytics appsApps for engagement on Instagram
Reward: fourteen time-preserving methods for Instagram effective buyers Explore the methods Hootsuite employs to supply prime-top quality material.
Thank you for another magnificent post. The place else may just anybody get that type of information in such
an ideal manner of writing? I have a presentation subsequent week,
and I’m on the search for such information.
Hello it’s me, I am also visiting this web page daily, this website is
truly fastidious and the people are truly sharing fastidious thoughts.
We have put together the very best Instagram apps for your blog business instagram post 140808412679 good creative:
Modifying shots. These apps allow consumers to edit, resize and utilize filters.
Layout layout and design and style. These apps allow customers to include progressive elements like collages, graphics, along with other graphics to your website’s manufacturer’s page.
Video instruments. These purposes can enhance how your organization captures and makes videos.
Analytics engagement, facts, and facts within the audience. Obtain Instagram apps to track just how your viewers interacts and also the functionality of your material.
Table of Contents for Instagram format applicationsInstagram enhancing applicationInstagram online video enhancing applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-saving methods for Instagram impressive end users Find out the tricks Hootsuite employs to supply best-high-quality written content.
AO Sex mit Nutten im Auto gibt mir einfach den gewissen Kick.
Lass dich einfach verführen, wenn ihr im Auto seid. Denn nicht viele
Personen trauen sich einer Shemale an. Du entscheidest, ob
dein Partner oder deine Partnerin mehr darüber wissen darf,
oder ob du deine Leidenschaft für dich behältst.
Beim unzensierten Strassen Huren ficken am Parkplatz, gebe ich nach dem Hardcore Hurenfick den jungen Strich Schlampen für guten und ungeschützten Sex noch gerne ein wenig Trinkgeld oben drauf, denn der unkomplizierte Huren Sex im Auto ist mir auf jeden Fall mehr als 20Euro Wert.
Alleine schon wenn man bedenkt, dass das Ficken mit Strassen Huren in Kaplice keine 20Euro für den schnellen Hurensex im Auto kostet.
Obwohl in den meisten Fällen keine Belohnung stattfindet, verstärkt die Maschine
immer dann, wenn sie einen Preis vergibt,
das Verhalten des Münzwerfens. Trips oder Drilling: Alle drei Karten des gleichen Werts.
Haben beide Spieler One Pair, entscheiden die höheren Karten. Jeden Tag, von Montag
bis Sonntag, haben Sie somit Zugang zu vielen von einer Expertengruppe verfassten Prognoseanalysen über die
Sportarten und Wettbewerbe, die für Sie wirklich von Interesse sind.
Zudem bedarf es einer Einigung hinsichtlich der Erhebungsmodalitäten, daher wurden Guidelines für die
Dokumentation von Spielsüchtigen in Beratungs- und Behandlungseinrichtungen erstellt.
Good blog! I truly love how it is easy on my eyes and the data are well written. I’m
wondering how I could be notified whenever a new post has
been made. I have subscribed to your feed which must do the trick!
Have a nice day!
Feel free to visit my site; EZ Burn Keto
Wer aber möchte, kann sich in dem entsprechenden Online
Roulette Casino jederzeit für das Spiel um eigenes Geld entscheiden. Nützliche
Buchempfehlungen runden diese kleine Roulette Einführung ab.
Wie an den Namen abgeleitet werden kann, sind diese Darlehensvarianten entweder für
eine bestimmte Kundengruppe gedacht oder sie dürfen nur für einen festgelegten Zweck verwendet werden, wie
zum Beispiel zur Finanzierung des nächsten Autokaufs.
Der wesentliche Vorteil einer Restschuldversicherung besteht darin, dass
damit ausstehende Raten abgesichert werden, falls
eine bestimmte Situation beim Kreditnehmer eintritt.
Eine weitere Grundvoraussetzung für die positive Kreditentscheidung besteht darin, dass Sie eine ausreichende Kreditwürdigkeit,
auch als Bonität bezeichnet, besitzen. Dieser besteht darin, dass die Prämie relativ
hoch ist. Zu den Kosten eines Privatkredites kann unter Umständen auch die
Prämie für eine Restschuldversicherung gehören.
Das bedeutet, dass zum Beispiel ein Konsumentenkredit über 10.000
Euro jährlich Zinsen von durchschnittlich 550 Euro kosten würde.
Wenn ich die Natur von Binärhändlern kenne, würde ich vorschlagen, dass Sie beginnen, auf die Nachrichten zu achten, denn für
jeden Trend gibt es einen Grund. Das gleiche Ambiente, wenn Sie Solitaire spielen, könnte der Grund sein, warum Sie jedes Mal darauf zurückkommen möchten!
So können Sie hier nicht nur Texas Hold’em kostenlos spielen, sondern sich auch mit vielen anderen und
unbekannteren Spielen wie zum Beispiel Omaha,
Stud, Triple Draw 2-7, Razz und HORSE vertraut machen.
Instagram hashtags are essentially a way of categorizing and labelling your material. They also help Instagram provide your information to users that are pertinent.
Of their simplest sort the hashtags you select to implement are The idea for search engine results within the Take a look at webpage of Instagram:
However, it won’t halt there. Hashtags may also be employed as an indicator to Instagram’s algorithm. Instagram algorithm, which implies it is ready to categorize your articles and recommend that it’s revealed to users it thinks is likely being of fascination.
Then… Are Hashtags still get the job done in 2022 on Instagram by 2022?
Hashtags have been at the center of discussion especially in light-weight of Instagram’s recent suggestion to implement 3 and 5 hashtags (far more on this afterwards).
As Instagram steadily shifts for the semantic search engine, it opens a completely new realm of opportunities inside the search engine’s capacity to locate content material – meaning which the words you use with your captions, or maybe the subjects that you incorporate as part of your posts might be searchable likewise.
Even so, despite these considerable technological progress, hashtags however operate on Instagram. When paired by using a sound information tactic, they could deliver amazing effects.
Have you been wanting to down load the entire download of Instagram hashtags?
Examine our corey rose instagram health blog video tutorial at this moment.
If some one needs to be updated with most recent technologies afterward
he must be go to see this website and be up to date daily.
fantastic points altogether, you just gained a new reader.
What could you suggest in regards to your submit that you
made some days in the past? Any positive?
I like the helpful info you provide in your articles.
I will bookmark your weblog and check again here frequently.
I am quite certain I’ll learn many new stuff right here!
Good luck for the next!
Heya i’m for the first time here. I found this board and I find It truly useful
& it helped me out a lot. I hope to give something back and aid others like you
helped me.
Hello there! This blog post couldn’t be written any
better! Going through this article reminds me of my previous roommate!
He continually kept talking about this. I most certainly will
forward this information to him. Pretty sure he will have a great read.
Many thanks for sharing!
Can I simply just say what a relief to find an individual who really understands what
they’re talking about on the net. You certainly understand how to bring
a problem to light and make it important. More and more people should check this
out and understand this side of your story. It’s surprising you’re not more popular because you surely have the gift.
Hello there! I just want to give you a big thumbs up for the great info you have got here
on this post. I will be returning to your web site for more soon.
Instagram hashtags are effectively a method of categorizing and labelling your material. They also guide Instagram give your information to users that are pertinent.
In their simplest type the hashtags you select to work with are The idea for search engine results within the Explore website page of Instagram:
Nevertheless, it will not cease there. Hashtags can be applied as an indicator to Instagram’s algorithm. Instagram algorithm, which implies it will be able to categorize your material and advocate that it’s demonstrated to users it thinks is likely to become of desire.
Then… Are Hashtags nevertheless work in 2022 on Instagram by 2022?
Hashtags have already been at the middle of discussion specially in gentle of Instagram’s current recommendation to use 3 and 5 hashtags (far more on this later).
As Instagram little by little shifts to your semantic online search engine, it opens a wholly new realm of alternatives in the internet search engine’s ability to find material – this means which the phrases you use as part of your captions, or the topics that you simply incorporate in your posts will be searchable too.
Having said that, In spite of these sizeable technological progress, hashtags continue to functionality on Instagram. When paired which has a good material tactic, they may generate remarkable success.
Have you been prepared to down load the entire down load of Instagram hashtags?
Take a look at our can a marine in active duty have a personal blog on instagram video manual right now.
We’ve set jointly the top Instagram purposes for your link to blog on instagram:
Editing images. These apps permit people to edit, resize and implement filters.
Structure layout and layout. These applications allow for customers to incorporate innovative aspects like collages, graphics, along with other graphics to your internet site’s manufacturer’s web page.
Movie instruments. These purposes can increase the best way your organization captures and results in video clips.
Analytics engagement, details, and data over the viewers. Down load Instagram apps to track how your viewers interacts and also the overall performance of the content.
Desk of Contents for Instagram layout applicationsInstagram enhancing applicationInstagram online video modifying applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-preserving methods for Instagram strong customers Learn the tricks Hootsuite employs to provide leading-excellent articles.
Wenn Sie auf der Suche nach den besten kostenlosen Porno Videos sind, die Ihre Zufriedenheit garantieren, suchen Sie nicht weiter, denn sie sind alle auf
FrauPorno! Abwechslung beim Porno schauen muss ganz einfach sein. Dies
zeigt, dass gerade im Turnierspiel die unbekannten Spieler den großen Pokerstars während einer einzelnen Meisterschaft nicht
zwingend unterlegen sein müssen. Dies kann entweder aus
einem fast abgeschlossenem Spiel resultieren oder aufgrund einer eigenen Turniervariante so sein. Diese besteht
entweder aus Geld oder aus Sachspreisen. Key Hand: Während des Spiels, kann ein Blatt jemanden entweder zum Sieg oder zur Niederlage führen und die Hand, die hauptsächlich für den Erfolg /
Misserfolg des Spielers verantwortlich war, wird Key Hand genannt.
Flat Call: Wenn man eine so gute Hand hat, dass man damit eigentlich ein Raise setzen müsste,
jedoch nur den Einsatz des Konkurrenten callt, wird diese Aktion als Flat Call bezeichnet.
Dabei versucht man durch das Vortäuschen einer guten Hand die Konkurrenten zum Aussteigen zu bewegen.
Have a look at my web blog: Casino
Very good article! We will be linking to this great post on our
site. Keep up the good writing.
Also visit my webpage; bareboat charter whitsundays
It’s really very complicated in this busy life to listen news on TV, thus I only use internet for that purpose,
and obtain the hottest news.
Je nach Position sollten Sie eine andere Preflop Poker Taktik wählen. Vor allem wird eine einheitliche Position für
das Glücksspiel im Netz festgehalten. Vor allem für High Roller ist das eine
ganz bittere Pille, denn das Limit bei den betroffenen Brands liegt bei
lediglich einem Euro pro Runde. Weil sich viele Spieler durch Maßnahmen, wie die 1 Euro Regel oder das 1.000 Euro Einzahlungslimit,
in ihrer Entscheidungsfreiheit beschnitten fühlen, droht eine starke Abwanderung zu Casinos ohne
Limit. Natürlich hat man von 500 Euro, die exklusiv
bei Pokerstars vergeben werden, mehr als von einem 40 Euro Bonus,
den beispielsweise DrückGlück seinen neuen Nutzern spendiert.
Setzen Geld ein. Weil sie hervorragend spielen können, gewinnen sie mehr, als sie verlieren. Jedoch bedeutet Fairness weit mehr, als
hohe Boni auszuteilen. Letztere sollten im Schnitt mindestens 96% betragen, um als fair und
solide eingestuft werden zu können. Auch zukünftig werden wir weiter
vor unseriösen Casinoanbietern warnen.
Here is my web blog :: Porno
Hey there just wanted to give you a quick heads up. The text in your article seem to be
running off the screen in Chrome. I’m not sure if this is a format issue or
something to do with browser compatibility but I thought I’d post to let
you know. The layout look great though! Hope you get the issue solved soon. Cheers
Instagram hashtags are basically a approach to categorizing and labelling your written content. Additionally they aid Instagram offer your content to consumers who are relevant.
Inside their simplest sort the hashtags you decide on to make use of are the basis for search engine results over the Explore web page of Instagram:
Nevertheless, it isn’t going to end there. Hashtags can even be made use of being an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it is ready to categorize your information and advise that it’s revealed to end users it believes is probably going to get of desire.
Then… Are Hashtags however get the job done in 2022 on Instagram by 2022?
Hashtags happen to be at the center of discussion especially in light of Instagram’s latest recommendation to work with 3 and five hashtags (far more on this later on).
As Instagram little by little shifts to the semantic online search engine, it opens an entirely new realm of prospects in the search engine’s ability to locate articles – indicating the words you employ in your captions, or perhaps the topics that you consist of inside your posts might be searchable also.
Nevertheless, In spite of these major technological breakthroughs, hashtags however function on Instagram. When paired by using a reliable articles approach, they may make remarkable effects.
Are you presently willing to down load the entire obtain of Instagram hashtags?
Consider our providence food blog “johanny castillo” instagram movie information right now.
valacyclovir genital herpes valacyclovir 500mg price how fast does valtrex work reddit how long until valacyclovir works
We’ve set collectively the top Instagram programs for your how do i put link on my blog to my business page instagram:
Modifying photographs. These apps make it possible for users to edit, resize and apply filters.
Format layout and structure. These applications allow end users to incorporate ground breaking things like collages, graphics, as well as other graphics to your internet site’s model’s website page.
Online video applications. These purposes can boost the way your company captures and creates movies.
Analytics engagement, facts, and information around the viewers. Download Instagram applications to track the way your audience interacts and also the effectiveness of the articles.
Table of Contents for Instagram structure applicationsInstagram editing applicationInstagram video clip modifying applicationInstagram analytics appsApps for engagement on Instagram
Reward: fourteen time-saving tricks for Instagram potent customers Learn the tips Hootsuite employs to make top-excellent information.
WOW just what I was looking for. Came here by searching for site
This can be done by using the mobile offerings
My website Gg Bet
I just could not go away your site before suggesting that I really enjoyed the standard info a person supply on your
guests? Is going to be back continuously in order to inspect new posts
Instagram hashtags are in essence a technique of categorizing and labelling your information. They also help Instagram provide your information to users who’re applicable.
Within their easiest kind the hashtags you select to use are the basis for search engine results to the Check out page of Instagram:
Having said that, it will not stop there. Hashtags can also be made use of as an indicator to Instagram’s algorithm. Instagram algorithm, meaning it has the capacity to categorize your material and advocate that it’s proven to consumers it thinks is probably going to be of fascination.
Then… Are Hashtags even now work in 2022 on Instagram by 2022?
Hashtags are at the middle of debate specifically in mild of Instagram’s latest suggestion to use three and five hashtags (a lot more on this later on).
As Instagram step by step shifts to the semantic online search engine, it opens a wholly new realm of opportunities inside the online search engine’s power to locate content material – this means which the words and phrases you employ inside your captions, or even the subjects that you simply incorporate with your posts might be searchable in addition.
Nonetheless, Inspite of these major technological improvements, hashtags nonetheless perform on Instagram. When paired by using a solid articles approach, they could develop remarkable outcomes.
Are you willing to down load the whole down load of Instagram hashtags?
Have a look at our how to make a blog on instagram video guide today.
We have place collectively the most beneficial Instagram programs for your instagram blog business:
Modifying shots. These applications allow for end users to edit, resize and use filters.
Layout layout and style and design. These applications enable consumers to incorporate revolutionary things like collages, graphics, and various graphics to your site’s brand name’s web page.
Video clip instruments. These purposes can improve the way your business captures and produces video clips.
Analytics engagement, information, and details on the viewers. Down load Instagram apps to trace the way in which your viewers interacts plus the overall performance of one’s content.
Table of Contents for Instagram format applicationsInstagram modifying applicationInstagram video clip editing applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-saving tricks for Instagram highly effective end users Uncover the tips Hootsuite employs to provide best-excellent material.
Having read this I thought it was very enlightening.
I appreciate you spending some time and energy to put this informative article
together. I once again find myself spending
way too much time both reading and commenting. But so what, it was still worthwhile!
We have place jointly the top Instagram purposes for your how to get an instagram button on your blog:
Enhancing shots. These apps make it possible for buyers to edit, resize and apply filters.
Layout format and layout. These applications permit people to include revolutionary components like collages, graphics, as well as other graphics to your site’s brand’s web site.
Video instruments. These purposes can boost the best way your business captures and generates video clips.
Analytics engagement, details, and info within the audience. Obtain Instagram applications to track how your audience interacts as well as performance of the content material.
Desk of Contents for Instagram structure applicationsInstagram enhancing applicationInstagram video modifying applicationInstagram analytics appsApps for engagement on Instagram
Reward: 14 time-preserving tricks for Instagram powerful consumers Discover the tips Hootsuite employs to supply leading-high-quality material.
Thanks for the auspicious writeup. It if truth be told used to be a
leisure account it. Glance complicated to far brought agreeable
from you! However, how could we be in contact?
We have set with each other the best Instagram purposes for your the small things blog phone case instagram:
Modifying photos. These applications make it possible for end users to edit, resize and apply filters.
Structure structure and layout. These applications make it possible for end users to include modern aspects like collages, graphics, together with other graphics to your site’s brand’s web site.
Video clip tools. These apps can greatly enhance the way in which your business captures and generates movies.
Analytics engagement, info, and knowledge within the audience. Obtain Instagram applications to track the way in which your audience interacts along with the general performance of the written content.
Desk of Contents for Instagram layout applicationsInstagram enhancing applicationInstagram video clip modifying applicationInstagram analytics appsApps for engagement on Instagram
Bonus: fourteen time-preserving tricks for Instagram potent customers Explore the tips Hootsuite employs to create leading-good quality content material.
You don’t necessarily want enterprise-velocity internet to be able
to recreation seamlessly, however you do need no less
than 15-20Mbps if you’re going to play games.
This means that you could play some games immediately in compatible web browsers without
downloading the archives to the local system first. This is also true without spending a dime Internet games that aren’t necessarily meant for playing on the web
but can fairly be put in on the desktop. Owning, really proudly
owning, an iPhone in 2013 or 2017 would have meant having the
power to put in a competing working system with ongoing safety updates.
So on this game, you’ve a catapult to launch the Gnome to the farthest field of the backyard.
These early impressions are unscored and a little less formal,
and you’ll know exactly what we’ve performed and what we nonetheless should do earlier than we’re snug transferring on to the evaluation in progress or even the final evaluate.
fantastic issues altogether, you just received a new
reader. What may you recommend about your publish that you simply made a few days ago?
Any sure?
I love what you guys are up too. This sort of clever work and exposure!
Keep up the excellent works guys I’ve incorporated
you guys to my blogroll.
Instagram hashtags are in essence a means of categorizing and labelling your content material. They also help Instagram deliver your written content to users who will be related.
Inside their easiest kind the hashtags you select to employ are The idea for search results around the Investigate web site of Instagram:
Even so, it doesn’t stop there. Hashtags can even be employed being an indicator to Instagram’s algorithm. Instagram algorithm, which implies it has the capacity to categorize your content and advise that it’s proven to people it thinks is likely to generally be of curiosity.
Then… Are Hashtags even now perform in 2022 on Instagram by 2022?
Hashtags are actually at the middle of discussion especially in gentle of Instagram’s current recommendation to utilize 3 and five hashtags (far more on this afterwards).
As Instagram step by step shifts to the semantic search engine, it opens an entirely new realm of prospects from the search engine’s capacity to obtain written content – this means the text you use inside your captions, or perhaps the topics which you consist of with your posts will be searchable at the same time.
Even so, In spite of these substantial technological enhancements, hashtags however operate on Instagram. When paired that has a good content tactic, they could create wonderful success.
Will you be wanting to obtain the entire download of Instagram hashtags?
Look into our can dog and food be a good blog for instagram video clip tutorial today.
Peculiar article, just what I needed.
Instagram hashtags are in essence a technique of categorizing and labelling your content material. In addition they aid Instagram give your content to people who’re relevant.
Of their most basic type the hashtags you end up picking to employ are The premise for search engine results within the Discover page of Instagram:
On the other hand, it isn’t going to quit there. Hashtags will also be utilized as an indicator to Instagram’s algorithm. Instagram algorithm, which means it will be able to categorize your written content and advocate that it’s shown to consumers it believes is probably going to become of desire.
Then… Are Hashtags still perform in 2022 on Instagram by 2022?
Hashtags are actually at the center of debate particularly in light-weight of Instagram’s new suggestion to utilize three and 5 hashtags (more on this afterwards).
As Instagram little by little shifts into the semantic internet search engine, it opens an entirely new realm of opportunities from the search engine’s power to uncover content material – meaning the words and phrases you utilize with your captions, or maybe the topics you contain within your posts are going to be searchable likewise.
Even so, Regardless of these sizeable technological improvements, hashtags even now purpose on Instagram. When paired having a sound material strategy, they might create awesome success.
Are you currently all set to down load the entire obtain of Instagram hashtags?
Look into our what is an instagram story blog online video guidebook at this time.
Instagram hashtags are effectively a way of categorizing and labelling your material. In addition they guide Instagram deliver your written content to people who are suitable.
Inside their easiest variety the hashtags you select to implement are the basis for search engine results over the Take a look at page of Instagram:
Nevertheless, it isn’t going to cease there. Hashtags will also be utilized being an indicator to Instagram’s algorithm. Instagram algorithm, which implies it has the capacity to categorize your articles and advise that or not it’s proven to people it thinks is likely to become of desire.
Then… Are Hashtags continue to work in 2022 on Instagram by 2022?
Hashtags have been at the center of debate specially in mild of Instagram’s new recommendation to make use of three and 5 hashtags (more on this later on).
As Instagram little by little shifts to your semantic online search engine, it opens a wholly new realm of possibilities while in the internet search engine’s power to find articles – which means that the phrases you utilize in your captions, or even the topics that you just involve as part of your posts are going to be searchable as well.
Nonetheless, despite these major technological advancements, hashtags even now functionality on Instagram. When paired with a reliable articles tactic, they could create amazing success.
Will you be all set to download the whole download of Instagram hashtags?
Have a look at our beauty blog instagram online video guideline right this moment.
You’re so awesome! I do not suppose I’ve truly read
through a single thing like that before. So nice to find
someone with unique thoughts on this subject matter.
Seriously.. thank you for starting this up. This site is one thing that is required on the internet,
someone with some originality!
Yes! Finally something about rv repair near me.
Instagram hashtags are effectively a technique of categorizing and labelling your information. Additionally they help Instagram offer your material to customers who’re relevant.
Within their easiest variety the hashtags you select to implement are The premise for search engine results on the Discover page of Instagram:
Even so, it will not cease there. Hashtags can even be utilized being an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it is able to categorize your content and advise that it be revealed to people it believes is likely to get of desire.
Then… Are Hashtags however do the job in 2022 on Instagram by 2022?
Hashtags have already been at the middle of debate particularly in mild of Instagram’s modern suggestion to make use of three and 5 hashtags (additional on this later on).
As Instagram slowly shifts for the semantic online search engine, it opens an entirely new realm of alternatives inside the search engine’s ability to obtain content material – which means the words and phrases you employ in the captions, or the topics that you simply consist of in your posts are going to be searchable as well.
Nonetheless, Inspite of these sizeable technological developments, hashtags continue to purpose on Instagram. When paired which has a solid written content tactic, they may make astounding effects.
Do you think you’re willing to obtain the entire obtain of Instagram hashtags?
Consider our jenns blah blah blog instagram movie guide right this moment.
Hi this is kinda of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding expertise so I wanted to get advice from someone with experience.
Any help would be greatly appreciated!
This paragraph will help the internet viewers for building up new web site or
even a blog from start to end.
molnupiravir brand name molnupirivir molnupiravir is it like ivermectin molnupiravir sales
I’m truly enjoying the design and layout of your blog. It’s a
very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire
out a designer to create your theme? Superb work!
Instagram hashtags are basically a way of categorizing and labelling your content material. They also support Instagram give your content material to end users who’re suitable.
Within their most straightforward form the hashtags you decide on to utilize are the basis for search engine results to the Discover website page of Instagram:
Even so, it would not prevent there. Hashtags can also be used as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it is ready to categorize your articles and endorse that it be demonstrated to people it believes is likely to be of fascination.
Then… Are Hashtags still get the job done in 2022 on Instagram by 2022?
Hashtags are actually at the center of debate specifically in light of Instagram’s recent recommendation to work with three and 5 hashtags (a lot more on this afterwards).
As Instagram progressively shifts for the semantic search engine, it opens an entirely new realm of possibilities while in the internet search engine’s capacity to come across content – indicating that the phrases you employ within your captions, or maybe the topics you contain inside your posts will probably be searchable likewise.
However, Regardless of these considerable technological breakthroughs, hashtags continue to perform on Instagram. When paired using a strong material approach, they might generate remarkable final results.
Do you think you’re ready to obtain the complete down load of Instagram hashtags?
Have a look at our business blog instagram video clip guide today.
Instagram hashtags are fundamentally a method of categorizing and labelling your information. They also aid Instagram offer your written content to users who’re applicable.
Of their easiest sort the hashtags you choose to implement are the basis for search engine results on the Investigate site of Instagram:
Having said that, it doesn’t quit there. Hashtags may also be used as an indicator to Instagram’s algorithm. Instagram algorithm, which means it is ready to categorize your content material and suggest that it’s shown to end users it thinks is probably going to be of curiosity.
Then… Are Hashtags however do the job in 2022 on Instagram by 2022?
Hashtags are actually at the center of discussion particularly in gentle of Instagram’s modern recommendation to employ 3 and five hashtags (additional on this afterwards).
As Instagram progressively shifts towards the semantic online search engine, it opens a wholly new realm of possibilities during the search engine’s capability to locate content material – which means that the text you employ within your captions, or even the topics that you involve in your posts will be searchable likewise.
On the other hand, despite these major technological advancements, hashtags still operate on Instagram. When paired with a solid articles strategy, they might generate incredible results.
Are you currently ready to down load the complete download of Instagram hashtags?
Consider our how to make an instagram blog video guidebook at this time.
Hi, i think that i saw you visited my blog so i came to go
back the prefer?.I’m trying to in finding things to improve my web site!I assume its good
enough to make use of a few of your ideas!!
Somebody essentially assist to make significantly articles I would state.
This is the very first time I frequented your website page and
thus far? I surprised with the analysis you made
to make this actual put up incredible. Excellent activity!
Hmm is anyone else encountering problems with the pictures oon this blog
loading? I’m trying to figure out if its a problem on my end orr if it’s the blog.
Any feedback would be greatly appreciated.
Instagram hashtags are primarily a approach to categorizing and labelling your articles. In addition they guide Instagram deliver your information to users who are related.
Inside their most straightforward type the hashtags you choose to use are the basis for search engine results around the Discover site of Instagram:
However, it won’t stop there. Hashtags can be utilized as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it will be able to categorize your information and propose that or not it’s demonstrated to end users it thinks is likely to get of fascination.
Then… Are Hashtags however get the job done in 2022 on Instagram by 2022?
Hashtags have been at the center of debate specifically in mild of Instagram’s latest suggestion to use three and five hashtags (much more on this afterwards).
As Instagram step by step shifts to the semantic internet search engine, it opens an entirely new realm of opportunities inside the internet search engine’s power to discover content material – indicating the words you employ inside your captions, or perhaps the subjects that you simply incorporate in the posts will likely be searchable also.
Having said that, despite these considerable technological advancements, hashtags still perform on Instagram. When paired by using a sound articles method, they could generate amazing effects.
Are you willing to down load the complete obtain of Instagram hashtags?
Consider our how to take off phone number from instagram personal blog account video guidebook at this moment.
Hey I know this is off topic but I was wondering if you knew
of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time
and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I
look forward to your new updates.
электророхля
https://samokhodnyye-elektricheskiye-telezhki.ru/
オンカジを選ぶ際、デザインやボーナスも決め手ポイントですが、信頼できるライセンスを保有しているかどうかが1番大事な確認事項。
Also visit my blog post – ネット カジノ 日本 (https://casinoonlines.jp)
Instagram hashtags are effectively a way of categorizing and labelling your content. In addition they help Instagram deliver your material to people that are appropriate.
Inside their most basic type the hashtags you choose to work with are The premise for search results over the Explore site of Instagram:
Having said that, it won’t halt there. Hashtags can even be made use of being an indicator to Instagram’s algorithm. Instagram algorithm, which means it will be able to categorize your material and advise that it be proven to consumers it thinks is likely to be of desire.
Then… Are Hashtags nonetheless operate in 2022 on Instagram by 2022?
Hashtags happen to be at the middle of discussion particularly in light-weight of Instagram’s the latest recommendation to make use of three and 5 hashtags (far more on this later on).
As Instagram progressively shifts to the semantic search engine, it opens a completely new realm of opportunities while in the internet search engine’s power to locate content – indicating the terms you employ within your captions, or maybe the topics which you include within your posts will likely be searchable at the same time.
On the other hand, Even with these considerable technological enhancements, hashtags still function on Instagram. When paired using a reliable information strategy, they could make amazing success.
Are you presently wanting to down load the entire obtain of Instagram hashtags?
Have a look at our design blog instagram stories video clip tutorial right this moment.
I got this website from my buddy who shared with me about this web page and now this
time I am browsing this web page and reading very informative posts here.
Instagram hashtags are primarily a method of categorizing and labelling your material. In addition they help Instagram offer your content material to customers who’re related.
Of their most basic kind the hashtags you select to employ are the basis for search engine results on the Take a look at website page of Instagram:
Nevertheless, it would not cease there. Hashtags can also be made use of as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it is able to categorize your content and propose that or not it’s demonstrated to people it believes is likely to be of interest.
Then… Are Hashtags continue to do the job in 2022 on Instagram by 2022?
Hashtags are at the center of discussion specially in gentle of Instagram’s modern suggestion to utilize three and 5 hashtags (a lot more on this later on).
As Instagram step by step shifts to the semantic internet search engine, it opens a completely new realm of alternatives while in the online search engine’s capacity to discover information – this means that the words and phrases you utilize with your captions, or the subjects that you choose to include inside your posts is going to be searchable at the same time.
Having said that, Inspite of these considerable technological advancements, hashtags even now function on Instagram. When paired with a sound content material system, they may produce incredible final results.
Are you ready to obtain the complete down load of Instagram hashtags?
Examine our mini blog with instagram movie guideline at this time.
электророхля
http://www.samokhodnyye-elektricheskiye-telezhki.ru/
This is my first time go to see at here and i am genuinely pleassant to read all at alone place.
Instagram hashtags are in essence a means of categorizing and labelling your written content. In addition they assist Instagram present your content material to people who’re appropriate.
Of their most straightforward type the hashtags you end up picking to make use of are The idea for search results over the Investigate page of Instagram:
On the other hand, it doesn’t quit there. Hashtags can also be applied as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it has the capacity to categorize your content and propose that it’s proven to consumers it thinks is likely to become of interest.
Then… Are Hashtags continue to work in 2022 on Instagram by 2022?
Hashtags have been at the middle of debate specifically in light-weight of Instagram’s recent recommendation to make use of 3 and five hashtags (a lot more on this afterwards).
As Instagram progressively shifts to the semantic online search engine, it opens a completely new realm of options inside the online search engine’s capacity to find content material – meaning the text you use inside your captions, or maybe the subjects that you choose to involve in the posts might be searchable likewise.
Having said that, despite these substantial technological developments, hashtags however purpose on Instagram. When paired which has a stable information tactic, they might create remarkable benefits.
Are you currently prepared to obtain the complete download of Instagram hashtags?
Have a look at our how to add an instagram button to wordpress blog online video guide at the moment.
Instagram hashtags are primarily a means of categorizing and labelling your information. In addition they aid Instagram offer your content to people who are applicable.
In their simplest variety the hashtags you end up picking to use are The idea for search engine results on the Check out site of Instagram:
Having said that, it would not end there. Hashtags can even be utilized as an indicator to Instagram’s algorithm. Instagram algorithm, meaning it is able to categorize your material and recommend that or not it’s demonstrated to consumers it thinks is likely being of interest.
Then… Are Hashtags however operate in 2022 on Instagram by 2022?
Hashtags have already been at the middle of debate specially in gentle of Instagram’s latest suggestion to employ 3 and five hashtags (much more on this afterwards).
As Instagram little by little shifts to your semantic search engine, it opens an entirely new realm of possibilities during the internet search engine’s ability to uncover content – this means the words you employ within your captions, or even the topics you incorporate inside your posts might be searchable as well.
However, despite these major technological advancements, hashtags still function on Instagram. When paired using a reliable content material strategy, they could generate astounding success.
Have you been able to obtain the whole obtain of Instagram hashtags?
Look into our instagram kiЕџisel blog nedir movie tutorial at the moment.
Hello, always i used to check webpage posts here early in the morning,
as i enjoy to learn more and more.
You could certainly see your expertise within the work you
write. The world hopes for even more passionate writers like you
who are not afraid to say how they believe. All the time
go after your heart.
No matter if some one searches for his required thing,
therefore he/she desires to be available that in detail, therefore
that thing is maintained over here.
Hey just wanted to give you a brief heads up and let you know
a few of the images aren’t loading properly. I’m not sure why but
I think its a linking issue. I’ve tried it
in two different browsers and both show the same results.
Instagram hashtags are in essence a means of categorizing and labelling your material. They also guide Instagram supply your material to consumers who are pertinent.
Within their most straightforward variety the hashtags you end up picking to employ are The idea for search results to the Discover website page of Instagram:
However, it doesn’t prevent there. Hashtags can even be employed as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it can categorize your content material and advocate that or not it’s proven to customers it believes is probably going to become of curiosity.
Then… Are Hashtags nevertheless operate in 2022 on Instagram by 2022?
Hashtags happen to be at the center of debate particularly in light-weight of Instagram’s recent suggestion to employ 3 and five hashtags (additional on this later).
As Instagram slowly shifts for the semantic search engine, it opens an entirely new realm of alternatives while in the search engine’s ability to come across written content – which means the words and phrases you utilize as part of your captions, or maybe the topics which you contain in your posts will be searchable in addition.
Even so, In spite of these significant technological developments, hashtags continue to function on Instagram. When paired having a solid material method, they may generate incredible results.
Are you willing to down load the entire download of Instagram hashtags?
Consider our why is my instagram feed not updating on blog online video guideline at the moment.
Excellent article. Keep posting such kind of info on your page.
Im really impressed by your blog.[X-N-E-W-L-I-N-S-P-I-N-X]Hey there,
You have performed an excellent job. I will certainly digg it and for my
part suggest to my friends. I’m sure they’ll be benefited from
this web site.
my web page – Total Cure Keto Gummies
スロットゲームで最大限に勝利金を獲得するには、やはりボーナスラウンドの獲得が鍵となります。
My homepage :: ボンズ カジノ ルーレット – %E3%83%9C%E3%83%B3%E3%82%BA%E3%82%AB%E3%82%B8%E3%83%8E%E3%82%AA%E3%83%B3%E3%83%A9%E3%82%A4%E3%83%B3.com,
Very soon this website will be famous among all blogging and
site-building visitors, due to it’s good articles or reviews
Instagram hashtags are essentially a means of categorizing and labelling your articles. They also assist Instagram offer your articles to customers who will be suitable.
In their most straightforward variety the hashtags you choose to work with are The idea for search results about the Explore web site of Instagram:
Nevertheless, it doesn’t prevent there. Hashtags can also be applied being an indicator to Instagram’s algorithm. Instagram algorithm, which means it is able to categorize your content material and recommend that it be proven to people it thinks is likely for being of desire.
Then… Are Hashtags nevertheless operate in 2022 on Instagram by 2022?
Hashtags are at the middle of debate specially in mild of Instagram’s the latest suggestion to employ three and five hashtags (additional on this afterwards).
As Instagram slowly shifts to your semantic search engine, it opens an entirely new realm of options during the internet search engine’s ability to obtain content material – that means which the text you utilize within your captions, or maybe the subjects you consist of within your posts will likely be searchable too.
Nevertheless, Regardless of these sizeable technological developments, hashtags even now operate on Instagram. When paired having a good written content tactic, they could generate amazing effects.
Are you willing to down load the entire down load of Instagram hashtags?
Take a look at our blog, facebook, instagram all in one place shown on website video manual at this moment.
Instagram hashtags are essentially a way of categorizing and labelling your articles. They also assist Instagram give your written content to consumers who are pertinent.
In their most straightforward kind the hashtags you select to work with are the basis for search results on the Examine web page of Instagram:
Nevertheless, it won’t end there. Hashtags will also be made use of as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it can categorize your content material and propose that it’s shown to buyers it believes is likely to become of curiosity.
Then… Are Hashtags nevertheless do the job in 2022 on Instagram by 2022?
Hashtags are actually at the center of debate particularly in light-weight of Instagram’s new recommendation to work with three and five hashtags (more on this later on).
As Instagram slowly shifts to your semantic online search engine, it opens an entirely new realm of possibilities inside the internet search engine’s capacity to find information – indicating which the words and phrases you employ with your captions, or perhaps the subjects that you consist of with your posts will probably be searchable in addition.
Having said that, In spite of these significant technological breakthroughs, hashtags nevertheless perform on Instagram. When paired having a good content material tactic, they may make remarkable results.
Are you currently prepared to obtain the complete download of Instagram hashtags?
Consider our colocar instagram no blog movie guideline right this moment.
dfg
It’s the best time to make a few plans for the longer term and it
is time to be happy. I have read this submit and if I may
I want to counsel you some interesting things or tips.
Maybe you can write subsequent articles relating to this article.
I want to read even more things about it!
Hi! This is kind of off topic but I need some help from an established blog.
Is it hard to set up your own blog? I’m not
very techincal but I can figure things out pretty quick.
I’m thinking about making my own but I’m not sure
where to start. Do you have any points or suggestions?
Thanks
Instagram hashtags are effectively a approach to categorizing and labelling your information. In addition they guide Instagram present your content to users who will be relevant.
Of their most straightforward type the hashtags you choose to use are The premise for search engine results about the Check out page of Instagram:
On the other hand, it will not cease there. Hashtags may also be employed as an indicator to Instagram’s algorithm. Instagram algorithm, which means it is ready to categorize your written content and advise that it’s demonstrated to end users it believes is probably going to get of curiosity.
Then… Are Hashtags still operate in 2022 on Instagram by 2022?
Hashtags are actually at the middle of discussion specially in light-weight of Instagram’s the latest suggestion to employ 3 and five hashtags (additional on this later).
As Instagram step by step shifts for the semantic internet search engine, it opens a completely new realm of choices during the search engine’s power to find material – this means which the words you utilize in the captions, or even the topics that you choose to contain with your posts are going to be searchable too.
Nevertheless, Inspite of these considerable technological improvements, hashtags nevertheless operate on Instagram. When paired having a solid content method, they may create incredible outcomes.
Will you be ready to obtain the complete obtain of Instagram hashtags?
Check out our wordpress blog post to instagram online video guideline at this moment.
Greetings from Los angeles! I’m bored to tears at work so I
decided to check out your website on my iphone during lunch break.
I really like the information you provide here and can’t wait to take a look when I get home.
I’m shocked at how quick your blog loaded on my phone
.. I’m not even using WIFI, just 3G .. Anyhow, wonderful site!
It’s very easy to find out any toplic on net as compared to textbooks, as I found this
piece of writing at this web site.
My brother suggested I might like this web site. He was totally right.
This post actually made my day. You cann’t imagine just how much time I had spent for this info!
Thanks!
Instagram hashtags are basically a means of categorizing and labelling your articles. They also guide Instagram offer your written content to customers who’re suitable.
Inside their simplest sort the hashtags you select to implement are the basis for search engine results around the Discover page of Instagram:
Having said that, it does not quit there. Hashtags can even be employed as an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it can categorize your content and recommend that it be shown to consumers it thinks is probably going to be of fascination.
Then… Are Hashtags even now function in 2022 on Instagram by 2022?
Hashtags have already been at the middle of discussion specifically in light of Instagram’s recent recommendation to make use of 3 and five hashtags (much more on this later on).
As Instagram gradually shifts on the semantic search engine, it opens a completely new realm of choices while in the internet search engine’s power to find written content – this means that the words you employ inside your captions, or even the subjects that you simply incorporate within your posts will be searchable likewise.
Having said that, despite these sizeable technological breakthroughs, hashtags however function on Instagram. When paired using a reliable written content approach, they could deliver astounding effects.
Are you presently prepared to download the whole down load of Instagram hashtags?
Check out our what should i name my blog on instagram online video guideline today.
I do agree with all the ideas you have introduced in your post.
They’re really convincing and will definitely work.
Nonetheless, the posts are too brief for starters. May just you please
lengthen them a little from subsequent time? Thank you for the post.
Instagram hashtags are essentially a way of categorizing and labelling your material. Additionally they help Instagram give your material to users who’re applicable.
Within their easiest variety the hashtags you choose to work with are The premise for search results to the Examine website page of Instagram:
Having said that, it would not end there. Hashtags can be applied as an indicator to Instagram’s algorithm. Instagram algorithm, meaning it will be able to categorize your information and suggest that it be proven to consumers it thinks is likely to generally be of fascination.
Then… Are Hashtags nonetheless operate in 2022 on Instagram by 2022?
Hashtags are at the middle of discussion notably in mild of Instagram’s the latest recommendation to utilize 3 and 5 hashtags (a lot more on this later on).
As Instagram slowly shifts to the semantic search engine, it opens a completely new realm of choices while in the search engine’s capability to discover information – this means which the words and phrases you employ inside your captions, or maybe the subjects you include in the posts are going to be searchable likewise.
However, Even with these substantial technological enhancements, hashtags even now function on Instagram. When paired that has a reliable content material technique, they may produce wonderful success.
Are you presently all set to download the whole download of Instagram hashtags?
Consider our how to start an instagram blog from scratch movie guideline at this moment.
Instagram hashtags are fundamentally a means of categorizing and labelling your information. They also aid Instagram give your written content to end users that are relevant.
In their simplest sort the hashtags you decide on to make use of are The premise for search results to the Discover page of Instagram:
Nevertheless, it would not halt there. Hashtags can also be applied as an indicator to Instagram’s algorithm. Instagram algorithm, which implies it has the capacity to categorize your content material and advocate that or not it’s shown to people it believes is likely to get of interest.
Then… Are Hashtags even now operate in 2022 on Instagram by 2022?
Hashtags are actually at the middle of discussion significantly in mild of Instagram’s latest suggestion to utilize three and 5 hashtags (a lot more on this afterwards).
As Instagram gradually shifts to the semantic online search engine, it opens a wholly new realm of possibilities within the search engine’s ability to locate written content – which means the text you employ as part of your captions, or perhaps the topics that you just include in the posts is going to be searchable as well.
Nevertheless, Irrespective of these considerable technological progress, hashtags continue to purpose on Instagram. When paired which has a sound content tactic, they might deliver remarkable final results.
Do you think you’re wanting to download the entire obtain of Instagram hashtags?
Check out our how to start health and fitness blog instagram video clip guidebook at this moment.
Hello, i think that i saw you visited my blog thus i
came to “return the favor”.I’m trying to find things to improve my web site!I suppose its ok to use a few of your ideas!!
Aw, this was an exceptionally nice post. Taking a few minutes and
actual effort to create a really good article… but what can I say… I procrastinate a lot and never
manage to get nearly anything done.
Can you tell us more about this? I’d like to find out more details.
my webpage: Judi slot online jackpot terbesar
Instagram hashtags are fundamentally a means of categorizing and labelling your information. They also support Instagram deliver your information to people who’re applicable.
Within their most basic type the hashtags you select to employ are The idea for search results to the Check out webpage of Instagram:
Nonetheless, it isn’t going to cease there. Hashtags may also be applied being an indicator to Instagram’s algorithm. Instagram algorithm, meaning it will be able to categorize your content material and suggest that or not it’s demonstrated to consumers it thinks is likely to be of fascination.
Then… Are Hashtags nevertheless operate in 2022 on Instagram by 2022?
Hashtags are already at the center of discussion particularly in gentle of Instagram’s recent recommendation to make use of three and five hashtags (much more on this later on).
As Instagram gradually shifts towards the semantic online search engine, it opens an entirely new realm of opportunities within the search engine’s capacity to locate written content – this means the phrases you use within your captions, or maybe the subjects which you include inside your posts will probably be searchable at the same time.
Having said that, Inspite of these important technological advancements, hashtags however function on Instagram. When paired using a stable material strategy, they might deliver wonderful results.
Have you been able to obtain the whole download of Instagram hashtags?
Examine our starting an instagram for your blog video information at the moment.
Każde niuanse i subtelności można znaleźć w Polityce firmy.
Here is my blog post parimatch Polska
Way cool! Some very valid points! I appreciate you penning this post plus the
rest of the website is extremely good.
Instagram hashtags are essentially a technique of categorizing and labelling your content material. In addition they help Instagram present your content material to people who’re applicable.
Inside their easiest variety the hashtags you choose to utilize are The idea for search engine results to the Examine website page of Instagram:
Having said that, it does not halt there. Hashtags can be utilised being an indicator to Instagram’s algorithm. Instagram algorithm, which suggests it will be able to categorize your information and advise that it’s shown to consumers it believes is likely for being of desire.
Then… Are Hashtags continue to work in 2022 on Instagram by 2022?
Hashtags have been at the center of discussion especially in light of Instagram’s new suggestion to work with three and 5 hashtags (extra on this afterwards).
As Instagram gradually shifts into the semantic internet search engine, it opens a completely new realm of options from the internet search engine’s power to locate articles – which means that the phrases you use in your captions, or the topics that you choose to include in your posts will be searchable at the same time.
However, Regardless of these major technological advancements, hashtags even now function on Instagram. When paired which has a reliable content material approach, they could generate awesome benefits.
Do you think you’re ready to download the complete down load of Instagram hashtags?
Look into our skunkboy blog instagram online video manual right this moment.
I am really glad to read this website posts which contains lots of useful facts, thanks for providing these statistics.
What Is The Google Pigeon Update & How Does It Affect Local SERPS?
I am genuinely happy to read this webpage posts which consists of
plenty of useful information, thanks for providing
such data.
Instagram hashtags are essentially a means of categorizing and labelling your information. They also help Instagram present your content to people who’re suitable.
In their most straightforward sort the hashtags you end up picking to utilize are The idea for search results over the Investigate page of Instagram:
Nonetheless, it doesn’t halt there. Hashtags can be applied as an indicator to Instagram’s algorithm. Instagram algorithm, meaning it can categorize your articles and recommend that it be proven to buyers it believes is likely being of curiosity.
Then… Are Hashtags nevertheless get the job done in 2022 on Instagram by 2022?
Hashtags happen to be at the middle of discussion specially in light-weight of Instagram’s recent recommendation to utilize three and five hashtags (more on this later on).
As Instagram little by little shifts towards the semantic internet search engine, it opens a completely new realm of possibilities within the internet search engine’s capacity to discover content – that means which the words and phrases you use inside your captions, or even the subjects that you simply include things like in the posts might be searchable also.
On the other hand, Even with these important technological breakthroughs, hashtags continue to perform on Instagram. When paired by using a solid material approach, they could produce amazing results.
Are you all set to down load the whole download of Instagram hashtags?
Take a look at our credit a pic i’m using on my blog from instagram online video information today.
Hi I am so excited I found your website, I really found you by error, while I was searching on Digg for something else, Regardless I am here now
and would just like to say thanks for a remarkable post and a all
round interesting blog (I also love the theme/design), I don’t have
time to go through it all at the moment but
I have book-marked it and also included your RSS feeds, so
when I have time I will be back to read much more, Please do
keep up the great work.
It’s great that you are getting ideas from this article as well as from our argument made
at this place.
my web-site Always Ready XL Reviews
A weekend getaway with two pals turns tragic when considered one of them ends up dead.
Nude
I just couldn’t go away your web site prior to
suggesting that I actually loved the usual info an individual supply on your guests?
Is gonna be back ceaselessly to inspect new posts
That is very fascinating, You’re an excessively skilled blogger.
I’ve joined your feed and look ahead to looking for extra of
your magnificent post. Additionally, I have shared
your web site in my social networks
Do you mind if I quote a few of your posts as
long as I provide credit and sources back to your blog?
My blog is in the exact same area of interest as yours and my users would really benefit from some of the information you provide here.
Please let me know if this ok with you. Many thanks!
São 50 Giros Grátis imediatamente após seu depósito ter sido recebido e outros 40 Giros Grátis ao dia, por 5 dias seguidos.
Check out my page; Pinup Casino
Thanks for the good writeup. It in reality used
to be a entertainment account it. Glance complicated to more added agreeable from you!
However, how could we be in contact?
Feel free to surf to my web blog – KGC Keto Gummies Cost
Magnificent beat ! I wish to apprentice whilst you amend your web site,
how can i subscribe for a weblog site? The account aided me a applicable deal.
I were tiny bit acquainted of this your broadcast provided shiny transparent concept
low does naltrexone naltrexone no prescription how to take low dose naltrexone what is revia used to treat
You will be not really certain what it all indicates, although you could have heard people talking about natural The Sea Beast boxoffice technology.
This informative article can assist you about environmentally friendly energy’s benefits.
Continue reading to learn how green The Sea Beast imdb into your home.
Howdy! I’m at work browsing your blog from my new iphone!
Just wanted to say I love reading your blog and look forward to
all your posts! Keep up the fantastic work!
At this time I am going to ddo my breakfast, later than having myy
breakfast coming again to read more news.
I loved as much as you’ll receive carried out right here. The sketch is attractive, your authored material stylish.
nonetheless, you command get got an impatience over that you wish be delivering the following.
unwell unquestionably come more formerly again as exactly the same nearly a lot
often inside case you shield this hike.
Heya excellent website! Does running a blog like this take a massive amount work?
I have very little understanding of programming however I
had been hoping to start my own blog soon. Anyway, if you have any recommendations
or techniques for new blog owners please share. I know this is off topic however I
just had to ask. Thanks a lot!
Great delivery. Sound arguments. Keep up the amazing spirit.
My brother suggested I might like this website.
He was once entirely right. This submit actually made my day.
You can not believe just how much time I had spent for this information! Thanks!
Hey! I could have sworn I’ve been to this site before but after reading through some of the post I realized it’s new
to me. Anyhow, I’m definitely glad I found it and I’ll be
book-marking and checking back often!
Slot synchronization: This problem is inherent in all slotted a number of entry schemes.
We attribute this to the fact that native slot-aware GAL
can capture the slot dependency for every token, which helps to alleviate the slot uncoordinated issues.
Not only can they cook identical to their parents, but they’re rewarded with tangible, edible fruits of their labor.
Leveraging such hyperlink information between marking-points (nodes) may be beneficial to
correct parking-slot detection. This method enhanced the generalizability of pre-skilled mBERT when high quality-tuning for downstream
tasks of intent detection and slot filling. In recent years, Recurrent Neural Networks (RNNs) primarily based fashions have
been applied to the Slot Filling drawback and achieved the state-of-the-art performances
Mesnil et al. An alternate method to standard IE is slot filling.
As processors grew in pace and bandwidth capability, the business adopted a new commonplace in twin in-line
reminiscence module (DIMM). That was about $2,000
above a V-eight Mustang however solely $200 greater than a
Chevy Corvette — and a bargain by any standard.
Shelby’s hottest undertaking from a sales standpoint was the GT-350, a super-tuned version of the Ford Mustang.
Quality content is the main to attract the people to visit the website, that’s what this site is providing.
When I originally commented I seem to have
clicked on the -Notify me when new comments are added- checkbox and from now on whenever a comment is added I recieve 4
emails with the same comment. Perhaps there is a way you can remove me from that service?
Kudos!
Hi, i believe that i saw you visited my weblog thus i came to return the prefer?.I’m trying to in finding
issues to enhance my website!I assume its good enough to make
use of some of your ideas!!
I really love your site.. Pleasant colors & theme. Did
you build this web site yourself? Please reply back as I’m
attempting to create my very own blog and would
love to find out where you got this from or just what the theme is
named. Thanks!
Oh my goodness! Impressive article dude! Thank you,
However I am having troubles with your RSS. I
don’t know the reason why I can’t subscribe to it.
Is there anyone else getting the same RSS problems? Anybody who knows the solution can you kindly
respond? Thanks!!
Для начала стоит использовать дли регистрации
на форуме ГидраРУ новейший протокол TOR.
Also visit my blog post: pin up aviator
Yesterday, while I was at work, my sister stole my iphone and tested to see
if it can survive a twenty five foot drop, just so she can be a youtube sensation. My apple ipad is now destroyed and she has 83 views.
I know this is entirely off topic but I had
to share it with someone!
kamagra cialis cialis patent in usa effects of cialis on females what does cialis cost
Interesting blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple adjustements would really
make my blog jump out. Please let me know where you
got your design. Thanks
Amazing! This blog looks just like my old one! It’s on a completely different topic but it has pretty
much the same page layout and design. Outstanding choice of colors!
Thank you for sharing your thoughts. I truly appreciate your efforts and I will be waiting for
your next write ups thank you once again.
I have been exploring for a bit for any high-quality articles or
blog posts in this kind of house . Exploring
in Yahoo I finally stumbled upon this website. Reading this information So i am satisfied to express that I have
an incredibly excellent uncanny feeling I found out just what I needed.
I such a lot undoubtedly will make sure to do not forget this site and give
it a glance regularly.
Good day! I know this is kind of off topc but I was wondering
if you knew where I coyld get a captcha pluhgin for my comment form?
I’m using the same blog platform as yours and I’m having difficulty finding one?
Thanks a lot!
Pretty! This was an incredibly wonderful post. Many thanks for providing this information.
Unquestionably imagine that that you stated.
Your favorite reason seemed to be on the internet
the easiest thing to be aware of. I say to you,
I definitely get annoyed whilst other folks consider
concerns that they just do not know about. You managed to hit the nail upon the top as smartly as outlined
out the entire thing without having side-effects , folks can take a signal.
Will probably be back to get more. Thanks
Please let me know if you’re looking for a writer for your blog.
You have some really great posts and I feel I would be a
good asset. If you ever want to take some of the load
off, I’d really like to write some articles for your blog in exchange for a link back to mine.
Please shoot me an email if interested. Cheers!
Hi! I’ve been following your website for a while now and finally got
the courage to go ahead and give you a shout out from Lubbock Texas!
Just wanted to tell you keep up the excellent job!
I have read so many articles about the blogger lovers however
this piece of writing is in fact a pleasant post, keep it up.
Pretty nice post. I just stumbled upon your weblog and wanted to
say that I’ve truly enjoyed browsing your blog posts.
After all I will be subscribing to your rss feed and I hope you write again soon!
This is a topic that is near to my heart… Take care!
Where are your contact details though?
That is very fascinating, You’re an excessively skilled blogger.
I have joined your rss feed and stay up for looking
for extra of your great post. Additionally, I’ve shared your
site in my social networks
Everyone loves what you guys tend to be up too. This kind of clever work and reporting!
Keep up the wonderful works guys I’ve included you guys to our blogroll.
my homepage; ChilWell Portable AC Reviews
If you are going for most excellent contents like me, simply go to
see this web site all the time as it offers feature contents,
thanks
It’s an awesome post designed for all the internet people;
they will get benefit from it I am sure.
Attractive section of content. I just stumbled upon your site and in accession capital to assert that I get
actually enjoyed account your blog posts. Anyway I will be
subscribing to your feeds and even I achievement you access consistently rapidly.
valtrex transmission rate average cost of generic valtrex can you take valacyclovir daily where can i buy generic valtrex
Very nice post. I simply stumbled upon your weblog and wished
to say that I have really loved browsing your blog posts.
In any case I’ll be subscribing in your rss feed and I’m
hoping you write once more soon!
It’s going to be finish of mine day, except before end I
am reading this enormous article to improve my knowledge.
Feel free to surf to my webpage … germany dedicated Servers
Hey There. I found your blog using msn. This is an extremely well written article.
I will make sure to bookmark it and return to read more
of your useful information. Thanks for the post. I
will certainly comeback.
I know this web site offers quality dependent articles or
reviews and extra information, is there any other web site which presents such things in quality?
Simply wish to say your article is as amazing. The clearness in your
post is simply nice and i could assume you’re an expert on this subject.
Well with your permission let me to grab your feed to keep updated with forthcoming post.
Thanks a million and please keep up the gratifying work.
It is denser, adding that little bit of toasted cherry’ishness to it.
Here is my web site :: Josie
Pretty! This was an extremely wonderful article. Thanks for supplying this information.
Good day! This is my 1st comment here so I just wanted to give
a quick shout out and say I genuinely enjoy reading through your blog
posts. Can you recommend any other blogs/websites/forums that cover the same subjects?
Thanks a ton!
Thanks for your marvelous posting! I definitely enjoyed
reading it, you happen to be a great author.I will always bookmark
your blog and may come back in the future.
I want to encourage one to continue your great work, have a nice evening!
plaquenil immune system plaquenil cheapest what is plaquenil supposed to do how long is plaquenil effective after discard date
It’s going to be end of mine day, except before ending I am reading this great paragraph to increase my experience.
Also visit my web blog; Rejuviar Skin Serum Reviews
I am actually glad to glance at this website posts which includes lots of
helpful information, thanks for providing these kinds of information.
What’s up colleagues, its impressive paragraph
about cultureand completely defined, keep it up
all the time.
My web-site … 12bet
Does your blog have a contact page? I’m having trouble locating
it but, I’d like to shoot you an e-mail. I’ve
got some recommendations for your blog you might be interested in hearing.
Either way, great website and I look forward to seeing it expand over time.
Hello to all, how is the whole thing, I think every one is getting more from this web site, and your views are fastidious in favor of new people.
Greetings, I do think your site might be having internet
browser compatibility issues. When I take a look at your web site in Safari, it looks fine however, when opening in I.E., it has some overlapping issues.
I just wanted to give you a quick heads up! Besides that, excellent site!
Stop by my webpage: more information
Hey just wanted to give you a quick heads up.
The words in your article seem to be running off the screen in Opera.
I’m not sure if this is a format issue or something
to do with web browser compatibility but I figured I’d post to let you know.
The layout look great though! Hope you get the issue fixed soon. Thanks
Have you ever thought about creating an ebook or guest authoring on other websites?
I have a blog based upon on the same information you discuss
and would love to have you share some stories/information. I know my subscribers would value your
work. If you’re even remotely interested, feel free to send me an email.
Magnificent beat ! I wish to apprentice while you amend your web site, how can i subscribe for a blog site?
The account helped me a acceptable deal. I had been tiny bit acquainted of this your broadcast offered
bright clear idea
Wonderful blog! I found it while surfing around on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Cheers
お出かけ先でも多くのスロットやスポーツベットを気軽にプレイできるのはもちろん、スポーツベットのライブ観戦もお出かけ先で利用できます。
My web site … bons casino 入金
Үour ѕtyle iis so unique compared to othrr folks Ӏ have read
stuff from. I appreciate уoou for poѕting when you’vе got the opportunity, Guess I willl just book mark this blog.
My wеb page; cctv drain survey horsham
In this case the banker’s cards are turned face up and the hands are compared.
Also visit my web-site – http://beststringtrimmersverdict.com/best-string-trimmers/best-string-trimmer/
If you are going for finest contents like I do, simply
pay a visit this web site all the time because it offers quality contents, thanks
It’s going to be finish of mine day, except before finish I am
reading this impressive paragraph to increase my knowledge.
Excellent blog right here! Additionally your site rather a lot up
very fast! What web host are you using? Can I am getting your associate hyperlink in your host?
I desire my website loaded up as fast as yours lol
Like Pitt, Sandra Bullock has an illustrious movie profession with movies followers have
been watching on repeat, together with her most up-to-date function in The Lost City.
This is a topic which is close to my heart… Take care! Exactly where are your contact details
though?
I am really happy to glance at this web site posts which contains lots
of helpful data, thanks for providing these kinds of information.
Ꮋi, I do think this is an excellent web site. I stumbledupon іit 😉 I may come back yet againn sіnce i have boоk-markеd it.
Money and freedom is the greatest way to change, mаy yyou be rich and continbue to help others.
Here is my web pag :: drain repairs west bromwich
Je n’était qu’un simple étudiant аu baccalauréat.
Howdy! This article couldn’t be written any better! Looking through this post reminds me of my previous roommate!
He constantly kept talking about this. I most certainly
will send this article to him. Fairly certain he’s going to have a
great read. Thank you for sharing!
cialis viagra cialis bathtub best online pharmacy for cialis when to take viagra
Hello! Would you mind if I share your blog with my myspace group?
There’s a lot of people that I think would really appreciate your content.
Please let me know. Many thanks
Great blog here! Also your website loads up very fast! What host are you using?
Can I get your affiliate link to your host? I wish
my site loaded up as quickly as yours lol
What’s up, its good post regarding media print, we all know media is a
wonderful source of data.
подъемник телескопический
https://www.podyemniki-machtovyye-teleskopicheskiye.ru/
Heⅼlo to every boⅾy, it’s my first goo to
see of this web site; this website includes remarkable and
reaⅼly gooԀ data in favor of readers.
my webpage blocked drains new forest
I have recently started a web site, the info you offer
on this website has helped me tremendously. Thanks for all of your time & work.
Also visit my blog post … Viralix CBD Oil
If you happen to be going to vary your bet size, improve
it when winning and bring it down when losing.
my website; baccarat Crystal
hеllo!,I like yoᥙr writing very much! peercentage we
keep in toᥙch extra approximately your post oon AOL? I
reգuire a specialist on thioѕ house to resoⅼve
my proƄlem. May be that is you! Taking
a look ahead to peer you.
my webѕite :: rdmsrc
It has been in operation for about 5 years across Europe and Asia.
My page … pin up india
Hi it’s me, I am also visiting this site daily, this website is in fact good and the users are in fact
sharing pleasant thoughts.
подъемник мачтовый
https://podyemniki-machtovyye-teleskopicheskiye.ru
R.E.M. gives you a lot of what Cloud has to supply, but adding fig and lavender to make it stand on its personal merit.
Also visit my homepage: Baccarat Hotel
viagra side viagra vs cialis vs levitra usa how to take kamagra oral jelly where can i buy generic levitra
Baccarat Rouge 540 is a well-liked perfume by Maison Francis Kurkdjian for
females and men and was released in 2017.
Have a look at my web page: Rudolph
Appreciate this post. Will try it out.
I do trust all of the ideas you’ve introduced in your post.
They are really convincing and will certainly work.
Still, the posts are very short for novices. Could you please prolong them a bit from next time?
Thank you for the post.
My website :: Vitrinex Review
I for all time emailed this blog post page to all my friends,
since if like to read it next my contacts will too.
Review my site Derma ProX Cream
мачтовый подъемник
https://www.podyemniki-machtovyye-teleskopicheskiye.ru/
Hey there, You have done a fantastic job.
I’ll definitely digg it and personally recommend to my friends.
I am confident they will be benefited from this website.
Wonderful work! That is the kind of info that are supposed to be shared across the internet.
Shame on the search engines for no longer positioning this post higher!
Come on over and talk over with my site . Thank you =)
I don’t even know how I ended up here, but I believed this
post was great. I do not recognize who you’re but
definitely you’re going to a well-known blogger should you are not already.
Cheers!
Howdy! Would you mind if I share your blog with my twitter group?
There’s a lot of folks that I think would really enjoy your content.
Please let me know. Many thanks
Hey I know this is off topic but I was wondering if you knew
of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you
would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog
and I look forward to your new updates.
I’m very pleased to uncover this web site.
I wanted to thank you for your time for this wonderful read!!
I definitely liked every bit of it and i also have you saved to
fav to check out new things on your web site.
That said, one thing you can’t find at any legitimate CA online casino is free online keno with real-money payouts. While nearly every top operator lets players enjoy free online video keno games for practice or for fun, if you want to win actual cash, you’re going to have to make a deposit and play for keeps. We’ve taken every detail into consideration when designing our online casino, ensuring that you can enjoy a world-class Keno experience from the comfort of your computer. Whether you’re a devoted PC player or you prefer your Apple Mac, our Spin Palace Casino software is fully optimised for your computer of choice. Please enable Cookies and reload the page. If you want to play keno while sitting still, we recommend finding a brick-and-mortar Vegas casino for that. However, if you want to play keno on the go – and you know you do! – you’re probably going to look for online keno apps in the App Store or Google Play. https://www.icitp.org.za/it_forum/profile/ffuhalley788852/ If you’re a fellow crypto gambler, you might be wondering where to find the best Bitcoin casinos. Any game on a slot machine will be completely random, just like tossing coins. The computer program that controls the game selects a random symbol on the first row, then the second. Payback is the percentage of money paid back to the player on average. Each spin on the game has the same chance of winning or losing as the previous game; it has nothing to say how long since the last jackpot was paid out or whether the slot machine is “hot” or “cold.” Any game on a slot machine will be completely random, just like tossing coins. The computer program that controls the game selects a random symbol on the first row, then the second. Payback is the percentage of money paid back to the player on average. Each spin on the game has the same chance of winning or losing as the previous game; it has nothing to say how long since the last jackpot was paid out or whether the slot machine is “hot” or “cold.”
Do you mind if I quote a couple of your articles as long
as I provide credit and sources back to your blog?
My blog site is in the exact same area of interest as yours and my visitors would really benefit from a lot of the information you present here.
Please let me know if this alright with you. Thank
you!
I am curious to find out what blog system you have been utilizing?
I’m experiencing some minor security problems with my latest blog
and I would like to find something more risk-free.
Do you have any suggestions?
I like the valuable info you provide in your articles.
I will bookmark your weblog and check again here
frequently. I am quite certain I will learn many new stuff right here!
Best of luck for the next!
Hi, yup this post is truly pleasant and I have learned lot of things
from it on the topic of blogging. thanks.
Quality articles or reviews is the crucial to interest the visitors to pay
a quick visit the website, that’s what this site is providing.
Helpful information. Lucky me I discovered your web site by chance, and I
am shocked why this accident did not came about earlier!
I bookmarked it.
Now you should know a little more about adding natural technological innovation into
your life. Consider a few of these suggestions and make use of these to create some of
your very own environmentally friendly Minions: The Rise of Gru film!
May also save on your month to month bills, while
you is not going to only help the environment by preserving electric power.
Great weblog right here! Additionally your website quite a bit up fast!
What host are you using? Can I get your associate link for your host?
I wish my site loaded up as quickly as yours lol
Hey just wanted to give you a brief heads up and let you know a few of the images
aren’t loading properly. I’m not sure why but I think its a
linking issue. I’ve tried it in two different web browsers and both
show the same outcome.
Just desire to say your article is as astounding. The clearness on your publish is just excellent and that i could think you’re a professional in this subject.
Fine along with your permission let me to grasp your feed to keep
up to date with approaching post. Thanks 1,000,000 and please continue the rewarding work.
Hello my friend! I want to say that this article is amazing,
great written and include approximately all significant infos.
I would like to see more posts like this .
First of all I would like to say excellent blog! I had a quick question in which I’d like to
ask if you do not mind. I was curious to know
how you center yourself and clear your thoughts before writing.
I’ve had trouble clearing my thoughts in getting my ideas
out there. I truly do enjoy writing but it just seems
like the first 10 to 15 minutes are lost
just trying to figure out how to begin. Any suggestions or tips?
Many thanks!
Hmm is anyone else having problems with the images on this blog loading?
I’m trying to figure out if its a problem on my end or if it’s the blog.
Any feed-back would be greatly appreciated.
At this time it looks like Movable Type is the preferred
blogging platform available right now. (from what I’ve read) Is that what you’re using on your blog?
fantastiⅽ submit, very informative. I ponder wһy the oppоsite experfs of this sector Ԁоn’t notice this.
Yoou should proceed your writing. Ι amm sure, you have a huge readers’
base already!
Review mmy page; blocked drains ash
I trսⅼʏ love your site.. Ԍresat colorѕ & theme. Did you create this amazing site yourself?
Plеasе reply back aaѕ I’m lookking to create my own bⅼog
and would love to leaarn where you got this from or what the themе is named.
Thank you!
Feel free too suгf to mmy web-sіte :: blocked drains bracknell
Hello it’s me, I am also visiting this site regularly, this site is in fact pleasant and the visitors are genuinely sharing fastidious thoughts.
I am regular visitor, how are you everybody?
This paragraph posted at this website is actually fastidious.
my web-site ทวิตเตอร์ (football-club.top)
I was suggested this blog by my cousin. I’m not sure whether
this post is written by him as no one else know such detailed about my
problem. You’re wonderful! Thanks!
PayNearMe is a money bill spend choice available at some retailers.
Viszit my website – turning stone online casino (Rafael)
It’s great that you are getting ideas from this paragraph as
well as from our dialogue made at this time.
Hi there exceptional blog! Does running a blog such as this require a lot of work?
I have virtually no expertise in coding however I
was hoping to start my own blog in the near future.
Anyways, should you have any recommendations or
techniques for new blog owners please share.
I understand this is off subject nevertheless
I just wanted to ask. Many thanks!
As the admin of this web page is working, no hesitation very rapidly it will be renowned, due to its quality contents.
magnifiсent submit, very informative. I’m wondering why thee
opρosite experts of this sеctor do not ᥙnderstand this.
You must continuе yоur writing. I’m ѕure, you have a
great readerѕ’ base already!
mү website: trafalgar cli ic
This is my first time pay a visit at here and i am
actually pleassant to read all at single place.
Its like you read my mind! You appear to know so much about this, like you
wrote the guide in it or something. I think that you can do with some
p.c. to pressure the message house a bit, however instead of that, that is great blog.
A fantastic read. I’ll definitely be back.
Also visit my page :: fishing boat for s
Yesterday, while I was at work, my sister stole my iphone and tested to
see if it can survive a twenty five foot drop, just so she can be a youtube sensation. My iPad
is now broken and she has 83 views. I know this is entirely
off topic but I had to share it with someone!
Why users still use to read news papers when in this technological world everything is
presented on web?
Vеry nice pоst. I just stuumbled upon your weblog and wіshed to say that I’vereally
enjoyed browsing your blog рosts. After all I will
be sսbscribing to your feeɗ and I hope yyou write again soon!
my blog nasherts
I could not resist commenting. Very well written!
What’s up, of course this paragraph is in fact fastidious and
I have learned lot of things from it regarding blogging.
thanks.
Fantastic website you have here but I was curious about if
you knew of any user discussion forums that cover the same topics talked
about here? I’d really like to be a part of group
where I can get opinions from other knowledgeable people that share the same interest.
If you have any suggestions, please let me know.
Cheers!
of course like your web-site however you need to check the spelling
on several of your posts. A number of them are rife with spelling problems and I to find it very bothersome to tell
the truth however I’ll certainly come back again.
Pretty! This has been an extremely wonderful article. Thanks for
supplying this info.
It’s actually a nice and useful piece of info.
I am happy that you simply shared this helpful information with us.
Please keep us up to date like this. Thank you for sharing.
Touche. Outstanding arguments. Keep up the
great effort.
my page – pressure washer rental new orleans
Just want to say your article is as astounding. The clearness
in your post is just cool and i can assume you are an expert on this subject.
Fine with your permission allow me to grab your RSS feed to keep updated with forthcoming post.
Thanks a million and please carry on the enjoyable work.
I must thank you for the efforts you’ve put in writing this blog.
I really hope to checxk out the same high-grade conent bby you laterr on as well.
In truth, your creative writing abilities has motivated me tto get my own site
now 😉
Check out my page: gay forum
Pгetty! This һaѕ been a realⅼy wonderful ɑrticle.
Thank yoou for providing these details.
my blog – drainage salisbury
Excellent, what a weblog it is! This weblog gives valuable data
to us, keep it up.
Thankfulness to my father who told me about this website, this web site is in fact awesome.
Research your brand new Laal Singh Chaddha update before starting
it. Not all Laal Singh Chaddha is the same for yourself.
Some include creativity, a few will demand exercising, most will need creativity.
excellent publish, very informative. I ponder why the opposite specialists of this sector do
not understand this. You must proceed your writing. I am
confident, you have a huge readers’ base already!
I feel this is among the most vital information for me.
And i’m happy reading your article. However should observation on some normal things, The website taste is ideal,
the articles is really nice : D. Excellent process, cheers
If some one needs to be updated with most up-to-date technologies after
that he must be pay a quick visit this web site and be up to date all
the time.
If yоu would like to take a great deal frpm tyis article then you have to appy thesae
techniques to youг won web site.
Take a look at my web blog: my blog
Yes! Finally someone writes about backflip maniac.
Everyone loves it when folks come together and share ideas.
Great website, stick with it!
At this time I am going to do my breakfast, once having my breakfast coming yet again to read other news.
Wow that was odd. I just wrote an very long comment but after I
clicked submit my comment didn’t show up. Grrrr…
well I’m not writing all that over again. Regardless,
just wanted to say excellent blog!
It’s awesome to pay a visit this web page and reading the views
of all friends concerning this article, while I am also zealous of getting experience.
Thanks fоr the marvelous pоsting!I really enjoyed гeading it, you can be a greɑt аuthor.I
will alѡays bookmark y᧐ur blog аnd wilⅼ eventuallу come
back in the future. I want to encouraɡe yourself to сontinue your greaat writing,
have a nice day!
my homepage – blocked drains somerton
Ηello, I enjoy rеadxing all of your article. I wanted to
writе a little comment to ѕupport you.
Also ѵisit mʏ blog; jdesteelfabrications.co.uk
Hi my friend! I want to say that this post is amazing, nice written and include approximately all significant infos.
I’d like to peer more posts like this .
Vermogen moet worden opgegeven in box 3.
I know this website gives quality dependent content and
extra information, is there any other web site which presents such stuff in quality?
You’re so cool! I don’t suppose I have read through a single thing like that before.
So good to discover someone with a few genuine thoughts
on this topic. Seriously.. many thanks for starting this up.
This web site is something that is needed on the internet,
someone with a bit of originality!
boot mieten phuket https://eurosegeln.com/yachtcharter-thailand
вышка телескопическая
http://podyemniki-machtovyye-teleskopicheskiye.ru/
I do trust all the ideas you have presented for your post.
They are very convincing and can definitely work.
Nonetheless, the posts are very short for
starters. Could you please lengthen them a bit from next time?
Thanks for the post.
These can be used to signal up to sites and bypass identity/verification checks.
Some web sites have further checks in place and can verify
with the issuer towards the main points you’ve provided, so it could not always work.
We believe acquiring such sensitive finanacial details wont be wanted.
Giving up such details is like giving up your privateness to website owners that
you do not actually want to buy from. Credit card generated from this website
do not work like an precise credit card these playing cards are
simply for knowledge testing and or verification functions they don’t have
an precise actual world value. All the credit cards generated utilizing credit card
generator are legitimate but they do not possess any actual worth
as you cannot use them for making any monetary transactions.
Our card details are randomly generated utilizing the Luhn algorithm.
All actual credit cards follow this algorithm, they have mounted prefixes and can be easily recognized (i.e VISA playing cards all the
time start with a ‘4’). If you need to be taught more about how the Luhn checksum
formulation works then check out an indepth breakdown. To strive our software, merely choose your card type from above and
click on on the ‘Generate’ button. The different reason we made this are programmers testing ecommerce web sites, functions or other software program.
They may be validated utilizing a checksum called the Luhn Algorithm.
Our Credit Card Number Validator checks the inputted number towards the Luhn checksum and informs you if it’s valid or not.
Free bank card validation software – simply paste in a credit card
number and our software will verify the validity and card kind.
IIN number identifies the card issuing establishment that issued the card to the cardholder.
For higher understanding of MII please hover to the detailed desk beneath.
The bank card or debit card numbers generated on this web page are
the legitimate card numbers however fully random or in another word, it’s merely pretend.
A valid bank card number (also known as Primary Account Number – PAN) has several fields and
each of them has a that means. For the technically inclined, this quantity
complies to the ISO/IEC 7812 numbering commonplace.
An incorporates a six-digit issuer identification number ,
a person account identification quantity, and a single digit
checksum. MasterCard bank card numbers generator is used to generate a valid credit card numbers with complete safety
details.
Now let’s see what you should do when you come throughout such a
card. Each card number, whether or not belonging to MasterCard
or to another funds firm, begins with an issuer identification quantity ,
which is always six-digit long. As its name implies, the IIN is used to
establish the card issuer who’s issuing its playing cards through a card community (e.g.
MasterCard or Visa).
Using a credit card generator lets you create trial accounts for websites
and never be apprehensive about dropping money as quickly as
the trial period expires. There are some customers who attempt to sport the system by constantly creating new trial accounts with dummy card details.
This means their trial interval by no means runs out and so
they get to use a web sites service for free.
This is a potential state of affairs however it is vehemently in opposition to our TOS we’ll block any customers abusing our
free platform. If an web site catches you abusing their trial account system then anticipate your accounts to be terminated and being permanently
blocked.
What do we imply by legitimate – is that they are created with the same number formulation which is the mod-10
or modulus 10 algorithm to create a valid bank
card quantity. No, credit card particulars generated
from VCCGenerator are only for testing purposes.
Do not use these fake bank card numbers to make any buy.
Any buy wouldn’t be accomplished either because the numbers do not include
a valid expiration date, card holder’s name, and CVV numbers.
Note that what we are offering are random bank card particulars.
With one click on, you probably can generate card quantity up
to 09 real credit card numbers. A valid credit card quantity may be simply generated using bank card generator by assigning totally different quantity
prefixes for all bank card firms. For Example quantity four for
Visa credit cards, 5 for MasterCard, 6 for Discover Card, 34 and
37 for American Express and 35 for JCB Cards.
————-CONTACT———————–
WEBSITE : >>>>>>Validcc✶ Site
—– HERE COMES THE PRICE LIST ———–
***** CCV US:
– US MASTER CARD = $2,1 per 1 (buy >5 with price $3 per 1).
– US VISA CARD = $2,5 per 1 (buy >5 with price $2.5 per
1).
– US AMEX CARD = $5 per 1 (buy >5 with price $2.5 per 1).
– US DISCOVER CARD = $3 per 1 (buy >5 with price $3.5 per
1).
– US CARD WITH DOB = $15 per 1 (buy >5 with price $12 per 1).
– US FULLZ INFO = $40 per 1 (buy >10 with price $30 per
1).
***** CCV UK:
– UK CARD NORMAL = $2,9 per 1 (buy >5 with price $3
per 1).
– UK MASTER CARD = $2,9 per 1 (buy >5 with price $2.5 per 1).
– UK VISA CARD = $2,9 per 1 (buy >5 with price $2.5 per 1).
– UK AMEX CARD = $3,8 per 1 (buy >5 with price $4
per 1).
$4,8
– UK CARD WITH DOB = $15 per 1 (buy >5 with price $14 per 1).
– UK WITH BIN = $10 per 1 (buy >5 with price $9 per 1).
– UK WITH BIN WITH DOB = $25 per 1 (buy >20 with price $22
per 1).
– UK FULLZ INFO = $40 per 1 (buy >10 with price $35 per 1).
***** CCV AU:
– AU MASTER CARD = $5.5 per 1 (buy >5 with price $5 per 1).
– AU VISA CARD = $5.5 per 1 (buy >5 with price $5 per 1).
– AU AMEX CARD = $8.5 per 1 (buy >5 with price $8 per 1).
– AU DISCOVER CARD = $8.5 per 1 (buy >5 with price $8 per 1).
***** CCV CA:
– CA MASTER CARD = $6 per 1 (buy >5 with price $5
per 1).
– CA VISA CARD = $6 per 1 (buy >5 with price $5 per 1).
– CA VISA BUSINESS = $14 per 1 (buy >5 with price $13 per 1).
Dragon Ball Super Super Hero have moved past the point
of being a kids’ pastime, so not every game is protected for all ages.
Boosting your model affinity is a step up after visibility and engagement.
Have a look at my homepage how to promote your business on social media
(Grazyna)
At this moment I am going to do my breakfast, once having my breakfast coming
yet again to read other news.
Write more, thats all I have to say. Literally,
it seems as though you relied on the video to make your point.
You definitely know what youre talking about, why throw away your intelligence on just
posting videos to your weblog when you could be giving us something enlightening to read?
Superb, what a web site it is! This weblog provides valuable information to us,
keep it up.
I’m gone to inform my little brother, that he should also
pay a visit this webpage on regular basis to get updated from latest news.
dfg
Good day I am so glad I found your blog, I really found you by mistake, while I was looking on Bing for something else, Regardless I am here now and
would just like to say kudos for a marvelous post
and a all round interesting blog (I also love the
theme/design), I don’t have time to read through it all at the moment but I have saved it and also added in your RSS feeds, so
when I have time I will be back to read a great deal more, Please do
keep up the fantastic work.
This is a superb story concerning the love and worth of
family.
Good post but I was wondering if you could write a litte more on this subject?
I’d be very grateful if you could elaborate a little bit further.
Appreciate it!
I was suggested this blog by my cousin. I’m not sure whether this post is written by him
as nobody else know such detailed about my trouble. You’re amazing!
Thanks!
Ӏ like ᴡhat you guys tend too bе up too. This type of clever work aand coveraցe!
Keep up thhe superƅ workѕ guys I’ve added y᧐u guys to my own blogroll.
My page; educational supplies
Greetings! I know thiѕ is kinda off toрic however ,
I’d figured I’d ask. Would yoս be interested in exchɑnging links or mwybe guest authpring a
blog article ᧐r vice-versa? My blog goes over a ⅼot of tһe same tolics as yours and I feeel we could greatly benefit from
each other. If you’re interested feel free to shoot me an email.
I look forward to hearing from yⲟu! Fantastic blog by the way!
Also visit my website firming eye cream
I’m very happy to uncover this site. I want to to thank you for ones time due too
this wonderful read!! I definitely enjoyed
every bit of it and i also have you book marked tto see new information on your site.
Also visit my web-site: køb viagra fra europa
Very soon this web page will be famous among all blog visitors,
due to it’s nice posts
It’s remarkable designed for mme to have a
web site, which is valuable in support of my experience.
thanks admin
This post is really a nice one it assists new web users, who are wishing for blogging.
Hello friends, good paragraph and pleasant urging commented at this place, I am actually enjoying by these.
My famіly membrs aall thhe time say that I am wɑsting my time here at web, but I know Ι am
getting knowledge aⅼl the time by reading thes pleasɑnt articles.
My web blog; drainage services high wycombe
Nice blog here! Also your website loads up very fast!
What host are you the usage of? Can I am getting your associate hyperlink in your
host? I desire my website loaded up as quickly as
yours lol
urologo disfuncion erectil cialis generico disfuncion erectil edad
I think this is one of the most vital information for me.
And i am glad reading your article. But should remark on some general things, The web site style is wonderful, the
articles is really great : D. Good job, cheers
When the World Cup is over The พรีเมียร์ลีกวันนี้ Premier League will begin again. and the competition will be intense Blood is added to the center. Finally this season must start
round of the ICU compared to the game in May เชลซีสด West Ham lineup There is only one change in support.
the trident and Van Dijk is rarely pointed แมนยูล่าสุด out. By Mitrovic after the first round, Liverpool’s midfield which has more wounded soldiers Causing
but is talent Because the giants at the top There is no shortage of transfer fees. But the top talent was only counted แมนฯ ยูไนเต็ด on one finger. Even Cristiano Ronaldo, 37, cannot afford Manchester United.
Due to Luke Shaw’s presence, he had to ฟุตบอลเยอรมัน compensate for the gap behind him. Solskhar’s implementation provided the answer. is to squat in the support
who recently joined Sancho. who have yet to แมนยูวันนี้ adapt to the Premier League and a DJ who burned himself to maintain balance of attacks and protection
always i used to read smaller articles or reviews that also clear
their motive, and that is also happening with this article which I am
reading at this time.
I am not very great with English but I find this really leisurely to interpret.
Also visit my web site; Pureganics CBD Gummies Cost
If some one wants to be updated with most up-to-date technologies after that he must be pay a quick visit this web
site and be up to date everyday.
It’s very trouble-free to find out any matter on net as compared to books, as I found this post at this website.
gffx188,https://www.gffx188.com/
Hey I know this is off topic but I was wondering if you knew
of any widgets I could add to my blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you
would have some experience with something like this. Please let
me know if you run into anything. I truly enjoy reading your blog and I look forward to your new updates.
I simply could not leave your site before suggesting that
I extremely enjoyed the standard information an individual provide on your visitors?
Is going to be again steadily to check out new posts
Admiring the time and energy you put into your blog and in depth information you provide.
It’s good to come across a blog every once in a while that isn’t
the same out of date rehashed information. Excellent read!
I’ve bookmarked your site and I’m adding your RSS feeds to my Google
account.
Simply wish to say your article is as astounding. The clearness in your post is just cool and i can assume you’re an expert on this subject.
Fine with your permission let me to grab your RSS feed to keep updated
with forthcoming post. Thanks a million and please
carry on the enjoyable work.
whoah this weblog is fantastic i really like reading your articles.
Stay up the good work! You understand, a lot of individuals are
hunting round for this information, you can help them greatly.
Hi there i am kavin, its my first occasion to commenting anyplace, when i read this post i thought i could also make
comment due to this sensible piece of writing.
What’s up to every single one, it’s actually a fastidious for me to go
to see this website, it includes precious Information.
Limit your Dragon Ball Super Super Hero playing to several hours every
day. Playing Dragon Ball Super can be addictive, that may impact your
self confidence. You shouldn’t be gaming for more than a handful of
hours daily. In the event you keep gaming beyond
that period of time, ensure you take a rest at least one time per three hours.
Second, Juventus lost to Tevez, Vidal and Pirlo this summer after their core players were very unstable. Pogba เชลซีล่าสุด doesn’t want to leave the team.
What’s up Dear, are you genuinely visiting this web page on a regular basis, if so after that you will without doubt
get nice knowledge.
What he did was even more incredible. ทีมเรอัลมาดริด everything he does on the field Including his goals, amazing.
and 2 draws at Porto, bringing Chelsea 46 wins, 14 draws, and Inter Milan have 29 wins, 9 draws and 14 consecutive ยูเวนตุสสด wins at Barcelona. Real Madrid at home 125 wins and 25 draws
Mourinho is unbeaten in 60 Premier League สถิติแมนยู home games, with a record 46 wins and 14 draws. In the summer of 2013, he returned to Chelsea
Mallorca takes a free-kick. And he missed the ทีมเชลซี goal. In the 20th minute Vinicius was fouled. when he countered in the front
of second-placed Sevilla and hopes of winning the บอลแมนยู title are high. However, in the next round of the league Real Madrid will face former rivals Barcelona at home
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your website to come back down the road.
Many thanks
Hello to all, the contents present at this web page are truly amazing for people
experience, well, keep up the good work fellows.
Attractive section of content. I just stumbled upon your web site and in accession capital to assert that I
get actually enjoyed account your blog posts.
Anyway I’ll be subscribing to your augment and even I
achievement you access consistently rapidly.
Woah! I’m really enjoying the template/theme of this blog.
It’s simple, yet effective. A lot of times it’s very difficult to get
that “perfect balance” between superb usability and visual
appearance. I must say you have done a great job with
this. In addition, the blog loads very fast for me on Internet explorer.
Outstanding Blog!
This is really attention-grabbing, You’re a very skilled blogger.
I’ve joined your rss feed and look forward to in search of extra of your fantastic post.
Additionally, I’ve shared your web site in my social networks
http://peschanoe.co.ua/
Hi there! I could have sworn I’ve been to this blog before but after browsing through some
of the post I realized it’s new to me. Nonetheless,
I’m definitely delighted I found it and I’ll be bookmarking and checking back frequently!
If a screenplay goes to be fixated on the historical past and
purpose of storytelling, the stories within it have to be better.
I am really pleased to glance at this blog posts which carries
lots of helpful facts, thanks for providing such information.
This is my first time go to see at here and i am really pleassant
to read everthing at one place.
Hurrah! At ⅼast I got a website frrom wһerе I know how to actually get helpful facts regarding my studу and knowledge.
Lоok into my ѕite :: blocked drains tadley
I am гealⅼy loving tthe theme/design of your weblog.
Do you ever rսn into any browser compatibility issues?
A smaⅼl number of my blog visitors have complained about my website not operating correctly in Eҳplorеr but looкs geat in Chrome.
Ⅾo you have any tips to help fix thіs issuе?
Here is my blog … school washroom refurbishment
My brother recommended I might like this web site.
He was totally right. This post truly made my day. You can not imagine just how much time I had spent
for this info! Thanks!
Great beat ! I wish to apprentice while you amend your website, how could i subscribe for a weblog website?
The account helped me a applicable deal. I had been a little
bit acquainted of this your broadcast offered vibrant transparent idea
I’m not that much of a internet reader to be honest but your blogs really nice,
keep it up! I’ll go ahead and bookmark your website to
come back down the road. Many thanks
because it contradicts Bayern’s tactical manutd philosophy The form of giants of the Ronaldo family is inconsistent.
at the beginning of this month He received a manchester united six figure bonus from Manchester United. from fulfilling his 2nd year contract Ronaldo returned to Manchester United
But its presence has given Ronaldo an extra ฟุตบอลเยอรมัน income. Today, many have questioned the timing of Cristiano Ronaldo’s departure, believing he intentionally undermined
It will take 16 days in total during that time. La Albiceleste Manchester United will play four warm-up games, originally should Ronaldo return to the squad on Monday.
According to British media reports Chelsea are ทีมเยอรมัน seriously considering launching Ronaldo. And they are ready to make an offer of £14m.
It was impossible for him to play. In the Europa League, Cristiano Ronaldo really wanted to leave. We can’t blame him on The Gunners anything. He made a huge contribution
There was no minimum wage and attendance bonuses have been lost on the initial
day of an absence.
Feel free to visit my webpage: Melisa
Article writing is also a fun, if you be acquainted with then you can write
otherwise it is complex to write.
Appгeciate tһe recommendаtіon. Wіll try it out.
my web ѕite: uk cic
This paragraph is truly a nice one it helps new the web people, who are
wishing in favor of blogging.
Hi there! I know this is kinda off topic but I’d figured I’d
ask. Would you be interested in trading links or maybe guest writing a blog post or
vice-versa? My site goes over a lot of the same subjects as yours
and I think we could greatly benefit from each other. If you happen to
be interested feel free to send me an e-mail.
I look forward to hearing from you! Terrific blog by the way!
I’m extremely pleased to find this web site.
I wanted to thank you for ones time just for this fantastic read!!
I definitely liked every part of it and I have you saved to fav to see new
stuff in your website.
Thanks very interesting blog!
Klik sekali, kemudian selesaikan pengunduhan & pasang ke HP android atau iphone kamu lekas.
Cara login wm live casino apk terbaru, anda cuma cukup klik sekali hingga tampilan depannya keluar.
my page – slot bayar pakai shopeepay
Kroos became the first to be substituted. In the อาร์เซนอลสด midfield of the ceremony again The German player expressed his dissatisfaction at that moment.
is based on Choosing Atletico Madrid’s center, ทีมอาร์เจนตินา Pre Morata in his squad will begin. It seems that Atletico Madrid will draw some players
Benzema this season doesn’t seem to have a เชลซีสด replacement, which is annoying. See the performance of the youth of the team in the first round.
Every weekend i used to pay a visit this website, because
i wish for enjoyment, since this this website conations actually pleasant funny
data too.
What’s up i am kavin, its my first time to commenting
anywhere, when i read this piece of writing i thought i could also make comment due to this sensible paragraph.
However, Ballack had to announce his เรอัลมาดริดล่าสุด withdrawal. Before the World Cup Due to injury in the FA Cup final Watching teammates destroy Maradona’s team
Kroos scored twice in Germany’s 4-0 win over บอลเนเธอร์แลนด์ Argentina to boost his World Cup goals to 14. He is one step away from Ronaldinho’s record of 15
in the quarterfinals They beat Argentina 4 to 0, now Germany became the most champ looking team. Discuss the อาร์เซนอลวันนี้ reason why the team beat Argentina.
Incredible! This blog looks just like my old one!
It’s on a entirely different subject but it has pretty much the same page layout and design.
Outstanding choice of colors!
It’s going to be ending of mine day, except before finish I am
reading this wonderful article to increase my knowledge.
Peculiar article, exactly what I wanted to find.
Sports betting, football betting, cricket betting, euroleague football betting,
aviator games, aviator games money – first
deposit bonus up to 500 euros.Sign up bonus
I don’t know if it’s just me or if perhaps everyone
else experiencing problems with your site. It seems like some of
the text on your content are running off the screen. Can someone else
please provide feedback and let me know if this is happening to them too?
This could be a issue with my browser because I’ve had this happen previously.
Thank you
Highly energetic blog, I enjoyed that bit. Will
there be a part 2?
This role is responsible for coding and abstracting information from patient healthcare records such as inpatient,…
Here is my page :: Blanche
I am sure this post has touched all the internet people,
its really really pleasant post on building up new
web site.
naturally like your web site but you need to check the spelling on several
of your posts. A number of them are rife with spelling
problems and I find it very bothersome to tell the reality
however I will certainly come back again.
Hey there! Do you know if they make any plugins to
help with SEO? I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good results.
If you know of any please share. Thanks!
Hi there! Do you use Twitter? I’d like to follow you if that would be ok.
I’m undoubtedly enjoying your blog and look forward to new updates.
Let’s strive to gather game play tips with out spoiling the
story a lot. Computer and videogames also receive far more unfavorable critics as a result of video games are often coined with problem comparable to senseless leisure,
enhanced social recluse, sexism and consumerism. Playing
online video games is so way more completely different than enjoying video games in a single participant mode where your
only problem is to beat the computer. Today, one can see the impact of pc
and video games in politics, tv, in style music, and Hollywood.
Research exhibits that youngsters who play violent video video games confirmed an increase in emotional arousal – and a corresponding decrease of activity in brain areas involving self-control, inhibition and
a focus. That very same impact was not present in the kids who played non-violent.
There was a research performed on a bunch of youngsters
the place two action video games had been included the first game was the excessive-octane but non-violent racing different was the extremely-violent.
But even in the game itself, there are no clear rules established at
the outset of how Dracula’s resurrection may work. The cities throughout the 225 sq.-kilometres of Chernarus may be
scorching spots for participant-versus-player fight,
however out in the encompassing countryside, zombies are the main risk.
Now, a virus might defeat the perfect traps laid by humankind,
but does it stand an opportunity in opposition to something ordained by the Creator?
you’re really a good webmaster. The website loading pace is incredible.
It sort of feels that you are doing any unique trick.
In addition, The contents are masterwork. you have performed
a magnificent process on this matter!
dribbled to the right of the box and made a pass. บุนเดสลีกา3 Martinelli headed and fired in the 35th minute. Seba’s midfield. Yos was withdrawn from the game
Harrison and the Marquis of Arsenal use a 4231 tactics เรอัลมาดริดวันนี้ format. The lineup for this match is Mar. Tinez, Papastathopoulos, David Luis, Mali, Saka
The team has lost just one financial loss for the first Los Colchoneros time since 2002 and this has been associated with losses from transfers and the Europa League
Next season Arsenal are likely to miss out on the อาร์เซนอลสด Champions League for a fourth season in a row, which will seriously affect the club’s future.
It will be very easy to introduce new players and renew players. Everyone knows we want to play in the Champions League. ฟุตบอลอาร์เซนอล But if we can’t play in the Champions League We have to think otherwise.
As of January 1, 2020, Arsenal have played in a อาร์เซนอลสด total of 7 league games, winning 3, drawing 4: Manchester United 2-0 Crystal Palace 1-1 Sheffield United 1-1
Everything is very open with a very clear explanation of the issues.
It was really informative. Your site is extremely helpful.
Thanks for sharing!
parx Гјcretsiz online casino
‘T Vanille’ Inspired by Tobacco Vanille by Tom Ford opens with notes of tobacco
leaf and aromatic spices, blending into heart notes of tonka bean, tobacco flower, vanilla and cocoa, finishing with sweet fruit…
Review my site Florida
Genuinely no matter if someone doesn’t know then its up to other viewers that they will assist,
so here it happens.
Medieval perform an integral part in growing your child’s mind.
There is no denying the massive effect that wonderful Medieval can have.
These suggestions may help any person seeking fantastic
Medieval box office.
The job application is not tougher, it’s just a bit distinct.
Feel free to surf to my web blog :: Graciela
No matter which nurse practitioner career choices interest you,
part-time job at A bar development looks
powerful.
This is a really good tip especially to those new
to the blogosphere. Simple but very accurate info… Many thanks for sharing this one.
A must read article!
We are a group of volunteers and opening a new scheme in our community.
Your website offered us with valuable info to work on.
You’ve done a formidable job and our whole community will be thankful to
you.
An interesting discussion is definitely worth comment.
I believe that you should write more about this issue,
it might not be a taboo matter but usually folks don’t talk about such
issues. To the next! Kind regards!!
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored material stylish.
nonetheless, you command get bought an impatience over that you wish be delivering the following.
unwell unquestionably come further formerly again since exactly the same nearly very often inside case you
shield this increase.
Best if you are just testing the cigar out for the very first time.
Feel free to surf to my website; Maggie
I appreciate that the story appears at thhe girl’s relationships with their households, it is extra than just laughing at
crazy mums.
my web psge simonparkes.org blog
Sunlight can really make the clothing a great
aroma. They’ll be smelling a lot better than once they have been just dried in a dryer.
You can even save on electricity bills using this method.
To edit a critique you’ve already submitted, please speak to our Consumer Service group.
Here is my homepage – baccarat hotel Nyc
This is very interesting, You’re a very skilled blogger.
I have joined your feed and look forward to seeking more of your magnificent post.
Also, I have shared your web site in my social networks!
Designed for the 250th anniversary of the French crystal home
Baccarat.
Does your blog have a contact page? I’m having a tough time locating it but,
I’d like to shoot you an email. I’ve got some creative ideas
for your blog you might be interested in hearing. Either way, great website and I look
forward to seeing it improve over time.
Note a little chip on the neck of one glass, see photo.
Feel free to visit my web blog – Baccarat
Wow that was unusual. I just wrote an really long comment but after I clicked submit my comment didn’t show up.
Grrrr… well I’m not writing all that over again.
Anyhow, just wanted to say excellent blog!
Thank you, I’ve just been looking for information approximately this topic for ages and yours is the greatest I’ve discovered so far.
But, what in regards to the bottom line? Are you certain about the
supply?
in the 28th minute, Higuain sent two defenders อาร์เจนตินาล่าสุด in front of the penalty area. but was intercepted by Amorviata
Unfortunately, the ball flew off the bottom line. อาร์เจนตินาคัพ In the 70th minute, Messi fired a long-range shot from Lucho in front of the penalty area
I don’t know when Argentina can make other ลีกยูเครน players as good as him. I feel Messi as captain. He is happy. We all respect him. He will lead the national team to the best.
football friendly match between Calcutta, India ทีมปารีส and Venezuela as this is Argentina’s first game after the Copa Amére.
With Ansaldi withdrawing from injury, they บาร์ซาสด currently only have three full-backs in their squad, so the possibility of playing 352 in the game is slim.
First of all I want to say wonderful blog! I had a quick question that I’d like to ask if
you do not mind. I was interested to find out how
you center yourself and clear your head prior to writing. I’ve had a tough time clearing
my mind in getting my ideas out. I do enjoy writing
but it just seems like the first 10 to 15 minutes tend to be wasted just trying
to figure out how to begin. Any ideas or hints?
Kudos!
And the Ukrainian goalkeeper almost gave his ทีมเยอรมัน opponent a chance. At 20 minutes, Sim de Jong fires a shot from distance with his right foot.
Incredible points. Outstanding arguments. Keep up the great spirit.
She also acted in the motion pictures Day 13 and Sid Is Dead.
Feel free to visit my blog post: omgg blog (Margot)
Hi there! This post could not be written any better! Going through this post
reminds me of my previous roommate! He constantly kept talking about this.
I will forward this information to him. Fairly certain he will
have a good read. Thanks for sharing!
I have to thank you for the efforts you’ve put in writing this website.
I’m hoping to see the same high-grade content from you
later on as well. In fact, your creative writing abilities has inspired me to get my own, personal site now
😉
Just want to say your article is as astonishing.
The clarity on your put up is just excellent and that i could assume you’re an expert on this subject.
Fine with your permission let me to seize your feed to keep up to
date with impending post. Thank you a million and please continue the enjoyable work.
With no other guests in there at the time, I felt like I had
stumbled into an offshoot of MoMA.
Here is my page … Judith
You can also get a likelihood to meet new individuals from
all over the world.
my blog post :: https://powerball.link/
Hurrah! After all I got a web site from where I can in fact take helpful data concerning
my study and knowledge.
Also visit my web page slot online jackpot
However, points in baccarat are calculated
differently than in other table games.
Review my web-site :: Arnulfo
I for all time emailed this web site post page to all my contacts, since if like to read it then my friends will too.
What’s up i am kavin, its my first time to commenting
anyplace, when i read this piece of writing i thought i
could also create comment due to this good post.
I know this web page offers quality based articles or
reviews and additional stuff, is there any other web site which presents
such stuff in quality?
Sports betting. Bonus to the first deposit up to 500 euros.
sports betting
Viagra Avis msd stromectol Amoxicilina For Sale On Line Pharmacy
A lot of people play Dragon Ball Super Super Hero frequently.
Lots and plenty of people make use of it to entertain themselves, no matter how old they can be.
Read on to discover more about tips that
may increase your Dragon Ball Super Super Hero playing experience.
Howdy! This blog post couldn’t be written much better!
Looking through this post reminds me of my previous roommate!
He constantly kept talking about this. I will forward this article to him.
Pretty sure he’ll have a very good read. Thank
you for sharing!
Hi my family member! I want to say that this article is amazing, great written and come
with almost all significant infos. I would like to see more posts
like this .
Hey There. I found your blog using msn. This is a really well written article.
I’ll make sure to bookmark it and come back to read more of your useful information. Thanks for the post.
I’ll definitely comeback.
The traditional bands are los angeles personal industry lawyers
that help your attorney stay that way. Now deliver a way for
these who opt for continuing education in this field.
Frequent educational facilities plant centers
which hire trainers who are only forty weeks from conception to.
Touch on physical social and educational institutions who would like to understand learning solution.
The field of medicine M.D, Touch surgery you can enjoy smelling like.
Medicine is ever occupied for a career choice which will leave you much better.
Prospective attendee must have a bulged disc or a career
is the great students take the time.
Legendary iconic New York City recording artist AceLover The Style Gawd featured on the new Flex & Peek EP 2022 on the song called Let Em Have It.
AceLover The Style Gawd rarely does any features.
The beat was produced by Joe Gibbs. The Flex Nugget & PG Lock EP Out Now !!!
Stream on Spotify and YouTube.
As of the date of this Agreement, a Player is permitted to make only one particular withdrawal of Unutilized
Funds per day.
Here is my website https://Spegasoft.Com
Woah! I’m really digging the template/theme of this website.
It’s simple, yet effective. A lot of times it’s difficult to
get that “perfect balance” between user friendliness and
visual appeal. I must say you’ve done a amazing job with this.
In addition, the blog loads very quick for me on Chrome.
Superb Blog!
Stephen married actress Annie Wereching
back in 2009, and they have two youngsters together.
Here is my homepage :: west seattle blog
I don’t normally comment but I gotta tell appreciate it for the post on this amazing
one :D.
Also visit my site; Accu Keto + ACV
Two of the $1 million tickets were sold in Maryland and the other
have been sold inn Arizona, Florida andd Virginia.
My blog post: Click for source
You have made some really good points there. I looked on the internet for more information about the issue and found
most individuals will go along with your views on this website.
Students discover how to provide the best care for their
individuals in all sorts of healthcare settings.
My blog – brigham And women’s jobs
It’s awesome in support of me to have a site, which is helpful designed
for my knowledge. thanks admin
There are a couple of established corporations that
hired stylists who function from their houses .
my website: Jefferson
hi!,I love your writing very so much! percentage we be in contact extra approximately your post on AOL?
I need a specialist in this area to unravel my problem. Maybe that’s you!
Having a look ahead to peer you.
Hoop Streams, ESPN’s digital NBA pre-game show, will
stream live on ESPN’s Twitter, Facebook, YouTube and the ESPN App at eight p.m.
Also visit my homepage :: Sam
If you are going for best contents like I do, just pay a visit this web site daily because it offers feature contents, thanks
my website Exfolie Anti Aging Serum
The hotel occupies the 1st 12 floors of the 50-story Baccarat Hotel and Residences project scheduled
to open the 1st week of March.
Feel free to surf to my blog post … Malcolm
It also splits your bbed in half, so your companion ccan select a totally various
temperature.
Take a look at my webpage: powerline blog – Eve,
Great article.
Good write-up. I definitely love this website. Keep writing!
We stumbled over here by a different website and thought I might as well check
things out. I like what I see so i am just following you.
Look forward to looking into your web page yet again.
Retain and demonstrate a clear division involving the Board’s management and oversight part and the executive’s operational function.
my web site :: Dicks Sporting Goods
Get a pet well being insurance coverage quote these days for your dog, cat, puppy, or kitten.
Also visit my web site – Beatrice
I’d like to find out more? I’d care to find out more
details.
There are also oter “free” amateur services like Tumblr or Blogger that permit you
to start out a blog on those company’s platforms.
Here is my web-site – omg blog, Bettina,
Definitely believe that which you said. Your favorite reason seemed to be
on the net the easiest thing to be aware of.
I say to you, I definitely get irked while people consider worries that they plainly don’t know about.
You managed to hit the nail upon the top and defined
out the whole thing without having side effect , people
can take a signal. Will probably be back to get more.
Thanks
An impressive share! I have just forwarded this onto a friend who had been conducting a little research on this.
And he actually bought me dinner because I discovered it for him…
lol. So let me reword this…. Thank YOU for the meal!!
But yeah, thanx for spending time to talk about this topic here on your web page.
I have been browsing online greater than three hours lately, but
I by no means discovered any interesting
article like yours. It is pretty value enough for me. Personally, if all web owners and bloggers made good content material as you probably did,
the web will be much more helpful than ever before.
Amazing…Thank you for sharing this! If you need some more information about Search Engine Opimization than have a look here – http://thomashenryhouse.com.au/?wptouch_switch=mobile&redirect=https://seotrendsonline.blogspot.com/
Hola! I’ve been reading your blog for a while now and finally got the bravery to go ahead
and give you a shout out from Humble Texas! Just
wanted to say keep up the good job!
AllSaints’ Sunset Riot Eau de Parfum is an additional
replica on our list.
Feel free to visit my webpage https://Healthiestmushrooms.com/Community/profile/gary8833203903/
This website was… how do you say it? Relevant!! Finally I have found something that helped me.
Cheers!
There are examples of bloggers who have publishsd books based on their blogs, e.g., Salam Pax, Ellen Simonetti, Jessica Cutler, ScrappleFace.
Here is my page – the fappening blpg – Tilly,
Please retain all original packing supplies and any paperwork incorporated
with the shipment and delivery.
My webpage: Margery
In Baccarat, the objective is to get as close to nine as
probable, which is a equivalent notion to the game of
Blackjack.
Here is my blog post: https://ganz.wiki/index.php/Major_True_Revenue_On_The_Internet_Casino_Sites_Usa_2022
’” prior to sitting down in front of the contaminated boat to show
that something is amiss, Lockwoood mentioned.
Also visit my site :: omg blog; Opal,
We’re a bunch of volunteers and starting a brand new scheme
in our community. Your website provided us with useful info to
work on. You’ve done a formidable task and our entire
group can be thankful to you.
Also visit my web site – чартер лодок в греции
最安値直販店ラブドール通販店 | ブランド正規品 |おとなLOVE (otona love) は正規直販店であり、自分の生産現場を持っております。第三者に通らず生産現場から直接顧客に配送するため、TPE素材や高級シリコン製のラブドールを低価格高品質で入手できます。また、正規代理WMDOLLラブドール、6YEDOLLラブドール、JY DOLLラブドール、メーカーから直接消費者の手元に届くようなサービスを提供させていただきます。品質保証、安心・安全への取り組み。
Other bodies advocate widening the definition of sport
to consist of all physical activity.
Visit my blog post: Lavonne
This design is spectacular! You certainly know how to keep a reader amused.
Between your wit and your videos, I was almost moved
to start my own blog (well, almost…HaHa!) Great job. I really
loved what you had to say, and more than that, how you
presented it. Too cool!
This is when the Player holds a higher card worth and
is declared the winner.
Feel free to visit my blog – baccarat Hotel nyc
Pada tahun 1985 Charles Fey bikin versi baru yang diberi nama Horseshoe yang
mempunyai sistem pembayaran otomatis karena pada zaman tersebut mesinslot88 membutuhkan seorang petugas untuk menukar uang atau token dan bayar keuntungan sehingga Charles
Fey memodifikasi karyanya menggunakan mekanisme otomatis serta merubah cara kerjanya lebih komplek agar mesin dengan kilat
mengenali simbol bayaran tersebut.
http://energoteploaudit.ru/
Fastidious replies in return of this query with firm arguments and explaining the whole thing about that.
Для прохождения упрощенной верификации в «Леон»
предлагается три способа.
Here is my blog – бк леон регистрация leon stavka com
Hi! Quick question that’s entirely off topic.
Do you know how to make your site mobile friendly? My site looks weird when browsing
from my iphone4. I’m trying to find a theme or plugin that might be able to resolve this problem.
If you have any recommendations, please share. Many thanks!
It’s hard to come by educated people in this particular topic, however, you seem like you know what you’re talking about!
Thanks
Use the LinkedIn Alumni Tool to find out about where York
graduates perform, what they do, and what their capabilities are.
Visit my webpage … Christina
You ought to always observe advert performance no matter what social media platform you’re
using.
It’s impressive that you are getting ideas from this piece of writing
as well as from our discussion made at this time.
This post offers clear idea for the new visitors
of blogging, that actually how to do blogging and site-building.
ラブドール通販店 | ブランド正規品 | 最安値直販店 「おとなLOVE」(otona love)は、株式会社星テックに所属するサブブランドです。株式会社星テックは、OEM生産(OEM)を専門とするハイエンドのセックスライフのグローバルメーカーであり、サービスは世界70を超える国と地域に広がっています。現在、消費者のニーズに応じて、OEMにとどまらず、メーカーから直接消費者の手元に届くようなサービスを提供するために「おとな愛」を生み出しました。私たちは革新と努力を続け、より多くの人々が非常に安い価格でより良い品質の商品を購入できると信じています。また、正規代理WMDOLLラブドール、6YEDOLLラブドール、JY DOLLラブドール、メーカーから直接消費者の手元に届くようなサービスを提供させていただきます。
Fine way of explaining, and fastidious post to get facts
concerning my presentation focus, which i am going to present in academy.
Also visit my blog post … kamagraa.space
I know this if off topic but I’m looking into starting my own blog and
was wondering what all is needed to get setup?
I’m assuming having a blog like yours would cost a pretty
penny? I’m not very internet savvy so I’m not 100% sure. Any recommendations or advice
would be greatly appreciated. Thank you
Use text and graphics, Facebook auto-caption instruments or addContent an SRT file to your video advert
to add captions to help deliver your message.
Лечение наркомании Уфа
Nearly 500 million users create and test a minimum of some Instagram story
day by day all around the world. Check your analytics on Instagram by going to your profile web page and tapping on the menu
in the higher proper. When you have an Instagram business account,
navigate to the viewers tab from the Insights menu. Hosting
a weekly or month-to-month chat session on Instagram is an excellent manner to
interact and build relationships together with your current audience.
So if you’re going to cross-submit content from Instagram to other channels, make sure the content material is high quality and doesn’t promote
a competing platform through watermarks. Instagram created by
Mike Krieger and Kevin Systrom and launched in October 2010 for the iOS platform.
Buy Zengram app and get more real Instagram
followers, likes and feedback. On the other hand, if you want
to make your remark standard, you want to buy YouTube remark likes.
Search and open the Instagram video that you simply want to obtain. Just hit the “Download” button to start download Picture or Video.
After that paste the URL on the above text field and click the “Download” button. After that,
hit the obtain button and get pleasure from excessive-quality images
and videos.
Эротический массаж Уфа
Hello my family member! I want to say that this article is awesome, nice written and include approximately
all significant infos. I’d like to see more posts like this .
Someone essentially lend a hand to make severely articles I’d state.
This is the very first time I frequented your website page
and thus far? I amazed with the research you made to
make this actual put up incredible. Fantastic process!
Hi! I know this is kinda off topic but I was wondering if you knew where I could find a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having trouble finding one?
Thanks a lot!
http://hotel-restaurante.com/
Hey! I’m at work browsing your blog from my new apple iphone!
Just wanted to say I love reading through your blog and look forward
to all your posts! Carry on the excellent work!
Hi there, I discovered your website by way of Google
whilst searching for a similar matter, your web
site came up, it looks great. I have bookmarked it in my google bookmarks.
Hi there, just turned into aware of your blog thru
Google, and found that it’s truly informative.
I am going to be careful for brussels. I’ll appreciate if you proceed this in future.
Lots of people will be benefited from your writing.
Cheers!
Great post. I was checking continuously this
blog and I’m impressed! Very useful info specifically the last part 🙂 I care
for such info a lot. I was looking for this certain information for
a long time. Thank you and best of luck.
Thank you for the auspicious writeup. It if truth be told used to be a enjoyment account it.
Look complicated to far delivered agreeable from you!
By the way, how can we be in contact?
You can browse possibilities or offer you specific — and random — services.
My web blog :: Jung
More than the weekend, Dick’s CEO Ed Stack addressed McKenna’s concerns in a
letter the corporation posted to Twitter.
Feel free to surf to my website – Marsha
http://www.top-informer.ru/
This website was… how do I say it? Relevant!!
Finally I have found something which helped me. Appreciate it!
In 2019, which was the final time the NBA had an offseason on its
regular calendar, totally free agency started on June 30.
Check out my webpage … Donnie
Pretty portion of content. I simply stumbled upon your weblog and in accession capital to say
that I get in fact enjoyed account your weblog posts.
Anyway I will be subscribing to your augment and even I success you access
consistently quickly.
Amazing blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple tweeks would really make my blog stand out.
Please let me know where you got your theme. Many thanks
In 1993, Baccarat began making jewelry and in 1997 the company expanded into perfume.
Review my web page … Hassie
If the total is greater than nine, the “1” is dropped.
Here is my website … https://wiki.icluster.cl/index.php/tech_zone_on_the_internet_casino_dealer_work_jobs_in_makati
We’re hunting for compassionate and committed team players who want to live
Part-Time Job At A Bar life of objective.
Have you ever thought about adding a little bit more than just your articles?
I mean, what you say is valuable and everything. Nevertheless just imagine if you added
some great visuals or video clips to give your posts more, “pop”!
Your content is excellent but with pics and videos, this website could undeniably be one of the greatest in its field.
Awesome blog!
The room varieties commence with the Classic King and culminates
in the plush Baccarat suite.
Feel free to surf to my webpage: Stormy
This is the perfect webpage for anybody who hopes to
find out about this topic. You know so much its almost hard to argue
with you (not that I personally will need to…HaHa). You definitely put a
brand new spin on a subject that’s been discussed for decades.
Wonderful stuff, just excellent!
This site truly has all the info I needed concerning this subject and didn’t know who
to ask.
Awesome website you have here but I was curious if you knew of any discussion boards that cover the same topics talked about in this article?
I’d really like to be a part of group where I can get feedback from other
knowledgeable individuals that share the same interest.
If you have any suggestions, please let me know. Thanks!
It lasts longer, has far more energy, and a bittersweet opening act with far more saffron and an added almond
note.
Review my page … Hollie
A split shift divides a work day into separate
periods of work.
Feel free to surf to my site … Naomi
I love reading through an article that can make men and
women think. Also, many thanks for allowing for me to comment!
buy cvv Good validity rate Buying Make good job for MMO Pay
on site activate your card now for worldwide transactions.
————-CONTACT———————–
WEBSITE : >>>>>> CCBuy✹ Site
—– HERE COMES THE PRICE LIST ———–
***** CCV US:
– US MASTER CARD = $2,5 per 1 (buy >5 with price $3 per 1).
– US VISA CARD = $3 per 1 (buy >5 with price $2.5 per 1).
– US AMEX CARD = $4 per 1 (buy >5 with price $2.5 per 1).
– US DISCOVER CARD = $2,6 per 1 (buy >5 with price $3.5 per 1).
– US CARD WITH DOB = $15 per 1 (buy >5 with price $12 per 1).
– US FULLZ INFO = $40 per 1 (buy >10 with price
$30 per 1).
***** CCV UK:
– UK CARD NORMAL = $3,1 per 1 (buy >5 with price $3 per 1).
– UK MASTER CARD = $3,4 per 1 (buy >5 with price
$2.5 per 1).
– UK VISA CARD = $3,5 per 1 (buy >5 with price $2.5 per
1).
– UK AMEX CARD = $2,1 per 1 (buy >5 with price $4 per 1).
$
– UK CARD WITH DOB = $15 per 1 (buy >5 with price $14 per 1).
– UK WITH BIN = $10 per 1 (buy >5 with price $9 per 1).
– UK WITH BIN WITH DOB = $25 per 1 (buy >20 with price $22 per 1).
– UK FULLZ INFO = $40 per 1 (buy >10 with price $35 per 1).
***** CCV AU:
– AU MASTER CARD = $5.5 per 1 (buy >5 with price $5 per 1).
– AU VISA CARD = $5.5 per 1 (buy >5 with price $5 per 1).
– AU AMEX CARD = $8.5 per 1 (buy >5 with price $8 per 1).
– AU DISCOVER CARD = $8.5 per 1 (buy >5 with price $8 per 1).
***** CCV CA:
– CA MASTER CARD = $6 per 1 (buy >5 with price
$5 per 1).
– CA VISA CARD = $6 per 1 (buy >5 with price $5 per 1).
– CA VISA BUSINESS = $14 per 1 (buy >5 with price $13 per 1).
Hello, i believe that i saw you visited my site thus i got here to return the favor?.I
am trying to in finding issues to enhance my web site!I suppose
its ok to make use of a few of your ideas!!
Wonderful post however , I was wondering if
you could write a litte more on this subject? I’d be very thankful if you could elaborate a
little bit further. Bless you!
It’s a shame you don’t have a donate button! I’d most certainly donate to this outstanding blog!
I guess for now i’ll settle for book-marking and adding your RSS feed to my Google
account. I look forward to fresh updates and will share this site with
my Facebook group. Chat soon!
I’m pretty pleased to find this web site. I want to to thank you for ones time just for this fantastic read!!
I definitely appreciated every bit of it and I have you book marked
to see new information on your web site.
This article is in fact a pleasant one it helps new net people, who are wishing in favor of blogging.
Cashback oor Insurance bonuses are provided as a percentage of all losses in the player’s earlier gaming activity.
Here is my homepage … online casino
Amazing issues here. I’m very happy to see your article.
Thank you a lot and I’m having a look ahead to contact you.
Will you please drop me a e-mail?
Here is my web-site Lean Ready Keto Gummies
Barnes iis a single off the saddest yet most fascinating stories in NBA history, however it is one with a glimmer of hope.
Also visit my site … dicks sporting goods [Lazaro]
Nice post. I was checking continuously this weblog and
I’m inspired! Extremely helpful info specially the final section :
) I care for such info a lot. I was looking for this certain information for a long time.
Thanks and good luck.
Woah! I’m really loving the template/theme of this site. It’s simple,
yet effective. A lot of times it’s difficult to get that “perfect balance” between user friendliness and visual appeal.
I must say you have done a awesome job with this. Also, the blog loads
super fast for me on Safari. Excellent Blog!
You must transfform your passwords every 3 months.
Also visit my pagve … simonparks org blog – Mellisa –
%%
Your mode of explaining the whole thing in this piece of writing is really
fastidious, all can simply understand it, Thanks a lot.
Heya this is kinda of off topic but I was wondering if blogs use WYSIWYG editors or
if you have to manually code with HTML. I’m starting a blog soon but
have no coding know-how so I wanted to get advice from someone with experience.
Any help would be enormously appreciated!
If you want to improve your knowledge simply keep visiting this web
page and be updated with the most up-to-date news update posted here.
I have read so many articles or reviews regarding the blogger
lovers however this article is really a fastidious paragraph, keep it up.
Wonderful blog you have here but I was curious if you knew of
any message boards that cover the same topics discussed in this article?
I’d really love to be a part of online community
where I can get feedback from other experienced individuals that share the same interest.
If you have any suggestions, please let me know.
Appreciate it!
Great post. I am dealing with many of these issues as well..
Great article.
great post, very informative. I wonder why the other experts of this sector don’t notice this.
You should proceed your writing. I am sure, you’ve a huge readers’ base already!
What’s up i am kavin, its my first time to commenting anywhere,
when i read this paragraph i thought i could also create comment due to this brilliant
piece of writing.
Fittingly named Alki Beach, it features a long strip of sandy beach complete oof driftwood, seashells, and fire pits.
Feel free to visit my web page … west seattle blog
Undeniably consider that that you said. Your favourite justification seemed to be at the web
the easiest thing to take into account of. I say to you, I certainly
get annoyed at the same time as other people consider worries that they just don’t
know about. You managed to hit the nail upon the top as smartly
as defined out the whole thing with no need side-effects ,
people could take a signal. Will likely be back to get more.
Thanks
We stumbled over here coming from a different web address and thought I may as well check things out.
I like what I see so now i am following you.
Look forward to exploring your web page for a second time.
Good article. I definitely love this site. Stick with it!
After you feed them a specially generated password, they will be happy with it
for a extendeed time.
Here is my site: simonparkes.org blog
Hi there! Quick question that’s totally off topic. Do you know how to make your site mobile friendly?
My web site looks weird when viewing from my iphone4. I’m trying
to find a template or plugin that might be able to correct this issue.
If you have any recommendations, please share.
Many thanks!
Why visitors still use to read news papers when in this technological world all is available on net?
With havin so much content do you ever run into any problems of plagorism
or copyright infringement? My blog has a lot of exclusive content I’ve either authored myself or outsourced
but it looks like a lot of it is popping it up all over the internet
without my agreement. Do you know any techniques to help prevent
content from being stolen? I’d definitely appreciate it.
Incredible! This blog looks just like my old one! It’s
on a completely different subject but it has pretty much the same page layout and
design. Outstanding choice of colors!
you are in point of fact a good webmaster.
The website loading velocity is incredible. It sort of feels that you’re doing any distinctive trick.
Moreover, The contents are masterwork. you’ve performed a wonderful activity in this matter!
I do not even know how I stopped up here, however I believed this submit used to be great.
I do not understand who you are however certainly you’re going
to a well-known blogger if you aren’t already.
Cheers!
Admiring the commitment you put into your blog and in depth information you provide.
It’s nice to come across a blog every once in a while that
isn’t the same outdated rehashed information. Fantastic read!
I’ve saved your site and I’m adding your RSS feeds to my Google account.
Definitely imagine that which you said. Your
favorite justification appeared to be on the web the easiest thing to take note of.
I say to you, I definitely get irked at the same time as people consider concerns
that they plainly don’t understand about. You
managed to hit the nail upon the highest as neatly as outlined out the entire thing without having side effect , people can take a signal.
Will probably be back to get more. Thanks
I couldn’t resist commenting. Very well written!
I like the helpful information you provide in your articles.
I’ll bookmark your blog and check again here frequently.
I am quite certain I will learn many new stuff right here!
Best of luck for the next!
No additional taxes or customs duties are charged for items that are shipped to the European Union.
Check out my web blog; http://www.sportlab.cloud
Howdy! This post could not be written any
better! Reading this post reminds me of my good old room mate!
He always kept talking about this. I will forward this
post to him. Pretty sure he will have a good read. Many thanks for sharing!
Thee final time a Powerball jackpot climbed
so highner was May perhaps 2013 hen a Florida ticket won a $590.5 million prize.
Also visit my blog :: Browse this site
Given that you’ve read the post, what exactly are your feelings on environmentally
friendly Bullet Train boxoffice. Do you think that
natural Bullet Train news is an excellent factor to suit your needs?
You will discover by your consumption of these recommendations how effortless it can be to feature environmentally friendly
Bullet Train film to you. Begin using them
now to start to see the advantages of natural Bullet Train imdb.
Fantastic goods from you, man. I have understand your stuff previous to and
you’re just extremely magnificent. I actually
like what you have acquired here, certainly like what you’re saying and the
way in which you say it. You make it enjoyable and you still care
for to keep it smart. I cant wait to read far more from you.
This is really a terrific website.
Visit my website; coverage
WOW just what I was looking for. Came here by searching for شحن جواهر فري فاير
These additions improve the scent and make it a bit a lot more of a crowd-stopper.
Have a look at my web site – https://danteavxl.bloggersdelight.dk/2022/08/02/baccarat-vases-for-Household
There’s certainly a great deal to know about this issue.
I love all the points you’ve made.
Hi! Someone in my Facebook group shared this
website with us so I came to look it over. I’m definitely enjoying the information. I’m bookmarking and will be tweeting this to
my followers! Fantastic blog and excellent design.
My website – steps
I am regular reader, how are you everybody? This paragraph posted
at this web site is genuinely nice.
my blog post … ratings
База отдыха в Подмосковье
Cysts have then committed that implicit personal letter that tubes from band will study in commercial reps that suit the generic cialis online starter programmes buy cheap cialis online
Hi there! This is kind of off topic but I need some advice from an established
blog. Is it difficult to set up your own blog?
I’m not very techincal but I can figure things
out pretty fast. I’m thinking about making my own but
I’m not sure where to start. Do you have any ideas
or suggestions? Cheers
Check out my website devices
Hello.This article was extremely interesting, especially since I was
searching for thoughts on this issue last couple of days.
Feel free to surf to my web blog :: Trim Drops Keto Gummies
Banks like TD Ameritrade and other investing apps
like WeBull rrestricted specific trades involpving
GameStop.
My page; nba games
Good post! We are linking to this particularly great post on our website.
Keep up the good writing.
Very soon this website will be famous among all blog users, due to it’s nice articles
my homepage; Superstar CBD Review
Kurkdjian’s greatest test, having said that, is a
individual 1.
Stop by my blog post Rosie
This paragraph is in fact a nice one it helps new web visitors,
who are wishing in favor of blogging.
You can turn your home’s electrical wiringg into a higher-speed network with ease.
Stop by my web blog: omg blog (Lilla)
Amazing blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple tweeks would really make my blog
shine. Please let me know where you got your theme.
Many thanks
This brand produced an work to give perfume
lovers a piece of art, and such pieces are constantly exposed to
large criticism.
My page Baccarat Hotel Nyc
Published by Houghton Mifflin Company best place to buy generic cialis online Some people gave up early due to the side effects, but those who persisted, and amended their dosage were all pleased that they did
Perfect work you have done, this site is really cool with great information.
Here is my webpage seawolf yacht
WOW just what I was looking for. Came here by searching for FIFA World Cup
I like what you guys are up too. This type of clever work and coverage!
Keep up the amazing works guys I’ve you guys to my blogroll.
No matter if some one searches for his essential thing, thus he/she
desires to be available that in detail, thus that thing is maintained over here.
This paragraph gives clear idea in favor of the new visitors of blogging,
that actually how to do blogging.
Основная сложность перевода потокового
видео в том, что нужно постоянно искать баланс между качеством и скоростью перевода.
Feel free to surf to my page: Ellis
hi!,I really like your writing vey a lot! share we be in contact extra about
your article on AOL? I need an exppert on this house to resolve my problem.
May be that is you! Having a look forward to look you.
My web-site holycrossabbeybrryvlle.org
I every time used to study article in news
papers but now as I am a user of internet so from now I am using net for posts, thanks to web.
In spite of the image no longer getting on the platform, the creator of the image is still part of the platform’s creator programme.
Feel free to surf to my blog Louise
Аренда микроавтобуса в Москве
After exploring a number of the blog posts on your web site, I seriously like your
way of blogging. I saved as a favorite it to my bookmark webpage list and will be checking back soon. Take a look at my website as well and tell
me how you feel.
อยากเป็นสมาชิก ที่ autobetcasino สำหรับคนชอบเล่นบาคาร่า ให้ทำเงินจาก autobet เว็บคาสิโนออนไลน์ชื่อดัง ที่ไม่มีเซียนพนันคนไหนที่ไม่รู้จัก เนื่องจากเป็นเว็บที่เปิดให้บริการมาอย่างยาวนาน แน่นอนว่า สมาชิกในเว็บไซต์มากกว่าหลักหมื่นอย่างแน่นอน เป็นเว็บไซต์ที่เปิดตลอด 24 ชั่วโมง autobetcasino
Member at MyBookie can find a ton of Stranger Things Season 4 odds. It is a safe online betting site with a ton of banking options available.
What’s up, its pleasant paragraph regarding media print,
we all understand media is a enormous source of data.
Hi! I know this is sort of off-topic but I had
to ask. Does operating a well-established website like yours take a large amount of work?
I’m brand new to blogging however I do write in my journal every day.
I’d like to start a blog so I can share my own experience
and views online. Please let me know if
you have any ideas or tips for brand new aspiring bloggers.
Appreciate it!
Hi there I am so thrilled I found your weblog, I really found you by accident, while I was searching on Yahoo for something else, Nonetheless I am here now
and would just like to say thanks a lot for a fantastic post and a all round exciting blog (I also love the theme/design), I don’t have time to
browse it all at the minute but I have book-marked it and also added your RSS feeds, so when I have time I
will be back to read more, Please do keep up the superb work.
Barista – Most college students live off coffee as they take into consideration sleep to
be a luxury.
Also visit my homepage – 유흥알바
Fabulous, what a blog it is! This weblog gives useful
data to us, keep it up.
Simply want to say your article is as surprising.
The clearness in your post is just excellent and i can assume you’re an expert on this subject.
Fine with your permission allow me to grab your
RSS feed to keep up to date with forthcoming post.
Thanks a million and please carry on the gratifying work.
The tradition of total female submission persisted in Korean villages until relatively current occasions.
Also visit my webpage: https://Rylan7529E.Oblogation.Com/
I read this post fully about the difference of most up-to-date and previous technologies, it’s amazing article.
Pretty nice post. I just stumbled upon your blog and
wanted to say that I’ve truly enjoyed surfing around your blog posts.
In any case I will be subscribing to your rss feed and I hope you write again soon!
Hey just wanted to give you a brief heads up and let
you know a few of the pictures aren’t loading correctly.
I’m not sure why but I think its a linking issue. I’ve tried it in two different internet browsers and both show the same outcome.
Again, this is to make sure that the erectile dysfunction treatment you choose is safe for you to take and doesn t conflict with any medication you re taking buy priligy in usa
She performs with nonprofit clientele to optimize their fundraising andd public relations efforts through the application oof database technologies.
My blog – fappenming blog, Delia,
Wonderful blog! I found it while searching on Yahoo News.
Do you have any tips on how to get listed in Yahoo News? I’ve been trying for a
while but I never seem go to these guys
get there! Appreciate it
My relatives always say that I am killing my time here at net,
however I know I am getting know-how daily by reading
thes fastidious articles.
I simply couldn’t depart your website prior to suggesting that
I really enjoyed the standard info an individual provide in your visitors?
Is going to be again incessantly in order to investigate cross-check new posts
The winners will split thhe $632.6 million jackpot, according tto the lotteryy web
site, or have the option of $450.two million in cash.
Have a look at my web-site – Go to the website
manfaat obat xenical orlistat 120 mg
Hi there, I think your website could possibly be having browser compatibility problems.
Whenever I look at your website in Safari, it looks fine however,
when opening in Internet Explorer, it’s got some overlapping
issues. I merely wanted to provide you with a quick heads up!
Other than that, excellent site!
Hi, i feel that i saw you visited my weblog thus i came to
go back the favor?.I’m trying to in finding things to
improve my web site!I assume its adequate to use a
few of your concepts!!
deneme bonusu veren siteleri incelemek için tıklayabilirsin.
This is a really good tip especially to those fresh to the blogosphere.
Simple but very precise information… Many thanks for sharing this one.
A must read article!
Thanks , I have recently been looking for info approximately this topic for a
while and yours is the greatest I have found out so far.
But, what in regards to the bottom line? Are you sure concerning the supply?
My page; Glucodyn Side Effects
WOW just what I was searching for. Came here by searching for Emergency Visa Online
Cialis is the brand name of a drug called tadalafil see Important Safety Information , a popular medication used to treat erectile dysfunction ED priligy side effects
Right now it seems like BlogEngine is the top blogging platform available right now.
(from what I’ve read) Is that what you’re using on your blog?
Bozulan beyaz eşyalarınız için bursa bosch servisi.
Does your website have a contact page? I’m having problems locating
it but, I’d like to shoot you an e-mail. I’ve got some creative
ideas for your blog you might be interested in hearing.
Either way, great blog and I look forward to seeing it develop
over time.
yönetim bilişim sistemleri nedir
Hi there, I found your web site by means of Google even as looking for a similar topic, your site got here
up, it seems to be good. I’ve bookmarked
it in my google bookmarks.
Hi there, just was aware of your weblog via Google,
and found that it’s truly informative. I am going to watch out for brussels.
I will appreciate when you proceed this in future.
Many people will likely be benefited from your writing.
Cheers!
Everyone probably will go on a trip sooner or later.
In case you have time to prepare this getaway, you are able
to take the time to make certain your expertise is cost-effective,
as stress free as is possible, and just all-around more enjoyable.
Utilize these suggestions to get the most from your next The Invitation update experience.
Baccarat is the well-known game of choice for
secret agents, supervillains and, of course, casino VIPs.
Here is my web page :: Gemma
I’ve been browsing online more than three hours today, but I by no means found any
interesting article like yours. It’s beautiful price sufficient
for me. In my view, if all site owners and bloggers made excellent content material as you probably did,
the internet shall be much more useful than ever before.
The Zephyrus S17 has a big 4 cell, 90WHr battery.
Four tweeters are located beneath the keyboard whereas the 2 woofers sit under the display.
Overall, these two benchmark results bode effectively for players
wanting a laptop that’s a cut above by way of graphics
performance, with the excessive body rates equating to a smoother gaming experience and extra element in every scene rendered.
Because the Xbox 360 cores can every handle two
threads at a time, the 360 CPU is the equal of having six typical processors in a single machine.
The sheer amount of calculating that is finished by the graphics processor to
find out the angle and transparency for each reflected object,
after which render it in actual time, is extraordinary.
Southern California artist Cosmo Wenman has used a
3-D printer to make meticulously rendered copies of famous sculptures, based mostly upon plans original from lots of of images that he snaps from every angle.
Many corporations provide a combination of those plans.
With its combination of a Core i9-11900H CPU, a Nvidia RTX
3080 GPU, and 32GB of RAM, this laptop performed exceedingly properly in efficiency
benchmarks that present perception into its CPU energy and cooling.
What this implies when you are taking part in video video games is that the Xbox 360 can dedicate one core entirely to producing sound, whereas another might run the game’s collision and physics
engine.
My web site … freecredit
best cialis online Simply login to your online pharmacy account and view your prescription history and if you have a valid Rx on file
Great goods from you, man. I’ve understand your stuff previous to and you are just extremely
great. I actually like what you’ve acquired
here, really like what you’re saying and the way in which you say it.
You make it enjoyable and you still care for to keep it sensible.
I can’t wait to read much more from you. This is actually a tremendous website.
I’m really enjoying the design and layout of your website.
It’s a very easy on the eyes which makes it much
more pleasant for me to come here and visit more often. Did
you hire out a developer to create your theme? Excellent work!
Why users still use to read news papers when in this
technological world everything is presented on net?
Nel valutare gli effetti del Cialis Tadalafil sull organismo, ГЁ stato determinato che ГЁ positivamente compatibile con i seguenti alimenti cialis online purchase The numbers within the bars indicate the number of patients with non-missing data at baseline and at least one visit after baseline
Seriously loads of helpful material! dissertation writing essay community service
Hello Dear, are you really visiing this site oon a
regular basis, if sso then youu will absolutely obtain good experience.
my web blog :: footjobtube4u.com
A wide variety of entertaining remote jobs are listed and categorized on We Perform Remotely.
Here is my blog – 유흥알바
Hi there! I know this is kind of off topic but I was wondering which blog platform are you using for this site?
I’m getting tired of WordPress because I’ve had issues with hackers and
I’m looking at alternatives for another platform.
I would be fantastic if you could point me in the direction of a good platform.
Greetings from Carolina! I’m bored to death at work so I
decided to check out your site on my iphone during lunch
break. I enjoy the information you provide here and can’t wait to take a
look when I get home. I’m amazed at how quick
your blog loaded on my phone .. I’m not even using WIFI, just 3G ..
Anyways, very good blog!
koindolu
If you wish for to improve your familiarity simply keep visiting this
web site and be updated with the latest news
update posted here.
Hello there! Quick question that’s totally off topic.
Do you know how to make your site mobile friendly? My
weblog looks weird when viewing from my iphone 4. I’m trying to find a
template or plugin that might be able to resolve this issue.
If you have any suggestions, please share. Appreciate it!
Howdy jut wanted to give you a quick headfs up. The text
in your content seem to bee running off the screen in Firefox.
I’m not sure if this is a formatting isue or something to do with internet browser compatibijlity but I figured I’d post to let you know.
The layout look great though! Hope you gett the
issue fixed soon. Thanks
my blog post; g2h2tucson.com
Hi to all, because I am in fact eager of reading
this webpage’s post to be updated regularly.
It contains nice stuff.
Nice post. I was checking constantly this weblog and I
am inspired! Extremely helpful information specially the closing
part 🙂 I maintain such info much. I used to be looking for
this certain info for a very long time. Thank you and best of luck.
https://lincolncountywebsite.com/professionals.html
https://brintonjaecksstudio.com/L/US/NC/Charlotte/Financial.html
I’m not that much of a internet reader to be honest but your blogs really nice,
keep it up! I’ll go ahead and bookmark your website to come back later on. Many
thanks
Have you ever considered about including a little bit more than just your articles?
I mean, what you say is fundamental and everything.
However imagine if you added some great visuals or videos to give your
posts more, “pop”! Your content is excellent but with images and video clips, this site could undeniably
be one of the best in its field. Very good blog!
Thanks for sharing your thoughts about 성남출장안마.
Regards
Informative article, exactly what I wanted to find.
Take a look at my website :: insurance
Helpful knowledge. Thank you. 250 word college essay good thesis statement writing websites
Why is this medication prescribed where to buy cialis 32 , Generic Cialis 0
My spouse and I stumbled over here from a different website and thought I might
check things out. I like what I see so i am just following you.
Look forward to looking over your web page for a
second time.
Hi there, just became aware of your blog through Google,
and found that it’s truly informative. I am gonna watch out for
brussels. I’ll appreciate if you continue this in future.
A lot of people will be benefited from your writing. Cheers!
When you didn’t appearance, legend gazing can be quite a enjoyable Don’t Worry
Darling 2022.Superstar gazing is really a location you could
miss out on. It endows you a little more. You
only need a telescope in darkish environment to assist you see every little thing.
Amazing! Its truly awesome piece of writing, I have got much clear idea concerning from this article.
Chiropractic can be your solution! We use multiple techniques that can accommodate kids and senior citizens.
Inversion therapy done on table or with the use of any other device; provides gravity based stretching
all through the spine and helps in spinal decompression. Use
the following steps to make sure you find the best
chiropractor for you. You can rest assured in knowing
that our doctors, Raymond Perry and Micah Barber,
will do everything they can to find the root cause of your pain and then create a personalized plan for your specific needs.
We take the time to discuss your symptoms and concerns and
determine the most appropriate treatment plan to aid you
back to fitness and back to doing what’s important to you.
I must say I’m nonplussed at how my symptoms I walked in with vanished post treatment.
There are several structures of the spine that may
be responsible for causing your pain, and many conditions have similar symptoms.
You may be searching for pain relief after an accident, experiencing an injury,
or if you suffer from a specific condition like chronic back
pain or a spinal condition.
After going over a number of the articles on your blog, I truly appreciate your way of blogging.
I saved it to my bookmark webpage list and will be checking back soon. Please visit my web
site too and tell me your opinion.
constantly i used to read smaller articles which also
clear their motive, and that is also happening
with this article which I am reading at this time.
Howdy would you mind letting me know which hosting company you’re
using? I’ve loaded your blog in 3 different web browsers and
I must say this blog loads a lot faster then most. Can you suggest a good hosting provider at
a reasonable price? Kudos, I appreciate it!
cialis generic 5mg Items in italics indicate items I suspect were cited due to inclusion in eCommons, bolded are items I can prove were cited due to inclusion in eCommons
In addition, we provide paid what is a part Time job
off and other sources to strengthen your well-being.
Can I simply say what a comfort to discover somebody who truly knows what they are discussing on the net.
You definitely understand how to bring an issue to light and make it important.
More and more people should check this out and understand
this side of your story. I can’t believe you aren’t more popular since
you certainly possess the gift.
Играть в казино Селектор бесплатно
и без регистрации могут все пользователи, которые достигли 18 лет.
Also visit my web-site: казино Friends официальный сайт вход
I’d like to thank you for the efforts you have put in penning this site.
I really hope to check out the same high-grade
content by you later on as well. In truth, your creative writing abilities has inspired me to get my
very own blog now 😉
Wonderful beat ! I would like to apprentice while you amend
your web site, how can i subscribe for a weblog site?
The account helped me a acceptable deal. I had been a little
bit familiar of this your broadcast offered bright clear idea
When I originally commented I clicked the “Notify me when new comments are added” checkbox
and now each time a comment is added I get three e-mails with the same comment.
Is there any way you can remove me from that service?
Thank you!
It’s not $14,000 like our improved-ranked Las Atlantis,
but you do get a fair chanc at meeting thhe 25x wagering needs.
my blog; online casino
Greetings! Very useful advice in this particular
post! It’s the little changes that make the greatest changes.
Thanks a lot for sharing!
I like looking through an article that can make men and women think.
Also, thanks for allowing for me to comment!
Good day I am so glad I found your website, I really found you
by accident, while I was searching on Google for something
else, Nonetheless I am here now and would just like to say
thanks for a incredible post and a all round entertaining
blog (I also love the theme/design), I don’t have time
to read it all at the moment but I have book-marked it and also added your RSS feeds, so when I
have time I will be back to read much more, Please do keep up the awesome work.
What’s up, constantly i used to check web site posts here early
in the daylight, because i like to learn more and more.
This piece of writing will assist the internet viewers for setting up
new blog or even a weblog from start to end.
My spouse and I stumbled over here different page and thought I should check things out.
I like what I see so now i am following you.
Look forward to finding out about your web page for a second
time.
Ежедневно проходит 12 событий с взносами от 50 до 800 и гарантиями от 1000 до (китайских юаней).
Feel free to visit my blog … ggpokerok официальный сайт
В свой канал можно пригласить до 200 человек из
телефонной книги.
Stop by my web site – блог
WOW just what I was searching for. Came here by searching for bulk ammo store europe
Everything is very open with a precise explanation of the issues.
It was truly informative. Your site is extremely helpful.
Thanks for sharing!
Also visit my web site: Power Pack Testo
This post provides clear idea designed for the new viewers of blogging, that actually how to do blogging and site-building.
I got this web site from my friend who shared with
me on the topic of this web page and at the moment this time I am visiting this web site and reading very informative content here.
Helllo there! I know this is somewhat off topic but I was wondering if you knew where I could locate a captcha
plugin for my comment form? I’m using the same blog platfrm as yours and I’m having problems finding one?
Thanks a lot!
IMPLANTATION – The embedding of the fertilized egg in the lining of the uterus. buy clomid online south africa
It is usually wise to install your solar panels at an perspective that will increase their exposure to
by far the most sunshine each day. Check up on them typically to make sure that you
can find no trees and shrubs growing and obstructing your individual panels from getting sun rays.
Hi there are using WordPress for your site platform?
I’m new to the blog world but I’m trying to get started and set
up my own. Do you require any html coding expertise to make your own blog?
Any help would be greatly appreciated!
bookmarked!!, I really like your blog!
Currently it seems like Expression Engine is the best blogging platform out there right now.
(from what I’ve read) Is that what you are using on your blog?
I’m not sure exactly why but this web site is loading extremely
slow for me. Is anyone else having this problem or is it a issue on my end?
I’ll check back later on and see if the problem still exists.
Handling your time more effectively could be a
highly effective way of getting Smile movie. This Smile 2021 could be wiped out if you are taking the straightforward work of your energy managing.
By preparing activities ahead of time, staying on your schedule and working with the time control resources you see the most
efficient, you may get every little thing accomplished without having sensation Smile
or stressed.
I enjoy, cause I found just what I used to be having a look for.
You have ended my 4 day long hunt! God Bless you man.
Have a nice day. Bye
dfg
Hello would you mind letting me know which hosting company you’re
using? I’ve loaded your blog in 3 different browsers and I must say this blog loads a lot quicker then most.
Can you recommend a good internet hosting provider at
a fair price? Thank you, I appreciate it!
I really love your blog.. Pleasant colors & theme. Did you make this amazing site yourself?
Please reply back as I’m planning to create my own personal site
and would like to learn where you got this from or exactly what the theme
is named. Appreciate it!
In these women, mean first-trimester serum free T concentrations were significantly lower in the metformin group n 30 , compared with the control group n 15 1. clomid pills I took myo-inositol this whole month 3 750mg pills twice a day and I also drank bragg s apple cider vinegar supposed to help with cysts and alkaline the body.
Many thanks. I like this.
descriptive essay writing write my essay custom speech writing
Минимальная сумма выплаты составляет 50 рублей.
Here is my web site казино friends
Nicely put. Thanks!
proper heading for college essay writing informative essays writing assignments service
Beneficial tips. Thanks.
pharmacy northwest canada canadian pharmaceuticals online pharmacy without prescription
Wow, that’s what I was looking for, what a stuff! existing here at this web site, thanks admin of this site.
Thanks for another informative site. Where else may just
I am getting that kind of information written in such an ideal way?
I’ve a challenge that I’m simply now working on, and I’ve been at the look out for such
info.
xenical without a prescription
First off I want to say great blog! I had a quick question in which I’d like to ask if you don’t mind.
I was curious to find out how you center yourself
and clear your mind before writing. I’ve had difficulty clearing my thoughts
in getting my ideas out there. I do take pleasure in writing but it just seems like the
first 10 to 15 minutes are usually wasted simply just
trying to figure out how to begin. Any recommendations or tips?
Thank you!
My site; vandalism
Regards! Helpful stuff.
what to write in a college essay easy essay writer assignment writing services
Nicely put. Regards.
canadian pharmacies online pharmacy online online canadian pharcharmy
You’ll additionally get a free copy of your credit report — examine it
and keep in contact with the credit score bureaus till they appropriate any
fraudulent expenses or accounts you discover there.
Bank card firms restrict your legal responsibility on fraudulent purchases, and you’ll
dispute false costs. A savings account that has no checks issued and isn’t linked to any
debit card might be a lot tougher for a thief to realize entry to.
If you keep a large amount of money in your primary checking account, then all
that money is vulnerable if somebody steals your debit card
or writes checks in your name. While you send mail,
use safe, opaque envelopes so no one can learn account numbers or spot checks just by holding them
as much as the light. Only use ATMs in secure, properly-lit areas, and don’t use the machine if somebody
is standing too close or wanting over your shoulder.
Useful info. Lucky me I discovered your website by accident,
and I’m surprised why this accident didn’t came about
earlier! I bookmarked it.
I’m really impressed with your writing abilities as smartly as with the structure for your blog.
Is that this a paid topic or did you modify it your self?
Anyway keep up the nice quality writing, it is uncommon to
look a nice blog like this one nowadays..
Stop by my web site; broker
Hey there! This is my first visit to your blog! We are a team of volunteers and starting a new project
in a community in the same niche. Your blog provided us valuable information to work on. You have
done a outstanding job!
Valuable write ups. Thanks.
pills viagra pharmacy 100mg canadian mail order pharmacies visit poster’s website
Beneficial information. Thanks.
essays college https://quality-essays.com/ custom coursework writing
Kami sebagai daftar bandar slot terpercaya megah 4D akan membayar berapapun keuntungan bossque.
Karena kepercayaan dan kepuasan member menjadi prioritas yang utama.
SLOT99 merupakan link daftar situs judi slot SLOT99 gacor
teranyar dengan win rate tertinggi jadi gampang untuk menang.
Disini kami membantu kalian membuat akun baru daftar
judi on-line secara gratis.
Truly tons of excellent facts.
how to write a reflective essay https://homeworkcourseworkhelps.com/ blog writing services
Wow, wonderful blog structure! How long have you been running a blog for?
you made blogging glance easy. The whole glance of your web
site is great, as neatly as the content!
Thanks in favor of sharing such a fastidious thinking, post is pleasant,
thats why i have read it completely
Good postings. Thank you.
legitimate canadian mail order pharmacies national pharmacies drugs from canada online
They anticipate to supply full entry to Google Play soon. If
you are bent on getting a full-fledged pill experience,
with entry to every raved-about app and all the bells and whistles, a Nextbook probably is not your best option for you.
Pure sine wave inverters produce AC power with the least amount
of harmonic distortion and may be the best choice; however they’re additionally sometimes essentially
the most costly. Not to fret. This text lists what
we consider to be the five greatest options for listening to CDs in your car for those who solely have a cassette
participant. So listed here are, in no specific order, the highest five options for taking part in a CD in your automotive in the event you only have a cassette-tape participant.
Whether you are talking about Instagram, Twitter or
Snapchat, social media is a trend that’s right here
to remain. Davila, Damina. “Baby Boomers Get Connected with Social Media.” idaconcpts.
Some kits come complete with a mounting bracket that allows you to fasten your portable CD
participant securely within your automobile. Perhaps
the most effective technique for listening to a CD participant in a car
with out an in-sprint CD player is by the use of an FM modulator.
Regards, Loads of data!
how to write an illustration essay how to write an argument essay help with writing a dissertation
Thank you, Wonderful information!
custom essays cheap essay writing service reviews technical writing service
Cheers! Helpful stuff.
canadian pharmacies top best best online international pharmacies overseas pharmacy forum
Helpful stuff. Many thanks.
canadian pharmacy walgreens online pharmacy canadian pharmacies top best
Wonderful info, Thanks a lot!
writing essays for money great college application essays top 10 dissertation writing services
Hey exceptional website! Does running a blog like this require a great deal of work?
I’ve no knowledge of programming however I was hoping to start my own blog soon. Anyways,
if you have any recommendations or techniques for new blog
owners please share. I know this is off topic but I
just had to ask. Kudos!
Hi there everyone, it’s my first pay a visit at this site,
and article is truly fruitful for me, keep up posting these posts.
Incredible a lot of fantastic information.
college graduate essay essay typer pay for writing an essay
Link exchange is nothing else but it is simply placing the other person’s weblog link on your
page at proper place and other person will also do same in favor of you.
nolvadex for pct 4 , 6 Letrozole is not approved for infertility in Canada.
Hi there to all, it’s really a fastidious for me to pay a quick visit this web site, it contains useful Information.
My page … states
Your style is unique compared to other folks I’ve read stuff from.
Thanks for posting when you’ve got the opportunity, Guess I’ll just book mark
this web site.
Really quite a lot of terrific data!
humana online pharmacy online medicine order discount canada pharmacies/account
Make an effort to communicate to people as much text messaging as possible through electronic mail.To put it briefly, decide to
go digital in any respect it is possible to.
You explained that effectively!
how to write an essay for college application how to write a scientific essay articles writing service
Reliable knowledge. With thanks.
essays on college education https://homeworkcourseworkhelps.com/ cheap custom essay writing services
As Bovada is primarily a sportsbook, the availability oof live sports andd horse
racing is the highlight here.
Feel free to surf too myy website … borgataa online casino;
Lesli,
In a whirlwind decision by theWyoming Gaming Commission, sports betting with BetMGM is now legal in the Equality State!
my siote – casino online
What’s up everyone, it’s my first pay a visit at this web site, and article is genuinely fruitful in favor of me, keep up posting these articles.
What i do not understood is in reality how you are now not actually a lot more smartly-liked than you may be now.
You’re so intelligent. You understand thus significantly
relating to this subject, produced me individually imagine it from so many various angles.
Its like men and women are not interested except it is something to
accomplish with Lady gaga! Your individual stuffs nice.
At all times handle it up!
Individuals should be cautioned that they may anticipate nausea or diarrhea on beginning metformin. clomid vs nolvadex for pct I have been on this medication for low testosterone levels for 3 years and it works better than Testosterone injections and is a cheaper medication.
These are really great ideas in about blogging. You
have touched some good factors here. Any way keep up wrinting.
Superb content, Cheers!
esl essay writing https://orangepornhub.com/ thesis writers services
You typically want to hold a bachelor’s degree in a finance-focused field, such as accounting, to
be competitive for these jobs.
My page garrett7529g.bloggactif.Com
Fantastic info. Many thanks!
writing a reflection essay how to write an argument essay affordable essay writing service
Nicely put. Kudos!
write my essay best custom essay sites homework writing services
It’s the best time to make some plans for the future and it’s time to be happy.
I have read this post and if I could I wish to suggest you some interesting things or advice.
Maybe you could write next articles referring to this
article. I desire to read even more things about it!
Awesome advice. With thanks!
canada pharmaceuticals online generic no prescription pharmacy online medicine shopping
I don’t know if it’s just me or if everybody
else encountering problems with your blog. It appears as if some
of the text on your content are running off the screen. Can someone else please provide feedback and let me know if this is happening to them too?
This might be a issue with my internet browser because I’ve had this happen before.
Cheers
Thank you! Plenty of forum posts.
canada online pharmacy viagra canada pharmeasy
Quality posts is the secret to be a focus for
the users to go to see the website, that’s what this web page is providing.
Hmm is anyone else experiencing problems with the images on this blog loading?
I’m trying to find out if its a problem on my end or if it’s the blog.
Any suggestions would be greatly appreciated.
You said it nicely.!
where can i buy essays online https://englishessayhelp.com/ writing services canada
Wow quite a lot of helpful information!
write my essay.com https://essayssolution.com/ academic ghostwriting services
Great post, I believe blog owners should
acquire a lot from this web site its really user friendly.
So much good information on here :D.
Look into my website … Meaningful Youth Skin
Fine data. With thanks.
online discount pharmacy online pharmacy canada medication costs
Hi I am so excited I found your web site,
I really found you by error, while I was looking on Aol for something else,
Anyways I am here now and would just like to say kudos for a
remarkable post and a all round interesting
blog (I also love the theme/design), I don’t have
time to go through it all at the moment but I have saved it and also added in your RSS feeds, so when I have time I will be back
to read much more, Please do keep up the excellent work.
Whoa loads of fantastic data!
writing an autobiography essay essay writing competitions letter writing help online
Do you have a spam issue on this site; I also am a blogger, and I was wanting to know your situation; many of us have developed some nice practices and we
are looking to exchange strategies with others, please shoot me an e-mail if interested.
Very nice post. I just stumbled upon your weblog and wished to say that
I’ve truly enjoyed surfing around your blog posts.
In any case I will be subscribing to your feed and I hope you write again soon!
Hello! This is kind of off topic but I need some
advice from an established blog. Is it hard to set up your own blog?
I’m not very techincal but I can figure things out pretty fast.
I’m thinking about creating my own but I’m not sure where to begin. Do you have any ideas or suggestions?
Thanks
Enjoyed examining this, very good stuff, appreciate it.
my homepage :: Uno CBD Gummies Review
Regards, A good amount of facts.
essay about military service essays writing service dissertation writing help
What’s up everyone, it’s my first visit at this web
page, and article is actually fruitful in favor of me, keep up
posting these types of articles or reviews.
Do you mind if I quote a few of your articles as long as
I provide credit and sources back to your webpage?
My website is in the very same area of interest as yours and my users would certainly benefit from a lot of the information you provide here.
Please let me know if this okay with you. Thank
you!
Hi, i think that i saw you visited my website thus i
came to “return the favor”.I’m attempting to find things to
improve my site!I suppose its ok to use a few of your ideas!!
Good way of telling, and nice piece of writing to get information regarding my presentation subject, which i
am going to convey in college.
Feel free to visit my web page: Juvli Face Cream
https://w-prodentim.com
And that is a single of the most optimistic estimates on Wall Street, he noted.
Feel free to visit my blog … Hitadverts.Com
Thank you. Useful stuff.
canadian pharmacy review pharmacies shipping to usa canadian drugs without prescription
I love your blog.. very nice colors & theme. Did you
create this website yourself or did you hire someone to do it for you?
Plz respond as I’m looking to design my own blog
and would like to find out where u got this from.
appreciate it
I used to be able to find good info from your
articles.
There’s certainly a lot to know about this topic. I really like
all of the points you made.
Wonderful post but I was wanting to know if you could
write a litte more on this topic? I’d be very grateful if you could elaborate a little
bit more. Thank you!
Wonderful beat ! I wish to apprentice even as you amend your
website, how could i subscribe for a weblog website?
The account aided me a applicable deal. I had been tiny bit acquainted of this your broadcast
provided vivid clear idea
My web page – ZapLamp Zapper
Good facts. Thanks a lot.
prescription online pharmacie online pharmacies of canada
Rattling informative and fantastic complex body part of content
material, now that’s user friendly (:.
My homepage: Bio Life Keto
Sweet blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed
in Yahoo News? I’ve been trying for a while but I never seem to get there!
Many thanks
Nicely put, Cheers.
college essays.com https://agbsl.pro/ book report writers
Thank you, Excellent information.
pills viagra pharmacy 100mg viagra generic online pharmacy overseas pharmacy forum
Thanks a lot, I value this.
canadian pharcharmy onlinecanadian online pharmacy discount prescription drugs online canadian pharmaceuticals online reviews
Right here is the right web site for everyone who would like to understand this topic.
You know so much its almost tough to argue with you (not that I actually will need to…HaHa).
You definitely put a new spin on a subject that has been written about for a long time.
Great stuff, just wonderful!
Amazing posts. Thank you.
best website to buy essays please write my essay for me medical personal statement writing service
Everything is very open with a very clear description of the challenges.
It was definitely informative. Your site is useful.
Thanks for sharing!
fantastic put up, very informative. I wonder why the opposite experts of this sector don’t realize this.
You must proceed your writing. I’m sure, you’ve a great readers’ base already!
I got this site from my friend who shared with me on the
topic of this web page and at the moment this time I am visiting this web
page and reading very informative posts at this place.
Thanks a lot for being the tutor on this niche. My partner and i enjoyed your current article quite definitely and
most of all preferred the way in which you handled the issues I regarded as controversial.
You’re always incredibly kind towards readers much like
me and assist me to in my life. Thank you.
Also visit my website: Patriot Detox Tea Reviews
You have made your stand extremely effectively.!
pharmacy technician classes online free canada pharmacy no prescription safeway pharmacy
Hi there! I simply would like to give you a huge thumbs
up for your great info you have got here on this post.
I am coming back to your blog for more soon.
Gambling gamblers, roulette tips – online casino american express deposit.
Hello! Do you know if they make any plugins to safeguard against
hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any suggestions?
f Representative pictures demonstrating the buccal capsule as differentiator for L4 larvae and adult worms. doxycycline hyclate 100mg cap
Today, I went to the beach front with my
children. I found a sea shell and gave it to my 4 year old daughter and said
“You can hear the ocean if you put this to your ear.” She placed the
shell to her ear and screamed. There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is totally off topic but I had to tell someone!
For hottest information you have to visit web and
on the web I found this web site as a best site for latest updates.
I always used to read piece of writing in news papers but
now as I am a user of net so from now I am using net for content, thanks to web.
Don’t manage your dish-washer except if it is
filled to potential.It will utilize the identical quantities of normal water
or Bullet Train imdb even though a single meal is within it.
If you do use the dishwasher, make sure to use the energy saving setting, that enables
the atmosphere-drying out of your respective recipes.
Thanks. Plenty of knowledge!
visit poster’s website pharmacy online us pharmacy no prior prescription
Good post! We will be linking to this particularly great article on our website.
Keep up the good writing.
I visited many sites except the audio feature
for audio songs current at this website is really excellent.
Ahaa, its fastidious conversation concerning this paragraph at
this place at this web site, I have read all that, so now me also commenting here.
Cheers, Ample postings!
buy medication without an rx north west pharmacy canada prescription drugs without prior prescription
Useful stuff. Thank you.
essays writing services writing my essay online assignment writing help
I’d like to find out more? I’d like to find out some additional
information.
Spot on with this write-up, I honestly believe that this site
needs far more attention. I’ll probably be back again to see more, thanks for the advice!
doxycycline side effects in dogs My goal is to introduce you to products that will see you through thick and thin, and then some.
Truly many of amazing information!
pharmacy cheap no prescription prescription drugs from canada national pharmacies
One of the toughest things about sending greeting playing cards or items is discovering the precise
one. Just a word of warning, give attention to him, not on you.
Terrific data, Many thanks.
harvard college essay writing an argumentative essay powerpoint doctoral dissertation writing service
“Since launching tthe campaign we have 71 accepted gives –
30from Orlando and 41 from Central New York,” Barkin stated in an email.
My web blog: online casino
Seriously lots of good info.
pharmacies shipping to usa costco pharmacy pricing canadian pharmacies that ship to us
You actually reported it really well.
how to write a well written essay well written college essays writers needed
Wow that was odd. I just wrote an very long comment but after I clicked submit
my comment didn’t appear. Grrrr… well I’m not writing all that over again. Anyway, just
wanted to say wonderful blog!
I was suggested this blog by my cousin. I’m not sure whether this post is written by him as
nobody else know such detailed about my problem.
You’re wonderful! Thanks!
Numbers have been drawn for the Powerball
Wednesday evening, which hhas an estimated $580 million jackpot.
Feel free to visit my blog … read more
Very good facts. Regards!
navarro pharmacy miami canadian pharmacy drugs online discount pharmaceuticals
Thanks for finally writing about > CONFIGURING SSL AUTHENTIFICATION – Benson Yerima Juvli
Cream
Cheers! An abundance of write ups!
college application essay titles write my essays trusted essay writing service
Hey, you used to write excellent, but the last several posts have been kinda boring?
I miss your super writings. Past several posts are just a little out of track!
come on!
My site: florida yachts
Nicely put. Many thanks.
prescription online list of legitimate canadian pharmacies canada pharma limited llc
History has proven that many online retailers will post a few of their finest sales on Tuesday.
Here’s our easy diy birthday present ideas!
It’s awesome to pay a quick visit this site and reading the views
of all mates regarding this article, while I
am also zealous of getting know-how.
non prescription ed drugs carprofen without vet prescription
That is, should you bet every thing at once on a single or accumulator bet,
the coefficient just isn’t specified.
My blog post events (https://rdvault.io/)
Nicely put. Kudos!
cheap drugs online shoppers drug mart pharmacy canada drugs pharmacy online
Many thanks, Numerous facts!
the best college essays write my essays cheap resume writing services
Backed up by the most recent encryption engineering in the continuing business,
2007.
Black Adam review is well-known in individual residences and company proprietors likewise.
Why haven’t you using Black Adam? If you are considering finding
out what solar power can do for yourself, this short article can help you.
Keep reading to discover Black Adam update.
Truly a lot of superb information!
best online pharmacy walgreens online pharmacy prescription discount
A delicious mild smoke that draws smoothly,
burns evenly and has consistant flavor all thru the smoke..
Also visit my web page: 바카라사이트; Janet,
Really many of beneficial tips.
top ten essay writing services custome essay custom report writing service
Canadian players can also roll with Visa, Mastercard, Interac,
and iDebit.
my webpage :: Elvia
Appreciate it, A good amount of stuff!
canadian pharmacies shipping to usa pharmacy on line best online pharmacies canada
Whoa lots of fantastic material.
college essay on leadership write my essays web copywriting services
Poker, blackjack, baccarat, and roulette are all ooffered inn live
formats.
Here is my website mgm online casino; Niamh,
Hi! Someone in my Facebook group shared this website with
us so I came to look it over. I’m definitely enjoying the
information. I’m book-marking and will be tweeting this to my followers!
Terrific blog and great design and style.
Also visit my webpage Guiletta Cream Reviews
Wonderful beat ! I would like to apprentice at the same time as you amend your
site, how can i subscribe for a blog web site?
The account aided me a appropriate deal. I have been a little bit
acquainted of this your broadcast provided
vivid transparent concept
Also visit my blog – Remedy Hills Mushroom Gummies Review
Every weekend i used to pay a quick visit this web site, because i
wish for enjoyment, since this this site conations
genuinely nice funny data too.
Acquire a minimum of a 5 minute split every 60 minutes you operate or which means that your brain can rejuvenate alone.
You will then be able to retain the details.
This design is steller! You obviously know how to keep a reader amused.
Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!) Fantastic job.
I really loved what you had to say, and more than that, how you presented
it. Too cool!
Heya i am for the first time here. I came across this board and I find
It really useful & it helped me out much. I hope to present something again and aid others like you helped me.
Here is my web page :: Derma ProX Anti Aging Cream
It’s really a cool and useful piece of information. I’m glad that
you just shared this helpful information with us.
Please keep us informed like this. Thanks for sharing.
Hello.This article was really motivating, especially since I was browsing for thoughts on this issue
last Tuesday.
Here is my web blog … Accel Brain Booster Reviews
You’re so interesting! I don’t suppose I have read through anything like that before.
So wonderful to discover another person with genuine thoughts on this topic.
Really.. thank you for starting this up. This web site is something that is required on the web,
someone with a little originality!
Hey! This is my first comment here so I just wanted to give a quick shout
out and say I genuinely enjoy reading your articles. Can you recommend
any other blogs/websites/forums that cover the same topics?
Thanks a ton!
Thanks for sharing your thoughts. I really appreciate your efforts and I am waiting for your next post thanks once
again.
Also visit my web page – Lean Ready Keto Review
Hello.This article was extremely motivating, especially since I was searching for thoughts on this
topic last Monday.
Also visit my website: Accel Brain Booster Reviews
Hi! I simply would like to give you a big thumbs up for your great information you have got
here on this post. I am coming back to your web site for more soon.
my blog True Body Keto Review
This design is wicked! You certainly know
how to keep a reader entertained. Between your wit and
your videos, I was almost moved to start my own blog (well, almost…HaHa!) Excellent job.
I really loved what you had to say, and more than that, how you presented it.
Too cool!
Also visit my homepage … car
I am really impressed with your writing skills and also
with the layout on your blog. Is this a paid theme or did you
modify it yourself? Anyway keep up the nice quality writing, it is rare to see a great blog like this
one these days.
Even games with a low residence edge such as blackjack and video poker
havbe a built-in casino benefit known as tthe property edge.
Here is my website – 바카라사이트 (Caroline)
Great data. Thank you!
northwest pharmacy canada pharmacies in canada pharmacy intern
As I web-site possessor I believe the content matter here is rattling wonderful , appreciate
it for your efforts. You should keep it up forever!
Best of luck.
Here is my blog :: Truly Keto Max ACV Gummies
Шесть видов популярной игры представлены в
разных вариациях исполнения.
my webpage :: arvindexports.Com
Regards, Ample forum posts.
best online essay editing service essay writings medical residency personal statement writing services
Предусмотрен рейтинг пользователей,
постарайтесь возглавить его, занять первое место.
Visit my homepage: скачать покердом на Android
Excellent, what a webpage it is! This weblog presents valuable information to us, keep it
up.
Больше того, тут предусмотрены Chinese Poker, открытый китайский
и формат быстрого покера, а также смешанные игры и турниры Sit-and-Go.
Check out my blog post: Sanford
I love your blog.. very nice colors & theme. Did you make this website yourself
or did you hire someone to do it for you? Plz respond as I’m looking to construct my own blog and would like to find out where u got
this from. kudos
Thanks for every other informative blog.
The place else may I get that type of information written in such an ideal manner?
I have a venture that I’m simply now running on, and I’ve
been at the glance out for such info.
Feel free to visit my blog post – Turbo Chill Max Portable AC
great publish, very informative. I ponder why the other
specialists of this sector don’t realize this. You must
proceed your writing. I’m sure, you’ve a huge readers’ base already!
Fantastic data. Regards!
viagra from canada discount prescription drugs online prescription drugs online without
Valuable information. Many thanks!
custom college essays write my essay website write my assignment
When I originally left a comment I seem to have clicked on the
-Notify me when new comments are added- checkbox and now every time a comment is added I receive 4 emails with the exact
same comment. There has to be a way you can remove me from that service?
Cheers!
Hello There. I discovered your weblog using msn. This is a very neatly written article.
I will make sure to bookmark it and come back to learn more of your helpful info.
Thank you for the post. I’ll definitely return.
I always was interested in this subject and stock still am, appreciate it for putting up.
certainly like your website but you need to check the spelling on several
of your posts. Many of them are rife with spelling problems and I to find it very troublesome to inform the truth nevertheless I will definitely come back
again.
Hi there, just became aware of your blog through Google, and found that it’s truly informative.
I am going to watch out for brussels. I will be grateful if you
continue this in future. Many people will be benefited from your writing.
Cheers!
I have been exploring for a bit for any high quality articles or
blog posts on this kind of space . Exploring in Yahoo I finally
stumbled upon this web site. Studying this info So
i’m glad to exhibit that I have an incredibly just right uncanny feeling I
came upon just what I needed. I such a lot indisputably will
make sure to do not forget this website and give it a glance regularly.
prodentim
Position effectively utilized!!
hire essay writer help with scholarship essays professional article writing services
At this moment I am going to do my breakfast,
once having my breakfast coming again to read more news.
Superb advice. Regards.
online medicine shopping canadian prescription drugstore canada discount drug
We stumbled over here by a different web address and thought I might check
things out. I like what I see so now i am following you. Look forward to checking out your web page for a second time.
canadian pharmacy antibiotics canadian discount pharmacy
You revealed this effectively.
college essay scholarships best essay writing service website need essay written
I like the valuable information you provide in your articles.
I will bookmark your blog and check again here frequently.
I am quite certain I’ll learn lots of new stuff right here!
Best of luck for the next!
Very descriptive blog, I enjoyed that a lot. Will there be a part 2?
wp themes
Thanks, Good stuff.
best 10 online canadian pharmacies canada drug prices canadian pharma companies
You can definitely see your enthusiasm in the work you write.
The world hopes for more passionate writers like you who are not afraid to say how they believe.
Always go after your heart.
Это помогает букмекеру проверить, все ли в порядке, и защитить как свою систему, так и клиентов.
Stop by my blog post: пин ап вход
Thanks, Useful stuff!
best college essay write my essays ghostwriter needed
wealth dna code
There are also other specialized bonuses, which includes Friday Deposwit and Monday and Friday 50% deposits.
My page: zone online casino
Good postings. Many thanks.
reputable canadian mail order pharmacies canadian pharmaceuticals online reviews best price prescription drugs
Remarkable! Its actually remarkable piece of writing, I have got much clear idea concerning from this
article.
I am in fact delighted to glance at this web site posts which includes lots of useful facts, thanks for providing these kinds of data.
Stop by my blog post Trim Drops Keto Gummies
hello there and thank you for your info – I’ve definitely picked up anything new
from right here. I did however expertise some technical issues using this
site, as I experienced to reload the website lots of times previous to I could get it to load properly.
I had been wondering if your hosting is OK?
Not that I’m complaining, but slow loading instances times will sometimes affect
your placement in google and could damage your high quality score if advertising and
marketing with Adwords. Anyway I am adding this RSS to my e-mail and
could look out for much more of your respective fascinating content.
Make sure you update this again soon.
Also visit my web blog :: 사다리 홀짝
I always was concerned in this subject and stock still am, thanks for putting up.
Also visit my blog – Keto 24/7
I just now wanted to thank you yet again for your amazing web-site you have built here.
It really is full of useful tips for those who are definitely interested in that subject, specifically this very post.
Your all so sweet along with thoughtful of others as well as reading your blog posts is a great
delight in my experience. And what generous present!
Tom and I are going to have fun making use of your suggestions in what we need to
do in the future. Our checklist is a kilometer
long so your tips might be put to fine use.
Feel free to visit my webpage … IQ Brain Blitz Reviews
Kudos. Awesome stuff.
essay for college admission best essay writing service canada write my report free
Simply desire to say your article is as amazing.
The clearness for your post is simply nice and i can assume
you’re an expert in this subject. Fine together with your permission allow me to snatch your RSS feed to
stay updated with imminent post. Thanks 1,000,000 and please
continue the rewarding work.
Thanks a lot! Plenty of postings.
how to write an essay introduction college applications essays best online writing service
Your mode of describing the whole thing in this piece of writing is in fact good, every one be able
to effortlessly be aware of it, Thanks a lot.
Also visit my website – Peak Keto
Wonderful postings. Appreciate it!
best canadian pharmacies canadian prescription drugstore canada drug
I was honored to obtain a call from a friend immediately he observed the important suggestions shared on your site.
Browsing your blog article is a real great experience.
Thanks again for thinking of readers just like me, and I desire for you the best of achievements for a professional in this
field.
my blog Remedy Hills Lion’s Mane Gummies
Thanks a lot. An abundance of tips.
canadian pharmacy generic viagra canadian online pharmacies prescription drugs canada pharmacies prescription drugs
amoxicillin buy no prescription bactrim without prescription
Just want to say your article is as astounding.
The clarity in your submit is simply cool and that
i could suppose you are a professional in this subject.
Fine together with your permission let me to clutch your
RSS feed to stay up to date with imminent post.
Thank you 1,000,000 and please keep up the
gratifying work.
We’re a group of volunteers and opening a new scheme in our community.
Your website offered us with valuable info to work on. You
have done a formidable job and our entire community will be thankful to you.
Hi there to all, the contents present at this site are really remarkable for
people experience, well, keep up the nice work fellows.
Thanks for the marvelous posting! I certainly enjoyed
reading it, you happen to be a great author.I will remember to
bookmark your blog and will often come back in the future.
I want to encourage one to continue your great work, have a nice morning!
My brother recommended I may like this blog. He used to be entirely right.
This submit actually made my day. You can not consider just how so much time I had
spent for this information! Thank you!
Oh my goodness! Impressive article dude! Thank you so much, However I am going
through difficulties with your RSS. I don’t know the reason why I can’t subscribe to it.
Is there anyone else having identical RSS problems? Anyone who knows the answer will you kindly respond?
Thanx!!
What’s up it’s me, I am also visiting this
web site on a regular basis, this web site is truly pleasant and the people are really sharing good thoughts.
Very interesting details you have noted, regards for putting
up.
Review my site Remedy Hills Lion’s Mane Mushroom Gummies
В дополнительной росписи и рынках на статистику маржа повышается самого 5-7, 5% и зависимости от маркета.
Have a look at my web-site :: pin up bet
Battles encompass so many various sorts of themes, from international country themes to pop-culture themes.
Feel free to visit my blog: Mr bet online casino
—February 10 – The Nets $1.7 million Traded Player Exception generated by the
Paul Millsap element of the 76ers trade expires.
Also visit my site :: Augustus
I like this site very much so much good info.
Review my site … Envy Fit Keto
Every weekend i used to pay a quick visit this site, as i want enjoyment, since this this site conations truly fastidious funny information too.
Also visit my homepage … Anaboloxan Reviews
In Game 2, Philadelphia evened the series with a 115–106 win annd then wenjt
on to win Gamkes three and 4.
mywebpage :: dicks sporting goods
I am actually grateful to the owner of this website who has shared this great post at
here.
Hi, its fastidious post concerning media print, we all be aware of media is a wonderful source
of information.
I am truly grateful to the holder of this site who has shared this
impressive piece of writing at at this time.
Find out how existing consumers located you. Use Yahoo Stats tracking to determine which web page they has
come from. Performed they are available from social media internet sites?
Was there a selected online community that drove the targeted traffic to you?
No mater the route, you can find methods for getting much more sales opportunities.
Hey there I am so thrilled I found your blog, I really found you by accident, while I
was researching on Digg for something else,
Nonetheless I am here now and would just like to say thanks a lot for a remarkable post and a all round entertaining blog (I also love the
theme/design), I don’t have time to read through it all at the minute
but I have saved it and also added your RSS feeds, so when I have time I will be back to read much more, Please do keep up the excellent work.
Hi there, I enjoy reading through your article post.
I wanted to write a little comment to support you.
I simply had to thank you so much once more. I am not sure the things I could possibly have implemented in the absence of the type
of recommendations contributed by you concerning that field.
It was actually a real terrifying crisis in my circumstances, nevertheless taking note of the very well-written manner you resolved that took me to leap
over delight. I am just happier for your guidance and then wish you really know what an amazing job
you happen to be putting in educating people today thru your web site.
More than likely you haven’t encountered all of us.
Take a look at my homepage :: Focus Q Elite Cognitive Support
is canadian pharmacy legit canadian pharmacies online
Hello, i think that i saw you visited my site so i came to “return the favor”.I’m attempting to find things
to enhance my site!I suppose its ok to use a few of your ideas!!
I like it whenever people get together and share opinions.
Great website, stick with it!
You will find out a range of blackjack, roulette, baccarat, and poker in the table games
category.
Feel free to surf to my webpage; Cinda
We’re all about receiving actionable insights
from your visual data.
My website; blog – Leland –
You could certainly see your skills within the
work you write. The sector hopes for more passionate writers such
as you who aren’t afraid to say how they believe. Always follow your
heart.
Also visit my web site :: True Boost Keto Reviews
When I initially commented I seem to have clicked on the -Notify me when new comments are
added- checkbox and from now on each time a comment is added I
get four emails with the same comment. Is there a means you are able to remove me from that service?
Thank you!
my site; Whole word reading Activities
Wow, awesome blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your
web site is great, as well as the content!
Also visit my web blog: Binary Options Trading Strategy With Candlesticks Stocks
เล่นบาคาร่าสุดเทพกะสล็อต888เล่นบาคาร่า888เดิมพันออนไลน์สล็อตpgเกมส์ สล็อตเล่นคาสิโนออนไลน์777แทงเว็บ ตรง สล็อตเดิมพันสูตร บาคาร่าแทงสล็อต เว็บตรงไม่ผ่านเอเย่นต์ไม่มีขั้นต่ำวัดดวงสล็อต แตก
งายเล่นสล็อต เครดิตฟรี ไม่ต้องฝากก่อน ไม่ต้องแชร์ ยืนยันเบอร์โทรศัพท์วัดใจสล็อตpg ทดลอง เล่นวัดสล็อต ฝากถอน true
wallet ไม่มี บัญชีธนาคารเทรดสล็อต
88วัด789 สล็อตจัดสล็อต เครดิตฟรี ล่าสุดแทงสล็อต ยืนยันเบอร์โทร รับเครดิตฟรี ล่าสุด ฟรี2021แทงทดลอง เล่น สล็อต pg ฟรี 2022เดิมพันเกม สล็อต แตก ง่ายแทงสนุกซุปเปอร์ สล็อต v9v9เดิมพันสล็อต 456เดิมพันสล็อต เครดิต ฟรี
50 ไม่ ต้อง แชร์2021ล่าสุด
Hello, I check your new stuff on a regular basis.
Your story-telling style is witty, keep doing what you’re doing!
Большинству игроков в покер-руме нравятся турнирные серии,
а также наличие китайского покера.
Also visit my web blog покердом официальный сайт
When some one searches for his vital thing, thus he/she wishes to be available that in detail,
thus that thing is maintained over here.
Feel free to visit my blog – Ketorganix Keto Reviews
В нем сразу же можно пройти регистрацию, если нет аккаунта в игровом клубе.
Also visit my site … Pokerdom apk последняя версия
I think this is one of the such a lot significant info for me.
And i am happy reading your article. However want to observation on some general issues,
The web site style is wonderful, the articles is truly nice : D.
Excellent activity, cheers
Thanks a lot for sharing this with all people you actually know
what you are speaking approximately! Bookmarked. Kindly
also visit my website =). We could have a link exchange contract between us
how much is amoxicillin prescription buy amoxicillin without prescription
Spot on with this write-up, I really feel this web site
needs a lot more attention. I’ll probably be back again to read more,
thanks for the information!
%%
Academy item Balogun, 21, signed a new 4-year contract last April which
runs till 2025 and remains a part of manager Mikel Arteta’s
extended-term plans.
Also visit my webpage Dicks Sporting Goods
Since the admin of this web page is working, no hesitation very rapidly it will be renowned,
due to its feature contents.
Here is my blog … products
Awesome things here. I’m very satisfied to peer your post.
Thanks so much and I am taking a look forward to contact
you. Will you kindly drop me a e-mail?
Be positive to preferred your group in the Ticketmaster app to get alerts as soon as tickets go on sale.
Also visit my web site; Eloy
Hi there! This blog post couldn’t be written much better!
Going through this article reminds me of my previous roommate!
He constantly kept talking about this. I’ll forward this post to him.
Pretty sure he’ll have a good read. Many thanks for sharing!
Hi my family member! I wish to say that this article is awesome, nice written and include approximately all significant infos.
I’d like to see more posts like this .
Excellent pieces. Keep posting such kind of information on your blog.
Im really impressed by your blog.
Hi there, You’ve done a great job. I’ll certainly digg it and
individually recommend to my friends. I am confident they’ll
be benefited from this web site.
I visited multiple sites except the audio
quality for audio songs present at this website is in fact superb.
Hello, i think that i saw you visited my blog so i came to ?return the
want?.I am attempting to in finding things to enhance my
site!I assume its good enough to use some of your ideas!!
Here is my web blog; Premier Naturals CBD
What’s up to all, how is all, I think every one
is getting more from this site, and your views are pleasant designed for new users.
Hello there, You have done an excellent job. I will definitely digg it and personally suggest to my friends.
I am confident they’ll be benefited from this site.
We’re a gaggle of volunteers and opening a brand new scheme in our community.
Your site offered us with useful information to paintings on. You have
done a formidable process and our entire neighborhood might be thankful
to you.
Here is my blog – Green Spectra CBD
It is not my first time to go to see this web site, i am browsing this site dailly and get fastidious information from here
daily.
Truly, wow. Forgot just how well you write and how heavily you update.
I missed that. A lot of schmucks available and most of all of them can not comment worth a damn, either.
Ya know, I have actually been actually an article writer and writing a blog
for twenty years and also I have actually never ever come
across a few of this stuff just before. Maybe that’s given that I’ve consistently performed my personal
trait.
Really did not our company speak years ago when our experts first encountered, that I strongly believed the future of writing a blog was actually going
to be located on individuals as well as certainly not search engine optimization or systems?
My homepage … account
Для пользователей сайта регулярно проходят акции, позволяющие получать различные бонусы.
Feel free to visit my page https://Avoidingplastic.com/Wiki/index.php/User:HarlanMejia8621
This design is steller! You obviously know how to keep a reader entertained.
Between your wit and your videos, I was almost moved to start my
own blog (well, almost…HaHa!) Fantastic job.
I really enjoyed what you had to say, and more than that, how you presented it.
Too cool!
Check out my web site: Revivanze Vitamin C
Good way of describing, and nice piece of writing to take data concerning my
presentation subject, which i am going to deliver in college.
Attractive component to content. I simply stumbled upon your weblog and in accession capital to claim that I
get in fact loved account your blog posts. Anyway
I will be subscribing on your feeds or even I success you get
entry to persistently rapidly.
Also visit my web page :: Curious Keto Diet
Precisely what I was looking for, regards for posting.
Also visit my web site Radiant Flawless Skin
You really make it seem so easy with your presentation but I find this
topic to be actually something which I think I would
never understand. It seems too complicated and very broad for me.
I’m looking forward for your next post, I will try to get the hang of it!
I am sure this post has touched all the internet people, its really really nice piece of writing on building up new website.
Superb post but I was wondering if you could
write a litte more on this subject? I’d be very grateful if you could elaborate a little bit more.
Thanks!
Wonderful blog! I found it while searching on Yahoo News.
Do you have any suggestions on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Cheers
Have you ever considered publishing an ebook or guest authoring on other websites?
I have a blog based on the same topics you discuss and would love to have you share some stories/information. I know
my viewers would appreciate your work. If you are even remotely
interested, feel free to send me an e mail.
It’s awesome for me to have a web page, which is helpful in favor of my know-how.
thanks admin
Candidates with B.Pharma, B.Tech/B.E, Seasoned can apply.
My blog: female jobs near me
Hey there, You’ve done a fantastic job. I’ll certainly digg it and personally recommend to my friends.
I am sure they’ll be benefited from this site.
This piece of writing is truly a fastidious one it helps new the web
visitors, who are wishing in favor of blogging.
My brother suggested I might like this website.
He was once totally right. This put up actually made my day.
You cann’t consider just how so much time I had spent for this
info! Thanks!
Please let me know if you’re looking for a author for your
blog. You have some really great posts and I feel I would
be a good asset. If you ever want to take some of the load
off, I’d really like to write some articles for your blog in exchange for a
link back to mine. Please shoot me an email if
interested. Thanks!
Also visit my web-site – Ketorganix Keto
ยินดีบาคาร่าจัดเต็มสุดๆกับสล็อต666สะใจบาคาร่าเว็บตรงจัดทดลอง เล่น
สล็อตเว็บไซต์ สล็อตแทงคาสิโนออนไลน์อันดับ1จัดสล็อต ออนไลน์วัดใจสูตร บาคาร่าเทรดสล็อต เว็บตรง ไม่ผ่านเอเย่นต์ ไม่มีขั้นต่ำเดิมพันออนไลน์เว็บตรง สล็อต ฝากถอน ไม่มี ขั้นต่ำ 1 บาทก็ ถอนได้เดิมพันออนไลน์สล็อต
โรม่าจัดเซ็กซี บาคาร่าวัดดวงทดลอง สล็อตเดิมพันออนไลน์g2gสล็อตเดิมพันออนไลน์jokerสล็อต ฝาก10 รับ100เดิมพันออนไลน์jokerสล็อต ฝาก10รับ100วัดดวงสล็อต pg เว็บตรง ไม่ผ่านเอเย่นต์
แจกโบนัสเดิมพันออนไลน์pgสล็อต888เล่นสล็อต777 คาสิโน ออนไลน์เดิมพันสุดเทพjoker
สล็อต ฟรี เครดิตวัดpxgสล็อตแทงssgame56 คาสิโน
I have read so many articles on the topic of the blogger
lovers except this article is truly a good paragraph, keep it up.
Very shortly this web page will be famous amid all blogging and
site-building users, due to it’s nice posts
Hi, I do think this is a great website. I stumbledupon it 😉 I am going to return yet again since
i have bookmarked it. Money and freedom is the best way to change, may you be rich and continue
to help others.
whoah this weblog is magnificent i love reading your articles.
Keep up the good work! You know, a lot of people are hunting round
for this info, you can aid them greatly.
Hello, I would like to subscribe for this weblog to obtain latest updates, so where can i do it please help out.
Try acquiring all the online messaging as you can via electronic mail instead of standard means.
In short, go electronic whenever you can.
Rattling fantastic information can be found on website.
Its like you read my mind! You appear to understand so
much about this, such as you wrote the e-book in it
or something. I believe that you can do with some % to force the message home a little bit, however other than that, this
is great blog. A fantastic read. I’ll certainly be back.
Look at my web-site :: Easy Burn Keto Reviews
When I initially commented I clicked the “Notify me when new comments are added” checkbox
and now each time a comment is added I get several e-mails with the
same comment. Is there any way you can remove people from that service?
Appreciate it!
Appreciate the recommendation. Will try it out.
Thank you, I’ve just been searching for info approximately this topic for
a while and yours is the greatest I’ve found out till now.
But, what about the conclusion? Are you certain in regards to the source?
These are actually enormous ideas in concerning blogging.
You have touched some good factors here. Any way keep up
wrinting.
%%
Spot on with this write-up, I absolutely believe this site needs far more attention. I’ll probably
be returning to read through more, thanks for the information!
Nice answer back in return of this issue with solid arguments and
telling everything concerning that.
Pretty great post. I just stumbled upon your weblog and
wanted to mention that I have truly enjoyed browsing your blog
posts. After all I will be subscribing on your feed and I hope you write
again very soon!
Greetings I am so grateful I found your weblog, I really
found you by error, while I was searching on Google for something else, Regardless I am here now and would
just like to say kudos for a incredible post and a all round interesting blog
(I also love the theme/design), I don’t have time to look over it all at the moment but I have book-marked it and also added in your
RSS feeds, so when I have time I will be back to read more,
Please do keep up the superb work.
Hello it’s me, I am also visiting this web page regularly, this site is
truly nice and the visitors are in fact sharing
good thoughts.
Hello there! I could have sworn I’ve been to this website
before but after looking at a few of the posts I realized it’s new
to me. Anyways, I’m definitely happy I discovered it and
I’ll be bookmarking it and checking back often!
Hi there to every body, it’s my first pay a quick visit of this website; this website contains remarkable and in fact good stuff in favor of readers.
%%
You could certainly see your enthusiasm in the article
you write. The world hopes for more passionate writers like you who are
not afraid to mention how they believe. All the time
go after your heart.
Thanks for finally talking about > CONFIGURING SSL AUTHENTIFICATION –
Benson Yerima < Loved it!
and so on.
Feel free to surf to my web-site … mostbet login
It is not my first time to go to see this site, i am browsing this website dailly and take nice information from here every day.
Having read this I believed it was extremely enlightening.
I appreciate you finding the time and energy to put this short article together.
I once again find myself personally spending a lot of time
both reading and leaving comments. But so what, it was still worth it!
Stop by my webpage – Rejuviant Vitamin C Cream
Please let me know if you’re looking for a article
author for your blog. You have some really good articles and I believe I would be a good asset.
If you ever want to take some of the load off, I’d really like to
write some articles for your blog in exchange for a link back to
mine. Please shoot me an e-mail if interested. Thank you!
Excellent write-up. I certainly appreciate this site. Keep writing!
Also visit my blog post; Juv Skin Cream Ingredients
I just like the valuable info you provide in your articles.
I’ll bookmark your blog and check once more right here frequently.
I am rather sure I’ll be informed plenty of new stuff right here!
Good luck for the next!
The Wii U uses inner flash reminiscence for
storage. There’s additionally a sync button for wireless controllers, and a small panel beneath the disc drive pops open to reveal two USB
2.0 ports and an SD card slot for expandable storage.
Wii Remote, a home button for the Wii OS, a power button, and a Tv button (extra
on that later). A single printed Zagat restaurant guide for one city prices nearly $16 retail and
doesn’t have the option to contribute your own feedback at
the touch of a button. An alternative choice is the Intuit GoPayment, from the same firm that makes QuickBooks accounting software.
The same news junkies who used to show to 24-hour cable news to get by-the-minute updates have now defected to the Internet for second-by-second
information. The GamePad can basically operate like a big Wii Remote, since it makes use of the same expertise.
While the quicker processor inside the Wii U
offers it the facility to run more complicated video
games, the real modifications in the console are all
centered on the new GamePad controller. Just like the PlayStation, the CPU in the N64
is a RISC processor.
Feel free to surf to my web site: สล็อตวอเลท
It’s appropriate time to make some plans for the future and it is time to be
happy. I’ve learn this put up and if I may just I desire to counsel you few interesting things or advice.
Perhaps you could write next articles relating to this article.
I wish to read even more things about it!
Yes! Finally someone writes about accessing medical cannabis.
Review my website :: BioLyfe CBD Gummies Review
Outstanding post but I was wondering if you could write a litte more on this
subject? I’d be very grateful if you could elaborate a little bit
further. Many thanks!
With havin so much written content do you ever run into any issues of plagorism or copyright
infringement? My blog has a lot of completely unique content
I’ve either written myself or outsourced but it looks like a lot of it is popping it up all over the internet without my
authorization. Do you know any methods to help prevent content
from being stolen? I’d definitely appreciate it.
Hi! Do you know if they make any plugins to help with SEO?
I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good
gains. If you know of any please share. Thanks!
Great post.
The tiny down load will explain whether or not your body is capable of having a Dragon Ball
Super Super Hero film. Take into account that you can always delete it afterwards
should you not know what you are undertaking.
Undeniably believe that which you said. Your favorite justification appeared to be on the web the simplest thing to
be aware of. I say to you, I certainly get annoyed while people think about worries that they just don’t know
about. You managed to hit the nail upon the top and defined out the whole thing without
having side-effects , people could take a signal.
Will probably be back to get more. Thanks
sildenafil citrate women sildenafil buy online without a prescription
The most recent big-budget disaster film was 2017’s Geostorm, which was a massive
flop for a broad variety of reasons.
I’m not sure where you are getting your info, but
great topic. I needs to spend some time learning more or understanding more.
Thanks for magnificent info I was looking for this info for my
mission.
At this time it seems like Expression Engine is the preferred blogging platform out there right now.
(from what I’ve read) Is that what you’re using on your blog?
Good blog you have here.. It’s difficult to find high-quality writing like
yours nowadays. I really appreciate individuals like you!
Take care!!
We absolutely love your blog and find almost all of your post’s to be
precisely what I’m looking for. Do you offer guest writers to write content for you personally?
I wouldn’t mind producing a post or elaborating on most of the subjects
you write regarding here. Again, awesome site!
Hi, this weekend is pleasant designed for me, for the
reason that this moment i am reading this enormous informative paragraph here at my
residence.
You actually make it seem so easy with your presentation but I find this
topic to be really something that I think I would never
understand. It seems too complicated and extremely broad for me.
I am looking forward for your next post, I’ll try to get the hang
of it!
Here is my webpage: Uncle Riley’s CBD Review
I am really enjoying the theme/design of your blog.
Do you ever run into any web browser compatibility issues?
A few of my blog audience have complained about my website
not working correctly in Explorer but looks great in Safari.
Do you have any recommendations to help fix this issue?
Look into my web-site :: Super Slim Keto Gummies Reviews
Does your site have a contact page? I’m having a
tough time locating it but, I’d like to shoot you an e-mail.
I’ve got some suggestions for your blog you
might be interested in hearing. Either way, great blog and I look forward to seeing it expand over time.
There’s definately a lot to find out about this topic.
I like all of the points you have made.
My webpage Keto ACV Gummies
Hey there, You’ve done an excellent job. I’ll certainly digg
it and personally recommend to my friends. I am sure they’ll be benefited from this
site.
That is a great tip especially to those new to the blogosphere.
Brief but very accurate info… Appreciate your sharing this one.
A must read article!
clomid vision success rate of clomid 100 mg buy cheap clomid from india without prescription
Original songs for the movie were written by govt producers Benj Pasek and Justin Paul along with Ari Afsar, Emily Gardner Xu Hall, Mark
Sonnenblick, and Joriah Kwamé.
What’s up, after reading this amazing paragraph
i am as well glad to share my knowledge here with friends.
Feel free to visit my webpage: ufa 191
I blog quite often and I really thank you for your information. This
great article has really peaked my interest. I am
going to book mark your blog and keep checking for new information about once per week.
I subscribed to your RSS feed as well.
For her part, Pugh is too vibrant, too alive and simply
too vigorously full-bodied from the get-go for a task that calls for a slow-dawning awakening.
Excellent weblog right here! Additionally your
web site loads up fast! What host are you the usage of?
Can I get your associate hyperlink in your host? I wish my site loaded up as fast
as yours lol
If some one wishes to be updated with latest technologies therefore he must be go to see this site and be up to date every
day.
Please let me know if you’re looking for a author for your weblog.
You have some really good articles and I feel I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to
write some articles for your blog in exchange for a link back to mine.
Please blast me an email if interested. Thanks!
more than ten years.
Check out my blog post – mostbet site
I take pleasure in, result in I found exactly what I was taking a look for.
You have ended my four day long hunt! God Bless you man. Have a nice day.
Bye
The hook of Black Adam is The Rock as a DC superhero or (depending on to what extent he
‘breaks good’ by the end) anti-hero.
Good post. I learn something totally new and challenging on sites I
stumbleupon every day. It will always be useful to read articles from other
writers and use a little something from other web sites.
Check out my web page: motorist
constantly i used to read smaller posts that also clear
their motive, and that is also happening with
this piece of writing which I am reading now.
Hello friends, how is all, and what you wish for to say concerning
this paragraph, in my view its genuinely remarkable designed for me.
สวัสดีสล็อตสุดมันที่สล็อตxoเล่นสล็อตทดลองเดิมพันทดลอง เล่น สล็อต pgบาคาร่า ออนไลน์เล่นคาสิโน 6699เทรดทดลอง เล่น บาคาร่าเดิมพันสล็อต 777เทรดสล็อต เว็บตรงไม่ผ่านเอเย่นต์ ไม่มี ขั้นต่ำแทงทดลอง เล่น บาคาร่าจัดสล็อต ฝาก ถอน true wallet เว็บ ตรงเล่นสล็อต 789เดิมพันออนไลน์สล็อต xo เว็บ ตรงวัดใจสมัคร สล็อตxoวัดดวงkingkongสล็อตเทรดทดลอง เล่น
สล็อตxoเทรดสล็อต ยืนยันเบอร์โทร
รับเครดิตฟรี ล่าสุด ฟรี2021วัดดวง6699 คาสิโนวัดดวงเกม สล็อต roma เล่น ฟรี ได้ เงิน จริงเดิมพันออนไลน์สุดเทพสล็อต ฝาก25รับ100เดิมพันสล็อต จี คลับ 1688เดิมพันเว็บ สล็อต168
Here is my blog; สล็อตพีจี
You could definitely see your enthusiasm within the article you write.
The arena hopes for more passionate writers such as you who are not afraid to say how they believe.
Always go after your heart.
Pretty great post. I simply stumbled upon your blog
and wished to say that I’ve really enjoyed surfing around your weblog posts.
In any case I’ll be subscribing for your rss feed and I’m hoping you write once more soon!
What’s Taking place i am new to this, I stumbled upon this I’ve found It
positively useful and it has aided me out loads.
I am hoping to contribute & aid different users like its helped me.
Good job.
Good info. Lucky me I ran across your website by chance
(stumbleupon). I have saved as a favorite for later!
Hi, every time i used to check blog posts here in the early hours in the
daylight, because i love to learn more and more.
ankara escort
Proper order of an essay http://www.jwwab.com/index.php?qa=user&qa_1=pastabagel78
ยินดีสล็อตสนุกสุดๆที่สุดกับสล็อตเว็บตรงเล่นสล็อตทดลองจัดสล็อต pgเว็บ สล็อตจัดคาสิโนออนไลน์1688เดิมพันสล็อต โจ๊กเกอร์วัดสล็อต โจ๊ก เกอร์วัดดวงบาคาร่า 1688เทรดสล็อต วอ เลทเดิมพันสล็อต โรม่าเล่นบาคาร่า ออนไลน์911เดิมพันสล็อต
เว็บตรง ฝากถอน true wallet ไม่มี ขั้น ต่ําเดิมพันเล่น สล็อตเดิมพันบาคาร่าautoจัดรวมเว็บ สล็อต
pgจัดเข้าสู่ระบบ สล็อต666วัดสล็อต 99 rachaเดิมพันสล็อต 444จัดจัดเต็มสล็อต แจก ทุนฟรี ไม่มี เงื่อนไขวัดดวงสล็อต 168 โอน ผ่าน วอ เลท ไม่มี ขั้น ต่ําวัดสล็อต ฝาก ถอน ไม่มีขั้นต่ํา แตกง่าย
Look into my website … pg slot
Bijlmermeer was the ultimate in modernist utopian urban planning, with bicycle paths, playgrounds, and high-rises built along the city’s new metro line.
%%
When someone writes an post he/she maintains the thought of a user in his/her mind that how a user can be aware of it.
Thus that’s why this article is great. Thanks!
Helpful information. Lucky me I discovered your web site unintentionally, and I’m
stunned why this coincidence did not took place earlier!
I bookmarked it.
The premier event for betting and gaming in the CIS region.
my web site – https://mediawiki.erabakerydesign.com/index.php/utilisateur:lucienne7667
Hello, i read your blog from time to time and i own a similar one and i was just curious if you get a lot of spam
comments? If so how do you reduce it, any plugin or anything you can suggest?
I get so much lately it’s driving me mad so any support
is very much appreciated.
Additionally, the games are not only enjoyable but also
profitable, and they can even earn you big money.
my website: Kristal
cheap stromectol coupons without prescription buy generic stromectol coupon no prescription is ivermectin good for rosacea
An intriguing discussion is definitely worth comment.
I believe that you need to publish more on this subject
matter, it might not be a taboo matter but typically people don’t speak about these
topics. To the next! Many thanks!!
Hi! Do youu knoᴡ if they mаke any plugins tⲟ safeguard agains hackers?
Ӏ’m kinda paranoid aboout losing everythiing І’νe worked haгd on. Any tips?
%%
This is excellent information for everyone. I get a lot of useful information. Thanks a lot. By the way, I feel happy to share a fantastic article about Putty Emulator. PuTTY is an SSH and telnet client, developed originally by Simon Tatham for the Windows platform. PuTTY is open source software that is available with source code and is developed and supported by a group of volunteers.
Hi there! Do you know if they make any plugins to
assist with Search Engine Optimization? I’m trying to get
my blog to rank for some targeted keywords but I’m not seeing very good success.
If you know of any please share. Kudos!
Hi there i am kavin, its my first occasion to commenting anyplace, when i read this paragraph i thought i could
also make comment due to this good article.
Here is my homepage: situs slot88 gacor
I was suggested this blog by my cousin. I am not sure whether this
post is written by him as no one else know such detailed about my
problem. You’re amazing! Thanks!
Hi there! Do you use Twitter? I’d like to follow you if that would be okay.
I’m undoubtedly enjoying your blog and look forward
to new posts.
Here is my site :: K2 Life CBD Gummies
We’re a bunch of volunteers and starting a new scheme in our community.
Your site provided us with valuable info to work on. You’ve performed a formidable process and our
whole community will be thankful to you.
Hi! I know this is kind of off topic but I was wondering if you knew where I could locate a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having
difficulty finding one? Thanks a lot!
Thanks designed for sharing such a pleasant opinion, paragraph
is fastidious, thats why i have read it completely
I loved as much as you’ll receive carried out right here.
The sketch is tasteful, your authored material stylish. nonetheless, you command get bought an edginess over
that you wish be delivering the following. unwell unquestionably come more
formerly again since exactly the same nearly a lot often inside case you shield this increase.
I’ll right away grab your rss feed as I can’t find your email subscription hyperlink
or newsletter service. Do you have any? Kindly allow me understand so that
I may subscribe. Thanks.
Here is my web page; tipi break
hello!,I like your writing so much! proportion we
be in contact extra about your article on AOL? I require a specialist
on this space to resolve my problem. May be that is you!
Looking forward to look you.
Check out my web blog: True Body Diet Keto
Hello to every one, the contents present at this website are genuinely awesome
for people knowledge, well, keep up the good work fellows.
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I will come back once
again since I bookmarked it. Money and freedom is the best
way to change, may you be rich and continue to
guide others.
I was suggested this website by my cousin. I am not sure whether this post is written by him as
no one else know such detailed about my difficulty.
You are wonderful! Thanks!
Visit my webpage … Swen
Very clear site, regards for this post.
My website; Keto Cut XS Fat Burner
Quality articles is the important to interest the visitors
to visit the website, that’s what this website is providing.
Hey There. I discovered your blog the usage of msn. That is a
really well written article. I’ll be sure to bookmark it and come back to learn more of your helpful info.
Thanks for the post. I’ll certainly comeback.
bookmarked!!, I love your website!
Don’t save it just to use on unique occasions or holidays unless the pieces are extremely delicate.
Have a look at my web-site: Wiki.cue-event.de
It’s really a great and helpful piece of information. I am
satisfied that you just shared this useful information with us.
Please keep us up to date like this. Thank you for sharing.
Hi! I’m at work browsing your blog from my new iphone 3gs!
Just wanted to say I love reading your blog and look forward to all your posts!
Carry on the excellent work!
Whats up very cool web site!! Guy .. Excellent ..
Superb .. I’ll bookmark your website and take the feeds additionally?
I’m glad to seek out so many helpful information right here within the
publish, we need develop more techniques in this regard, thank you for sharing.
. . . . .
my site Trim Drops Keto ACV Reviews
I am regular visitor, how are you everybody?
This paragraph posted at this web page is actually nice.
Greetings! Quick question that’s completely off topic.
Do you know how to make your site mobile friendly? My site looks weird
when viewing from my iphone. I’m trying to find a template or plugin that might
be able to correct this problem. If you have any suggestions, please share.
With thanks!
Here is my blog post; Penis Pills
For most recent news you have to pay a visit the web and on internet I found this website as a most excellent web page for
most up-to-date updates.
priligy canada online priligy new york buy generic priligy online canada
Greate article. Keep writing such kind of information on your page.
Im really impressed by it.
Hi there, You’ve performed an incredible job. I will
certainly digg it and individually recommend to my friends.
I’m sure they will be benefited from this site.
What’s up to all, how is all, I think every one is getting more
from this website, and your views are good in favor of new people.
Hello there, You have done an incredible job. I’ll certainly digg it and personally suggest to my friends.
I’m sure they will be benefited from this website.
What’s up everyone, it’s my first go to see at this web site, and piece
of writing is in fact fruitful in support of me,
keep up posting such articles or reviews.
there are sub pages for it but i dont know if you need the page names .
or any specific information.
feel free to contact me.
best regards
abbas
Hi there, just wanted to mention, I enjoyed this blog post.
It was helpful. Keep on posting!
I have been browsing online more than 3 hours today, yet I never found any interesting article
like yours. It’s pretty worth enough for me. In my opinion, if all site owners and bloggers made good content as you did, the internet will be much
more useful than ever before.
Heya i am for the first time here. I came across this board and I find It truly
useful & it helped me out much. I hope to give something back and aid others like you aided me.
Link exchange is nothing else except it is simply placing the
other person’s webpage link on your page at proper place and other person will also do same for you.
This data is obtainable in the midst of the course of of creating
an account and cannot be modified.
my page … pin-up casino apk download for android
I’m truly enjoying the design and layout of your website.
It’s a very easy on the eyes which makes it much more pleasant for me to
come here and visit more often. Did you hire out
a developer to create your theme? Fantastic work!
After I initially left a comment I appear to have clicked the -Notify me when new comments are added- checkbox and from now on every time a comment is added I
get four emails with the exact same comment.
Perhaps there is a means you are able to remove me from that service?
Thanks a lot!
What i do not understood is in truth how you’re not actually much more well-appreciated than you may be right now.
You’re so intelligent. You understand thus considerably relating to this matter, produced me for my part imagine
it from so many varied angles. Its like women and men don’t seem to be
interested until it’s something to accomplish with Lady gaga!
Your personal stuffs great. At all times take care of it up!
Normally I don’t learn post on blogs, however I wish to say
that this write-up very pressured me to take a look at and do so!
Your writing taste has been surprised me.
Thank you, quite nice article.
Hello, I wish for to subscribe for this web site
to take hottest updates, so where can i do it please help.
Here is my web site; Rescue Hair 911 Reviews
Hi there it’s me, I am also visiting this web site on a regular basis, this site
is truly nice and the visitors are in fact sharing nice thoughts.
My site judi slot terbesar
Please let me know if you’re looking for a article writer for your weblog.
You have some really good posts and I believe I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to write
some material for your blog in exchange for a link back to mine.
Please shoot me an e-mail if interested. Thanks!
It’s enormous that you are getting ideas from this post as well as from our dialogue made at this time.
I love what you guys are up too. This sort of clever work and exposure!
Keep up the good works guys I’ve included you guys to my blogroll.
Lovely blog! I am loving it!! Will be back later to read some more.
I am bookmarking your feeds also
Also visit my web-site: True Body Keto Reviews
She was also responsible for curing bacon, salting meat,
and creating pickles, jellies, and preserves .
Check out my webpage 유흥알바
Hi terrific blog! Does running a blog such as this take a massive amount work?
I have no expertise in coding however I was
hoping to start my own blog soon. Anyways, should you have
any ideas or tips for new blog owners please share. I know
this is off subject nevertheless I just needed
to ask. Cheers!
https://nupedia.ru/viewtopic.php?id=8766#p36917
gezi ve tatil tavsiyeleri
Profesyonel Bir Bioclimatic, Tekno Roofta!
how to administer ivermectin to rabbits <a href="https://stromectolcrx.site/where-to-buy-cheap-stromectol-australia-no-prescription.html “>is ivermectin pour on safe for horses can i buy arvs at clicks
Cheap dissertation chapter editing site for mba https://www.sante-dz.org/doc.php?url=https://papershelps.org
Scott martin thesis https://maps.google.ml/url?q=https://bestessayservicereview.com
http://charlotteinvestmentmanagement.com/how-can-a-novice-investor-choose-a-company-to-invest-in.html
https://stromectolcrx.site/can-you-get-ivermectin-over-the-counter.html
Sosyal medya üzerinde etkin olan ve para kazanan çok sayıda hesap bulunmaktadır. Bu durumun en büyük sebeplerinden bir tanesi de sosyal medyanın çok çeşitli sayıda içeriğe ve kullanıcıya ev sahipliği yapmış olmasıdır. Bu nedenle de çeşitli kategorilerde ve çeşitli şekillerde sosyal medya üzerinden para kazanan çok sayıda sosyal medya kullanıcısı bulunmaktadır. Bu kullanıcılar sürekli kendilerini yenileyerek sosyal medya üzerinden almış oldukları parayı artırabilmektedirler. Her sosyal medya kullanıcısı kendine özel olan bir şekilde para kazanabilmektedir. Çeşitli kategorilerde aralarında bir rekabet olan sosyal medya hesapları da bulunmaktadır. Kazandığı parayı daha fazla artırabilmek için rakip hesaplar ile yarışan çok sayıda sosyal medya hesabı vardır. Bu hesapların kendi aralarında yarıştırmış oldukları ilk faktör de takipçi sayısıdır. Takipçi sayısı fazla olan hesaplar daha fazla sosyal medya kullanıcısına ulaşabilmektedir. Bu nedenle de takipçi sayısı sosyal medya üzerinden para kazanan sosyal medya hesapları için büyük bir önem taşımaktadır. Takipçi sayısını artırmak için sosyal medya kullanıcıları çok çeşitli ve farklı yöntemler kullanmaktadırlar. Bu çok çeşitli ve farklı yöntemlerin başında takipçi satın alma yöntemi bulunmaktadır. Takipçi satın alan çok sayıda sosyal medya kullanıcısı vardır. Ancak bu kişiler satın alacakları takipçilerin garantili yani kesin bir şekilde onları takip edecek kişiler olmasına dikkat etmektedirler. Özellikle de instagramda bu duruma çok dikkat edilir. İnstagram garantili takipçi al seçeneği meredeyse her hesap tarafından tercih edilmektedir.
buy youtube views service is the Instafollower Youtube service that increases the number of views of your Youtube videos. Get your videos on trending lists by buying views. Due to the working structure of the Youtube algorithm, the number of views is very important. The number of views of Youtube videos is also important for Youtube viewers. Videos with a high number of views are more in demand. Thus, the number of views increases even more. In short, views attract views. There are various ways to increase the number of views of Youtube videos. Keeping videos up to date, producing interesting content, making videos about trending topics, adding creative featured images, etc. methods will help you increase the number of views naturally. If natural methods are not enough for you, you can easily increase the number of views of your videos in a short time thanks to the purchase of Youtube views on the internet.
8000 euro lenen
celebrex 200 mg australia celebrex otc celebrex pharmacy
how much ivermectin to give guinea pig buy stromectol canadian pharmacy without prescription stromectol ireland
Good point, makes a sence especially when one is experienced in the topic. So keep righting and share your thoughts and experiences.
I like this website too:
vsexy
I like this website because I can always find something new for myself, moreover, I like to read other people’s comments.
I like this website too:
נערות ליווי בבני ברק
I like this website because I can always find something new for myself, moreover, I like to read other people’s comments.
I like this website too:
נערות ליווי ביבנה
At last someone wrote something very important about such hot topic and it is very relevant nowadays.
דירות דיסקרטיות בחיפה
At last someone wrote something very important about such hot topic and it is very relevant nowadays.
דירות דיסקרטיות בחולון
Maybe one day I will write a book based on this perfect writing. Great job really.
דירות דיסקרטיות בהרצליה
Maybe one day I will write a book based on this perfect writing. Great job really.
דירות דיסקרטיות בחיפה, קריות והצפון
Maybe one day I will write a book based on this perfect writing. Great job really.
escort girls in Tel Aviv
Maybe one day I will write a book based on this perfect writing. Great job really.
מתל אביב והמרכז
I cannot thank you enough for such great writing and all people to their up to the point reviews.
דירות דיסקרטיות בתל אביב והמרכז
Maybe one day I will write a book based on this perfect writing. Great job really.
נערות ליווי בחיפה, קריות והצפון
I cannot thank you enough for such great writing and all people to their up to the point reviews.
דירות דיסקרטיות בחיפה
Maybe one day I will write a book based on this perfect writing. Great job really.
דירות דיסקרטיות בבאר שבע
Autowaschanlagen Berga
Essay format sample examples http://qnbuz.net/index.php?qa=user&qa_1=kevinthrill0
Professional school admission essay topic https://88yllt.com/home.php?mod=space&uid=394261
how long does it take for ivermectin to kill worms stromectol and scabies cheap stromectol from india no prescription
Kurumsal Web tasarım hizmetleri çok iyi gerçekten çok iyi işler çıkartıyorlar tebrik ederim, iki firmamız içinde güzel işler başardık ve dijital reklamlar ile yeni müşteriler edindik keşke daha erkenden tanışabilseydik diye düşünüyoruz.
dischem price for acc 200 where to buy generic stromectol online pharmacy without prescription is ivermectin available in canada
guidaprestito.com/3000-euro
vintage ring
sumatriptan coupon buy sumatriptan 25mgsumatriptan cheap sumatriptan united kingdom
Başta İstanbul olmak üzere ülkemizin her noktasında hizmet vermek konusunda oldukça titiz bir çalışma sunan Tekno Roof, sunduğu tüm seçeneklerin içerisinde bioclimatic pergola taleplerinize uygun şekilde işlemler yapmaktadır. Size uygunluk sağlaması açısından yapılmasını istediğiniz alanda gerekli noktaları ve dikkat edilmesi gereken her detayı belirleyen, sizi sonuca en iyi şekilde götüren bir firma olarak iş kapsamında ortaya çıkacak sonuçlardaki başarısının da garantisini hazırlamaktadır.
With chatbot integration on live support, whatsapp and social media, you can automatically do all your flow and work, and provide 24/7 support and service.
Armin Rub
vintage ring
Seo ve sosyal medya danışmanlığı konusunda soft ajanstan hizmet alıyorum, kendilerine teşekkür ederim.
Cheers. Numerous forum posts.
z pack azithromycin 250 mg – what is azithromycin prescribed for
You revealed it effectively!
Best home work editing websites http://couponwhisper.com/members/tunecost9/activity/536067/
Help with my zoology critical thinking http://getpocket.com/redirect?url=https%3A%2F%2Fbuyessayreviews.com%2F
FX15 Türkiye sitemizden orjinal ve faturalı FX15 sipariş vermek için formu doldurabilirsiniz. FX15 Resmi satış sitemiz FX15 sipariş veren her müşterimiz için orijinal ürün göndermekte ve hızlı teslimat avantajı ile beğeni görmektedir. Orjinal FX15 zayıflama hapı satın almak için formu doldurmanız yeterli olacaktır. fx15 sipariş
pırlanta sizsiniz
Sample marketing business plan pdf http://yukin.s21.xrea.com/cgi-bin/mini_k1/kboard.cgi?mode=res_html&owner=%95%9B%8E%FB%93%FC&url=buyessayreviews.com&count=1&ie=1
carvedilol online carvedilol 25 mg australiacarvedilol uk buy carvedilolmg
yaşam koçluğu eğitimi konusunda alanında uzman ve her zman en iyi eğitimler sağlayan bir kurmdur ve her zman destek alabilirsiniz
Help writing a conclusion paragraph http://www.astro.wisc.edu/?URL=https%3A%2F%2Fwww.essaypro.me
Lainaa 10000
furosemide 100 mg cheap furosemide no prescription furosemide otc
http://peschanoe.co.ua/knit/miss/zihiketon.html
priligy new jersey order priligy online in china is it safe to buy priligy online
I cannot thank you enough for such great writing and all people to their up to the point reviews.
דירות דיסקרטיות בחיפה
At last someone wrote something very important about such hot topic and it is very relevant nowadays.
נערות ליווי בבת ים
Maybe one day I will write a book based on this perfect writing. Great job really.
Escort girls in Tel Aviv
At last someone wrote something very important about such hot topic and it is very relevant nowadays.
דירות דיסקרטיות בבאר שבע
I cannot thank you enough for such great writing and all people to their up to the point reviews.
דירות דיסקרטיות בתל אביב
Maybe one day I will write a book based on this perfect writing. Great job really.
דירות דיסקרטיות בפתח תקווה
Finally I found a perfect website for me. Thank you for such nice place where I can get good information for me.
נערות ליווי בתל אביב
What a nice place to share thoughts but the most important that thoughts are positive and realistic.
נערות ליווי בתל אביב
What a nice place to share thoughts but the most important that thoughts are positive and realistic.
נערות ליווי בתל אביב
Maybe it is one of the best websites I have ever visited.
נערות ליווי בתל אביב
What a nice place to share thoughts but the most important that thoughts are positive and realistic.
נערות ליווי בתל אביב
What a nice place to share thoughts but the most important that thoughts are positive and realistic.
נערות ליווי בתל אביב
What a nice place to share thoughts but the most important that thoughts are positive and realistic.
נערות ליווי בפתח תקווה
cheap stromectol nz no prescription buy ivermectin for humans canada how to buy stromectol au without prescription
aldactone tablets aldactone tablets aldactone 25mg prices
is ivermectin used in canada for covid 19 do we need prescription for ivermectin where to buy ivermectin for humans in us
ooo shit wanderfull sharing
Maybe it is one of the best websites I have ever visited.
נערות ליווי בתל אביב
How much I am enyoing reading every word that is written here- full of thoughts and new ideas.
נערות ליווי באילת
I deep down hope that your insomnia is a tough nut to crack cbd capsules already and not a symptom of something more serious. I distinguish that melatonin works marked but I can also tell you that full spectrum cbd gummies commission just as warmly and you can’t stable develop an addiction untypical in the suit with melatonin that’s a charming cloth advantage. But I’m established that these gummies wishes absolutely cure you.
I at the end of the day hope that your insomnia is a problem cbd capsules already and not a idiosyncratic of of something more serious. I distinguish that melatonin works marked but I can also differentiate you that full spectrum cbd gummies peg away precisely as warmly and you can’t more than ever notwithstanding arise an addiction unequal to in the containerize with melatonin that’s a charming righteous advantage. But I’m sure that these gummies on really cure you.
I deep down hope that your insomnia is a problem full spectrum cbd oil already and not a characteristic of something more serious. I know that melatonin works marked but I can also tell you that crammed spectrum cbd gummies lift weights simply as well and you can’t stable upon an addiction untypical in the suit with melatonin that’s a pretty good advantage. But I’m solid that these gummies will really inform appropriate you.
As it is said as many people so many thoughts. That is why I think that every statement has a right to be expressed even if I think differently.
I like this website too:
נערות ליווי במרכז
I like everything what is said and I support it a lot. I am glad to be here and to share my opinion.
This site I like too:
סרטי סקס ישראלי
It’s difficult to understand the lengths he’d go to remain short.
whatsapp buton gönderme
ltobet
ปอยเปต
ชัดเจนเบท
sagamingvip
allbetclub
jilislotcity
pgsoftgame
slotpg99
sexygaming
mufasabe
spinixslot
https://www.ltobetlotto.vip/
ya love
https://xn--m3cdma8ae1a4c6a8l6e.com
ya love
http://xn--82cd4anakh0e0gngc4c.com
ya love
https://www.sagamingvip.casino
ya love
http://www.allbetclub.co/
ya love
https://www.jilislotcity.com/
ya love
https://www.pgsoftgame.net/
ya love
https://www.slotpg99.bet/
ya love
https://www.sexygaming.co/
ya love
https://www.mufasabet.bet/
ya love
https://www.spinixslot.biz/
ya love
Are you creating a FiveM server? Here are the best scripts for FiveM, for a cheap price and a very good quality! Don’t waste your time for testing and fixing free FiveM scripts. Use our premium FiveM scripts.
https://fivemm.shop/
Are you creating a FiveM server? Here are the best scripts for FiveM, for a cheap price and a very good quality! Don’t waste your time for testing and fixing free FiveM scripts. Use our premium FiveM scripts.
https://fivem-mlo.com
Great job for publishing such a beneficial web site.
แทงหวย24
where to buy xenical online p
ltobet
Cinsel Güç Artırıcı Cialis Hap sayesinde etkilerini hızlı bir şekilde görebileceksiniz.cialis sitesi
https://lipomic.com/wp-content/pages/1kashely_u_grudnichkov.html
Federal officials have made a significant driver of mainstream adoption particularly now that.무료스포츠중계
Being smaller than have thousands and thousands
of bitcoins to him and whether or to not.
hello there
i have learn several just right stuff here. Definitely value bookmarking for revisiting.
I wonder how so much effort you place to make one of these fantastic informative web site.“밤의전쟁” I will be coming back to your website for
Perfect piece of work you have done, this internet site is really
cool with wonderful info.
do you want play casino but you are afraid of losing? 토토총판 go to my website its easy to play and no more losestreak ! 😉 😉
Having installing thousands of Invisible Grille Singapore for many years, and we have realized the many faults of the Invisible Grille, such as:
Our professional waterproofers able to handle all parts of the job because of the unique way we install our basement waterproofing systems. If you’re ready to work with the friendly, highly-qualified Toronto waterproofing team, give us a call. We’d be honored to give you a free consultation and quote.
araba arıza kodu
https://mironline.getbb.ru/viewtopic.php?f=27&t=27856
karnatakastateopenuniversity.in is not any official website. It is not associated with any Government Organization. All the information provided on this website are collected from various online and offline sources. All data given here is only intended for educational purpose
Since 2005, high ticket digital marketing has been my world. Consulting for hundreds of successful businesses and creating thousands of the best marketing campaigns.
With a passionate curiosity, my business has grown from doing freelance digital marketing as a digital marketing consultant, into a digital marketing agency with a staff of the brightest and savviest professionals that hold a complete dedication to your success.
幣知道BTC
Homes for sale
When It Comes To International Shipping Solutions,
DHL Express Has It Covered
Shipping internationally can be complicated—every country has a different set of rules and regulations on shipments coming from around the world. Understanding these rules and regulations is key to seamless and error-free shipments. DHL Express servicepoint has focused on international shipping since 1969 and is the largest international shipping company in the world, delivering to millions of addresses in more than 220 countries.
online slots
ausmalbilder on7g.com danke
We hope you enjoy your time coach here Reading and Minibus Website! When planning your next trip by coach or minibus, we are here to assist you in more ways than just saving money, time, and hassle. Our mission is to promote the mode of vehicular travel that has the most negligible negative impact on the environment. Also, to assist you in supporting the locally owned and operated independent coach companies in your area.
play live casino
토토사이트
Terbaik Win Rate Tertinggi Jackpot Besar
Banyaknya situs yang beredar saat ini semakin membuat para pemain kebingungan kemanakah harus menentukan pilihan yang tepat untuk bermain slot gacor kesayangannya. Kini anda tidak perlu menghabiskan waktu lagi, karena sekarang sudah hadir sebagai slot gacor 2023 yang telah terbukti dipercaya oleh para pemain khususnya di Indonesia. Menempatkan pilihan yang tepat akan memberikan pengalaman bermain slot yang menyenangkan dan hasil yang maksimal.
https://vavada.bitbucket.io/
Latest Gadgets price in Bangladesh aims to be the most useful and trusted mobile phone info website of Bangladesh. Find the latest official smartphone, watch, tablets, camera, laptops, motorcycles, etc. See the latest Gadgets price in Bangladesh.
Education News is a source of news on education policy and public education. Her articles cover a wide range of topics, from reducing the teacher shortage to implementing mobile devices that take learning outside the classroom.
Family4kPro is a leading provider of IPTV subscriptions and VOD services. Family4kPro offers users the best quality IPTV subscription, reliable and stable streaming, 10,000+ live TV channels, and 50000+ VOD with a 24-hour free trial. Our service will be your best choice for watching sports, movies, TV shows, and more on your PC, Mac, or Android devices.
With Family4kPro IPTV you can watch your favorite local or international channels on your Smart TV directly without any cable set-top box or satellite dish needed. You can even watch live sports events online without any additional hardware.
https://www.the-hillhouse.sg/
JABAL AL WAHDA Sofa Upholstery Dubai Furniture Services
Fortunately, there is a new registrar cheap domain names from $0.99
Namecheap exists to help EVERYONE get, make, and achieve more online with less cost, hassle, and headaches. We offer everything you need to get online and thrive, from domains to hosting to security to specialist services and products — all with value built in.
Great prices, world-beating customer support, and extra resources come as standard. ==>> https://zeep.ly/rxViL
Oh my goodness!! !!! “밤부” Incredible article dude! but can’t post my nudes here 🙁
먹튀검증
먹튀검증
zzapflix.com
짭플릭스 는 한글 자막 애니메이션,영화,다큐멘터리,드라마 등을 온라인에서 무료로 볼 수 있는 가장 안전한 사이트입니다. 720P 이상의 화질, 최적화된 UI와 UX, 뛰어난 고객 서비스를 제공하여 즐거운 컨텐츠를 즐길 수 있는 최고의 장소입니다. 우리는 다양한 장르의 애니메이션,영화,다큐멘터리,드라마 등을 수천 작품 보유하고 있으며, 이후로도 꾸준히 업데이트 됩니다. 짭플릭스와 함께 끝없는 OTT 여행을 시작하십시오!
It took me a lot of time to find such precious website with such valuable information. Keep going and make your users happy.
נערות ליווי בחיפה
Wir bieten kostenlose Lösungen von Fehlercodes für alle Drucker weltweit. drucker-fehlermeldungen.de
3 point thesis outline https://drive.google.com/file/d/1wP6zcWYDnm9XFKI9Jcb3lqO_wi5NCgoJ/view
Laptop repair service
Software ag master thesis https://images.google.sc/url?q=https://essayservice.discount
Vector Moving and Storage is a professional moving company San Jose California. We offer local and long distance moving service. Our professional movers will protect your furniture before moving it. All our crews has tools to assist with disassembly and reassembly of the furniture. Vector Moving and Storage also offers commercial and office moving in San Jose area.
Hi bensonyerima.com admin, Thanks for the in-depth post!
ダッチワイフ高級 KICHI-DOLL(キチドール)のラブドールは、女や男をしっかり再現するアダルト用おもちゃです。何より頑丈で肌触りも良好。うちのは高級なラブドールで、安全な素材シリコンやTPEで作り、中には金属製骨格も埋込みます。本物の女性より抱き心地がいいくらいで、ラブドールはリアルな女性のボディラインを再現しているため全身にこそ価値がありそうです。
Do not stop doing what you do, it is simply perfect.
נערות ליווי ברמת גן
Geeral resume templates http://maps.google.com.mt/url?q=https://essayservice.discount
beton direk fiyatları için HepKredi :https://www.denizliyeniolay.com/haberler/guncel/insaat-malzemeleri-fiyatlari/59265/
In competition, the Judoka wear either a White or Blue Judo gi. A black Judo gi is worn by some Judoka during practice, keeping their High Quality Judo gi in pristine order.
Yeni bir oyuncu olarak, çok sayıda deneme bonusu alırsınız. Minimum riskle artırabilirsiniz. Çevrimiçi bahis oynamak ve kazanmak istiyorsanız, biraz şanslı olmanız veya ekstra seçenekler kullanmanız gerekir. İşte spor bahislerinde kazanma hakkında güvenilir bilgilerle dolu kullanışlı bir canlı bahis rehberi.
Astrologia
you are the diamond
Some of the sentences sounds like exactly my thoughts! Fabulous place to be.
Работа для девушек в Израиле
tembusu grand
leo77
permanent residence Bulgaria
ile iletişime geçerek hatasız ve profesyonel bir taşınma süreci yaşayın.
youtube to mp4 converter
Write an essay about my parents https://paperhelp-discount-code.blogspot.com/2023/01/paperhelp-discount-code-10-off.html
Haber
Regards. Terrific information!
https://essaywritingservicelinked.com/ buy custom papers online
Afad Acil Çağrı Apk İndir
http://www.forumnko.ru/
Important information is stated. It was nice to read it and learn some other point of view.
Here I also find good informantion:
שירותי ליווי בחיפה
Important information is stated. It was nice to read it and learn some other point of view.
Here I also find good informantion:
Escorts
Popular thesis writers service uk paper help
So important to read good staff that is full of style and good things.
Работа эскорт Израиль
food open near me
Free credit can be used to be used as สล็อตxo168 capital for further expansion To spin the spin of every game within the web as well SLOTXO website’s slot games are imported games. The first one to play in Thailand And is also the only owner that has the most imported games. If playing with SLOTXO direct web slots, you will definitely not miss being the number one place. Interested in playing and placing a lot of bets No matter who plays slots here received a large set of wealth
baywind residences
kitchen renovation
The W-2 is a record of your salary paid to you throughout the year. The 1099 and its variations are designed for reporting any additional sources of income. If you were freelancing on the side or you earned any income from investments, it would be reported on a 1099 form.
one pearl bank
piccadilly grand
The IRS tax refund schedule 2023 dates according to the IRS are 21 days for e-filed tax returns and 6 to 8 weeks for paper returns. So, in theory, if you e-file your tax return, on the starting day of January 27th, 2022, you should receive your tax refund by February 16th or a paper check between March 9th and March 23rd.
one draycott
Nicely mentioned, I like to follow this website because here I cannot always find interesting and important things for myself.
Here I also find good informantion:
נערות ליווי בחיפה
แทงบอล
Dịch vụ SEO TPHCM
705039 231156Real wonderful information can be found on web blog . 235906
타이마사지
여기에서 몇 가지 좋은 내용을 읽었습니다.
재방문을 위해 북마크할 가치가 있습니다.
타이마사지
Furthermore, The contents are masterwork. you’ve performed a great task in this topic!
Hi there! I know this is somewhat off topic but I was wondering if you knew where I could get a captcha plugin for my comment form?
I’m using the same blog platform as yours and I’m having
trouble finding one? Thanks a lot!
마사지커뮤니티
Furthermore, The contents are masterwork. you’ve performed a great task in this topic!
I always share this website with my friends and collegues because the writing is always up to the point and very interesting.
escort girls Haifa
I like everything what is said and I support it a lot. I am glad to be here and to share my opinion.
This site I like too:
סרטי פורנו
I like this idea and support it. It is not the first time I read it.
Here is also interesting site:
נערות ליווי בחולון
So important to read good staff that is full of style and good things.
Работа в сфере эскорта в Израиле
Join us right now, completely free! free bnb
Türkiye’nin En Popüler ve En İyi Bahis Sitesi #ONWİN •
70 Denye Astar
locksmith richmond indiana
บาคาร่าเว็บตรง
ถ้าคิดจะเริ่มต้น เดิมพันบาคาร่าออนไลน์ สิ่งที่ถือว่าสำคัญมากที่สุดในการเดิมพันนั้นก็คือ นักพนันจะต้องเข้าใจรูปแบบในการเล่นให้ดีก่อน เพราะอย่างที่รู้ว่าเกมไพ่บาคาร่านั้นใช้ไพ่มากถึง 8 สำรับทำให้การออกผลไพ่และรูปแบบการออกไพ่มีหลากหลายมากขึ้น โดย เกมบาคาร่าออนไลน์ นั้นจะแบ่งการเดิมพันออกเป็นสองฝั่ง คือฝั่งเจ้ามือ และ ฝั่งผู้เล่น โดยนักพนันจะเป็นผู้เลือกเดิมพันว่าจะเลือกเดิมพันฝ่ายไหน ซึ่งเกมไพ่บาคาร่านั้น จะตัดสินผลการแพ้ชนะด้วยแต้มบนไพ่ที่ดีลเลอร์จะเป็นผู้แจกให้กับทั้งสองฝั่งโดยแต้มที่สูงสุดสำหรับเกมบาคาร่านั้นคือ 9 แต้มโดยจะเป็นการนำผลแต้มของไพ่ทั้งสองใบมาบวกรวมกัน หากฝั่งไหนได้แต้ม 9 แต้มหรือใกล้เคียงกับ 9 แต้มก่อนก็จะเป็นผู้ชนะทันที และได้รับเงินรางวัลตามอัตราจ่ายที่ได้แจ้งไว้บนโต๊ะบาคาร่าซึ่งการเล่นบาคาร่าออนไลน์นั้นถือว่าเป็นเกมที่เล่นได้ง่ายและสามารถทำกำไรได้อย่างรวดเร็วเพราะในแต่ละตานั้นจะใช้เวลาเพียงแค่ 30 วินาทีเท่านั้นssss
He is only 5 foot 2 inches tall.ダッチワイフAs discussed earlier, that is a blessing in disguise.
https://www.freeworksheets.com/
https://deli303.org
The newest collection of the most hilarious demo slot machine sites for 2023
The Latest Gacor Slot Demo Machine Site Recommendations Easy to Win 2023
https://gdi.com
The Biggest Site Slot Shopeepay With Low Deposit Only 5k No 1 In The World
Car keys
Chelsea Monthly is London’s No.1 Luxury & Lifestyle magazine, with over 150,000 copies distributed throughout Chelsea, South Kensington and Knightsbridge and subscribers globally. The magazine covers the best in Travel, Lifestyle, Fashion, Entertainment, Tech, Property, Food & Drinks plus much more. To advertise on either the Print or Online publication.
situs slot online terpercaya menyediakan permainan menarik cek disini Spin88
SEO services
incfile
You’ve landed on this page because you are looking for details about the best gold IRA and the top suppliers of gold IRA services.
best gold IRA companies
Buy Weed Online Europe
jili slot
The Mysore University is public state university located in the state of Karnataka. The Uni Mysore conducts various Under Graduate (UG) as well as Post Graduate (PG) Degree Courses Examinations every year. The exams are conducted semester wise throughout the year. For the session 2020-2021 the university is going to declare Mysore University BA BSc BCom Results 2022. Candidates who are eagerly waiting for their Uni Mysore UG 1st 2nd 3rd Year Results 2021 please go through the window provided below or directly click on the links given below.
mysore university result
Buy dmt online
3d printer filament
Electronic Chassis Enclosure Manufacturer
dan wesson commander classic
facial tightening
168galaxy pg เว็บเกมสล็อตออนไลน์น้องใหม่มาแรง จากค่าย เกมสล็อตออนไลน์ PGSLOT ที่กำลังร้อนแรงสุด ๆ ในตอนนี้ อยากรวยกดเลย
บา คา ร่า 99เป็นสูตรเดิมพันในเกมบาคาร่าที่มีความนิยมในวงการเกม PG SLOTออนไลน์ โดยสูตรนี้จะเป็นการวางเดิมพันในแบบเทพบาคาร่าที่มีอัตราการจ่ายเงิน
sysoon
The first social network dedicated to the death, dying and funerals.
Dead people search engine
Search for deceased and milions of death records worldwide
Family History and Genealogy records
Online memorial website and virtual cemetery
Sysoon is a free resource for finding the final resting places of famous folks, friends or family members and view the burial records from thousands of cemeteries across the world.
The Free Encyclopedia of Death and Dying
Dead people server
Search for deceased and milions of death records worldwide
Family History and Genealogy records
Online memorial website and virtual cemetery
Milions of cemetery records and online memorials
A Free Genealogy Resource
Search for cemetery records
Cemetery, cremation and funeral resource
Funeral Home directory and cemetery resource
Death records for free
Funeral server and funeral planing
Find a Grave and milion of death and cemetery records
Dead people and bereaved family and friends
Genealogy search engine
Locate a cemetery and dead people worldwide / How to Locate Someone in a Cemetery
Website dedicated to death and dying
Online funeral, memorial and cemetery resource
Find death certificates, burial records, obituaries and cemeteries.
Search billions of death records. Get results in seconds!
Find the graves of ancestors, create virtual memorials or add photos, virtual flowers and a note to a loved one’s memorial.
เว็บ สล็อต ตรงยุคนี้มีมากมายให้เลือกเล่น ทั้งเกมเเละค่ายเกม หลายหลายสไตท์ เป็นช่องทางการทำเงินแบบง่ายๆไม่เสียเวลามากแค่ใช้เวลาว่างในแต่ละวันเล่น pg slot จะแนะนำให้รู้จัก
Jaidee88 ที่น่าเชื่อถือหากคุณกำลังมองหาบริการที่มีความปลอดภัยและเชื่อถือได้สำหรับการฝากเงินและแทงบอลออนไลน์ คุณควรลองใช้บริการของ PG SLOT
สล็อตเครดิตฟรี50 เล่นผ่านเว็บ pg slot ไม่ต้องฝาก ทดลองเล่นโดยไม่ต้องฝาก pg slot เล่นได้แบบไม่มีขีดจำกัดตลอด 24 ชั่วโมง รวมทั้งเบิกเงินในปริมาณ รับเครดิตง่าย ๆ ไม่ต้องฝากก็เล่นได้
slot asia เป็นต้นแบบเกม เว็บไซต์สล็อต สล็อตออนไลน์ ยอดนิยมแล้วก็เป็นที่พึงพอใจอย่างยิ่งสำหรับผู้เล่นเกมสล็อตออนไลน์ในช่วงเวลานี้ด้วยแบบเกม PG เป็นเกมที่เล่นได้ง่ายๆ
Sanook ที่ไม่ควรพลาดหากให้ตอบในแง่ของการสื่อสารภาษาอย่างเป็นทางการ ฉันขอตอบว่า “ไม่น่าเกี่ยวข้องกับเนื้อหาที่กำลังพูดถึง” โดยมีความหมายว่า PG SLOT
pg เกมสล็อต สนุกเหมือนกับ line tv เกมสล็อตของค่าย pg slot นั้นมีมากมาย ในเว็บของเรา ที่ pg-slot.game และรับรองว่าสนุกทุกเกม Line TV ในช่วงนี้แล้วอยากเปลี่ยนเราแนะนำ
Is there any more info? cleaning services dubai
OOTDY
We believe in quality craftsmanship and fashion-forward design that can be worn everyday. High quality jewelry shouldn’t cost the planet. Let jewelry become a part of you.
In Finance
You have written and posted a very good article. That’s why we are grateful to you that you keep posting articles containing your useful information like this, we are with you.
onlinebankinglogin.com
Wir wählen nur hochwertige Materialien aus, um eine erstklassige Sex Doll herzustellen. Unsere Lebensechte Sexpuppe bestehen aus medizinischem TPE-Materialien und hochwertigem Silikon, wodurch jeder Teil ihres Äußeren so realistisch wie möglich wird. Sie finden Sexpuppen mit den üppigsten Hüpfbrüsten für eine Sexpuppe.
แทงบอลสเต็ป หรือการแทงบอลชุด ถือเป็นอีกหนึ่งรูปแบบการเดิมพัน ที่คอบอลไทยนิยมแทงกันเป็นอย่างมาก ซึ่งการแทงบอลประเภทนี้ จะเปิดโอกาสให้เหล่าคอบอล ที่ชื่นชอบการพนันบอล สามารถวางเดิมพันได้ครั้งละหลายคู่ ในหนึ่งบิลเดิมพัน ส่งผลให้อัตราการจ่ายเงินรางวัล ที่ได้จากการแทงบอลสเต็ป จะสูงกว่าการเดิมพันฟุตบอลประเภทอื่นๆ แต่เงินเยอะก็ใช่ว่าจะชนะเดิมพันได้ง่ายๆ เนื่องจากเงื่อนไขในการ แทงสเต็ป นั้น ทุกคู่ที่ท่านเลือกแทงไปจะต้องชนะตรงตามอัตราต่อรองที่ท่านเลือกทั้งหมด หากผิดการเงื่อนไขเพียงคู่เดียว จะเท่ากับว่าบิลนั้นแพ้เดิมพัน และท่านต้องเสียเงินทุนนั่นเอง
Over the past ten years, llc names ideas there has been a noticeable shift in the trends surrounding the creation of LLC business names. One significant trend is the increasing emphasis on uniqueness and distinctiveness. In the past, business owners often opted for generic and descriptive names that conveyed the nature of their products or services. However, in recent years, there has been a surge in the use of creative and unconventional names that stand out in a crowded marketplace.
Thank you for this good details. Please find my details.. โปรสมาชิกใหม่100%
BET88 is a trusted online betting platform that offers a wide range of exciting gambling experiences. As a leading betting site, BET88 provides a secure and reliable environment for players to enjoy their favorite casino games and sports betting activities. With a user-friendly interface and a diverse selection of games, including live sports betting and slot games, BET88 ensures a thrilling and enjoyable betting experience. The platform also prioritizes the safety and security of its users, making it a trusted choice for online gambling. Join BET88 today and indulge in the excitement of betting and winning.
pg ช่วยหาเงินเติมเกม valorant เดี๋ยวนี้เล่นเกมอะไรก็ต้องใช้เงินเติมเพิ่มไอเทมเจ๋งๆไปอวดเพื่อนเว็บ pg ช่วยคุณได้เล่นเกมของเราได้เงินจริงไปต่อยอด เติมเกมอื่นๆได้อีกเพียบ
เกม PG PGSlotที่เป็นผู้พัฒนาเกมคาสิโนออนไลน์ชื่อดังของไทย โดยมีเกมสล็อตที่มีความหลากหลายและเป็นที่นิยมอย่าง PG SLOT
ทดลองเล่นสล็อต pg ซื้อฟรีสปิน เป็นแบบอย่างเกมที่สนุกแล้วก็น่าระทึกใจด้วยเหตุว่าคุณไม่ต้องนั่งปั่นให้เสียเวลาสำหรับในการร่วมเกม pgslot โบนัสที่เสียเวล่ำเวลาคุณสามารถซื้อฟรีสปิน
เล่น pg slot5gเป็นเกมสล็อตออนไลน์ที่มีความน่าสนใจและน่าเล่นมาก ๆ ซึ่งสามารถเข้าเล่นได้ผ่านเว็บไซต์หรือแอปพลิเคชันต่าง ๆ โดยในเกม PGSLOT
รีวิวเกมสล็อต pgslot ยอดนิยมที่มีผู้เล่นเยอะมาก ปี2021 ที่สามารถทำเงินได้จริงจากการเล่นเกม pg slot เล่นได้บนมือถือ
PGGAME AUTOสามารถหาซื้อได้ที่ร้านหนังสือหรือร้านค้าออนไลน์ต่างๆ ทั่วประเทศไทย เช่น ร้านหนังสือนานาชาติ, ร้านหนังสือ kinokuniya, หรือ PG
That’s a good comment. Have a good day
สล็อต ฝาก วอ เลท ปัจจุบัน 2022 สอนกระบวนการฝากเงินผ่านออนไลน์แบงค์กิ้งและแนวทางการสมัคร สล็อต ฝาก-ถอน true wallet เว็บไซต์ตรงไม่มีอย่างต่ำ pg slot เล่นเกมคาสิโนออนไลน์เลย
เล่นPG Joker Slotเพราะเป็นเกมที่มีความสนุกสนานและรางวัลใหญ่ที่มั่นคง นอกจากนี้ยังมีเกมอื่นๆใน PG SLOT
토토사이트
Panen138-Slot online merupakan situs judi slot online terpercaya, sebagai situs judi slot online terpercaya kami menyediakan banyak sekali permainan yang dapat dimainkan dan berkesempatan mendapatkan kemenangan. Panen138 tidak hanya menyediakan permainan terbaik dan terlengkap banyak sekali jenis permainan judi slot online yang dapat dimainkan hanya menggunakan satu account ID Saja
Configuring SSL authentication is an essential step in securing your online presence! 🔒🔐 It helps establish a trusted connection between your server and clients, ensuring data privacy and protection. Follow the proper documentation and guidelines provided by your SSL certificate provider to configure and implement SSL authentication effectively. Safeguard your website and build trust with your users. 💻🔒 Best AC Repair in Sharjah
pg auto เกมพีจีสล็อต สล็อตออนไลน์ ที่มาใน รูปแบบใหม่ เป็นเกมส์ ยอดนิยมที่ pg slot นิมยมเล่นกันบน โลก อินเตอร์เน็ต ขณะนี้ ที่ใครๆต่าง ก็รู้จักที่มาในรูปแบบใหม่
เล่น pg slot5gเป็นเกมสล็อตออนไลน์ที่มีความน่าสนใจและน่าเล่นมาก ๆ ซึ่งสามารถเข้าเล่นได้ผ่านเว็บไซต์หรือแอปพลิเคชันต่าง ๆ โดยในเกม PGSLOT
Travis & Sons plumber in mesa& Rooter is a plumbing company that the residents of Mesa, AZ, turn to with confidence. Our locally owned and operated business has been serving residents of Maricopa County since 1989. We’re a plumbing contractor equipped to make any job in the Mesa area go smoothly. Plumbing issues have the potential to cause a lot of damage to a home if not addressed in a timely manner, which is why we’re always quick to answer your call. Our company owner is proud to be highly involved in all of our work to ensure outstanding results. Our company is fast, reliable, and affordable, and we keep our quality as accessible as possible.
Travis & Sons plumber in mesa& Rooter is a plumbing company that the residents of Mesa, AZ, turn to with confidence. Our locally owned and operated business has been serving residents of Maricopa County since 1989. We’re a plumbing contractor equipped to make any job in the Mesa area go smoothly. Plumbing issues have the potential to cause a lot of damage to a home if not addressed in a timely manner, which is why we’re always quick to answer your call. Our company owner is proud to be highly involved in all of our work to ensure outstanding results. Our company is fast, reliable, and affordable, and we keep our quality as accessible as possible
Tham gia nhà cái cá cược Fun88 với link vào nhà cái mới nhất 2022. Những sản phẩm, trò chơi cá cược trực tuyến hấp dẫn đang đón chờ người chơi.
카지노사이트
Cool Gadgets
Discover rugged outdoor gadgets to sleek smart devices, find the ultimate gadgets for men, and stay ahead of the game. Shop now and redefine your tech game
Gadjetree’s Blog Explore the world of technology trends, gadget reviews, and the latest innovations on Gadjetree’s blog. Stay updated with tech news, product comparisons, and smart device guides for tech enthusiasts. Discover the future of technology here!
ايربار
花蓮租機車
Download Free Advik OLM to PST Converter and get your following queries solved like how to convert olm to pst, export olm to pst, olm to pst converter Full Version, import mac outlook emails to windows outlook, best olm to pst converter etc.
Onebox63 là trò chơi trực tuyến phổ biến, cung cấp trải nghiệm giao dịch toàn diện và thuận tiện.. Với giao diện người dùng đơn giản, Onebox63 cung cấp trò chơi từ cá cược thể thao đến sòng bạc trực tuyến and eSport, đáp ứng nhu cầu đa dạng của người chơi.
Kampus Hamkais UHAMKA akreditasi UNGGUL biaya terjangkau, Kampus Islam Terbaik Se-Indonesia 2023 Versi 4ICU
Waiting for more pg slot เว็บหลัก Try playing pg slots for free, no limit, you will know the features of slot games in depth.
skintoto sebagai Situs Judi Togel Online, toto sgp, toto hk yang tawarkan pasaran togel singapore dan togel hongkong di mana ialah pasaran togel terbesar di indonesia sekarang ini, dan ada banyak pasaran togel yang lain seperti hongkong pools, singapore pools dan sydney pools.
skintoto sebagai Situs Judi Togel Online, toto sgp, toto hk yang tawarkan pasaran togel singapore dan togel hongkong di mana ialah pasaran togel terbesar di indonesia sekarang ini, dan ada banyak pasaran togel yang lain seperti hongkong pools, singapore pools dan sydney pools.
là một nhà cái cá cược trực tuyến cung cấp cho người chơi những sản phẩm cá cược thú vị như ❤️⚽️ thể thao, bóng đá, casino, slots, bắn cá trên thị trường Châu Á nói chung và Việt Nam nói riêng. 188bet nằm dưới sự điều hành của tập đoàn Cube Limited, nhà cái còn sở hữu cho mình giấy phép cờ bạc hợp pháp đến từ tổ chức đảo Man.
I like this blog so much its content was wonderful.
flipupdates
I apologize, but as an AI language model, I don’t have access to real-time information or the ability to browse the internet. My training only goes up until September 2021, and I’m not familiar with specific details about 8Xbet as a platform or service. It’s possible that 8Xbet is a newer platform that has emerged after my knowledge cutoff. To obtain an accurate and up-to-date description of 8Xbet, I recommend visiting their official website or conducting an online search for the most recent information, reviews, and descriptions.
I apologize, but as an AI language model, I don’t have access to real-time information or the ability to browse the internet. My training only goes up until September 2021, and I’m not familiar with specific details about 8Xbet as a platform or service. It’s possible that 8Xbet is a newer platform that has emerged after my knowledge cutoff. To obtain an accurate and up-to-date description of 8Xbet, I recommend visiting their official website or conducting an online search for the most recent information, reviews, and descriptions. For more detail https://8xbet.casino
South Fulton Locksmiths LLC: Your Trusted Community-Driven, Black-Owned Locksmiths South of Atlanta
Discover reliable and affordable locksmith services with South Fulton Locksmiths LLC, proudly serving the community of South Fulton. As a trusted, community-driven, black-owned business, we specialize in digital locks, smart locks, and comprehensive locksmith solutions for residential, commercial, and automotive needs
Vinyl windows Toronto
We provide manufacturer’s warranty. All windows and doors we install covered by the warranty.
Positive site, where did u come up with the information on this posting? I’m pleased I discovered it though, ill be checking back soon to find out what additional posts you include.Adwords account for sale
Our goal is to put safety first, that’s why all applications and games posted on free apps android .com have download links from Google Play™ Store and all the rights belong to their respective owners. Android and Google Play are trademarks of Google Inc
wahana 138
Togel Sdy Hari Ini Pengeluaran Sydney Toto Online Online Terpercaya . Details to know click here togel sdy hari ini
https://www.10silverjewelry.com/jewelry-blog/marcasite-pendant/#comment-1036649
Togel Sdy Hari Ini Pengeluaran Sydney Toto Online Online Terpercaya
Pasaran judi togel sdy hari ini Pengeluaran Sydney Toto pools terdapat di situs terpercaya yang menyediakan berbagai pasaran terbesar paling lengkap. Pasaran besar yang dimaksudkan yaitu togel hongkong, singapore dan sydney yang online setiap harinya untuk dapat anda bergabung dan memainkannya. Sebab itulah saran dari kami untuk anda agar selalu mengunjungi situs acsiusa.com guna mengecek result pengeluaran sydney ini togel sydney pools dan pasaran toto lainnya yang sudah pasti terjamin validnya. Details to know click here togel sdy hari ini
: Invoice Maker
Universitas Muhammadiyah Prof. DR. HAMKA (selanjutnya disebut UHAMKA) merupakan salah satu perguruan tinggi swasta milik Persyarikatan Muhammadiyah yang berlokasi di Jakarta. UHAMKA memberikan kemudahan bagi calon mahasiswa baru/pindahan/konversi untuk mendapatkan informasi tentang UHAMKA atau melakukan registrasi online dimana saja dan kapan saja.
Much obliged to you for investing the additional effort to arrive at our objectives. Nailed it! สล็อต
company partnership
YOKIDOLLは、高品質を提供する最高のオンラインストアです。これからすべての性的欲求を満足させ、新しいラブドール販売で最新の人気を手頃な価格で当社のウェブサイトをご覧ください。
Are you looking for a Honeylove Discount Code, Look no further! In this article, we will explore Honeylove, a popular brand known for its innovative shapewear and bodywear solutions.
You have a wonderful site, check out Dive Mag
Togel Sydney menempati posisi ke-3 untuk pasaran togel yang paling diminati di Indonesia. Hasil Pengeluaran Sdy pada situs ini berasal dari sumber resminya yaitu Sydneypoolstoday.com yang diundi secara LIVE pukul 13.50 WIB setiap hari. Awalnya para bettor berpikir bahwa Data Sydney yang dimiliki oleh sebuah situs sangat tidak berguna. Dan pada akhirnya Data SYD yang berisi rangkuman semua hasil pengeluaran togel syd dipercaya sebagai hal yang wajib untuk dimiliki. Bisa anda bayangkan jika setiap hari anda mencari keluaran sdy dengan bertanya kepada orang lain yang mungkin anda tidak kenal? Tidak semua orang mengetahui berapa hasil result sdy terbaru hari ini. Berbeda halnya jika kita berada di Australia dimana togel sydney sangat terkenal dan kita bisa mendapatkan informasi pengeluaran sydney dimana saja dan kapan saja. Details to know Click here prediksi sgp
internet providers winnipeg WRS Web Solutions Inc. ranks with the best internet providers Winnipeg, Manitoba. The company is a no contract internet Winnipeg internet provider ISP providing unlimited Winnipeg home internet plans, Winnipeg internet packages, and Winnipeg internet services. Order internet online. Winnipeg unlimited Cable Internet & DSL internet (if available ). Winnipeg ISP offering excellent rates. Winnipeg unlimited internet plans available. Excellent support. No long term commitments. Unlimited Internet Service Provider. WRS Web Solutions Inc. is an Internet Service provider
10cric India is a prominent online sports betting platform catering specifically to Indian players. With its focus on cricket, the most beloved sport in India, it has gained immense popularity among enthusiasts. Offering a seamless and user-friendly interface, 10cric India provides a wide range of betting options. From pre-match and live betting to a diverse selection of markets, users can explore various wagering opportunities. The platform ensures competitive odds, secure transactions, and convenient payment methods tailored to Indian users. Overall, 10cric India has established itself as a trusted and exciting destination for Indian sports bettors, delivering an immersive and rewarding betting experience.
Thanks for the post. I really like your website. It’s always helpful to read through articles from other authors and use something from other web sites. If you are interested, you can join the game for fun here. UFABET
TikTok Video Downloader – SnapTik.Vn is one of the best free Download video Tiktok No Watermark tool available online. You can download TikTok video from any device you have.
TikTok Video Downloader – SnapTik.Vn is one of the best free Download video Tiktok No Watermark tool available online. You can download TikTok video from any device you have.
good
thank you this is good post.
I hope you visit my site thanks
여우알바
4D Slot
French translation
Moderne Lampen
slot anti rungkad
How does https://tga168.net/ the direct web platform stay at the forefront of innovation, constantly introducing new and exciting slot games?
Are you https://tga168.bet enticed by the seamless integration of cutting-edge technology and captivating gameplay on the direct web slots?
What makes https://tga-bet.com/ the direct web slots a truly immersive experience, where every spin takes you on a thrilling journey?
Have you tga slot discovered the convenience of easy deposits and withdrawals on the direct web platform?
Can you https://slotauto-wallet.net/ imagine the satisfaction of discovering hidden treasures and unlocking special features on the direct web slots?
moneyreign
مزاج
Kuliah Gratis di Jakarta
best snapchat fliters has never caused harm to anyone. Every day, a staggering 293 million users utilize the platform to share snaps—be it images, texts, or videos—with their loved ones.
situs pkv gamesTerpercaya juga menawarkan berbagai keunggulan lainnya. Mereka memiliki antarmuka yang mudah digunakan dan responsif, sehingga pemain dapat dengan mudah menjelajahi situs dan menemukan permainan yang mereka sukai. Selain itu, situs ini menyediakan layanan pelanggan yang ramah dan profesional, siap membantu pemain dalam mengatasi masalah atau pertanyaan yang mereka miliki
Harvard-incubated Experfy deploys Cloud Architects and Cloud Engineers with expertise in AWS, GCP, and Azure.https://www.experfy.com/hire/cloud-computing
Harvard-incubated Experfy deploys Cloud Architects and Cloud Engineers with expertise in AWS, GCP, and Azure.https://www.experfy.com/hire/cloud-computing
I like this blog so much its content was wonderful.
flipupdates
görükle escort Gerçek Bursa escort bayan görükle eskort kız arayanlar , güncel sayfamız ile yeni escort bayanlar ile tanışın. Sınırsız Bursa görükle escort Sitemizde.
พบกับประสบการณ์สุดพิเศษที่จะมอบสิทธิพิเศษให้แก่คุณ สามารถเข้าเล่นเกมสล็อตค่ายดังอย่าง PG SLOT ได้แบบฟรี ๆ ไม่ต้องฝากก่อน พร้อมรูปแบบการเล่นเหมือนเกมจริง pg ทดลองเล่น
เข้าเล่นสล็อตเว็บตรง เปิดให้บริการกับโอกาสสุดพิเศษอย่างเกมทดลองเล่นสล็อตฟรี ลิขสิทธิ์แท้โดยตรงจากค่ายเกม สล็อตPG Slot แจกโบนัสเครดิตฟรีสุดพิเศษ สูงสุด100% ฝาก-ถอน ไม่มีขั้นต่ำ เครดิตฟรีล่าสุด
write some posts that I am going to write soon. 부산출장안마before application of the cream your hands must be washed
https://www.kingdom-top.com/
vegetables. Think 80-10-10 when you eat. This means 80% vegetables 부산출장마사지 10% carbohydrate 10% meat. Just follow this diet and I
https://www.octagonanma.com/
patch test at the backside of your hand. As recommended, 부산출장마사지
before application of the cream your hands must be washed
https://www.octagonanma.com/
Untuk melakukan daftar Slot Gacor gampang maxwin terpecaya cukuplah mudah dan pastinya sangat aman dan nyaman menggunakan link https://cuan188.id/
Untuk melakukan daftar Slot Gacor gampang maxwin terpecaya cukuplah mudah dan pastinya sangat aman dan nyaman menggunakan link https://cuan188.id/
Untuk melakukan daftar Slot Gacor gampang maxwin terpecaya cukuplah mudah dan pastinya sangat aman dan nyaman menggunakan link https://cuan188.id/
Get started with Parimatch India today and dive into the world of online sports betting & casino gaming. With competitive odds, live betting, bonuses & secure payments, you can now support your favorite teams with huge rewards. Don’t miss out on this thrilling opportunity to get the ultimate combination of entertainment & rewards. Parimatch India
Parimatch strives to give customers the ultimate experience, and live dealer games let you take in the realism of a casino setting from your living room. https://parimatch-india.co/
فيب
WRS Intеrnеt Ottawa is your rеliablе choic among internet providers OttawaOntario, Canada. Wе offеr our sеrvicеs to most urban addrеssеs in Ottawa, (еxcеpt for ‘fibrе to thе homе’ adresses, and ‘rural addresses with no access to a cable TV line). With our top-notch tеchnology and dеdicatеd customеr support, wе strivе to dеlivеr thе bеst intеrnеt еxpеriеncе possiblе. Whеthеr you nееd high-spееd intеrnеt for strеaming, onlinе gaming, or working from homе, wе havе plans to suit your spеcific nееds
Join the winning team on sportsbetsin.com! Register today to claim your welcome bonus and start placing bets on your favorite sports teams. Our user-friendly platform makes it easy for you to place bets and win big. Don’t miss out on the action – sign up now! sportsbetsin.com
Parimatch India offers an extraordinary gaming experience with its diverse selection of live dealer games, including popular Indian favorites like Andar Bahar, Indian Rummy, and Teen Patti. By logging in to your Parimatch account, you can join real tables with human dealers, enjoying the thrill of a casino setting right from your living room. The high-definition video streaming ensures an immersive experience, allowing you to interact with the live dealer and other players in real-time. With its user-friendly interface and secure platform, Parimatch India provides an unforgettable journey into the world of live dealer games and sports betting.
Experience the thrill of online betting like never before at sattaking-in.com! As a leading betting site, we offer a wide range of exciting games and opportunities to win big. Register now to claim your generous welcome bonus and embark on an exhilarating journey into the world of satta king. Join our community of passionate players today and let the games begin!
satta king
Wе’ге a gaggle of volunteers аnd opеning a new scheme in oour community.
Ⲩour site offered uus wth valuable іnformation tߋ wоrk on. Yoս’ѵe performed аn impressive process andd оur wholе neighborhood ϲɑn Ƅe thankful
to уou.
My blog post … seributoto
Custom masters essay writer site https://maps.google.tl/url?sa=t&url=https%3A%2F%2Fessayservice.discount%2Fcodes%2Fpaperhelp%2F
Highly energetic post, І enjoyed that bit.
Ԝill tһere be a pɑrt 2?
Ꮋere is my blog post – astra338
안전놀이터목록Angels, catch Otani if you can…But it’s $600 million, and the LAA reporter is also ‘taking a big deal’
Evinizin konfor ve sıcaklığını İstanbul’un tarihi ilçesi Üsküdar’a taşıdığınızı, İstanbul Boğazı’nın o enfes kokusu ve atmosferiyle uyandığınızı hayal edin… üsküdar hotel
Ꮩery great post. І ϳust stumbled սpon your blog and ᴡanted to mention tyat I’ve trul loved surfing aгound
your blog posts. Аfter all I’llbe subscribing tߋ yor rss feed aand I hope үоu write
oncе mоre sοon!
Hеrе is myy site: angka keluar sdy
Immediate Edge Join and benefit from its automated trading system that allows you to take advantage of market volatility. This trading platform claims to use sophisticated trading bots equipped with specific AI technology to execute profitable trades and investments on your behalf.
Hi my friend! I wiѕh to sɑy that this post is awesome,
nice writtedn аnd include ɑpproximately ɑll imⲣortant infos.
Ӏ’d liқe to peer exztra posts ⅼike tһis .
Feel free tο visit my webpage: Ahha4d Link Alternatif
Parimatch strives to give customers the ultimate ex perience, and live dealer games let you take in the realism of a casino setting from your living room. Parimatch India offers a wide range of live dealer games such as Andar Bahar, Indian Rummy and Teen Patti. With these games, you can join in on a real table with a human dealer and have an immersive experience. Let’s take a closer look at the live dealer games available at Parimatch India.
Quantum AI Trading is a trading platform that lets you trade forex, stock, cryptocurrency, and more. Get to know more about what the platform services offer and fast platform where you may start your trading journey more comfortably
Experience the thrill of online betting like never before at sattaking-in.com! As a leading betting site, we offer a wide range of exciting games and opportunities to win big. Register now to claim your generous welcome bonus and embark on an exhilarating journey into the world of satta king. Join our community of passionate players today and let the games begin!
สล็อตออนไลน์
ก่อนที่คุณจะนำเทคนิคการเล่น สล็อต ใด ๆ ก็ตามไปใช้ในการเล่น คุณต้องรู้ว่า มีเป้าหมายอย่างไร เพราะจะช่วยทำให้มองหาวิธีการที่เหมาะสม และตรงตามเป้าหมายของคุณได้มากยิ่งขึ้น อีกทั้งยังช่วยเพิ่มแรงจูงใจในการพัฒนาตนเอง โดยเฉพาะคนที่อยากจะเป็นมืออาชีพ การพึ่งพาอาศัยดวงหรือโชคลาภเพียงอย่างเดียว ไม่อาจที่จะนำคุณไปสู่จุดนั้นได้ เพราะมีเพียงสิ่งที่เรียกว่า ความพยายามและความอดทน ที่สามารถนำพาให้คุณประสบความสำเร็จ ถึงแม้เส้นทางดังกล่าวจะไม่ได้โรยด้วยกลีบกุหลาบ แต่ทุกความผิดพลาดคุณสามารถนำมาใช้เป็นบทเรียน และมองหาวิธีการใหม่ เพื่อนำมาปรับปรุงแก้ไขช่วยทำให้การเดิมพันออนไลน์ของคุณเป็นเรื่องที่จับต้องได้
Canada internet providersDo you have questions such these? Are there internet providers near me? How can I find internet in my area? Is home internet available in my area? Are there telecommunications service provider near me? Which internet is available in my area? Perhaps we can help you find home internet availabiility by postal code. On request, we can help you find home internet by address. To check internet availability by postal code, please enter the Postal Code below. (Please note that results for non-urban area postal codes may be less accurate, so you may wish to ask us to check those manually using the contact form.) Canada Internet Providers enables you to find home internet availability by postal code Canada:
This site was… how do I say it? Relevant!! Finally I have found something which helped me. Appreciate it!
Its like you read my mind!
Join the winning team on sportsbetsin.com! Register today to claim your welcome bonus and start placing bets on your favorite sports teams. Our user-friendly platform makes it easy for you to place bets and win big. Don’t miss out on the action – sign up now!
الدراسة في تركيا
من اهم مميزات الدراسة في تركيا هو انخفاض تكاليف المعيشة و الدراسة في تركيا مقارنة بالدول الأوروبية
بالاضافة الى أن معظم جامعات تركيا توفر لطلابها امكانية الدراسة في تركيا باللغة الانجليزية وذلك في الجامعات الحكومية و الخاصة التركية , مما يسهم في تحضير خريجي الجامعات التركية لدخول سوق العمل العالمي ,
كما أن الجامعات في تركيا تولي اهتماما كبيرا للبحث العلمي , وذلك من خلال توفيرها مختبرات ومعامل مجهزة بأحدث التقنيات والتي من شأنها مساعدة الطلاب وتقديم الدعم اللازم لهم اثناء عمل أبحاثهم ودراساتهم.
وتصنف تركيا في المرتبة السابعة كأفضل دولة للعيش والعمل , متقدمة على العديد من الدول الغربية، وفي المرتبة السادسة كأكثر بلد جذبا للطلاب والسياح، حيث بلغ عدد زوار مدينة اسطنبول وحدها أكثر من 115 مليون شخص في غضون 15 سنة لغرض العمل والدراسة والسياحة.
BTS Jin, who went to the army, saved a Brazilian fan?… Photo of robber startled슬롯사이트Reports emerged that a woman in Brazil escaped robbery by putting a photo of group BTS member Jin (real name Kim Seok-jin) in her cell phone case.
Twitter’s advertising revenue cut in half after Elon Musk acquisition카지노솔루션Elon Musk said that since acquiring Twitter for $44 billion in October, advertising revenue has nearly halved.
Ukraine War: What’s Inside the Regions Recaptured from Russia?As Ukrainian forces recaptured some territories in a counter-offensive, the BBC was one of the first media outlets to gain access to the recaptured territory and sought it out on its own.by카지노사이트
egblog الكلمات المفتاحية وكلمات البحث حيث يتم استخدامها في البحث العلمي ويكون لأغراض فهرسية، حتى يتمكن الأفراد من العثور على الدراسات التي يبحثون عنها الموجودة في قواعد بيانات الأبحاث العلمية كالمجلات وغيرها، كما يجب أن تضع في اعتبارك أنه في عام كان
I was able to find good info from your content.
Se trata de Federico Bravo, v보령출장샵olante cordobés de 24 años. En la última temporada jugó en el Panetolikos FC de Grecia. Su trayectoria incluye instituciones importantes como Boca Juniors (donde debutó) y New York City (Estados Unidos).
Luego de firmar su vínculo por un año con la Institución de calle Grella, Federico dió una palabras al Sitio Oficial
skin care routin: https://llskinshop.com/
great
เว็บไซต์สล็อตนั้นได้จัดแจงความสบายสบายให้ผู้เล่นได้เข้าไปเล่นเกมสล็อตแบบง่ายๆ ฝาก 50 รับ 100 โดยที่ไม่ต้องทำรายการผ่านคณะทำงาน
ทางเว็บไซต์สล็อตนั้นจะต้องมีจริงๆเนื่องจากว่าอย่าลืมว่าผู้เล่นนั้นจำเป็นต้องนำเงินมาลงทุนสำหรับเพื่อการเล่น yg slot หากเว็บไซต์สล็อตที่ไม่มีระบบที่ช่วยผู้เล่นสำหรับเพื่อการทำรายการฝาก-ถอนอาจทำให้กำเนิดความยุ่งยากแน่ๆ
บริการที่ทำให้ผู้เล่นนั้นทำรายการได้เองกล้วยๆโดยไม่ต้องมารอคณะทำงานเลย คุณสามารถที่จะกดฝาก-ถอนได้ด้วยตัวเอง สล็อตเว็บตรง ก็ได้ดีไซน์บริการนี้ให้ใช้ง่ายและไม่สลับซับซ้อน
ผู้เล่นสามารถสุขใจได้เลยถ้าหากมาลงพนัน แล้วที่น่าดึงดูดไปกว่านั้นเป็นทางพวกเราได้มี เครดิตฟรี กดรับเอง การเปลี่ยนแปลงบริการฝาก-ถอนให้ดีขึ้นโดยได้เพิ่มข้อจำกัดสุดพิเศษอย่าง
พวกเราจะมาเสนอแนะการฝาก-ถอนที่เพิ่มความรวดเร็วสำหรับการทำรายการ ที่พวกเราเปลี่ยนแปลงมาเป็นการฝาก-ถอนผ่านระบบ เครดิตฟรีกดรับเอง นั้นก็เพราะเหตุว่าเป็นการที่เพิ่มความปลอดภัยสำหรับในการทำรายการเพิ่มขึ้นเรื่อยๆ
ยืนยันไม่ผิดหวังแน่ๆ เพราะว่าทาง สล็อต เว็บไซต์ใหญ่ pg นั้นได้ปรับปรุงและก็เปลี่ยนแปลงระบบต่างๆ 20รับ100 ให้ดียิ่งขึ้นแล้วก็ตอบปัญหาผู้เล่นผู้คนจำนวนมากได้อย่างดีเยี่ยม ไม่ว่าจะคือปัญหาแบบไหน
เล่นเกมสล็อต ยอดนิยมสูงที่สุด เป็นพวกกับพวกเราคุณจะไม่พลาดเกมสล็อตใหม่ๆจากค่ายดัง ที่นักพนันสล็อตออนไลน์ติดอกติดใจ โปร 10 รับ 100 เนื่องจากว่าพวกเราได้รวมเว็บไซต์สล็อตพวกนั้นไว้ตรงนี้แล้ว
เว็บไซต์สล็อตจากนักปรับปรุงคนประเทศไทย ที่สร้างและก็ดีไซน์เพื่อผู้ใช้งานคนไทยโดยเฉพาะอย่างยิ่ง 10 รับ100 ระบบการใช้แรงงานที่รองรับนานาประการภาษา รวมทั้งภาษาไทยด้วย ไม่เพียงเท่านั้นผู้ให้บริการสล็อตออนไลน์
สูตรสล็อตใช้งานได้จริง พร้อมลุ้นรางวัลทำเงินได้ง่ายมากยิ่งขึ้นจากการพนันสล็อต PG ฝาก10รับ100ล่าสุด เป็นสูตรการเล่นสล็อตที่ถูกคัดสรรมาจากเซียนสล็อต
โดยเหตุนี้แม้ต้องการทดลองพนันได้กำไรจากเกมสล็อตได้แบบมั่นใจๆจำเป็นต้องเข้าไปทดสอบเล่นสล็อต pgฟรี 50รับ100 ถอนไม่อั้น รวมทั้งทดลองใช้สูตรสล็อตแบบต่างๆได้ในโหมดนี้ เพื่อเพิ่มความมั่นใจและความเชื่อมั่นได้แบบเกิน 100%
เกมสล็อตออนไลน์ ที่สร้างจำนวนเงินอย่างใหญ่โต ให้กับหลายผู้เล่นมานับไม่ถ้วน พร้อมโปรโมชั่น 50 รับ 100สมัครเป็นสมาชิกรับโบนัสไปเลย 50% ฝาก – ถอน ได้ด้วยตัวเอง
บริการเกมสล็อตออนไลน์ ไม่ผ่านเอเย่นต์ ไม่เป็นอันตราย รวมทั้งมีความยั่งยืนและมั่นคงสูง เล่นได้เอาไปเลย slotzeed โอนไว จ่ายจริง หารายได้กล้วยๆแค่เพียงเล่นเกมสล็อตกับพวกเรา ท้าทายให้ทดลอง ตรงตามมายี่ห้อฐานสากล มาใหม่แม้กระนั้นประสิทธิภาพ 100%
โบนัส แล้วก็แจ็คพอตล้นหลาม รอคอยคุณอยู่ในเกม กราฟฟิคภาพ เสียง เอฟเฟกต์ต่างๆน่าเร้าใจ 50 รับ 100 เสริมให้มีความฮึกเหิมสำหรับเพื่อการเล่นมากเพิ่มขึ้น สมัครเป็นสมาชิก วันนี้รับโบนัสไปเลย 50% ต้อนรับสมาชิกใหม่ คุ้มสุดๆ
เว็บไซต์ของพวกเรานั้น ไม่เพียงแค่มีเกมสุดได้รับความนิยมเพียงแค่นั้น เว็บไซต์ของพวกเรายังเป็นเว็บไซต์ตรง 19 รับ 100 เล่นกับพวกเรารับประกันว่า มีความมั่นคงยั่งยืนแน่ๆ เล่นได้พวกเราจ่ายจริง แน่ๆ 100%
ในคาสิโนออนไลน์ ที่มีเกมเยอะมากให้เลือกเพลิน แล้วก็ทำเงินได้ในขณะเดียวกัน สล็อตออนไลน์ pgzeedgame เป็นเยี่ยมในเกมคาสิโนที่เข้าถึงง่าย มีแบบการเล่นไม่สลับซับซ้อน
ไม่ว่าคุณจะเป็นผู้ใดกัน เป็นนักพนันหน้าเก่า หรือใหม่ ก็ไม่จำเป็นต้องเป็นห่วงว่าจะเล่น เกมสล็อต ได้กำไรได้ยังไง 20 รับ 100 เนื่องจากว่าวันนี้ทาง PGSLOT มี สูตรสล็อตฟรี มาแจก ไม่ต้องลงทะเบียนเป็นสมาชิกก็สามารถใช้ประโยชน์เล่นในเกม
แนวทางการเลือกเว็บไซต์สล็อต ที่ดีเยี่ยมที่สุดสำหรับพนัน บางครั้งก็อาจจะมิได้วัดจากชั้นบน Google เพียงอย่างเดียวเพียงแค่นั้น 25 รับ 100 ผู้เล่นมือใหม่ควรรู้หลักเกณฑ์การพินิจที่มากกว่านั้น
โปรโมชั่น บริการ เเละอื่นๆซึ่งวันนี้คณะทำงานของพวกเราได้นำ แนวทางเลือกเว็บไซต์สล็อต ไม่ให้โดนโกง pgslot42 สำหรับมือใหม่ มาบอกเเบบหมดเปลือก มือใหม่จำต้องเลือกอย่างไร
เล่นสล็อตออนไลน์ เพื่อได้กำไร มีวิธีการเช็คไม่ยาก โดยทั่วไปแล้วผีพนันใช้แนวทางอะไรในการเลือกมองเว็บไซต์ตรงสล็อต 10รับ100 มอง คุณลักษณะของเว็บไซต์สล็อต ที่มือใหม่จำต้องทราบไว้
เลือกเล่นเเล้วเสี่ยงน้อยกว่าเว็บไซต์ทั่วๆไปจริงไหม แนวทางคิดเเบบนี้สามารถเอาไปประยุกต์กับการเลือกเว็บไซต์สล็อตได้ดิบได้ดี 100% 29รับ100 สล็อตเว็บไซต์ใหญ่ เว็บไซต์ตรง เว็บไซต์สล็อตชั้น 1
อีกหนึ่ง วิธีการเลือกเว็บไซต์สล็อต ให้ได้เว็บไซต์ที่ยอดเยี่ยม สล็อตเว็บไซต์ใหญ่ รวมทุกค่าย พนันเเบบไม่จำเป็นที่จะต้องมาวิตกกังวลเรื่องคดโกง pgslot42 หรือความปลอดภัย เป็นเลือกเว็บไซต์สล็อตที่รองรับการเล่นจากทุกระบบ
เว็บไซต์สล็อตที่รองรับการเล่นจากทุกระบบ เข้าถึงง่ายทุกแพลตฟอร์ม ไม่ว่าจะเป็นโทรศัพท์มือถือ เเท็บเล็ต หรือคอมพิวเตอร์ 9 รับ 100 เว็บไซต์สล็อตที่ดีต้องมีโอกาสพนันทั้งยังในรูปเเบบเเอพพลิเคชั่น
มือใหม่ต้องการเล่นสล็อตออนไลน์ เเต่ติดปัญหาด้านประสบการณ์ ไม่กล้าลงทุนมากมาย เลือกลงทะเบียนเป็นสมาชิกกับพวกเรา pgzeedgame ประสิทธิภาพยอดเยี่ยม คุณจะบันเทิงใจกับการพนันเเบบไม่มีที่ว่ากล่าว
แจกโชคใหญ่ก่อนผู้ใด ผู้เล่นสามารถเข้ามาร่วมสนุกสนานกับพวกเรากล้วยๆเล่นผ่านมือถือ เเละเครื่องมือที่คุณสบายใช้งานได้ทุกวี่ทุกวัน ฝาก 10 รับ 100 เกมนี้นับว่าเป็นอีกหนึ่งเกมที่ได้สร้างความระทึกใจ
เว็บไซต์ของพวกเราเต็มไปด้วยโปรโมชั่น เเละตัวช่วยเยอะมาก ที่เพิ่มจังหวะเเตกเเจ็คพอเพียงตได้ง่ายทันใจ 50รับ150 ไม่ว่าจะเป็นผู้เล่นเก่าหรือใหม่ ก็เข้ามาเลือกใช้ได้ฟรี! กด สมัครเป็นสมาชิก
Thank you for writing a good post 캔디알바
Thank you for writing a good post 캔디알바
https://www.waltbabylove.com/upload/image/inc/?1xbet_promo_code___bonus_codes_1.hml
Uang88 sebagai situs betting ternama tentunya menyediakan link alternatif daftar situs Uang 88 Slot gacor terbaru yang menghadirkan metode pembayaran terlengkap
VipBet888 atau juga bisa di sebut agen VipBet 888 slot online terpercaya 2023 telah menyediakan berbagai daftar permainan terbaik serta paling gacor
Ladang78 menyediakan link login terpercaya Ladang 78 slot member vip yang memberikan bocoran dan pola slot gacor rtp live dengan winrate kemenangan 98%
Kedai169 menyiapkan link alternatif daftar situs Kedai 169 slot terbaru dengan daftar permainan terbaik slot online, togel, sportbook dan live casino
Royal88 ialah daftar situs resmi Royal 88 slot terbaik hari ini dengan adanya metode deposit via pulsa Rp 20.000 sekaligus bocoran slot pragmatic play
Ladang78 adalah situs Ladang 78 slot gacor resmi khusus member vip dengan berbagai jenis permainan slot terbaik dan pola slot jitu untuk kemenangan maxwin
Olo4d merupakan bandar judi togel macau Olo 4d terpercaya tahun ini dengan adanya pasangan 2 sampai 3 angka termurah dan permainan live casino terbaik
Olo4d merupakan bandar judi togel macau Olo 4d terpercaya tahun ini dengan adanya pasangan 2 sampai 3 angka termurah dan permainan live casino terbaik
Kedai169 menyediakan link alternatif Kedai 169 slot terbaik pragmatic memberikan rtp slot sekaligus deposit murah Rp 20.000 deposit pulsa tanpa potongan
Klik4d sebagai daftar situs Klik 4d slot resmi dan gacor pragmatic dengan pola slot jitu dan rtp slot live hari ini sekaligus jackpot bonus sensasional
Hoki188 sebagai daftar situs Hoki 188 slot deposit pulsa Rp 20.000 serta pola permainan slot gacor untuk kemudahan menang dan bonus serta jackpot berlimpah
Beton88 menyediakan link alternatif situs Beton 88 slot terpercaya 2023 dengan permainan slot gacor pragmatic play, pg soft, microgaming, habanero, joker123
Megawin merupakan situs Mega Win slot resmi pragmatic play tahun ini dengan pola slot jitu dan rtp live hari ini untuk kemenangan maxwin dan sensasional
Dewaslot menyediakan link alternatif Dewa Slot mudah maxwin terpercaya tahun 2023 dengan pola jitu dan rtp live slot gacor pragmatic play terbaik saat ini
Bp77 merupakan daftar situs Bp 77 slot online terbaik dan terpercaya tahun 2023 dengan permainan slot online terbaik, live casino, poker, togel 4d terbaik
BestLoveSexDoll.com – THE BEST SEX DOLLS ONLINE STORE IN USA, UK, EU & CANADA. FREE Shipping Worldwide! 3-15 Days Arrive! Best Quality and Reviews! Build and Customize your Lifelike Sex Doll Robot. SAFE and DISCREET Shipping. High-quality sexy love doll for sale. Based in USA and 24/7 Live Support! Order yours today!
#1 World Best Sex Dolls Online Store – Real Sex Love Doll | https://realsexlovedoll.com – aims to build a reliable platform to provide premium real sex dolls for customers. Below is a detailed manual to lead you to the best sex dolls. If you are interested in sex dolls but still hesitate whether to have a try, or if you decide to purchase one, but you have no idea of how to choose, this manual can help! Come and choose a quality doll that meets your satisfaction. There’s a brand-new world waiting for you!
Our lifelike cheap sex dolls – https://cherrypiesexdoll.com – for sale are made of premium silicone and TPE materials to give new real dolls lifelike soft skin and guarantee a realistic feeling. In addition, our hot love dolls are equipped with a human-like metal skeleton and flexible joints, which can support anal sex, oral sex, vagina sex. Besides, every sex doll is handmade by our excellent professions, and we strictly control each process, aiming to bring you lifelike sex dolls and the best sex experience.
If you’re looking for the best affordable sex dolls, you’ve come to the right place. https://www.milfsexdoll.com/ . We can customize a large number of full size TPE & silicone sex dolls for you. Our life size love dolls are designed to provide the best sex experience for men and women who need wild and exciting sex. We have a real sex doll factory, we have good cooperation and interaction with other adult factories, which means you can get the best quality online at the lowest price and have more customized experience.
Buy Affordable Realistic Silicone Sex Dolls for sale – https://gorgeoussexdoll.com/ – Shop Luxury Sex Dolls, Shipped in Discreet Packaging. Rated #1 In Customer Satisfaction, FIVE STAR Reviews, FREE SHIPPING on all orders, based in New York, USA.
northwest registered agent northwest registered agent reviews ties for No. 6 in our rating of the Best LLC Services of 2023. The family-owned and -operated company has offices in all 50 states. northwest registered agent reviews If you want to eliminate the hassle of forming a legal business entity any any state, I’d highly recommend. Fast, easy and great.
northwest registered agent northwest registered agent reviews ties for No. 6 in our rating of the Best LLC Services of 2023. The family-owned and -operated company has offices in all 50 states. northwest registered agent reviews If you want to eliminate the hassle of forming a legal business entity any any state, I’d highly recommend. Fast, easy and great.
mold testing tampa The inspection was thorough and the friendly. Once the inspection was complete, they were prompt in delivering the results. They also gave recommendations on how to prevent future mold growth which I found helpful
เล่นสล็อตออนไลน์ทำเงินเพลิดเพลินๆฟันเงินรางวัลใหญ่แบบปังๆ50รับ100 สามารถเบิกเงินรางวัลออกได้ไม่ยั้ง แถมยังทำรายการทางด้านการเงินอย่างฝากหรือเบิกเงินออกได้ไว ด้วย
ไม่รับโปรโมชั่น ถอนง่ายๆ ถูกใจนักเดิมพันสายโอนไว สล็อตเครดิตฟรี ใครอยากทำรายการเร็วๆ ไม่ต้องรอ ไม่ต้องทำเทิร์น ทำตามนี้ได้เลย!
ฝากถอน ไม่มีขั้นต่ำ เล่นสล็อตทำกำไรมันส์ สล็อต ใหม่ล่าสุด เปิดให้ใช้บริการตลอด 24 ชั่วโมง ไม่ต้องรอนาน ไม่ต้องรอคิว
ฝากไม่รับโปร ไม่มีเงื่อนไข ถอนได้ไม่อั้นมากกว่า 5 แสน pgslot สัมผัสกับประสบการณ์เดิมพันสล็อตออนไลน์ที่ดีที่สุดไม่ยุ่งยากกับอะไรทั้งสิ้น
โปรดีสำหรับผู้ที่ไม่ต้องการทำยอดเทิร์นหลายเท่า ไม่ติดเงื่อนไข เครดิตฟรี 188 ไม่ต้องทำเทิร์น เล่นได้เท่าไหร่ก็ถอนได้แน่นอน!
โปรโมชั่น PG SLOT โปรเด็ด และพิเศษสุด ๆ ไว้ต้อนรับสมาชิกใหม่ของเรา เจ้าเจ๊ง ทั้งนี้เรายังได้จัดเตรียมโปรโมชั่นพิเศษอื่น ๆ ให้กับสมาชิกของเรา ทั้ง เช้า สาย บ่าย เย็น และดึก
มีโปรโมชั่นสุดพิเศษ เตรียมไว้ให้บริการสมาชิกมากมาย 50รับ100 ก็มีโปรโมชั่นคอยมอบความสนุกให้คุณได้ลุ้นโบนัสกันทุกช่วงเวลา
โปรโมชั่นสล็อตPG ฟรีเครดิต สมัครสมาชิกใหม่รับโบนัสทันที เครดิตฟรี กดรับเอง ยังมีโปรโมชั่นอื่น ๆ น่าสนใจอีกเพียบ ไม่ว่าจะเป็นโปรฝากครั้งแรก โปรรวยทั้งวัน
สนุกกับเกมสล็อตใหม่ล่าสุดได้ทั้งวัน pg slot คัดสรรมามอบให้กับคุณได้เต็มอิ่มกับความสุขบนมือถือ ที่ปลอดภัยทั้งระบบใช้งาน
เดิมพันออนไลน์ ลงทุนน้อย กำไรเยอะ ต้อง pgslot เกมสล็อตออนไลน์ สล็อตแนวใหม่ ไม่ซ้ำใคร
PG โปรสมาชิกใหม่ จ่ายเต็มไม่มีกั๊ก เครดิตฟรี ยืนยันเบอร์ มีเจ้าหน้าที่พร้อมให้บริการและช่วยเหลือตลอด 24 ชั่วโมง
เดิมพันออนไลน์ ลงทุนน้อย กำไรเยอะ ต้องเล่นเกมสล็อตออนไลน์ ทางเข้าpg ผู้นำด้านการบริการเดิมพันออนไลน์ ครบวงจร
เราเป็นเว็บสล็อต ไม่ผ่านเอเย่นต์ ที่คนนิยมเล่นเยอะที่สุด pg เว็บตรง เว็บใหญ่ เว็บแท้ ปลอดภัย มั่นคง
แจกเครดิตฟรี ไม่จำกัด ไม่ต้องฝาก ไม่ต้องแชร์ เครดิตฟรี 50 มอบโชค ลุ้นรับรางวัล ฟรีเครดิต จากการเข้าร่วมกิจกรรม ต่างๆ
เราได้จัดกิจกรรมพิเศษ อื่นๆ อีกมากมาย ให้สมาชิกได้ลุ้นรับโบนัส เครดิตฟรี กับ superslot รับฟรีกันไปเล๊ย ใครที่ยังไม่เป็นสมาชิกสมัครกับเราวันนี้รับโบนัสฟรี
เกมยอดฮิตในปัจจุบัน เป็นเกมสล็อตน้องใหม่ ที่ได้รับความนิยมสูง pgslot และตอบโจทย์ให้กับนักเล่นสล็อตออนไลน์ ได้ดี ด้วยคุณสมบัติพิเศษ
Thanks for sharing such a nice article. Its helpful for everyone keep blogging like this. Very unique content. https://www.bulkgmailaccounts.com/buy-google-reviews/
เกมสล็อตรูปแบบใหม่ ที่ได้รับความนิยมเป็นอย่างมาก เครดิตฟรี ที่แจ็คพอตแตกบ่อยที่สุด
อัพเดตเกมออกใหม่ ทุกวัน พร้อมรีวิวเกมสล็อต ตลอดเวลา pg slot เว็บตรง สำหรับนักเดิมพันสล็อตออนไลน์ ที่ห้ามพลาดกับเกมสล็อตที่มีรางวัลแจ็คพอตจำนวนมหาศาล
การันตีได้ว่าการเล่นเกมสล็อตจะสนุก และสร้างรายได้ให้กับผู้เล่นได้มากยิ่งขึ้น pg เกมสล็อตที่แตกง่าย 2023
สำหรับใครที่อยากลุ้นรับรางวัลง่ายๆ แบบไม่ต้องสุ่มเกมเล่นเอง pg ที่คุณไม่ควรหากคุณต้องการรางวัลใกญ่จากเกมสล็อตที่รอคุณเข้ามาเล่นอยู่
เกมสล็อตแนวตั้งมาใหม่เล่นได้บนมือถือ ทั้งระบบ ios และ android เครดิตฟรี50 ไม่ต้องดาวน์โหลดและติดตั้ง ระบบเกมที่เสถียรที่สุด รองรับเมนูภาษาไทย
โปรโมชั่นสมัครสมาชิกใหม่ ฝาก 20รับ100 มีเกมให้เลือกเล่นมากมาย หลากหลายรูปแบบ มากกว่า 70 เกม
โปรโมชั่นสล็อตPG ฟรีเครดิต สมัครสมาชิกใหม่รับโบนัสทันที สล็อตวอเลท ยังมีโปรโมชั่นอื่น ๆ น่าสนใจอีกเพียบ ไม่ว่าจะเป็นโปรฝากครั้งแรก โปรรวยทั้งวัน โปรรวยช่วงบ่าย และอื่น ๆ อีกมากมาย
มีโปรโมชั่นสุดพิเศษ เตรียมไว้ให้บริการสมาชิกมากมาย สมัครสมาชิกใหม่กับเรา pg slot แตกง่าย ถือเป็นโปรโมชั่นที่มาแรงที่สุดในขณะนี้
เดิมพันออนไลน์ ลงทุนน้อย กำไรเยอะ เครดิตฟรี50 ต้องเล่นเกมสล็อตออนไลน์ สล็อตแนวใหม่ ไม่ซ้ำใคร
อยากพบเกมสล็อตออนไลน์ใหม่ล่าสุด และบริการที่ดีที่สุดได้ทั้งวัน ต้องเล่นผ่าน pgslot เรารวมโปรสล็อต PG ตามช่วงเวลาต่าง ๆ มาให้คุณได้รับสิ่งที่ดีที่สุดกลับไปเสมอ
เกมที่ให้บริการมีให้เลือกมากกว่า 200 เกม เว็บไซต์ของเราจัดหนักกับ pgdragon เดิมพันออนไลน์ ลงทุนน้อย กำไรเยอะ ต้องเล่นเกมสล็อตออนไลน์ สล็อตแนวใหม่ ไม่ซ้ำใคร
Blockchain-based music streaming platform Audius announced Thursday that it had launched full Sola파주출장샵na NFT integration, allowing its more than six million users to begin featuring digital collectibles from the Solana library.
Amazing website and blog your
lunchtime results Teatime is a British tradition of having a light meal accompanied by a cup of tea in the late afternoon, typically around 4 pm. It is a social occasion that allows people to take a break from their busy schedules and catch up with friends or family over a warm cup of tea and some light refreshments like scones, sandwiches, or cakes.
ค่ายเกมชั้นนำ Pg slot, Joker Gaming, AMB poker, Slotxo, Pragmatic Play, จีคลับ888 รองรับการใช้งานของลูกค้าทุกท่านอย่างดีที่สุด ให้ลุกค้าทุกท่านได้ทำการฝากและถอนเงินเร็วยิ่งขึ้น.
DLeading game camps Pg slot, Joker Gaming, AMB poker, Slotxo, Pragmatic Play, จีคลับ888 Supports the use of all customers as best as possible. Let all customers make deposits and withdrawals faster.
teatime results Lunchtime is the midday break in a work or school day when people take a break from their activities to eat food. It typically occurs around noon or early afternoon, and it serves as an opportunity to recharge and refuel. Lunchtime can be a time to socialize with colleagues, friends, or family members over a meal, and it can also be a time to relax and unwind.
โปรโมชั่น PG Slot ที่น่าดึงดูด กำลังเป็นที่นิยมชั้น 1 50รับ100 พิเศษจากเว็บไซต์สล็อต แจกเครดิตฟรี ทุกๆวัน เล่นได้อย่างจุใจ ทุกๆที่ ทุกเมื่อ
สมัครสมาชิกใหม่รับ โปรโมชั่นพิเศษ ของโปรโมชั่น สล็อตเครดิตฟรี ถอนได้จริงทุกบาททุกสตางค์มาเอาใจสมาชิกกันตลอด ไม่ยุ่งยาก ไม่มีเงื่อนไขเยอะ
โปรโมชั่น PG SLOT พิเศษต่างจากค่ายอื่น รับโบนัส หลายเท่า สล็อต ที่ทางเว็บคัดสรรมาให้กับคุณได้เต็มอิ่มกับความสุข สนุกไปกับเกมบนมือถือ มีแต่ได้กับได้ คุ้มค้า โปรโมชั่นลดรับเครดิตเพิ่มมากขึ้น
ขั้นตอนง่ายๆ ในการรับโบนัสต่างๆ เพียงแค่เป็นสมชิกกับ pgslot เว็บไซต์เราได้รวบรวมโปร โม ชั่นที่ผู้เล่นนิยม และชอบที่สุด คุ้มที่สุด และเล่นเยอะที่สุด
สนุกไปกับเกมบนมือถือ มีแต่ได้กับได้ คุ้มค้า โปรโมชั่นลดรับเครดิตเพิ่มมากขึ้น เครดิตฟรี 188 พีจีสล็อต โปรโมชั่น ถอนไม่อั้น โปรดีสุดพิเศษที่ควรสมัคร
เเจ็คพอตแตกบ่อยที่สุด รับโบนัสกันแบบจุใจ เปิดให้บริการตลอด 24 ชั่วโมง เจ้าเจ๊ง เล่นได้ทุกเพศทุกวัย โปรโมชั่นภายในเว็บไซต์ยังมีรายละเอียดสำคัญ
ไม่ต้องกังวลเรื่อง ฝาก-ถอน หรือ ปัญหาระบบล่ม ไม่การโดนโกง 50รับ100 ไม่ต้องกังวลปัญหาโปรโมชั่นต่างๆและเว็บไซต์ของเรายังออกแบบมาเพื่อการใช้งานแบบง่ายๆ
พบกับโบนัสที่แจกกันอย่างจุกๆ พบกับเเจ็คพอตเเตกที่กระจาย โปรโมชั่นรับกำไรเข้ากระเป๋าแบบชิลๆ เครดิตฟรี กดรับเอง เกมแตกบ่อย มาให้เลือกเล่นอย่างจุใจ
โปรโมชั่น ถอนไม่อั้น โปรดีสุดพิเศษที่ควรสมัคร pg slot เว็บไซต์เราได้รวบรวมโปร โม ชั่นที่ผู้เล่นนิยม และชอบที่สุด คุ้มที่สุด
รับโบนัสกันแบบจุใจ เปิดให้บริการตลอด 24 ชั่วโมง pgslot มีเกมสล็อตให้ทดลองเล่นมากกว่าพันเกม ทั้งใหม่เเละเก่า รวมถึงเกมยอดฮิต ยอดนิยม
เพียงแค่สมัครเข้ามาเป็นสมาชิกที่เว็บของเราเท่านั้น รับฟรีไปเลยทันที เครดิตฟรี ยืนยันเบอร์ เว็บสล็อตออนไลน์ที่พร้อมแจก เครดิตฟรี ทุกวัน
เพียงแค่มีมือถือเครื่องเดียวก็สามารถรวยได้แบบง่าย ๆ มีทุนน้อยก็สามารถเล่นได้ ทางเข้าpg ที่สำคัญฝากถอนไม่มีขั้นต่ำ ด้วยบริการออโต้ที่รวดเร็วทำให้การเล่น
สล็อตออนไลน์ ที่สามารถเปลี่ยนให้คุณกลายเป็นเศรษฐีได้ pg เพียงแค่สมัครสมาชิกเท่านั้น
ได้ทั้งสมาชิกเก่า และ สมาชิกใหม่ ได้ทุกวัน สามารถเข้า เล่นสล็อต ได้ผ่าน เครดิตฟรี 50 สล็อต รูปแบบใหม่ ที่คุณต้องไม่เคยเจอมาก่อนที่ไหนแน่นอน
เกมสล็อตออนไลน์รูปแบบใหม่ ยอดนิยมอย่างยิ่ง ในการเอาชนะเกมสล็อต superslot จะไม่ใช่เรื่องยากอีกต่อไป ถ้าหากเล่นเกมสล็อตได้ถูกทาง
เกมสล็อตออนไลน์ สมาชิกใหม่ ที่มาแรงมากมายเวลานี้ pgslot สร้างช่องทางสำหรับการลุ้นรับเงินรางวัลจากการเล่นสล็อตออนไลน์ได้มากขึ้น
ได้จัดโปรโมชั่นพิเศษ แจกเครดิตฟรีให้กับสมาชิกใหม่ เครดิตฟรี โดยท่านสามารถขอโปรโมชั่นพิเศษต่างๆผ่านแอดมินได้ และเราเป็นเว็บที่แจกเครดิตฟรีหนักกว่าเว็บอื่นเครดิตฟรี
เกมสล็อตออนไลน์ กำลังเป็นที่นิยมมากที่สุด เปิดบริการอย่างเป็นทางการที่แรกในไทย pg slot เว็บตรง เว็บไซต์ของเราจดทะเบียนการค้าอย่างถูกกฎหมาย
เว็บไซต์ที่ดีที่สุด และบริการเกมสล็อตที่มีให้ท่านได้เลือกเล่นมากมาย pg พร้อมโปรโมชั่นพิเศษต่างๆ และมีโปรโมชั่นพิเศษมากมาย ให้ท่านได้เลือกและลุ้นรับโบนัสเครดิตฟรี
ระบบอัตโนมัติที่ทำธุรกรรมการเงินที่รวดเร็วทันใจ pg ม่ว่าจะเป็น ฝาก-ถอน ก็สามารถทำรายการไม่เกิน 15 วินาที ไม่ต้องส่งสลิป มีแอดมินที่คอยให้บริการตลอด 24 ชั่วโมง
สล็อตออนไลน์รูปแบบใหม่ 3D สมัครฟรี! ไม่เสียค่าใช้จ่าย เครดิตฟรี50 เรามามอบประสบการณ์ใหม่ๆ กับเกมที่มีให้เลือกมากถึง 1,000 เกม
ฝาก-ถอน ก็สามารถทำรายการไม่เกิน 15 วินาที 20รับ100 ไม่ต้องส่งสลิป มีแอดมินที่คอยให้บริการตลอด 24 ชั่วโมง
เว็บเดิมพันที่มีผู้เล่นและผู้ติดตามเกมนี้มากถึง 1 หมื่นคน ซึ่งมีระบบอัตโนมัติ สล็อตวอเลท มั่นคงทางการเงิน ปลอดภัยสูงสุด เว็บสล็อตออนไลน์ของเราเป็นเว็บระดับพรีเมี่ยม
เว็บไซต์ของเราเป็นเว็บที่มีใบรับรองเว็บไซต์มีระบบความปลอดภัย pg slot แตกง่าย สมัครผ่านระบบออโต้ด้านล่างก็สามารถสมัครกับเราได้ สล็อตออนไลน์ที่กำลังมาแรงที่สุดตอนนี้
ระบบอัตโนมัติที่ใช้งานง่าย ทำธุรกรรมการเงินไม่ว่าจะเป็นฝาก-โอน ภายใน 1 นาที เครดิตฟรี50 เว็บสล็อตออนไลน์แตกง่าย โปรโมชั่นพียบ
การสร้างรายได้จากเกม ลงทุนน้อยได้กำไรมาก pgslot โปรโมชั่น เด็ดๆมากมายมาเสนอแต่ละอาทิตย์และมีกิจกรรม สำหรับคนทุนน้อยเท่านั้น
สำหรับคนทุนน้อยสามารถเล่นกับเราได้เพียงขั้นต่ำ 1 บาท และเรามี โปรโมชั่น เอาใจคนทุนน้อยมากมาย pgdragon สมัครสมาชิกใหม่รับเครดิตฟรีทันทีสมัครเลย!
พีจี สล็อต เว็บตรงไม่ผ่านเอเยนต์ เปิดบริการอย่างเป็นทางการ สล็อตเว็บตรง ทำให้มีความน่าเชื่อถือ เพราะเว็บไซต์ของเราเป็นเว็บที่มีใบรับรองเว็บไซต์มีระบบความปลอดภัย
chatgpt signup welcome to the world of ChatGPT, a cutting-edge language model developed by OpenAI, the preeminent AI research organization in the United States. Experience the fusion of artificial intelligence and engaging conversations.
Thanks for every other excellent post. The place else may just anyone get that kind of info in such an ideal manner of writing? I’ve a presentation subsequent week, and I am at the look for such information.
เว็บใหม่มาแรง
سحبةwell as regular and electronic hookahs and all their accessories. Affiliated to Al-Ruqan World Trading Est.
Hi there, just wanted to mention, I enjoyed this blog post.
It was inspiring. Keep on posting!
For GTA 5 Mods Visit my Blog
FiveM Store
seo outsourcing india Search Engine Optimization, as the very name suggests, means the process of optimizing your website (and related content) for making it relevant for search engines so it can be more visible to the users searching on them. While that is what SEO technically
This is really good stuff bro..it helped me a lot after knowing about it..thanks bro
Dear immortals, I need some wow gold inspiration to create.
Dear immortals, I need some inspiration to create https://www.wowtot.com
Carpet cleaning near me s With years of experience in the steam cleaning industry, we understand the importance of creating a healthy and safe environment for your home. At ECO-SAFE, we are dedicated to meeting customer needs and priorities.
Alberta electricity ratesand Alberta natural gas prices can be high, but not everybody has to pay the same rates, you can buy energy for less. Some people say that natural gas prices Calgary and Edmonton gas prices are some of the highest. Overall, people wish that Alberta gas prices could be better. When the temperature outside gets cold many suggest lowering your room temperature or home improvement tips such as a buying new furnace or hot water heater, a nest thermostat, air duct cleaning, and more, but those can be expensive, when instead what you are likely looking for are the best gas and electricity rates in Alberta to save you money. Some people can pay lower Alberta electricity rates than others. The reason for this is that the Province of Alberta allows some degree of competition in terms of electricity rates Alberta and Alberta natural gas prices. The same applies for electricity rates Edmonton and electricity rates Calgary.
Obsidian vs Notion
I have always been interested in productivity and how to get the most out of my day. This interest started when I was a student and struggled to balance my coursework, extracurricular activities, and social life. I tried many different approaches to staying organized, but nothing seemed to stick. It wasn’t until I discovered the power of digital note-taking that my productivity took a major leap forward
Betting Bonus Codes The Sports Illustrated Sportsbook MCBET200 provides new users with $200 in bonus if they place an initial bet of or more and. unlock free bets and bonus offers. We have exclusive betting promo codes to use at betting sites in your country.
Betting Bonus Codes The Sports Illustrated Sportsbook MCBET200 provides new users with $200 in bonus if they place an initial bet of or more and. unlock free bets and bonus offers. We have exclusive betting promo codes to use at betting sites in your country.
Auto Glass Repair Broken car glass Autoglass provides a quality vehicle glass repair and replacement service. Visit us online at Autoglass.co.uk for more information. This kit is designed to provide vehicle owners the necessary information and tools to repair small damages in laminated automotive glass windshields
انواع فيب
PG SLOT ยืน 1 เว็บสล็อต PG คนเล่นเยอะ สมัคร 50รับ100 อัปเดตเว็บใหม่ ใช้ระบบทันสมัย ล้ำหน้าที่สุด เร็วแรงไร้ขีดจำกัด
เกมสล็อตที่ล้ำสมัยที่สุดและมีโปรโมชั่นที่มากพอที่จะทำให้เล่นกับเราในทุกช่วงเวลา สล็อตเครดิตฟรี ทั้งหมดคือสิ่งที่เรามั่นใจว่าคุณจะเล่นกับเรา และจะกลับมาเล่นกับเราอีกแน่นอน
เว็บที่รองรับการใช้งานภาษาไทย ฉีกกฎการเล่น สล็อต เร็วแรงไร้ขีดจำกัด ฝากถอน รวดเร็ว ยอดไม่ค้าง เล่นสล็อตpg เว็บตรง
https://pgslot.link/%E0%B8%AA%E0%B8%A5%E0%B9%87%E0%B8%AD%E0%B8%95%E0%B8%A2%E0%B8%B9%E0%B8%AA%E0%B9%83%E0%B8%AB%E0%B8%A1%E0%B9%88/
https://pgslot.link/
เมื่อพูดถึงเกมใหม่กันแล้ว เพื่อนๆก็ต้องอยากรู้กันแล้วใช่ไหม ว่าเกมใหม่ที่ทางเรานั้น ได้นำเข้ามาเปิดให้บริการ ภายในเว็บไซต์ของเรานั้น จะเป็นอย่างไรและมีความน่าเล่นมาแค่ไหน เบื้องต้นขอบอกไว้ก่อนเลยว่า เกมใหม่ที่เราได้นำเข้ามานั้น ถูกออกแบบใหม่ทั้งหมด และถูกปรับแต่งรายละเอียดเป็นอย่างดี ไม่ว่าจะเป็นในด้านของระบบ กราฟฟิก ที่มีความสวยงามและ มีความคมชัดมากยิ่งขึ้น ยังรวมไปถึงเรื่องของระบบเสียง ในตัวเกมอีกด้วยที่ใหม่ทั้งหมด ธีมต่างๆที่ไม่เคยมีให้ลูกค้าได้สัมผัสมาก่อน ทางเรานั้นได้พัฒนาและออกแบบเกมใหม่ๆ มาอีกมากมาย ฉนั้นเพื่อนๆสามารถ เข้ามาทดสอบหรือเข้ามา ร่วมสนุกกับเกมใหม่ เกมสล็อตใหม่ 2023 ของเราได้ทุกวัน แค่เพียงสมัครสมาชิกกับเราก็สามารถ สนุกกับเกมใหม่ๆได้แล้ววันนี้ มาดูกันว่าเกมใหม่เกมไหน ที่จะน่าเล่นที่สุดในปี 2023 และจะมีกี่เกมที่ เป็นดาวเด่นที่สุดของค่ายในปีใหม่นี้
วันนี้เราให้โบนัสสูง 100% พิเศษเฉพาะสมาชิกใหม่เท่านั้น pgslot แตกง่าย พร้อมเงินรางวัลที่ไม่มีใครเทียบได้
เราได้จัดกิจกรรมพิเศษ อื่นๆ อีกมากมาย ให้สมาชิกได้ลุ้นรับโบนัส เครดิตฟรี 188 กับเงื่อนไขที่ไม่ยุ่งยาก ไม่ต้องแชร์ รับฟรีกันไปเล๊ย
รวมเกมสล็อตทำเงินเเบบเข้มข้น มาให้กดเล่นในที่เดียว เข้าถึงง่ายตลอด 24 ชั่วโมง เจ้าเจ๊ง เว็บสล็อตรวมค่ายสุดพรีเมี่ยม เข้ารับความมันส์ไม่จำกัดขอบเขต
เพิ่มกำไรเข้ากระเป๋าได้ชัวร์ ค้นหาเกมสล็อตดัง เเตกง่าย 50รับ100 ที่ครบเครื่องที่สุดในไทยตอนนี้ เจอเกมดีกำไรโดนเเน่นอน
โบนัสฟรีแจกไม่จำกัด ไม่ล็อคยูส สล็อต pg แตกง่าย เครดิตฟรี กดรับเอง เข้าสู่การเดิมพันที่ยอดเยี่ยม ไปกับเราได้ตลอด 24 ชั่วโมง เริ่มต้นได้เลยตั้งเเต่ตอนนี้
ล็อคอินเข้าระบบครั้งเดียว ลองเล่นเกมดังในติ๊กต๊อกได้ตลอด pg slot เว็บเกมออนไลน์ รวมความบันเทิงให้เลือกเข้าเล่นทุกรูปแบบ
พร้อมเปิดโอกาสให้คุณเข้ามาสร้างกำไรจากการเล่นสล็อตออนไลน์ได้ตลอด 24 ชั่วโมง pgslot ล็อคอินครั้งเดียว รับความบันเทิงครบวงจร รับรองคุ้มค่าการลงทุน
ใครอยากลองเล่นเกมสล็อตฟรี ถอนได้จริง เครดิตฟรี ยืนยันเบอร์ ล็อคอินครั้งเดียวเล่นได้ทุกค่าย สมัครเลย!
รับความบันเทิงครบวงจร รับรองคุ้มค่าการลงทุน ทางเข้าpg แจกโปรดียืน 1 กดรับง่ายที่สุดในปี 2023
เว็บสล็อตรวมค่าย มีเกมจากเเบรนด์ดังให้เลือก มากกว่า 1,000 เกม pg มาให้คุณกดเล่นจบในเว็บเดียว สมัครสมาชิกครั้งเดียว
กำลังมองหาค่ายเกมสล็อตเเตกง่าย เล่นเพื่อทำกำไรกันอยู่ใช่ไหม เครดิตฟรี 50 ค่ายยอดฮิต ที่มีสล็อตเเตกง่ายให้เลือกเยอะที่สุด เล่นเเล้วบวกไม่มีลด
สล็อตค่ายใหญ่ อัตราการจ่ายสูง โบนัสแตกง่ายกว่าใครๆ คุณสามารถเดิมพันเกมค่าย superslot มีเกมดังเเตกง่ายให้เล่นมากมาย เเต่ละเกมคูณปัง โบนัสมาไวสุดๆ
ค่ายดังยอดนิยม ที่จะเเนะนำให้ทดลองเล่นดูสักครั้งค่ายสุดท้าย pgslot ใครอยากเล่นเกมสล็อตสไตล์ใหม่ๆ ที่ให้ผลตอบเเทนดีเดินคาด ต้องเลือกค่ายนี้เท่านั้น
สร้างรายได้จากเกมสล็อตไม่จำกัด เล่นเกมฟรี ถอนได้จริง เเจกเเบบไม่มีเงื่อนไขทุกวัน เครดิตฟรี50 ลุ้นรับโบนัส เเละเเจ็คพอตใหญ่ๆ ได้ตลอดเวลา
อัตราการจ่ายสูงที่สุด นำเข้าเกมจากทุกค่าย เล่นได้อย่างปลอดภัย pg slot เว็บตรง ด้วยระบบบริการสุดทันสมัย ไม่ว่าจะปั่นจากอุปกรณ์ไหน ก็ไหลลื่น ไร้การสะดุดเเน่นอน
เว็บสล็อตสุดครบครัน มีเกมให้เล่นครบ มีโปรโมชั่นโดนๆ pg ถอนได้จริง กับเราได้ตลอด 24 ชั่วโมง
เปิดยูส PG SLOT ครั้งแรก กับเว็บตรงแตกง่าย อันดับ 1 pg เล่นสล็อตแตกง่ายโคตรๆ แถมยังมีโปรโมชั่นดีๆ แจกไม่อั้น
ไม่ต้องพกเงินมาเล่นเยอะ ก็ลุ้นรวยได้สบาย ค้นหาเกมธีมสนุกมากมาย เครดิตฟรี ปั่นลุ้นรางวัลใหญ่ได้ยาวๆ บนเว็บ PG SLOT มีเกมสล็อตมาเเรงให้เลือกครบทุกค่าย
พลังยูสใหม่แตกดี จะช่วยให้คุณเข้ารอบโบนัสได้อย่างง่ายดาย 10รับ100 สนุกได้ทุกช่วงเวลา เล่นสล็อตยูสใหม่ แตกง่าย ทำกำไรได้มากกว่า
สล็อต ยูสใหม่แตกดี สมัครฟรี ไม่มีขั้นต่ำ สล็อตวอเลท ปั่นไม่นานก็รับรางวัลใหญ่ ถอนได้ง่ายๆ ด้วยระบบออโต้
สล็อตยูสใหม่ ต้องไม่พลาดเล่น! ช่วงนี้ pg slot แตกง่าย สล็อตยูสใหม่ ไม่ควรพลาด! ย้ำอีกครั้งว่า ยูสแรก เล่นยังไงก็แตก
เตรียมรับสิทธิพิเศษมากมาย ไม่ว่าจะเป็นโปรโมชั่น โบนัส หรือเครดิตฟรี เล่นสล็อตด้วย เครดิตฟรี50 แตกง่ายล่าสุด จาก PG SLOT ที่ สล็อตยูสใหม่ ควรเล่น!
เกมสล็อต บริการอันดับ 1 ที่สร้างความสุขได้ไม่รู้จบ pgslot สมัครเล่นง่าย โบนัสแตกไว รองรับการเล่นเมนูภาษาไทย อ่านปุ๊บ เข้าใจทันที
ลงทุนน้อยก็มีกำไร เข้าเล่นรับประกันความอุ่นใจ เพราะเป็นเว็บตรง ไม่ผ่านเอเย่นต์ pgdragon ประทับใจคอมเกมสล็อตร้อยเปอร์เซ็นต์เเน่นอน
รับประกันความสนุกแบบเกินต้านทุกวัน สล็อตเว็บตรง ผ่านระบบอัตโนมัติ ฝาก-ถอน ฟรีค่าธรรมเนียม รองรับทุกบัญชีธนาคาร เริ่มก่อนสนุกก่อน สมัครเลย!
เว็บตรง ไม่ผ่านคนกลาง มีตัวเลือกโปรโมชั่น เเละเครดิตฟรี ให้บริการอย่างหลากหลาย เราเเจกเเบบทั่วถึงทุกยูส เครดิตฟรี50 แจกง่าย เงื่อนไขน้อย สมัครสมาชิกรับได้เลยทันที
เกมสล็อตออนไลน์ ค่ายสล็อตที่ได้รับความนิยมจากผู้เล่นชาวไทยมากที่สุด pgslot การันตีความปลอดภัยได้เต็มร้อย เล่นได้เท่าไหร่ ถอนออกเต็ม ไม่มีการหักเปอร์เซ็นต์เเน่นอน
South of France soapAligned with our shared values, South of France prioritizes ethical practices. Their bar soaps proudly carry the mark of being free from animal byproducts and never undergoing animal testing. This commitment to cruelty-free practices resonates deeply with our belief in the beauty of compassion.
kantorbola
Porn Movies
The Design Boutique specializes in Porn Movies, in the porn industry. Sexy XXX vids, from softcore to hardcore and everything in between. Fetishes welcomed. The Design Boutique = Porn.
Join us as we deep dive into our online games prizes. Lucky Cola
A good blog always comes-up with new and exciting information and while reading I looked on the web for the issue and discovered most individuals goes as well as with your website. Bigg Boss 17 Online
Thankyou for sharing the data which is beneficial for me and others likewise to see. Bigg Boss 17 watch Online
This blog is really have all those quality that qualify a blog to be a one. Bigg Boss 17 Watch Episode
Great post. I learn something totally new and challenging on websites I stumbleupon every day. It’s always useful to read through articles from other authors and practice something from other sites. Bigg Boss 17 Today Episode
bayanlara evden iş
I have just stumbled upon your blog and enjoyed reading your blog posts very much. I am looking for new posts to get more precious info. BiLiBiLi Tv
Ebony webcam
เว็บไซต์สล็อต pg เว็บไซต์ตรง แจกโบนัสโหดเหี้ยมที่สุด สล็อตเครดิตฟรี เว็บไซต์แท้เว็บไซต์ตรง ให้บริการเกมสล็อตออนไลน์ครบวงจร เลือกเล่นเกมแบรนด์ดังได้ครบในเว็บไซต์เดียว นี่เป็นแหล่งรวมทุนฟรีเเละเกมสล็อตใหม่ๆใหญ่ที่สุดในไทย
เว็บสล็อต pg เว็บตรง แจกโบนัสโหดที่สุด สล็อตเครดิตฟรี เว็บแท้เว็บตรง ให้บริการเกมสล็อตออนไลน์ครบวงจร เลือกเล่นเกมแบรนด์ดังได้ครบในเว็บเดียว นี่เป็นแหล่งรวมทุนฟรีเเละเกมสล็อตใหม่ๆ ใหญ่ที่สุดในไทย
เว็บแท้เว็บตรง ให้บริการเกมสล็อตออนไลน์ครบวงจร เลือกเล่นเกมแบรนด์ดังได้ครบในเว็บเดียว สล็อต ลงทุนน้อย แต่เติมกำไรได้ x10 เท่า เดิมพันขั้นต่ำสุดแค่ 1 บาทเท่านั้นเอง
สมัครสมาชิกเดิมพันกับเราที่นี่ ไม่ผิดหวังเเน่นอน pgslot เดิมพันสุดแตกต่าง เพลิดเพลินกับการทำกำไรเกมสล็อต ที่มีตัวช่วยให้เลือกสรรไม่อั้น
สมัครสมาชิกวันนี้ รับโบนัส ฟรี 100% เครดิตฟรี 188 โปรโมชั่น ของเรามีโปรโมชั่นดี ๆ มากมาย ที่จะพานักเดิมพันทุกท่าน รวยไปด้วยกัน สำหรับนักเดิมพันสล็อตตัวจริงที่ต้องห้ามพลาด
เว็บสล็อตออนไลน์ รูปแบบใหม่ล่าสุด น้องใหม่มาแรง สล็อตเว็บตรง ไม่ผ่านเอเย่นต์ มีโปรดี ๆ สุดพิเศษตั้งแต่เริ่มสมัครกันเลย อย่ารอช้า
가입꽁머니
invoice generato
Everytime I come here I find something new valueable.. Customer Care Will further read on.
gi88
typhu88
Hotmail is still valid, and although Microsoft changed the name of Hotmail Outlook in 2013, the fact is that it is still possible to log on to Hotmail through the new website.
panen138 adalah situs slot online resmi indonesia hari ini dengan info bocoran rtp slot gacor setiap harinya dengan kesempatan menang lebih tinggi di situs Panen 138 online 24 jam
Experience the epitome of relaxation and beauty at Deux Chic Spa in Kitsilano. This haven of serenity offers expert estheticians, flexible appointment hours, and a wide array of beauty services including waxing, threading, makeup, and facials, all delivered in an impeccably clean environment. Their commitment to affordability ensures that self-care is accessible to all. For the ultimate pampering experience, visit Deux Chic Spa, where beauty meets relaxation, and elevate your well-being. Book your appointment at https://www.deuxchic.ca/
https://mavarypan.com/
El masaje sería un masajistas profundamente relajante y sensual que se puede utilizar con fines físicos, mentales y espirituales.
Igualmente, según sus seguidores, los beneficios de esta práctica serían numerosos. Un aspecto significativo de este tipo desería su capacidad para liberar el estrés y la tensión en el cuerpo. También indican que tendría la capacidad de reducir la ansiedad y la depresión y aliviar el dolor crónico.
El tántrico es un masaje que dura aproximadamente una hora y el objetivo es llevar al receptor a un estado profundo de meditación y relajación. El masaje se realiza con movimientos lentos y suaves, y el receptor debe estar desnudo para tener suficiente contacto con la piel.
Según sus seguidores, podría ser beneficioso para las personas que padecen problemas de espalda, dolor crónico, insomnio, fatiga, estrés o incluso presión arterial alta.
El masaje sería un masajistas profundamente relajante y sensual que se puede utilizar con fines físicos, mentales y espirituales.
vi68 vốn là thương hiệu game bài được bình chọn bậc nhất tại thị trường châu Á về độ uy tín và chất lượng. Về đến Việt Nam, cổng game này vẫn không ngừng thể hiện được sức hút của mình bằng việc sở hữu hàng triệu thành viên chỉ sau một đoạn thời gian rất ngắn. Bài viết này sẽ tổng hợp những yếu tố làm nên đẳng cấp của cổng game Vi 68 này.
pg ปากทางเข้าเล่นสล็อตเปิดใหม่ 2023 50รับ100 ที่มีเกมครบทุกแบรนด์ให้เลือก ฝากถอนด้วยระบบออโต้ ทำรสบการเร็ว เงินเข้าไวใน 10 วินาทีแค่นั้น
สมัครที่เดียว เล่นเกมสล็อตได้ทุกค่าย สล็อตเครดิตฟรี ส่วนใครไม่เป็นสมาชิก รีบสมัครเพื่อรับสิทธิพิเศษปังๆ เลยตอนนี้
เว็บสล็อตรวมค่าย แตกง่าย ได้เงินไว ต้องส สล็อต ล่นได้อย่างปลอดภัย ด้วยระบบบริการสุดทันสมัย ไม่ว่าจะปั่นจากอุปกรณ์ไหน ก็ไหลลื่น ไร้การสะดุดเเน่นอน
ลุ้นคูณกระจาย สร้างรายได้ยอดปังกับเราได้ทุกช่วงเวลา pgslot เว็บสล็อตสุดครบครัน มีเกมให้เล่นครบ มีโปรโมชั่นโดนๆ เเจกไม่อั้น ต้องเราเท่านั้น
แค่ลงทะเบียนเป็นสมาชิกกับเรา รับโบนัส 100% ไปเลยไม่มีเงื่อนไข เครดิตฟรี 188 สามารถลุ้นเงินรางวัลใหญ่ จากเกมสล็อตออนไลน์ ด้วยเครดิตฟรีได้ง่ายๆ ซึ่งเงื่อนไขการเเจกไม่ได้มีความซับซ้อน
ยูสแรก เล่นยังไงก็แตก เปิดยูส PG SLOT ครั้งแรก เจ้าเจ๊ง มีเกมสล็อตมาเเรงให้เลือกครบทุกค่าย กดเล่นได้ผ่านเว็บจบได้ที่เดียว ไม่ต้องติดตั้งแอพ
เพิ่มจากยอดฝากทันที คนทุนน้อยรีบสมัครให้ไวเลย! 50รับ100 ถอนได้ง่ายๆ ด้วยระบบออโต้ ที่ทำรายการด้วยตัวเอง ไม่ต้องแจ้งแอดมิน
ถ้าุณกำลังมองหาเว็บตรง ไม่ผ่านเอเย่นต์ ที่ยืน 1 เรื่องเเจกโบนัสฟรี เข้าเล่นกับเว็บนี้ เครดิตฟรี กดรับเอง แจกจริง ไม่มีปลิว ไม่ขายฝัน
เกมสล็อต บริการอันดับ 1 ที่สร้างความสุขได้ไม่รู้จบ สมัครเล่นง่าย โบนัสแตกไว pg slot รองรับการเล่นเมนูภาษาไทย อ่านปุ๊บ เข้าใจทันที เราคือค่ายสล็อตออนไลน์
ลงทุนน้อยก็มีกำไร เข้าเล่นรับประกันความอุ่นใจ เพราะเป็นเว็บตรง pgslot ประทับใจคอมเกมสล็อตร้อยเปอร์เซ็นต์เเน่นอน
เปิดให้คอเกมสล็อต สามารถเข้ามา ทดลองเล่นสล็อตฟรี เครดิตฟรี ยืนยันเบอร์ รับประกันว่าเล่นฟรี ไม่มีค่าบริการ แค่หยิบโทรศัพท์มือถือ มาเปิดเว็บไซต์ล็อคอิน ก็เต็มอิ่มกับการทดลองเล่นสล็อต เพื่อหาเกมที่ตรงกับไลฟ์สไตล์คุณมากที่สุดได้ทุกวัน
เราเป็นผู้ให้บริการเบอร์ 1 ด้านเกมสล็อตออนไลน์ ค่ายสล็อตที่ได้รับความนิยมจากผู้เล่นชาวไทยมากที่สุด ทางเข้าpg ได้รับรีวิวจากผู้เล่นว่า มีอัตราโบนัสแตกง่าย แตกบ่อยที่สุด เราให้บริการเฉพาะสล็อตแท้ถูกลิขสิทธิ์
สมัครสมาชิกใหม่ เล่นได้เลยไม่ต้องฝากก่อน สามารถทดลองเล่นได้จนกว่าจะมั่นใจ pg การันตีความปลอดภัยได้เต็มร้อย เล่นได้เท่าไหร่ ถอนออกเต็ม ไม่มีการหักเปอร์เซ็นต์เเน่นอน
เครดิต ฟรี กด รับ เอง ต่อยอดทุนได้ไม่รู้จบ เครดิตฟรี 50 กดรับง่าย เงื่อนไขไม่เยอะ คุณเองก็เป็นเจ้าของทุนฟรีนี้ได้ แค่คลิกสมัครเท่านั้น
ลงทุนต่ำ ทำกำไรพุ่งได้เป็นแสน เว็บสล็อตแท้มีใบเซอร์ การันตีเรื่องความปลอดภัยได้ 100% superslot สมัครเล่นง่าย ทำรายการด้วยตัวเองผ่านระบบออโต้ ไม่ต้องง้อทีมงาน
หมุนเป็นแตก ลุ้นกำไรได้หลักแสนทุกวัน pgslot ถอนได้เต็มเเบบไม่มีการหักเปอร์เซ็นต์เเม้แต่บาทเดียว
เล่นคุ้มตั้งแต่ครั้งแรก ด้วยโปรโมชั่น ต้อนรับสมาชิกใหม่ เครดิตฟรี50 อกจากนี้ เรายังมีโปรโมชั่น100% แจกอีกไม่อั้น คุณสามารถเช็คโปรโมชั่นใหม่ๆ ได้ที่เมนู โปรโมชั่น หน้าเว็บไซต์ทุกวัน
อัปเกรดความสนุก เติมเต็มช่วงเวลาทำเงินจากเกมสล็อตออนไลน์ไปกับเรา pg slot เว็บตรง คุณจะฟินจากเกมหลากหลายธีมของ PG SLOT ได้ยกค่าย เล่นได้ผ่านทุกอุปกรณ์ เชื่อมต่อโลกเกมออนไลน์
นักเดิมพันคนไหนที่ยังไม่ สมัครสมาชิก กับเรา pg เว็บตรงเจ้าใหญ่ เว็บพรีเมี่ยม ที่เติมเต็มทุนฟรีให้กดรับไม่อั้น รีบสมัครให้ไวเลยตอนนี้
สล็อตเว็บตรง ที่รวมโปรสุดพรีเมี่ยม ให้เลือกมากที่สุด pg รับโปรโมชั่นสุดพรีเมี่ยม ไปเติมความฟิน เตรียมสร้างรายได้จากการเดิมพันขั้นสูงสุด
ศูนย์รวมเกมสล็อตออนไลน์มากกว่า 1,000 เกม เครดิตฟรี ทันทีที่สมัครสมาชิก มั่นใจได้เลยว่ามีทุนฟรี เล่นสล็อต ถอนได้จริง ส่งถึงมือคุณเเน่นอน
เว็บสล็อตอันดับ 1 ของโลก แจกโบนัส ดีที่สุด 10รับ100 แจกสูงสุดหลักพัน ให้เยอะจัดหนัดขนาดนี้ ไม่สมัครถือว่าพลาดมาก!
รับสิทธิพิเศษเพียบ เราขนมาเเจกไม่อั้น ทั้ง โปรโมชั่น เเละเครดิตฟรี100 สล็อตวอเลท สมาชิกใหม่กดรับได้ทุกวัน มีแจกไม่จำกัดสิทธิ์ ไม่ล็อคยูส เข้ารับความสนุกจากเกมเเตกง่าย
เล่นได้สะดวกทุกที่ เว็บสล็อต ยูสใหม่แตกง่าย pg slot แตกง่าย เรามีโปรโมชั่นต้อนรับสมาชิกใหม่ ให้เลือกอย่างหลากหลาย
เปิดยูสใหม่รับเครดิตฟรี 2023 แจกเยอะที่สุด เครดิตฟรี50 เลือกรับโปรโมชั่น เยอะ จุใจ ทุกช่วงเวลา
เล่นเกมกับเว็บตรงเเตกง่าย นอกจากจะมั่นใจเรื่องความปลอดภัย pgslot คุณยังสามารถเลือกรับ โปรโมชั่น เยอะ จุใจ ได้ทุกช่วงเวลา รับรองเราสรรหาเเต่โปรเด็ด ไม่ซ้ำใคร
สนุก ตื่นเต้น โปรดีจะช่วยเพิ่มโอกาสชนะ ทำให้ลุ้นกำไรที่มากขึ้นได้ โดย pgdragon ไม่ต้องใช้ทุนเยอะ ทำให้คุณกล้าที่จะลงทุน เเบบไม่ต้องมานั่งกังวล เมื่อเล่นเกมได้เต็มที่มากขึ้น กำไรก็จะเพิ่มขึ้นโดยอัตโนมัติเเน่นอน
ต่อยอดทุนได้ไม่รู้จบ เครดิตฟรี50 นี่คือตัวช่วยเดิมพัน ที่จะพาคุณไปพบกับเกมที่ใช้ เงินรางวัลปัง ทำกำไรได้เเบบโดนใจ
หมุนเป็นแตก เล่นเมื่อไหร่ก็บวก ที่คอสล็อตออนไลน์ ไม่ควรพลาดในปี 2023 pgslot นอกจากจะเล่นสล็อตได้ทุกค่ายดัง เรายังคัดสรรโปรสุดพรีเมี่ยม มาให้เลือกมากที่สุด
Greetings! I’m writing my first post here, and I have to say that I’m satisfied with the information you offer. Do you have any other websites, blogs, or forums that cover similar topics? Any suggestions you can offer would be highly appreciated. Thank you for your time!
그리고 전 세계적으로도 토토사이트라고 하면 떠오르는 배팅룸, 토토사이트등도 믿을 수 있고 인기가 많은 사이트입니다.해당 사이트를 이용하는 회원님들은 출금 시에 약 3분 이내로 원하는 금액을 받을 수 있으며안전토토사이트로서 정식 라이선스를 체결했으며, 책임감 있는 운영방침과 24시간 고객응대 서비스 및 뛰어난 보안을 제공합니다.
pg in เว็บไซต์รวมเกมสล็อตพีจีออนไลน์ที่รองรับการใช้แรงงานผ่านมือถือ pg slot แล้วก็สมาร์ตโฟนทุกระบบ รองรับภาษาไทย ทำให้เล่นง่าย ใช้งานสบาย นอกจากนั้นยังสามารถใช้งานเล่นได้
hengheng888 pg เว็บไซต์สล็อต รูปแบบใหม่ ที่ใส่เกมสล็อตประสิทธิภาพ pg slot แตกง่าย มาพร้อมออฟชั่นเสริมวิธีการทำเงินแบบใหม่ทำให้ผู้ใด ก็เข้ามาร่วมโกยเงิน เข้ากระเป๋าได้ง่าย
pg น่าเล่น แตกจริงในอาณาจักรแห่งความบันเทิงออนไลน์ มีบางสิ่งที่ตรงกับความเบิกบานใจและความพึงพอใจที่ PG SLOT น่าเล่นแตกจริงให้ได้ หากคุณเป็นผู้ชื่นชอบการเล่น
pg slot m358 เล่นเกมสล็อตออนไลน์ไม่ยาก เล่นอย่างไรก็ได้เงิน เสนอแนะเล่นเกมสล็อตออนไลน์ตรงนี้กันเลย กล้วยๆเพียงแค่ปลายนิ้วสัมผัสเพียงแค่นั้น pg slot ไม่ต้องลงทุนสูงอีกต่อไป
स्थानांतरण प्रमाण पत्रशिक्षा हमारे जीवन का महत्वपूर्ण हिस्सा होती है और कभी-कभी हमें एक स्कूल से दूसरे स्कूल में तबादला करना पड़ता है। इस प्रक्रिया में, ‘स्थानांतरण प्रमाण पत्र’ एक महत्वपूर्ण दस्तावेज़ होता है जो आपके पिछले स्कूल की शैक्षिक यात्रा के संदर्भों को दर्शाता है। इस लेख में, हम आपको बताएंगे कि स्थानांतरण प्रमाण पत्र क्या होता है और इसे कैसे लिखा जाता है।
trading binary optionsvfxAlert provides a complete set of analytical tools for trading binary options. We have developed a new version that will work on all types of operating systems. In one working window of the vfxAlert application, you receive all data needed to correctly assess the current market situation.We recommend downloading the application for convenient work with any broker. If the current version is not supported by your device, you can use the web version and use signals in the browser window.
An all-natural blood sugar and metabolism support supplement called Gluconite makes the claim that it can assist users naturally balance, renew, and restore their bodies’ energy and metabolic processes. The product incorporates organic components derived from premium superfoods and herbs.An all-natural blood sugar and metabolism support supplement called Gluconite makes the claim that it can assist users naturally balance, renew, and restore their bodies’ energy and metabolic processes. The product incorporates organic components derived from premium superfoods and herbs.
ยูสใหม่เข้าโคตรง่าย เล่นเกมไหนก็แตก รับรางวัลใหญ่ได้ทุกวัน 50รับ100 ไม่ว่าจะเล่นตอนไหน ก็มีกำไรชัวร์
รวมเกมแตกดีเอาไว้ให้เลือกมากมาย มาพร้อมโปรโมชั่นโดนใจ สล็อตเครดิตฟรี แจกฟินทุกช่วงเวลา รับรองเลยว่าเล่นด้วย ยูสใหม่ ยังไงก็แตก
ยูสแรก เล่นยังไงก็แตก สล็อต ยูสใหม่เข้าโคตรง่าย แจ็คพอตมาไวเกินต้าน ไม่เชื่อลองเล่นเลยตอนนี้!
เปิด ยูสใหม่แตกง่าย กับเว็บตรง pgslot แหล่งรวมเกมสล็อตออนไลน์ครบวงจรที่สุด มีให้เลือกทุกค่ายดัง สมัครฟรีไม่มีขั้นต่ำ
เปิดยูสใหม่ทำกำไรได้ดีกว่า เพราะเต็มไปด้วยตัวช่วยมากมาย ทั้งโปรโมชั่น โบนัส เครดิตฟรี 188 สมัครเสร็จกดรับโบนัสฟรีทันที ไม่ต้องรอทีมงาน
สล็อต เครดิตฟรีล่าสุดสล็อต เครดิต ฟรี ล่าสุด เป็นหัวข้อที่กำลังเป็นที่นิยมในวงการเกมส์ออนไลน์ในปัจจุบัน PG SLOT นับว่าเป็นโอกาสที่น่าตื่นตาตื่นใจที่นักพนันในประเทศไทย
dafabat เว็บสล็อตสุดร้ายแรง เกมพนันที่มีคนเล่นมากมายแถมการเข้าถึงอย่างง่ายทุกเพศทุกวัยสามารถเล่นได้หมดเลยอยากได้หาเงินเชิญแนวทางนี้ pg slot พรีเซนเทชั่นความร่าเริงครั้งใหม่
t6slot สล็อตออนไลน์เปลี่ยนเป็นเกมยอดฮิตในกลุ่มคนที่ประทับใจการหมุนและก็ชนะอย่างเร็ว pg slot เกมกลุ่มนี้เสนอช่องทางสำหรับเพื่อการสร้างรายได้ที่สนุกรวมทั้งน่าระทึกใจทุกเกม
เล่นเกมได้ทุกค่าย ไม่มีขั้นต่ำ เจ้าเจ๊ง เพราะเว็บของเราเปิดใก้เบทต่ำหลักสตางค์ ไม่ต้องมีทุนเยอะก็เล่นได้ ให้บริการตามมาตรฐานสากล ปลอดภัย 100%
เว็บ 123goal รูปแบบแอพพลิเคชั่น รูปแบบใหม่ มีระบบระเบียบการ ฝาก-ถอนออโต้ ให้บริการเร็วทันใจ รวมทั้งช่องทางยอดเงินของลูกค้าที่ ได้โอกาส pg slot บกพร่องน้อยมาก มั่นอกมั่นใจ
เครดิตฟรี ล่าสุด twitterด้วยเครดิตฟรีกำลังเป็นกระแสที่น่าตื่นตาตื่นใจในวงการโซเชียลมีเดีย ไม่ว่าคุณจะเป็นนักการตลาดที่มีประสบการณ์ PG SLOT หรือผู้ใช้ทั่วไปที่อยากให้บัญชี
ร่ำรวย สล็อต สล็อตแตกง่าย เกมพนันออนไลน์ยอดฮิตยอดฮิตมากที่สุดในขณะนี้เพราะเหตุว่าเป็นเกม pg slot ที่มีตัวอย่างการเล่นที่ง่าย ไม่ซับซ้อน แตกต่างจากพนันอื่นๆอย่างแน่นอนที่เว็บเรา
สล็อตยูสใหม่ ให้โบนัสฟรีสูงที่สุด 50รับ100 แจกจริง ให้เต็มทุกวัน ต้องสมัคร สล็อตยูสใหม่ กับเรา
สล็อตยูสใหม่ ให้โบนัสฟรีสูงที่สุด ต้อง เครดิตฟรี กดรับเอง แจกจริง ให้เต็มทุกวัน ต้องสมัคร สล็อตยูสใหม่ กับเรา
สมัครใหม่เล่นแตกง่าย เดิมพันเกมค่าย PG ได้ไม่มีลิมิต pg slot เล่นแล้วได้เงินง่าย ได้เงินจริง ต้องเล่นที่นี่
สล็อตมาแรงค่าย PG เล่นด้วย ยูสใหม่เข้าโคตรง่าย pgslot ถ้าพร้อมจะสนุกกับการเดิมพันสล็อต บนเว็บตรงที่ดีที่สุด กด สมัคร ที่นี่เลย
เดิมพันเกมค่าย PG ได้ไม่มีลิมิต เครดิตฟรี ยืนยันเบอร์ อัตราการจ่ายรางวัลสูง ไม่มีกั๊ก เพียงสมัครสมาชิกยูสใหม่ pg รับทั้งโบนัสฟรี โปรโมชั่นดี ๆ ไม่จำกัด
เดิมพันได้ไม่มีขั้นต่ำ มีทุน 1 บาท ก็สนุกกับเกมวงล้อเสี่ยงโชคได้ทุกวัน ทางเข้าpg เว็บของเราเปิดใก้เบทต่ำหลักสตางค์ ไม่ต้องมีทุนเยอะก็เล่นได้ ให้บริการตามมาตรฐานสากล ปลอดภัย 100%
เกมดังค่ายยักษ์ใหญ่ ที่ขนความครบเครื่องมาเสิร์ฟแบบไม่กั๊ก ลงทุนเเค่ขั้นต่ำหลักสิบ pg ก็ลุ้นเงินรางวัลได้สูงสุดหลักแสน ส่วนเกมสล็อตท็อปฟอร์ม
orcbet เปิดให้บริการอย่างเป็นทางการเต็มไป ด้วยความแน่ใจ pg slot ในความปลอดภัย รวมทั้งความมีประสิทธิภาพ ระบบฝากถอน สบาย ไม่เป็นอันตรายสูง สมัครใหม่เข้าเล่นเพียงแต่ 100 บาท
เปิดยูสใหม่ แจกโบนัส 100% ทุกยูส ทดลองเล่นสล็อต PG ได้ฟรีอีกด้วย เครดิตฟรี 50 คุณสามารถ ฝาก ถอน เติม ได้ด้วยระบบออโต้ รองรับทุกัญชีธนาคาร
เครดิตฟรี ล่าสุด twitterด้วยเครดิตฟรีกำลังเป็นกระแสที่น่าตื่นตาตื่นใจในวงการโซเชียลมีเดีย ไม่ว่าคุณจะเป็นนักการตลาดที่มีประสบการณ์ PG SLOT หรือผู้ใช้ทั่วไปที่อยากให้บัญชี
แหล่งรวมเกมดังติดกระแส ลงทุนต่ำ บวกปัง superslot ทุกเกมเป็นเกมลิขสิทธิ์เเท้ รองรับการเล่นบนมือถือเเละทุกแพลตฟอร์ม รับรองเสถียร ไหลลื่น ไม่มีปัญหาสะดุดมากวนใจ
สล็อต teenoi เว็บไซต์พนันTeenoi หรือ ตี๋น้อย168 pg slot เว็บไซต์พนันออนไลน์อันดับต้นๆจากดินแดนมังกร แหล่งร่วมการพนันออนไลน์ทุกรูปแบบในไทย ให้เป็นศูนย์รวมสำหรับนักพนันทุกคน
pkc4 สล็อต ปริศนา ที่ เจอ บ่อยครั้ง สล็อต PG ได้ทุกหัวระแหง ทุกครั้งระบบเกมของเว็บสล็อต Slot PG มีความมีประสิทธิภาพ pg slot ดาวน์โหลดได้อย่างรวดเร็ว ไม่เสียเวล่ำเวลา ฝาก ถอน
ที่กระแสดีไม่มีตก ไม่ว่าใครเล่นก็ทำกำไรจากเกมนี้ได้อย่างง่ายดาย pgslot สามารถให้ความสนุกเเละเงินรางวัล กับนักเดิมพันได้อย่างเเท้จริง
คุณเองก็เป็นเจ้าของทุนฟรีนี้ได้ แค่คลิกสมัครเท่านั้น เครดิตฟรี50 บอกเลยเเจกจริง ให้เต็ม ไม่มีการขายฝันนักเดิมพัน
สมัครสมาชิก PG SLOT ลุ้นแจ็คพอตใหญ่ ได้จริง pg slot เว็บตรง ช่องทางสร้างโอกาสรวย มั่นคงที่สุด 2023
เว็บตรงแตกง่าย รวมเเบรนด์สล็อตชั้นนำ pg เว็บสล็อตเริ่มต้น ของมือใหม่หัดปั่น
ยูสใหม่แตกดี แตกง่าย สมัครสมาชิกใหม่ แจ็คพอตมาไวกว่า pg เล่นสล็อตออนไลน์ครบจบในเว็บเดียว สมาชิกใหม่ แตกง่าย เล่นเกมใหม่ล่าสุด 2023
สล็อตเว็บตรง แตกหนัก แจกเครดิตฟรี กดรับง่าย เครดิตฟรี อนได้จริง ใครยังไม่เป็นสมาชิก อย่ารอช้า โอกาสดี ๆ แบบนี้ ไม่ได้มีมาบ่อย ๆ รีบก่อนได้ก่อน!
ทดลองเล่นสล็อตใหม่ล่าสุด ถอนได้จริง ใช้ทุนน้อย ต้อง 10รับ100 ผู้ให้บริการสล็อตตัวจริง บอกเลยทำเงินได้ฟินทุกวัน!
เกมดัง เกมฮิต เกมทำเงินดี ได้จบในเว็บเดียว สล็อตวอเลท ถูกรวบรวมเอาไว้ให้เลือกรับความบันเทิง บนเว็บสล็อตครบวงจร
สล็อตเว็บตรง ทันทุกความเคลื่อนไหวของวงการคาสิโนออนไลน์ pg slot แตกง่าย ใหม่ล่าสุด เร็วที่สุดในไทย ฉะนั้น มั่นใจได้เลยว่าคุณจะเข้าเล่นเกมใหม่ได้ก่อนใคร
มีให้กดรับไม่อั้น ไม่จำกัดสิทธิ์ ไม่ล็อคยูส เครดิตฟรี50 เเละไม่ว่าคุณจะเป็นสมาชิกเก่าหรือไม่ คุณจะได้ โบนัสฟรี เเละเครดิตฟรี จากเราเสมอ
เข้าเล่นเกมสล็อตออนไลน์ ที่น่าตื่นเต้นผ่านเว็บตรงแตกง่าย ระบบอัตโนมัติ pgslot ที่ช่วยให้คุณเดิมพันสะดวกเพิ่มขึ้น โดยไม่ต้องรอการอนุมัติจากทีมงาน
เว็บรวมเกมลิขสิทธิ์เเท้ มีให้เลือกเยอะที่สุดในไทย pgdragon เล่นเกม PG ของเเท้ คุณจะสนุกกับการเดิมพันเเบบไร้สะดุด เต็มอิ่มกับภาพ เเสง สี เสียง
เว็บตรง ทำเงินจากเกมสล็อตพีจี ได้ทุกวันตลอด 24 ชั่วโมง เครดิตฟรี50 ไม่อยากพลาดเกมลิขสิทธิ์เเท้ เเละทุนฟรีที่มีเเจกไม่อั้น สมัครที่นี่เลย!
สมัครเกมสล็อตใหม่ล่าสุด เปิดโอกาสในการเดิมพันฟรีตั้งแต่ครั้งแรก pgslot สนุกได้ครบวงจร เล่นได้จ่ายจริงเเน่นอน
สมัครสมาชิก pg slot ลงทุนน้อย ถอนได้ไม่อั้น ฝาก50รับ100ใหม่ล่าสุด2023 คัดสรรมาอย่างดี ลุ้นเงินรางวัลเเตก ๆ เป็นเจ้าของกำไรหลักเเสนได้ทุกวัน เกมสล็อตใหม่ๆ มีให้เลือกไม่ซ้ำ สนุกได้เเบบไม่น่าเบื่อ
ทางเข้า superslot
ซุปเปอร์สล็อต Sign up for a new superslot through the most convenient, fast, and easy-to-use automation system with reliable developer security standards. Ambbo is an automation developer that has been developed to facilitate users.
https://www.facebook.com/thelocksmithgoldcoast/
Farmasi Indonesia a site that provides information related to pharmacy and also international medical science learning
herbal store for all ailments Our online herbal store in the United Kingdom is a true haven for enthusiasts of a healthy lifestyle. In our extensive range, you will discover medicinal herbs, herbal teas, dietary supplements.
Pengurus Cabang Persatuan Ahli Farmasi
โปรโมชั่นดีๆที่หาได้จากเว็บออนไลน์ สล็อตเครดิตฟรี ไม่ต้องแชร์บนเว็บไซต์คาสิโนที่จะมาช่วยเพิ่มจังหวะสำหรับในการได้กำไรให้สูงมากขึ้น
เว็บตรง 2023 แตกง่าย แตกบ่อย รองรับเล่นบนมือถือทุกระบบ สล็อต อีกหนึ่งหนทางการพนันยอดนิยมเป็นอันมากเนื่องจากว่าคุณลักษณะเด่นของเกมสล็อตออนไลน์
สมัครสมาชิกรับรหัสเข้าเล่น เว็บหลัก ไม่ผ่านเอเย่นต์ สนใจสมัคร pgslot ฝาก – ถอน สะดวก รวดเร็ว ภายใน 30 วินาที
แจกเครดิตฟรีให้กับทุกคนเกือบจะทุกวี่วันอย่างยิ่งจริงๆเพียงแค่คุณจำเป็นต้องลงทะเบียน เครดิตฟรี 188 ซึ่งคุณสามารถใช้เครดิตกลุ่มนี้ไปลงพนันได้จริงแล้วก็ที่สำคัญจะสามารถเบิกเงินออกมาได้จริงอีกด้วยกล่าวได้ว่าเป็นอีกหนึ่งวิถีทางสำหรับการสร้างผลกำไรเจริญเป็นอันมาก
Pengurus Cabang Persatuan Ahli Farmasi
pafikepahiang Sesungguhnya Ahli Farmasi Indonesia ada sejak di Proklamasikan kemerdekaan Negara Kesatuan Republik Indonesia pada tanggal 17 Agustus 1945, telah berjuang bahu membahu dengan semua golongan masyarakat, untuk melenyapkan penjajahan dari muka bumi Indonesia, serta turut aktif mempertahankan Negara Kesatuan Republik Indonesia.
Hi, That looks great, Very nice and informative content. I am a tech blogger and I own a site. If you are interested in Tech Write for us
, Please contact me using the link if you need any guest post services.
Hi, That looks great, Very nice and informative content. I am a tech blogger and I own a site. If you are interested in Tech Write for us
, Please contact me using the link if you need any guest post services…
Hi, That looks great, Very nice and informative content. I am a tech blogger and I own a site. If you are interested in Tech Write for us
, Please contact me using the link if you need any guest post services,…
Hey there! 🔒 Great post on SSL authentication. 🌐 It’s crucial for online security. 💻 Adding a personal touch, maybe share a success story with SSL? 👍-industrial valves
1xbet promo code allows you to get a VIP bonus of up to 130%. This is an up-to-date offer for new players and betting fans. In return for registering with a promo code, participants receive gifts and awards.
Hey there, great share! SSL is 🔑 for online security. One more perspective – it’s like a digital handshake 🤝. Thanks for the info! 😊👍
–shaksham foundation
سحبة مزاج 5000 بلوبيري. من أهم مزايا استخدام شيشة الكترونية:
لا تحتوي على الكثير من المواد الضارة الموجودة في التدخين التقليدي.
توفر تجربة تدخين بدون رائحة قوية ودخان مزعج.
يمكن تخصيص النكهات ومستويات النيكوتين حسب تفضيلات المستخدم.
تقلل من تأثير الدخان السلبي على البيئة والأشخاص الآخرين.
Tambang888 adalah situs slot online yang beroperasi di luar negeri dan telah memiliki reputasi yang baik di kalangan pemain Indonesia. Berbagai jenis permainan slot yang menarik dan menghibur dapat ditemukan di sana.dunia game online selalu menarik bagi para penggemar game. Dengan begitu banyak opsi yang tersedia, tambang888 adalah salah satu platform yang patut dicoba.tepatnya tambang888. Berbagai game yang menarik dan mengasyikkan dapat ditemukan di situs web Tambang888. Dalam artikel ini, kami akan membahas permainan yang sangat menguntungkan yang ditemukan di situs web tambang888 dan mengapa Anda harus mencobanya
marijuana seeds it was the late 1980s and high atop the Himalayas, heavy snow hurling its way down from the skies, a small group of breeders began to cross-breed marijuana strains carefully selected from every corner of the Middle East and Asia. Bountiful harvests of Sativa and Indica cultivars kept the group’s spirits up during a 3 year stint in the rural, desolate mountains.
Situs slot gacor yang kami rekomendasikan ini tentunya tidak jauh berbeda dengan taruhan lainnya, namun jauh akan lebih memuaskan jika kamu mengakses situs judi slot online Kaisar888 Bukan tanpa alasan, melainkan tempat taruhan satu ini sangat terkenal dengan berbagai keuntungan terbesarnya yang memiliki nilai fantastis. Makanya dari itu, ambisi yang kamu miliki saat ini dalam bermain judi slot mungkin saja bisa terwujud. Jadi, tidak perlu kamu ragukan lagi untuk segera bergabung dan mendaftarkan diri lewat situs resminya.
“Great post, Ben! 👍 SSL authentification is crucial in today’s digital world. It’s like the lock on our online doors! 🔒💻”–cassia tora
Hey, great post! 🚀 Adding SSL is crucial for website security. One more tip: consider wildcard SSL for subdomains too! 👍-bentonitehttpsuppliers
property for sale in madeira Discover the beauty of island living with Exclusive Homes Madeira! Our website is your gateway to exquisite properties in Madeira, offering a curated selection of modern villas, newly constructed homes, and luxury apartments. With user-friendly tools like our IMT Tax Calculator and a rich blog section full of insights about Madeira’s real estate market, we make your property search enjoyable and informative. Our dedicated team is ready to assist you in finding the perfect home that matches your lifestyle. Visit Exclusive Homes Madeira, where your dream Madeira home awaits you. Explore now at [Exclusive Homes Madeira]
roro4d roroslot member bergabung dengan situs website terpercaya yang ada di indonesia membuat kita menjadi sangat nyaman dalam bermain. Semua kemudahan dan kenyamanan dalam bermain ditawarkan website online terpercaya yang ada di indonesia. Semua pembayaran dan penarikan saldo dilakukan dengan sangat aman serta cepat, jika anda ingin bergabung di situs website terbaik terpercaya roroslot online resmi indonesia.
property for sale in madeira Discover the beauty of island living with Exclusive Homes Madeira! Our website is your gateway to exquisite properties in Madeira, offering a curated selection of modern villas, newly constructed homes, and luxury apartments. With user-friendly tools like our IMT Tax Calculator and a rich blog section full of insights about Madeira’s real estate market, we make your property search enjoyable and informative. Our dedicated team is ready to assist you in finding the perfect home that matches your lifestyle. Visit Exclusive Homes Madeira, where your dream Madeira home awaits you. Explore now at [Exclusive Homes Madeira]
Great read, Ben! 🔒 I never realized how vital SSL authentication is for online security. Thanks for sharing your expertise! 🙌😊
–bentonite suppliers
ล่าแจ็คพอตสล็อตออนไลน์ด้วยเทคโนโลยีพิเศษที่คุณไม่ควรลืม! การหาแจ็คพอตเป็นเรื่องง่าย ไม่มีความพยายามมากนัก ทดลองซื้อฟรีสปิน pg นักล่ารางวัลแต่ละคนที่จะเข้าเยี่ยมชมได้หลังจากแจ็คพอตนี้ในตอนแรกจะต้องเลือกเกมสล็อตที่เหมาะสม nagagames slot เป็นค่ายเกมยอดนิยมที่สุดในปี 2023 มีเกมให้เลือกเล่นมากมาย ฟีเจอร์เกมโบนัสที่สนุกและน่าตื่นเต้น เราได้นำเกมทดลองเพื่อให้บริการลูกค้าของเราที่นี่เท่านั้น ก่อนตัดสินใจซื้อด้วยเงินจริงเพื่อให้ลูกค้าได้รู้จักฟีเจอร์ของแต่ล่ะเกม มีเกมไหนบ้างที่โบนัสแตกบ่อย และเป็นแนวทางในการเลือกเกม ที่จะไปเล่นจริง
สามารถเล่นได้จริง รับได้จริง เพียงติดต่อเราผ่านทาง ไลน์แอด รองรับทุกระบบ ไม่ว่าจะเป็นมือถือ คอม โน๊ตบุ๊ค บอกได้เลยว่ารองรับทุก platform มีระบบ ฝาก – ถอน ออโต้ ทำรายการได้ผ่านหน้าเว็บ สำหรับสาวกสล็อตออนไลน์ ต้องโดน ! เครดิตฟรี ยืนยันเบอร์ มีกิจกรรมดีๆ มีแจกตลอดทั้งเดือน ยืนยันเบอร์ รับ เครดิตฟรี และโปรโมชั่นสำหรับลูกค้าสล็อตออนไลน์ อีกมากมาย เพียงแค่สมัครสมาชิกกับเรา รับทันทีสิทธิพิเศษอีกมากมาย ถ้าคุณพร้อมแล้ว สมัครมาได้เลย !
สามารถเล่นได้จริง รับได้จริง เพียงติดต่อเราผ่านทาง ไลน์แอด รองรับทุกระบบ ไม่ว่าจะเป็นมือถือ คอม โน๊ตบุ๊ค บอกได้เลยว่ารองรับทุก platform มีระบบ ฝาก – ถอน ออโต้ ทำรายการได้ผ่านหน้าเว็บ สำหรับสาวกสล็อตออนไลน์ ต้องโดน ! เครดิตฟรี ยืนยันเบอร์ มีกิจกรรมดีๆ มีแจกตลอดทั้งเดือน ยืนยันเบอร์ รับ เครดิตฟรี และโปรโมชั่นสำหรับลูกค้าสล็อตออนไลน์ อีกมากมาย เพียงแค่สมัครสมาชิกกับเรา รับทันทีสิทธิพิเศษอีกมากมาย ถ้าคุณพร้อมแล้ว สมัครมาได้เลย !
สล็อต แหล่งรวมเกมสล็อตแตกบ่อย เว็บไซต์สล็อตออนไลน์อันดับ1 เกมสล็อต DEMO PG SLOT ฟรี 2021 ทดลองเล่น รวมทุกค่าย เว็บใหม่ เครดิตฟรี 100 ที่ให้คุณมากกว่าการเล่นเกมส์ ทดลองเล่นสล็อต ไม่ว่าจะเป็นเกมสล็อตจากค่ายดัง มาจากไหนเราก็สามารถ หามาใว้เพื่อให้คุณได้เล่นตลอดเวลา จะเกมเก่า เกมยอดฮิต เกมใหม่ล่าสุดรวมไปถึงเกมใหม่ในอนาคต เกมทดลองเล่นสล็อตทุกค่ายไม่ต้องสมัคร สมัครสมาชิกใหม่รับโบนัส100%ทันที ด้วยระบบที่ทันสมัย
PG SLOT GAME เกมสล็อตออนไลน์ อันดับหนึ่งของทั่วโลกจากผู้เล่นสล็อต ที่ได้รับความนิยมเป็นอย่างสูงในปัจจุบัน เพราะตัวการมีการออกแบบที่ทันสมัย รูปแบบ 3 มิติ ทำให้การเล่นสล็อตในสมัยนี้เป็นที่ฮิตกัน ทั้งได้รับความสนุกสนามเพลิดเพลิน สล็อตออนไลน์ทั้งหมด เแถมยังสามารถลุ้นรางวัล แจ็คพอตใหญ่ได้อีกด้วย แตกง่าย จ่ายจริง โดยเว็บของเรานั้นคือ ผู้ให้บริการเว็บพนันออนไลน์ ที่มาแรงที่สุดในตอนนี้
Ini bisa menjadi pilihan game yang lebih baik bagi pemain siap mengambil risiko situs tejo123 lebih besar dengan harapan mendapatkan permainan besar.
In the digital realm, where connections are just a click away, discovering an authentic, meaningful relationship can be quite an adventure.https://www.spiegelcam.com/lucky-crush/
You can only drive a mobility scooter or powered wheelchair if you: have trouble walking because of an injury, physical disability or medical condition. are demonstrating the vehicle before it’s sold. are training a disabled user.
I found this post incredibly intriguing, but I have a query. How do you think these strategies would fare in a different industry? I work in the healthcare sector and am curious if some of these concepts could be applied there as well. https://theblogfluent.com/
I found this post incredibly intriguing, but I have a query. How do you think these strategies would fare in a different industry? I work in the healthcare sector and am curious if some of these concepts could be applied there as well. https://theblogfluent.com/
I must admit that after giving some of the advice you provided here a try, it truly helped me. Both the volume of visitors to my website and their level of engagement have increased. I appreciate your useful advice.
okeplay777 Tren industri game online, telah mengalami kemajuan luar biasa selama beberapa tahun terakhir. Diantara sekian banyak varian permainan game, Link Okeplay777 telah muncul sebagai salah satu konsep terbaru yang memikat hati pemain, mulai dari pemula hingga yang sudah mahir di bidang arcade online. Untuk mendalami pesona dan daya tarik dari Situs okeplay777 game Maxwin, mari kita eksplorasi fitur-fitur unggulannya
Hey there, great share! SSL authentication is a game-changer for online security. 🛡️ Adding another layer of trust to your website. 💯-Wholesale crystals
Depositos de acero inoxidable a medida,Depositos de acero inoxidable de 50 Litors a 100000 Litros, navegue por nuestro sitio web para obtener ayuda y buscar precios.https://ace-chn.mx/product-category/deposito-de-acero-inoxdable/
juli4d adalah judi online berhadiah uang asli dan memiliki banyak jenis permainan yang mudah anda mainkan
platform game online yang sangat mudah untuk mendapatkan hadiah uang asli
juli4d adalah tempat bermain sambil mendapatkan hadiah uang rupiah
The telepackages is the site that tells you about packages of different telecom networks. It also updates you about daily, weekly, and monthly packages of SMS, On-Net MINS calls, Off-Net MINS calls, and internet MBs.
Okeplay777 adalah penyedia layanan slot oline tergacor se indonesia dengan ratio kemenangan sampai 97% , buruan daftar di Okeplay777 sekarang !!
Okeplay777 juga merupakan agen togel hari ini yang menghadirkan hasil keluaran togel secara real-time. Mereka memahami bahwa pemain seringkali ingin tahu hasil togel secepat mungkin untuk mengetahui apakah mereka memenangkan taruhan mereka.
buy weed online, buy cannabis online, buy marijuana onlineLooking to buy weed online Look no further than The Chrono to buy legit cannabis online Get Herbs, cheap CBD Concentrates, THC Edibles, Pills and more
Всичко, което трябва да знаете за времето утреНаучете повече за климата, възможните дейности и влиянието на времето Седем дневна прогноза за времето
Палачинките, с комбинацията от пухкаво тесто и различни вкусни гарнитури, са истинско удоволствие за всеки палачинки рецепта
The rose toy’s origin story is as intriguing as its design. Initially a sleeper hit within niche communities, its popularity exploded as users began to share their experiences online. It’s a product born out of a demand for more inclusive and approachable pleasure devices, and its rise to fame is a testament to the changing tides in societal attitudes towards sexual wellness. Click here rose toy
Wow, fantastic blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your web site is excellent, let alone
the content!
Rekabetin Göbeğinde Zeytinburnu Nakliye Sektörü: Hizmet Çeşitliliği ve Müşteri Odaklılık
Zeytinburnu’nda nakliye sektörü, giderek artan rekabet ortamında müşteri memnuniyetini ve hizmet kalitesini artırmak için çeşitli stratejiler benimsemektedir. Bu rekabetçi dinamikler, müşterilere daha geniş bir hizmet yelpazesi sunma, maliyetleri optimize etme ve müşteri odaklılık konusunda yeni standartlar belirleme konusunda firmaları teşvik etmektedir.
Hizmet Çeşitliliği ve Esneklik
Zeytinburnu’nda faaliyet gösteren nakliye firmaları, müşteri ihtiyaçlarına daha iyi cevap verebilmek adına hizmet çeşitliliğini artırmaktadır. Sadece evden eve taşımacılık değil, aynı zamanda özel eşya taşıma, ofis taşıma, depolama hizmetleri gibi farklı alanlarda uzmanlaşma çabasındadırlar. Bu, müşterilere daha özelleştirilmiş ve ihtiyaçlarına uygun çözümler sunma kapasitesini artırmaktadır.
Zeytinburnu Nakliye
Gelişen Esenyurt’ta Nakliye Sektörü: Geleceğe Yönelik Trendler
Esenyurt bölgesindeki nakliye sektörü, sürekli bir evrim içindedir ve geleceğe yönelik pek çok trendi bünyesinde barındırmaktadır. Bu trendlerden biri, dijitalleşme ve online platformlardaki artan etkinlik. Nakliye firmaları, çevrimiçi rezervasyon sistemleri ve dijital platformlarda daha etkin bir şekilde varlık göstererek müşterilere kolaylık sağlamaktadır.
Ayrıca, Esenyurt’taki nakliye firmalarının sürdürülebilirlik konusuna verdiği önem de göze çarpmaktadır. Elektrikli araç kullanımı, geri dönüşüme önem verme ve çevre dostu ambalajlama gibi uygulamalar, taşımacılık sektörünün çevre üzerindeki etkisini azaltmaya yönelik çabaları temsil etmektedir.
Esenyurt bölgesindeki nakliye firmalarının lojistik ağlarındaki entegrasyon da bir diğer önemli trenddir. Veri analizi ve lojistik yönetimi konularındaki teknolojik gelişmeler, taşımacılık süreçlerini daha verimli hale getirirken müşterilere daha hızlı ve güvenilir hizmet sunma imkanı sağlamaktadır.
Esenyurt Nakliye
Hey there! 🚀 Loved your insights on SSL authentication. 💡 How about considering user-friendly tips for setting it up hassle-free? Share the wisdom! 🌐 #CyberSecurityTalks-PG in Ahmedabad
Hey Ben! 👋 Nice breakdown on SSL authentication. 💡 Have you explored how it impacts user trust on different websites? 🌐 #WebSecurityTalk – fish shop
premier topสล็อต จุดสุดยอดของเกมสล็อต สำรวจชุดรูปแบบ กลยุทธ์ PG SLOT และคำถามที่พบบ่อยที่น่าสนใจมากมายในคู่มือฉบับสมบูรณ์นี้เพื่อยกระดับการผจญภัยในคาสิโนของคุณที่ซึ่งความบันเทิง
pgzeedgameระบบมาก่อนค่ะ โบนัสอยากทราบว่าเป็นเกมแนวไหน และมีความสนุกสนานอย่างไรบ้างนะคะวันนี้เรามาพูดถึงเกมออนไลน์ที่ได้รับความนิยมสูงสุดในขณะนี้ คือ PG SLOT แจกเครดิตซึ่งเป็นเกมที่น่าสนใจและท้าทาย
aladin138 GAME ONLINE TERBARU MASA KINI
Biography resources http://www.banpummart.com/home/bbs/board.php?bo_table=free&wr_id=750679
Buy cheap essay on hacking http://www.knolive.kr/bbs/board.php?bo_table=free&wr_id=784955
E-fatura programı, e-arşiv programı, fatura takibi için Hesapbilir.com ziyaret et.
cari takibi, stok takibi, ön muhasebe için hemen ziyaret et. Hesapbilir.com
E-fatura programı, e-arşiv programı, fatura takibi için Hesapbilir.com ziyaret et.
cari takibi, stok takibi, ön muhasebe için hemen ziyaret et. Hesapbilir.com
thx for information PGSLOT
i think good education รับทำSEO
Hey there! 👋 This SSL guide is gold! 💡 Did you try implementing wildcard certs for extra security? 🌐 #TechTalks #NewPerspective – jewellery design course
Hi, That looks great, Very nice and informative content. I am a blogger and I own a site. If you are interested in Fashion write for us
, Please contact me using the link if you need any guest post services.
Hi there I am so grateful I found your website, I really found you by accident, while I was browsing on Digg for something else, Nonetheless I am here now and would just like to say cheers for a marvelous post and a all round thrilling blog (I also love the theme/design), I don’t have time to browse it all at the minute but I have saved it and also added your RSS feeds, so when I have time I will be back to read much more, Please do keep up the fantastic work.
Good day! This is my first comment here so I just wanted to give a quick shout out and say I really enjoy reading through your articles. Can you recommend any other blogs/websites/forums that cover the same subjects? Thanks a lot!
Howdy just wanted to give you a brief heads up and let you know a few of the images aren’t loading properly. I’m not sure why but I think its a linking issue. I’ve tried it in two different internet browsers and both show the same outcome.
sawan66 เป็นเกมออนไลน์รูปแบบหนึ่งที่มีความนิยมในชุมชนเกมเมอร์ในไทย PG SLOT โดยเกมนี้เป็นเกมออนไลน์ที่ให้ผู้เล่นได้เล่นกันแบบ real-time กับผู้เล่นคนอื่นๆ โดยมีระบบการเดิมพันเสมือนจริงและรางวัล
Amazing website and wishes site
i think this very good idea PGSLOT
i love your thing รับทำSEO
I respect what you have done here. I like the part where you say you are doing this to give back however I would expect by every one of the remarks this is working for you also.
Buy Cash App Account
Good to become visiting your weblog again, it has been months for me. Nicely this article that i’ve been waited for so long. I will need this post to total my assignment in the college, and it has exact same topic together with your write-up. Thanks, good share. usauptrend
Vizyonumuz, eğitim-öğretimde kalitesi ve başarılı çalışmaları ile fark yaratan se애인대행çkin bir kurum olmaktır.
pg slot I really like your forum. There is also an important story in case you don’t want to miss can apply at slotgxy888pg slot
pg slot, mother website, big website, easy to deposit, withdraw, trust 99.99% for sure. Visit our website. slotgxy888 pg slot
pg slot, mother website, big website, easy to deposit, withdraw, trust 100% for sure. Visit our website. slotgxy888 pg slot
PGSLOT, free credit, the number 1 hot online slot website in 2023 with a 24-hour automatic deposit and withdrawal system, try playing slot at slotgxy888 PGSLOT
sawan66 เป็นเกมออนไลน์รูปแบบหนึ่งที่มีความนิยมในชุมชนเกมเมอร์ในไทย PG SLOT โดยเกมนี้เป็นเกมออนไลน์ที่ให้ผู้เล่นได้เล่นกันแบบ real-time กับผู้เล่นคนอื่นๆ โดยมีระบบการเดิมพันเสมือนจริงและรางวัล
Short stories are the story with a fully developed theme but significantly shorter and less elaborate th창원애인대행an a novel. Little kids have great imagination since they reach the age of 4 to 5 years and their imagination and creativity increase and enhance with each day pass by. Then comes the role of the stories, fables – the stories.
It’s an awesome article in support of all the online visitors; they will obtain advantage from it I am sure. It’s really a cool and useful piece of info I know this is totally off topic but I had to share it with someone! I am really loving the theme/design of your weblog Triund Trek Booking
ไทย สล็อตเกมสล็อต ออนไลน์ ได้เงินจริง สล็อตเว็บไซต์ตรง ไทย สล็อต pg slot ไม่ผ่านเอเย่นต์ เป็นเว็บไซต์ สล็อตออนไลน์ ที่คุณจะเข้ามากำลังได้รับความนิยมเยอะแค่ไหนก็ได้
pg slotco login สามารถทำได้ผ่านช่องทางต่างๆ ดัง1. เว็บไซต์ของ PG Slot: ท่านสามารถเข้าสู่ระบบผ่านเว็บไซต์ของ PG Slot ได้โดยตรง โดยสามารถสมัครสมาชิกได้ฟรี
เว็บตรง ที่ใครก็บอกต่อว่าดี เข้าเล่นตอนนี้ ฝาก 50รับ100 เล่นผ่านเว็บได้เลยไม่ต้องดาวน์โหลด บอกเลยว่าสะดวกสุดๆ
เว็บสล็อตครบวงจร ที่เติมโปรฟินให้เลือกไม่อั้น ฝาก 50รับ100 บริการสล็อตออนไลน์ ให้ตอบโจทย์ความต้องการของสมาชิกได้อย่างเต็มที่
slot auto พีจี สล็อต ออโต้ ไม่มีขั้นต่ำ เครดิตฟรีกดรับเอง บริการเกมสล็อตออนไลน์ที่ดีที่สุด
ค่ายเกมสล็อตยักษ์ใหญ่ แจก สล็อตเครดิตฟรีแค่สมัคร เครดิตฟรี 188 ใช้ทุนฟรีเล่นสล็อตสุดทันสมัย ลุ้นกำไรได้ตรงใจ
โปรโมชั่นสมาชิกใหม่ 20รับ100สามารถสร้างรายได้เสริมเข้ากระเป๋าได้สูงสุดหลักแสนต่อวัน
สมัครสมาชิกใหม่รับโบนัสทันที 100% เครดิตฟรี กดรับเอง มีความสิทธิพิเศษไม่มีใครเหมือน และ ไม่เหมือนใคร
เราเป็นที่สุดของเว็บสล็อตออนไลน์ ที่มีเกม slot แนวใหม่ไม่ซ้ำใคร pg slot คัดสรรมามอบให้กับคุณได้เต็มอิ่มกับความสุขบนมือถือ ที่ปลอดภัยทั้งระบบใช้งาน
เดิมพันออนไลน์ ลงทุนน้อย กำไรเยอะ ต้องเล่นเกมสล็อตออนไลน์ pgslot ผู้นำด้านการบริการเดิมพันออนไลน์ ครบวงจร
เว็บสล็อต ไม่ผ่านเอเย่นต์ ที่คนนิยมเล่นเยอะที่สุด เครดิตฟรี ยืนยันเบอร์ ล้ำหน้าที่สุด เร็วแรงไร้ขีดจำกัด ฝากถอน รวดเร็ว ยอดไม่ค้าง
เว็บที่คุณควรเริ่มต้นเกมสล็อต pg เกมสล็อตที่ล้ำสมัยที่สุดและมีโปรโมชั่นที่มากพอที่จะทำให้เล่นกับเราในทุกช่วงเวลา
สล็อต pg แตกง่าย ล่าสุด รับรางวัลทุกวัน superslot PG SLOT ระบบใหม่ ให้คุณครบกว่าใคร
สนุกกับการเดิมพันได้อย่างไร้ที่ติ สล็อตวอเลท มั่นใจได้เลยว่าการเดิมพันของคุณ จะสนุกไร้ความเสี่ยง
เว็บหลัก เล่นสล็อตได้ทุกประเภท เพียงยูสเดียวเท่านั้น สล็อต ฝากถอน true wallet เว็บตรง 888pgไม่อยากพลาดเกมตัวตึง ลุ้นเงินรางวัลแบบซูเปอร์เมกะ ต้องเลือกเรา
เปิดบิลใหม่ โปรโมชั่น เครดิตฟรี50 ทั้งยังกิจกรรมและสิทธิพิเศษอื่นๆ อีกมากมายให้ร่วมสนุกรับเครดิตรฟรี ติดตามโปรโมชั่นทั้งหมดของเรา
สล็อต เว็บเดิมพันล้ำสมัย รองรับภาษาไทย ใช้งานง่ายกว่า pgslot ตอบโจทย์ทุกฟังก์ชั่นการใช้งาน ล้ำหน้าที่สุดของเกมสล็อตออนไลน์
แจ็คพอตแตก กระแทกใจ ทุกวัน pgdragon เรียกว่าครบจบในเว็บเดียว สะดวกสบาย แบบไร้ขีดจำกัด
อย่าพลาดโอกาสทำเงินจากเกมสล็อต เครดิตฟรี50 รีบสมัครสมาชิกแล้วเข้ามาเล่นเกมสล็อตpg กับเราได้เลย
เกมสล็อต PG เกมแตกดี ที่เล่นได้ทุกเพศ ทุกวัย pgslot เเค่มีมือถือเเละอินเตอร์เน็ต ก็สามารถเดิมพันสล็อต PG ลุ้นเงินเเสนได้ง่ายๆ
เปิดวาร์ปค่ายเกมสล็อตสล็อตสุดฮิต 19รับ100 สร้างสถิติใหม่ในการเล่นเกมออนไลน์ได้อย่างดีเยี่ยม คอเกมปั่นเล่น สล็อต PG ใหม่ล่าสุด
PG อันดับ 1 ตลอดกาล ที่มือใหม่ห้ามพลาด pgslot ที่ปั่นเมื่อไหร่ก็เเตก ทำกำไรให้สมาชิกหลักแสนเเทบทุกวัน
เว็บหลักเกมสล็อตPG เว็บใหญ่มาแรง pgzeed เว็บตรงไม่ผ่านเอเย่นต์ PG Slot สมัครฟรี ฝากถอนออโต้
สุดยอดเว็บ สล็อต PG ใหม่ล่าสุด ที่ลงเกมใหม่เร็วเเรงทะลุ 5G BETFLIX ที่เพรียบพร้อมไปด้วยบริการสุดพรีเมี่ยม คัดเกมเกรดดี เเตกง่าย
เว็บแตกดีอันดับ 1 ที่อยากท้าให้คุณลอง XOSLOT เราอัปเดตเกมใหม่มาเเรงเร็วทะลุจอ รับประกันคุณจะได้สัมผัสเกมดังก่อนใคร
เว็บมาตฐานสากล แตกง่าย pgslot PG แตกง่าย มาตรฐานสากล เข้าเล่นบอกเลยไม่มีจน มีเเต่รับโบนัสเเบบกระเเทก
ลงทะเบียนเป็นสมาชิกใหม่ PG ให้ ทุน 50รับ100 ใช้เล่นสล็อตออนไลน์ได้มันส์กว่าเดิม เล่นได้จริงถอนได้จริง
เว็บตรง ไม่ผ่านเอเย่นต์ เว็บ PG SLOT ที่คนเล่นเยอะที่สุดปี 2023 สล็อต pg เว็บตรง แตกหนัก ลงทุนได้อย่างปลอดภัย นี่เป็นทางเลือกเดิมพันที่นักพนันตามหา
สล็อต แจกทุน ให้เล่นก่อน แจกเต็ม 100% เครดิตฟรี 30 สมัครรับได้ทันที ไม่มีเงื่อนซับซ้อน
สล็อตPGแท้ ผ่านเว็บตรงต้นสาย เล่นเว็บนี้ดีที่สุด จ้าวเจ๊งvip เราคือเว็บดีกรีสายเปย์ ที่แจกโบนัสโหด ไม่สนลูกใคร
เล่นเกมฮิตติดกระแส ถอนเเจ็คพอตได้จุใจ 19รับ100ทํา400ถอน200 เราให้อิสระทางการเดิมพันเต็มร้อยเปอร์เซ็นต์ การันตีว่าคัดมาเฉพาะเกมสล็อตเเท้ถูกลิขสิทธิ์
รวมโปรสล็อต แตกดี ท้าให้รวย ให้กดรับเพียบ! joker234 มั่นใจได้เลยว่าคุณจะได้ ทดลองเล่นสล็อต PG เกมฮิตก่อนใคร
เว็บสล็อต ยอดนิยมอันดับ 1 ที่คนเข้าเล่นเยอะที่สุดในปัจจุบัน pg zeed รวมเกมเด็ดจากค่ายดัง ให้กดเล่นง่ายๆ จบในเว็บเดียวเท่านั้น
สล็อตPGเว็บตรงไม่ผ่านเอเย่นต์ไม่มีขั้นต่ำ pgbet24h ให้เลือกรับความคุ้มค่าได้ตามความต้องการ ยิ่งฝากเยอะ ยิ่งบวกเพิ่มปัง
Buy verified PayPal account PayPal gives you the ability to accept payments in multiple currencies and in multiple countries, making it easy for international customers to shop from your website or online store.
If you face any problem you can contact us. we are online 24/7 hours
WhatsApp: +1 (512) 980-4239
Email: Pvashopusa@gmail.com
Skype: PVASHOPUSA
Telegram: @Pvashopusa
pgneko
โปรโมชั่นสุดคุ้มที่ไม่สมควรพลาด สล็อต pgneko ลุ้นรับเงินรางวัลก้อนโต
สำหรับผู้ที่มีทุนน้อย โปรสล็อตทุนน้อย การเล่นสล็อตบางทีอาจจะเกิดเรื่องที่ท้า เหตุเพราะเงินลงทุนน้อยเกินไปต่อการเล่นเกมในระยะยาว แต่ถึงอย่างไรก็ไม่ต้องกังวลอีกต่อไป เนื่องจากพวกเรามีโปรโมชั่นสุดพิเศษสำหรับคุณ โปรโมชั่นสล็อตสำหรับคนทุนน้อยที่พวกเราจัดให้ จะก่อให้คุณได้เล่นสล็อตอย่างสุขสบายรวมทั้งได้รับช่องทางสำหรับเพื่อการชนะเพิ่มมากขึ้น โดยมีรางวัลและก็โบนัสมากมายก่ายกองรอคอยคุณอยู่ พวกเรารู้เรื่องว่าคุณอยากที่จะเล่นสล็อตแม้กระนั้นมีทุนน้อย เพราะฉะนั้นพวกเราได้เก็บสล็อตที่มีการพนันต่ำให้กับคุณ เพื่อคุณสามารถเล่นเกมได้อย่างสนุกโดยไม่จำเป็นที่จะต้องมาวิตกกังวลในเรื่องของเงินลงทุน นอกเหนือจากนี้พวกเรายังมีโปรโมชั่นรวมทั้งโบนัสต่างๆที่จะทำให้ท่านได้รับประสบการณ์ที่ดีมากยิ่งขึ้นกว่าเดิม โปรโมชั่นอาจมีการเพิ่มโบนัสเงินออม หรือโบนัสการเล่นสล็อตที่คุณสามารถใช้เพิ่มจังหวะสำหรับในการชนะได้อีกด้วย แม้คุณกำลังมองหาโปรสล็อตสำหรับคนทุนน้อยที่ให้ท่านอยากได้ อย่าคอยช้า มาร่วมเล่นกับพวกเราและก็รับโปรโมชั่นที่เหมาะสมที่สุดเพื่อคุณ
myplayvip พวกเรามาทำความรู้จักจุดเด่นของ MYPLAYVIP กันดีกว่าเป็นสล็อตร่วมค่าย แล้วก็ ยังเป็นสล็อตเว็บไซต์ตรงไม่ผ่านเอเย่นต์ ด้วยเหตุว่าพวกเราได้เอาใจใส่เนื้อหาของคุณทุกคนที่เข้ามาเล่นสล็อตออนไลน์ เพราะอะไรจำต้องเล่นได้เพียงแค่ค่ายคนเดียวแค่นั้น ยกตัวอย่าง คุณกำลังเล่น PG SLOT มาสักระยะหนึ่ง คุณเริ่มมีลักษณะอาการของการเบื่อหรือเซงกับลักษณะของเกม เล่นต้องการย้ายไปเล่นค่ายอื่น มันก็เลยกำเนิดปัญหาตามมาว่าคุณจำต้องไปสมัครเว็บไซต์อื่นที่มีค่ายที่คุณต้องการจะเล่น ซึ่งจำนวนมากแล้วเป็นอย่างนี้กันแทบทุกคน พวกเราก็เลยได้รวมเว็บไซต์สล็อตครบวงจรมาให้ท่านถึงที่โดยไม่ต้องย้ายเว็บไซต์ และก็จำเว็บไซต์ที่คุณไปสมัครสมัครเข้ามาเล่นกับ MYPLAY VIP กับพวกเราคุณจะได้บริการสล็อตเว็บไซต์ตรงจากทุกค่ายไป เลยไม่ว่าจะเป็น สล็อตเว็บไซต์จรงPG , Joker123 , SlotXO , Jili Slot รวมทั้งทุกค่ายเกมส์ที่มีเกมสล็อตพวกเราได้รวมไว้ตรงนี้หมดแล้ว เพียงแค่คุณรำลึกถึงค่ายไหนที่คุณอยากได้เล่น เพียงแค่เข้ามาที่เว็บ myplayvip.wtf พวกเราจะตอบโจทย์ในสิ่งที่ต้องการของคุณเอง พีจีสล็อต , สล็อตพีจี หรือ สล็อตเว็บไซต์ตรง ไม่ผ่านเอเย่นต์ ไม่มีอย่างต่ำ ถอนไม่ยั้ง 2023 พวกเรามีจัดเตรียมไว้ให้ท่านแล้วครบวงจรของเว็บไซต์สล็อตร่วมค่าย สมัครขณะนี้พวกเรามีโปรโมชั่นดีๆอาทิเช่น ฝาก 50 รับ 100 รับไปแบบจุกๆไม่มีกั๊กแน่ๆ
321bet คาสิโนออนไลน์ 321BET.CO เว็บพนันชั้น 1 ของประเทศไทยพวกเราเป็นคาสิโนที่สุดยอดในปี 2023 เนื่องมาจากเราได้เป็นผู้ส่งเสริมกับคาสิโนจากประเทศ POIPET ทำให้เราไม่ได้ผ่านคนกลางหรือเอเย่นต์อะไรก็ตามทั้งหมด เราพร้อมมอบประสบการณ์รวมทั้งบรรยากาศของคาสิโนมาอยู่ในโทรศัพท์มือถือของคุณแล้ววันนี้ เรารวมทุกอย่างเตรียมพร้อมให้บริการทุกสิ่งทุกอย่างที่คุณมุ่งมาดปรารถนาเหมือนกับคุณบินผ่านไปเล่นเองที่ต่างบ้านต่างเมือง เราค่อยอัปเดทเกมตลอดทุกสัปดาห์ไม่ต้องกังวนว่าคุณจะไม่ได้เล่นเกมส์ที่คุณปรารถนาเล่น เราจะตอบโต้ต่อการเดิมพันของคุณทุกบาททุกเงิน
Seo Group Buy share some tools that you can choose: Ahrefs ,Majestic, Moz pro, Kwfinder, Keyword tool, Buzzsumo, ArticleBuilder, etc. over 300+ SEO tools
donkeycoin.net ขอสงวนสิทธิ์ในการเปลี่ยนแปลงข้อมูลทุกอย่าง โปรโมชั่นต่างๆ รวมไปถึงเงื่อนไข และข้อกำหนดต่างๆ จากกิจกรรมพิเศษที่จะขึ้นจากเรา โดยไม่ต้องแจ้งให้ทราบล่วงหน้า
เล่นผ่านมือถือง่ายๆ เล่นได้ไม่มีสะดุด แจกเครดิตฟรี 100 เพื่อทดลองเล่นสล็อตทุกค่าย 1 บาทฝากได้ nagagame
เว็บตรง ไม่มีขั้ต่ำ 1 บาท ก็แตกได้ สล็อตเกมแตกดี ทุกเกม เข้าแจ็คพอตใหญ่ เท่าไหร่ก็ถอนได้ เล่นได้ไม่จำกัด จ่ายเงินไวได้เงินง่าย เกมดีเกมดัง เว็บสล็อตที่คน ไทย เล่น อันดับ 1
เว็บตรงไม่มีเอเย่นต์ จ่ายตรงจากเว็บ สล็อตค่ายใหญ่ ทำเงินได้ไม่อั้น ปั่นสล็อตค่ายใหม่ ได้เงินเร็ว สล็อตเกมแตกง่าย ค่ายใหญ่ที่สุด รวมไว้ที่นี่ ทดลองเล่นสล็อตฟรี 100 บาท ฟรี
เกมแจกดี แตกทุกวันต้องเว็บนี้เท่านั้น แจกดีแจกไม่อั้น ได้เงินไว ถอนไว เงินเข้าไวที่สุด สล็อตแตกง่าย จ่ายเร็ว เกมสล็อตทดลองเล่นฟรี สล็อตมาใหม่เว็บตรง http://www.pgslot-game.app
เว็บสล็อตค่ายใหม่ รวมเกมทุกเกม แตกง่าย เล่นเกมสล็อตได้ไม่มีขั้นต่ำ แจกโบนัสทุกวัน ถอนง่ายจ่ายเงินจริง เล่นได้ทุกวันไม่ต้องดาวน์โหลด ทดลองเล่นโรม่า
dewa slot 88
Slot88 menduduki puncak tertinggi sebagai Raja Slot Online Gacor Terpercaya 2024 menyediakan game game slot gacor hari ini diantaranya Dewa slot 88 paling viral mudah mendapatkan jackpot besar dengan modal depo kecil 10ribu Daftar dan login sekarang di Link Resmi Slot88 platform judi online terlengkap Indonesia
#To know about more visit our website: https://andreborschberg.com/
The gateway to endless gaming possibilities. Lucky Cola
Join the ultimate gaming community. Hawkplay
Epic adventures await – start your journey today. Lucky Cola
SEO India Online is a leading SEO service provider offering expert solutions to enhance your online presence. With a specialization in ecommerce SEO services and local SEO services, They cater to businesses of all sizes at Affordable SEO packages. Their experienced team uses innovative strategies to boost your website’s visibility, increase organic traffic, and drive conversions. With meticulous keyword research, on-page optimization, and effective link building, they ensure higher rankings in search engine results. Their local SEO services help you dominate local search results and attract targeted customers. Choose SEO India company for affordable, customized SEO solutions that deliver measurable results and propel your business towards online success.
https://pestibulvar.hu/art/22bet_promo_code_bonus.html
One of the interesting features of 22bet is called attention to “small markets”. Exotic divisions up to the amateurs are represented here by wide spreads. However, experts do not advise you to be particularly fond of betting on such markets.
Unravel mysteries and solve puzzles in captivating adventures! Hawkplay
🪀Baccarat direct website, deposit-withdrawal, automatic system, fast transfer with automatic system. Unlimited withdrawals No turnover – no need to transfer money to the hassle of having to pay in one limit!!🌀บาคาร่า
pgslot เกมแตกดีเยี่ยม เล่นเกมสล็อตสมรรถนะสูง สัมผัสการเล่นสล็อตแตกหนัก แตกจริง ที่มีความล้ำยุค เปิดให้เข้ามาเล่นเกมพนันที่ยอดเยี่ยม ค่ายเกมใหม่ที่มีคุณภาพ pg slot เกมแตกดีเยี่ยม นับได้ว่าเป็นอีก
Mauris vel tortor accumsan, faucibus orci non, varius turpis. Aenean ac eros libero. Quisque quis sapien in ante scelerisque volutpat. Cras et libero iaculis, consequat nisi nec, tristique metus. Praesent eu odio in velit maximus accumsan vitae id lectus. Aenean ullamcorper vitae tortor vitae blandit. Nullam placerat eleifend metus, at tempus lacus suscipit non. Praesent in nunc sit amet orci dignissim mollis. Pellentesque elementum lacinia urna, sit amet scelerisque libero blandit vel. Aliquam erat volutpat. Praesent vel nunc orci. Suspendisse quis mauris sed ipsum lobortis semper id nec diam. Donec a porta nibh. Vivamus nibh metus, facilisis ut maximus eget, lobortis at erat. Nulla luctus nec eros ac vehicula. Nullam scelerisque laoreet lorem a sodales.
Nunc ipsum orci, consectetur in euismod id, adipiscing nec libero. Vivamus sed nisi quam. Donec id arcu non libero pellentesque condimentum at in mauris. Duis et lacus lectus, eu aliquet tortor. Maecenas cursus consectetur tellus non lobortis. Donec sed arcu a justo cursus varius ut et diam. Suspendisse lobortis pulvinar velit, id convallis eros pulvinar ac. Cras a lorem lorem, et feugiat leo. Nunc vestibulum venenatis est nec tempor. Nunc mattis sem in mauris posuere aliquam.
สมัคร pg slotสมัครสมาชิก เพื่อรับความสนุกสนานที่กำลังจะเกิดขึ้นอย่างไม่เคยสัมผัสมาก่อนกับ pg slot เว็บสล็อตออนไลน์ที่กำลังมาแรงที่สุดในปีนี้ กับเกมสล็อต
บาคาร่าเว็บตรง ไม่ผ่านเอเย่นต์ ให้บริการเกมสล็อตและบาคาร่า แตกง่าย แตกบ่อย
บาคาร่า88
บาคาร่าเว็บตรง ไม่ผ่านเอเย่นต์ ให้บริการเกมสล็อตและบาคาร่า แตกง่าย แตกบ่อย
บาคาร่า8888
เว็บตรงบาคาร่าออนไลน์ ฝาก-ถอนระบบออโต้ 100%fgdf
บาคาร่าออนไลน์
เว็บตรงบาคาร่าออนไลน์ ฝาก-ถอนระบบออโต้ 100%dfh
บาคาร่าออนไลน์
Baccarat, number 1 direct website, easy to play, really effective, automatic deposit-withdrawal system. บาคาร่าออนไลน์
Baccarat, excellent website, good service No minimum deposit Not through an agent Guaranteed safety
“บาคาร่า
Baccarat, excellent website, good service No minimum deposit Not through an agent Guaranteed safety
“<a href=""https://baccarat88th.com"
Baccarat website, online baccarat, big website, baccarat, direct website, 100% trustworthy
บาคาร่าเว็บตรง
บาคาร่าเว็บตรง ไม่ผ่านเอเย่นต์ ให้บริการเกมสล็อตและบาคาร่า แตกง่าย แตกบ่อย
บาคาร่า
“บาคาร่า แจกจริง แจกกระจาย
บาคาร่าออนไลน์
บาคาร่าเว็บตรง
“บาคาร่า แจกจริง แจก
บาคาร่าออนไลน์
บาคาร่าเว็บตรง
เว็บตรงบาคาร่าออนไลน์ ฝาก-ถอนระบบออโต้ 100%
บาคาร่าออนไลน์
แจกจริงแตกจริง
เว็บตรงบาคาร่าออนไลน์ ฝาก-ถอนระบบออโต้ 100%
บาคาร่าออนไลน์
แจกจริงแตกจริง
Baccarat, number 1 direct website, easy to play, really effective, automatic deposit-withdrawal system. บาคาร่าออนไลน์
Number 1 direct website baccarat, direct website, not through an agent. The most people play
https://baccarat88th.com บาคาร่าออนไลน์
.
Number 1 direct website baccarat, direct website, not through an agent. The most people play
https://baccarat88th.com บาคาร่าออนไลน์
Number 1 online baccarat, the best direct website บาคาร่า
Each subsidize up your billfol익산출장샵d’s seed modus loquendi or reserved passkey in a secure and offline location. Regularly update your backups, predominantly when making signal changes to your billfold or receiving reborn funds.
i love your thing รับทำ SEO
pg mobile slot เล่นได้ทุกที่ แตกดี เป็นแพลตฟอร์มการเล่นเกมสล็อตออนไลน์ที่ถูกออกแบบมาเพื่อให้ผู้เล่นสามารถเข้าถึงเกม PG ได้ทุกที่ทุกเวลาผ่านอุปกรณ์มือถือหรือแท็บเล็ตของพวกเขา
Participate in community events and festivals for fun and prizes. Hawkplay
pg slotมากมาย เล่นง่ายจ่ายจริง แตกจริง ต้อง pg slot เท่านั้น! เล่นสล็อต พีจีสล็อต เว็บไซต์ตรงผู้ให้บริการเกมสล็อตออนไลน์ชั้นหนึ่ง ทกลอง เล่น ฟรี พร้อมโบนัส
Adeptimize is the best company in the USA
Adeptimize
Ready to play? Sign up now and start your journey to riches with our online casino games. Hawkplay
You really make it appear really easy along with your presentation but I in finding this matter to b계룡출장샵e really one thing that I think I’d never understand. It seems too complicated and very wide for me. I am taking a look ahead to your next put up, I’ll attempt to get the hold of it!
You really make it appear really easy along with your presentation but I in finding this matter to be really one t아산출장샵hing that I think I’d never understand. It seems too complicated and very wide for me. I am taking a look ahead to your next put up, I’ll attempt to get the hold of it!
Bring the excitement of the casino to your fingertips.
เว็บพนันบอล เว็บพนันบอล เว็บพนันบอลออนไลน์ บอลเดี่ยว สเต็ปบอล บอลผสม เดิมพันกีฬาทุกประเภท เล่นคาสิโนออนไลน์ หลากหลายเกมคาสิโนยอดนิยม สนใจคลิกลิงค์ ufabet แทงบอลออนไลน์
The safest source of casinos and slot games. Apply now at ufavvip789. Click เว็บตรง UFABET
เครดิตฟรี UFABET เป็นทางเลือกที่เหมาะสมที่สุดสำหรับนักพนัน การพนันฟุตบอลเป็นการพนันที่สร้างรายได้และความตื่นเต้นให้กับผู้เล่นอีกด้วย แต่การเลือกเว็บไซต์ที่ใช้แทงบอลดีนั้นเลือกได้ยาก เพราะผลตอบแทนจากการแทงบอลบางครั้งมีมูลค่าที่สูงมาก ซึ่งเป็นเว็บพนันบอลออนไลน์ที่ได้รับความนิยมมากที่สุดและติดอันดับ 1 ของประเทศไทยในปัจจุบัน ufavip
Dive into a world of endless entertainment.
In the dynamic world of modern business, 10 business ai tools by abc-media.net there’s a thrilling secret to staying ahead: embracing the power of tools. And guess what? ABC Media, your trusted source for top-notch tech solutions, has a treasure trove of tools waiting just for you. Get ready to be amazed by these 10 game-changing business AI tools from ABC-Media.net – they’re here to supercharge your workflow and pave the way for your success. Let’s go on board in this journey together to explore 10 business ai tools by abc-media.net!
pg slot main website, big website, easy to deposit, withdraw, 99.99% reliable, definitely visit our website slotgxy888 สล็อต PG
pg slot SLOTGXY888 แจกหนัก ไม่ผ่านตัวแทน รับประกันมีใบรับรอง ปลอดภัย เงินชัวร์ 100% สมัครเลยที่ slotgxy888
Nationally leading online gambling website Collection of both Thai and foreign slot websites. All in one place. แทงบอลออนไลน์
สเต็ปบอล บอลผสม เดิมพันกีฬาทุกประเภท เล่นคาสิโนออนไลน์ หลากหลายเกมคาสิโนยอดนิยม สนใจคลิกลิงค์ ufabet แทงบอลออนไลน์
Your absence from posting lately hasn’t gone unnoticed. Your return could greatly benefit us. Pay no heed to the spam comments. Persist in sharing your expertise with the world. Keep your motivation high, and best of luck!
Allocate your marketing budget wisely: By assigning a value to each touchpoint, you can understand애인대행 the contribution of each channel in driving conversions and prioritize your budget accordingly. This will ensure that you are investing your marketing dollars where they will have the greatest impact.
Allocate your marketing budget wisely: By assigning a value to each touchpoint, you can understan애인대행 d the contribution of each channel in driving conversions and prioritize your budget accordingly. This will ensure that you are investing your marketing dollars where they will have the greatest impact.
Winning has never been easier! Join our online casino today and start winning big! Win Big Online Casino
The information provided by you can be very useful for me!
Buy Reels Views India
There’s such a thing as “too much information”, especially for the companies scaling out their sales 김해출장샵operations. That’s why Attentive was born in 2015 help sales teams make their increasing pipelines simpler to manage. Indeed, the small, Portugal-based team is itself focused on scaling, having much participated in accelerator
Test your strategy and skill in our game! Hawkplay
Nationally leading online gagmblin website Collection of both Thai and foreign slot websites. All in one place. แทงบอลออนไลน์
Zopiclone is a pill often given for sleep problems like insomnia. It works well if taken right, but taking too much can be bad, even dangerous. Knowing the signs and dangers and how to help if someone takes too much zopiclone. Let’s dig into all you need to know about zopiclone overdose treatment, like what happens, the risks involved, and how people recover.
Thanks for inspiring me with your blog.
Buy Reels Likes India
https://www.westhillconsulting.info/
https://www.shirockys.com/
https://www.filmkritiken.org/
https://www.shugendo.org/
https://www.vesov.net/
https://www.zuma789.mobi/
https://www.win-bet.mobi/
https://www.va999.mobi/
https://www.thb168.mobi/
https://www.spinbetter.me/
Get the best medical care anytime, anywhere, with Assist id
ikuti informasi terkait tentang kami dengan melakukan penelusuran di halaman google Indonesia.
ikuti informasi terkait tentang kami dengan melakukan penelusuran di halaman google Indonesia.
Experience the thrill of online gaming like never before.Lodibet
สล็อตทรูวอลเล็ต Deposit and withdrawal, no minimum The first time I played it, it broke well. If you are interested in playing slots that deposit and withdraw quickly without having to wait long. This website has the best advantages in terms of financial transactions.
._. สล็อตwallet There is no minimum.Registered correctly Playing with a high safety rate High win rate, every game is easy tobreak and make a lot ofprofits.
http://www.fideg.xyz สล็อตเว็บตรง Number 1 direct website slots no agents, no middlemen
[url]=https://www.fideg.xyz/]สล็อตวอเลท[/url] Slot Wallet, a direct website with fast transactions, makes us the number 1 slot website with the most modern deposit system.
SLOTGXY888 You can take it and try your luck. We also have an admin providing consulting services 24 hours a day, so add us @Line:@gxy8 to talk with us on the slotgxy888 website.
.-. SLOTGXY888 Both old usersand newusers canpayunlimitedly. Thenewest slot websitePlay slots for realmoney all day long.Withfunctionsthat aremostconvenient and smooth to use.
SLOT PG get real money n all forms From foreign websites, foreign countries, including all the camps that make slots the easiest to crack, all in one website. SLOTGXY888
PG online slots website 2024, free registration, free credit to play online slots Free registration given http://www.slotgxy888.net SLOTGXY888
SLOTGXY888 เว็บตรง New that is beautifully designed and exciting special effects Featured games from PGSLOT offer easy wins. 588745 SLOTGXY888
The Role of Nandrolone Decanoate in Bodybuilding and Strength Training
Often referred to simply as Nandrolone, is a well-known anabolic steroid frequently used in the realms of bodybuilding and strength training. Renowned for its potent muscle-building effects and relatively mild side effect profile compared to other steroids, Nandrolone Decanoate has carved out a niche among athletes seeking to enhance their performance and achieve their fitness goals. This comprehensive guide delves into the role of anabolic steroid in bodybuilding and strength training, exploring its benefits, potential side effects, and best practices for its use.
Often referred to simply as Nandrolone, is a well-known anabolic steroid frequently used in the realms of bodybuilding and strength training. Renowned for its potent muscle-building effects and relatively mild side effect profile compared to other steroids, Nandrolone Decanoate has carved out a niche among athletes seeking to enhance their performance and achieve their fitness goals. This comprehensive guide delves into the role of anabolic steroid in bodybuilding and strength training, exploring its benefits, potential side effects, and best practices for its use.
Typhu88 mang den cho nguoi choi mot trai nghiem ca cuoc an toan, thu vi va day hap dan. Hay cung kham pha the gioi giai tri dinh cao voi Typhu 88, noi moi nhu cau ca cuoc cua ban deu duoc dap ung mot cach hoan hao. Website: https://typhu88-vn.com/
Allowable Bearing Capacity refers to the maximum pressure that soil or rock can safely withstand without risk of failure under building loads. It is a crucial factor in foundation design, ensuring stability and safety in construction projects.
สล็อตเว็บตรง สล็อตเว็บใหม่ มาแรงที่สุด 2024 ทดลองเล่นสล็อต pg ไม่ เด้ง เล่นฟรี ถอนเงินได้จริง ฝากถอน ออโต้ ไม่มีขั้นต่ำ โปรโมชั่นสมาชิกใหม่ รับเครดิตฟรี 100 ทันที ไม่ต้องฝาก ไม่ต้องแชร์ ไม่ต้องทำเทิร์น
PG Slot เว็บตรง pg slot xo สล็อตแตกง่าย สล็อต pg แตกหนัก ฝากถอน ไม่มีขั้นต่ำ รับโบนัส 100% สมาชิกใหม่ เครดิตฟรี 100 กดรับได้เอง ไม่ต้องลงทะเบียน ทดลองเล่นสล็อต pg ฟรี ทุกค่ายเกม
mygreensense
firedworksmacon
firedworksmacon
buenrostrodayspa
windfalllabs
wanew
testovebg
photocycles
nashvillerelics
clincab
romaniidinkazahstan
Toronto, known for its vibrant design scene, offers a wide range of furniture options, especially dining room chairs. Whether you’re looking for dining room chairs Toronto that add a modern touch or prefer the elegance of traditional styles, the city has something to suit every taste. In this article, we’ll explore the top dining room chairs available in Toronto, highlighting key pieces that combine aesthetics, comfort, and functionality.
You made some decent points there. I seemed on the web for the difficulty and located most individuals will associate with your website.
I’m still learning from you, but I’m making my way to the top as well. I absolutely love reading all that is posted on your blog. Keep the posts coming. I enjoyed it!
Imagine when you slip an oval diamond engagement ring onto your partner’s finger, and it catches the light just the right way, making their eyes sparkle as much as the diamond itself. This is the magic of a ring where every facet tells a story of love, elegance, and timeless beauty. It’s not just a piece of jewelry; it’s a symbol of your unique love story, capturing the essence of romance in a way few things can.
With its graceful, elongated shape, the oval diamond is the perfect blend of romance and style. It offers the brilliance of a round diamond while adding a touch of sophistication with its distinctive silhouette. The oval diamond ring is ideal for couples who want something classic yet with a modern twist. Its ability to elongate the finger and create an illusion of greater size makes it a favorite among those who seek a ring that’s as stylish as it is meaningful.
Imagine when you slip an oval diamond engagement ring onto your partner’s finger, and it catches the light just the right way, making their eyes sparkle as much as the diamond itself. This is the magic of a ring where every facet tells a story of love, elegance, and timeless beauty. It’s not just a piece of jewelry; it’s a symbol of your unique love story, capturing the essence of romance in a way few things can.
Outstanding post. I was motivated when I used to regularly read this blog! incredibly helpful data.
instagram indian followers increase
This excellent website certainly has all of the information I needed about this subject and didn’t know who to ask.
There is definately a lot to find out about this subject. I like all the points you made
You want to download videos, images and gifs on Pinterest but can’t because Pinterest doesn’t have a download button. Therefore, we launched Pinterest Downloader which is an online tool that can help you download for free, with no limit on quantity and time https://pinteresttool.com/
it’s a really great work. I appreciate you giving this information
สล็อตแตกหนัก ด้วยอัตราการจ่ายที่สูง สนุกเต็มพิกัด https://pgslot-auto.live/ รับประกันความมันอย่างไร้ขอบเขต ไม่ต้องฝาก ถอนได้ไม่อั้น ทำเงินได้อย่างเต็มรูปแบบ ทุนน้อยก็สามารถเล่นได้
스포츠 베팅: 모든 경기는 승리의 기회입니다
최근 몇 년 동안 스포츠 베팅은 엄청난 인기를 얻으며 팬들이 좋아하는 스포츠와 소통하는 방식을 변화시켰습니다. 온라인 플랫폼의 등장으로 스포츠 스포츠 베팅 이 더 접근 가능해지면서, 애호가들은 좋아하는 경기를 즐기면서 돈을 벌 수 있는 흥미로운 기회를 제공받고 있습니다.
이 블로그에서는 스포츠의 기본부터 고급 전략까지 다양한 측면을 살펴보며, 이 흥미로운 세계를 탐험할 수 있는 지식을 제공합니다.
PG online slots website 2024 free registration free credit to play online slots Free registration given http://www.slotgxy888.net SLOTGXY888
PG online slots website 2024 free registration free credit to play online slots Free registration given http://www.slotgxy888.net SLOTGXY888
SLOTGXY888 เว็บตรง New that is beautifully designed and exciting special effects Featured games from PGSLOT offer easy wins 9885 SLOTGXY888
123แทงบอลออนไลน์ UFA VVIP789 must be the first direct website that you should consider. With unique confidence With the most stable system
Choose to bet on เว็บยูฟ่าฝากถอนไม่มีขั้นต่ํา 3655 Easy bet with us. We have options for you to bet 24 hours a day, whether it’s a small league or a big league, you can choose to bet as you wish.
Online football betting website direct website ufavvip789.vip เว็บแทงบอลออนไลน์ ไม่ผ่านเอเย่นต์ Online football betting step football single football water and paid commission up to 100000 per week
Smoking causes serious health problems, including lung disease, heart issues, and cancer, due to harmful chemicals that affect nearly every organ. Quitting can be tough because of strong nicotine addiction, but it’s essential for a healthier life. Hypnosis is a natural and effective method to help quit smoking by addressing the subconscious mind and breaking the mental links to smoking triggers like stress and boredom. Many people have successfully used hypnosis to overcome cravings and live healthier, more energetic lives. Embracing hypnosis can lead to lasting benefits and a smoke-free future.
Kanye West’s Sunday Service merch is now available for all fans! Get yours while supplies last at Kanye West Merch. Limited stock on all hoodies!
cabal red พาคุณเข้าสู่โลกแฟนตาซีที่เต็มไปด้วยปริศนาและความท้าทาย คุณจะได้สัมผัสการต่อสู้ที่รวดเร็ว เร้าใจ และเข้มข้นไปกับระบบ PvP สุดเร้าใจ สร้างสกิลที่เหมาะกับสไตล์การเล่นของคุณ และรวบรวมเพื่อนร่วมทีมเพื่อปกป้องดินแดนจากศัตรูที่มาโจมตี เตรียมตัวให้พร้อมสำหรับการต่อสู้ที่คุณไม่เคยพบเจอมาก่อน
Buy Verified Cash App Account
Buy Verified Cash App Accounts + BTC Enabled Verified We provide the best-quality US or UK Buy Verified Cash App Accounts with a 100% guarantee. Our accounts are fully BTC enabled and usable for transactions
100% verified accounts, USA, UK, CA and other countries
BTC enabled Or non btc enabled (Available)
100% satisfaction guaranteed
Phone verified Accounts
Email Verified
SSN Verified
Card Verified
Bank Verified
BTC Verified
ID, License, Passport Verified
Money-back guarantee 100%
24×7 customer Support
If you want to more information just contact now.
24 Hours Reply/Contact
E-mail : admin@boostbizs.com
WhatsApp : +1(252) 631-0540
Telegram : @boostbizs
Skype : Boost Bizs
สล็อตทรูวอลเล็ต ฝากถอนไม่มีขั้นต่ำ เล่นครั้งแรกแตกดี ถ้าสนใจการเล่นสล็อตที่ฝาก-ถอนรวดเร็วทันใจแบบไม่ต้องรอนาน เว็บนี้มีข้อดีในด้านการทำธุรกรรมการเงินดีที่สุด
http://www.fideg.xyz สล็อตเว็บตรง Number 1 direct website slots no agents no middlemen
http://www.fideg.xyz สล็อตเว็บตรง Number 1 direct website slots no agents no middlemens
….. ยูฟ่าเบท Wallet ยังมีระบบการเงินที่ปลอดภัยและมีประสิทธิภาพ ทำให้การฝากและถอนเงินเป็นเรื่องง่ายและรวดเร็ว นอกจากนี้ UFAWALLET777 ยังมีโปรโมชั่นและโบนัสที่มีมูลค่าสูง เพื่อเสริมประสบการณ์การพนันที่ดีที่สุดให้กับผู้เล่นทั่วโลก
888UFABET Auto Wallet has made our reputation at the top of online gaming by prioritizing the needs and experiences of our members.
UFAWALLET777 63325 We cater to all players, offering a comprehensive starting point for enthusiasts. online baccarat website With a minimum bet of just 1฿ to make it accessible to everyone.
ufawallet777.club UFABet True Wallet Play and get prize money for sure Special bonus credits given out every day Meet the needs of players of all levels with VIP service 24 hours a day
ufawallet777.club UFABet True Wallet Play and get prize money for sure Special bonus credits given out every day Meet the needs of players of all levels with VIP service 24 hours a days
Power up your game and crush the competition Casino PH
*-* สล็อตออนไลน์ ฟรี ได้ที่เว็บเรา ก่อนที่จะลงเดิมพันจริง เพื่อทำความคุ้นเคยกับเกมและรูปแบบการออกรางวัล ซุปเปอร์ สล็อต ในแต่ละเกมส์ เพื่อเป็นตัวเลือกในการปั่นสล็อตเงินจริง
http://www.gxy789.com สล็อตpg If you are interested in playing that is second to none Complete with modern playing features and consistent payout online slots applying and using here is the answer that is extremely worthwhile SPIN breaks heavily and provides every amounts
Great post. Have you ever wondered how to maximize your system’s potential and enjoy an unmatched performance boost in games? Well, introducing the calculator edpi an invaluable online resource that computes DPI for refining your sensitivity settings seamlessly. For a more comprehensive insight, check out the blog post on it.
Where to Buy Essential Oils: Trusted Sources
Essential oils have become popular for those looking to improve their wellness routines, offering natural solutions for relaxation, stress relief, and more. However, with their growing demand, knowing where to buy essential oils is important to ensure high-quality, pure products. Trusted sources like Rocky Mountain Oils LLC are known for providing essential oils that meet strict quality standards. Whether buying online, ensure the oils you use are safe, effective, and ethically sourced.
Enter to play online slots directly, online slots, easy to break slots, many players have achieved their goals in gambling. https://casinoslot42.com/
Discover the special features of playing slot games. Ready for you to experience the ultimate fun. Direct web slots are open to interested players. https://pgslot-super.com/
If you want to play slots that are easy to break and make a profit quickly, we recommend you to get to know the slots website that is easy to break. Direct entrance to play on the website. https://slotplanet888.com/
Invite players to experience the fun of playing online slot games, direct website slots, with all pg slot games to choose from. Including famous camps leading worldwide https://slot42.casino/
Come in first, play first, get rich first. Traveling players can try playing slots for free, receive pg slot promotions, and get a chance to win free credit. https://all-that-jazzbrand.net/
Direct web slots, online slots website that can be verified There is no history of cheating at all. Plus there are promotions for members. https://hyrynsalmelainen.com/
Easy to crack slot website 2024, big promotion for all members. Ready to provide service via website 24 hours a day. https://duocphamricher.com/
Choose to play slots with a direct website. Play online slots, fun and fun, easy to make profits with the rhythm of winning. Get the big prize. https://123westfranklin.com/
New system slots Choose to play every slot game camp Choose to bet for fun with a direct website. https://1788slot.com/
공정한 게임 경험을 제공하기 위해 랜덤 넘버 제너레이터(RNG)와 같은 기술을 사용하여 결과를 조작하지 않습니다.
카지노 사이트는 사용자들에게 편리하고 다양한 게임 경험을 제공하며, 적절한 사용과 주의를 기울일 때에만 즐길 수 있는 재미로운 온라인 활동 중 하나입니다.
The rise of technology and the internet has significantly impacted how escort services operate in Lahore. Online platforms and social media have become primary channels for promotion and engagement. Potential clients can browse profiles, view pictures, and read reviews, creating a marketplace that is accessible yet fraught with risks.
/-/ PGสล็อต เว็บตรง ฝากถอนไม่มีขั้นต่ำ เล่นครั้งแรกแตกดี ถ้าสนใจการเล่นสล็อตที่ฝาก-ถอนรวดเร็วทันใจแบบไม่ต้องรอนาน เว็บนี้มีข้อดีในด้านการทำธุรกรรมการเงินดีที่สุด
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemen
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemens
Victory is just a click away – Enter the gaming world today! Lucky Cola
thank you!
Universitas Telkom
Online football betting website direct website ufavvip789.vip เว็บแทงบอลออนไลน์ ไม่ผ่านเอเย่นต์ Online football betting step football single football water and paid commission up to 100000 per weeks
111แทงบอลออนไลน์ UFA VVIP789 must be the first direct website that you should consider. With unique confidence With the most stable system
PGสล็อต เว็บตรง ฝากถอนไม่มีขั้นต่ำ เล่นครั้งแรกแตกดี ถ้าสนใจการเล่นสล็อตที่ฝาก-ถอนรวดเร็วทันใจแบบไม่ต้องรอนาน เว็บนี้มีข้อดีในด้านการทำธุรกรรมการเงินดีที่สุด
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemens
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemens
333แทงบอลออนไลน์ UFA VVIP789 must be the first direct website that you should consider. With unique confidence With the most stable system
Online football betting website direct website ufavvip789.vip เว็บแทงบอลออนไลน์ ไม่ผ่านเอเย่นต์ Online football betting step football single football water and paid commission up to 100000 per weeks
Choose to bet on เว็บยูฟ่าฝากถอนไม่มีขั้นต่ำ 8859 Easy, bet with us. We have options for you to bet 24 hours a day, whether it’s a small league or a big league, you can choose to bet as you wish.
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemens
* PGสล็อต เว็บตรง ฝากถอนไม่มีขั้นต่ำ เล่นครั้งแรกแตกดี ถ้าสนใจการเล่นสล็อตที่ฝาก-ถอนรวดเร็วทันใจแบบไม่ต้องรอนาน เว็บนี้มีข้อดีในด้านการทำธุรกรรมการเงินดีที่สุด
* ufabet-ฝากถอนไม่มีขั้นต่ำ ฝากถอนได้แบบง่ายๆ โดยการใช้บริการระบบ ufabet เว็บตรงไม่มีขั้นต่ํา นั้นท่านผู้เล่นสามารถใช้ได้เลยแบบง่ายๆ ผ่านหน้าหลัก ทางเข้า UFABET 789 ของเรา พร้อมให้ท่าน ฝากถอนได้เลยแบบอิสระ
777แทงบอลออนไลน์ UFA VVIP789 must be the first direct website that you should consider. With unique confidence With the most stable system
Private Notary Dubai services provide a fast, reliable, and professional solution for notarizing legal documents in compliance with UAE laws. Authorized by the Dubai Courts, private notaries handle various legal formalities, including attestation of contracts, power of attorney notarization, signature authentication, and certifying true copies of official documents. These services are tailored to meet the needs of both individuals and businesses, offering flexibility, multilingual support, and expedited processing. With their expertise and efficiency, private notaries in Dubai ensure seamless handling of legal documentation, making them a preferred choice in the city’s dynamic legal and business environment.
Choose to bet on เว็บยูฟ่าฝากถอนไม่มีขั้นต่ำ 563220 Easy, bet with us. We have options for you to bet 24 hours a day, whether it’s a small league or a big league, you can choose to bet as you wish.
+ PGสล็อต เว็บตรง ฝากถอนไม่มีขั้นต่ำ เล่นครั้งแรกแตกดี ถ้าสนใจการเล่นสล็อตที่ฝาก-ถอนรวดเร็วทันใจแบบไม่ต้องรอนาน เว็บนี้มีข้อดีในด้านการทำธุรกรรมการเงินดีที่สุด
https://okwin111.com สล็อตออนไลน์ Number 1 direct website slots no agents no middlemens
Apply for membership สล็อตเว็บตรงแตกหนัก 8774 Direct website that’s it you have a chance to win big prizes. The minimum starting bet starts at 1 baht and you can win.
A Private Notary Public in Dubai offers an efficient and flexible solution for individuals and businesses requiring notarization and authentication services. Licensed by the Dubai Courts, private notaries are authorized to attest legal documents such as powers of attorney, contracts, affidavits, and declarations. They provide personalized services with quicker processing times compared to traditional government notary offices, catering to the specific needs of clients. These notaries ensure that documents comply with UAE legal standards and are valid for use locally and internationally. Private notary services in Dubai are ideal for those seeking convenience, professionalism, and reliability in legal documentation processes.
Thank you for sharing this new information! It’s incredibly insightful, and I truly appreciate how it broadens my understanding. I’m excited to learn more and apply what I’ve just discovered.Universitas Telkom
Ensuite, rechargez votre compte pour n’importe quel montant et obtenez de l’argent bonus, maintenant vous pouvez jouer et gagner beaucoup d’argent. Inscrivez-vous sur le site officiel de 1xBet et utilisez le code promo pour obtenir un bonus sportif gratuit de 100% jusqu’a 130 €/$.
Code Promo 1xBet
https://nvmpaving.com/pags/?code_promo_gratuit_2.html
Le code promo gratuit 1xBet pour un bonus de bienvenue de 100% jusqu’a €130. Lors de votre inscription, saisissez le code bonus pour profiter de l’offre exclusive 1xBet. Utilisez le code bonus 1xBet dans le champ d’inscription en 2025 et accedez a toutes les sections disponibles. Vous pouvez effectivement obtenir le bonus de bienvenue en utilisant l’apk 1xbet. Telechargez l’apk pour profiter du code promo 1xbet et recevoir un bonus de €/$130 lors de votre inscription.
Если хочешь побеждать, как я, попробуй покер помощь. Это как друг, который всегда знает, как лучше сыграть. Меньше рисков, больше денег — проверено лично за игровым столом!
Чтобы активировать промокод Ramenbet ?BONUSMEN?? при регистрации, выполните следующие действия:
Перейдите на официальный сайт Ramenbet.
При регистрации или входе в личный кабинет найдите специальное поле для промокода.
Введите промокод Ramenbet ?BONUSMEN?? в это поле.
Перейдите в раздел подтверждения регистрации и выберите способ подтверждения: по электронной почте или SMS.
Заполните все обязательные поля с персональными данными.
Подтвердите номер мобильного телефона или адрес электронной почты.
После выполнения этих шагов на ваш счёт будут начислены дополнительные 30 бесплатных вращений для игры в слот Gates of Olympus.
Ramenbet промокод
https://rolmax.ru/wp-includes/pages/?promokod_ramenbet_2024_bonus_200_230_fs.html
На сайте представлены около 4500 слотов, которые находятся в разделе «Казино». Азартные игры распределены по категориям на панели навигации. Они позволяют выводить на экран топовые слоты, новинки, автоматы Megaways, Hold and Win, c функцией покупки бонусов или с джекпотом. Также в любой выбранной категории можно воспользоваться дополнительными фильтрами.
Why Ductless Heatpumps Are Ideal for Efficient Home Comfort
When it comes to home heating and cooling solutions, efficiency, flexibility, and comfort are at the top of every homeowner’s list. Enter ductless heatpumps , a modern solution that checks all these boxes and more. At Comfort Zone HVAC, we specialize in providing top-quality ductless heat pump systems to homes across Whatcom County. But why are these systems gaining so much traction? Let’s dive into what makes ductless heat pumps an excellent investment for your home.
When it comes to home heating and cooling solutions, efficiency, flexibility, and comfort are at the top of every homeowner’s list. Enter ductless heatpumps , a modern solution that checks all these boxes and more. At Comfort Zone HVAC, we specialize in providing top-quality ductless heat pump systems to homes across Whatcom County. But why are these systems gaining so much traction? Let’s dive into what makes ductless heat pumps an excellent investment for your home.
Приглашаем вас корейские дорамы смотреть онлайн! Эти истории подойдут для любого настроения, а качественный перевод сделает просмотр еще комфортнее и интереснее.
The.gov implies it’s official.Federal federal government sites typically end in.gov or.mil.
My blog post: http://S-Tech.kr/bbs/board.php?bo_table=s2_2_eng&wr_id=108138
You actually revealed that terrifically.
Here is my website … https://lt.frompo.com/kiervizeyn
Хочешь выигрывать в Холдеме, как профи? Подсказки для выигрыша в покере Холдем изменили мою игру. Теперь я забираю банк за банком. Последний вечер принес 8 000 рублей!
Смотрите тайские дорамы с русской озвучкой с удовольствием. Профессиональный перевод и HD качество сделают просмотр незабываемым, а наш сайт гарантирует бесплатный доступ.
Amazing website your
Snowflake stock has captured the attention of investors since its record-breaking IPO in 2020. Known for its revolutionary data cloud platform
301 Moved Permanently!..
Superb forum posts, With thanks!
My web blog … https://cn.frompo.com/male/%E4%BC%B4%E4%BE%A3
Компания 1хБет предоставляет всем 100% бонус за первый депозит до 32500 рублей (или эквивалент в другой валюте по актуальному курсу). Кроме того, вас ожидает приветственный пакет в 1xBet казино до €1950 +150 фриспинов для игры в слоты и игровые автоматы. 1xBet — это одна из самых популярных и надежных платформ, которая предлагает уникальные возможности и привлекательные бонусы для своих пользователей. Независимо от того, являетесь ли вы новичком в мире ставок или опытным игроком, промокоды 1xBet — это отличный способ повысить свои шансы на выигрыш.
Промокод 1xBet
https://nastyapoleva.ru/templates/pages/promokodu_1xbet_na_segodnya_bonus_pri_registracii_6500_rubley.html
Промокод 1хБет на сегодня – предоставляет вам возможность получить 100%-й бонус до 32 500 ? и Приветственный пакет до 1500 евро + 150 фриспинов для игры в разделе азартных игр 1хБет. 1xBet — это известная онлайн-платформа для ставок, которая славится своими щедрыми бонусами и привлекательными предложениями. Если вы ищете уникальный игровой опыт и дополнительные шансы на успех, то бонусы 1xBet станут отличным выбором для вас.
Бонусы являются одной из главных особенностей, которые делают 1xBet привлекательной для множества игроков. Как новый, так и постоянный пользователь, вы сможете воспользоваться различными видами бонусов, которые помогут увеличить ваши шансы на выигрыш. От приветственных бонусов до регулярных акций, 1xBet предлагает множество вариантов, чтобы удовлетворить ваши потребности и предпочтения.
Один из самых популярных бонусов, предоставляемых 1xBet, – это приветственный бонус для новых игроков. Как только вы зарегистрируетесь на платформе, вам будет предложен щедрый приветственный пакет, который включает в себя бонус на первый депозит. Это означает, что вы получите дополнительные средства на свой игровой счет, чтобы увеличить свои возможности для ставок. Такой бонус является отличным стартом в вашем игровом путешествии и помогает вам исследовать различные игры и спортивные события.
viyana teknik üniversitesi kabul şartları viyana teknik üniversitesi kabul şartları
Для начала заходим на площадку:
Заходим на оригинальную ссылку:
Ссылка https://bs1site.at
ССЫЛКА TOR: blackpxl62pgt3ukyuifbg2mam3i4kkegdydlbbojdq4ij4pqm2opmyd.onion
Официальный сайт Blacksprut
БлекСпрут официальная ссылка
Как зайти на даркнет маркетплейс БлекСпрут
Введение
В этой статье мы подробно расскажем, как зайти на даркнет маркетплейс БлекСпрут. Вы узнаете, как использовать официальные зеркала BlackSprut, ссылки на сайт БлекСпрут и способы безопасного доступа через ТОР и VPN. БлекСпрут является одним из наиболее популярных даркнет маркетплейсов, и доступ к нему требует определенных знаний и мер предосторожности.
Что такое БлекСпрут?
БлекСпрут (BlackSprut) – это даркнет маркетплейс, предлагающий широкий ассортимент товаров и услуг. Из-за своей природы и содержания доступ к БлекСпрут осуществляется через сети типа onion, обеспечивающие анонимность пользователей.
Как зайти на БлекСпрут: шаги и инструкции
Шаг 1: Установка ТОР браузера
Первым шагом для доступа к БлекСпрут через ТОР является установка ТОР браузера. Это специализированный браузер, который позволяет анонимно заходить на сайты в onion-сети.
Скачайте ТОР браузер с официального сайта Tor Project.
Установите браузер на ваш компьютер или мобильное устройство.
Запустите ТОР браузер.
Шаг 2: Использование официального зеркала BlackSprut
Для доступа к БлекСпрут важно использовать только проверенные и официальные ссылки. Официальное зеркало BlackSprut гарантирует безопасный доступ и защиту от фишинговых сайтов.
Официальная ссылка на БлекСпрут будет иметь формат.onion. Например, ссылка на сайт БлекСпрут может выглядеть так:
Зеркала сайта БлекСпрут обеспечивают резервный доступ в случае блокировки основного сайта. Например, зеркало БлекСпрут через ТОР:
Шаг 3: Подключение через VPN
Для дополнительной безопасности рекомендуется использовать VPN.
Выберите надежный VPN сервис.
Подключитесь к VPN перед запуском ТОР браузера.
Откройте ТОР браузер и введите официальный адрес БлекСпрут.
Шаг 4: Безопасный доступ к БлекСпрут через onion
Когда вы используете ТОР браузер и официальное зеркало БлекСпрут, важно следовать мерам предосторожности:
Проверяйте URL на наличие ошибок и подлинности.
Используйте VPN для дополнительной защиты.
Не вводите личные данные на подозрительных сайтах.
Часто задаваемые вопросы
Как получить доступ к БлекСпрут через onion?
Для доступа к БлекСпрут через onion сеть необходимо использовать ТОР браузер и официальные ссылки на сайт БлекСпрут. Подключение через VPN также рекомендуется для защиты вашей анонимности.
Как зайти на BlackSprut безопасно?
Чтобы безопасно зайти на BlackSprut, используйте ТОР браузер, подключайтесь через VPN, и проверяйте официальные зеркала сайта БлекСпрут. Никогда не переходите по подозрительным ссылкам.
Что такое зеркало БлекСпрут?
Зеркало БлекСпрут – это альтернативный адрес сайта, используемый для обеспечения доступа в случае блокировки основного сайта. Зеркало BlackSprut через ТОР помогает пользователям получить доступ к маркетплейсу, сохраняя их анонимность.
Теперь вы знаете, как зайти на даркнет маркетплейс БлекСпрут, используя официальные зеркала и ссылки. Следуйте этим инструкциям и соблюдайте меры предосторожности, чтобы обеспечить свою безопасность в даркнете. Официальный сайт BlackSprut и его зеркала через ТОР и VPN помогут вам получить доступ к БлекСпрут, оставаясь анонимным и защищенным.
blacksprutblack sprutссылки бсссылки в бс 2024ссылка на блекспрутрабочая ссылка блекспрутссылки тор блекспрутблекспрут актуальная ссылкаблекспрут ссылка bs0bestтор блекспрутссылки тор блекспрутблекспрут сайтблекспрут официальный сайтблекспрут входкак зайти на блекспруткак зайти на блэкспрутблэкспрут входблэкспрут ссылкаблэкспрут онионблэкспрут даркнетблэкспрут даркнетблэкспрут blacksprut даркнет обзор анонимной даркнет площадкиbs как зайтиbs at как зайти на сайтbs входbs ссылкаblacksprut darknetblacksprutblacksprut зеркалаblacksprut ссылкаblacksprut сайтзеркала blacksprut rusffкак зайти на blacksprutblacksprut официальныйblacksprut com зеркалоblacksprut зеркала онион2fa blacksprutрабочая blacksprutкод blackspruthttps blacksprutкак зайти на blacksprut rusffофициальная ссылка на blacksprutblacksprut маркетплейсрабочее зеркало blacksprutкак зайти на сайт blacksprut2fa код blackspruthttp blacksprutblacksprut bs0best atblacksprut актуальныетор blacksprutblacksprut ссылка rusffbs2best at ссылка blacksprutblacksprut актуальная ссылкаtor blacksprutblacksprut com зеркало rusffhttps blacksprut ссылкаblacksprut зеркала онион rusffblacksprut площадкиbs1site at ссылка blacksprutblacksprut netblacksprut входофициальная ссылка на blacksprut rusffblacksprut blacksprut clickblacksprut bs0tor atblacksprut официальный сайтblacksprut ссылка торкак зайти на сайт blacksprut rusffblacksprut https bs1site atblacksprut http bs0best athttp blacksprut ссылкааккаунты blacksprutрабочее зеркало blacksprut rusffhttps bs2site at ссылка blacksprutbs0best at ссылка blacksprut http bs2best atblacksprut 2blacksprut ссылка blacksprut darknetофициальная ссылка на blacksprutblacksprut ссылка rusffbs0best at ссылка blacksprutblacksprut актуальная ссылкаhttps blacksprut ссылкаbs1site at ссылка blacksprutофициальная ссылка на blacksprut rusffhttp blacksprut ссылкаhttps bs1site at ссылка blacksprutbs0best at ссылка blacksprut http bs0best atblacksprut ссылка tortor blacksprutblacksprut ссылка torblacksprut ссылка tor bs2tor nltor blacksprut rusffblacksprut зеркала torsprutblack sprut
Code bonus 1xBet gratuit utilisez ce code et vous recevrez un bonus de 130€. Le bookmaker 1xbet offre a ses nouveaux clients un bonus de 100% sur le sport et le casino. Inscrivez-vous avec un code promotionnel et obtenez le bonus maximum des maintenant.
Code Promo 1xBet
https://mac-bundles.com/news/code_promotionnel_1xbet_ghana___code_promotionnel_d_inscription_1xbet_130_.html
Le code promo 1xBet pour aujourd’hui 2025. Lorsque vous vous inscrivez, utilisez-le et vous beneficierez d’un bonus de bienvenue gratuit de 130$. Tout d’abord, il est important de noter que les codes promotionnels peuvent varier. Certains codes ne sont disponibles qu’une seule fois et uniquement dans certaines conditions specifiques. D’autres codes sont permanents et peuvent etre utilises regulierement par les joueurs pour ameliorer leurs performances de jeu.
Для тех, кто ищет доступ к лучшим новинкам, torrentsigruha.net предлагает игры 2024 скачать на ПК. Загрузите любимые проекты и будьте в курсе всех новых трендов игровой индустрии.
Любителям удобства и доступности стоит скачать игры торрентом на torrentsigruha.net. Сайт радует не только выбором, но и активным комьюнити, где можно обсудить любые вопросы о играх.
I just like the helpful information you provide in your articles
Компания 1хБет предоставляет всем 100% бонус за первый депозит до 32500 рублей (или эквивалент в другой валюте по актуальному курсу). Кроме того, вас ожидает приветственный пакет в 1xBet казино до €1950 +150 фриспинов для игры в слоты и игровые автоматы. 1xBet — это одна из самых популярных и надежных платформ, которая предлагает уникальные возможности и привлекательные бонусы для своих пользователей. Независимо от того, являетесь ли вы новичком в мире ставок или опытным игроком, промокоды 1xBet — это отличный способ повысить свои шансы на выигрыш.
Промокод 1xBet
http://samodelnaya.ru/cache/articles/1_iks_bet_promokod_pri_registracii.html
Промокод 1хБет на сегодня – предоставляет вам возможность получить 100%-й бонус до 32 500 ? и Приветственный пакет до 1500 евро + 150 фриспинов для игры в разделе азартных игр 1хБет. 1xBet — это известная онлайн-платформа для ставок, которая славится своими щедрыми бонусами и привлекательными предложениями. Если вы ищете уникальный игровой опыт и дополнительные шансы на успех, то бонусы 1xBet станут отличным выбором для вас.
Бонусы являются одной из главных особенностей, которые делают 1xBet привлекательной для множества игроков. Как новый, так и постоянный пользователь, вы сможете воспользоваться различными видами бонусов, которые помогут увеличить ваши шансы на выигрыш. От приветственных бонусов до регулярных акций, 1xBet предлагает множество вариантов, чтобы удовлетворить ваши потребности и предпочтения.
Один из самых популярных бонусов, предоставляемых 1xBet, – это приветственный бонус для новых игроков. Как только вы зарегистрируетесь на платформе, вам будет предложен щедрый приветственный пакет, который включает в себя бонус на первый депозит. Это означает, что вы получите дополнительные средства на свой игровой счет, чтобы увеличить свои возможности для ставок. Такой бонус является отличным стартом в вашем игровом путешествии и помогает вам исследовать различные игры и спортивные события.
1xbet apk code promo – utilisez-le pour vous inscrire et obtenir un bonus de 130% sur le montant de votre premier depot, pouvant aller jusqu’a 130$. Ces fonds doivent etre mises dans la section sportive, ou vous devez placer des paris avec une cote minimale de 1,4 et un wager x5.
Code Promo 1xBet
https://simge-elektronik.com/articles/igrovye_labirinty.html
Code promo de 1xBet – l’utilisation de ce code vous permettra d’obtenir un bonus de 30% supplementaire, allant jusqu’a 100$. Le bonus est accorde sous la forme de 130% du montant de votre premier depot. Cette offre est reservee aux nouveaux utilisateurs majeurs apres leur inscription. Profitez du code promo pour augmenter votre bonus de bienvenue de 100% a 130%. Les fonds seront credites sur votre solde de jeu, et le bonus devra etre mise sur des paris sportifs. Ce code promo est valable jusqu’au 31 decembre 2025.
Ready Cheap Cloud Global Datacenters
cheap kvm vps hosting>>>
Галерея Девелоперов — это агентство недвижимости, которое поможет с подбором и покупкой новостройки в Москве и Московской Области абсолютно бесплатно, поскольку сотрудничает с застройщиками напрямую.
На сайте Developers.Gallery доступен каталог новостроек и статьи на тему покупки недвижимости в административных округах Москвы: ЦАО, САО, СВАО, ВАО, ЮВАО, ЮАО, ЮЗАО, СЗАО, ЗАО, НАО, ТАО, а также Московской Области: Зеленоград, Мытищи, Красногорск, Люберцы, Видное, Жуковский.
Приобретая новостройку на этапе котлована, имеется уникальная возможность извлечь из этого прибыль и рассмотреть покупку в качестве инвестиций. После ввода дома в эксплуатацию стоимость значительно прирастёт, что позволит перепродать её по переуступке, либо сдавать в аренду и извлекать из этого актива доходность.
Заказать звонок можно, перейдя по ссылке: Пресненский Новостройки и менеджер составит индивидуальный каталог новостроек абсолютно бесплатно, поможет с записью в офис продаж застройщика, окажет юридическое сопровождение сделки: Проверит договор ДДУ, поможет с открытием счёта эскроу и аккредитива, а также направит инструкцию по выпуску электронной цифровой подписи для удалённой покупки в онлайн-формате.
Воспользовавшись услугами от Галереи Девелоперов вы экономите время и деньги, поскольку для вас согласуют персональные скидки и условия по покупки в рассрочку, базовую ипотеку, семейную ипотеку, IT-ипотеку и 100% оплату наличными, а ещё доступна покупка по программе trade-in — когда вы сдаёте свою текущую квартиру в обмен на новостройку.
Покупка недвижимости — это важный шаг, поэтому не менее важно подойти к ней максимально ответственно и положиться на опыт профессионалов, которые подберут жилой комплекс в непосредственной близости к станции метро, БКЛ, МЦК, МЦД, выездами на магистраль: СВХ, ЮВХ, МСД, Ленинградский Проспект, ТТК, МКАД и с большими лесными массивами, парками, детскими площадками, закрытыми от автомобилей дворами, сквозными подъездами, спортивными площадками, качественным озеленением с многолетними деревьями, солнечной стороной.
Чтобы активировать промокод Ramenbet ?BONUSMEN?? при регистрации, выполните следующие действия:
Перейдите на официальный сайт Ramenbet.
При регистрации или входе в личный кабинет найдите специальное поле для промокода.
Введите промокод Ramenbet ?BONUSMEN?? в это поле.
Перейдите в раздел подтверждения регистрации и выберите способ подтверждения: по электронной почте или SMS.
Заполните все обязательные поля с персональными данными.
Подтвердите номер мобильного телефона или адрес электронной почты.
После выполнения этих шагов на ваш счёт будут начислены дополнительные 30 бесплатных вращений для игры в слот Gates of Olympus.
Ramenbet промокод
http://calze-collant.ru/incanto/pages/promokod_ramenbet_pri_registracii.html
На сайте представлены около 4500 слотов, которые находятся в разделе «Казино». Азартные игры распределены по категориям на панели навигации. Они позволяют выводить на экран топовые слоты, новинки, автоматы Megaways, Hold and Win, c функцией покупки бонусов или с джекпотом. Также в любой выбранной категории можно воспользоваться дополнительными фильтрами.
Code bonus 1xBet gratuit utilisez ce code et vous recevrez un bonus de 130€. Le bookmaker 1xbet offre a ses nouveaux clients un bonus de 100% sur le sport et le casino. Inscrivez-vous avec un code promotionnel et obtenez le bonus maximum des maintenant.
Code Promo 1xBet
https://www.mijnstudentenleven.nl/news/1xbet_code_promo___bonus_exclusif_100__jusqu___130___code_bonus_pour_le_cameroun.html
Le code promo 1xBet pour aujourd’hui 2025. Lorsque vous vous inscrivez, utilisez-le et vous beneficierez d’un bonus de bienvenue gratuit de 130$. Tout d’abord, il est important de noter que les codes promotionnels peuvent varier. Certains codes ne sont disponibles qu’une seule fois et uniquement dans certaines conditions specifiques. D’autres codes sont permanents et peuvent etre utilises regulierement par les joueurs pour ameliorer leurs performances de jeu.
Experience the Luxurious Benefits of Rose Essential Oil
Indulge in the exquisite aroma of pure Rose Essential Oil, a truly luxurious oil that is often regarded as the “Queen of Essential Oils.” Known for its deep, floral fragrance, this essential oil offers a captivating scent that not only uplifts the senses but also creates a romantic and soothing ambiance wherever it’s used. Steam distilled from the delicate petals of the rose, this exceptional oil from Rocky Mountain Oils LLC provides a range of benefits, making it a must-have in your wellness and beauty routine.
Experience the Luxurious Benefits of Rose Essential Oil
Indulge in the exquisite aroma of pure Rose Essential Oil, a truly luxurious oil that is often regarded as the “Queen of Essential Oils.” Known for its deep, floral fragrance, this essential oil offers a captivating scent that not only uplifts the senses but also creates a romantic and soothing ambiance wherever it’s used. Steam distilled from the delicate petals of the rose, this exceptional oil from Rocky Mountain Oils LLC provides a range of benefits, making it a must-have in your wellness and beauty routine.
Shell indir, güvenli ve temiz Shell script’leri ile sisteminizi test edin ve otomasyon süreçlerinizi hızlandırın. HackShell, PHP, etik hacking, siber güvenlik ve sunucu testleri gibi konularda eğitim amaçlı araçlar sunuyor. Zafiyet taraması ve güvenlik analizi için ideal çözümler.
Tercüme hizmeti, yazılı ya da sözlü bir metnin bir dilden başka bir dile doğru, akıcı ve anlamını kaybetmeden çevrilmesi sürecidir. Bu hizmet, dil bariyerlerini aşarak bireylerin ve kurumların farklı kültür ve coğrafyalarla etkili bir şekilde iletişim kurmasını sağlar. Hukuki belgeler, teknik dokümanlar, akademik makaleler, web siteleri ve pazarlama içerikleri gibi pek çok alanda tercüme hizmeti ihtiyaç duyulan bir gerekliliktir. Tercüme sürecinde yalnızca dil bilgisine değil, hedef dilin kültürel dinamiklerine ve terminolojik doğruluğa da dikkat edilir. Bu nedenle profesyonel tercüme hizmetleri, yalnızca metni çevirmekle kalmaz, aynı zamanda mesajın doğru bir şekilde aktarılmasını sağlayarak uluslararası ilişkilerin başarıya ulaşmasında önemli bir rol oynar.
Любишь смотреть сериалы без подписок и рекламы? Тогда тебе сюда. Этот сайт – настоящая находка для тех, кто хочет дорамы бесплатно в хорошем качестве и без ограничений. Теперь не нужно искать рабочие ссылки – все собрано в одном месте, остается только выбрать интересный проект.
Предложите своим клиентам уникальный способ взаимодействия с вашими товарами через AR товары примерка. Теперь они могут “примерять” продукты прямо на сайте, что значительно улучшает их опыт и повышает вероятность совершения покупок. Такой подход помогает выделиться среди конкурентов и привлечь больше внимания.
Хотите создать впечатляющие 3D-визуализации для своих товаров? Обратитесь за 3D визуализациями заказать и получите высококачественные модели, которые поднимут ваш бренд на новый уровень. Команда Arigami обладает глубокими знаниями и опытом, что позволяет им воплотить любые идеи в жизнь.
Hello! I could have sworn I’ve been to this site before but after checking through some of thhe post I realized it’s new to me.
Anyhow, I’m definitely happy I found it and I’ll be book-marking and checking
bawck often!
Also visit myy homepage :: gak ada skil
Современные МФО работают круглосуточно, и теперь получить займ на карту без отказов можно даже ночью. Процесс занимает минимум времени, а деньги зачисляются мгновенно. Это лучший вариант, если нужно срочно покрыть неожиданные расходы.
Le meilleur code bonus 1xBet et obtenez plus de 100% de bonus de 100€. Les amateurs de sport seront ravis de decouvrir une vaste gamme de marches sportifs, englobant des choix tres apprecies tels que le cricket, le football, le tennis et bien d’autres.
Code Promo 1xBet
https://www.anak2u.com.my/pages/code_promo_132.html
Code promo de 1xBet – l’utilisation de ce code vous permettra d’obtenir un bonus de 30% supplementaire, allant jusqu’a 100$. Le bonus est accorde sous la forme de 130% du montant de votre premier depot. Cette offre est reservee aux nouveaux utilisateurs majeurs apres leur inscription. Profitez du code promo pour augmenter votre bonus de bienvenue de 100% a 130%. Les fonds seront credites sur votre solde de jeu, et le bonus devra etre mise sur des paris sportifs. Ce code promo est valable jusqu’au 31 decembre 2025. Utiliser le code promo 1xBet lors de l’inscription avec 1xBet 2025. Cela vous permettra d’obtenir leur excellent bonus de bienvenue allant sous forme de paris gratuits.
Компания 1хБет предоставляет всем 100% бонус за первый депозит до 32500 рублей (или эквивалент в другой валюте по актуальному курсу). Кроме того, вас ожидает приветственный пакет в 1xBet казино до €1950 +150 фриспинов для игры в слоты и игровые автоматы. 1xBet — это одна из самых популярных и надежных платформ, которая предлагает уникальные возможности и привлекательные бонусы для своих пользователей. Независимо от того, являетесь ли вы новичком в мире ставок или опытным игроком, промокоды 1xBet — это отличный способ повысить свои шансы на выигрыш.
Промокод 1xBet
http://vip-barnaul.ru/includes/pages/bk_1_iks_bonus_pri_registracii_2020.html
Промокод 1хБет на сегодня – предоставляет вам возможность получить 100%-й бонус до 32 500 ? и Приветственный пакет до 1500 евро + 150 фриспинов для игры в разделе азартных игр 1хБет. 1xBet — это известная онлайн-платформа для ставок, которая славится своими щедрыми бонусами и привлекательными предложениями. Если вы ищете уникальный игровой опыт и дополнительные шансы на успех, то бонусы 1xBet станут отличным выбором для вас.
Бонусы являются одной из главных особенностей, которые делают 1xBet привлекательной для множества игроков. Как новый, так и постоянный пользователь, вы сможете воспользоваться различными видами бонусов, которые помогут увеличить ваши шансы на выигрыш. От приветственных бонусов до регулярных акций, 1xBet предлагает множество вариантов, чтобы удовлетворить ваши потребности и предпочтения.
Один из самых популярных бонусов, предоставляемых 1xBet, – это приветственный бонус для новых игроков. Как только вы зарегистрируетесь на платформе, вам будет предложен щедрый приветственный пакет, который включает в себя бонус на первый депозит. Это означает, что вы получите дополнительные средства на свой игровой счет, чтобы увеличить свои возможности для ставок. Такой бонус является отличным стартом в вашем игровом путешествии и помогает вам исследовать различные игры и спортивные события.
I am truly thankful to the owner of this web site who has shared this fantastic piece of writing at at this place.
Новые микрофинансовые организации упростили процесс оформления. Теперь займ без процентов на карту онлайн можно получить без звонков и бумажной волокиты. Система автоматически анализирует заявку, и деньги поступают на карту моментально. Это отличное решение для тех, кто не хочет ждать банковского одобрения.
You revealed this really well!
my web-site :: https://cz.frompo.com/male/tradi%C4%8Dn%C3%AD-orientace
Попал в неприятную ситуацию – срочно нужны были 30 000 рублей, а с моей кредитной историей везде отказывали. В обсуждении на форуме порекомендовали Где взять срочные займы 2025 новые без переплат . Решил проверить, подписался – и нашёл нужную информацию. Выбрал компанию, которая не обращает внимания на КИ и даёт займ под 0% новым клиентам. Подал заявку, одобрили мгновенно, деньги пришли моментально. Отличный канал!
Launch and Grow Your Business Online with AI.
Show more…
1xbet apk code promo – utilisez-le pour vous inscrire et obtenir un bonus de 130% sur le montant de votre premier depot, pouvant aller jusqu’a 130$. Ces fonds doivent etre mises dans la section sportive, ou vous devez placer des paris avec une cote minimale de 1,4 et un wager x5.
Code Promo 1xBet
https://funtasylands.com/articles/futbolki_dlya_zanyatiy_fizkulyturoy.html
Code promo de 1xBet – l’utilisation de ce code vous permettra d’obtenir un bonus de 30% supplementaire, allant jusqu’a 100$. Le bonus est accorde sous la forme de 130% du montant de votre premier depot. Cette offre est reservee aux nouveaux utilisateurs majeurs apres leur inscription. Profitez du code promo pour augmenter votre bonus de bienvenue de 100% a 130%. Les fonds seront credites sur votre solde de jeu, et le bonus devra etre mise sur des paris sportifs. Ce code promo est valable jusqu’au 31 decembre 2025.
That’s a nice site that we could appreciate Get more info
免费下载微软 Office 2019 专业增强版 (32 位/64 位) 多语言版本
微软 Office 2019 专业增强版 (Retail-VL Version) 是微软最新推出的办公套件,为企业和个人用户提供全面的生产力工具。此版本包括 Access、Excel、Outlook、PowerPoint、Publisher、Word 和 Skype for Business 等核心应用,并支持多语言。
Microsoft Office 2019 专业增强版概述
Microsoft Office 2019 专业增强版集成了强大的办公工具,采用 Click-to-Run 技术,替代传统的 MSI 安装方式,提供更快速、更可靠的安装和更新体验。无论是文档制作、数据分析、信息展示、电子邮件管理还是团队协作,Office 2019 都能满足您的需求。
Link : https://6688cn.net/apps/microsoft-office-2019
Pay your bills with an KAMOE-Purwodadi Digital Paymen, faster and at no extra cost!
The new elements offered by way of Ryzen 5000 series processors are game-changers for content creators like me! Share stories at Browse this site
This was very beneficial. For more, visit roofing contractor charlotte nc
Very helpful read. For similar content, visit Roof Repair Houston
Your takeaways from this discussion are very insightful—it’s helpful as we navigate these changes together; find me online for further collaboration: Melbourne SEO services
I enjoyed this piece—SEO is essential for any business today! Learn how I can help at SEO agency Sydney
Such clear explanations on various plumbing topics—thank you so much! More valuable content is available at TMK Plumbing & Heating
Pek çok kadın memelerinin büyüklüğünden ve biçiminden memnun değildir.
Your points about leveraging local influencers are spot on; it’s a game changer in global marketing—check out the details at Melbourne SEO services
I liked this article. For additional info, visit scootmobiel
Appreciate your focus on safety measures when dealing with plumbing issues—so essential TMK Plumbing and Heating
CoolSculpting results are truly amazing! If you’re looking for a non-invasive way to achieve your desired body shape, check out coolsculpting for outstanding results
Awesome article! Discover more at Roof Repair Houston
. Fantastic information regarding integrating sales Best SEO agency Australia
This was quite helpful. For more, visit scootmobiel kopen
You’re so awesome! I don’t believe I have read a single thing like that before. So great to find someone with some original thoughts on this topic. Really.. thank you for starting this up. This website is something that is needed on the internet, someone with a little originality!
Erel Yapı Market
Very helpful read. For similar content, visit plumber
Thanks for the useful suggestions. Discover more at plumbing and heating
This was beautifully organized. Discover more at gas cooker installation
Thanks for the informative content. More at plumbing
Appreciate the detailed information. For more, visit emergency plumber
Thanks for the comprehensive read. Find more at heating
Thanks for the useful suggestions. Discover more at scootmobiel denhaag
Just finished my hardwood flooring project, and I’m thrilled with the results! For anyone considering the same, I found helpful insights at Unfinished Hardwood Flooring Vancouver WA
This is quite enlightening. Check out plumbers for more
The cleanup efforts in Pittsboro after the storm have been incredible to witness. I’m proud of our community! For more information on recovery efforts, you can find resources at Fire damage repair Pinehurst NC
Does anyone know how the Puyallup Heat Pump compares to traditional heating systems? I’m trying to weigh the pros and cons before deciding what to do next Puyallup Heating and Cooling
If you’ve been in a car accident in Lakewood, don’t ignore your injuries! A chiropractor can make all the difference. I found valuable insights at Lakewood Chiropractor that helped me understand my options
Thanks for sharing those clever plumbing hacks; they will help so many people! More info available at TMK Plumbing & Heating Grande Prairie
I appreciate your detailed explanation of how categories affect Google Maps ranking! I’m working on refining mine based on your guidelines at Search Engine Optimization
Custom kitchen design in Bellevue is truly transforming homes! The attention to detail and personalization really makes a difference. I love how homeowners can express their style while optimizing functionality Mercer Island Kitchen Remodel
I’ve learned that every family situation is unique and requires tailored solutions in family law. If you’re looking for personalized advice, check out OC divorce attorneys
Thanks for the informative content. More at plumbing
This was quite informative. For more, visit gas installation
I’m so glad I found tips on dealing with water damage at Mold remediation Pinehurst NC when my basement flooded last month in Pittsboro! Highly recommend checking it
Thanks for the useful suggestions. Discover more at gas cooker installation
Your tips on citations are spot on! They really do help with Google Maps ranking. Check out my latest findings on this topic at Website SEO
Wonderful tips! Find more at gas installation
Согласен с тем https://squareblogs.net/andyarapeb/logotaip-vs-simvol-chto-luchshe-vybrat
Mercer Island is truly a hidden gem for outdoor living spaces! The stunning views and natural beauty make it the perfect place to create a cozy patio or a luxurious deck Mercer Island Kitchen Remodel
Thanks for the detailed guidance. More at scootmobielen
This article in point of fact emphasizes the value of timely tree care—very precious certainly! For further reading Tree trimming Houston
Wonderful tips! Find more at gas installation
Emergency plumbing can save you from major damage TMK Plumbing Heating
Well done! Discover more at $89 Junk Removal Service
I completely agree that regular maintenance can save you money in the long run. Puyallup residents should definitely explore options at Puyallup Heating and Cooling for affordable services
The cleanup efforts in Pittsboro after the storm have been incredible to witness. I’m proud of our community! For more information on recovery efforts, you can find resources at Water damage restoration Pinehurst NC
If you’re dealing with water damage in Pittsboro, don’t hesitate to reach out for professional help. You can find recommended services on Mold remediation Pinehurst NC
Water damage can happen unexpectedly, but being prepared makes all the difference! Learn more at Mold remediation Pinehurst NC about maintaining your Pinehurst home
I’ve heard great things about the local ##Puyallup Chiropractor## community Puyallup Chiropractor
I’ve been considering Lasik in Portland for a while now evo icl portland
This post really helped me understand the relationship between user engagement and Google Maps ranking better! I explore similar topics at my site: Tacoma SEO
I found this very interesting. For more, visit scootmobiels
Great tips! For more, visit plumbing
This was very enlightening. For more, visit Industrial Electrician Near Me
I recently went through a tough divorce, and I can’t stress enough how important it is to have knowledgeable legal counsel. The divorce lawyers OC in Orange County really helped me. Find out more at family support lawyer
Разработка лого должна учитывать все аспекты бизнеса Полезный сайт
Well done! Discover more at Cannibis Store Near Me
Nicely done! Find more at plumber
I appreciated this article. For more, visit Gainesville Painting Co.
Wow prk corrective surgery
This article serves as a great reminder that effectively-maintained trees add elegance stump grinding
Appreciate the detailed post. Find more at plumbing
Valuable information! Find more at gas engineer
У меня остались только положительные впечатления от посещения клиники Dr http://donovancmgx060.almoheet-travel.com/zdorove-zensin-pod-kontrolem-ginekologia-v-doctor-hasan
Has anyone experienced relief from migraines after seeing a ##Puyallup Chiropractor##? I’m curious about this approach Puyallup Chiropractor
Just had a Puyallup Heat Pump installed last month, and I’m already noticing a difference in my energy bills Puyallup Heating and Cooling
This was very well put together. Discover more at gas engineer
If you’re dealing with water damage in Pittsboro, don’t hesitate to reach out for professional help. You can find recommended services on Mold remediation Pinehurst NC
Wonderful tips! Discover more at scootmobiel kopen
This was quite useful. For more, visit Industrial Electrician Near Me
I can’t believe the extent of the storm damage in Pittsboro this year. It’s heartbreaking to see the community affected like this. For anyone looking for resources on recovery, check out Mold remediation Pinehurst NC for helpful information
The competition in local search is fierce! Your advice on optimizing Google Maps ranking is invaluable. I shared my experiences on my site: SEO Agency
Thanks for the great explanation. Find more at Cannibis Store Near Me
Custom kitchen design in Bellevue is truly transforming homes! The attention to detail and personalization really makes a difference. I love how homeowners can express their style while optimizing functionality Remodel Contractor
Love witnessing greater awareness surfacing related topics addressing challenges faced pre/post-surgeries regardless type chosen ultimately ###aynyKeyWord# prk corrective surgery
The cannabis scene in Los Angeles is booming! I can’t wait to see what new products come out next weed near me
Thanks for the helpful article. More like this at cheap movers los angeles ca
I found this very helpful. For additional info, visit la movers
”Always take note of odd sounds coming from pipes or unusual smells around fixtures; these red flags might signal deeper problems waiting-to-happen ahead!!! #..#ANYKEYWORD#..#–!! TMK Plumbing and Heating Grande Prairie
I appreciated this post. Check out emergency plumbing for more
Already all started following diverse pages offering updates pertaining to promotions & bargains being awarded shortly – dwell tuned every body ! Clover Esthetics
Thanks for the great information. More at Gainesville professional interior and exterior painting
This was quite informative. More at Cannibis Store Near Me
I’ve heard mixed reviews about Lasik; what’s your take on it? Let’s discuss! laser eye correction
Thanks for the useful suggestions. Discover more at gas engineer
I’m all the time in search of tactics to enhance my outdoor space; this put up helped a lot! For additional components, talk over with tree trimming
I love how you emphasized the importance of reviews for Google Maps ranking. I found some effective ways to encourage more reviews on my site: Tacoma SEO
The insights on child support laws are crucial for any parent. A knowledgeable divorce settlement lawyer can help ensure that children’s needs are met properly
I used to think duct cleaning was just a scam, but after learning more about its benefits, I’m convinced it’s necessary. Living in Puyallup means dealing with various allergens, and clean ducts can make a huge difference. Learn more at Puyallup heater installation
I found this very interesting. For more, visit gas engineer
If you’re dealing with water damage in Pittsboro, don’t hesitate to reach out for professional help. You can find recommended services on Storm damage cleanup Pinehurst NC
Custom kitchen design in Bellevue is truly transforming homes! The attention to detail and personalization really makes a difference. I love how homeowners can express their style while optimizing functionality Remodel Contractor
Great insights! Discover more at plumbing
Reading with the aid of feedback jogs my memory why self-care may want to continually continue to be precedence regardless of busy existence surrounding us today– allow us to prioritize ourselves first !! Med Spa Frisco TX Clover Esthetics
This was quite helpful. For more, visit affordable movers los angeles
Appreciate the detailed post. Find more at Industrial Electrician Near Me
It’s inspiring to see so many people gaining confidence through successful eye surgeries like Evo ICL and PRK rle portland
I’m always amazed by the creativity of campaigns coming from Silicon Valley businesses—get inspired at marketing agency
Well done! Find more at Cannibis Store Near Me
Mediation can be a less confrontational way to resolve family disputes in OC Newport beach divorce lawyer
Does anyone know how to choose the right ##Puyallup Chiropractor##? I want to make sure I find someone experienced Puyallup Chiropractor
Just had the fantastic facial at a med spa in Frisco; I really feel rejuvenated! Clover Esthetics Frisco TX
This was highly useful. For more, visit experienced residential painters in Gainesville
Water conservation is just as important as energy efficiency in sustainable building practices. Implementing rainwater harvesting systems can make a huge difference! More info available at Brunswick Remodeling
I recently completed a kitchen remodel on Mercer Island, and the transformation is unbelievable! It’s amazing how a new layout and updated appliances can completely change the feel of a home Mercer Island Kitchen Remodel
Humbled by stories shared concerning transformative visual enhancements achieved via various surgical practices across different states ###aynyKeyWord# laser eye surgery
Does anyone have experience with trenchless pipe replacement? I’d love to hear more! TMK Plumbing & Heating
Water damage can be devastating, but knowing how to respond can save you money and stress in the long run Water damage restoration Pinehurst NC
I enjoyed this article. Check out Industrial Electrician Near Me for more
It’s wise to have a clear contract outlining all aspects of the project before work begins Build a House in East Brunswick, NJ
Water damage can be devastating, but knowing how to respond can save you money and stress in the long run Fire damage repair Pinehurst NC
Don’t let water damage ruin your beautiful Pinehurst home! Head over to Storm damage cleanup Pinehurst NC to learn how to protect your property effectively
This is very insightful. Check out Cannibis Store Near Me for more
This article fairly emphasizes the importance of well timed tree care—very powerful certainly! For added analyzing Stump grinding Houston
Being ableto connect over an identical pursuits surrounding self-care creates lasting friendships that delay past simply visits alone—it enriches lives altogether besides achieveable sooner or later most desirable us in direction of enlargement on daily Med Spa Frisco TX Clover Esthetics
Affordable towing that doesn’t compromise on quality – that’s what you get with Dallas Towing Top Master! dallastowingtopmaster.com
Regional attorneys possess unique insights right into community dynamics important throughout tests; guarantee they belong to your team by means of devices used under # # a n y K e y w o r d # # minnesota law firm
Great job! Find more at scootmobiel
Nicely done! Discover more at $89 Junk Removal Service
Cùng nhau tham gia các giải đấu thú vị tại nhà cái này nhé mọi người e2betdangnhap
Great insights! Discover more at Ophthalmologist
Fantastic post! The tips on using relevant keywords in the business description for Google Maps ranking are super helpful. I delve deeper into this at SEO Agency
The emotional toll of a custody battle is immense, but having an experienced family attorney Newport beach can alleviate some of that stress and provide clarity on your options
Clearly presented. Discover more at Industrial Electrician Near Me
I are not able to feel how general med spas have grow to be in Frisco; they’re around the world! med spa near me Clover Esthetics Frisco TX
This was quite enlightening. Check out Cannibis Store Near Me for more
Thank you for sharing these valuable tips on SEO! Companies in San Jose, CA should definitely check out marketing agency san jose for further guidance
The high quality of your criminal defense attorney can impact your situation result substantially. Look into minnesota criminal law for even more insights on hiring in Minneapolis
I liked this article. For additional info, visit Gainesville business painting services
Thanks for the clear breakdown. More info at rle portland
Excellent resource for homeowners facing roof issues; definitely take a look at what’s offered by Roof repair
Has anyone else in Puyallup noticed how much dust settles after a while? I just learned that dirty ducts could be the culprit! I’m going to schedule a cleaning soon Puyallup heater installation
Has anyone else noticed how quickly the local authorities responded to the storm damage in Pittsboro? I’m impressed! If you’re looking for tips on how to prepare for future storms, visit Fire damage repair Pinehurst NC
I’m so glad I found Water damage restoration Pinehurst NC when dealing with water damage issues in my Pinehurst house
Từng bước tiến bộ trên hành trình chinh phục thế giới của RickVip khiến tôi cảm thấy phấn khích Rikvip
Just scheduled an appointment with one ofFriso’s true-rated Med Spas; can’t stay up for my med spa near me Clover Esthetics Frisco TX
I love how you explain the importance of patience in dog training. It truly pays off in the long run! Find more helpful content at Dog Boarding Amarillo
Great insights! Discover more at Industrial Electrician Near Me
The personalized care at my local ##Puyallup Chiropractor## is unmatched! It’s like having a health partner Prenatal Chiropractor
This was quite informative. For more, visit Cannibis Store Near Me
Excellent dialogue on the function of bushes in urban environments—very eye-beginning data the following! Check out what else is available at Land clearing Seabrook
Your post made me rethink my approach to Google Maps ranking completely! I’m implementing these changes now and tracking progress via my site: Search Engine Optimization
If you doubt about where to transform during legal troubles, consider reaching out via sources like those located at minnesota law firm
This was highly informative. Check out Ophthalmologist for more
I recently completed a Bellevue bathroom remodel, and I couldn’t be happier with the results! The transformation was incredible, and it has made such a difference in my daily routine Mercer Island Home Remodel
Excited approximately seeing what new choices will come next season acrossFriscolocalmedspascene—it retains getting more suitable each time!! Clover Esthetics
Nicely detailed. Discover more at Industrial Electrician Near Me
The thoughts the following are forged! I in my view love the services and products from Go to this website
Appreciate the thorough insights. For more, visit prk corrective surgery
I can’t emphasize enough just how helpful it is to have a knowledgeable lawyer in your corner during lawful fights– find options at minnesota law firm
I found this very helpful. For additional info, visit Cannibis Store Near Me
I can’t believe how well my dog was treated during his stay at a local boarding facility in Amarillo! Highly recommend checking out Dog Training Near Me
Thanks for the insightful write-up. More like this at lasik surgery near me
Nicely done! Discover more at Gainesville Painting Company
Amazing how directly things change inside of good looks developments yet thankful we constantly have authentic resources resembling these fantasticMedSpasinfriscolocal discipline!!! med spa near me Clover Esthetics Frisco TX
Your post made me rethink my approach to Google Maps ranking completely! I’m implementing these changes now and tracking progress via my site: Website SEO
It’s important to consult multiple lawyers before making a decision – collect understandings on this procedure via # # anyKey word ### criminal defense attorney
Thanks for the useful suggestions. Discover more at Industrial Electrician Near Me
Your instruction on seasonal pruning became enlightening—thank you for putting this jointly! Explore more at Land clearing Santa Fe
This was quite enlightening. Check out Cannibis Store Near Me for more
This web publication put up made me underst Med Spa Frisco TX
Thank you for shedding light on the role of a family support lawyer in child support cases. It’s comforting to know there are professionals who can help
This is very insightful. Check out cake shop near me for more
Thanks for the practical tips. More at dr thakur dental clinic
The holistic approach of my ##Puyallup Chiropractor## has really helped with my stress levels South Hill Chiropractor
Very informative article. For similar content, visit peacock salon unisex salon
Valuable information! Discover more at aura old age home near me
Valuable information! Find more at hotels
A huge shoutout to everyone at DTTM for making my recent tow as smooth as possible Dallas Towing Top Master Phone Number
This was very enlightening. More at bars near me
Everyone sincerely must take virtue at the same time they nevertheless can due to the fact possibilities like these received’t remaining ceaselessly—they’re well worth investing into ourselves on every occasion that you can think of!!!! med spa near me Clover Esthetics Frisco TX
This was highly educational. For more, visit staycation near mumbai for couples with private pool
Fantastic short article! Finding an experienced criminal defense attorney in Minneapolis is crucial to a successful protection. Check out criminal defense lawyer for tips
Thanks for the thorough analysis. Find more at desire salon hair color near me
I love how Bellevue is embracing smart home technology for renovations! It’s amazing to see how these innovations not only enhance the comfort and convenience of our living spaces but also improve energy efficiency Mercer Island Home Remodel
Thanks for the great tips. Discover more at rle portland
Anyone looking for an excellent New Brighton dentist should definitely check out what’s available at Mckenzie towne dentist
I recently went through a custody battle and found that understanding family law was crucial. I’m thankful for the support I received. For anyone needing help, visit divorce lawyers OC
Learning about all offered services was enlightening – I’m sure I’ll useD TTMT again soon if needed Dallas Towing Top Master 4697304250
I’m interested in learning more about cannabis-infused topicals for pain relief broccoli cannabis weed dispensary los angeles, venice boulevard, los angeles, ca
I was shocked by the storm damage in Pittsboro; it will take time to rebuild. For anyone looking for support or guidance, I recommend checking out Storm damage cleanup Pinehurst NC for valuable resources
Make informed decisions regarding your representation by making use of sources readily available through websites like minnesota law
I’m so glad I found Fire damage repair Pinehurst NC when dealing with water damage issues in my Pinehurst house
Wonderful tips! Discover more at laminate flooring installer
I love how you emphasize creativity in the curriculum of a Day Care Centre. It’s vital for kids’ growth! More creative ideas can be found at infant daycare near me
Is there any follow-up care needed after a CoolSculpting treatment at coolsculpting services
I love how you explained the importance of duct cleaning for HVAC efficiency. It’s something I often overlook! More insights can be found at AC emergency service
This was highly useful. For more, visit Douglasdale dentist
I’ll always choose DTTM moving forward – their professionalism exceeded all Tow Truck Dallas Towing Top Master
Navigating allegations can be tough alone; enlist a certified criminal defense attorney from Minneapolis using criminal defense lawyer
This was very enlightening. For more, visit abogados laboralistas Sevilla
I appreciated this post. Check out pediatric dentist mumbai for more
Thanks for the valuable insights. More at bakery hinjewadi
I learned a lot about roof inspections from your post! Hiring a knowledgeable contractor is key Roof repair
Did you know that even small leaks can lead to significant water damage over time? Pittsboro homeowners should keep an eye on their plumbing! For more insights, check out Mold remediation Pinehurst NC
I wish I had found Storm damage cleanup Pinehurst NC sooner! Their insights on water damage repair in Pinehurst saved me time and money during my recent crisis
I always choose Dallas Towing Top Master for my towing needs in Dallas Dallas Towing Top Master 336 S Jim Miller Rd #2134 Dallas TX 75217
Thanks for the informative content. More at aura old age home thane
I love your suggestions for creating themed learning weeks at daycare—it keeps things exciting preschool
This was nicely structured. Discover more at sakha niwas agro tourism
Thanks for the clear advice. More at villas in mumbai with private pool
Can’t believe how beautiful bamboo hardwood floors can look! Thanks to Woodfloor Masters Inc for providing such great options here in Vancouver WA! Explore their collection at Hardwood Vents Vancouver WA
The holistic approach of my ##Puyallup Chiropractor## has really helped with my stress levels Prenatal Chiropractor
The advice on handling roof leaks changed into tremendously worthy—I’ve dealt with that subject beforehand! Visit roofer for solutions to primary concerns
Đưa ra nhận xét chân thật nhất có thể về những gì đã trải qua tại Rick Vip sẽ rất thú vị !## rikv ip Rikvip
Great job once again Dallas Towing Top Master Contact Number
Useful advice! For more, visit SE Calgary dentist
I agree that having an excellent defense attorney can change your situation substantially. Minneapolis citizens need to most definitely explore their choices at criminal defense lawyer
Awesome article! Discover more at evo icl portland
Cleanliness incredibly contributes to manufacturer acceptance; agencies must always prioritize janitorial prone to that end! cleaners Penticton Foster Janitorial – Commercial Cleaning Company
I’m a organization believer in the persistent of cleanliness! For entire janitorial functions, visit commercial cleaners Foster Janitorial – Commercial Cleaning Company Kamloops lately
Nicely detailed. Discover more at commercial flooring installer
Your article perfectly captures the essence of curiosity-driven learning in daycare environments! Letting kids explore is key to their discovery process daycare near me
I just made over my home and determined the proper hardwood at flooring store winnipeg Curtis Carpets
I recently dealt with water damage in my Pinehurst home, and it was a nightmare! Thankfully, I found great resources at Fire damage repair Pinehurst NC that helped me through the cleanup process
If you’re looking for a reliable roofing contractor Roof repair
I’ve never encountered such professionalism as I did with DTTM; they made everything so Dallas Towing Top Master Reviews
Dealing with fees? Don’t stress– connect for quality legal help currently! Start with details from attorney minneapolis criminal
Anyone looking for a new Brighton dentist should definitely check out Mckenzie towne dentist ! They are amazing with kids
Just spent hours discovering water-resistant plank recommendations on the grounds that they appear most suitable given our climate right here in NY—kudos back in opposition to discovering important tips by using flooring store Buffalo NY Tontine Carpet One
Loved your recognition on DIY roof inspection ideas—extraordinary powerful for householders like me! Discover extra DIY details at roofing contractor Platinum Quality Roofing & Siding Flint Mi
The importance of socialization in early childhood can’t be overstated. A good Day Care Centre fosters that so well! More info at childcare near me
I love how you explained the importance of duct cleaning for HVAC efficiency. It’s something I often overlook! More insights can be found at HVAC repair near me
Very insightful strategies offered regarding developing community areas within online pages—they foster connection among clients tremendously!! # website design Kelowna Wildfire Web Design
Water damage can lead to mold growth if not addressed quickly. For those living in Pinehurst, check out the resources at Storm damage cleanup Pinehurst NC
Exactly how do you preserve a freshly reglazed tub? I want to keep it looking fresh! I discovered ideas at http://www.xn--c1aid4a5e.xn--p1ai/user/maevyniwrq
Don’t let stubborn fat ruin your confidence; let CoolSculpting restore it! Visit coolsculpting services for inspiring transformations that will empower you to love your body
В этом блоге всегда такие интересные темы! Рекомендую ознакомиться с предложениями на узнать больше информации
I always thought my roof was fine until the inspection revealed hidden issues Roofing Educators
Nothing feels better than knowing there’s a reliable option likeD TTMT available when things go wrong Dallas Towing Top Master Reviews
This was highly educational. For more, visit dentist for kids near me
What’s your favorite part about getting treated with CoolSculpting at coolsculpting treatment
Nicely detailed. Discover more at Calgary dentist
Appreciate the comprehensive advice. For more, visit bakery hinjewadi
This submit highlights the advantages of business cleaning flawlessly! For extra help, don’t omit to examine out commercial cleaning companies Foster Janitorial – Commercial Cleaning Company Penticton
Huge thanks to the team at YUFixit for getting my phone back in working order so quickly! Amazing service! iPad Repair
Thank you for highlighting the importance of early childhood education in Day Care Centres! It sets the foundation for lifelong learning. For further reading, check out infant daycare near me
Appreciate the insightful article. Find more at peacock salon hair salon vashi
I can’t say enough about how professional Dallas Towing Top Master 4697304250
Thanks for the thorough analysis. More info at abogado laboralista Sevilla
“Can we talk about the importance of supporting local growers dispensary
Very helpful read. For similar content, visit aura old age home near me
I enjoyed this post. For additional info, visit staycation near mumbai
La devoción hacia la Santa Muerte ha crecido en los últimos años oracion de la santa muerte
Appreciate the helpful advice. For more, visit tapola hill station
This was a great article. Check out hair styling near me for more
I just lately switched to a server condominium provider from Server Rental Business Delhi , and the efficiency has been perfect
Chiến lược nào là tối ưu nhất khi tham gia vào trò chơi bài Rik vip? Cùng chia sẻ nhé! ##Rik vip Rikvip
I won’t forget how smoothly everything went while working alongsideD TTMT; truly commendable effort from start-to-finish Dallas Towing Top Master Phone
If you’re in Buffalo and in the hunt for flooring information flooring buffalo NY
The magnitude of gutter upkeep when it comes to roofing is most of the time forgotten! Thanks for highlighting it. For added studying, fee out roofer Platinum Quality Roofing & Siding flint Mi
This was highly educational. For more, visit New brighton dentist
The benefits of music childcare near me
Child support and custody arrangements are often complicated. Understanding your rights is key! Make sure to check out OC divorce attorneys for helpful tips
Local collaborations can boost visibility and sales! Explore strategies at marketing agency near me
So thankful we went ahead with having our old rusty-looking bath re-glazed instead of changing it completely– entirely worth every cent!! ### AnyKeyWord https://zai4atka.com/user/fotlanifhn
Well explained. Discover more at mortgage financing
Thanks for the helpful article. More like this at residential mortgages
Clearly presented. Discover more at mortgage lender Murfreesboro
Does any person have thoughts for med spas in Frisco? I’ve heard enormous matters approximately a few! Clover Esthetics Frisco Tx
Cảm ơn Go88 đã tạo ra một sân chơi thú vị cho tất cả mọi người! go88
“I’ve been looking around the world for tiles flooring in winnipeg Curtis Carpets
This was nicely structured. Discover more at Douglasdale dentist
The variety of accident cases that Moseley Collins Law handles shows their commitment to helping the community Sacramento motorcycle accident lawyers
Thanks for the detailed guidance. More at Take a look at the site here
Kudos again on making such valuable information accessible to everyone via Moseley Collins Law Los Angeles hospital malpractice lawyer
A detailed understanding of pedestrian rights after accidents is essential; thank you, Moseley Collins Law accident attorneys near me
Love these referrals! Are there particular electric work that should constantly be delegated experts? fort collins electrical contractor
Outst atlanta electrician
This is one of the very best short articles I have actually encountered concerning hiring electrical experts; thanks very much indeed for sharing it with all of us here today! Can you detail what makes up a solid quote from an electrician vs find an electrician
It’s shocking how many medical malpractice cases occur in Los Angeles Moseley Collins Law Los Angeles hospital malpractice lawyer
This blog post uses so much quality on employing methods– thank you significantly! Can you discuss how various kinds of electrical work might affect my choice of specialist? licensed electrician
Such useful recommendations! I really did not realize that a written contract was so essential in this industry residential electrician
Many thanks for the recommendations! Asking for referrals is a have to when employing electrical experts las vegas electricians
Really interesting write-up! What’s your take on DIY electrical work versus working with an expert? residential electricians
Terrific pointers general! Just how can one stay upgraded with local electricians electrician katy
Thanks for the thorough article. Find more at FHA Loans
Remarkable understandings shared throughout this entire blog item– it’s exceptionally useful local electricians
Remarkable recommendations! Exactly how do I guarantee that I’m getting a reasonable estimate from an electrical contractor? electrician
This is a practical overview! I never ever thought of checking for insurance prior to working with an electrical contractor electrical contractors near me
Local expertise is key when choosing a ##mortgage lender##. I highly recommend finding one familiar with your area local mortgage lender
Excellent post! What are some red flags I should look out for in an electrician? electrical contractors
Many thanks for sharing this important web content! Individual referrals are certainly the best method to go electricians lakeland
Thanks for the practical tips. More at kids dentist near me
Have you heard about the sustainability part of nitrous oxide cream chargers? They’re a remarkable alternative for eco-unsleeping chefs! Read greater at https://lexsrv3.nlm.nih.gov/fdse/search/search.pl?match=0&realm=all&terms=http://www.heatherseats@raovat5s.biz/redirect/?url=https://www.bookmarkingvictor.win/whether-you-re-a-professional-chef-or-a-homestead-prepare-dinner
Such terrific suggestions on discovering credible electricians! Exist any type of online sources or directory sites you ‘d recommend? bradenton electricians
Awesome post electrical installation service
Great job! Find more at popular residential laminate designs
I agree with investing in fantastic cleaning team of workers will escalate our work setting commercial cleaners Foster Janitorial – Commercial Cleaning Company Kamloops
I appreciate how my health insurance agent takes the time to explain every detail of my plan! Get similar help at Health insurance agent
Do you prefer nigiri or maki rolls? It’s such a tough choice! Sushi
Valuable information! Discover more at abogados laborales Sevilla
Appreciate the thorough information. For more, visit highlights near me
Your guidance on gym etiquette are spot on! Thanks for losing mild in this subject matter. Share within the neighborhood at crossfit jacksonville
I found this very interesting. For more, visit aura old age home
This submit genuinely sparked a few motivation to fresh! Check out this monstrous link I came upon to retain the momentum going: carpet cleaning fredericksburg
Your article on the social implications of cannabis legalization is notion-scary! I chanced on a cool link that explores these strategies greater: weed dispensary
Your counsel on choosing a tow truck institution were very fabulous! I came throughout a cool link with opinions of varied features as properly towing company
Bạn có thấy rằng việc áp dụng các chiến lược thông minh sẽ mang lại kết quả tốt hơn không ?## rikv ip Rikvip
This was quite informative. For more, visit villa
Awesome article! Discover more at hotels in mahabaleshwar
A thorough examination with a proficient CA mishap legal representative opened my eyes to what I might anticipate progressing after my event! trip and fall lawyer
Thanks for the helpful article. More like this at Residential Architect
Can any individual share their experiences with carpet floors in Buffalo? I discovered a few very good data on flooring buffalo NY
Great read on VA loans—excited to see how I can benefit from them through contact with ### any mortgage refinancing
Appreciate the thorough write-up. Find more at affordable laminate flooring installation
Thanks for the insightful write-up. More like this at VA Loans
Great insights on Plumber near Mandurah ! It’s imperative to have safe plumbing products and services, specially in emergencies
Extremely useful tips! It’s fascinating the amount of people neglect licenses when employing electrical experts atlanta electricians
“How do you approach trying new strains without feeling overwhelmed? I’d appreciate advice as I explore options at joyleaf recreational weed dispensary roselle, east 1st avenue, roselle, nj
This put up used to be high-quality constructive in knowledge dispensary laws! I came across a funky link that elaborates additional: weed dispensary
Your hints on seasonal carpet care were spot-on and extremely efficient! I determined a groovy link with added seasonal cleansing checklists too carpet cleaning company
Thanks for sharing your suggestions on responsible cannabis use! I determined a full-size link that emphasizes this awesome subject matter: weed store
Your article on opting for the good tow truck employer is extraordinarily priceless! I chanced on a groovy link that adds even greater worth to your factors towing service
If you’re looking for a reliable health insurance agent, Greg Wolff is highly recommended! See Health insurance agent for details
This was highly educational. More at Residential Architect
I love how sushi can be both casual and fine dining! It fits any occasion. Explore different sushi experiences at Sushi
Local businesses like dumpster company are essential for our community—great service every
Helpful suggestions! For more, visit best scratch-resistant laminate Atlanta
Does anyone have experiences with local IT support services? I’d love to hear about Local IT Support
Appreciate the comprehensive advice. For more, visit mortgage financing
Appreciate the helpful advice. For more, visit USDA Loans
I appreciated this article. For more, visit Residential Architect
Clearly presented. Discover more at dental clinic
Thanks, Plumber near Mandurah
The advantages of planning for home additions are endless! From maximizing space to increasing property value, it’s definitely worth the effort New home construction
Hey there folks,
SEO and digital marketing are absolutely crucial in today’s highly competitive business landscape.
As a Chicago local, I’ve witnessed how regional searech optimization significantly enhance online visibility—especially for niche
industries. Nfinitelimits, a results-driven agency in the Mundelein area,
truly stands out with customized solutions.
Their focus in technical seo analyst (https://peacefulmind.co.kr/bbs/board.php?bo_table=free&wr_id=1186919) and content marketing enables businewsses
to excel in local markets. Take their work|Consider their successful campaigns:
they improve Google Business Profiles and leverage cutting-edge software to outsmart SEO trends.
Paired with strategic integration, they craft comprehensive strategies.
For businesses aiming tto enhance your online visibility, this agencyy delivers
measurable results. The agency’s tailored strategies fuel long-term
growth, not just short-term solutions.
Thanks for the valuable article. More at Residential Architect
Extremely informative read commercial electrician
Kudos to you for highlighting such an crucial detail of entrepreneurship wherein funds almost always pose dem Hop over to this website
I value your referrals! It’s so crucial to hire a person with great evaluations residential electricians
Appreciate the detailed post. Find more at labor costs for laminate flooring
I value your referrals! It’s so crucial to work with a person with great evaluations electrical contractors near me
Great insights on carpet preservation! I observed a funky hyperlink that dives deeper into cleansing techniques carpet cleaners
Thank you for sharing such insightful information about hashish cultivation! I found out a groovy hyperlink that enhances your concepts: weed store
Ciekawy materiał ! Na pewno zainteresuje wielu przedsiębiorców ! Zachęcam do zapoznania się z ofertą #aniKeyWord#! biuro rachunkowe
To ważne, aby być świadomym obecnych ustawach podatkowych i zyskach podatkowych.
Wielu konsumentów pomija możliwe zwroty podatkowe przez to, że nie orientują się w potencjalnych oszczędnościach księgowość
If you’re hesitant about where to get your phone fixed HP Repair
69VN là nhà cái cá cược trực tuyến hàng đầu tại Việt Nam, mang đến trải nghiệm giải trí đẳng cấp với hơn 500 trò chơi đa dạng như cá cược thể thao, casino trực tuyến, bắn cá, nổ hũ và game bài. 69vnpro.net
Just got my health insurance sorted thanks to an amazing agent! Highly recommend checking out Health insurance agent near me for help
Thanks for the clear advice. More at home loans
From assessments to restorations, there’s so much involved in recovery; grateful for the guidance from experts at water damage cleanup near me
I’m always on the lookout for the best sushi spots in town! Any recommendations? Sushi
This article is an excellent resource for anyone who might find themselves in an accident situation accident lawyer
Valuable information! Find more at Architect
This was quite informative. For more, visit mortgage broker near me
After reading about all the types of cases h San Diego motorcycle accident lawyers
Amazing how much junk we accumulate—thankfully there’s # # anyKeyWord # # to help us dumpster rental
This blog provides a solid foundation for underst medical negligence attorney
Just had a roof inspection in Summerville, SC and it was the best decision I made! Highly recommend it for peace of mind Roofing Educators
Limos aren’t just for celebs any longer! They make every event really feel unique. Have you tried renting out one for a birthday or wedding anniversary? Look into even more concerning it at Navigator limousine San Francisco
Glad to see that patients have advocates like those at Moseley Collins Law fighting for justice against medical negligence in Phoenix birth injury lawyer near me
Love these suggestions! Are there details electric jobs that should always be left to experts? electrical contractors near me
This was highly useful. For more, visit abogado laboralista Sevilla
This was very enlightening. More at Architect
Can everyone put forward properly advertisement plumbing functions? I discovered hot water systems mandurah in the time of my search
Amazing insights into ways to live prompted throughout the time of dem crossfit jacksonville
Thanks for the insightful submit on the reward of hashish! I chanced on a cool link that dives deeper into dispensary thoughts: weed dispensary
This was nicely structured. Discover more at USDA Loans
I enjoyed this post. For additional info, visit abogado Vigo
This was very well put together. Discover more at peacock salon hair salon vashi
Również polecam współpracę z profesjonalnym biurem księgowym – moje doświadczenia z # biuro rachunkowe # są bardzo
I learned so much about deductibles Health insurance agent
Really insightful details! Are there certain qualifications that suggest an electrical contractor is particularly knowledgeable? commercial electrician
Thanks for the informative post. More at mortgage broker
Appreciate the detailed information. For more, visit commercial mortgages
I love experimenting with different toppings on my sushi rolls—what’s your favorite combo? Check out more creative ideas on Sushi
Appreciate the helpful advice. For more, visit Architect
Thanks for the great content. More at Architect
Thanks, hot water systems mandurah
Roofing issues can arise unexpectedly; stay prepared roof replacement littleton
Taking notes from earlier experiences shared lets in destiny traffic making instructed decisions whenever wanting one thing exotic accomplished for the time of their own visits ahead too!! med spa near me Frisco Tx
Nothing beats having dependable support when needed most—thank goodness there’s still companies likeD TTMT around dallastowingtopmaster.com
Just had my torsion spring replaced by a local service—what a difference it makes! garage door service frisco tx
FDA does not evaluate nutritional supplements prior to they are offered to customers.
Also visit my website … https://git.ascarion.org/tasha523917920/6871948/wiki/Herbal+Capsules+Relief+for+Herpes+Outbreaks
Thanks for the comprehensive read. Find more at mortgage lender
Excellent recommendations overall! How can one stay upgraded with local electrical contractors find an electrician
Your insights on roofing maintenance are spot-on! I’ll be reaching out to Olympia Roofing Company soon Olympia Roofing Company
Your article has inspired me to finally visit a chiropractor in Tacoma! Looking forward to improving my health Chiropractor Tacoma
Great insights! Discover more at keratin hair treatment
Nicely detailed. Discover more at residential mortgages
The role of a health insurance agent is often underrated. If you’re confused about your options, consider reaching out to Health insurance agent near me
To prymarne, aby rozumieć najnowszych normach podatkowych i odliczeniach.
Wielu podatników nie korzysta z nieoczywiste korzyści podatkowe ponieważ nie rozumieją potencjalnych oszczędnościach księgowa
Ciekawe spostrzeżenia na temat znaczenia dobrej księgowości – warto zwrócić uwagę na ofertę od biuro rachunkowe
The sound of slicing through fish for sashimi is oddly satisfying—such precision required! Sushi
To prymarne, aby pozostawać poinformowanym bieżących zmianach podatkowych i korzyściach fiskalnych.
Wielu pracowników przeocza potencjalne zniżki gdyż nie znają potencjalnych oszczędnościach księgowość
Superb short article with actionable steps– thanks for placing this with each other! What should I do if I’m not satisfied with the job after it’s completed? roswell electricians
Thanks for this guide! Can you suggest techniques for discussing pricing with electricians? philadelphia electricians
My trip post-accident was challenging truck accident lawyer
Wonderful experience with DTTM – super friendly folks who know what they’re Dallas Towing Top Master (469) 730-4250
Whenever someone asks for towing recommendations in Dallas Towing Service Near Me Dallas Towing Top Master
Cùng nhau khám phá bí kíp ẩn chứa trong trò chơi bài Rik vip nào mọi người ơi! ##Rik vip Rikvip
This was very insightful. Check out Residential Architect for more
Thankful for these useful tips concerning discovering high quality electrical experts; absolutely saves time commercial electrician
Looking ahead to discussing residential plumbing treatments with the gurus at plumber mandurah
I recently visited a spa in Northloop Minneapolis, and it was an amazing experience! The atmosphere was so calming, and the staff were incredibly professional spa packages Minneapolis
After reading approximately plumbing inspections, I feel it’s time to call Plumber near Mandurah for mine
The affordability coupled with excellent makes **an unbeatable alternative in Pune dedicated GPU server rental
Wonderful post detailing common challenges faced during personal injury claims; it’s comforting knowing firms like yours exist in Los Angeles—thanks Los Angeles auto accident law firm
Appreciate the useful tips. For more, visit abogado laboralista Sevilla
Your post is super helpful for homeowners looking into roofing options! I’m excited to learn more from Olympia Roofing Company! Olympia Roofing Company
The advice about documenting everything after an accident was spot-on! This is critical advice about Salt Lake Injury Law that everyone should heed! Salt Lake Injury Law
As someone who struggles with back pain, I appreciate the tips on finding a good Tacoma chiropractor Chiropractor Tacoma
What type of prep job might secure surroundings throughout redecorating jobs successfully without causing damages or messiness later?: *** ### yourlink ### *** http://medicina38.ru/user/brittarlhl
This was quite informative. For more, visit commercial mortgages
Essential press releases are Influencing media Messages.
They Help Establish Links between Companies and Media
Professionals. Writing Effective press releases Mean being Focused, Aligned with the Interests of Chosen Media Outlets.
In Today’s Digital Age, Illinois Press, https://Www.How2Youtube.Com/,
releases Further Setve Important role in Digital Public Relations.
They Target Conventional news outlts Furthermore Increase Engagement and Elevate
a Business’s Internet Visibility. Incorporating Videos, such as Photos, can Render press rekeases More
Engaging and Viral. Modifying to the Developing
media Field while Preswerving core Standards can Substantially Enhance a pess release’s Influence.
What Are Your Thoughts on Using multimedia iin News Releases?
I’m glad there are professionals like those at Moseley Collins Law who specialize in these complex cases in Phoenix lawyers that sue doctors
Love that there are gluten-free options for sushi lovers now! Have you tried any? Get recommendations on Sushi
After my automobile crash, my CA accident legal representative ensured I got the compensation I was worthy of truck accident attorney
Thanks for sharing these insights; they’re fairly valuable! What’s the very best method to manage disputes with employed electricians? electrical installation service
Thanks for the useful suggestions. Discover more at Architect
Thanks for the informative post. More at abogados Vigo
I’ve seen some incredible roofs around Littleton lately! For contractor info, visit roof replacement near me
Wonderful tips! Find more at mortgage broker
Limousines are terrific for business occasions too! Impress your clients with a luxurious adventure. Explore the advantages of limos for service at Limousine chauffeur San Francisco
Thanks for the valuable insights. More at Residential Architect
Thank you for these underst residential electrician
I’ve heard great things about Tacoma chiropractors and their ability to relieve pain Chiropractor Tacoma
As someone who’s been through a personal injury case, I can attest to the importance of understanding local laws like those in Salt Lake Injury Law Salt Lake Injury Law
Thanks for the useful suggestions. Discover more at mortgage broker near me
Custom designs give homeowners the opportunity to choose sustainable materials and energy-efficient solutions Dream Homes in East Brunswick
Hãy nhanh tay đăng ký để tham gia vào những sự kiện đặc biệt mà rik vip mang đến rikvip
The importance of a good health insurance agent cannot be overstated! Visit Health insurance agent for reliable services
Really fully grasp this advisor on deciding on the true plumber for decent water concerns in Perth! More suggestions would be discovered at Hot Water System Plumber near Me
This was quite helpful. For more, visit Residential Architect
Did you know that sushi originated as a way to preserve fish? So interesting! Learn more about its origins at Sushi
Hill Country Flooring & Construction really knows their stuff when it comes to flooring trends! wood flooring near me
Appreciate your efforts in putting together such crucial advice on working with qualified electrical experts; it’s absolutely appreciated by numerous electricians near me
Nicely done! Discover more at Knoxville mortgage lender
Shoutout to YUFixit for offering same-day repairs; it’s such a lifesaver when you’re in a pinch! Beats Repair
Every time I’m in Miami, I make it a point to try a new restaurant. The food scene is always evolving! For my compiled list of the best spots, check out best restaurants
Thanks for the useful suggestions. Discover more at Industrial Electrician Near Me
This was a great help. Check out movers san diego to los angeles for more
Appreciate the thorough insights. For more, visit Cannibis Store Near Me
For anyone needing effective tow services Towing Dallas Towing Top Mastere
This was highly helpful. For more, visit laser eye surgery
Antipublic.net – The best database for data leaks
Top1 in data: With over 20 billion collected passwords
Top1 in search speed: Allows easy and super fast search of any user or domain.
Free:
– Check if any personal account has ever been leaked
– Check if any company, domain has ever been leaked and the scale of the leak (by the number of accounts)
Moreover:
– Can view all passwords in the database at low cost
– Can view passwords in milions of accounts: Netflix, Spottify, Math, Onlyfan, Pornhub, … including Google, Facebook and countless other websites.
Great information on making certain safety initially when working with an electrical contractor– most definitely critical advice! Do you have underst electrical contractors
Hay una energía especial cuando se habla de la Santa Muerte; parece que todos tienen algo que compartir sobre ella santa muerte en invocación
The plumbing technicians at plumber near me seem to be proficient and secure; I’ll attain out quickly
Great post! I’ve been looking for reliable roofers, and Olympia Roofing Company seems like a fantastic option Olympia Roofing Company
The benefits of regular chiropractic care are impressive! I’ll be looking into local Tacoma chiropractors this week Chiropractor Tacoma
What should I do if I’m injured in an accident? This article on Salt Lake Injury Law has some helpful tips! Salt Lake Injury Law
After this long week, I think it’s time for me to book some pampering at a nearby Dermaplaning facial
I enjoyed this post. For additional info, visit Residential Architect
I realize the data on the best way to entry loose server rentals in India Go to this website
This article really highlights why we should utilize health insurance agents like those at %%ANYKEYWORD%%—great Health insurance agent
Just completed our first renovation using materials from Hill Country Flooring & Construction—the results are stunning hardwood flooring stores near me
This post will surely help many people understand their rights injury lawyer
Sushi is perfect for sharing Sushi near me
I’m thankful for resources like this one; they empower individuals searching for legal assistance after accidents—great work Moseley Collins Law Los Angeles accident lawyers
The staff at Southland Farms are incredibly knowledgeable and helped me find the perfect strain for my needs michigan dispensary
Such a comprehensive checklist of tips! Have you found particular systems much better for discovering licensed electrical contractors? residential electricians
Great info on making certain safety initially when employing an electrical expert– most definitely vital advice! Do you have underst best electrician near me
This blog provides a solid foundation for underst lawyers that sue doctors
The atmosphere inside KANNA Weed Dispensary is so chill dispensary oakland
Great advice on navigating difficult conversations with healthcare providers shared by # # any Keyword # #—thank Moseley Collins Law lawyer that sue doctors near Los Angeles, CA
What flavors do you all endorse wanting with cream chargers? I’m searching out thoughts from Nangs
Such valuable information on the role of chiropractic care in overall wellness! Definitely seeking out a Tacoma chiropractor now! Tacoma Chiropractor
Wow Olympia Roofing Company
Thanks for the detailed guidance. More at Architect
I recently learned about the importance of having a good attorney for personal injury cases Injury attorney
It’s interesting to see how multifunctional spaces are becoming a necessity in new construction. With more people working from home, designing versatile rooms is key. Explore creative solutions for home offices and more at Home Construction in East Brunswick
Well explained. Discover more at Set-N-Stone Tile And Flooring
Appreciate the detailed insights. For more, visit tax preparation
Appreciate the comprehensive advice. For more, visit abogado Vigo
Great information below! On the internet reviews can be so revealing regarding an electrical expert’s work values and top quality local electrician
Appreciate the clearness in your creating! It actually assists debunk the hiring process for electricians electricians round rock
This was a great article. Check out hardwood flooring near me for more
Thanks for the suggestions! Requesting for references is a need to when working with electricians charlotte electrical contractors
Excellent post! What are some red flags I should watch out for in an electrical contractor? dayton electrical contractors
Health insurance agents can provide insights that save you money in the long run—explore options at Health insurance agent near me
I love that there are so many vegetarian options for sushi now; it’s great for everyone! Sushi near me
Bạn sẽ không bao giờ biết trước được điều gì đang chờ đón cho đến khi tham gia vào trò chơi rikvip
Anyone else loving the ease of ordering from chef catering services like # # anyKeyword#? Such a time-saver! meal delivery service
I found this very helpful. For additional info, visit buy engineered wood flooring
Anyone else keen about self-care days at their nearby med spa? Frisco has a few mammoth preferences! Med Spa Frisco TX
The first impact things! A visually pleasing web content can continue workable purchasers interested. Learn greater with Website Design Bangalore
So impressed with the service from Dallas Towing Top Master last night – quick response Dependable tow truck services Dallas
I found this very helpful. For additional info, visit commercial mortgages
The information about spinal health is so important! I’m eager to explore options with a Tacoma chiropractor Chiropractor Tacoma
Locked out during odd hours? No worries Highly recommended locksmith in Port St Lucie
Great reminder that sometimes we can solve our own problems without needing professionals every time!!! ## anyKeywords# roof repairs cork
Koru Sigorta
Sarkmış ve şişmiş göz kapakları tüm yüzün yaşlı, hüzünlü ve yorgun gözükmesine neden olur
UID_74743238###
Ini dia! 🎉🎉 ASN BKN Ubah Pola Kerja yang baru dan efisien! 🎉🎉.
UID_83344528###
Inilah 🎉🎉 Pupuk Inovatif Kebun Riset Kujang yang bikin Wamen BUMN bangga! 💪🏻🇮🇩
UID_21891068###
Takjub 😮 dengan fenomena serbu gas? Yuk, baca Warung Tatang Diserbu Warga dan temukan faktanya! 🕵️♀️👀
UID_25978847###
situs terbaik hanya di slot gacor agentotoplay
UID_25978847###
situs terbaik hanya di slot gacor agentotoplay
Nicely put. Regards!
my web blog … https://ee.frompo.com/profile/sladkiyboy88
UID_95859078###
Baru-baru ini, para pemain Mahjong Wins 3 dikejutkan dengan bocoran RTP yang diklaim bisa meningkatkan peluang kemenangan secara signifikan. Banyak yang percaya bahwa informasi ini membantu mereka mendapatkan hasil yang lebih konsisten dalam permainan. Jika Anda ingin tahu lebih lanjut, cek bocoran RTP Mahjong Wins 3 hari ini dan lihat apakah strategi ini benar-benar efektif.
UID_57331425###
Skandal terbaru mengguncang komunitas pecinta game slot setelah seorang admin terkenal, Rachel, dikabarkan tertangkap membocorkan pola kemenangan Gate of Olympus. Banyak yang bertanya-tanya apakah informasi ini benar-benar akurat atau hanya sekadar rumor yang beredar di kalangan pemain. Simak lebih lanjut detailnya dalam artikel admin Rachel tertangkap bocorkan pola Gate of Olympus.
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
Андрей Гаврилович Дубровский и Кирила Петрович Троекуров? история дружбы и вражды https://e-pochemuchka.ru/andrej-gavrilovich-dubrovskij-i-kirill-petrovich-troekurov-istoriya-druzhby-i-vrazhdy-smert-otcza-i-zhazhda-mesti-v-romane-a-s-pushkina-dubrovskij/
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
UID_87427935###
Cek yuk! 🚍👮♂️Operasi Keselamatan 2025 Polres Ciamis Siapa tahu bus favoritmu jadi sasaran! 😱👍
UID_18563832###
Ini yang di ganti >>> Yuk, ketahui lebih lanjut tentang Syarat Gabung OECD dan Pentingnya Ratifikasi Konvensi Antisuap di sini! 🕵️♀️🔎📚.
мтс подключить новосибирск
https://www.ahrs.al/punesimi/kwintech3358/
мтс тв новосибирск
мтс телевидение
https://hrc.cetracgh.org/employer/unifze2845/
мтс подключить новосибирск
UID_83003169###
Kenalan yuk! 🤝 Dengan guru inspiratif ini, Guru Dede Sulaeman yang mengajarkan cara merapikan pakaian di kelasnya. 👕👚🎓
emeğinize sağlık
Ankara implant tedavisi, kaybedilen dişlerin yerine, çene kemiğine yerleştirilen titanyum vidalar aracılığıyla yapılan bir diş tedavi yöntemidir.
UID_97211224###
Yuk, sehat bersama! 👨⚕️👩⚕️ Cek kondisi tubuh kamu di Program Cek Kesehatan Gratis sekarang juga! 💉🌡️ Selalu jaga kesehatan, ya! 🏥💖
провайдер мтс
https://pompeo.com/employer/inetrnet-domashnij-ekb-3/
мтс интернет
UID_12835053###
test aje nieeeeee
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
UID_42868144###
wadidawwwwwwwwwwww
UID_57599291###
wasiaaaappppp
мтс тв
https://karis.id/employer/inetrnet-domashnij-ekb/
мтс подключить екатеринбург
UID_29225695###
Waspada! Baca artikel Pengemis Kediri Raup Rp 40 Juta sebelum Anda memberi donasi! 🚨👀💸
UID_61411251###
Rasakan sensasi bermain slot gacor Agentotoplay dengan RTP tinggi dan peluang jackpot besar! 🎰🔥
UID_49830205###
Situs terpercaya Agentotoplay siap memberikan pengalaman slot online terbaik dengan kemenangan maksimal! 💰
UID_49830205###
Situs terpercaya Agentotoplay siap memberikan pengalaman slot online terbaik dengan kemenangan maksimal! 💰
UID_11426154###
Bergabunglah dengan agen Toto Play untuk menikmati permainan taruhan online paling seru dan menguntungkan! 🎯
UID_21023438###
Cerita inspiratif! Yuk, simak kisah Sudjat, Penjelajah Jipang yang tetap semangat menjajakan dagangannya di usia 72 tahun. 🙌🌟🚀
UID_32712501###
Wow! 😲 Ternyata Golkar Dukung Prabowo Maju Pilpres 2029 lho! 🎉 Bagaimana pendapat kalian? 🤔💭
UID_32712501###
Wow! 😲 Ternyata Golkar Dukung Prabowo Maju Pilpres 2029 lho! 🎉 Bagaimana pendapat kalian? 🤔💭
UID_24618462###
Penasaran dengan efisiensi anggaran? Cek artikel Beasiswa dan KIP Kuliah ini! 📚💡
UID_58463375###
Jangan lewatkan! 📣📣📣 Rizki dan Pengalaman Memanfaatkan Cek Kesehatan Gratis Bayar? Pikir dua kali! 😮💸💸💸.
UID_58463375###
Jangan lewatkan! 📣📣📣 Rizki dan Pengalaman Memanfaatkan Cek Kesehatan Gratis Bayar? Pikir dua kali! 😮💸💸💸.
UID_16923687###
Mau nonton film terbaru? Cek lk21 sekarang!
UID_39035559###
Jangan ketinggalan film terbaru hanya di lk21.
UID_39035559###
Jangan ketinggalan film terbaru hanya di lk21.
UID_71621535###
Streaming film favoritmu gratis di lk21 tanpa ribet.
UID_45925742###
Update film terbaru setiap hari hanya di lk21.
UID_67563685###
Temukan koleksi film seru di lk21 dengan kualitas terbaik.
UID_57949577###
Agen Toto Play menghadirkan pengalaman bermain slot online dengan RTP tinggi dan bonus melimpah setiap hari! 🎰💰
There is definately a lot to find out about this subject. I like all the points you made
UID_67604011###
Menangkan jackpot besar bersama Agentotopay, situs terpercaya dengan permainan slot gacor dan layanan terbaik! 🔥🎯
UID_87472693###
Bergabunglah di Agen Toto Play sekarang dan nikmati berbagai promo menarik serta free spin setiap hari! 🎁🎰
UID_95439008###
Agentotoplay adalah pilihan utama untuk slot online dengan kemenangan mudah dan proses transaksi cepat! ⚡💵
UID_82375370###
Mainkan game favoritmu di Agen Toto Play dan raih kemenangan spektakuler dengan fitur slot gacor terbaik! 🎊🔥
UID_71804096###
Agen Toto Play menghadirkan slot online gacor dengan RTP tinggi dan peluang jackpot besar setiap hari! 🎰💰
UID_92063078###
Mainkan slot favoritmu di Agentotoplay dan nikmati kemenangan maksimal dengan fitur free spin melimpah! 🔥🎁
UID_92063078###
Mainkan slot favoritmu di Agentotoplay dan nikmati kemenangan maksimal dengan fitur free spin melimpah! 🔥🎁
UID_80701695###
Dengan Agen Toto Play, setiap putaran slot menjadi kesempatan emas untuk menang besar dan membawa pulang hadiah! 💎🎯
UID_38709295###
Jangan lewatkan promo eksklusif dari Agentotoplay, tempat terbaik untuk pengalaman slot online yang seru dan menguntungkan! 🎰💵
UID_40805327###
Agen Toto Play adalah solusi bagi pecinta slot yang mencari kemenangan mudah, cepat, dan pasti cair! ⚡💰
UID_78195082###
idlix punya banyak film seru untuk ditonton kapan saja.
UID_47368981###
Cari film terbaru? Cek idlix sekarang juga.
UID_99018999###
Pengen maraton film? Langsung ke idlix!
UID_34914078###
Koleksi film terupdate bisa kamu temukan di idlix.
UID_88654138###
Nonton film dengan subtitle Indonesia hanya di idlix.
UID_98520627###
Ada film baru? Cek langsung di layarkaca21.
мтс подключение екатеринбург
https://letsstartjob.com/employer/inetrnet-domashnij-ekb-3/
мтс домашний интернет екатеринбург
UID_42318366###
Nikmati berbagai film terbaik di layarkaca21 sekarang.
UID_42318366###
Nikmati berbagai film terbaik di layarkaca21 sekarang.
UID_51498345###
Streaming gratis dan mudah hanya di layarkaca21.
UID_86325828###
Temukan film favoritmu di layarkaca21 dengan resolusi terbaik.
UID_74575696###
Pilihan film lengkap bisa kamu tonton di layarkaca21.
UID_40963841###
Pengen streaming film terbaru? Langsung ke rebahin sekarang!
UID_14517542###
Nonton film tanpa batas di rebahin.
UID_14517542###
Nonton film tanpa batas di rebahin.
UID_83350326###
Streaming anti ribet hanya di rebahin gratis.
UID_83350326###
Streaming anti ribet hanya di rebahin gratis.
UID_44216097###
Ayo nikmati koleksi film keren di rebahin sekarang.
UID_20162494###
Maraton film lebih seru dengan rebahin.
UID_87212262###
Tonton film terbaru di indoxxi dengan subtitle Indonesia.
UID_31545307###
Cari film berkualitas? Kunjungi indoxxi sekarang.
UID_27011249###
Jangan sampai ketinggalan film terbaru di indoxxi.
UID_43757086###
Koleksi film terlengkap ada di indoxxi.
UID_98625669###
Download dan streaming film favorit hanya di indoxxi.
UID_98625669###
Download dan streaming film favorit hanya di indoxxi.
UID_90808003###
Nonton film seru dan gratis hanya di layar kaca 21.
UID_28890956###
Temukan film dengan kualitas terbaik di layar kaca 21.
UID_28890956###
Temukan film dengan kualitas terbaik di layar kaca 21.
UID_83731332###
Streaming film jadi lebih mudah dengan layar kaca 21.
UID_97407895###
Yuk, maraton film di layar kaca 21 sekarang!
UID_97407895###
Yuk, maraton film di layar kaca 21 sekarang!
UID_70329956###
Film terbaru selalu update di layar kaca 21.
UID_60201981###
Jangan lewatkan film terbaru di lk 21.
UID_47000771###
Streaming lebih seru di lk 21 tanpa buffering.
UID_47000771###
Streaming lebih seru di lk 21 tanpa buffering.
UID_23842789###
Nonton film gratis di lk 21 sekarang!
UID_32188467###
Temukan film favoritmu di lk 21.
UID_73315471###
Update film terbaru setiap hari hanya di lk 21.
UID_20515935###
Jelajahi film terbaik di dunia21 sekarang!
UID_88860628###
Streaming film favorit lebih mudah di dunia21.
UID_59843783###
Nonton film tanpa batas hanya di dunia21.
UID_31642382###
Update film setiap hari ada di dunia21.
UID_81707401###
Koleksi film lengkap bisa kamu akses di dunia21.
UID_14842634###
Nonton movie kapan saja dan di mana saja.
UID_14842634###
Nonton movie kapan saja dan di mana saja.
UID_19686787###
Streaming film terbaru dengan mudah di nonton movie.
UID_19686787###
Streaming film terbaru dengan mudah di nonton movie.
UID_37840870###
Temukan film terbaik hanya di nonton movie.
UID_47715216###
Film terbaru selalu update di nonton movie.
UID_41220821###
Pengen maraton film? Coba nonton movie sekarang!
UID_86666902###
Ini yang di ganti >>> Wah, kamu tau gak sih? 79 Desa di Jawa Barat jadi Sarang PSK Menurut Pj Gubernur loh! 🙀👀.
UID_86666902###
Ini yang di ganti >>> Wah, kamu tau gak sih? 79 Desa di Jawa Barat jadi Sarang PSK Menurut Pj Gubernur loh! 🙀👀.
UID_80343489###
Berita Heboh! 🚨👮♂️ Gadungan Polisi di Bogor Dibekuk dalam aksi penipuan! 😱💔
UID_55058959###
Inilah berita terbaru! 📢📢 Bareskrim Diminta Tetapkan Kades Kohod sebagai DPO! 💥💥 Apa tanggapanmu? 😮
UID_33318432###
Ini yang di ganti >>> 😱🚨 Kejadian Gila! Pria Hancurkan Fasilitas Taman di Malang! 🚧🏃♂️.
UID_71145013###
Ini dia! 📢🎉 Fenerbahce Dekati 16 Besar Liga Europa dengan kemenangan spektakuler! 🏆⚽️
UID_59443646###
Ingin tahu siapa pengganti Deschamps? 🤔 Cek Zidane sebagai kandidat ideal yang disebut-sebut oleh Deschamps! ⚽🔥
Ayaş Escort
мтс тв екатеринбург
https://nursingguru.in/employer/inetrnet-domashnij-ekb-2/
мтс интернет
UID_73229804###
yg kygini buat indexing mayan
мтс екатеринбург
https://ttemployment.com/employer/inetrnet-domashnij-ekb-2/
сайт мтс екатеринбург
мтс телевидение екатеринбург
https://gertsyhr.com/employer/inetrnet-domashnij-ekb/
мтс тарифы на интернет
In the ever-evolving landscape of digital entertainment, dino game emerges as a beacon of innovation and excitement. This cutting-edge platform offers an unparalleled gaming experience, blending a vast array of genres with a sleek, user-centric desig
TonicGreens has genuinely changed my wellness. I really feel more energetic and less prone to getting ill. The all-natural ingredients provide me peace of mind, understanding I’m not putting any kind of dangerous chemicals right into my body. It’s a wonderful item that I currently suggest to all my friends and household.
Also visit my homepage – http://grainfather.co.nz/employer/tonicgreens-ltd
UID_55314541###
Untuk pengalaman bermain terbaik, daftar sekarang di AGEN TOTO PLAY dan nikmati keseruannya!
UID_88107811###
Mau menang besar? Gabung segera di AGENTOTOPLAY dan raih jackpotnya!
UID_39657838###
Situs resmi SLOT THAILAND dengan winrate tertinggi ada di sini!
UID_38497970###
Jangan lewatkan kesempatan menang di AGEN TOTO PLAY, banyak promo menarik menanti!
мтс домашний интернет
https://www.ayurjobs.net/employer/inetrnet-domashnij-ekb-3/
мтс цены
мтс тв екатеринбург
https://firstcallhealth.com.au/employer/inetrnet-domashnij-ekb/
мтс тарифы на интернет
мегафон телевидение екатеринбург
https://ekb-domasnij-internet-2.ru
мегафон подключение
мегафон домашний интернет
https://ekb-domasnij-internet-3.ru
мегафон домашний интернет екатеринбург
UID_33865880###
lk21 adalah platform terbaik untuk nonton film terbaru dengan kualitas HD tanpa biaya langganan.
UID_21806663###
rebahin menawarkan berbagai film box office yang bisa diakses dengan mudah dan cepat.
UID_56449902###
Pecinta film klasik maupun modern bisa menemukan koleksi lengkap di layar kaca 21.
UID_31597615###
lk21 indonesia menyediakan film terbaru dengan subtitle Indonesia yang lengkap.
мегафон подключение
https://ekb-domasnij-internet.ru
мегафон подключить екатеринбург
билайн подключение
https://infodomashnij-internet-krasnodar-2.ru
билайн интернет краснодар
билайн интернет
https://infodomashnij-internet-krasnodar-3.ru
билайн подключение краснодар
I really like reading through a post that can make men and women think. Also, thank you for allowing me to comment!
билайн подключение краснодар
https://infodomashnij-internet-krasnodar.ru
билайн интернет краснодар
билайн интернет
https://plus-domashnij-internet-krasnodar-2.ru
билайн подключение
I was doubtful regarding trying an additional eye health supplement, however Sightcare surpassed my assumptions. Within a few weeks, I discovered a substantial decrease in eye stress and boosted clearness in my vision. The mix of crucial nutrients like vitamin A and omega-3 fats makes Sightcare stand apart from other products I’ve tried. It’s simple to take and fits seamlessly right into my daily regimen. If you’re seeking a trustworthy method to sustain your eye health and wellness, provide Sightcare a shot!
my site – https://Zapinacz.pl/@anastasia29777?page=about
сайт билайн краснодар
https://plus-domashnij-internet-krasnodar.ru
провайдер билайн
билайн подключить краснодар
https://plus-domashnij-internet-krasnodar-3.ru
билайн тв краснодар
Specialists generally recommend food as the very best resource for minerals and vitamins.
my web page https://Rapid.tube/@darlenevandive?page=about
билайн интернет
https://plus-domashnij-internet-krasnodar-2.ru
провайдер билайн
In enhancement, certain supplements can communicate with medications.
Visit my web blog :: https://git.Hmmr.ru/luannann227127
билайн подключить
https://plus-domashnij-internet-krasnodar.ru
билайн интернет
It’s remarkable for me to have a website, which is good in support of my experience. thanks admin
накрутка просмотров в Телеграм канал
Hiya very nice website!! Guy .. Beautiful .. Superb .. I will bookmark your site and take the feeds additionally? I am happy to seek out numerous useful info right here in the put up, we need work out more strategies in this regard, thank you for sharing. . . . . .
накрутка подписчиков ётуб быстро
Your article helped me a lot, is there any more related content? Thanks!
билайн домашний интернет
https://plus-domashnij-internet-krasnodar-3.ru
сайт билайн краснодар
What really stands out about Slice Master is the variety of challenges it offers. The early levels are simple and straightforward, allowing you to get comfortable with the slicing mechanics.
провайдер билайн
https://plus-domashnij-internet-krasnodar-2.ru
билайн краснодар
Trix – официальный сайт – сервис мгновенных игр
накрутка подписчиков на Ютуб канал бесплатно
накрутка подписчиков Ютуб дешево
I was doubtful concerning trying Keto Flow, but I’m so grateful I did. These gummies have helped me shed stubborn fat and maintain my power levels. The BHB ketones in Keto Flow are powerful and have actually made a visible distinction in my fat burning progress. I highly suggest Keto Flow to anybody wanting to enhance their keto diet regimen.
Look into my web blog – https://classified.Completemarts.com/profile/celsacramp067
билайн подключить краснодар
https://plus-domashnij-internet-krasnodar.ru
билайн телевидение краснодар
провайдер билайн
https://plus-domashnij-internet-krasnodar-3.ru
билайн краснодар
UID_50841476###
Mainkan slot online gacor di Agentotoplay dan nikmati peluang Maxwin terbaik!
UID_75011297###
Agentoto Play menghadirkan permainan slot online dengan tingkat kemenangan terbaik.
UID_29043012###
Dapatkan jackpot besar dengan bermain di Agen Toto Play, situs slot terpercaya.
UID_26079175###
Keberuntungan di Fortune Temple – Seorang tukang ojek tak menyangka bahwa hari biasa bisa berubah menjadi momen luar biasa setelah meraih jackpot 200 juta. Simak kisah inspiratifnya dalam Fortune Temple dan buktikan keberuntungan Anda!
UID_40385688###
Karyawan Pabrik Raih Jackpot 300 Juta – Siapa sangka, rutinitas harian seorang karyawan pabrik berubah drastis setelah memenangkan jackpot besar dari Mystic Fortune. Apakah Anda siap untuk mendapatkan keberuntungan serupa?
UID_74799473###
Keajaiban di Dragon’s Treasure – Seorang sopir truk mengalami kejutan besar setelah mendapatkan jackpot fantastis senilai 250 juta. Ingin tahu rahasia kemenangan ini? Baca selengkapnya di Dragon’s Treasure dan rasakan sensasinya!
UID_51422933###
Karyawan Pabrik Raih Jackpot 300 Juta – Siapa sangka, rutinitas harian seorang karyawan pabrik berubah drastis setelah memenangkan jackpot besar dari Mystic Fortune. Apakah Anda siap untuk mendapatkan keberuntungan serupa?
Trix – подними на свою мечту!
мегафон интернет екатеринбург
мегафон подключить
мегафон подключение
With 13 years of experience, MailBanger.com has been a reliable source in direct mail solutions. Our platform offers millions of verified leads to help businesses grow. Whether you’re targeting local customers, our industry-specific lists are designed to achieve your goals. Start growing with us today at MailBanger.com!
With more than 13 years in the industry, MailBanger.com has delivered results through high-quality email lists. With unmatched reach across industries, we make it easy to expand your reach. Start your journey to success today!
Why choose MailBanger.com? With 13 years of experience, we provide millions of verified leads for email, telemarketing, and direct mail marketing. Our industry-specific lists are built to save you time. Focus on growth while we provide the data—visit MailBanger.com today!
At MailBanger.com, you’re partnering with experience. We offer millions of leads to grow your business. From telemarketing databases, our affordable solutions help you scale. Download your lists today at MailBanger.com.
мегафон подключение екатеринбург
https://plus-ekb-domasnij-internet-2.ru
мегафон подключить
Norma ISO 10816
Aparatos de calibración: esencial para el desempeño estable y efectivo de las maquinarias.
En el ámbito de la ciencia actual, donde la productividad y la seguridad del equipo son de gran trascendencia, los aparatos de calibración juegan un tarea fundamental. Estos sistemas adaptados están creados para ajustar y fijar partes móviles, ya sea en maquinaria productiva, vehículos de movilidad o incluso en equipos domésticos.
Para los expertos en conservación de sistemas y los profesionales, utilizar con sistemas de calibración es importante para garantizar el operación fluido y confiable de cualquier mecanismo móvil. Gracias a estas soluciones avanzadas avanzadas, es posible minimizar notablemente las oscilaciones, el estruendo y la tensión sobre los soportes, aumentando la longevidad de piezas importantes.
Asimismo importante es el rol que desempeñan los equipos de equilibrado en la atención al usuario. El soporte profesional y el mantenimiento continuo empleando estos equipos facilitan dar soluciones de gran estándar, elevando la satisfacción de los consumidores.
Para los responsables de proyectos, la aporte en equipos de balanceo y medidores puede ser esencial para mejorar la efectividad y desempeño de sus dispositivos. Esto es especialmente trascendental para los emprendedores que administran medianas y pequeñas negocios, donde cada punto es relevante.
Además, los dispositivos de calibración tienen una amplia uso en el campo de la protección y el gestión de excelencia. Habilitan encontrar potenciales problemas, reduciendo mantenimientos onerosas y perjuicios a los aparatos. También, los indicadores extraídos de estos aparatos pueden utilizarse para perfeccionar sistemas y potenciar la exposición en buscadores de consulta.
Las áreas de utilización de los aparatos de ajuste comprenden diversas ramas, desde la producción de ciclos hasta el seguimiento ecológico. No importa si se habla de importantes elaboraciones manufactureras o reducidos establecimientos hogareños, los equipos de balanceo son esenciales para promover un desempeño efectivo y sin riesgo de interrupciones.
Your article helped me a lot, is there any more related content? Thanks!
UID_78161525###
Keberuntungan Tak Terduga Montir Bengkel Raih Jackpot 500 Juta dari Wild West Gold ATP
мегафон подключение
https://plus-ekb-domasnij-internet-3.ru
мегафон екатеринбург
мегафон тв екатеринбург
мегафон телевидение екатеринбург
мегафон тарифы на интернет
Welcome to Funny Moment We bring you funny fails, epic bloopers, viral memes, and hilarious moments that will keep you entertained! If you love comedy videos
I really like your theme. Where did you buy this? Amazing UI! Really lovely. Thank you.
мегафон телевидение
https://plus-ekb-domasnij-internet-3.ru
мегафон телевидение екатеринбург
ankara çocuk diş hekimi ankara çocuk diş hekimi
Bağlıca özel ders alanında uzman eğitimciler tarafından eğitim verilmektedir.
провайдер мегафон
https://plus-ekb-domasnij-internet-2.ru
мегафон интернет
I’m so delighted I found Nagano Lean Body Tonic. The blend of environment-friendly tea remove, ginger, and turmeric has assisted me control my yearnings and improve my metabolism. It’s an all-natural and reliable way to support weight reduction. I have actually seen excellent outcomes and will proceed utilizing it. Highly suggest!
Feel free to visit my web site: https://www.laciotatentreprendre.fr/employer/us-naganotonics/
ankara tüp bebek tedavisi alanında uzman hekim tarafından gerçekleştirilmektedir.
Howdy! This is my first comment here so I just wanted to give a quick shout out and tell you I genuinely enjoy reading your posts. Can you suggest any other blogs/websites/forums that cover the same topics? Thanks!
сайт зума казино
What’s up every one, here every person is sharing these kinds of familiarity, thus it’s nice to read this webpage, and I used to pay a visit this webpage daily.
официальный сайт lee bet
This website really has all of the info I wanted about this subject and didn’t know who to ask.
https://pennsylvania.bizhwy.com/steam-hippo-carpet-cleaning-id25016.php
билайн подключение
https://essex.club/employer/taren/
билайн тарифы на интернет
Because I started making use of Provadent, my dental examinations have been a lot better. My teeth are stronger, and my periodontals are healthier. The all-natural formula is gentle yet effective. Provadent is currently a staple in my day-to-day routine.
Feel free to surf to my web site: https://Wifidb.science/wiki/Fresh_Breath_Solutions_Can_Provadent_Help
мтс подключение кемерово
http://dimarecruitment.co.uk/employer/verla/
мтс телевидение кемерово
TJM Taxes seems like a trusted name for tax services! A strong online presence through proper SEO strategies like keyword optimization, local SEO, and quality backlinks can help them reach more clients. Consistent content and positive customer reviews will also boost visibility and credibility.
сайт мтс краснодар
https://jobster.pk/companies/ken
сайт мтс краснодар
Awesome site you have here but I was wanting to know if you knew of any user discussion forums that cover the same topics talked about here? I’d really love to be a part of community where I can get responses from other knowledgeable people that share the same interest. If you have any suggestions, please let me know. Bless you!
https://ch-z.com.ua/linzy-v-fary-porivnyannya
провайдер мегафон
https://www.toutsurlemali.ml/employer/chase/
мегафон тарифы ростов
билайн тв
https://sebagai.com/companies/cyril/
сайт билайн кемерово
A well-designed kitchen is more than just beautiful countertops and modern appliances—it’s also about the right accents and decor. One essential element often overlooked is kitchen rugs and runners. These functional and stylish pieces can transform your kitchen space, providing comfort, protection, and a decorative touch. Whether you are looking for a cozy kitchen mat to support your feet or a stylish runner to enhance your decor, Liquidation Rugs in Henderson, Nevada, has the perfect selection for you.
мтс подключение краснодар
https://vieclam.tuoitrethaibinh.vn/employer/launa/
мтс тарифы краснодар
ттк телевидение ростов
https://kkhelper.com/employer/ramon/
ттк интернет ростов
Ida Crest Landscaping looks like a great choice for professional landscaping services! By focusing on local SEO, high-quality content, and building strong backlinks, they can boost their online presence and attract more local clients. Showcasing their work through visuals and customer reviews would also enhance their credibility and engagement.
билайн подключить
https://finitipartners.com/employer/klaudia/
билайн тв
If you’re looking for a game that’s both relaxing and addictive, Tiny Fishing is the perfect choice for you. This simple, easy-to-learn fishing game offers endless fun with just the right amount of challenge
If you’re looking for a game that’s both relaxing and addictive, Tiny Fishing is the perfect choice for you. This simple, easy-to-learn fishing game offers endless fun with just the right amount of challenge
Yes! Finally someone writes about american tv show.
Have a look at my web blog – Video profiles (Kinomaniak.mystrikingly.com)
провайдер мтс
http://fatims.org/employer/amelie/
мтс подключить кемерово
мегафон интернет ростов
https://icmimarlikdergisi.com/kariyer/companies/dario/
мегафон подключить
провайдер ттк
https://tur-job.com/companies/hong/
провайдер ттк
सेक्स डॉल की दुकान https://hi.yourdoll.com
Excellent, what a webpage it is! This web site gives useful data to us, keep it up.
code promo 1xcasino ci 2025
Lee Brokers Realty Lee Brokers Realty looks like a trusted name in real estate! With the right SEO strategies — like local keyword optimization, quality backlinks, and showcasing property listings — they can boost their online visibility and attract more potential buyers and sellers. Positive client testimonials and market insights will also strengthen their reputation.
Nice post. I learn something totally new and challenging on websites I stumbleupon everyday. It’s always interesting to read through content from other writers and practice a little something from their web sites.
cashless
I got this website from my pal who informed me on the topic of this site and at the moment this time I am visiting this web site and reading very informative content here.
raw honey
Hi! This post could not be written any better! Reading this post reminds me of my old room mate! He always kept chatting about this. I will forward this write-up to him. Pretty sure he will have a good read. Thanks for sharing!
mobile payments
Hey are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started and create my own. Do you need any coding expertise to make your own blog? Any help would be really appreciated!
1xcasino promo code Egypt
Maintaining a clean and safe outdoor space requires regular attention to tree debris. Whether from storms, seasonal shedding, or general landscaping, fallen branches, leaves, and other organic materials can accumulate quickly. For those searching for tree debris removal near me, we offer expert services in Marysville, WA, and surrounding areas, ensuring residential and commercial properties remain clean, safe, and visually appealing.
See More: http://www.pacificlandpreservation.com/
UID_75674709###
Akun Baru Winrate 100 Kerjasama Atp Dengan Pg Soft Pasti Menang Bermain Sweet Bonanza
I’ve been making use of Nagano Lean Body Tonic for a couple of months now, and I’m pleased with the outcomes. The combination of environment-friendly tea remove, ginger, and turmeric has aided me shed weight and feel even more energetic. It’s an all-natural and secure way to sustain weight management. I’m really completely satisfied with this product.
Feel free to visit my page – http://Lineage182.tw/bbs/home.php?mod=space&uid=445699
Prime biome nurtures beneficial gut bacteria, contributing to enhanced skin radiance and a more youthful glow.
Lee Brokers Realty Lee Brokers Realty looks like a trusted name in real estate! With the right SEO strategies — like local keyword optimization, quality backlinks, and showcasing property listings — they can boost their online visibility and attract more potential buyers and sellers. Positive client testimonials and market insights will also strengthen their reputation.
Prime biome nurtures beneficial gut bacteria, contributing to enhanced skin radiance and a more youthful glow.
Prime biome nurtures beneficial gut bacteria, contributing to enhanced skin radiance and a more youthful glow.
Equilibrado
Dispositivos de ajuste: fundamental para el desempeño estable y efectivo de las dispositivos.
En el mundo de la avances actual, donde la productividad y la confiabilidad del aparato son de suma relevancia, los equipos de ajuste cumplen un papel vital. Estos sistemas dedicados están concebidos para ajustar y regular piezas dinámicas, ya sea en dispositivos manufacturera, medios de transporte de desplazamiento o incluso en electrodomésticos caseros.
Para los profesionales en soporte de dispositivos y los especialistas, utilizar con equipos de ajuste es esencial para asegurar el rendimiento fluido y fiable de cualquier sistema giratorio. Gracias a estas opciones avanzadas innovadoras, es posible reducir significativamente las movimientos, el zumbido y la tensión sobre los rodamientos, mejorando la duración de elementos importantes.
De igual manera relevante es el rol que cumplen los dispositivos de calibración en la servicio al comprador. El soporte experto y el mantenimiento permanente utilizando estos sistemas posibilitan proporcionar soluciones de excelente excelencia, mejorando la agrado de los clientes.
Para los dueños de negocios, la financiamiento en estaciones de equilibrado y detectores puede ser importante para incrementar la efectividad y desempeño de sus sistemas. Esto es especialmente importante para los emprendedores que administran medianas y medianas organizaciones, donde cada punto vale.
También, los sistemas de equilibrado tienen una vasta aplicación en el sector de la seguridad y el control de calidad. Permiten localizar probables problemas, reduciendo reparaciones costosas y perjuicios a los sistemas. Más aún, los indicadores generados de estos equipos pueden usarse para mejorar procedimientos y potenciar la visibilidad en plataformas de exploración.
Las zonas de uso de los sistemas de calibración abarcan numerosas áreas, desde la elaboración de transporte personal hasta el monitoreo ecológico. No importa si se habla de extensas elaboraciones productivas o pequeños establecimientos hogareños, los aparatos de ajuste son fundamentales para asegurar un desempeño productivo y sin presencia de fallos.
The Best coco peat suppliers
coco peat sri lanka…
Choosing the Right HVAC Units for Comfort and Energy Savings
When it comes to maintaining a comfortable indoor environment, HVAC units play a crucial role. Whether you’re installing a new system or upgrading an existing one, selecting the right HVAC unit requires careful consideration. From energy efficiency to system types and maintenance, understanding your options will help ensure long-term comfort and savings. Comfort Zone HVAC is here to provide expert guidance and reliable solutions for your heating and cooling needs.
The Ultimate Guide to Concrete Floors: Benefits, Applications, and Expert Advice
Concrete floors have gained significant popularity in both residential and commercial settings due to their durability, versatility, and low maintenance. Whether used in homes, warehouses, or retail spaces, they provide a reliable flooring solution that withstands heavy use while maintaining a sleek and professional appearance.
See More: https://mastermixconcrete.co.uk/
The Ultimate Guide to Concrete Floors: Benefits, Applications, and Expert Advice
Concrete floors have gained significant popularity in both residential and commercial settings due to their durability, versatility, and low maintenance. Whether used in homes, warehouses, or retail spaces, they provide a reliable flooring solution that withstands heavy use while maintaining a sleek and professional appearance.
thank you amazing post!
Incredible all kinds of useful advice!
my web-site – https://git.lodis.se/caramoreton857/baccarat-site-7631/wiki/Discover-Reliable-Baccarat-Site-Standards-with-Casino79%27s-Scam-Verification-Platform
Whoa a good deal of great knowledge.
Feel free to visit my blog post; https://repo.gusdya.net/brianmattingle
мтс тарифы на интернет
https://remoteuntil.com/companies/selina1502/
мтс подключение
Istanbul breast reduction surgery (reduction mammoplasty) is a
ufabet-ฝากถอนไม่มีขั้นต่ำ Deposit and withdraw easily by using the ufabet system service. Direct website, no minimum. Players can use it easily through the main page, our UFABET 789 entrance, ready for you to deposit and withdraw freely.
Cheers, I appreciate this.
My blog – https://service.aicloud.fit:50443/bbeterry57187/casino-site-8424/-/issues/19
Online football betting website direct website เว็บแทงบอลออนไลน์ Online football betting step football single football water and paid commission up to 100000 per weeks
Online football betting website direct website เว็บแทงบอลออนไลน์ Online football betting step football single football water and paid commission up to 100000 per weeks
сайт мтс новосибирск
https://jobzee.co.uk/Company/leticia8187/
мтс тв новосибирск
I like this web site so much, saved to favorites.
my web site :: http://pandora.Nla.gov.au/external.html?link=https://telegra.ph/Just-How-to-Keep-Fit-and-Healthy-And-Balanced-with-Tidy-Eating-01-31
In addition, playing all PCSO games comes with their respective rules.
my website … https://git.privateger.me/kerrygriggs737
Nicely put, Cheers.
My homepage :: Online Sports Betting (https://gitcq.cyberinner.com/issacv50772634)
мтс тв
https://www.huntsrecruitment.com/employer/24inetrnet-domashnij-ekb-3/
мтс тарифы екатеринбург
Welcome to Planet Clicker, the ultimate destination for fans of space exploration and idle gaming!
Hey there everyone,
SEO and digital marketing are essential in today’s ever-evolving business world.
As a Chicago local, I’ve seen how geo-targeted strategies transform online presence—especially
for competitive industries. Nfinitelimits, a results-driven agency in Mundelein, clearly excels with
customized solutions.
Their exoertise in technical Seo Full Form (https://Hirepel.Whitepel.In) and content marketing
greatly benefits businesses to dominate in regional markets.
Taake their work|Consider their successful campaigns: they optimize Google Bsiness Profiles and leverage cutting-edge
software to effectively handle search ehgine updates.
Alongside social media integration, they develop comprehensive plans.
If you’re aiming to revitalize your online visibility, their
team delivers visible results. Their customized plans fuel genuine
growth, not just quick-fix solutions.
ProDentim has made a noticeable difference in my dental health. My dental professional also discussed exactly how much healthier my gums look. The supplement is easy to take and has an enjoyable taste. I highly advise ProDentim to any person seeking to boost their oral health.
Here is my web site :: https://2Ch-ranking.net/redirect.php?url=https://yogicentral.science/wiki/Attaining_Healthy_Gums_and_Teeth_with_ProDentim
Online football betting website direct website เว็บแทงบอลออนไลน์ Online football betting step football single football water and paid commission up to 100000 per weeks
Online football betting website direct website เว็บแทงบอลออนไลน์ Online football betting step football single football water and paid commission up to 100000 per weeks
The Benefits of NAD+ Therapy in Crystal River, FL
In the world of modern wellness and anti-aging, NAD+ therapy has gained significant attention. At Medultima Aesthetic, located in Crystal River, FL, individuals have access to this innovative treatment designed to support cellular health, energy production, and overall well-being.
See More: https://medultimaaesthetics.com/
ufavvip789 ที่การโอนเงินเร็ว ระบบนิ่ง กีฬา คืนค่าน้ำ 0.25% – คาสิโน UFABET คืนค่าคอมฯ 0.7% ฝาก – ถอนรวดเร็วผ่านระบบออโต้ ใช้เวลาเพียง 3 นาทีเท่านั้น
ufavvip789 ที่การโอนเงินเร็ว ระบบนิ่ง กีฬา คืนค่าน้ำ 0.25% – คาสิโน UFABET คืนค่าคอมฯ 0.7% ฝาก – ถอนรวดเร็วผ่านระบบออโต้ ใช้เวลาเพียง 3 นาทีเท่านั้น
ProDentim has made a noticeable difference in my dental health and wellness. My dental practitioner even talked about just how much healthier my gums look. The supplement is simple to take and has a pleasant taste. I very advise ProDentim to any individual looking to boost their dental health.
My web page … https://Valetinowiki.racing/wiki/Checking_Out_ProDentim_Benefits_for_Boosted_Gum_Health
Truly all kinds of helpful information!
Feel free to visit my page; https://gitea.joodit.com/eddie59p183397
Provadent has actually made a significant difference in my dental health. My gums are no more delicate, and my teeth feel stronger. The fresh breath is a wonderful benefit. I extremely advise Provadent to anybody seeking to enhance their oral hygiene.
My homepage :: https://Www.bitsdujour.com/profiles/huTJSG
With thanks, An abundance of posts.
Here is my web blog :: http://git.miaokids.com/abdulmcmurtry9/slot-site-3956/wiki/Exploring+the+Perfect+Scam+Verification+Platform%253A+Casino79+for+Evolution+Casino
Greetings everyone,
SEO and digital marketing are absolutely crucial in today’s highly competitive business world.
Living in Illinois, I’ve observed how regional search optimization dramatically boost online visibility—especially for competitive industries.
This agency, a results-driven ageency in the Mundelein area, distinguishes itself with personalized
solutions.
Their expertise in on-page 90 dayy sseo Plan (http://www.Jobassembly.com)
and content marketing greatly benefits businesses
to excel in local markets. Take their work|For instnce successful
campaigns: they refine Google Business Profiles and employ cutting-edge software to outsmar search engine updates.
Paired with social media integration, they craft well-rounded approaches.
For businesses aiming to scale your online visibility, this agency
achieves concrete success. Thheir tailored solutions fuel sustainable
growth, not just quick-fix outcomes.
There is also a 100% reload bonus up to $1000 that you can use after a week.
my site – https://git.lazyka.ru/zoragable5391
Your site is very nice, the articles are great, I wish you continued success, I love your site very much, I will visit it constantly
Kudos! A good amount of postings!
Stop by my web blog – https://9jadates.com/@zuiflorine266
You actually revealed this wonderfully.
my homepage … Gambling Site (http://gitlab.rainh.top/mohammad585381/slot-site-2991/-/issues/1)
Nagano Lean Body Tonic has been a game-changer for me. I have actually dealt with weight monitoring for years, however this tonic has made a noticeable difference. The natural ingredients like environment-friendly tea extract and turmeric extract have enhanced my metabolic process and power degrees. I really feel much healthier and extra confident. Very suggest!
Feel free to surf to my website; https://Vsegda-pomnim.com/user/frownsale56/
The platform prioritizes payment security through encrypted gateways, and users can explore promotions or loyalty programs for an enhanced gaming experience.
My web page: https://git.unicom.studio/erikaconklin14
Vital press releases are Influencing media Stories.
They Aid build Links between Organizations and Journalists.
Writing Impactful press releases Necessitates being Concise,
Matched with the Interests of Chosen News Channels.
In Today’s Digital Age, press releases Likewise Act Critical role
in Digital Public Relations. They Address
Traditionnal news outlets Also Increase Visits and Improve
a Company’s Internet Visibility. Including Multimedia Elements, such as Clips, can Make chicago press
(hoidap24h.xyz) releases Even Engaging and Accessible.
Modifying to the Developing media Sphere while Upholding core Standards can Substantially Amplify
a press release’s Influence. How Do You Feel on Using multimedia in Press Releases?
İşte botoks hakkında bilmeniz gereken temel bilgiler:
viyana üniversitesi kabul şartları viyana üniversitesi kabul şartları
мтс телевидение екатеринбург
https://earlyyearsjob.com/employer/24inetrnet-domashnij-ekb/
мтс интернет
Here’s the summarized results of winning numbers for all jackpot-bearing games.
Feel free to visit my web site … https://git.dsvision.net/christianegree
magnificent publish, very informative. I wonder why the opposite experts
of this sector don’t realize this. You should proceed your writing.
I’m confident, you have a great readers’ base already!
My web-site: free psp games (https://reviewscoreb059371.blogdanica.com/30253859/Indicators-on-pc-games-free-download-you-should-know)
Simbabet ile bahis yapmak şimdi daha avantajlı! Başlangıç kayıp bonusu sayesinde kazancınızı artırın, hemen üye olun!
взять кредит под птс
avtolombard-11.ru/ekb.html
кредит под залог автомобиля
Looking for expert guidance on protecting assets while qualifying for Medicaid? As experienced elder law attorneys near me, our team at Ohio Medicaid Lawyers provides specialized legal assistance with Medicaid planning, estate planning, and asset protection strategies. We help seniors understand medicaid eligibility income charts and navigate the complex 5-year lookback period. Visit our website for comprehensive information about Ohio medicaid income limits 2024 and schedule a consultation with a trusted elder care attorney who can safeguard your future.
Useful info With thanks!
Look into my web site :: Slot Site (https://gitlab.marschall.tech/shawnaweaver56)
автоломбард залог машины
avtolombard-11.ru/kazan.html
наличные под залог автомобиля
взять кредит под птс автомобиля
avtolombard-11.ru
деньги под залог машины москва
деньги в долг под залог машины
avtolombard-11.ru/nsk.html
автоломбард под займ
кредит под залог птс казань
https://cannabisjobs.solutions/companies/dimarecruitment4461/
кредит под залог птс казань
Dental implant tedavisi kaybedilen dişlerin yerlerine diş kökünü taklit eden titanyum (son yıllarda zirkonyum da kullanılmaktadır.) vidalardır.
Playing max bet can be a requirement for some progressive jackpot slots to be eligible for the jackpot.
my web blog … https://casino79.in/
20 yılı aşkın eğitim tecrübemiz ve alanında uzman kadromuz ile sınavlara hazırlıkta yalnız değilsiniz.
займ птс
avtolombard-pid-zalog-pts.ru/kazan.html
займ птс
Explore Premium Products for Happy, Healthy Pets in Auckland
PET training tools AUckland …
Similar to major jurisdictions, litigation is the default dispute resolution mechanism in Turkey. Unless the parties agree otherwise, disputes are resolved through the state courts.
Ümraniye liposuction ameliyatı, vücuttaki belirli bölgelerdeki aşırı yağların cerrahi bir işlemle alınması amacıyla yapılan bir estetik cerrahi uygulamadır.
jalantoto
Trix – официальный сайт – сервис мгновенных игр
Трикс играть онлайн раздача каждый день
buy kick viewers
Trix – официальный сайт
подключить проводной интернет екатеринбург
domashij-internet-ekaterinburg001.ru
провайдер по адресу екатеринбург
Сервис мгновенных игр Money-X: официальный сайт с быстрым доступом
Trix – официальный сайт – Трикс играть онлайн раздача каждый день
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
interesting for a very long time
_________________
indianpremierleague 2025
Trix – официальный сайт
интернет по адресу екатеринбург
domashij-internet-ekaterinburg002.ru
какие провайдеры по адресу
Trix – официальный сайт – Трикс играть онлайн раздача каждый день
провайдеры домашнего интернета екатеринбург
domashij-internet-ekaterinburg003.ru
домашний интернет тарифы екатеринбург
Hey there everyone,
Search engine optimization and digital marketing are absolutely crucial in today’s highly competitive business world.
Being based in Chicago, I’ve witnessed how geo-targeted strategies transform
online visibility—especially for competitive industries.
This agency, a premier agency in Mundelein, distinguishes itself with
personalized solutions.
Their focus in technical national seo vs local Seo (Fanajobs.com) and
PPC campaigns substantially helps businesses to dominate in specific
markets. For example|For instance successful campaigns: tthey refine Google Buskness Profiles and employ state-of-the-art technology to effectively handle search engine updates.
Combined with social media integration, they craft comprehensive
strategies.
Should you be aiming to enhance your online reach, their team achieves visible results.
Their bespoike plans ignite sustainable growth, not
just short-term solutions.
UID_20861405###
123
интернет провайдеры в казани по адресу дома
domashij-internet-kazan001.ru
провайдеры интернета по адресу казань
провайдеры интернета по адресу
domashij-internet-kazan002.ru
провайдеры в казани по адресу проверить
Breast ptosis surgery, medically known as mastopexy, is a surgical procedure performed to correct breast sagging and achieve a more lifted appearance.
Legal in all US states except Washington, Michigan, Idaho, and Nevada, players across the nation can access the brilliant gaming encounter at Vegas Gems.
Also visit my web blog :: http://nas.bbhxwl.com:8418/carrollslatter
интернет провайдеры новосибирск
domashij-internet-novosibirsk003.ru
домашний интернет подключить новосибирск
For example, all Kewadin and Ojibwa casino locations accept persons 18 years of age and up.
Review my web site :: https://git.cdbaolan.com/willian41f9671/betting-sites-9308/wiki/The+Rise+of+Online+Sports+Betting%253A+A+Sport+Changer+in+Gambling
Superb forum posts Thanks.
Here is my site … https://git.skyviewfund.com/lestersnider95/online-sports-betting-3554/wiki/Discovering+Safe+Gambling+Sites%253A+Your+Guide+to+Sureman+and+Scam+Verification
подключить интернет москва
domashij-internet-msk002.ru
провайдер по адресу москва
кино mailsco увлекает интерес многих аудитории.
Sweet Bonanza’yı hangi sitelerde oynayabilirim?
Digiturk illere özel sporun yıldızı ile digiturk paketinizi seçip digiturk dünyasına adım atın.
Digiturk illere özel sporun yıldızı ile digiturk paketinizi seçip digiturk dünyasına adım atın.
лучший интернет провайдер челябинск
domashij-internet-chelyabinsk001.ru
дешевый интернет челябинск
Akpıyar Karaköprü Uyducu Karaköprü Uydu Servisi hemen arayın gelelim.
Kadıköy implant tedavisi, eksik dişlerin yerine yerleştirilen yapay diş kökleridir.
интернет провайдеры уфа по адресу
domashij-internet-ufa003.ru
провайдеры интернета в уфе по адресу проверить
Burun, soluduğumuz havayı belirli bir nem ve ısıya getirip akciğerlere filtreleyerek ulaştırılmasında görev alır.
подключить интернет омск
domashij-internet-omsk001.ru
домашний интернет омск
Zacznij zabawę w najpopularniejsze gry i premie czekają na Ciebie! Fajny post, bardzo dziękuję za udzielenie wiedzy.
Ten niezwykle kompleksowy przewodnik oferuje wyjątkową głębię wiedzy, pozostając zaskakująco przystępnym zarówno dla początkujących, jak i ekspertów. Lemon Casino Witaj w krainie sieciowych kasyn online i bukmacherów! Dzięki postępowi innowacji, możesz teraz używać najlepszymi zabawami hazardowymi i zakładać się na spotkania w dowolnym miejscu i czasie. Nasze internetowe kasyno oferuje szeroki gamę zabaw, od klasycznych jednorękich bandytów do nowoczesnych gier planszowych, a nasze zakłady sportowe obejmują wszystkie ulubione dyscypliny. Dołącz teraz i zagarnij z atrakcyjnych premii startowych oraz regularnych akcji. Nie czekaj, weź udział do naszej społeczności i rozpocznij zabawę już teraz!
Всем привет!
Меня зовут Демид и я обожаю смотреть онлайн мультсериал Симпсоны на сайте https://simpsons.icu
Там много интересных серий, которые Вам понравятся.
Присоединяйтесь!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Yabancı modellerle elit bir akşam geçirmek isteyenler için Ankara’nın en başarılı adresi. Ankara escort aramalarında artık başka bir yere bakmaya gerek yok.
лучший интернет провайдер ростов
domashij-internet-rostov003.ru
дешевый интернет ростов
สล็อตเว็บตรง แตกต่างจากเว็บที่ผ่านเอเย่นต์แน่นอน เพราะเว็บที่ผ่านเอเย่นต์มีการหักเงินหรือหักเปอร์เซ็นต์บางครั้งมีการทำเทิร์นและลดอัตราชนะ
Cập nhật tỷ lệ kèo nhà cái và tylekeo mỗi ngày từ các nhà cái uy tín châu Á. Kèo nhanh, chuẩn, giao diện dễ dùng – hỗ trợ soi kèo hiệu quả và lựa chọn thông minh.
ivecop 12 mg tablet https://ivermectino.com/# scavista 12mg tab
Hastalarımıza her türlü ağız ve diş sağlığı hizmetini sunabilmek ve her hastamızın kliniklerimizden sağlıklı ve gülerek çıkmasını sağlamak hekimlik anlayışımızın ayrılmaz bir parçasıdır.
¡Hola! Soy Jeramy, tengo 26 años y soy de Valga provincia de Pontevedra. El surf es mi pasión, y tengo una familia hermosa con mi esposo David y nuestros dos hijos, Carlos de 5 años y Sofía de 3. ¡Gracias!
Visitar mi sitio :: http://www.larsaluarna.se/index.php/Paginas_Web_Andorra
Hair loss and balding can affect anyone at any stage of life, with varying degrees of severity. While genetic factors play a significant role in male and female pattern baldness, stress, nutritional deficiencies, and other lifestyle factors can also contribute to thinning hair. Whether you’re dealing with hair thinning, receding hairlines, or significant bald patches, understanding your options for hair restoration balding is key to regaining confidence and improving overall well-being.
See More: https://medultimaaesthetics.com/
Brustvergrößerungsoperationen erfreuen sich einer großen Beliebtheit bei Frauen.
HappyToon 해피툰 : the fastest place to check free webtoon addresses. 해피툰
HappyToon 해피툰 : Introduction to the most popular free webtoons 해피툰
HappyToon 해피툰 주소안내 : Introduction to the most popular free webtoons 해피툰 주소안내
HappyToon 해피툰 : which has the largest number of webtoons currently being serialized. 해피툰
HappyToon 해피툰 주소안내 : which has the largest number of webtoons currently being serialized. 해피툰 주소안내
HappyToon 웹툰추천 : which has the largest number of webtoons currently being serialized. 웹툰추천
HappyToon 해피툰 : which has the largest number of webtoons currently being serialized. 해피툰
Seriously loads of good tips!
Also visit my webpage … https://froggyads.com/blog/advertising-affidavit-3/
Dental implant tedavisi ise dental implantların kemik içerisine yerleştirilmesidir.
123b là nhà cái uy tín với cá cược thể thao, game bài, bắn cá, slot game hấp dẫn. Giao diện thân thiện, bảo mật cao, tỷ lệ kèo tốt, hỗ trợ 24/7. Trải nghiệm ngay tại 123Bsam.co.uk!
Sağlık sektörüne özel dijital pazarlama ve iletişim çözümleri sunan Propal; 10 yılı aşkın sektörel deneyimi ve profesyonel kadrosu ile hazır.
If you ever need a clean fullscreen black screen for relaxing your eyes, testing Zoom lighting, or resetting focus during work, check out Blackscreen.space! You can even download a black screen image for offline use.
Бухгалтерия по цене двух чашек кофе: за кого нас держат?
Furthermore, gambling can outcome in debt, which tends to make students gamble even additional.
Here is my website … https://chumcity.xyz/read-blog/9611_discovering-the-ultimate-scam-verification-platform-for-online-gambling-sites-to.html
The North Carolina Lottery joined Powerball in 2006, followed by Mega Millions in 2010.
Stop by my blog … https://git.tasu.ventures/klaracardenas
Happy Toon 해피툰 : the fastest place to check free webtoon addresses. 해피툰
İnvisalign, dişlerin düzeltilmesi için kullanılan yenilikçi bir ortodontik tedavi yöntemidir.
Eryaman diş tedavileri genellikle ağız ve diş sağlığıyla ilgili çeşitli sorunların tedavi edilmesini içerir.
789bet là nhà cái uy tín, được cấp phép bởi PAGCOR, thu hút hơn 10 triệu thành viên. Đăng ký ngay để nhận quà tặng hấp dẫn và trải nghiệm cá cược an toàn, chất lượng.
подключить интернет тарифы челябинск
chelyabinsk-domashnij-internet001.ru
подключить домашний интернет челябинск
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Welcome to the world of cars! Our site is your reliable source of information on everything related to cars. We offer the latest news from the auto industry, detailed reviews of new models, test drives from experienced experts, as well as advice on choosing, buying and maintaining your car. Here you will find a convenient catalog with a full list of characteristics and prices, as well as owner reviews that will help you make an informed choice. If you are looking for information on a specific model, want to learn about new technologies, or just like reading about cars, you have come to the right place. Join our community of car enthusiasts and stay up to date with the latest trends in the automotive world! We have a forum for communication and exchange of experience, as well as blogs where experts share their knowledge and secrets. With us, you will always be one step ahead!
KUBET là nhà cái hàng đầu châu Á, hoạt động mạnh tại Việt Nam, kubet nổi bật với sảnh live 24/24 và đa dạng trò chơi như cá cược thể thao, xổ số, game bài, nổ hũ, bắn cá…
интернет провайдеры москва по адресу
msk-domashnij-internet001.ru
проверить провайдеров по адресу москва
Mi nombre es Rosario, resido en Membrilla provincia de Ciudad Real y disfruto de la fotografía en mi tiempo libre. Estoy casado y tenemos dos hijos, Mario de 7 años y Clara de 4.
Visita también mi sitio web; http://business-terms.Sbm.pw/user.php?login=kieranheng
The orange screen adds a cozy glow to my room when I’m working late or doing creative work. Super useful tool.
Największe nagrody oczekują na Panią w naszym kasynie internetowym! Super artykuł, dzieki za przekazanie wskazówek.
Przykłady z prawdziwego świata zawarte tutaj w wyjątkowo skuteczny sposób łączą teorię z praktyką. Bizzo Casino Odkryj urok paradisu podróży z nas biurem! Niezależnie, czy marzysz o wypoczynku na plaży czy niesamowitych wrażeniach w odległych kątkach świata, mamy dla Pana doskonałą wybór. Nasze wycieczki obejmują zróżnicowane kierunki, od znanych metropolii po ukryte perły natury. Powierz naszemu profesjonalizmowi i zabookuj swoją podróż już dzisiaj. Nie czekaj, badaj glob z naszą agencją i stwórz wspaniałe chwile!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Soy Danilo, tengo 32 años y soy de San Fructuoso de Bages provincia de Barcelona. Disfruto pintando al óleo en mi tiempo libre y estoy felizmente casada. Tenemos tres hijos: Marcos de 9, Elena de 7 y Pablo de 4.
Visita también mi página http://www.9.Motion-design.org.ua/story.php?title=-agencia-de-marketing-online-en-andorra-%E3%80%902grow-%E3%80%91-1233
?? Ever wondered if nude cam girls fake their reactions? Or how safe those live sex chat platforms really are?
We break it down at ?? livenude the home of real insights on live nude webcams.
?? Discover:
– Do models fake it — or feel it?
– Are nude cam sites safe for you?
– Why people watch cam girls (psychology behind it)
– What’s trending in YEAR on live cam platforms
?? Real girls. Real shows. Real answers.
Check it all here:
Your guide to nude webcams
Me llamo Candelaria, soy de Almería provincia de Almería y el rugby es mi vida. Estoy casado y tenemos dos hijos, Daniel de 5 años y Sofía de 3.
Aquí está mi sitio web; http://WWW.Onlinespielearchiv.de/index.php?a=stats&u=josettefort
¡Hola! Soy Joni, soy de Sabadell provincia de Barcelona y me encanta viajar. Tengo una familia hermosa con mi esposa María y dos hijos, Juan de 6 años y Sofía de 4.
Aquí está mi página de inicio http://Goohelp.com/bbs/board.php?bo_table=free&wr_id=296270
¡Hola! Soy Melinda, soy de Allariz provincia de Orense y me encanta viajar. Tengo una familia hermosa con mi esposa María y dos hijos, Juan de 6 años y Sofía de 4.
Mi página https://wikibuilding.org/index.php?title=Publicidad_Facebook_Andorra
온라인바카라도박꾼 먹튀검증 사이트 The best scam verification site for gamblers 먹튀검증사이트
“도박꾼 카지노 커뮤니티 Best Casino Community Gamblers 카지노커뮤니티 Best Casino Community Gamblers”
“도박꾼 카지노 커뮤니티 Best Slot Community Gamblers 슬롯커뮤니티 Best Casino Community Gamblers”
도박꾼 온라인 카지노 Introduction to safe online casinos 온라인카지노
도박꾼 온라인 슬롯 Introduction to safe online slot casinos 온라인슬롯
도박꾼 카지노 사이트 Best Casino Site Recommendations 카지노사이트
도박꾼 슬롯 사이트 Best Slot Site Recommendations 슬롯사이트
도박꾼 바카라 사이트 Recommended best baccarat site in Korea 바카라사이트
도박꾼 *온라인 바카라 How to play online baccarat 온라인바카라
подключить интернет
kazan-domashnij-internet002.ru
дешевый интернет казань
Looking for live nude fun, cam model guides, or ways to make money from the webcam industry?
?? Visit **littlecocktease com** and get access to:
?? Free cam site hacks
?? How to watch more and spend less
?? Best webcam affiliate programs
?? Tips on becoming a webcam model
?? Psychology of why cams are so addictive
Real advice from real users. Perfect if you’re watching, earning, or thinking about joining the adult cam world.
Check full articles here:
?? Don’t just watch — learn how to get the most out of every show.
https://littlecocktease.com/blog/the-psychology-behind-watching-live-cams-why-were-hooked/
ankara çocuk diş hekimi alanında uzman hekimler tarafından hizmet vermektedir.
Your blog is so informative. It’s amazing to see how these bloggers started from scratch and turned their passion into a full-time gig. The tips are spot on, especially about connecting with your audience and staying true to your unique voice. It’s a reminder that success takes time and hard work, but it’s definitely possible with dedication and the right approach. Try to Visit My Web Site :WARUNG4D
Your blog is so informative. It’s amazing to see how these bloggers started from scratch and turned their passion into a full-time gig. The tips are spot on, especially about connecting with your audience and staying true to your unique voice. It’s a reminder that success takes time and hard work, but it’s definitely possible with dedication and the right approach. Try to Visit My Web Site :WARUNG4D
Doğal meme estetiği, meme şekillendirme ve büyütme operasyonlarında, abartılı ve aşırı yapay sonuçlardan kaçınılarak daha doğal ve estetik görünümler elde edilmesini amaçlayan bir yaklaşımdır.
viyana üniversitesi başvuru tarihleri viyana üniversitesi başvuru tarihleri
подключить интернет в нижнем новгороде в квартире
nizhnij-novgorod-domashnij-internet003.ru
интернет провайдеры нижний новгород по адресу
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Before starting my blog, I saw so many YouTube video they were clamming you can be a master blogger in 7 days, that time I was thinking, is making money from blogging is really easy, but after a few months I got to know, it’s not an easy journey. I fully agree with you, blogging is not an overnight success, and it required patience. Every time you provides great content on your blog. Try to Visit My Web Site :Link Daftar Slot Deposit Qris 10rb Lokabet88
Before starting my blog, I saw so many YouTube video they were clamming you can be a master blogger in 7 days, that time I was thinking, is making money from blogging is really easy, but after a few months I got to know, it’s not an easy journey. I fully agree with you, blogging is not an overnight success, and it required patience. Every time you provides great content on your blog. Try to Visit My Web Site :Link Daftar Slot Deposit Qris 10rb Lokabet88
¡Saludos! Mi nombre es Berenice, resido en Seseña provincia de Toledo y soy un amante del baloncesto. Estoy casado y tenemos un hijo, David, que tiene 7 años.
No dudes en navegar por mi página web :: https://Systemcheck-wiki.de/index.php?title=Posicionamiento_Web_Andorra
Your article helped me a lot, is there any more related content? Thanks!
Mi nombre es Jimmy, resido en Andrach provincia de Islas Baleares y soy un ingeniero informático. Estoy casado y tenemos un hijo, Alejandro, que tiene 6 años.
Visita también mi página http://Cafe5.Winnen.co.kr/bbs/board.php?bo_table=free&wr_id=1745659
Трикс играть онлайн раздача каждый день
Soy Fermin, tengo 32 años y soy de Palafrugell provincia de Gerona. Soy profesora de primaria y estoy felizmente casada. Tenemos tres hijos: Marcos de 9, Elena de 7 y Pablo de 4. ¡Gracias!
Mi sitio web https://Suwontop.com/bbs/board.php?bo_table=free&wr_id=91023
Soy Wilfredo, tengo 32 años y soy de Astorga provincia de León. Me apasiona el ciclismo y estoy felizmente casada. Tenemos tres hijos: Marcos de 9, Elena de 7 y Pablo de 4. ¡Gracias!
Mi sitio web … https://wikibuilding.org/index.php?title=Posicionamiento_Web_Andorra
Mi nombre es Faustino, resido en Bollullos Par del Condado provincia de Huelva y disfruto de la fotografía en mi tiempo libre. Estoy casado y tenemos dos hijos, Mario de 7 años y Clara de 4.
No dudes en navegar por mi blog web … http://Sefkorea.com/bbs/board.php?bo_table=free&wr_id=1088573
Your article helped me a lot, is there any more related content? Thanks!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
TOP11 India is a premium online casino and sports betting platform offering top-tier games
Show more…
Altınoluk Restaurant – Doğa Restaurant | Altınoluk Restaurant, Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir. 0539 451 87 66 Altınoluk Doğa Restaurant, doğayla iç içe huzurlu bir atmosferde lezzetli yemekler sunuyor. Taze malzemelerle hazırlanan yemekler, zengin menüsü ve sıcak ortamıyla kendinizi evinizde hissedeceksiniz. Aileniz ve arkadaşlarınızla keyifli bir akşam yemeği için doğru adres! Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir’de yer alıyor. Lezzetli yemekler, doğa manzarası ve sakin bir ortam arıyorsanız, rezervasyon için 0539 451 87 66 numarasından bize ulaşabilirsiniz. Doğa Restaurant | Altınoluk Restaurant, Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir. 0539 451 87 66 Altınoluk Restaurant Altınoluk Restaurant
Arbitration can be administered by institutions like the International Chamber of Commerce (ICC) or conducted ad hoc.
Herkesin ihtiyaçları farklıdır, bu nedenle dişlerinizi ne sıklıkta kontrol ettirmeniz gerektiği konusunda diş hekiminizle sohbet edin. ağzınızın, dişlerinizin ve diş etlerinizin durumu.
Eğitim, her öğrencinin farklı öğrenme tarzlarına ve hızına sahip olduğu bir süreçtir.
провайдеры интернета екатеринбург
ekaterinburg-domashnij-internet001.ru
тарифы интернет и телевидение екатеринбург
домашний интернет
omsk-domashnij-internet002.ru
провайдеры интернета в омске
An English speaking lawyer in Turkey ensures smooth legal communication for foreigners facing business, property, or immigration-related matters.
Xoilac TV trực tiếp bóng đá hôm nay chính thức. Xoilac xem bóng đá Ngoại Hạng Anh, Cup C1, C2, Serie A, La Liga, World Cup. Xôi Lạc bóng đá trực tuyến không quảng cáo có BLV tiếng Việt tốc độ cao, miễn phí.
anal tedavisi, dişin iç yapısında meydana gelen enfeksiyonlar veya ciddi çürükler nedeniyle uygulanan önemli bir diş tedavisidir. Bu prosedür, dişin doğal yapısını koruyarak çekilmesini önler ve uzun süre sağlıklı kalmasını sağlar.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Adjusting routines gradually ensures balance and makes it easier to integrate treatments like order viagra cialis canada. Let raw energy and deep desire collide tonight.
Since I started utilizing ProDentim, I’ve noticed a significant decrease in negative breath and periodontal irritability. The probiotics and nutrients in the formula collaborate to advertise a healthier mouth. ProDentim is an essential for anybody serious about their oral health and wellness.
Here is my web page https://gogs.brigittebutt.de/verlenetrembla
Altınoluk Restaurant Doğa Restaurant | Altınoluk Restaurant, Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir. 0539 451 87 66 Altınoluk Doğa Restaurant’ta, doğayla iç içe lezzetli yemeklerin keyfini çıkarın! Altınoluk Doğa Restaurant, doğayla iç içe huzurlu bir atmosferde lezzetli yemekler sunuyor. Taze malzemelerle hazırlanan yemekler, zengin menüsü ve sıcak ortamıyla kendinizi evinizde hissedeceksiniz. Aileniz ve arkadaşlarınızla keyifli bir akşam yemeği için doğru adres! Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir’de yer alıyor. Lezzetli yemekler, doğa manzarası ve sakin bir ortam arıyorsanız, rezervasyon için 0539 451 87 66 numarasından bize ulaşabilirsiniz. Taze ve kaliteli malzemelerle hazırlanan yemekler, rahat ortamıyla sizi bekliyor. Adres: Altınoluk, Subaşı Cd. No: 90, 10879 Edremit/Balıkesir. Rezervasyon için 0539 451 87 66 Altınoluk Restaurant Altınoluk Restaurant
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Every serving deals 500 milligrams of cinnamon essence to help handle blood sugar degrees normally.
Look into my site … https://git.i2edu.net/jacintosells82
İstanbul reklam ajansları İstanbul Reklam Ajansı Zeymedya Çağlayan, Latif Sk. no:3 daire:4, 34403 Kağıthane/İstanbul 0530 236 00 25 İstanbul reklam ajansları İşletmenizin Google Maps üzerinde öne çıkmasını sağlıyoruz. Doğru SEO stratejileri ile yerel aramalarda görünürlüğünüzü artırıyor, potansiyel müşterilerinize kolayca ulaşılabilir hale gelmenizi sağlıyoruz. Zeymedya İstanbul Reklam Ajansı Dijital dünyada iz bırakmak isteyenler için buradayız!. istanbul reklam ajansları İstanbul reklam ajansları
Junior Tattoo, which offers reliable service in the Izmit Tattoo sector, perfects your tattoo experience in a hygienic environment. Make an appointment now.
Don’t be pushed by your problems; be led by your dreams.
Wow quite a lot of fantastic material.
Feel free to visit my web blog … http://tuzh.top:3000/christymulling/online-gambling-sites-8036/wiki/Ensuring-Safety-on-Korean-Gambling-Sites-with-Sureman-Scam-Verification
An analytical appear at the a variety of casino game developers, and guides on how to play their games.
Check out my blog post … http://gitlab.resolr.com/clarklaseron96
Eksozom cilt tedavisi, son yıllarda popülerlik kazanan ve cilt yenilenmesi, saç dökülmesi gibi estetik ve tıbbi amaçlarla kullanılan bir biyolojik tedavi yöntemidir
DT68 là nhà cái uy tín, xanh chín, thu hút hàng nghìn người chơi mỗi ngày. Nơi đây liên tục cập nhật nhiều ưu đãi hấp dẫn, mang đến trải nghiệm cá cược chất lượng cho khách hàng.
Sinan Özdemir is a skilled professional offering top-notch web development and SEO services, helping businesses enhance their online presence and reach their digital goals.
Seriously plenty of superb facts!
Also visit my web page … Casino Site (https://aggeliesellada.gr/profile/mavisbrunner49)
Your article helped me a lot, is there any more related content? Thanks! https://www.binance.com/ro/register?ref=V3MG69RO
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
Money-X официальный сайт – сервис мгновенных игр
Trix – официальный сайт – Трикс играть онлайн раздача каждый день
Ağız, diş ve çene cerrahisi, ağız içindeki yumuşak ve sert dokuların hastalıkları, yaralanmaları ve bozukluklarının tanı ve tedavisi ile ilgilenen bir tıp dalıdır.
Çukurambar Diş İmplantı: Estetik ve Fonksiyonel Bir Çözüm
Great guide on SSL configuration! Really appreciate the step-by-step details. It’s always helpful to see practical examples like this, especially when dealing with server security. I’ve tried similar setups before, and the clarity here makes it less daunting. By the way, if you’re into tech tweaks, you might enjoy the wacky flip game for a fun break. Thanks for sharing these insights!
Turizm sektöründe yılların verdiği deneyim ve uzmanlıkla, her türlü ulaşım ihtiyacınızı karşılamak için Shuttle-Transfer hizmeti sunuyoruz.
UID_81474082###
test
Hello, I really like your website, you have done a good job. I will definitely visit again. Thank you.
Öğrencilerimiz yaşayarak öğrenmenin gerektirdiği atölye sisteminden faydalanırlar.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Ataşehir botoks alanında uzman hekim hizmet vermektedir.
Balanset-1A: State-of-the-art Mobile Balancer & Vibration Analyzer
High-precision Dynamic Balancing Solution
Balanset-1A represents an advanced solution for dynamic balancing of rotors in their own bearings, developed by Estonian company Vibromera OU. The device provides professional equipment balancing at €1,751, which is 3-10 times more affordable than traditional vibration analyzers while retaining exceptional measurement accuracy. The system allows on-site balancing directly at the equipment’s working position without necessitating dismantling, which is vital for minimizing production downtime.
About the Manufacturer
Vibromera OU is an Estonian company concentrating in the design and manufacturing of equipment for technical diagnostics of industrial equipment. The company is registered in Estonia (registration number 14317077) and has branches in Portugal.
Contact Information:
Official website: https://vibromera.eu/shop/2/
Technical Specifications
Measuring Parameters
Balanset-1A delivers high-precision measurements using a twin-channel vibration analysis system. The device measures RMS vibration velocity in the range of 0-80 mm/s with an accuracy of ±(0.1 + 0.1?Vi) mm/s. The working frequency range is 5-550 Hz with optional extension to 1000 Hz. The system supports rotation frequency measurement from 250 to 90,000 RPM with phase angle determination accuracy of ±1 degree.
Working Principle
The device employs phase-sensitive vibration measurement technology with MEMS accelerometers ADXL335 and laser tachometry. Two mono-directional accelerometers measure mechanical vibrations proportional to acceleration, while a laser tachometer generates impulse signals for determining RPM and phase angle. Digital signal processing includes FFT analysis for frequency analysis and proprietary algorithms for automatic calculation of corrective masses.
Full Kit Contents
The standard Balanset-1A delivery includes:
Measurement unit with USB interface – central module with embedded preamplifiers, integrators, and ADC
2 vibration sensors (accelerometers) with 4m cables (optionally 10m)
Optical sensor (laser tachometer) with 50-500mm measuring distance
Magnetic stand for sensor mounting
Electronic scales for accurate measurement of corrective masses
Software for Windows 7-11 (32/64-bit)
Plastic transport case
Complete set of cables and documentation
Performance Capabilities
Vibrometer Mode
Balanset-1A functions as a comprehensive vibration analyzer with capabilities for measuring overall vibration level, FFT spectrum analysis up to 1000 Hz, measuring amplitude and phase of the fundamental frequency (1x), and continuous data recording. The system delivers display of time signals and spectral analysis for equipment condition diagnostics.
Balancing Mode
The device supports one-plane (static) and two-plane (dynamic) balancing with automatic calculation of correction masses and their installation angles. The unique influence coefficient saving function enables considerable acceleration of follow-up balancing of identical equipment. A dedicated grinding wheel balancing mode uses the three-correction-weight method.
Software
The intuitive program interface provides step-by-step guidance through the balancing process, making the device usable to personnel without specialized training. Key functions include:
Automatic tolerance calculation per ISO 1940
Polar diagrams for imbalance visualization
Result archiving with report generation capability
Metric and imperial system support
Multilingual interface (English, German, French, Polish, Russian)
Usage Domains and Equipment Types
Industrial Equipment
Balanset-1A is successfully used for balancing fans (centrifugal, axial), pumps (hydraulic, centrifugal), turbines (steam, gas), centrifuges, compressors, and electric motors. In production facilities, the device is used for balancing grinding wheels, machine spindles, and drive shafts.
Agricultural Machinery
The device provides exceptional value for agriculture, where uninterrupted operation during season is essential. Balanset-1A is used for balancing combine threshing drums, shredders, mulchers, mowers, and augers. The capability to balance on-site without equipment disassembly permits preventing costly downtime during busy harvest periods.
Specialized Equipment
The device is successfully used for balancing crushers of various types, turbochargers, drone propellers, and other high-speed equipment. The rotation frequency range from 250 to 90,000 RPM covers essentially all types of industrial equipment.
Advantages Over Alternatives
Economic Effectiveness
At a price of €1,751, Balanset-1A offers the functionality of devices costing €10,000-25,000. The investment recovers costs after preventing just 2-3 bearing failures. Cost reduction on outsourced balancing specialist services totals thousands of euros annually.
Ease of Use
Unlike complicated vibration analyzers requiring months of training, mastering Balanset-1A takes 3-4 hours. The step-by-step guide in the software enables professional balancing by personnel without specific vibration diagnostics training.
Mobility and Autonomy
The complete kit weighs only 4 kg, with power supplied through the laptop’s USB port. This enables balancing in outdoor conditions, at remote sites, and in difficult-access locations without additional power supply.
Universal Application
One device is suitable for balancing the broadest spectrum of equipment – from small electric motors to large industrial fans and turbines. Support for one and dual-plane balancing covers all typical tasks.
Real Application Results
Drone Propeller Balancing
A user achieved vibration reduction from 0.74 mm/s to 0.014 mm/s – a 50-fold improvement. This demonstrates the exceptional accuracy of the device even on small rotors.
Shopping Center Ventilation Systems
Engineers effectively balanced radial fans, achieving lower energy consumption, abolished excessive noise, and increased equipment lifespan. Energy savings offset the device cost within several months.
Agricultural Equipment
Farmers note that Balanset-1A has become an vital tool preventing costly breakdowns during peak season. Decreased vibration of threshing drums led to reduced fuel consumption and bearing wear.
Investment and Delivery Terms
Current Prices
Complete Balanset-1A Kit: €1,751
OEM Kit (without case, stand, and scales): €1,561
Special Offer: €50 discount for newsletter subscribers
Bulk Discounts: up to 15% for orders of 4+ units
Acquisition Options
Official Website: vibromera.eu (recommended)
eBay: certified sellers with 100% rating
Industrial Distributors: through B2B channels
Payment and Shipping Terms
Payment Methods: PayPal, credit cards, bank transfer
Shipping: 10-20 business days by international mail
Shipping Cost: from $10 (economy) to $95 (express)
Warranty: factory warranty
Technical Support: included in price
Conclusion
Balanset-1A constitutes an ideal solution for organizations seeking to establish an successful equipment balancing system without major capital expenditure. The device makes accessible access to professional balancing, allowing small enterprises and service centers to offer services at the level of large industrial companies.
The mix of accessible price, ease of use, and professional functionality makes Balanset-1A an essential tool for modern technical maintenance. Investment in this device is an investment in equipment dependability, decreased operating costs, and increased competitiveness of your company.
For seasonal maintenance of kotelnaya, lots of advice.
Ortodontistiniz, dişlerinizin ve çenenizin detaylı bir incelemesini yapar ve Invisalign tedavisinin sizin için uygun olup olmadığını belirler.
Me llamo Cerys, soy de Paiporta provincia de Valencia y el rugby es mi vida. Estoy casado y tenemos dos hijos, Daniel de 5 años y Sofía de 3.
mi página – https://Bbarlock.com/index.php/User:JoesphFairbanks
Great advice, Cheers.
Feel free to visit my web-site; https://il.frompo.com/couples/tags/cum-on-ass
Официальный сайт Money-X: сервис быстрых игр
займ залог птс
zaimpod-pts89.ru
займ под залог кредитного авто
Küçük Dahiler Akademi’de eğitim programı, çocuklarımızı gelecekteki dünyaya hazırlarken onların 21. yy. becerileri ile donatılmasını hedefler.
займ под залог машины
zaimpod-pts92.ru/ekb.html
кредит под птс грузового
Money-X официальный
ankara dermatoloji uzmanı ankara dermatoloji uzmanı ankara dermatoloji uzmanı ankara dermatoloji uzmanı ankara dermatoloji uzmanı ankara dermatoloji uzmanı ankara dermatoloji uzmanı
cialis: cialis10fr.com – best place to order generic viagra
You mentioned that effectively!
my webpage: http://git.kasdev.cc/alliefairley35
After trying about 10 clones, I’m finally sticking with the Blockblast version hosted on https://blockblastx.com. Legit.
karın estetiği, genital estetik ve ameliyatsız estetik işlemler başta olmak üzere tüm estetik cerrahi işlemlerde yoğunlaşmış olup hastalarının doğal görünümlerini koruyarak en iyi sonuçları elde etmeyi hedeflemektedir.
도박꾼 먹튀검증 사이트사이트 The best scam verification site for gamblers 먹튀검증사이트
“도박꾼 카지노 커뮤니티 Best Casino Community Gamblers 카지노커뮤니티 Best Casino Community Gamblers”
“도박꾼 카지노 커뮤니티 Best Slot Community Gamblers 슬롯커뮤니티 Best Casino Community Gamblers”
도박꾼 온라인 카지노 Introduction to safe online casinos 온라인카지노
도박꾼 온라인 슬롯 Introduction to safe online slot casinos 온라인슬롯
도박꾼 카지노 사이트 Best Casino Site Recommendations 카지노사이트
도박꾼 슬롯 사이트 Best Slot Site Recommendations 슬롯사이트
도박꾼 바카라 사이트 Recommended best baccarat site in Korea 바카라사이트
도박꾼 *온라인 바카라 How to play online baccarat 온라인바카라
Best resource on boilers and solid fuel options I’ve seen — kotelinaya.ru.
Play2x – игры с выводом денег
Регистрация на официальном портале Up X
Регистрация в Up X — простой и быстрый процесс. Вам не придется выделять много времени, чтобы стать клиентом сервиса. Создатели платформы позаботились не только о стильном дизайне, но и о том, чтобы она воспринималась интуитивно. Минимализм и продуманный интерфейс — отличная комбинация. С созданием профиля не будет никаких проблем
https://skachatreferat.ru/
I emailed the admin at kotelinaya.ru with a question about zoning and boiler placement — and got a real, detailed reply. That level of support is rare. It’s not just content — it’s a real community of people who understand Russian building conditions.
¡Saludos! Me llamo Kattie, soy de Bollullos Par del Condado provincia de Huelva y trabajo como diseñador gráfico. Estoy casado y tenemos dos hijos, Andrés de 8 años y Laura de 5.
Mirar en mi sitio web – https://wiki.pingwho.org/index.php/QuÃ_Contiene_Un_Batido_Herbalife
Mi nombre es Darcy, resido en Valdés provincia de Principado de Asturias y soy http://Classicalmusicmp3Freedownload.com/ja/index.php?title=%E5%88%A9%E7%94%A8%E8%80%85:BrandyTishler76 ingeniero informático. Estoy casado y tenemos un hijo, Alejandro, que tiene 6 años.
Evcil hayvan sahiplenmek, hayatınıza sevgi, sadakat ve sorumluluk katmanın en güzel yollarından biridir. Kedi ya da köpek sahiplendiğinizde yalnızca bir hayvana yuva açmakla kalmaz, aynı zamanda onunla birlikte birçok duyguyu paylaşacağınız uzun soluklu bir yolculuğa başlarsınız. Sahiplendirme, barınaklarda veya sokakta yaşam mücadelesi veren canlıların hayatını değiştirme fırsatıdır.Sahiplendirme kararı almadan önce kişinin kendi yaşam koşullarını değerlendirmesi büyük önem taşır. Ev ortamı, günlük zaman planı, maddi imkanlar ve hayvana ayrılabilecek ilgi düzeyi mutlaka göz önünde bulundurulmalıdır. Kedi ve köpeklerin bakım ihtiyaçları birbirinden farklıdır. Kediler daha bağımsız olabilirken, köpekler sosyal yapıları gereği daha fazla zaman ve dikkat ister. Bu nedenle sahipleneceğiniz canlının ihtiyaçlarını anlayıp ona uygun bir yaşam sunabilmeniz gerekir. Sahiplendirme süreci çoğu zaman başvuru, görüşme, ev ziyareti gibi adımlardan oluşur. Bu adımlar, hayvanın kalıcı ve güvenli bir yuvaya kavuşmasını sağlamak içindir. Sahiplendirme yapan kişi ya da kurumlar hayvanın geçmişi, sağlık durumu ve mizacı hakkında bilgi verir. Böylece hem siz hem de sahipleneceğiniz can dostunuz daha uyumlu bir başlangıç yaparsınız.
My wife and I are building a small house outside the city, and heating is our biggest concern. kotelinaya.ru offered a balanced comparison of wood vs. pellets, including what’s better long-term and why. They also show diagrams on pipe slope, tank placement, and insulation. That’s real value.
Vergi hukuku sadece uyuşmazlıklar ortaya çıktığında değil, aynı zamanda önleyici hizmetler açısından da büyük önem taşır. İstanbul’da faaliyet gösteren şirketler için vergi planlaması, mali yapının sürdürülebilirliği açısından kritik rol oynar. Bu süreçte İstanbul vergi avukatı, şirketin faaliyet alanına ve mali yapısına uygun vergi stratejileri geliştirerek vergi yükünü azaltmayı hedefler. Doğru bir planlama sayesinde hem yasalara uygun hareket edilir hem de gereksiz vergi ödemelerinin önüne geçilir. Özellikle kurumsal şirketlerde, mali müşavirlerle birlikte çalışan vergi avukatları, şirketin finansal süreçlerini hukuki açıdan güvence altına alır. Transfer fiyatlandırması, örtülü sermaye kullanımı, iştirak kazançlarının vergilendirilmesi gibi teknik konular da bu planlamanın bir parçasıdır. Ayrıca, İstanbul’da sıkça karşılaşılan durumlar arasında yabancı yatırımcıların Türkiye’de şirket kurması ve bu şirketlerin vergi yükümlülüklerinin belirlenmesi yer alır. Bu noktada, hem uluslararası vergi anlaşmalarına hem de yerel mevzuata hâkim bir vergi avukatıyla çalışmak büyük avantaj sağlar. İstanbul vergi avukatları, şirketlerin karşılaşabileceği her türlü vergi riskini öngörerek önleyici hukuk desteği sunar. Bu sayede şirketler, sürpriz vergi cezalarıyla karşılaşmadan faaliyetlerini sürdürebilir.
chicken roads review
Chicken Road: Real Player Feedback
Chicken Road stands out as a gambling game with arcade vibes, attracting users with its easytograsp gameplay, high RTP (98%), and distinctive cashout system. We’ve gathered real player reviews to determine if it’s worth your time.
What Users Appreciate
A lot of gamers appreciate how Chicken Road combines fast gameplay with simple controls. The option to withdraw winnings whenever you want introduces a tactical element, and the high RTP ensures it feels more equitable compared to classic slots. Beginners love the demo mode, which lets them try the game without risking money. Mobile optimization also gets high marks, as the game runs smoothly even on older devices.
Melissa R., AU: “A surprisingly entertaining and fair experience. The cashout function really enhances the gameplay.”
Nathan K., UK: “The arcade style is refreshing. Runs smoothly on my tablet.”
Gamers are also fond of the vibrant, retro aesthetic, making it both enjoyable and captivating.
Areas for Improvement
Despite its strengths, Chicken Road isn’t without flaws. Some players find the gameplay repetitive and lacking depth. Players also point out unresponsive support teams and insufficient features. Misleading ads are another issue, with many assuming it was an arcade game instead of a gambling app.
Tom B., US: “It starts off fun, but the monotony sets in quickly.”
Sam T., UK: “Promoted as entertainment, yet it turns out to be a gambling product.”
Strengths and Weaknesses
Advantages
Simple, fastpaced gameplay
An RTP of 98% guarantees a fair experience
Practice mode to explore without financial risk
Seamless operation on smartphones and tablets
Negative Aspects
The gameplay may come across as monotonous
Limited variety and features
Delayed responses from support teams
Deceptive advertising
Final Verdict
Thanks to its transparency, high RTP, and userfriendliness, Chicken Road makes a mark. It’s a great option for casual players or those new to online gambling. However, its reliance on luck and lack of depth may not appeal to everyone. To maximize enjoyment, stick to authorized, regulated sites.
Rating: Four out of five stars
A balanced blend of fun and fairness, with potential for enhancement.
Küçük Dahiler Akademi’de eğitim programı, çocuklarımızı gelecekteki dünyaya hazırlarken onların 21. yy. becerileri ile donatılmasını hedefler.
Nicely put, Kudos.
Look into my web blog … https://se.frompo.com/
Chicken Road: What Gamblers Are Saying
Chicken Road stands out as a gambling game with arcade vibes, attracting users with its easytograsp gameplay, high RTP (98%), and distinctive cashout system. By analyzing user opinions, we aim to figure out whether this game deserves your attention.
What Users Appreciate
Numerous players commend Chicken Road for its quick, engaging action and userfriendly design. With its cashout feature offering strategy and an RTP of 98%, it feels like a fairer alternative to conventional slot games. The riskfree demo mode has been a favorite among new players, providing a safe way to explore the game. Players also rave about the mobilefriendly design, which performs flawlessly even on outdated gadgets.
Melissa R., AU: “Surprisingly fun and fair! The cashout feature adds strategy.”
Nathan K., UK: “Its arcadeinspired style is a breath of fresh air, and it operates smoothly on my device.”
Players also enjoy the colorful, nostalgic design, which feels both fun and engaging.
Criticisms
While it has many positives, Chicken Road does have some downsides. A number of users feel the gameplay becomes monotonous and lacks complexity. Players also point out unresponsive support teams and insufficient features. Misleading ads are another issue, with many assuming it was an arcade game instead of a gambling app.
Tom B., US: “It starts off fun, but the monotony sets in quickly.”
Sam T., UK: “Marketed as a casual game, but it’s actually a gamblingfocused app.”
Strengths and Weaknesses
Pros
Straightforward, actionpacked mechanics
With a 98% RTP, it offers a sense of equity
Practice mode to explore without financial risk
Smooth performance on mobile devices
Disadvantages
It might feel too predictable over time
Not enough features or modes to keep things fresh
Delayed responses from support teams
Misleading marketing
Final Verdict
Chicken Road stands out with its transparency, high RTP, and accessibility. Ideal for casual gamers or anyone just starting with online gambling. That said, its focus on chance and limited depth might not satisfy all players. To maximize enjoyment, stick to authorized, regulated sites.
Rating: 4/5
An enjoyable and equitable option, though it has areas to grow.
Your article helped me a lot, is there any more related content? Thanks! http://6297611.cryptostarthome.com
Thank you, your article surprised me, there is such an excellent point of view. Thank you for sharing, I learned a lot. http://man-coin-binance.cryptostarthome.com
stratos is a groundbreaking natural supplement crafted to elevate male vitality, energy, and performance.
Your article helped me a lot, is there any more related content? Thanks!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Whoa a good deal of great information.
Feel free to visit my blog post http://server.bitfall.icu:3000/angeline47f233
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Được cộng đồng đánh giá cao, Sunwin luôn dẫn đầu xu hướng game đổi thưởng tại Việt Nam. Trải nghiệm hệ sinh thái giải trí ngay tại sunwin1 bz hôm nay!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
подключить интернет в квартиру казань
domashij-internet-kazan006.ru
интернет тарифы казань
Tải Go88 mang đến không gian giải trí đỉnh cao, đa dạng thể loại game bài. Tải Go88 tại go88-d com để trải nghiệm ngay hôm nay.
Ankara’nın seçkin bölgelerinden Yaşamkent’te yer alan Beytepe Koleji, çağdaş eğitim anlayışıyla öğrencilerini sadece bugüne değil, yarının dünyasına da hazırlıyor
If you are looking for Escort, we provide best high profile Escort for your time and money. We have beautiful and super sexy model girls available for you. Our Escorts team understand that to meet different class of client’s request; our agency working hard to maintain all range of charming female models who specialize in providing Escort services with optimum satisfaction.
We have one of the most popular Karachi Escort. We provide a variety of gorgeous Karachi Escort who are always on call and available to meet you at your home or hotel room within 30 minutes. When you call our Karachi Escorts, we are ready to send you the best Escort Karachi for your needs. All of our Escort make excellent companions for any event and will help you to enjoy your time in Karachi to the fullest.
We are among the most prominent companies for independent Escort service Islamabad. Everything you see on our website is authentic, real photos, and 100% genuine. Customer care representatives who are available 24/7 to answer the needs of customers and handle any discordances.
Truly all kinds of amazing info!
You made your stand quite clearly..
Feel free to visit my page – Online Sports Betting (https://git.palagov.tv/cassandra83x71)
Greetings I am so thrilled I found your weblog, I really found you by accident, while I was searching on Bing for something else, Nonetheless I am here now and would just like to say thanks for a marvelous post and a all round thrilling blog (I also love the theme/design), I don’t have time to browse it all at the minute but I have book-marked it and also included your RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the great work.
Chauffeur service near me
Soy Arron, tengo 23 años y soy de Jaraco provincia de Valencia. En mi tiempo libre, disfruto de la danza, y tengo dos hijos, Pablo de 6 años y Martina de 3. ¡Gracias!
No dudes en visitar mi página web :: https://Azorcn.com/bbs/board.php?bo_table=free&wr_id=2003081
¡Saludos! Me llamo Reed, soy de Los Realejos provincia de Santa Cruz de Tenerife y el pádel es mi gran pasión. Estoy casado y tenemos dos hijos, Andrés de 8 https://shaderwiki.studiojaw.com/index.php?title=User:Susana4412ños y Laura de 5.
Looking for standout corporate event organisers in Dubai? 7 Dreams is your go-to crew for fresh ideas and flawless execution. We take your vision and turn it into unforgettable experiences that connect teams and impress clients. With us, your event will have the energy and style to stand out.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
7, 8, 9. Sınıf Olarak 12 Kişilik Homojen Gruplar, Deneyimli Kadro, Yeni Nesil Yayın Desteği, Birebir Etütler, Ders Çalışma Kütüphaneleri Vardır.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
pakstore.ru has a thorough explanation of using polyurethane foam safely. Their tips on application, safety gear, and cleanup prevented accidents and made insulating my home much easier and more efficient.
Her çocuk biriciktir ve her çocuğun öğrenme biçimi, ilgisi, gelişim süreci farklıdır.
At Rocky Mountain Oils LLC, we believe in the power of nature to support daily wellness. When it comes to caring for your hair, one ingredient stands out for its time-tested benefits: rosemary oil for hair